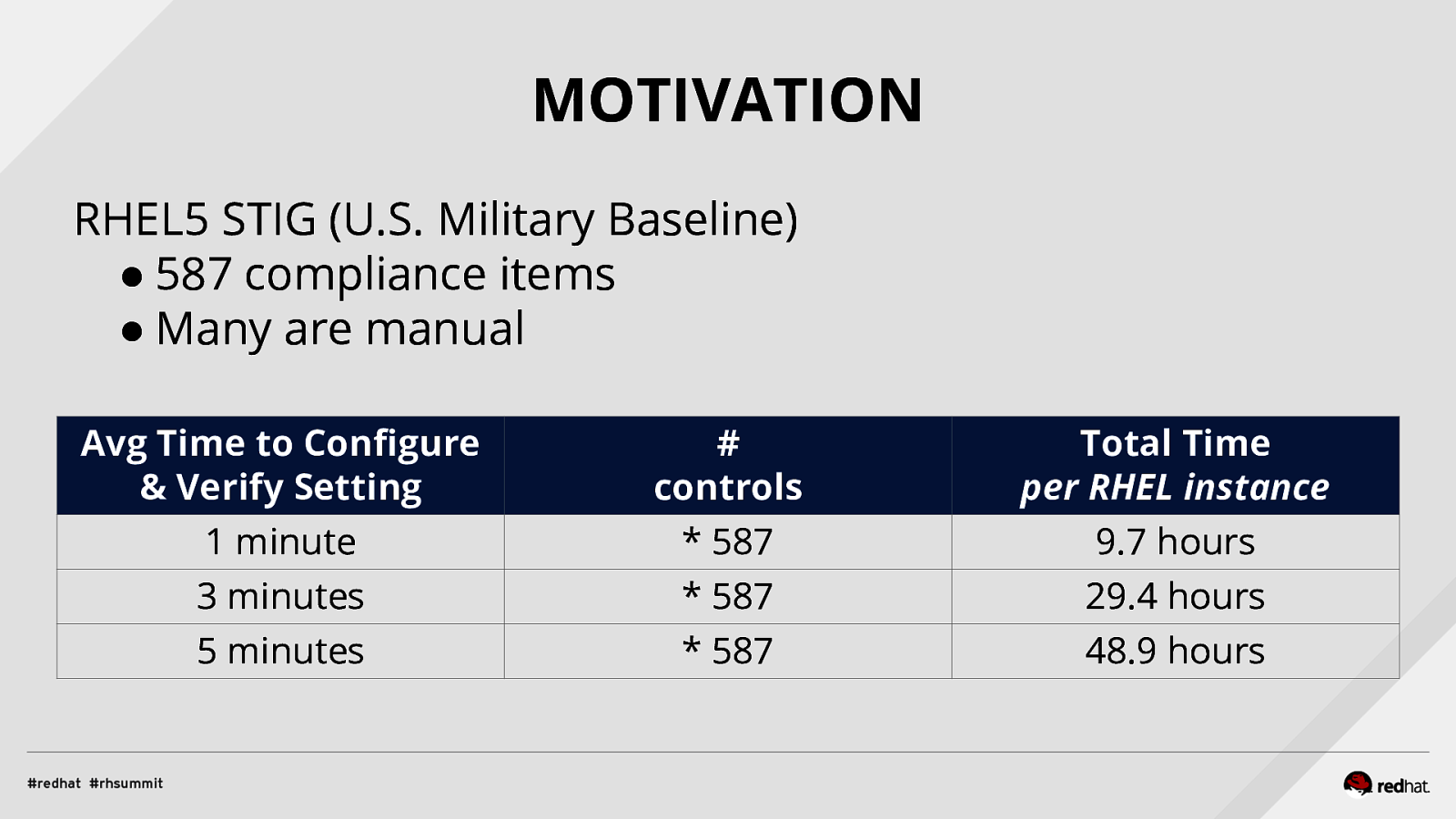
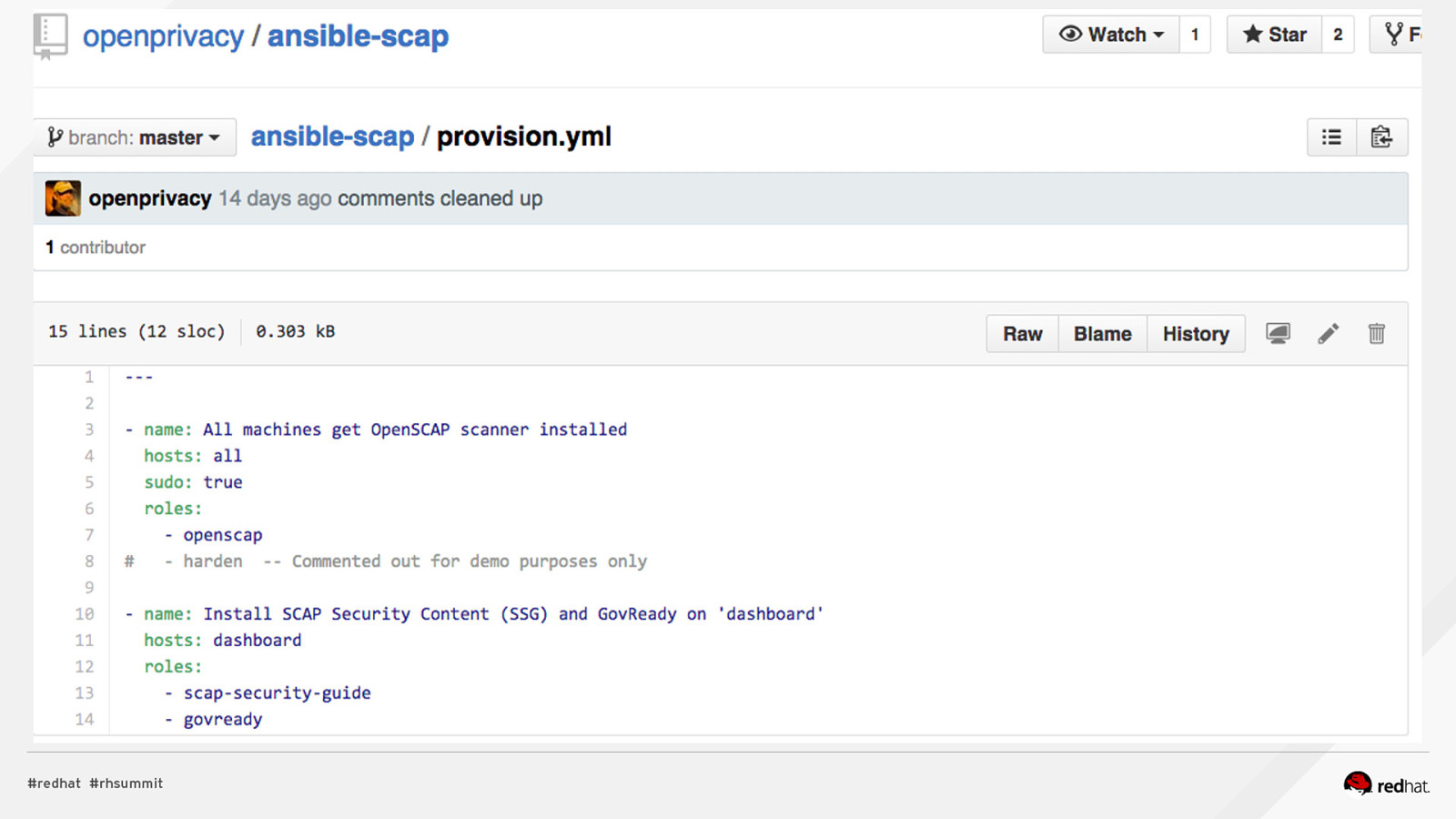
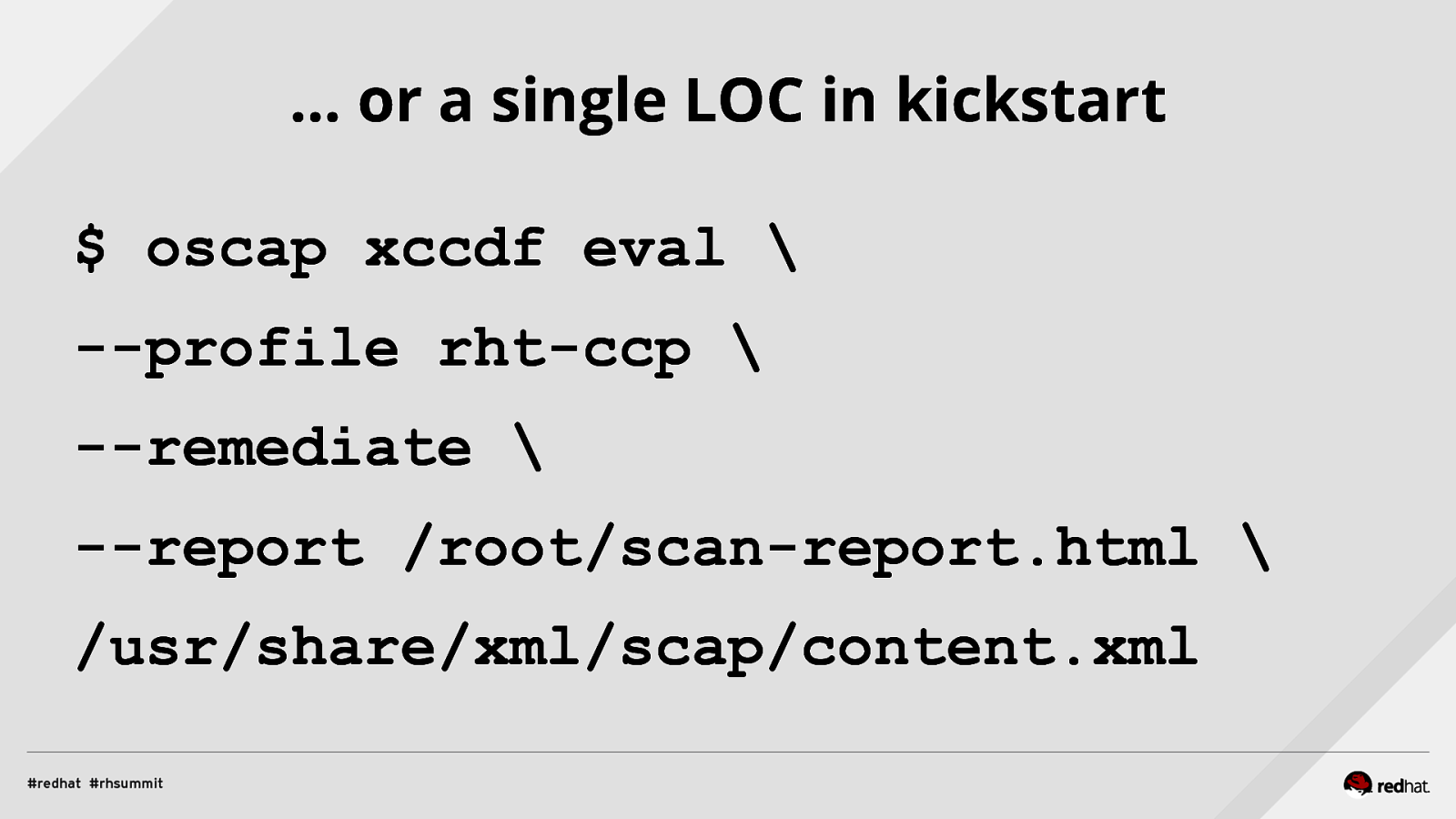
