Applied SCAP Lab: Automating Security Compliance & Remediation
A presentation at Defense in Depth Conference in in Tysons, VA, USA by Shawn Wells

Applied SCAP Lab Automating Security Compliance & Remediation Shawn Wells Office of the Chief Technologist Director, Innovation Programs Red Hat Dave Smith Infosec Engineer / Penetration Tester / OpenSCAP Upstream Maintainer Secure Innovations, LLC ADD NAME (View > Master > Slide master)
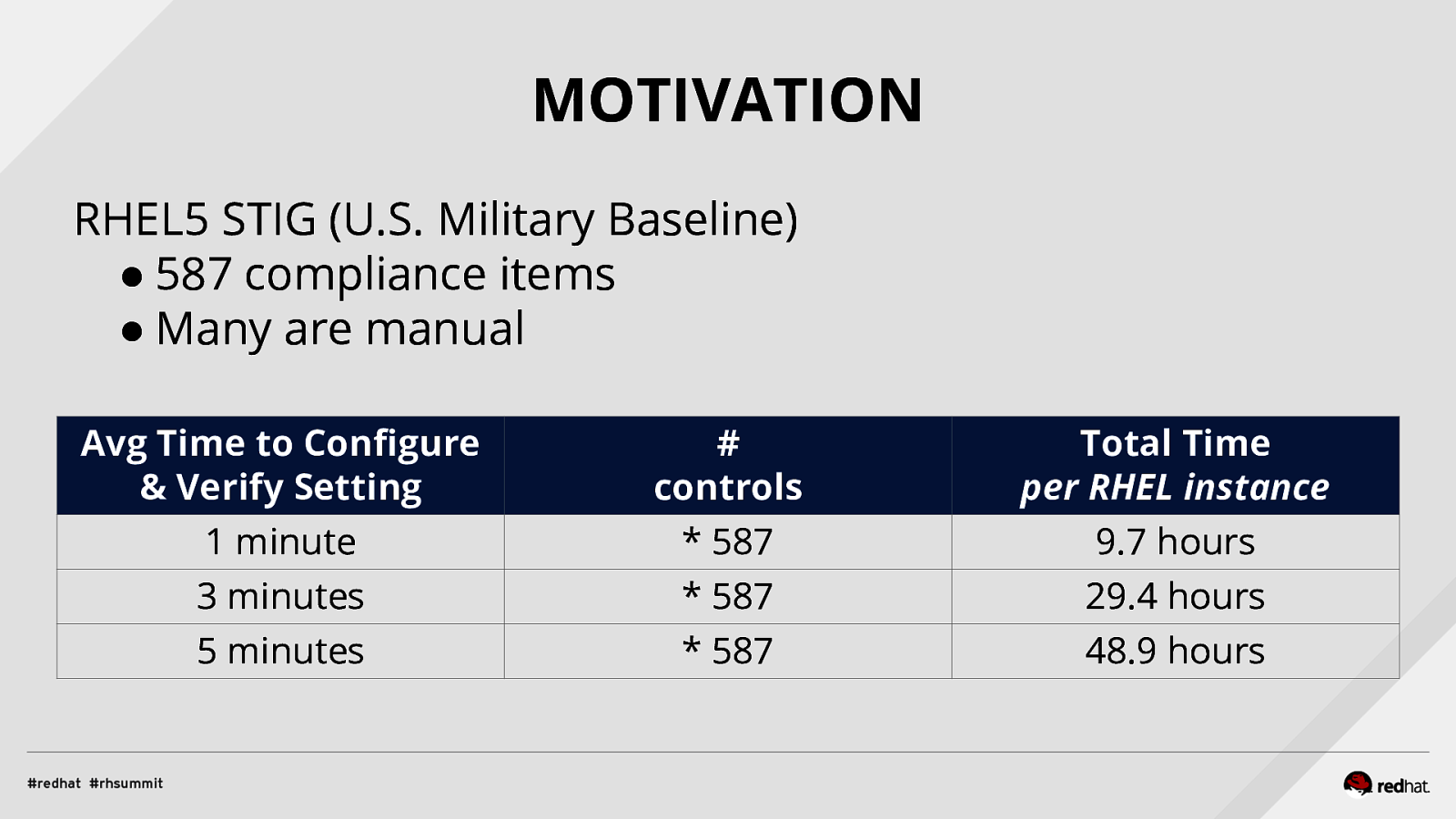
MOTIVATION RHEL5 STIG (U.S. Military Baseline) ● 587 compliance items ● Many are manual Avg Time to Configure & Verify Setting 1 minute 3 minutes 5 minutes
controls * 587 * 587 * 587
Total Time per RHEL instance 9.7 hours 29.4 hours 48.9 hours
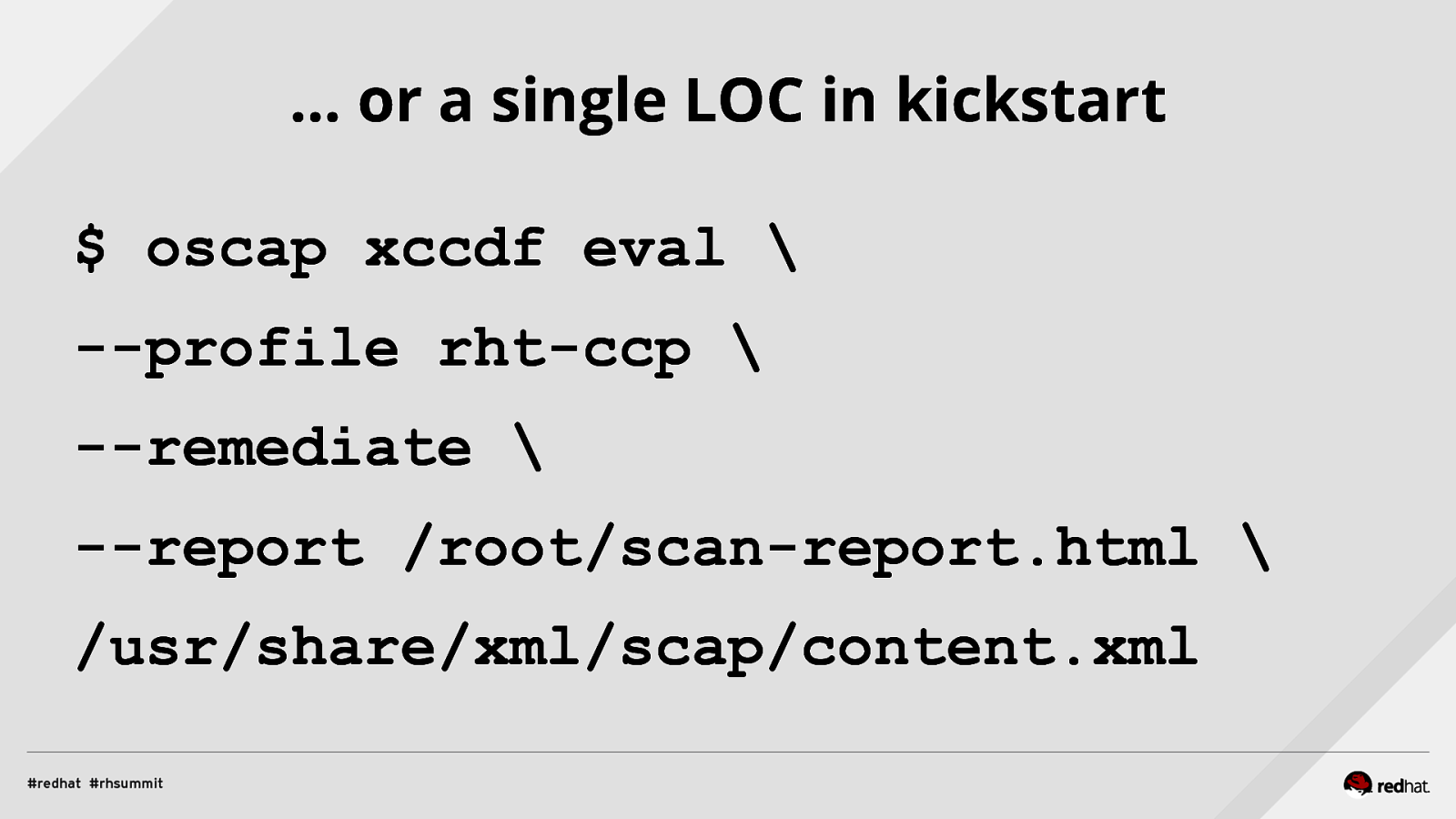
… or a single LOC in kickstart $ oscap xccdf eval \ —profile rht-ccp \ —remediate \ —report /root/scan-report.html \ /usr/share/xml/scap/content.xml

