DevOpsSec: Building CI/CD with Security Teams
A presentation at AFCEA Fort Knox Event in in Fort Knox, KY 40121, USA by Shawn Wells


DevOpsSec: Building CI/CD with Security Teams Shawn Wells Chief Security Strategist Red Hat Pubic Sector shawn@redhat.com || 443-534-0130

Late 1990’s



Early 2000’s



Find the “software pirate”

Y2K

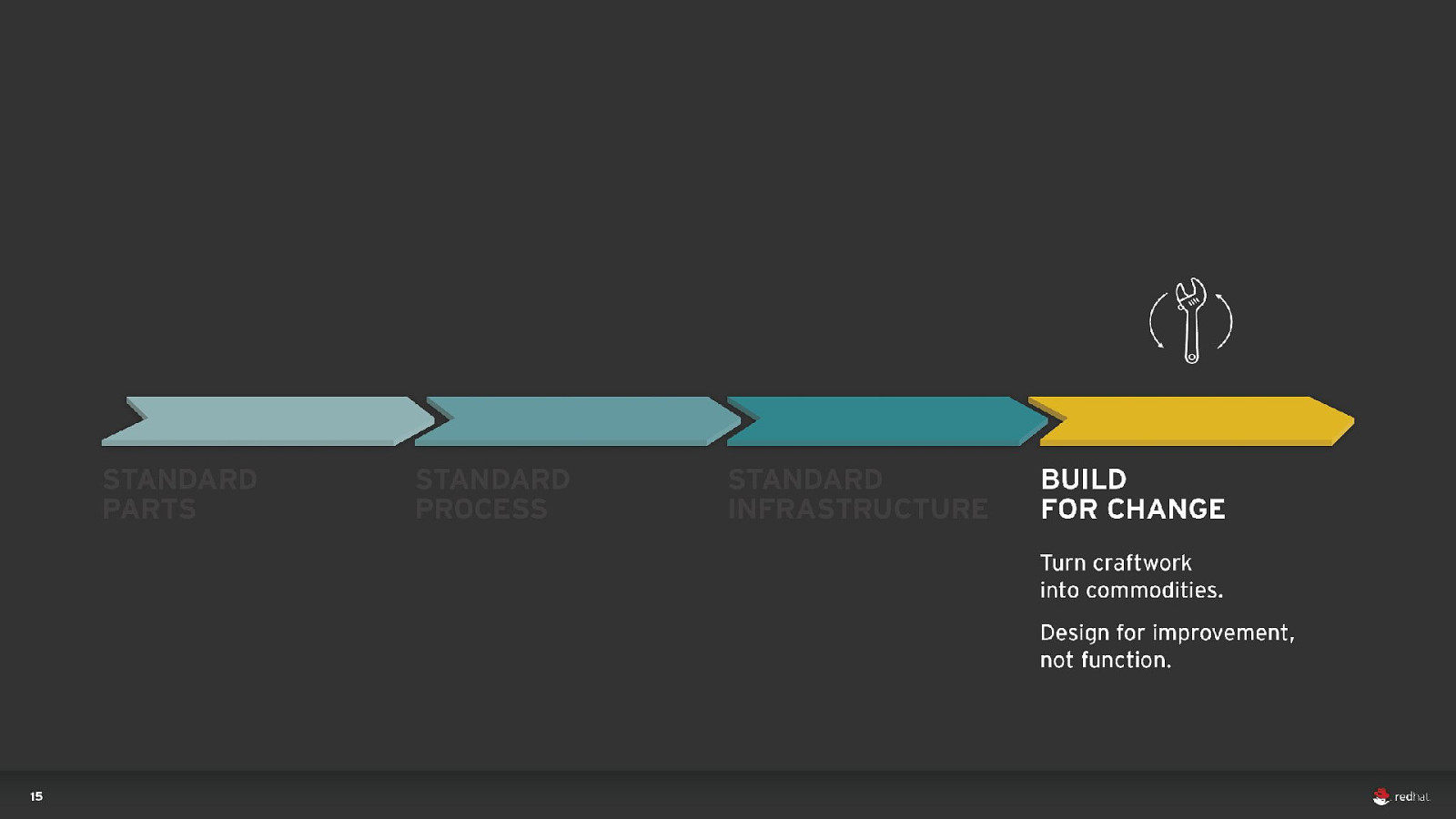
15 d l o s r a ye






15 d l o s r a ye