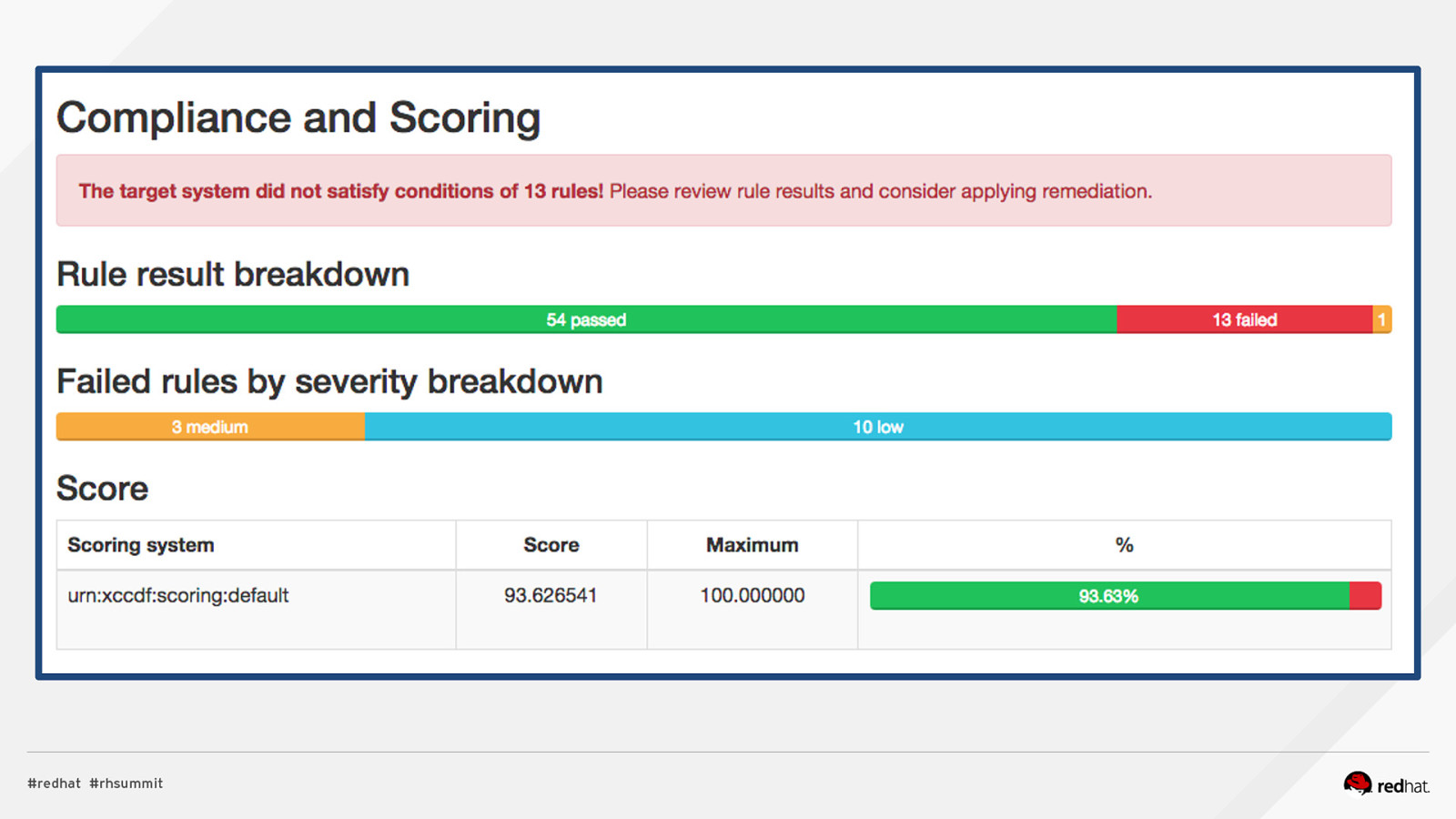
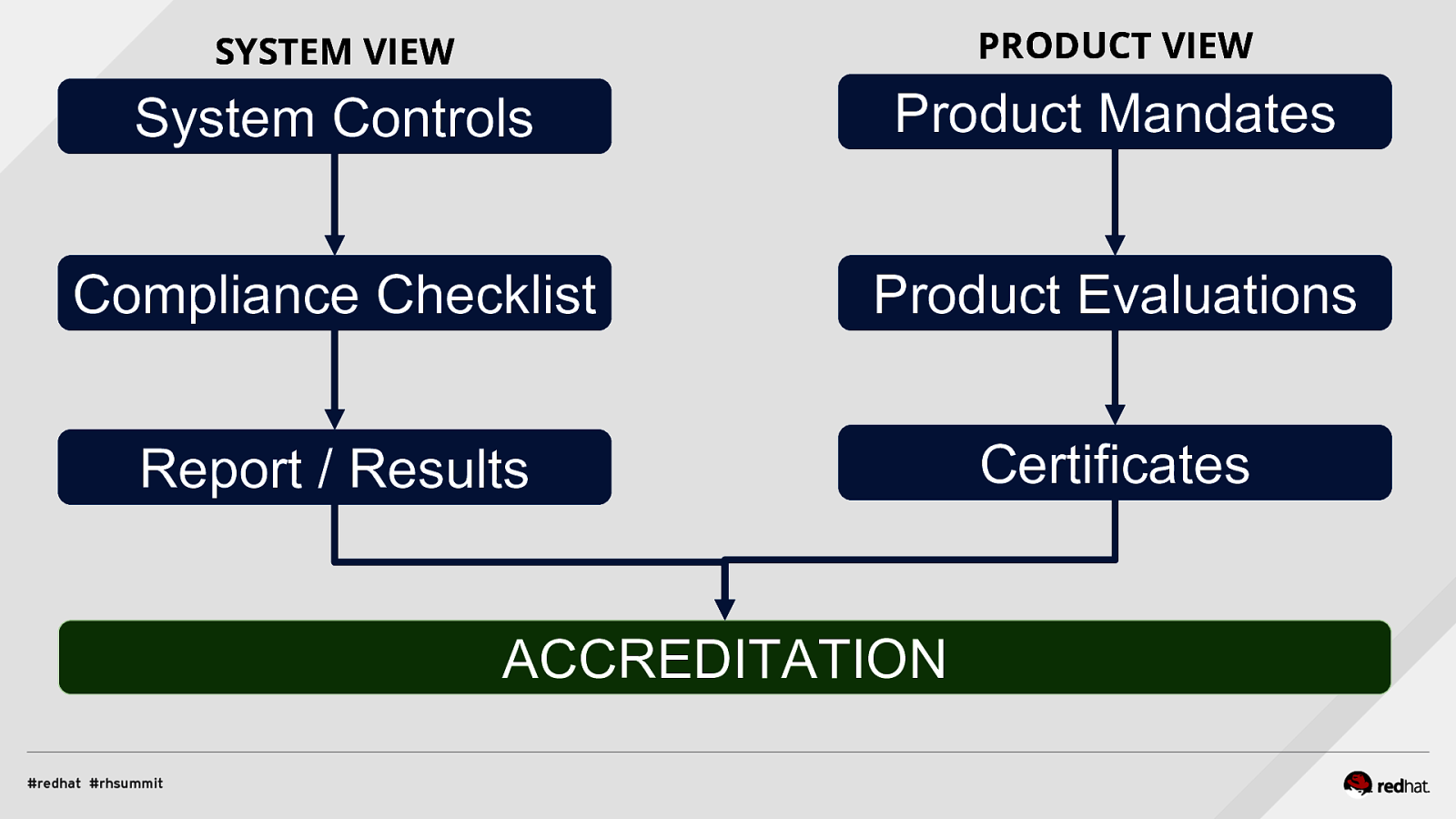
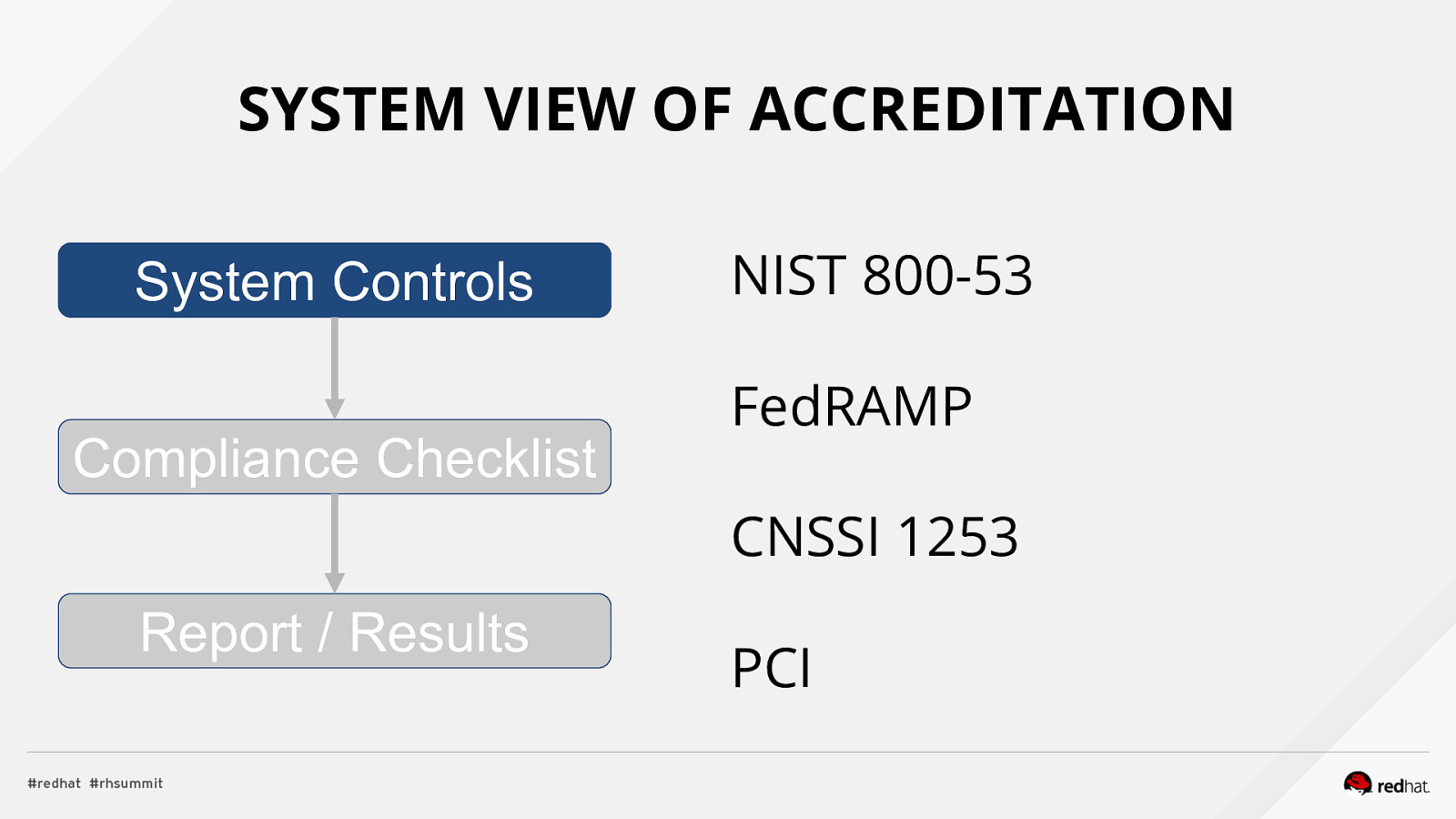
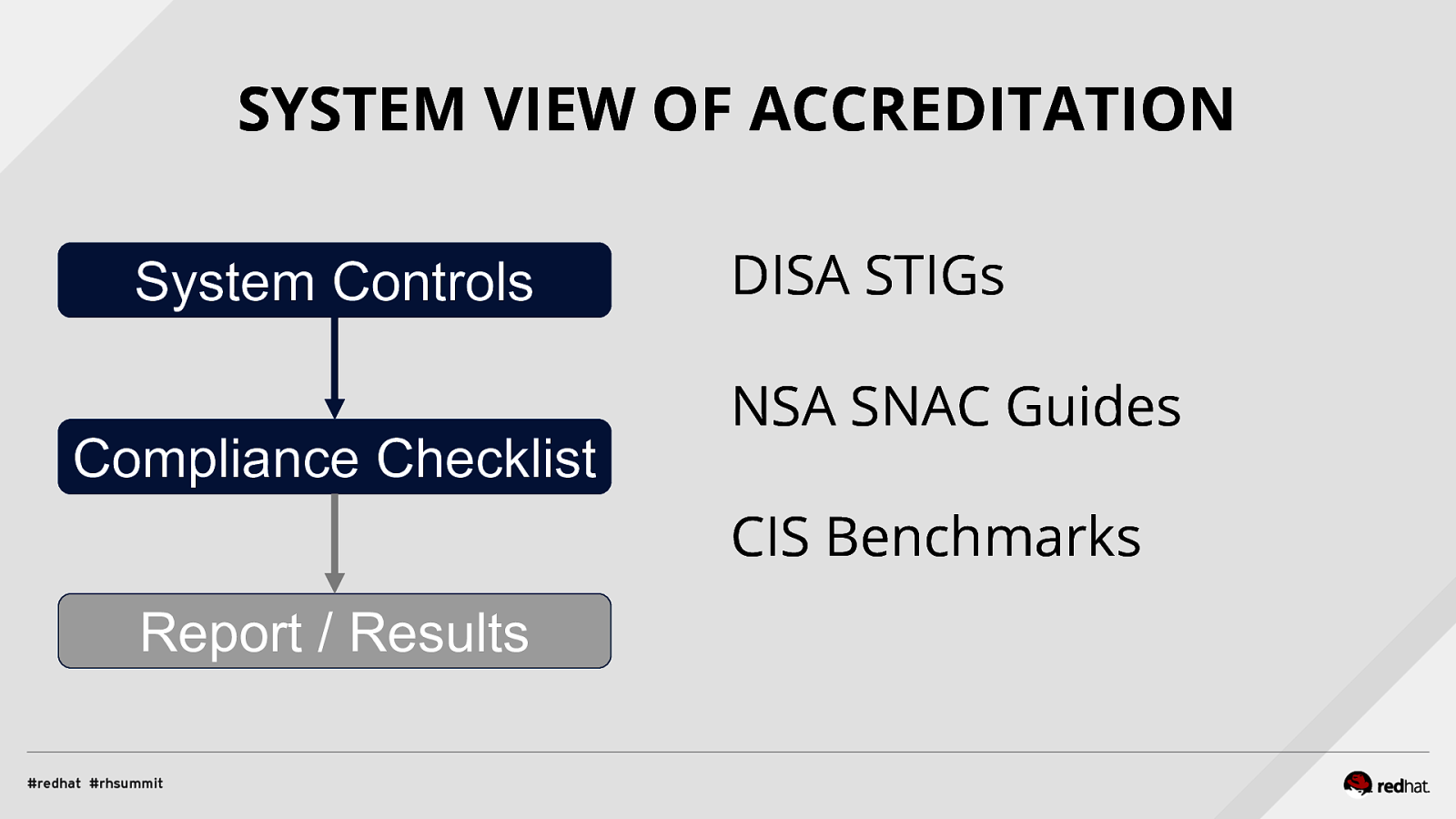