OUR (very ambitious) AGENDA 1.What’s the latest in the Security Automation space? a.Government & Commercial Initiatives b.Formal and Emerging SCAP Standards 2.What tools and content are available today? a.For enumerating (known) software vulnerabilities b.For assessing configuration

LABS 1.Install & Review SCAP profiles in RHEL 7 2.Performing a Compliance Scan 3.System Remediation 4.Creating Custom (derived) Configuration Baselines with SCAP Workbench 5.RHEL 7 “Easy Button” Installations

COMPLIANCE BIG PICTURE: PRODUCTS AND SYSTEMS ADD NAME (View > Master > Slide master)
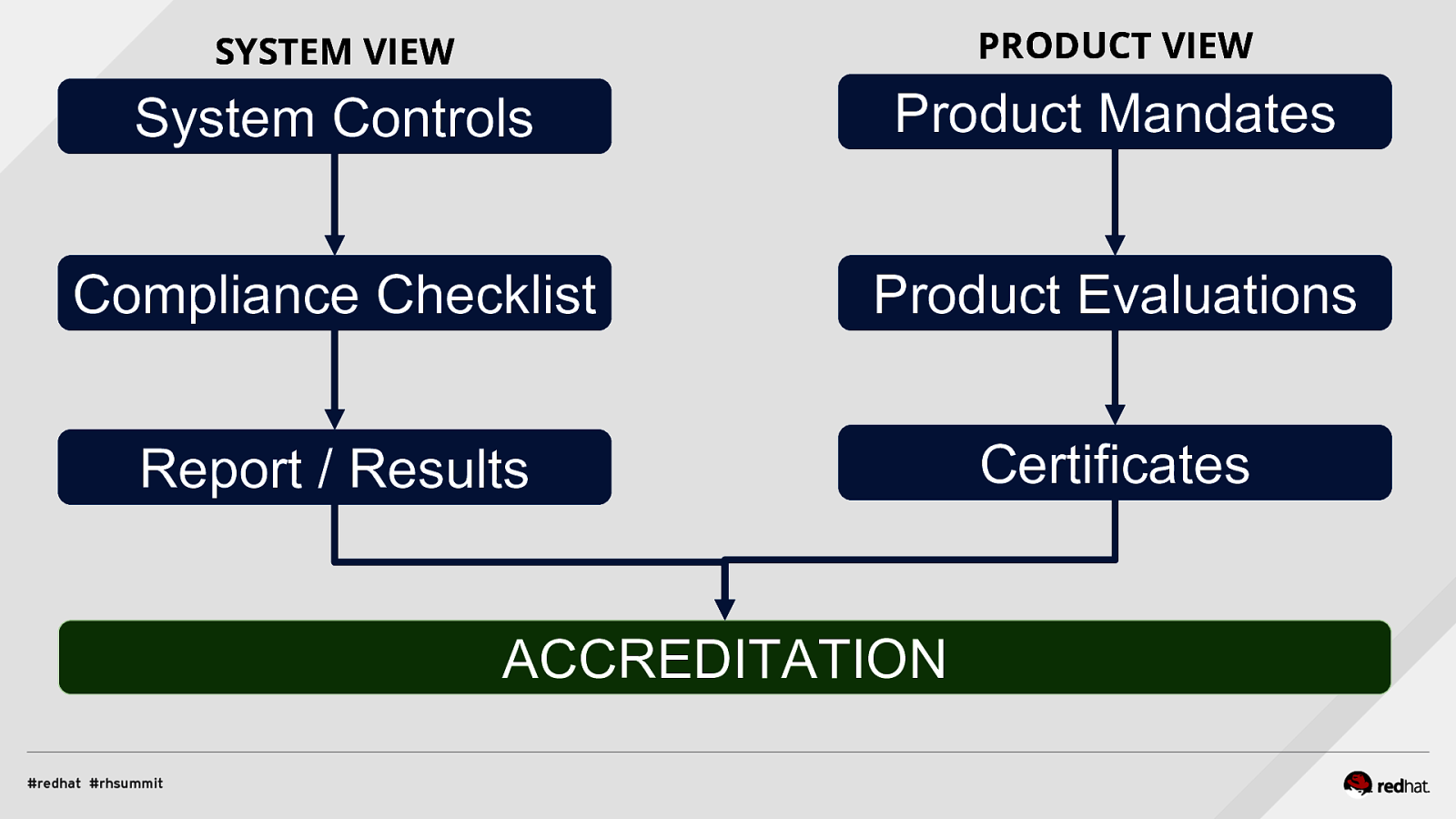
SYSTEM VIEW PRODUCT VIEW System Controls Product Mandates Compliance Checklist Product Evaluations Report / Results Certificates ACCREDITATION
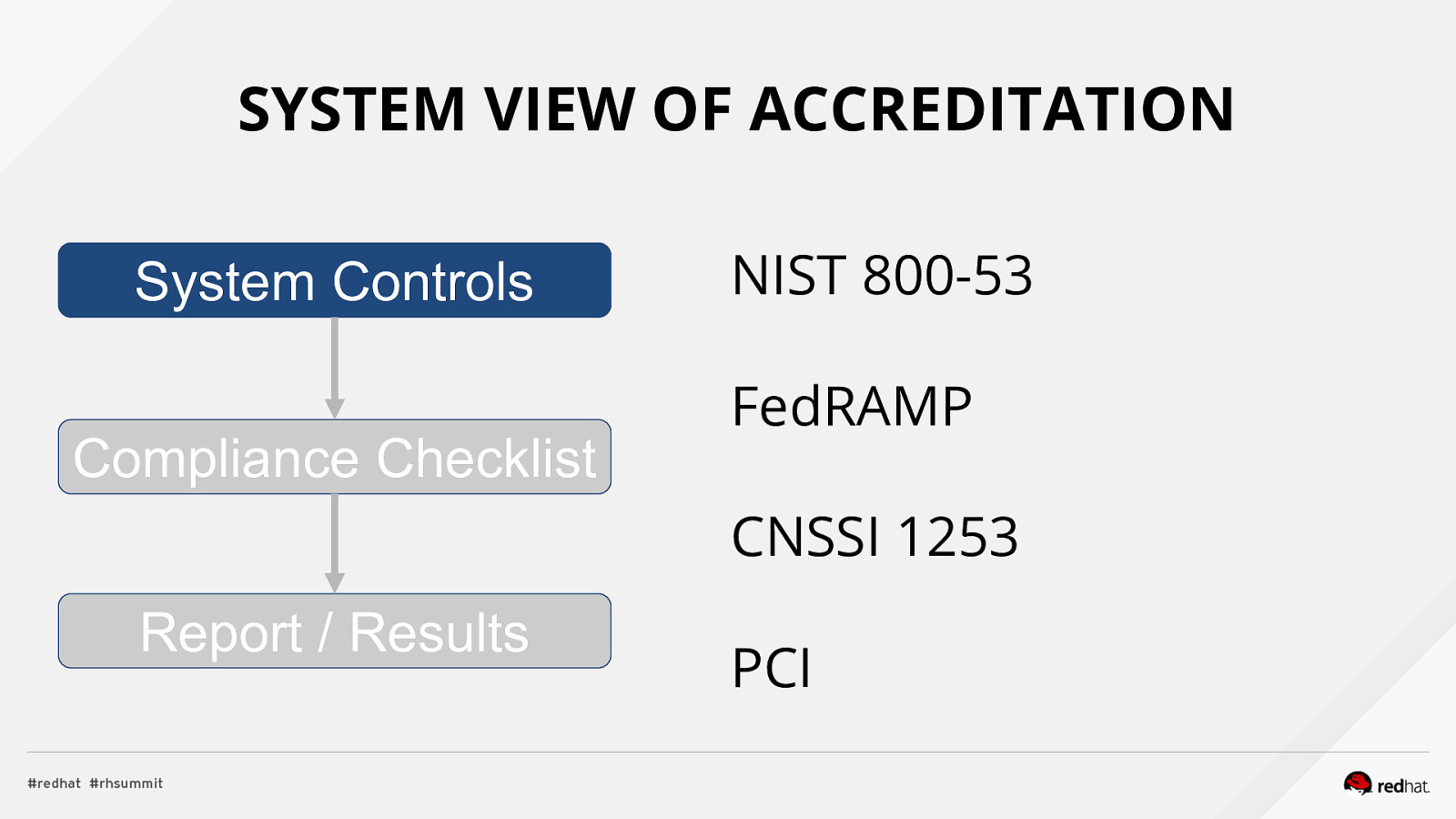
SYSTEM VIEW OF ACCREDITATION System Controls Compliance Checklist NIST 800-53 FedRAMP CNSSI 1253 Report / Results PCI