o t ess c c a g n i l l , c Se i s u m , ” s e i v o M “ e r a w t f so

g n i z i t e n o M r o s n e “S ” a t da

d e t s u B 0 0 0 2 l Fal :(


: 1 0 0 2 Spring 15yo y t i r u c e s a h t i w … e c n a r a cle

g n i t i o l p x E g n i z i t e n o M r o s n e “S ” a t da





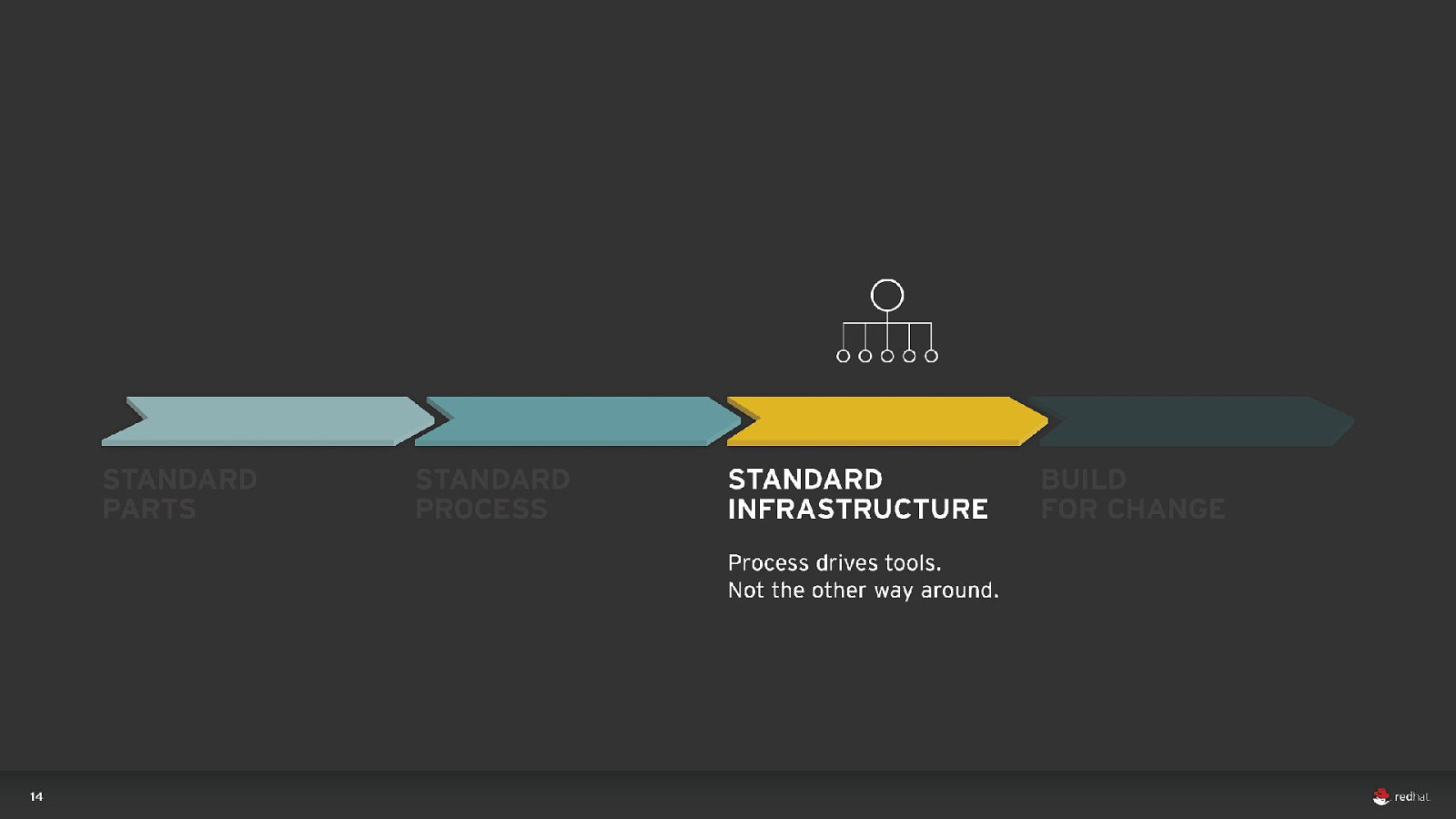
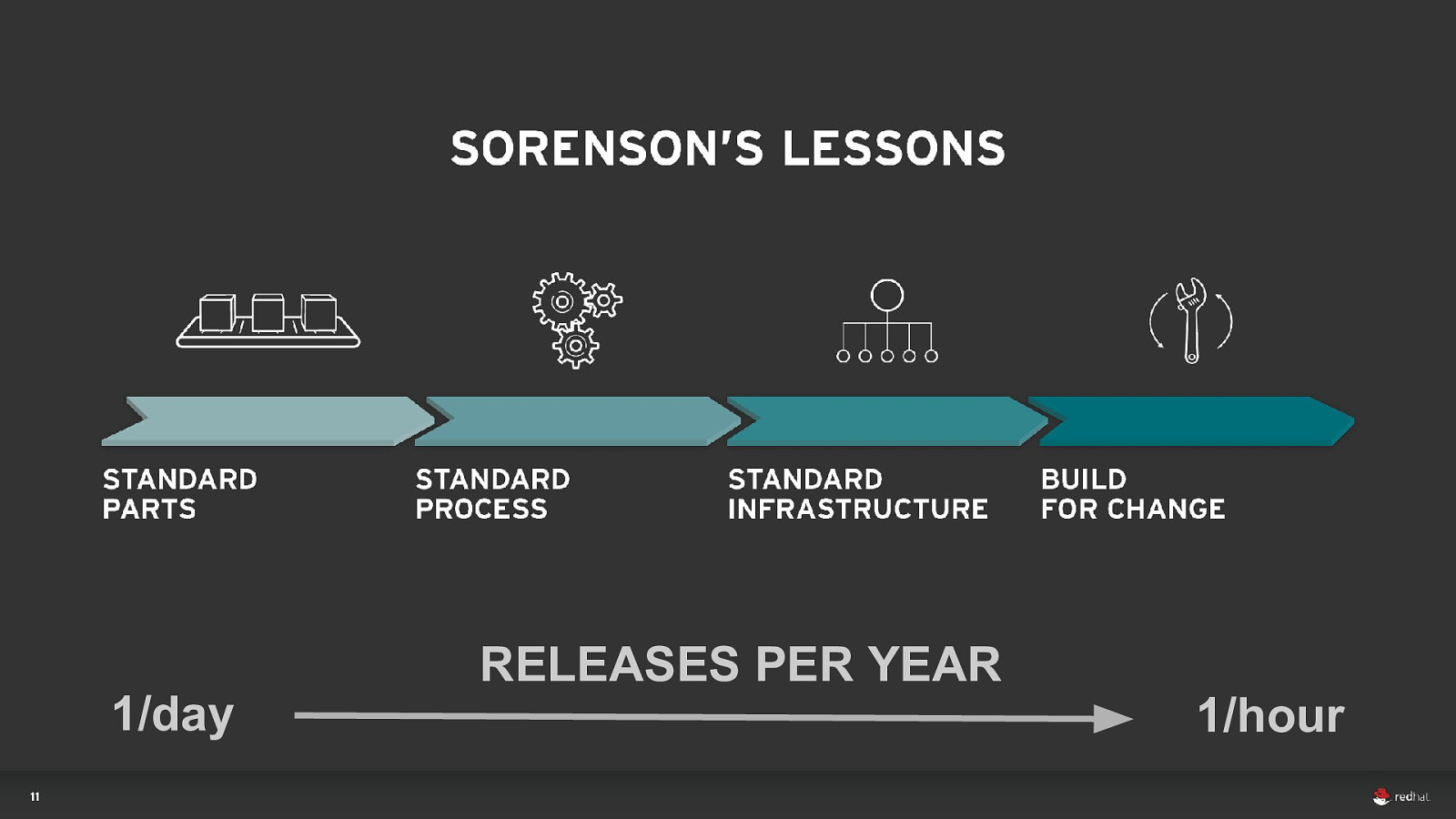
RELEASES PER YEAR 1/day 1/hour
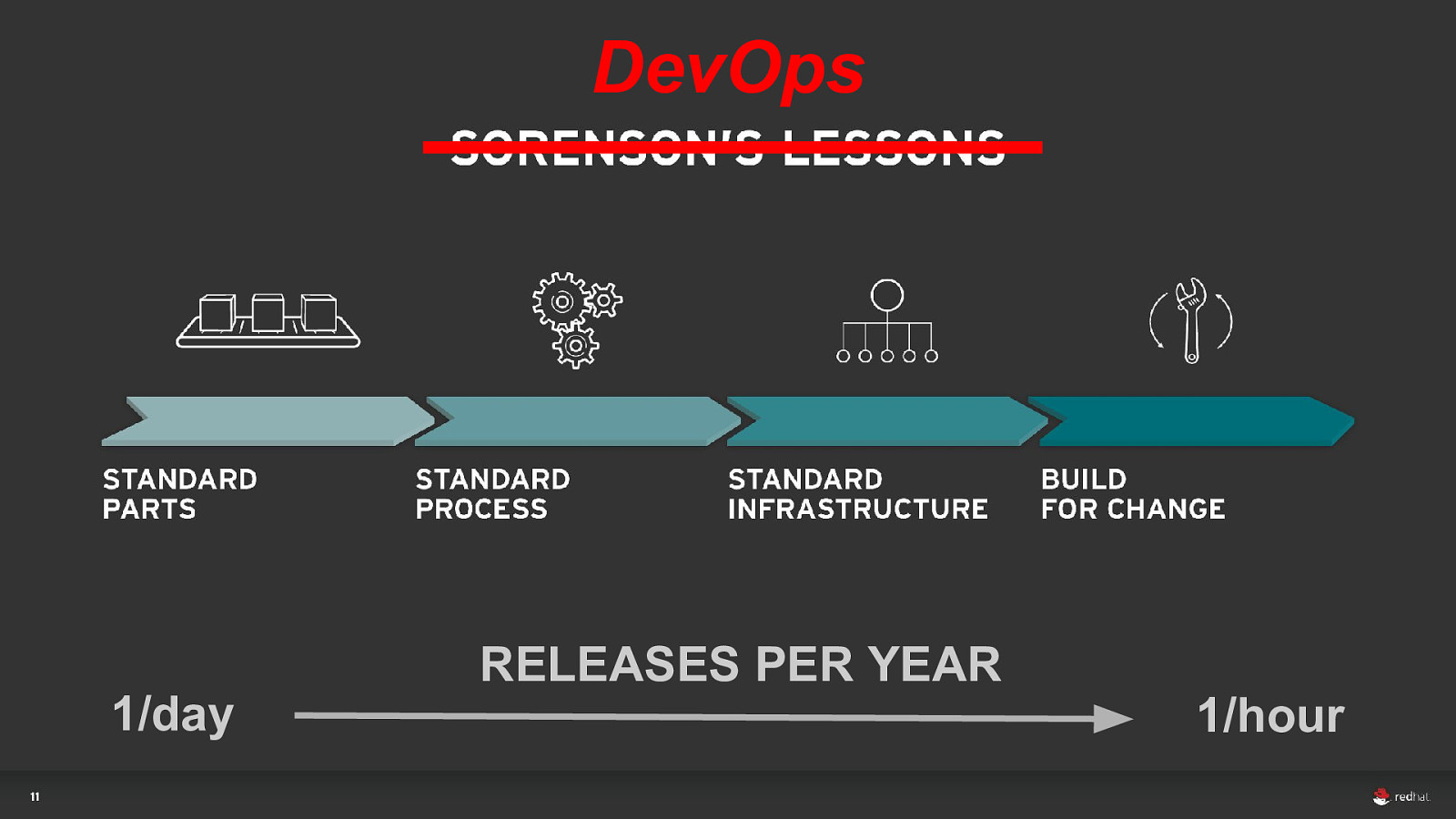
DevOps RELEASES PER YEAR 1/day 1/hour