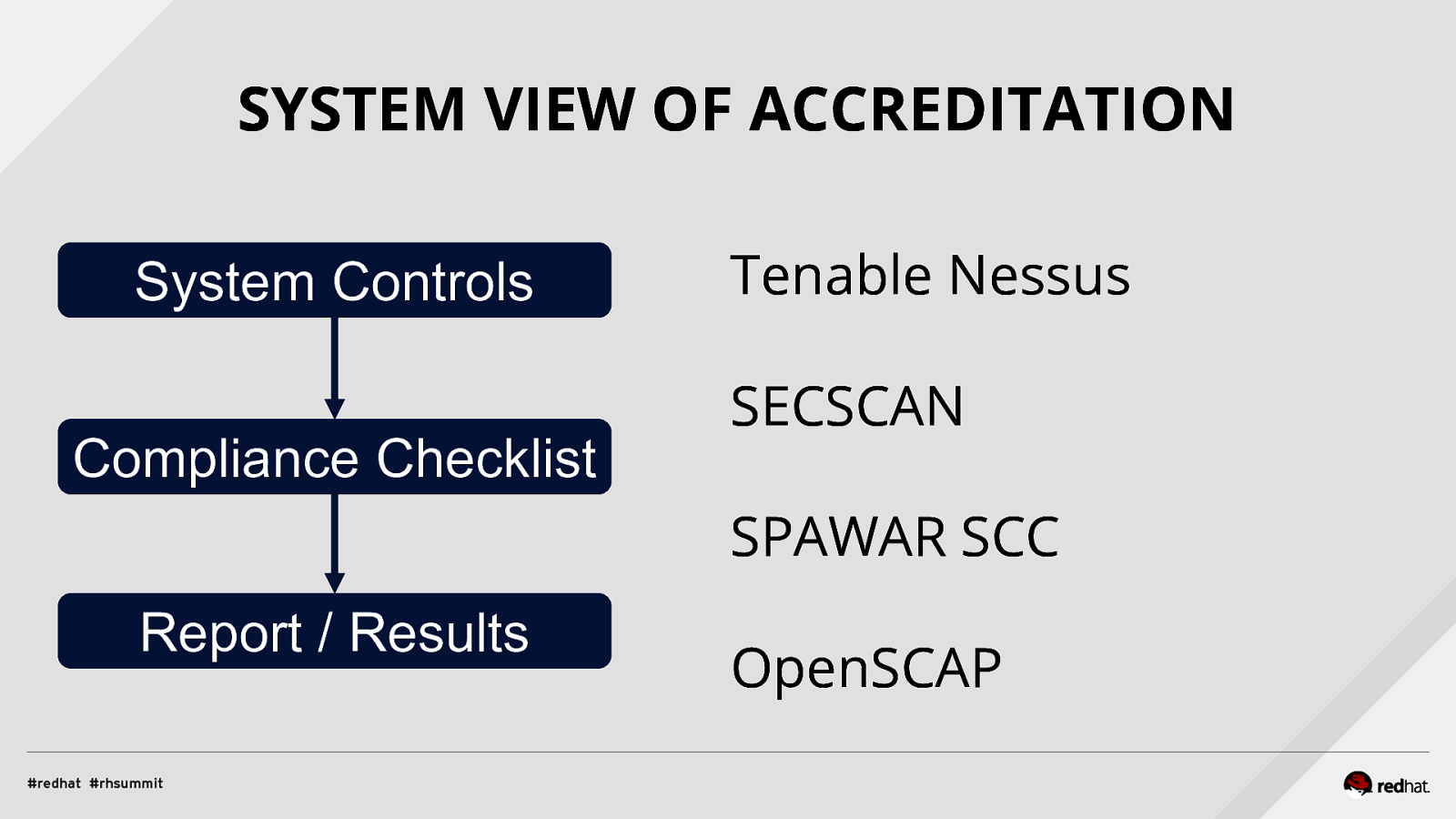
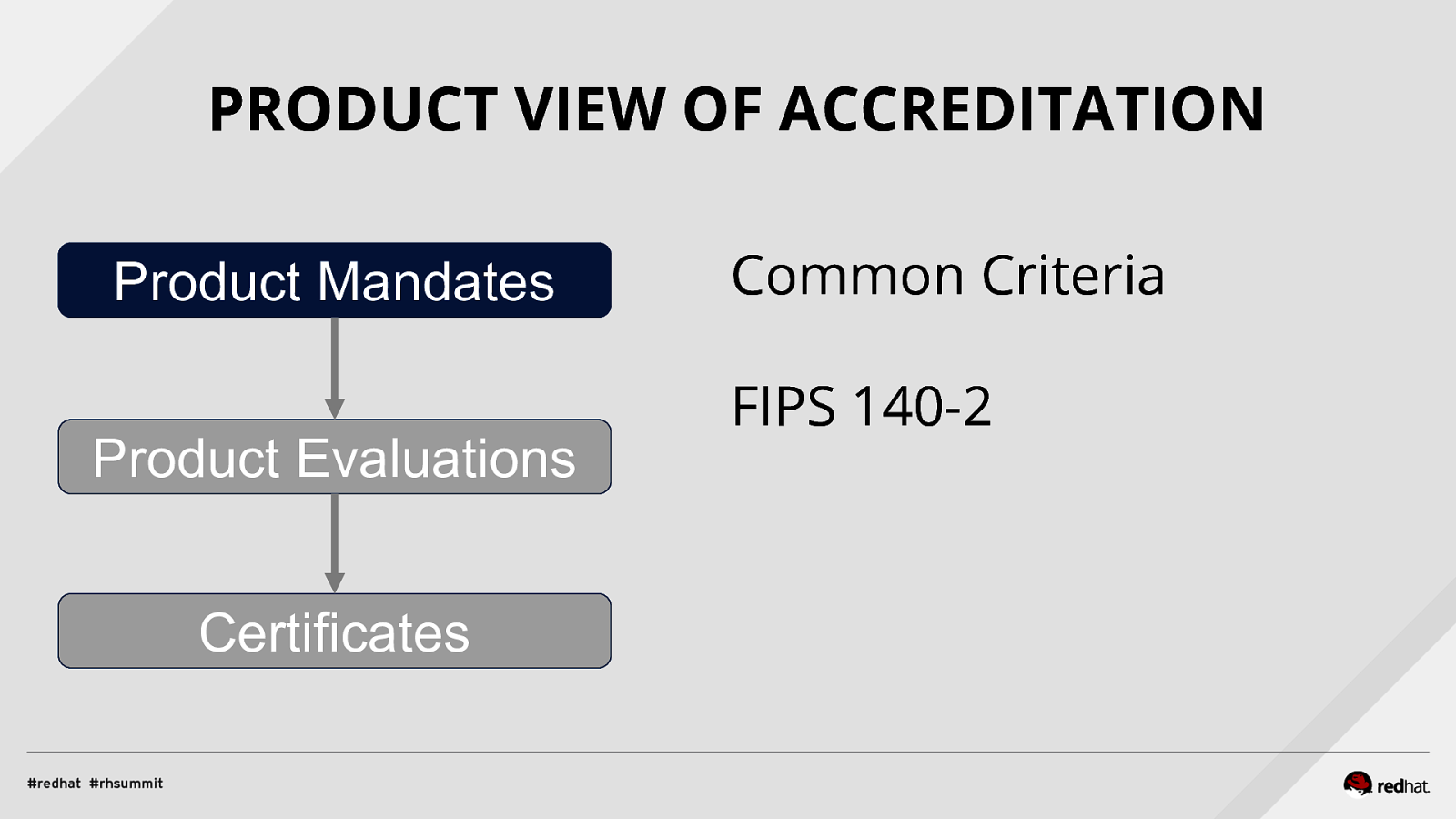
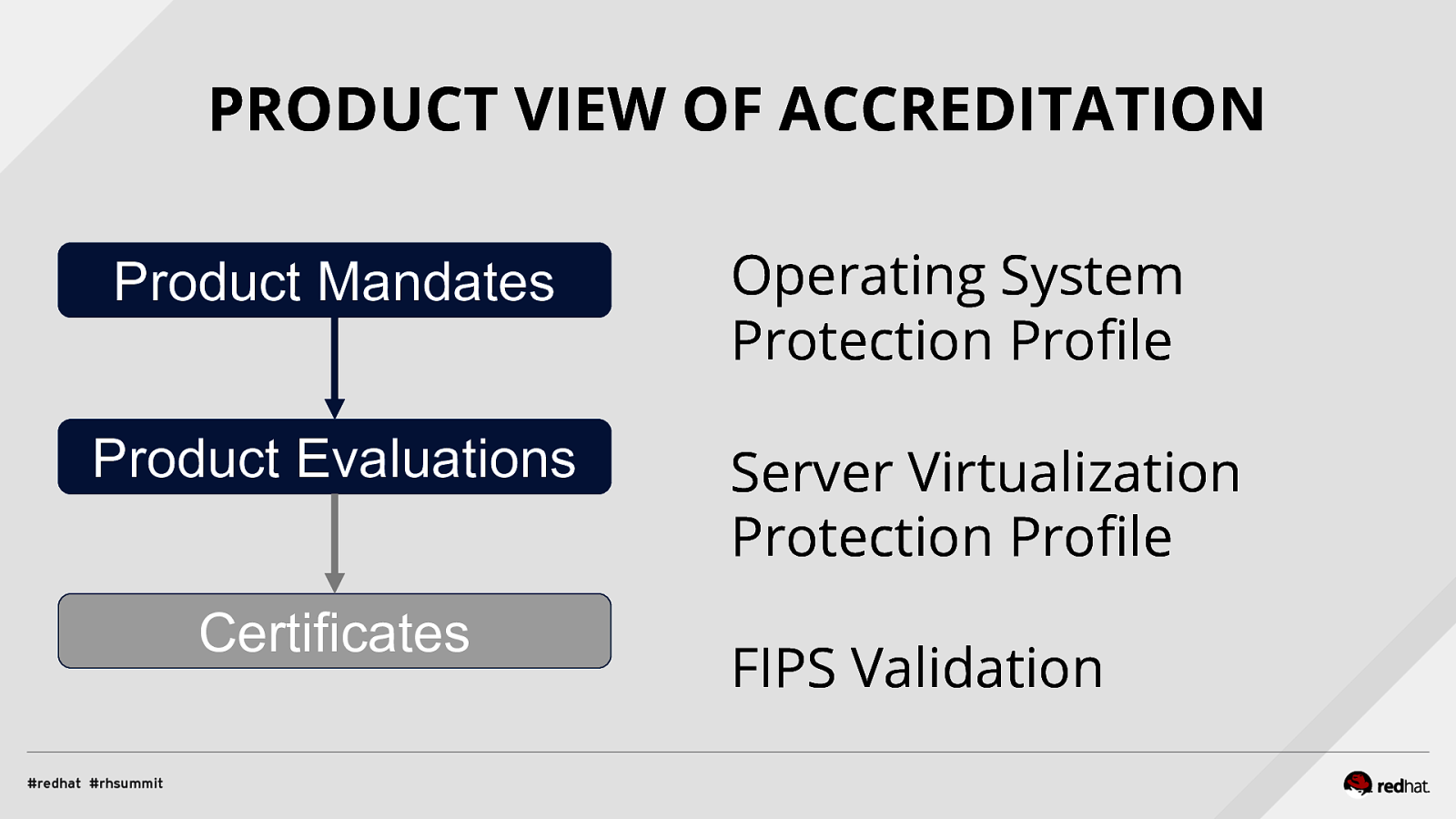