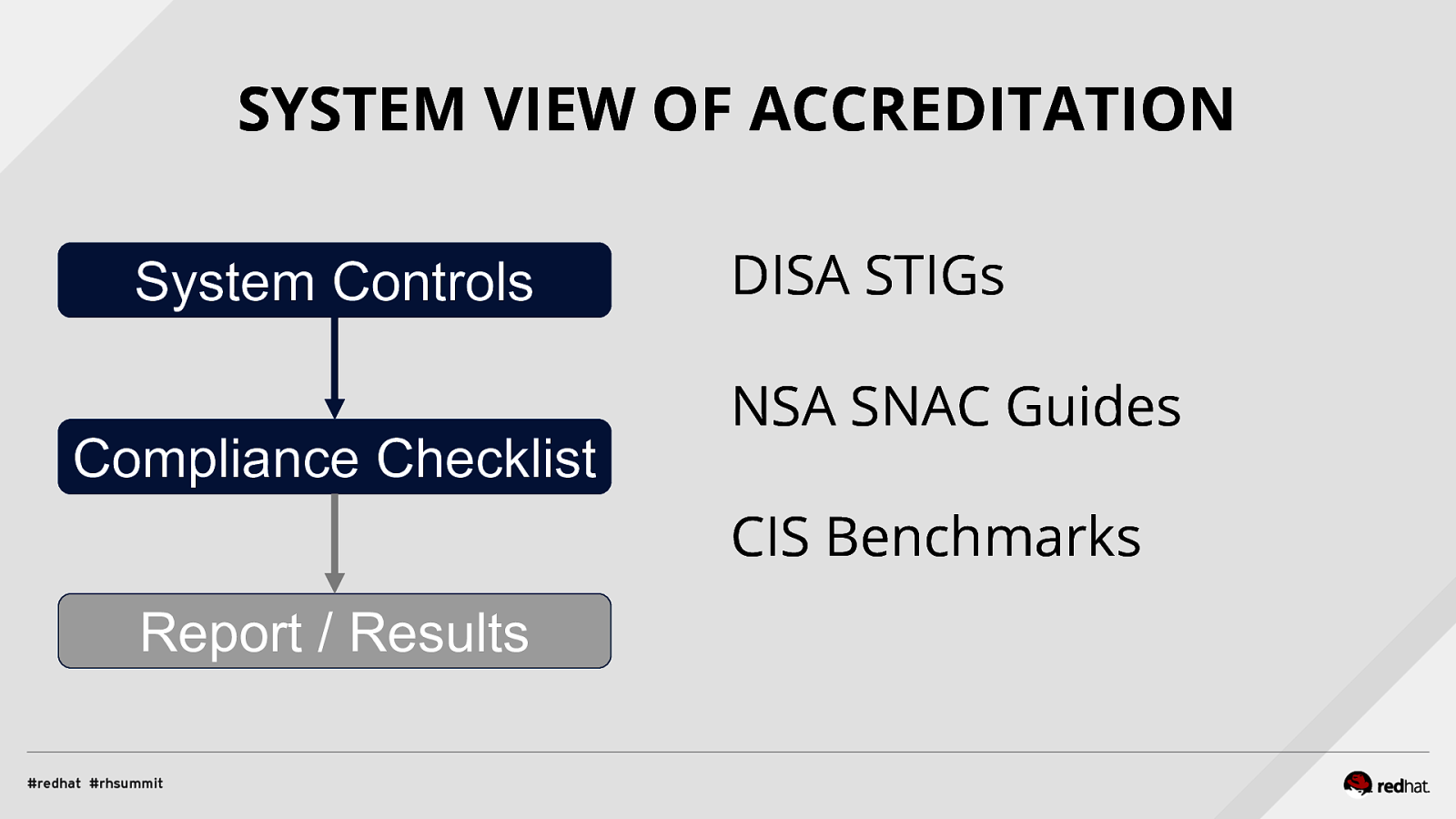
SYSTEM VIEW OF ACCREDITATION System Controls Compliance Checklist DISA STIGs NSA SNAC Guides CIS Benchmarks Report / Results
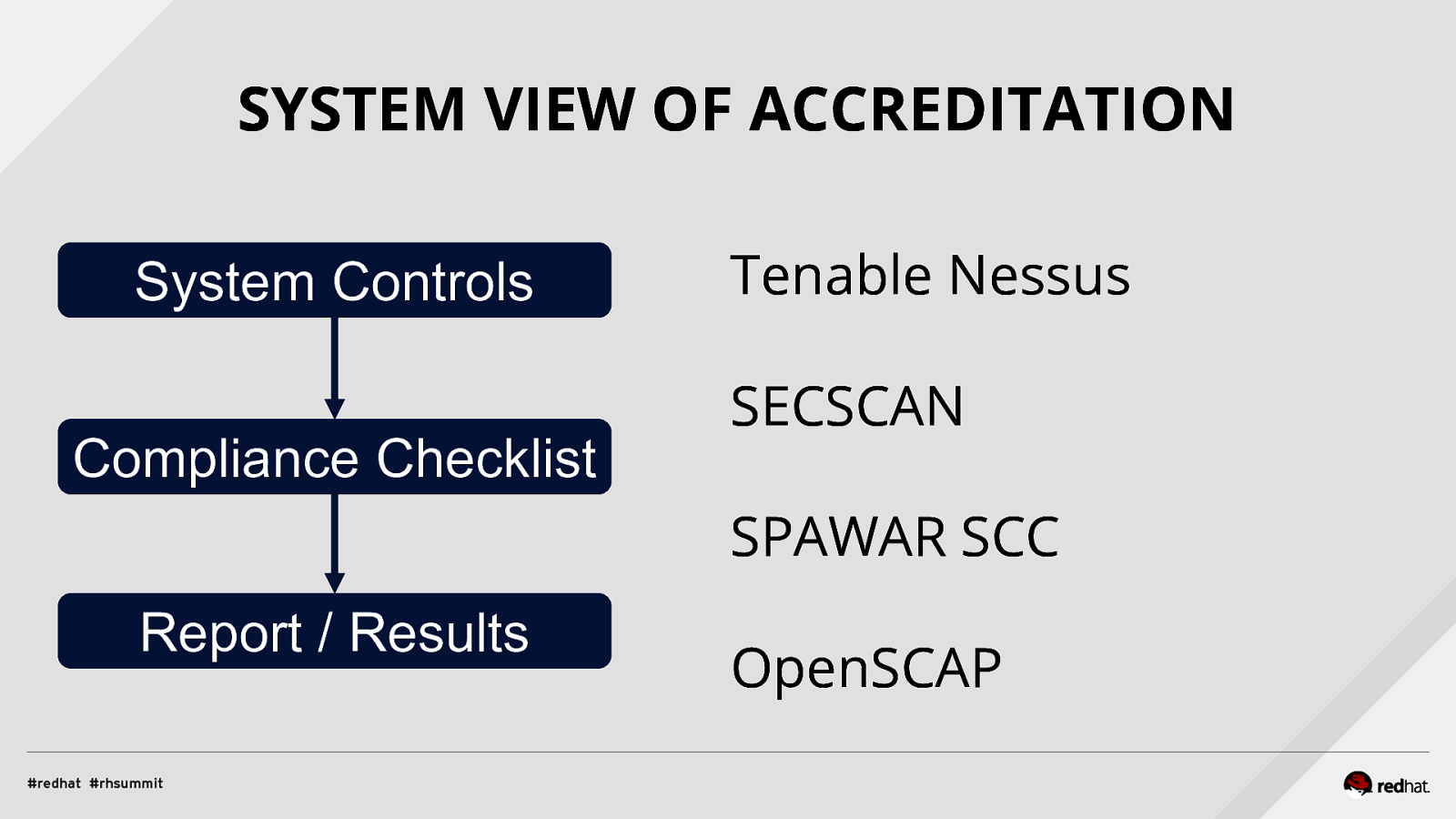
SYSTEM VIEW OF ACCREDITATION System Controls Compliance Checklist Tenable Nessus SECSCAN SPAWAR SCC Report / Results OpenSCAP
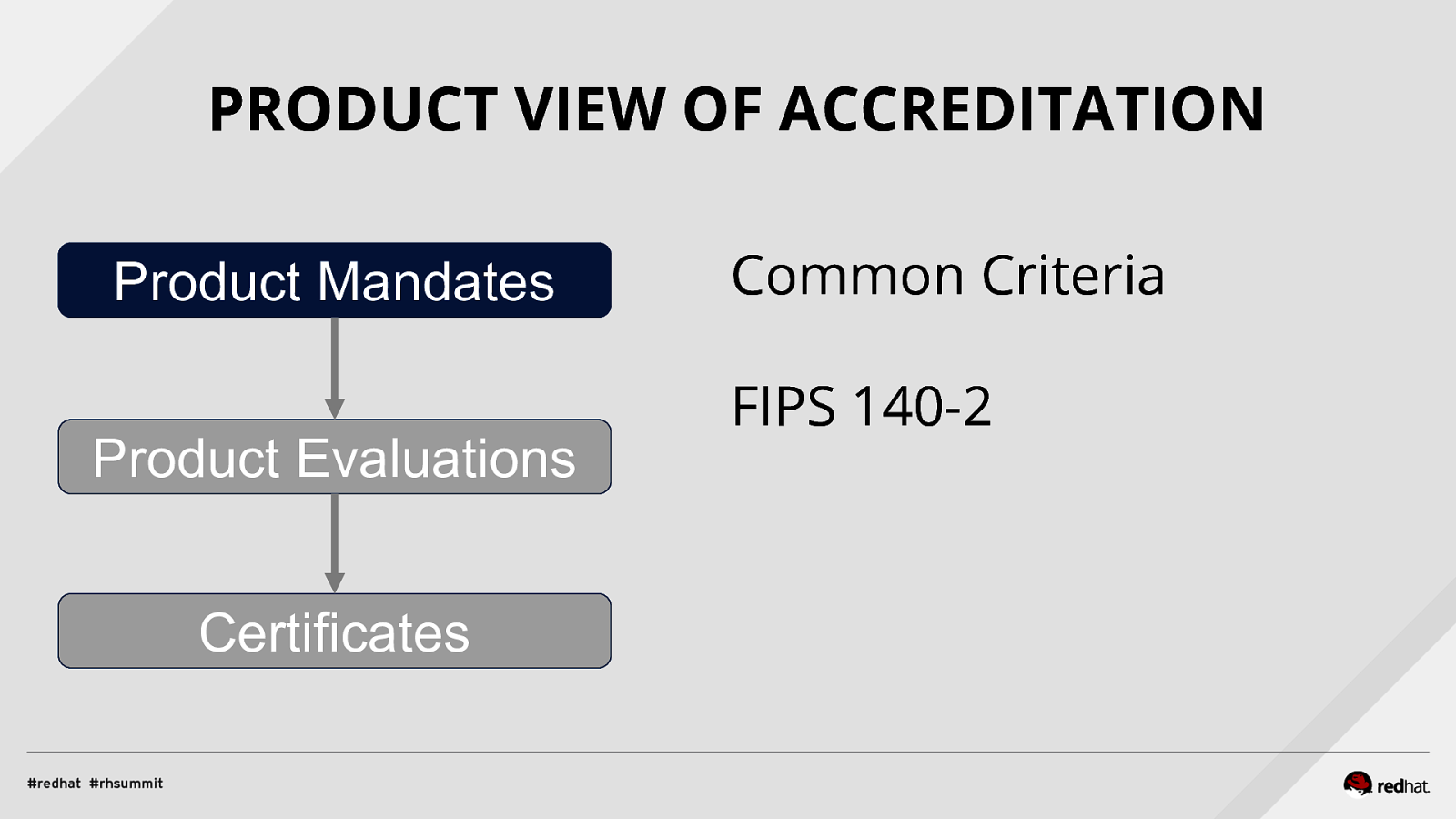
PRODUCT VIEW OF ACCREDITATION Product Mandates Product Evaluations Certificates Common Criteria FIPS 140-2

…. wait… what’s COMMON CRITERIA? - international framework for specifying and testing security functional and assurance requirements in IT products - through the use of Protection Profiles (PPs) - vendors can then implement and/or make claims about the security attributes of their products, and testing laboratories can evaluate the products to determine if they actually meet the claims.