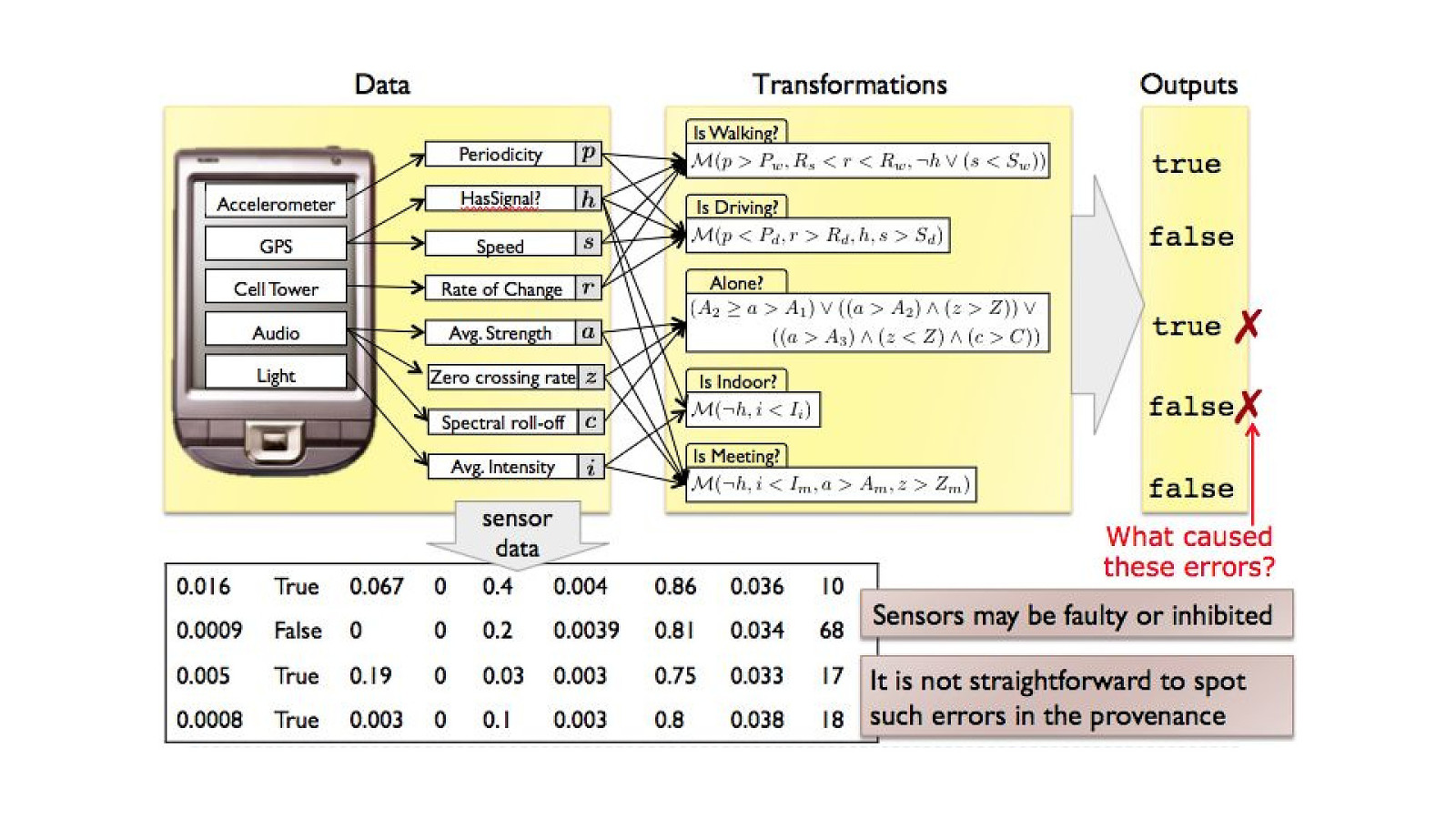
The Problem Applications require complicated installation and integration