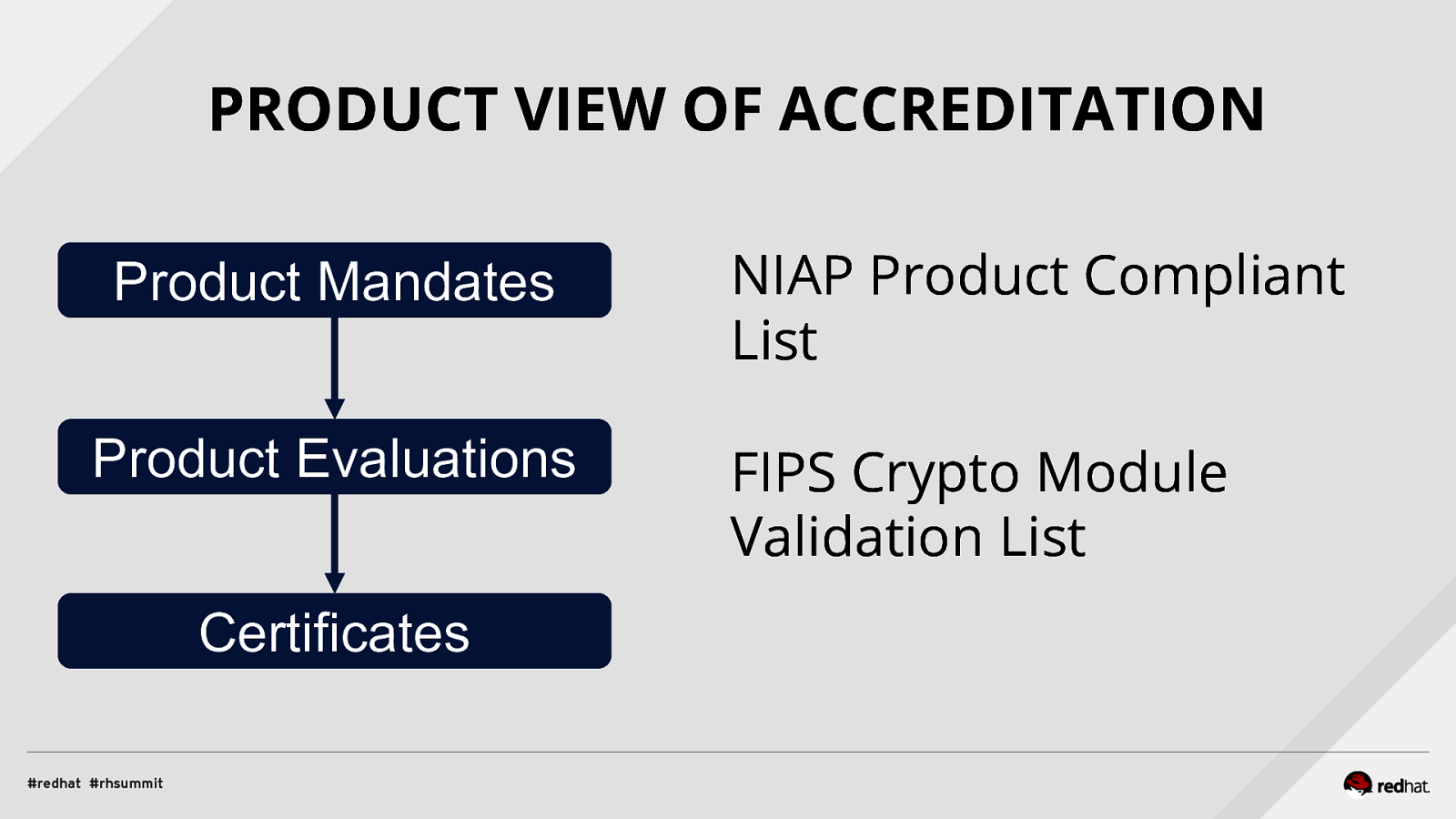
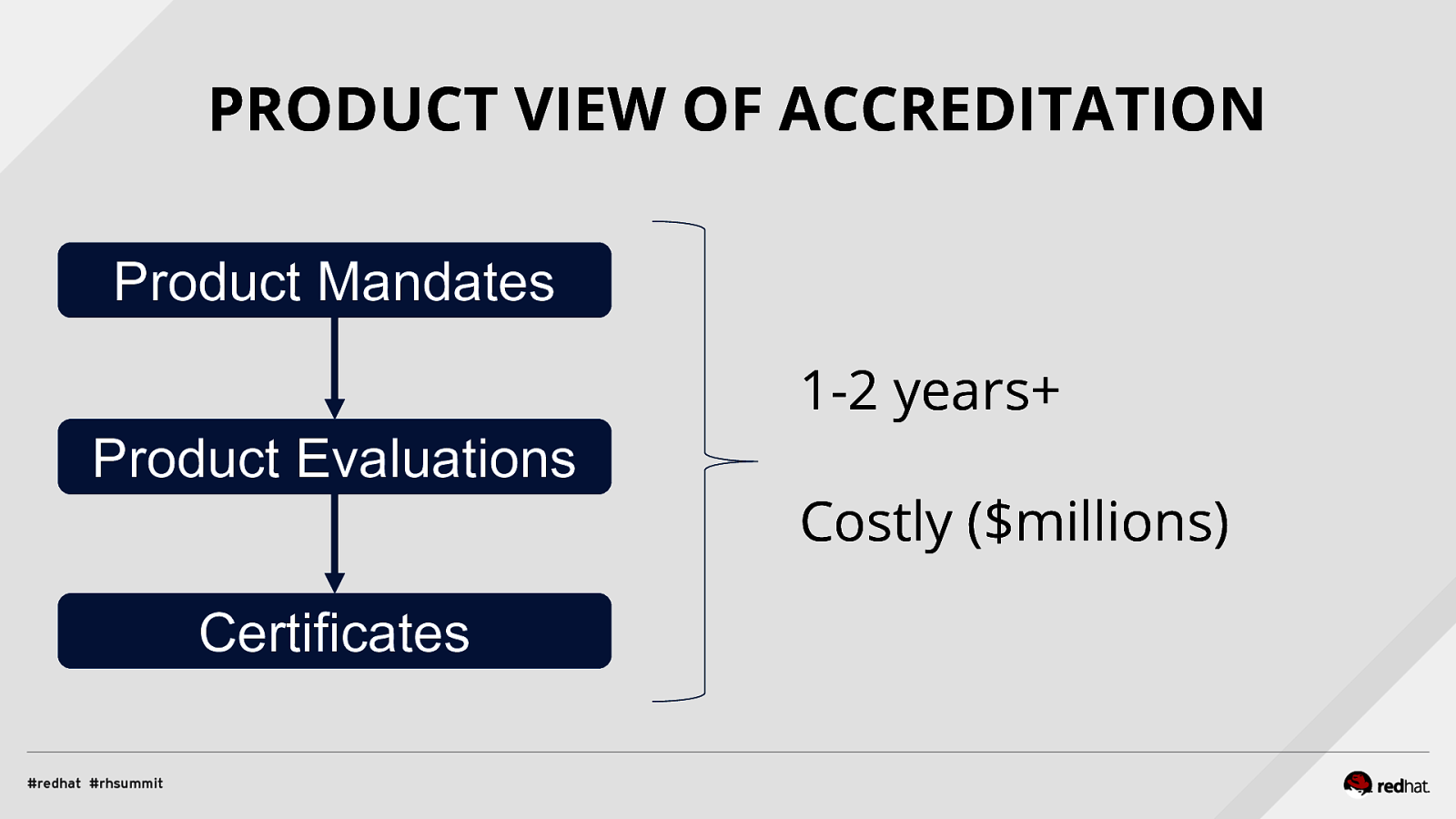
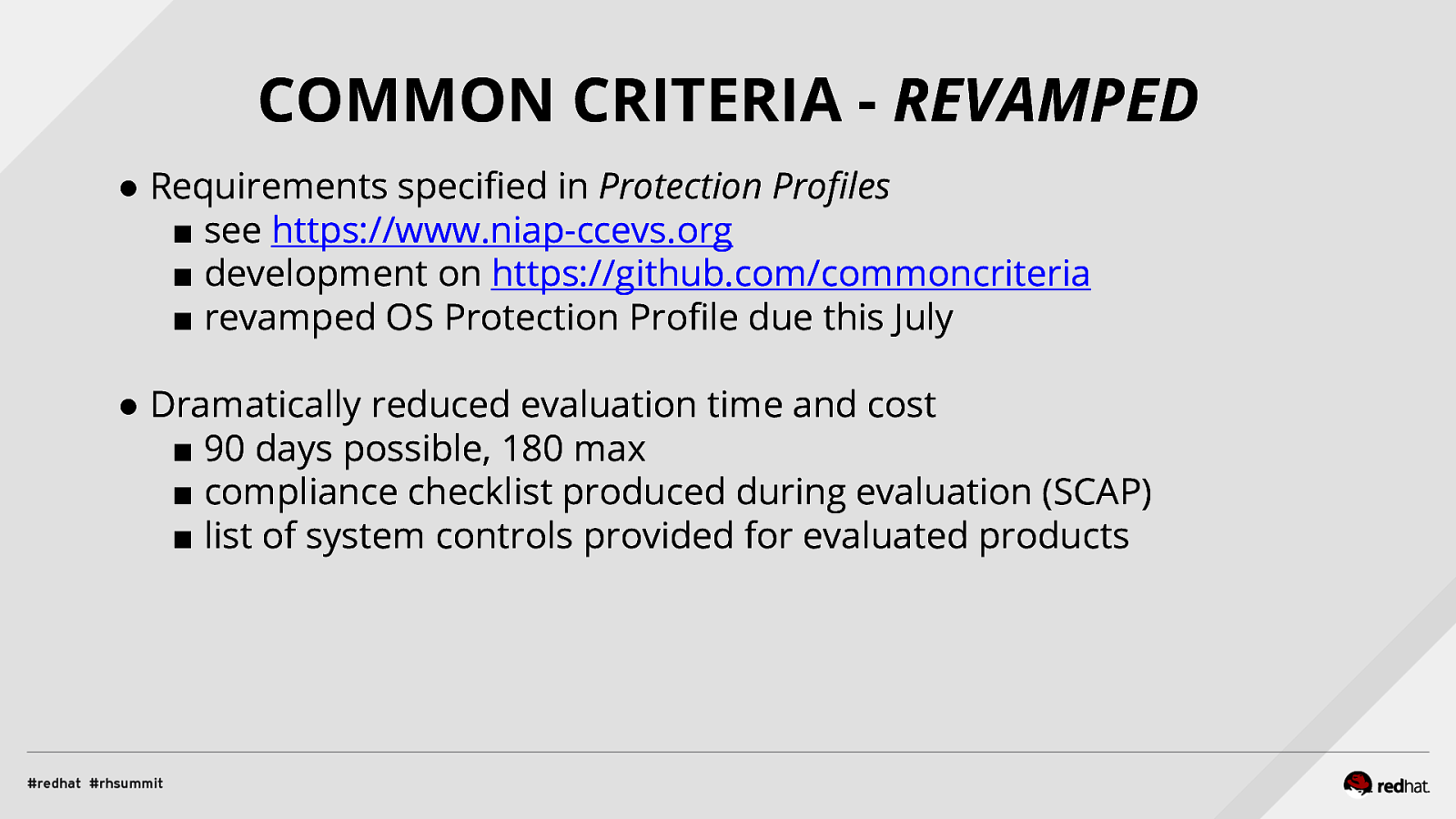
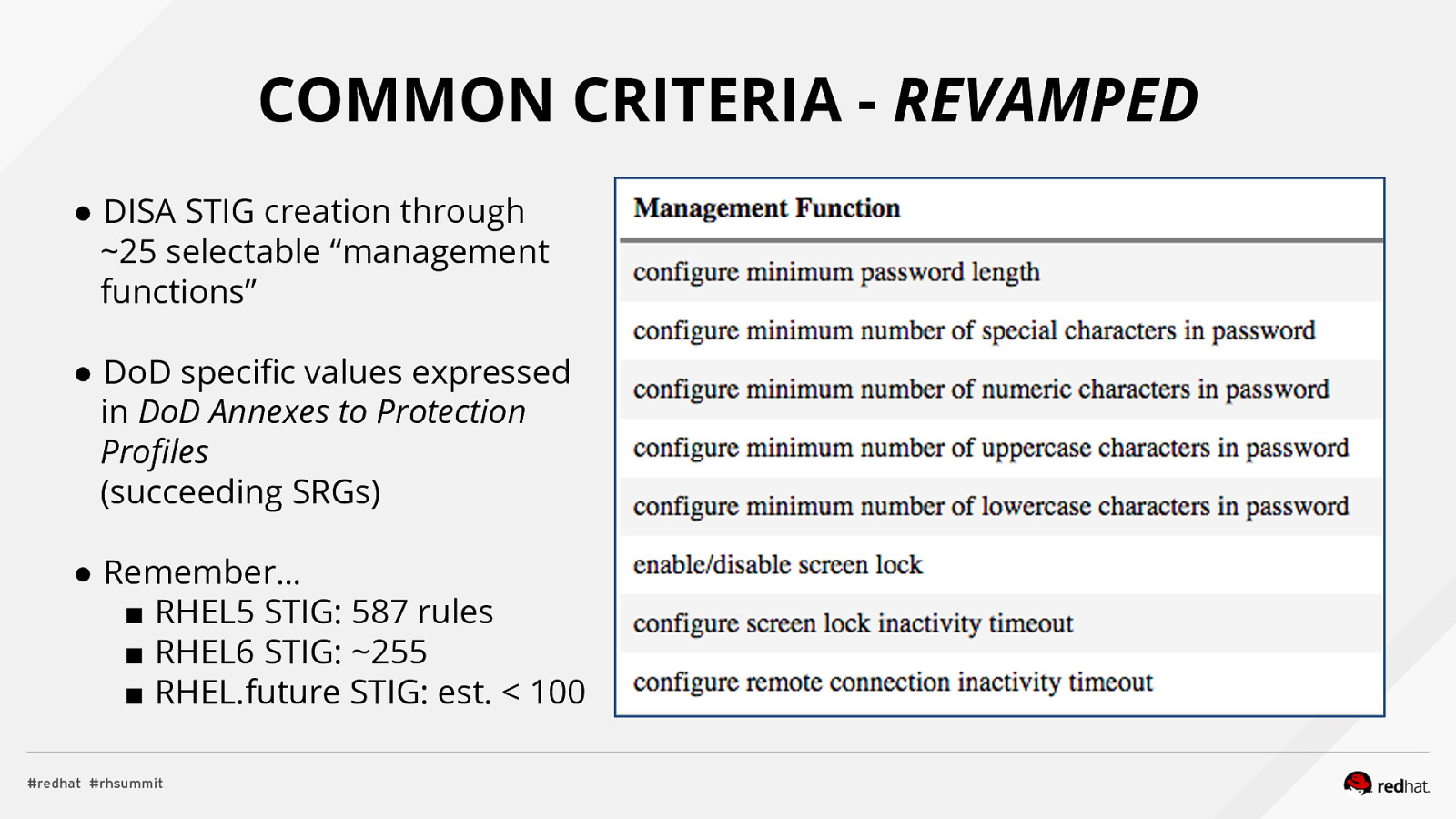