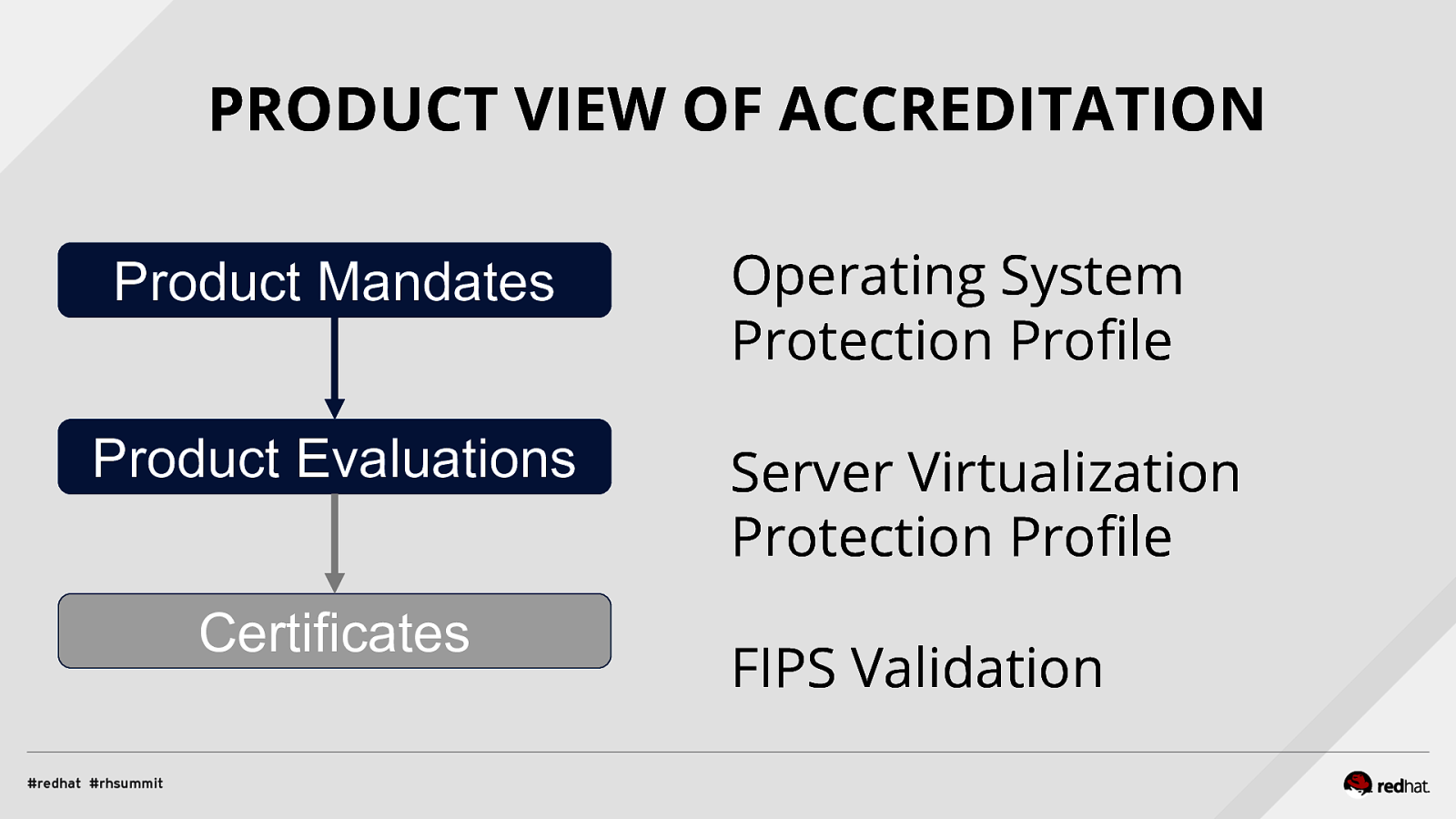
PRODUCT VIEW OF ACCREDITATION Product Mandates Product Evaluations Certificates Operating System Protection Profile Server Virtualization Protection Profile FIPS Validation
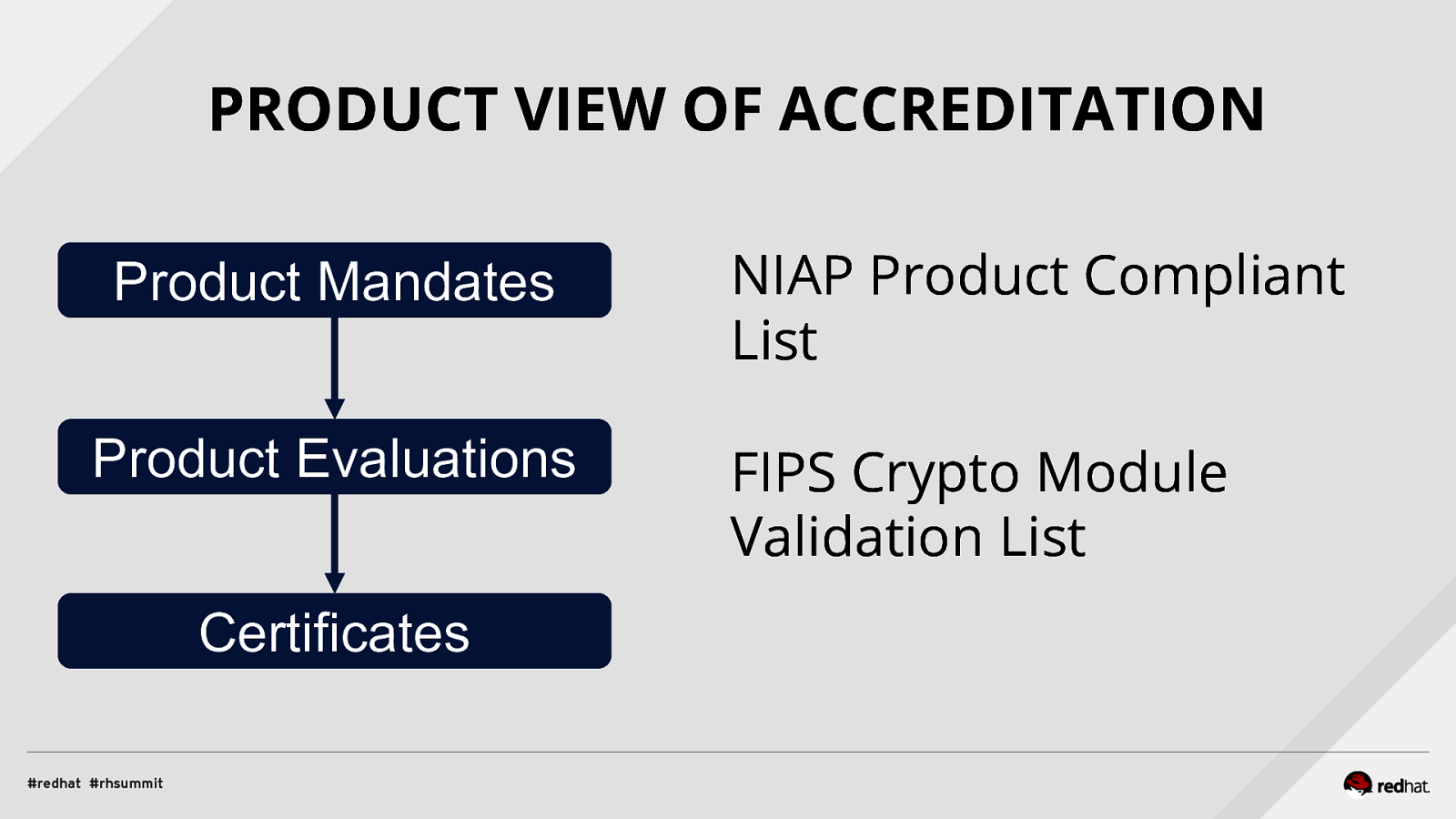
PRODUCT VIEW OF ACCREDITATION Product Mandates Product Evaluations Certificates NIAP Product Compliant List FIPS Crypto Module Validation List
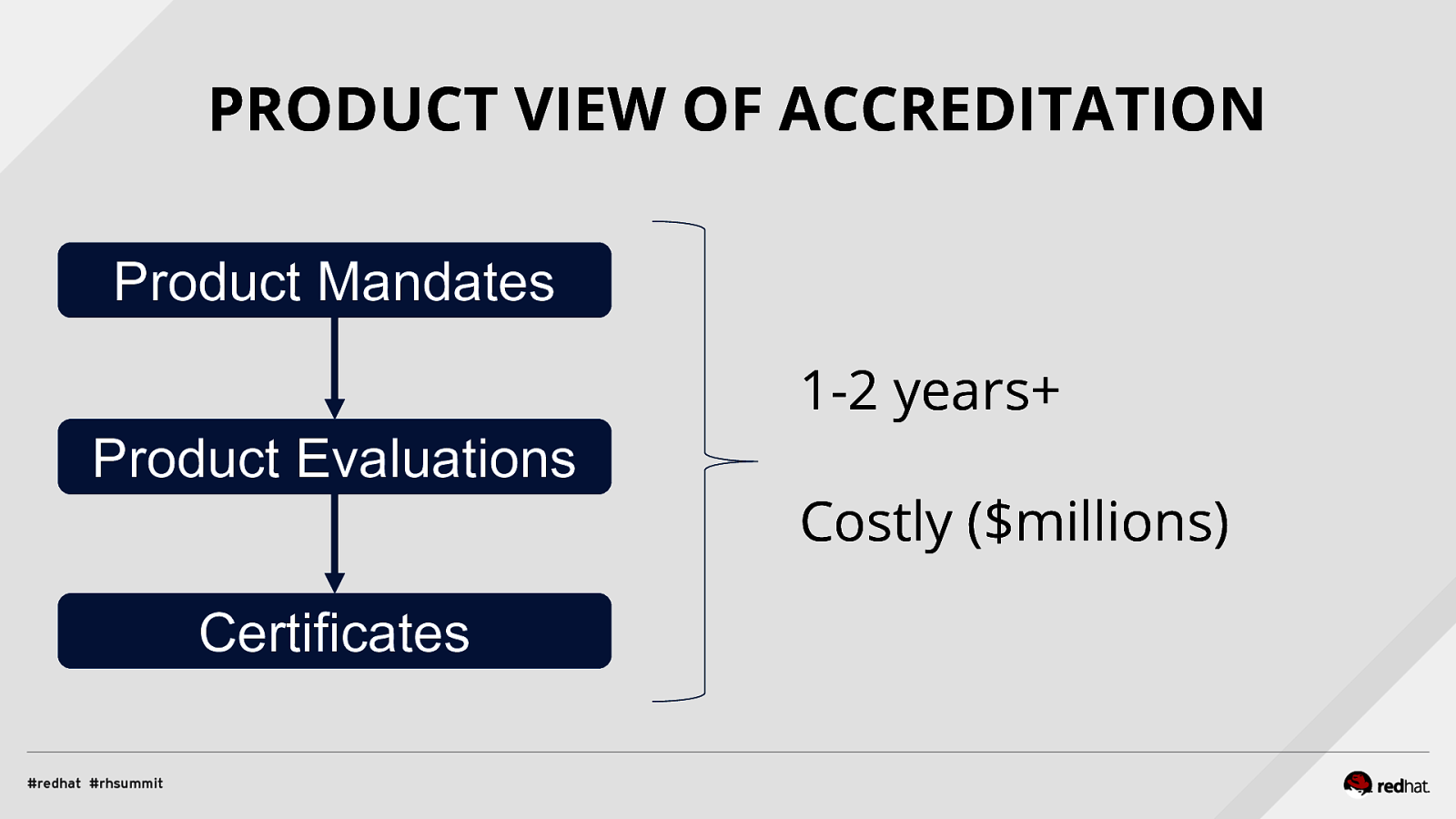
PRODUCT VIEW OF ACCREDITATION Product Mandates 1-2 years+ Product Evaluations Certificates Costly ($millions)

COMMON CRITERIA - REVAMPED ● Requirements specified in Protection Profiles ■ see https://www.niap-ccevs.org ■ development on https://github.com/commoncriteria ■ revamped OS