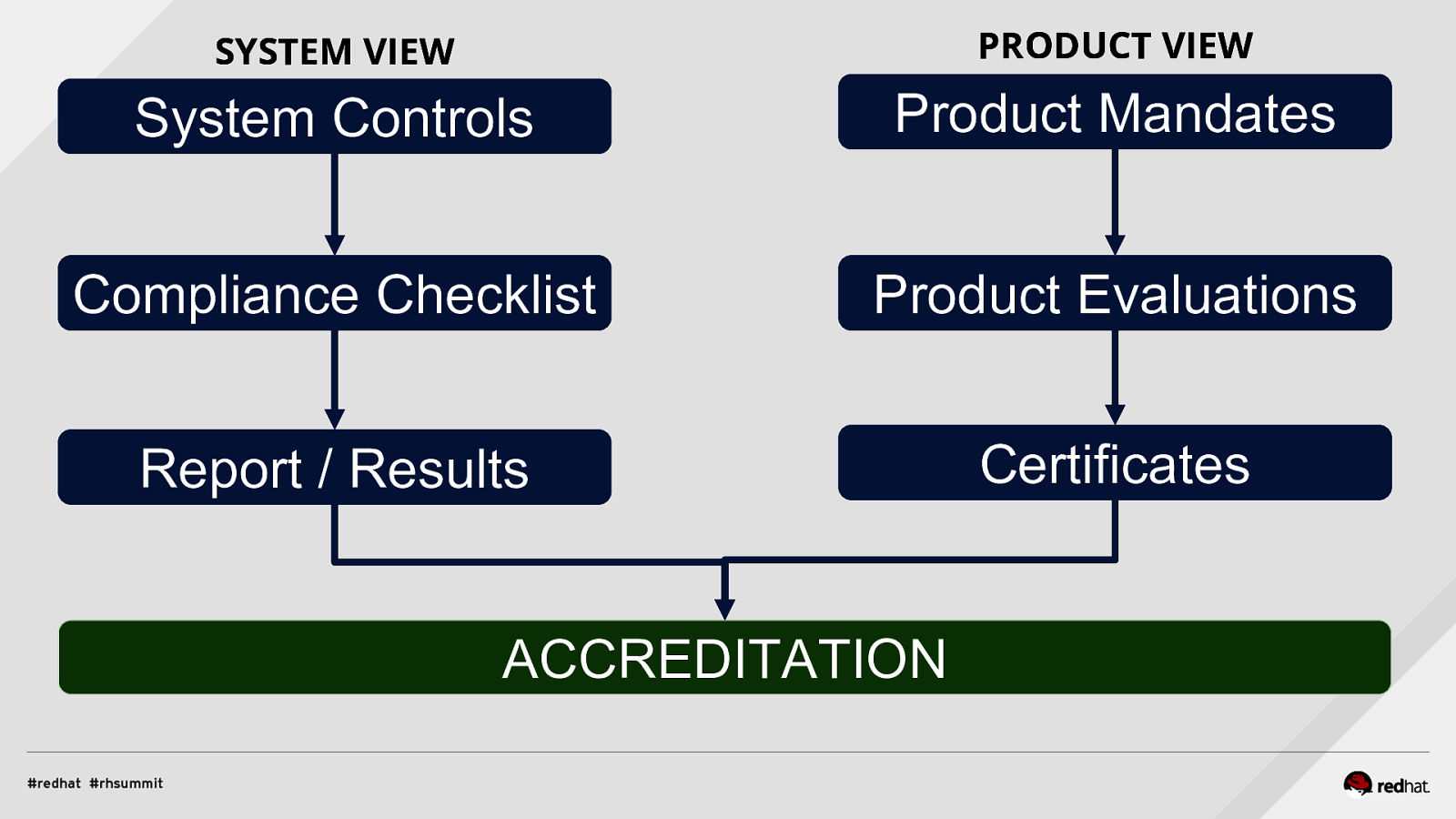
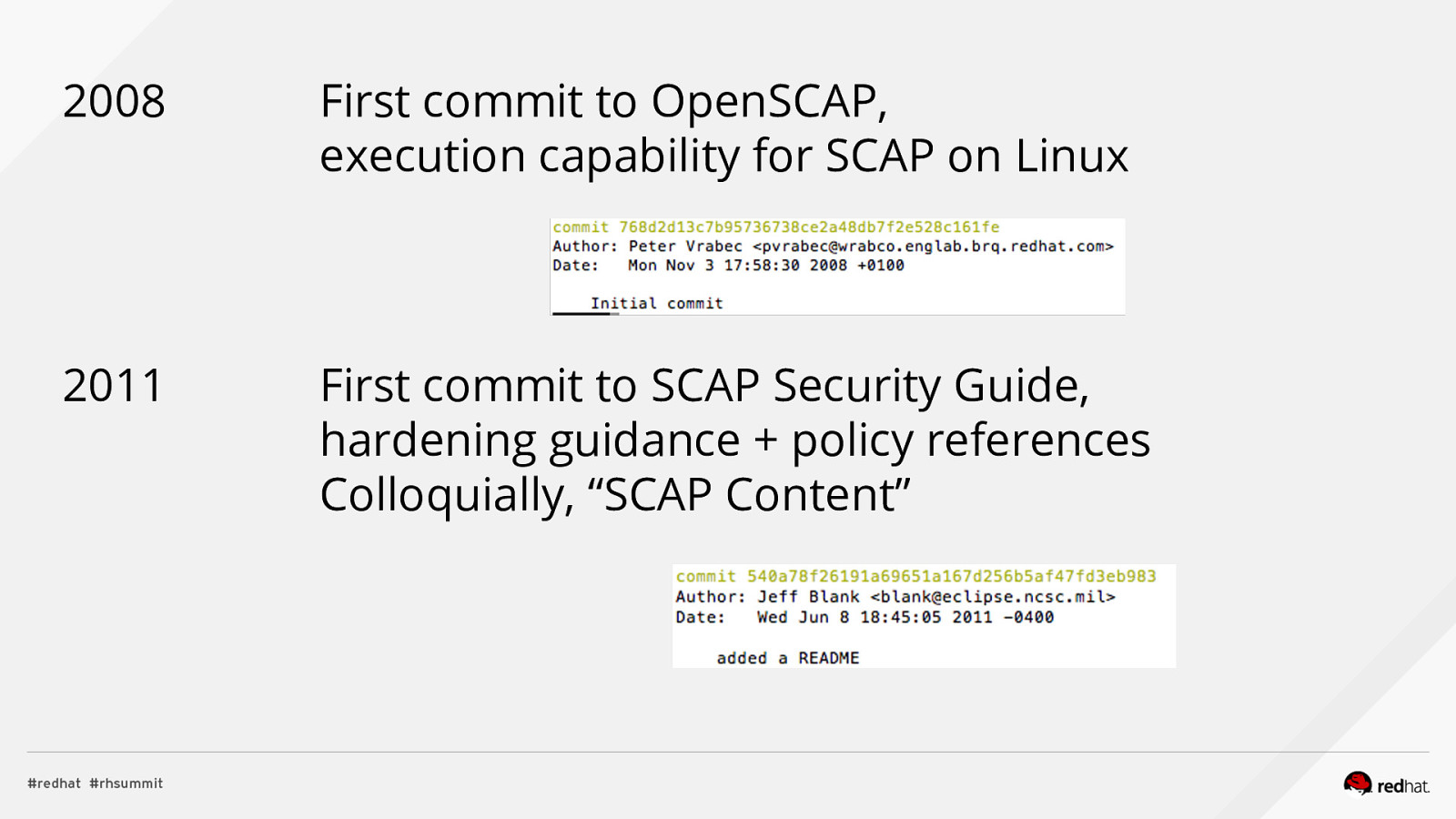
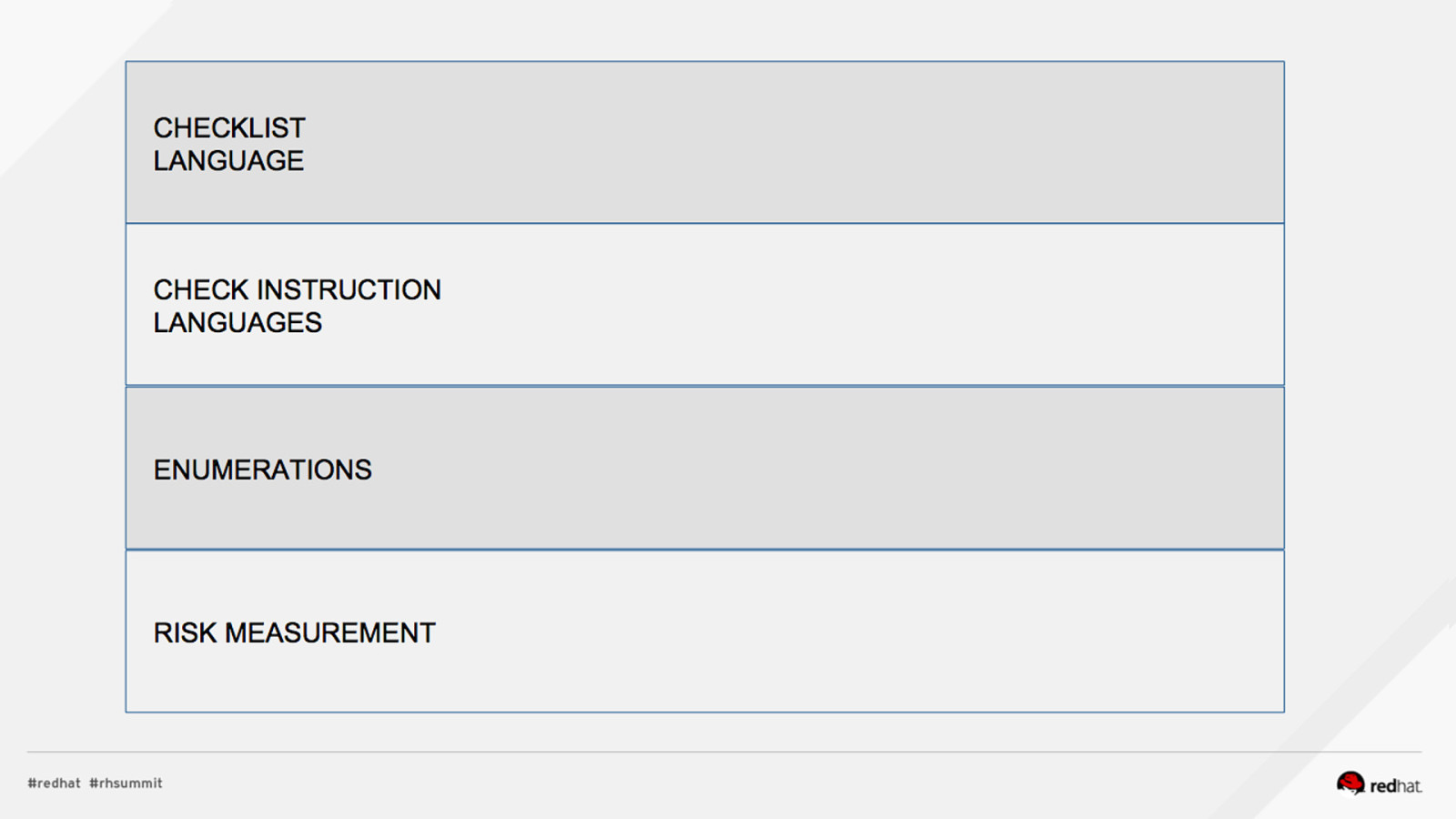
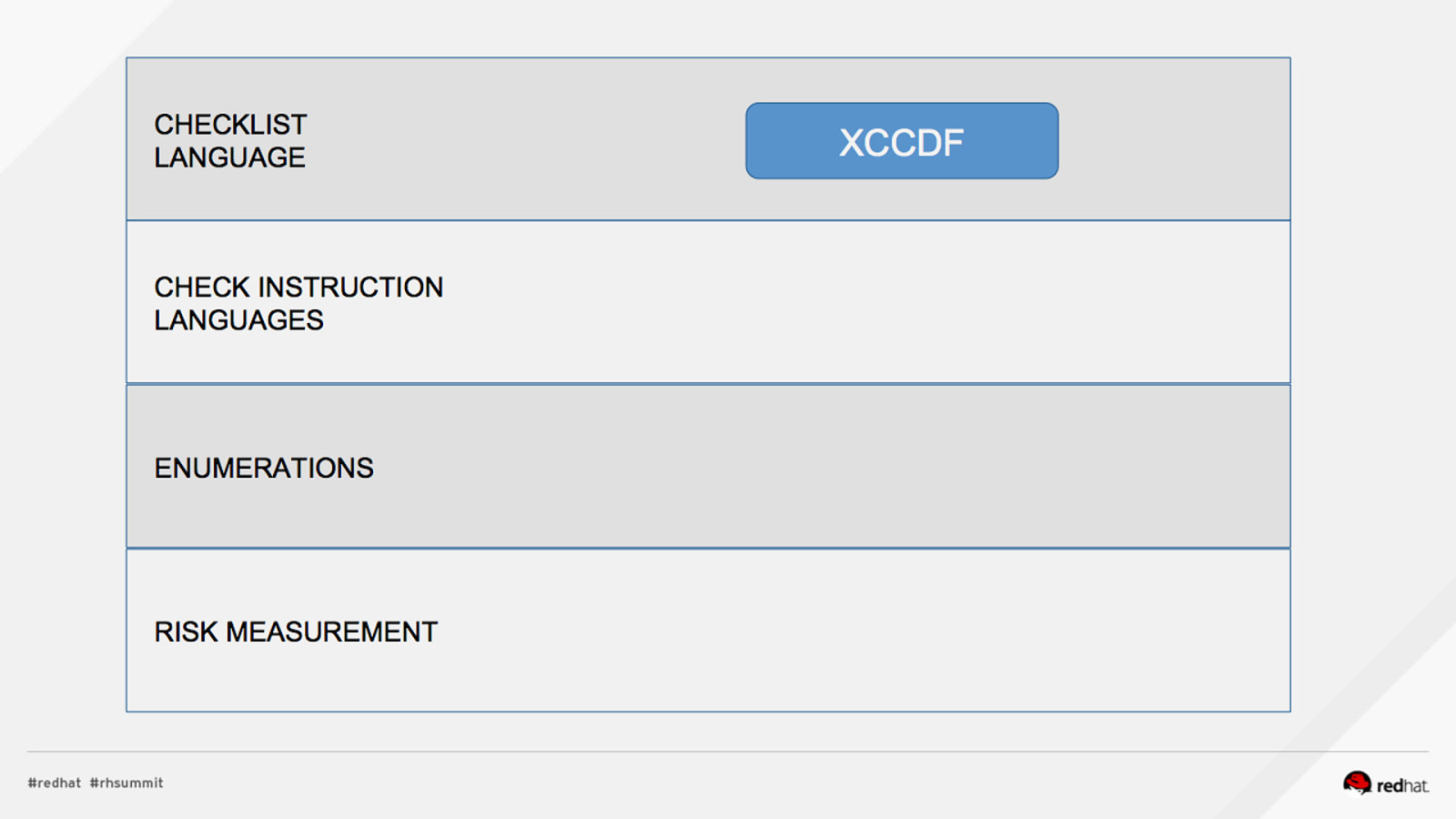
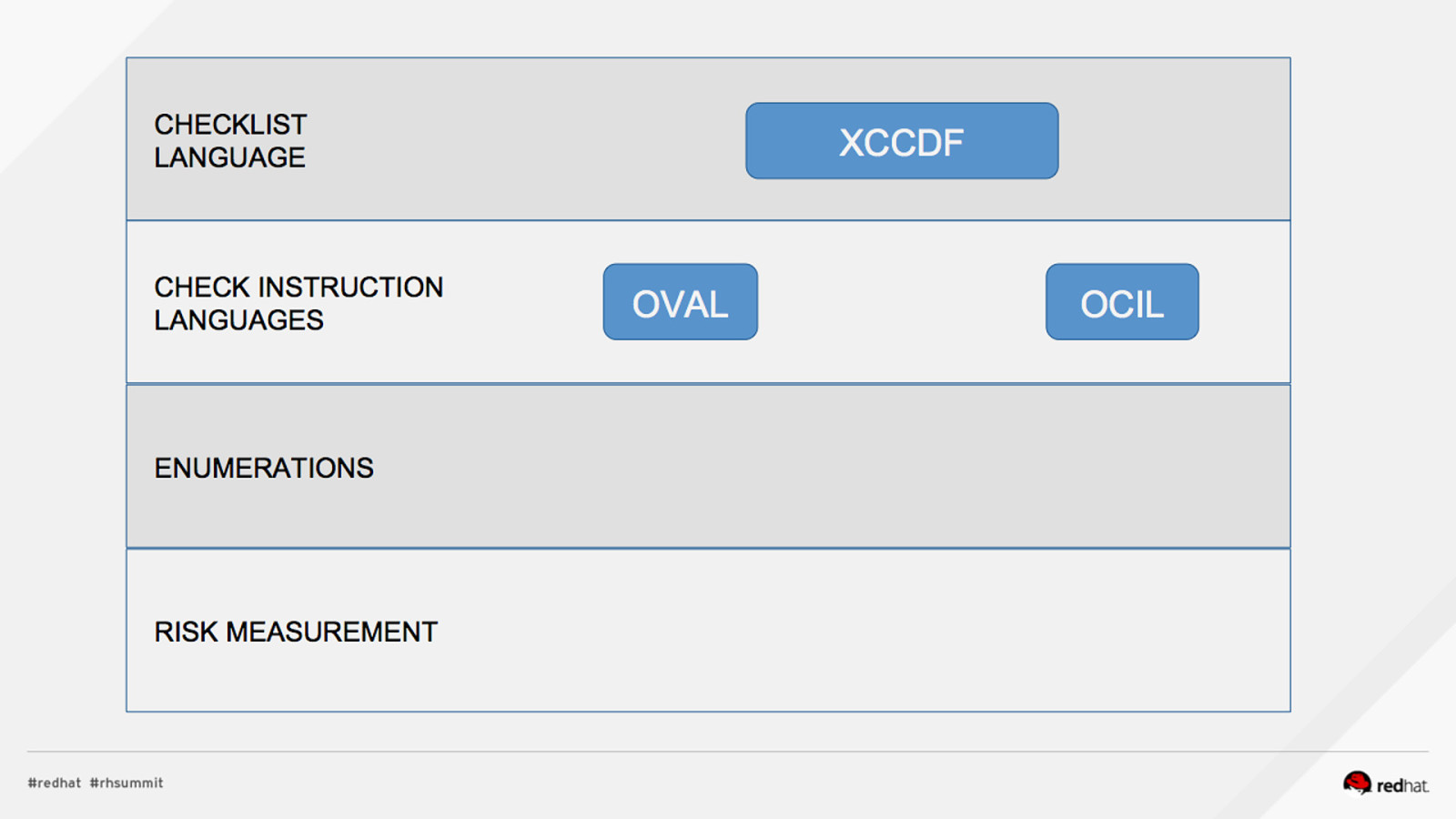
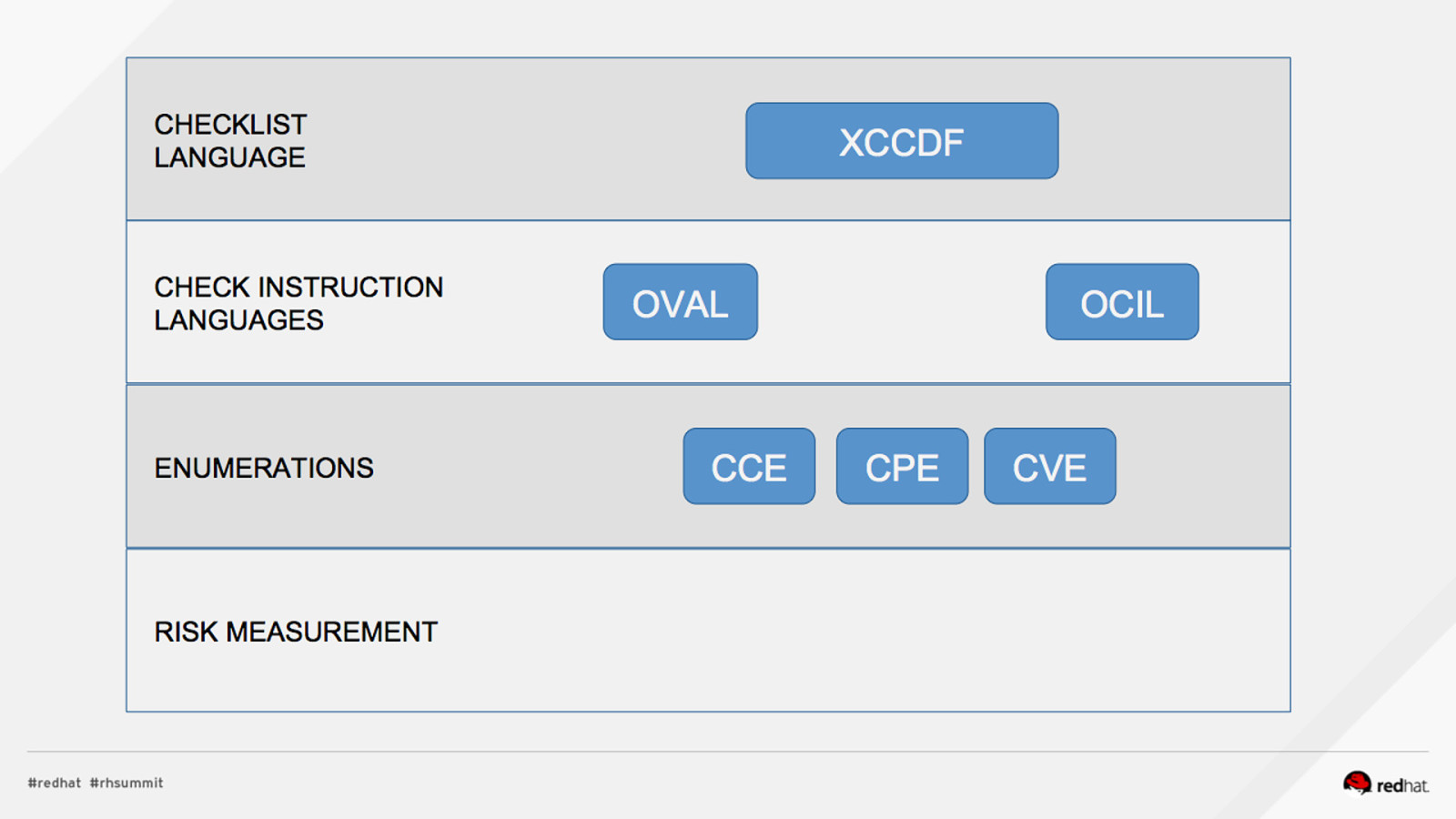
Applied SCAP Lab Automating Security Compliance & Remediation Shawn Wells Office of the Chief Technologist Director, Innovation Programs Red Hat Dave Smith Infosec Engineer / Penetration Tester / OpenSCAP Upstream Maintainer Secure Innovations, LLC ADD NAME (View > Master > Slide master)