Protection Profile due this July ● Dramatically reduced evaluation time and cost ■ 90 days possible, 180 max ■ compliance checklist produced during evaluation (SCAP) ■ list of system controls provided for evaluated products
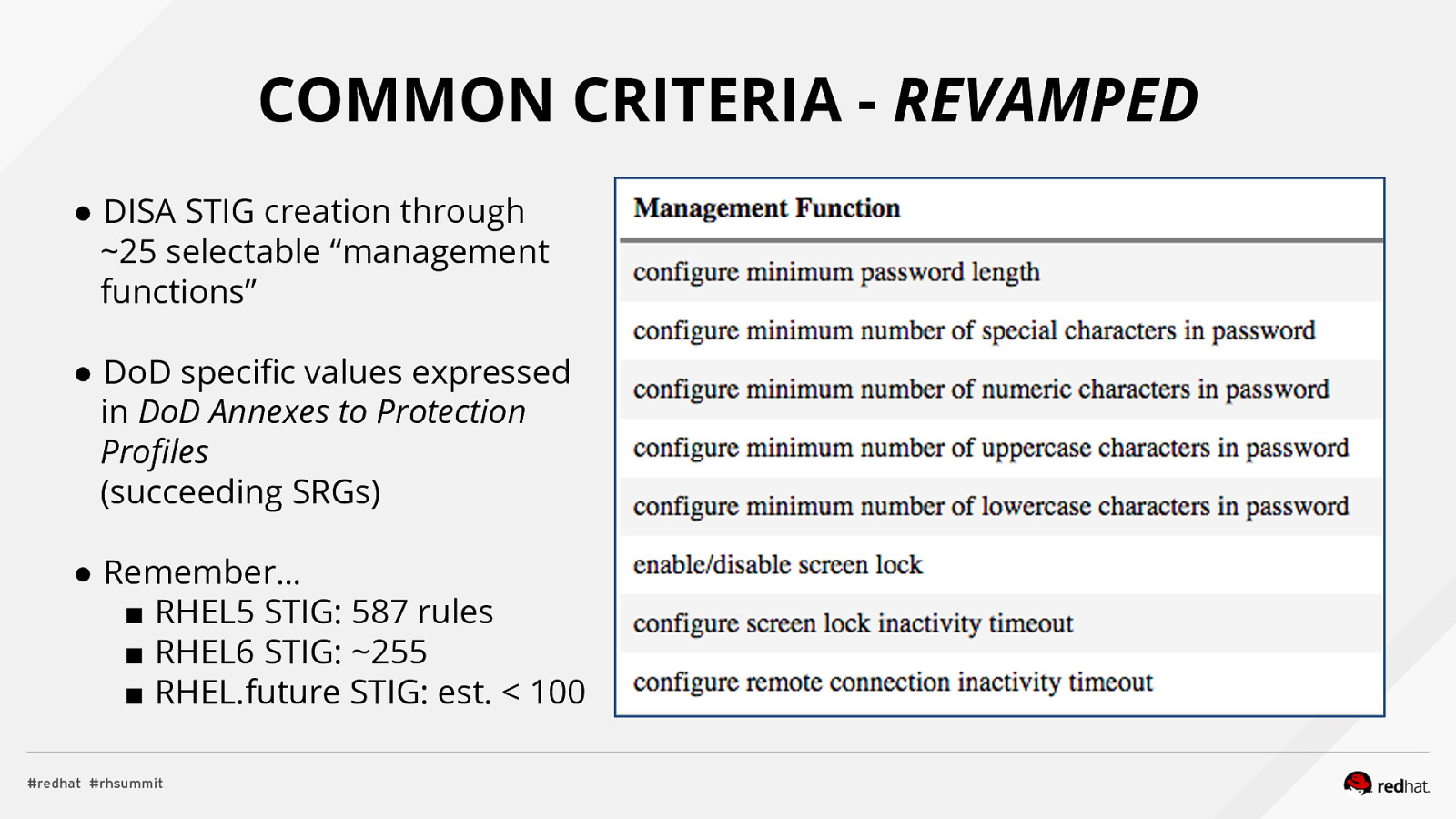
COMMON CRITERIA - REVAMPED ● DISA STIG creation through ~25 selectable “management functions” ● DoD specific values expressed in DoD Annexes to Protection Profiles (succeeding SRGs) ● Remember… ■ RHEL5 STIG: 587 rules ■ RHEL6 STIG: ~255 ■ RHEL.future STIG: est. < 100
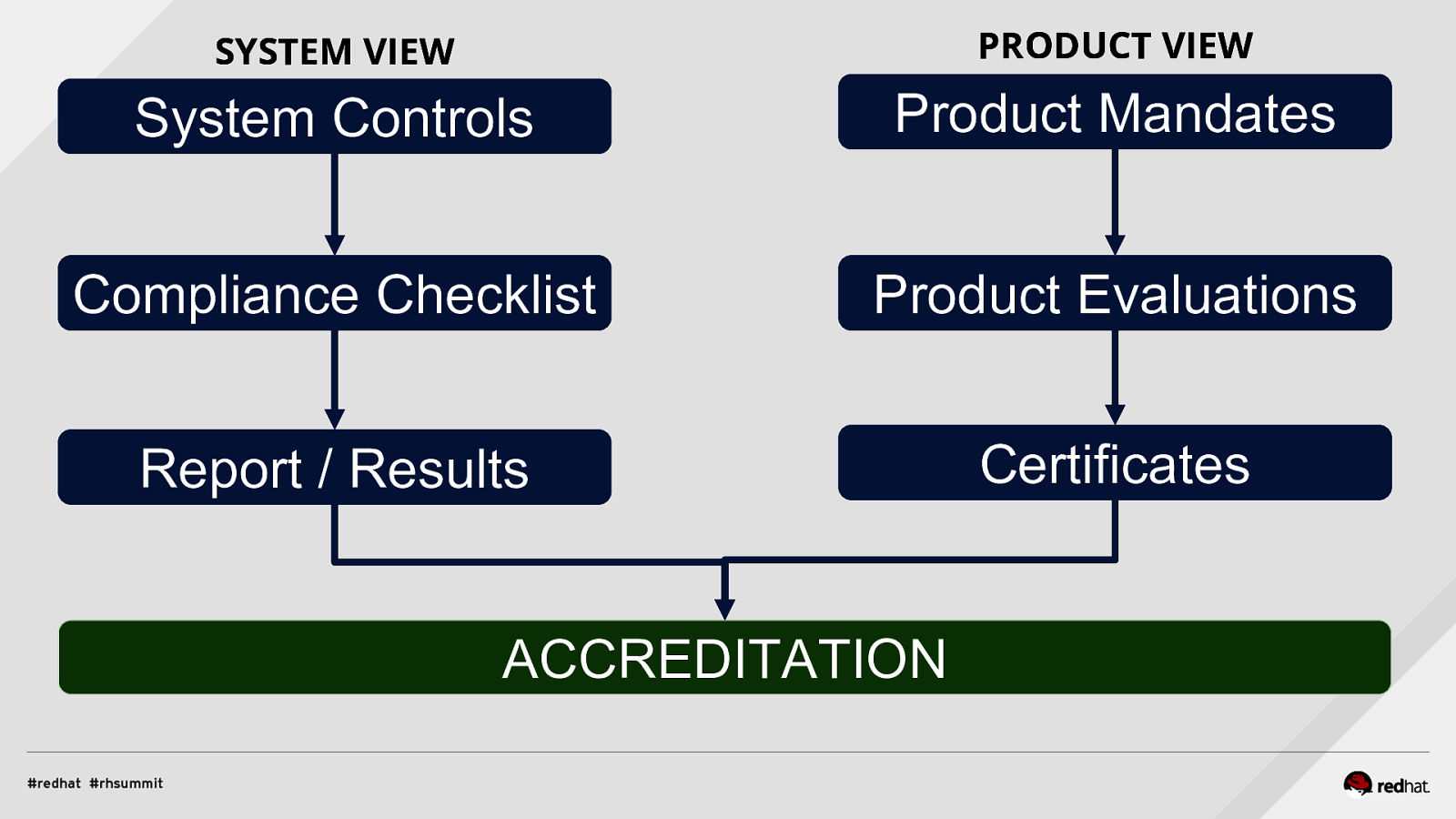
SYSTEM VIEW PRODUCT VIEW System Controls Product Mandates Compliance Checklist Product Evaluations Report / Results Certificates ACCREDITATION

OPEN SOURCE CONFRONTS THE C&A CHALLENGE: SYSTEM COMPLIANCE ADD NAME (View > Master > Slide master)

Community created portfolio of tools and content to assess systems for known vulnerabilities. https://github.com/OpenSCAP
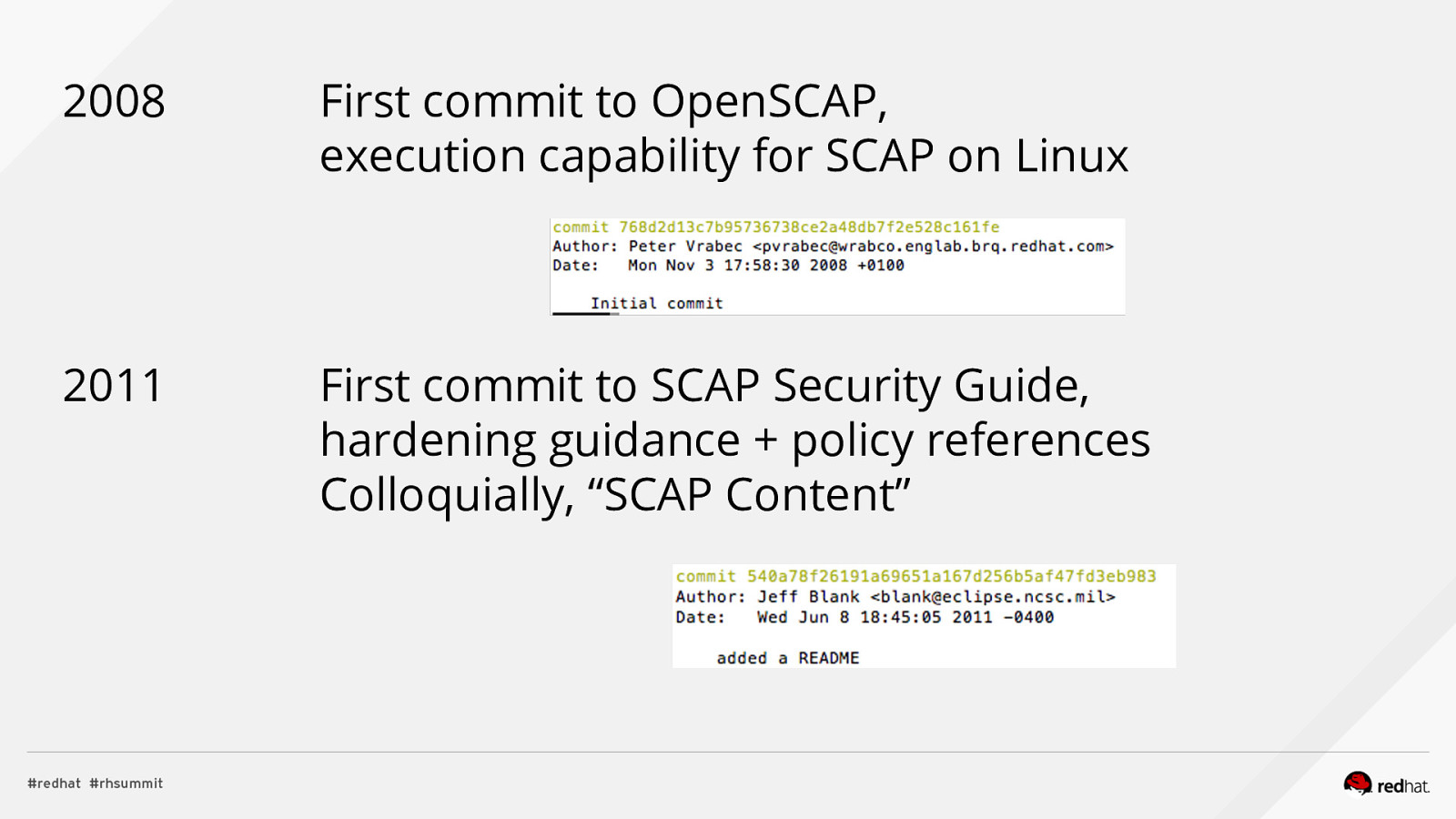
2008 First commit to OpenSCAP, execution capability for SCAP on Linux 2011 First commit to SCAP Security Guide, hardening guidance + policy references Colloquially, “SCAP Content”


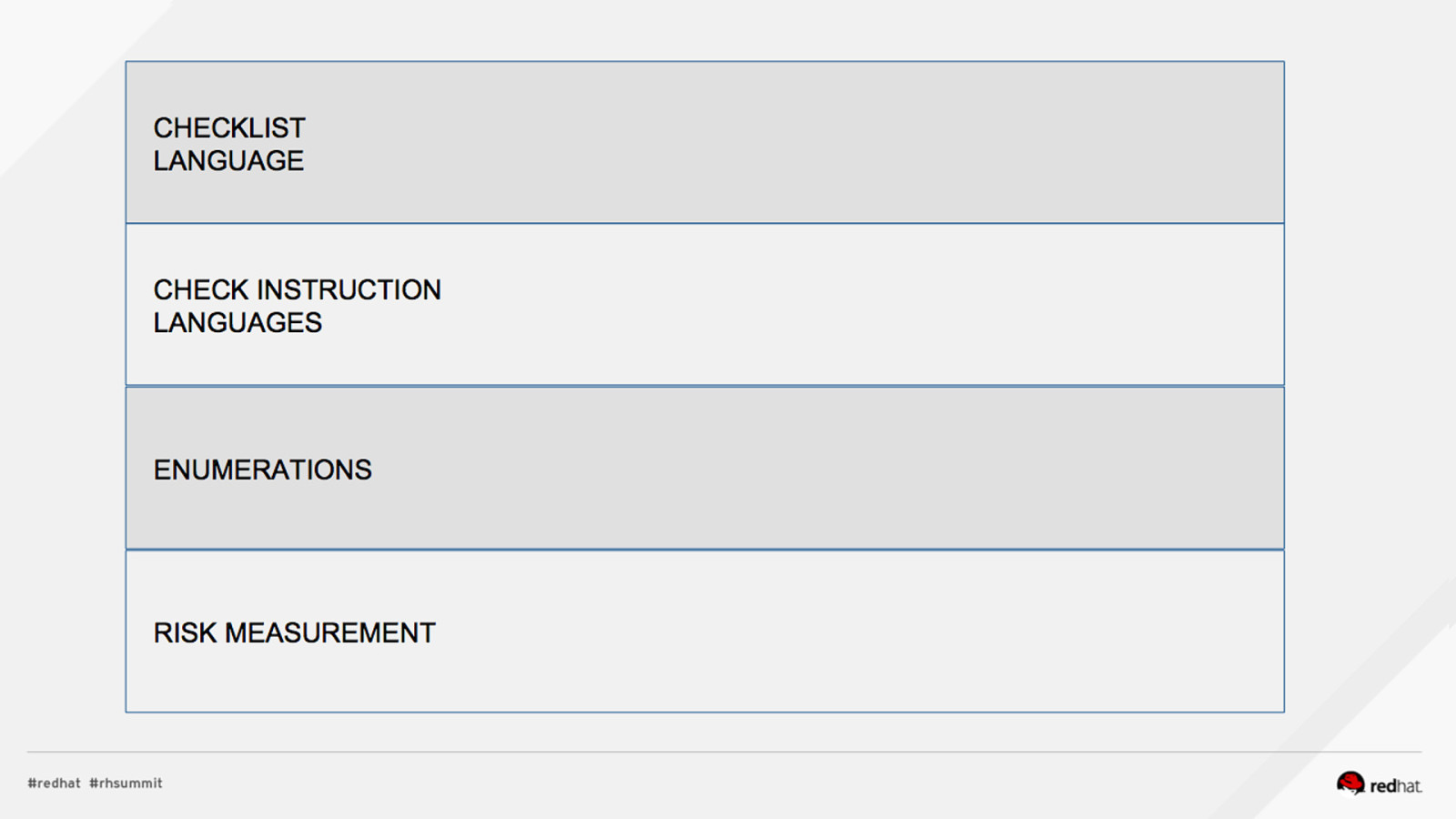
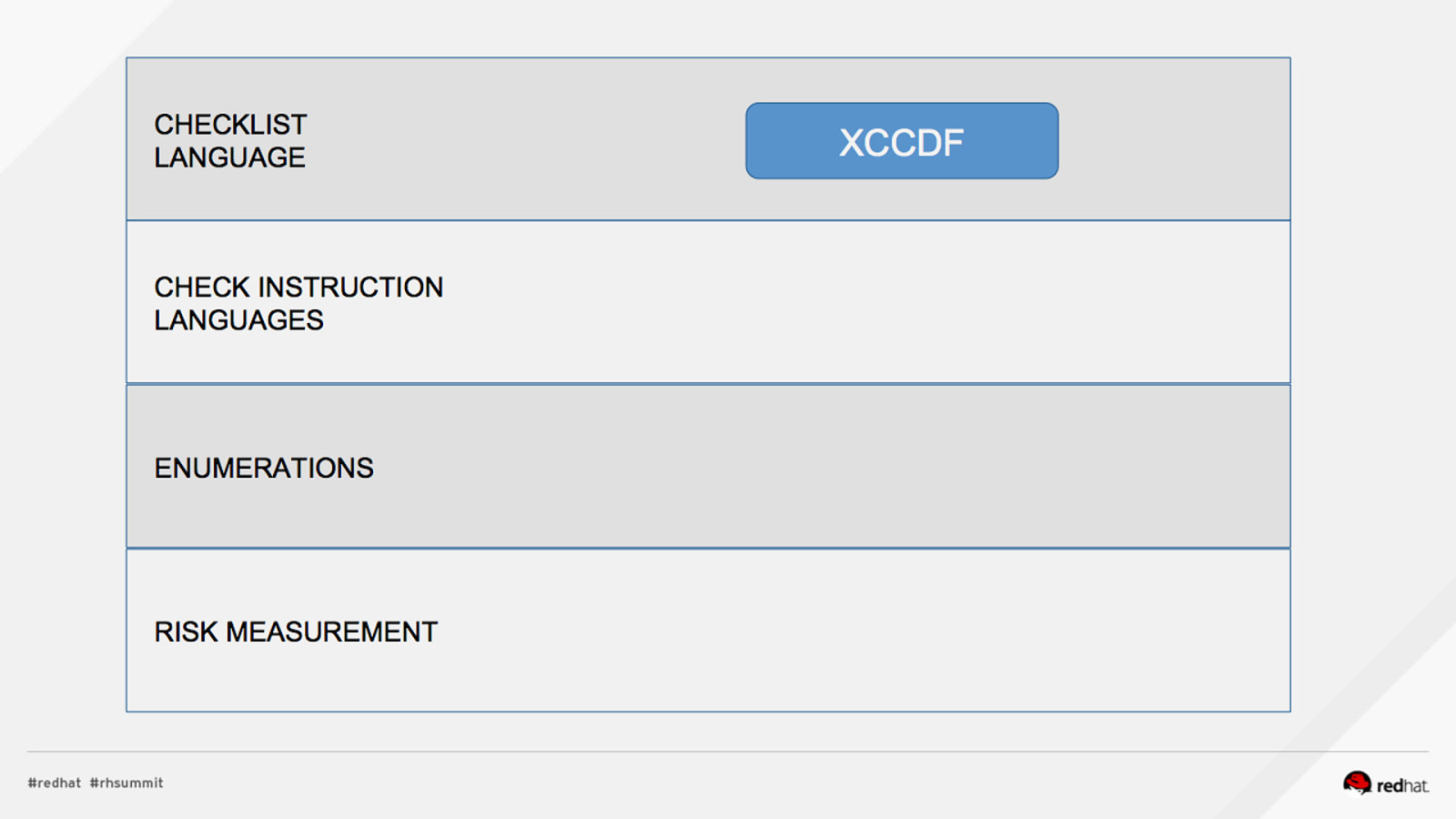
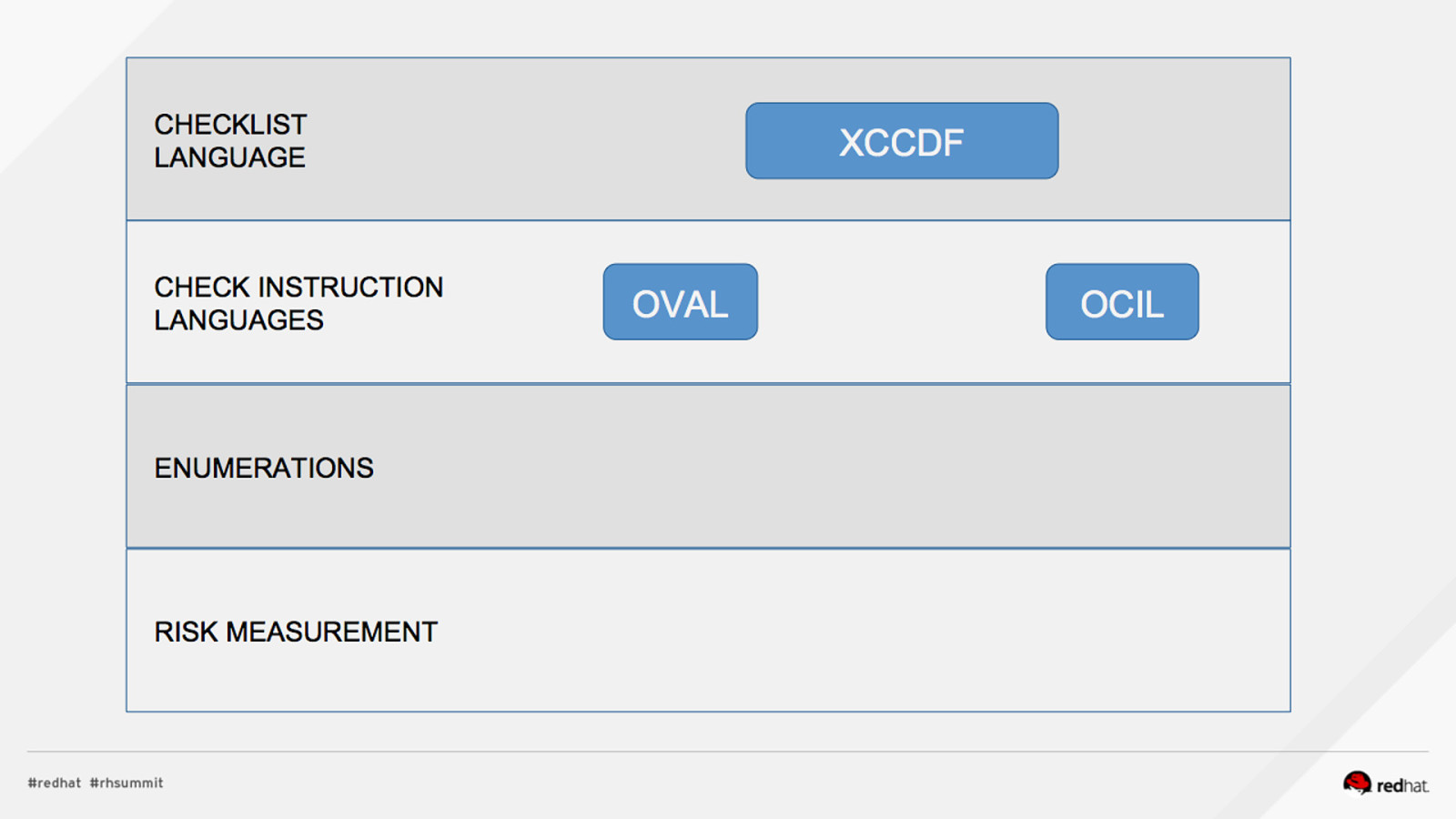
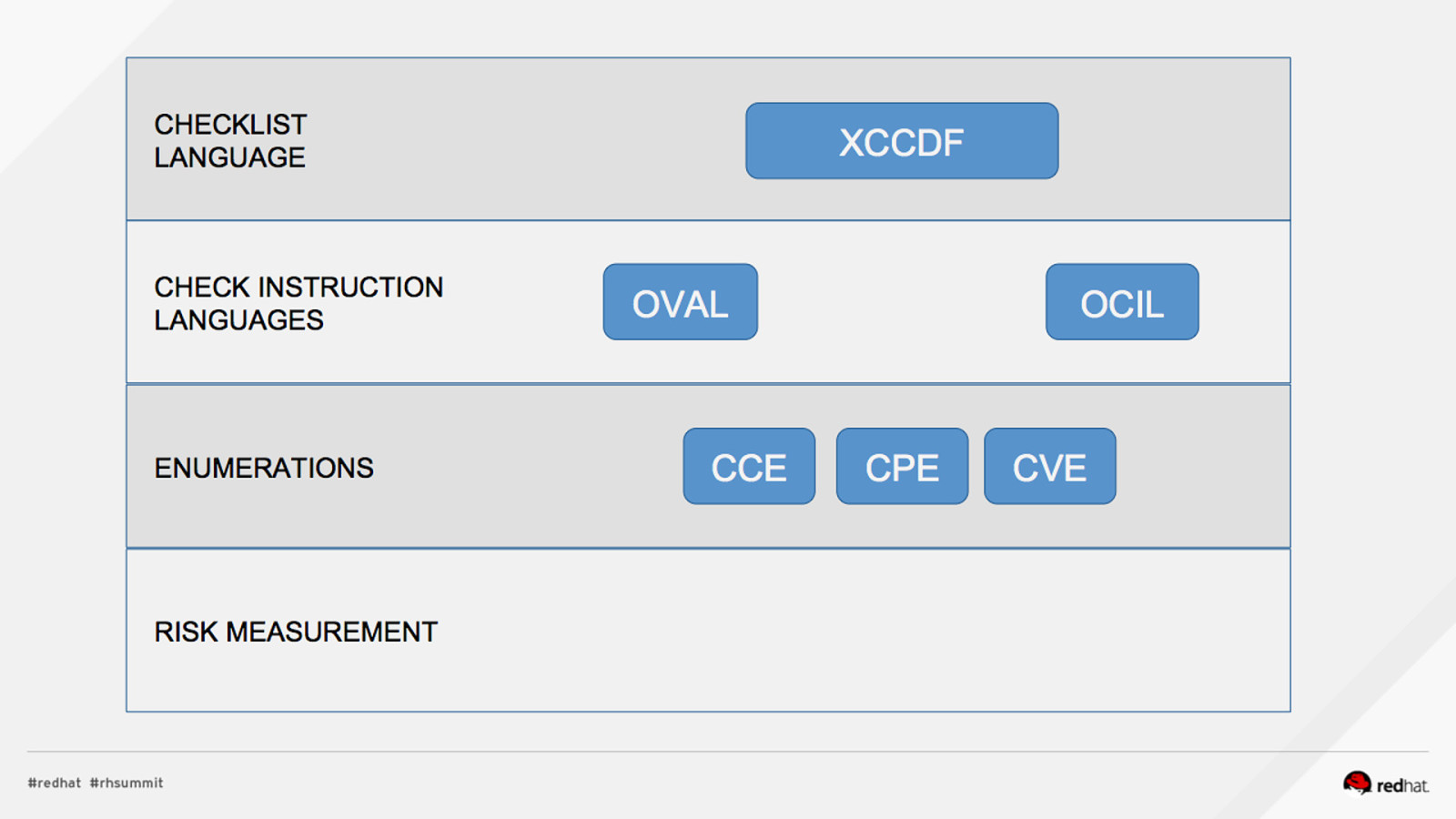
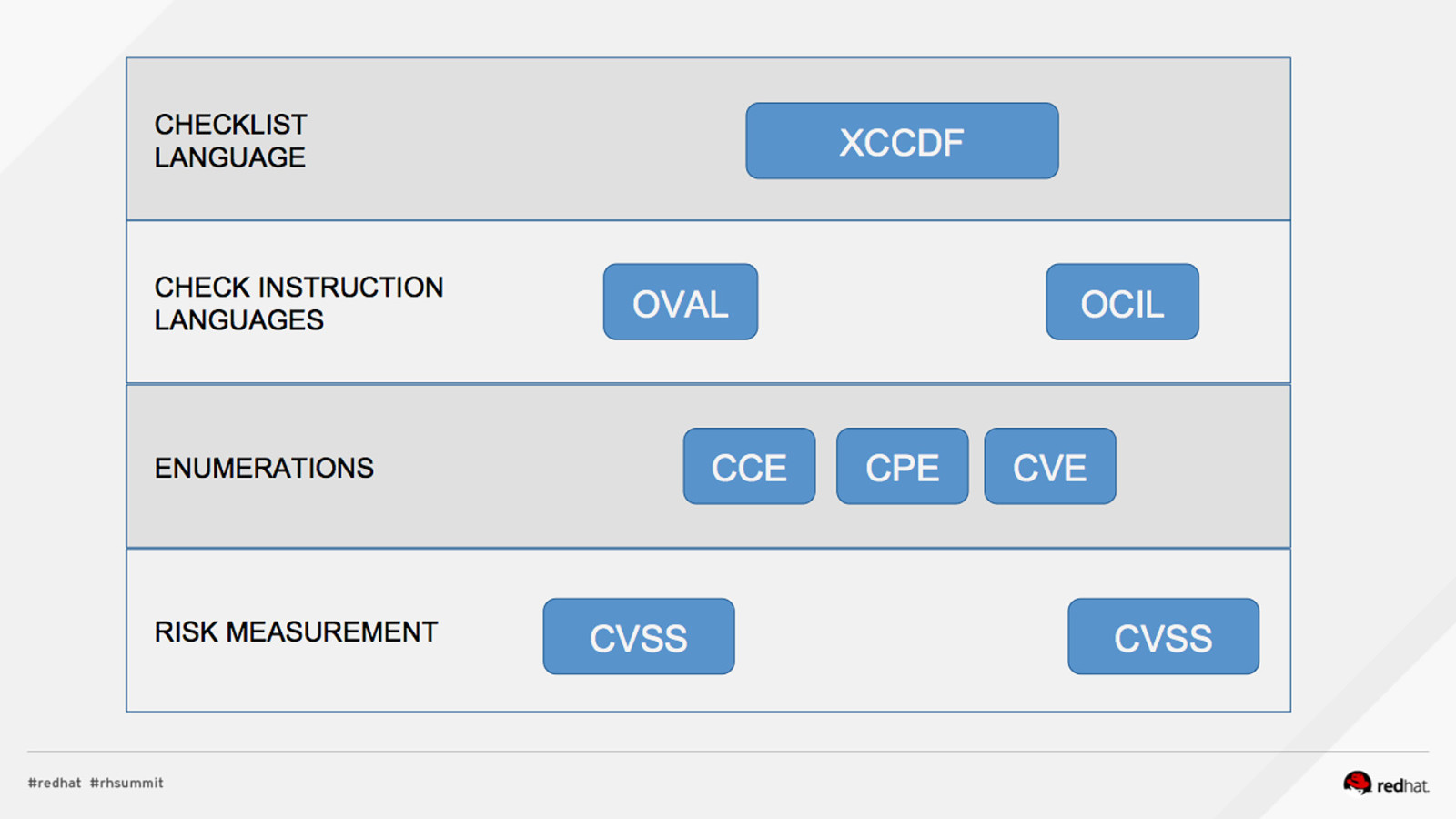
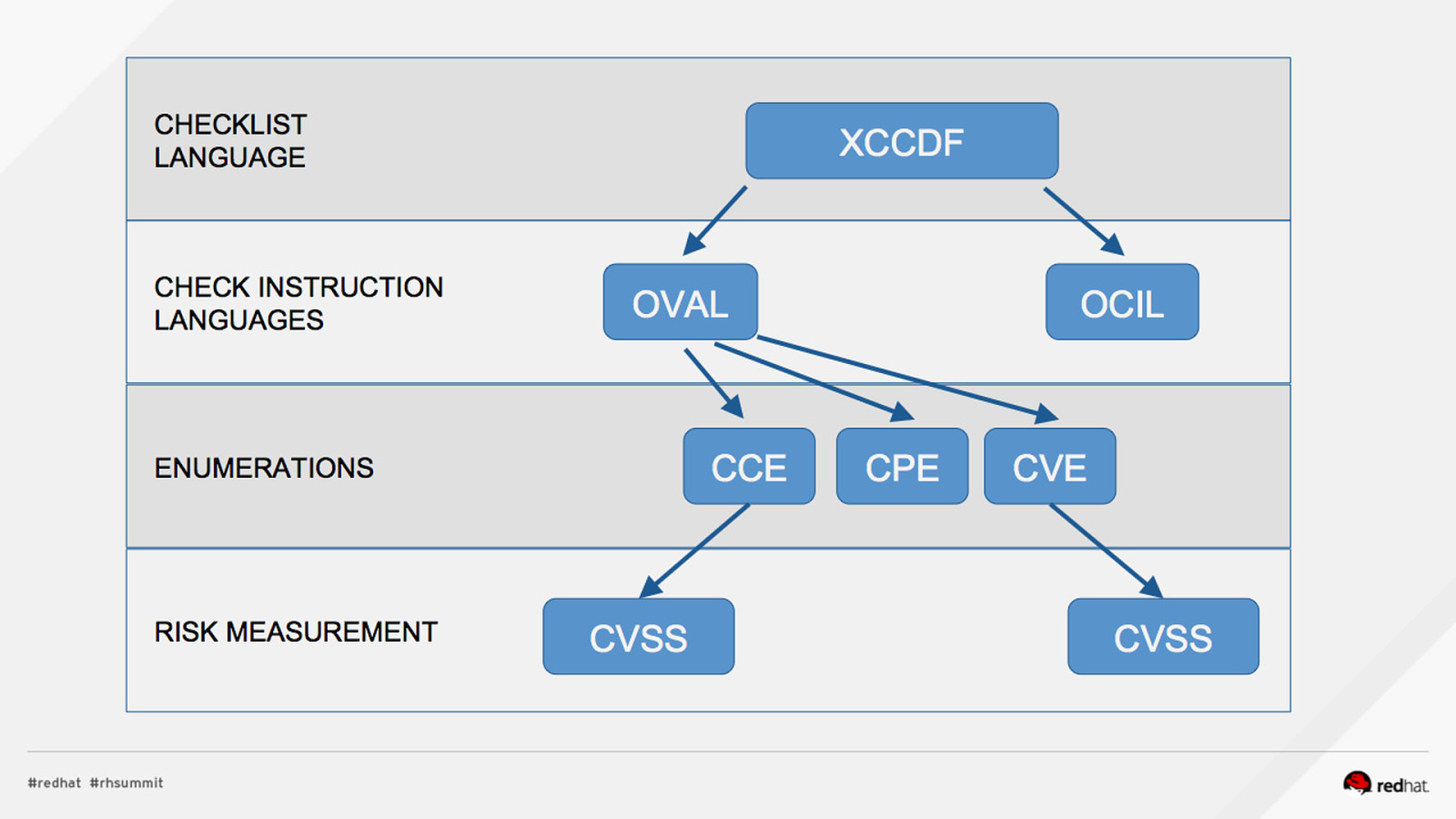


DEMO #1: INSTALL, REVIEW PROFILES Install OpenSCAP and SCAP Content $ sudo yum install openscap-scanner scap-security-guide What default profiles exist? $ oscap info /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml …. Profiles: pci-dss rht-ccp common stig-rhel7-server-upstream ….

DEMO #2: REVIEW HARDENING GUIDES Review manpage $ man scap-security-guide Review HTML gudes $ ls -l /usr/share/doc/scap-security-guide/rhel7-guide.html

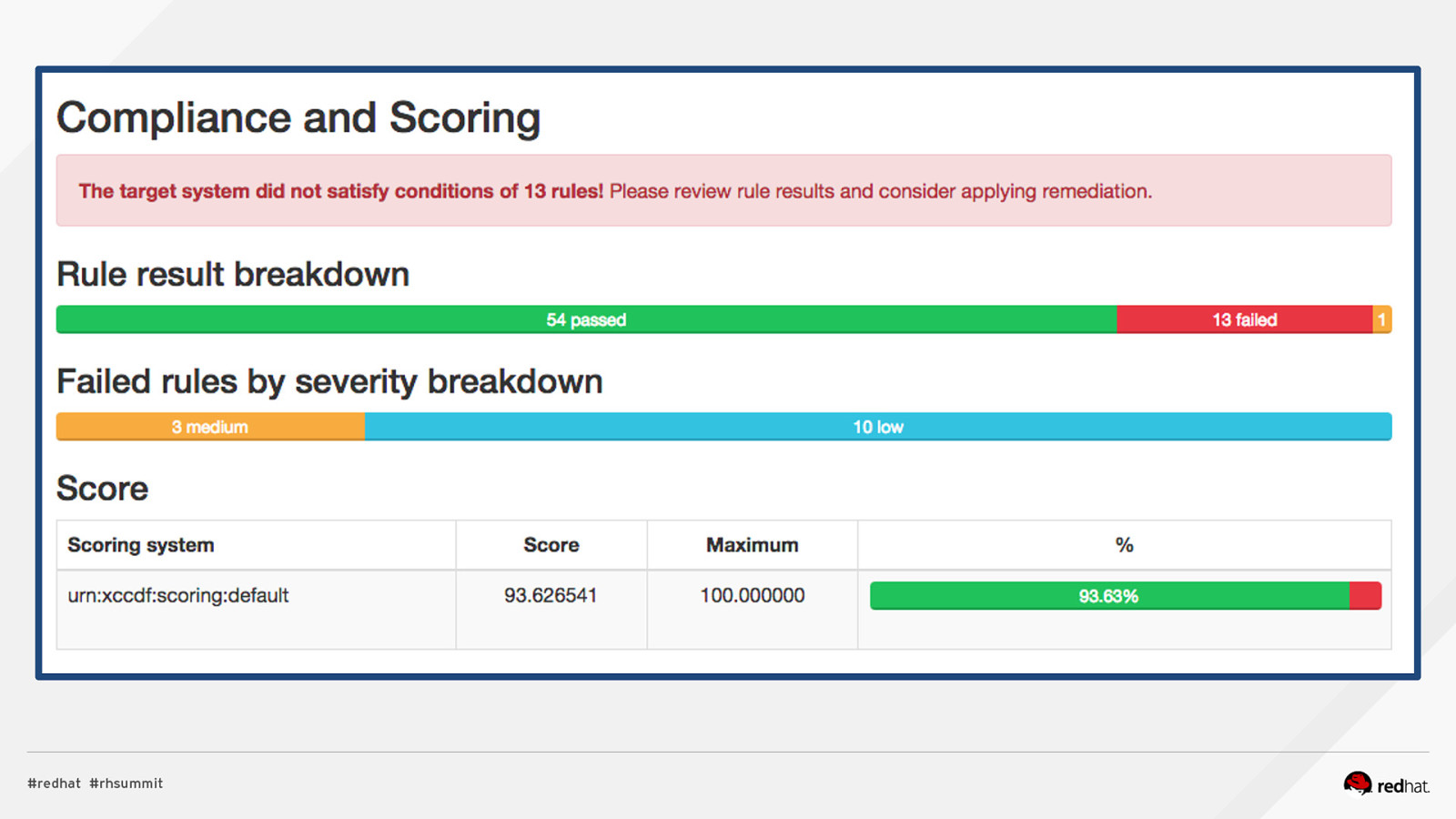
DEMO #3: LOCAL SCAN, REVIEW RESULTS Perform 1st Scan $ sudo oscap xccdf eval —profile rht-ccp \ —results /root/afternoon-results.html \ —report /root/afternoon-report.xml \ /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml Review Results $ ${web_browser} /root/afternoon-results.html
DEMO #4: REMEDIATION Generate remediation scripts from results $ sudo oscap xccdf generate fix \ —result-id xccdf_org.open-scap_testresult_rht-ccp \ /root/afternoon-results.xml Or, remediate automatically (be careful - no “undo”!) $ sudo oscap xccdf eval —profile rht-ccp \ —results /root/afternoon-results.xml \ —report /root/afternoon-report.xml \ —remediate \ /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml
DEMO #5: SCAP WORKBENCH Download SCAP Workbench $ sudo yum -y install scap-workbench Much of this demo is live. For extra details, https://open-scap.org
Hands on lab that instructed attendees on how to use the SCAP Security Guide project to perform compliance scans of Red Hat Enterprise Linux hosts.