every time they are deployed 38
THE PROBLEM DEVELOPERS 39 I.T. OPERATIONS
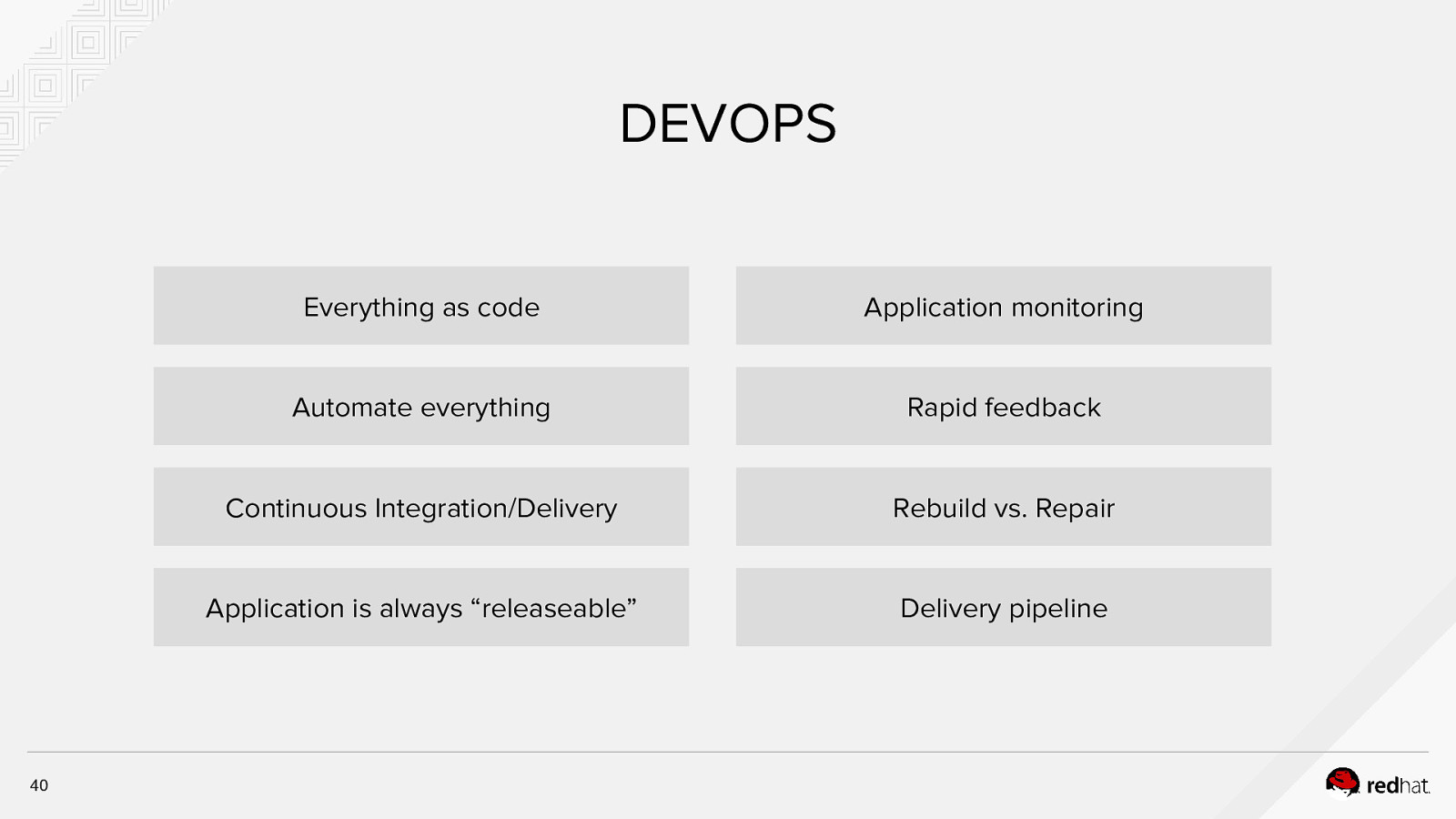
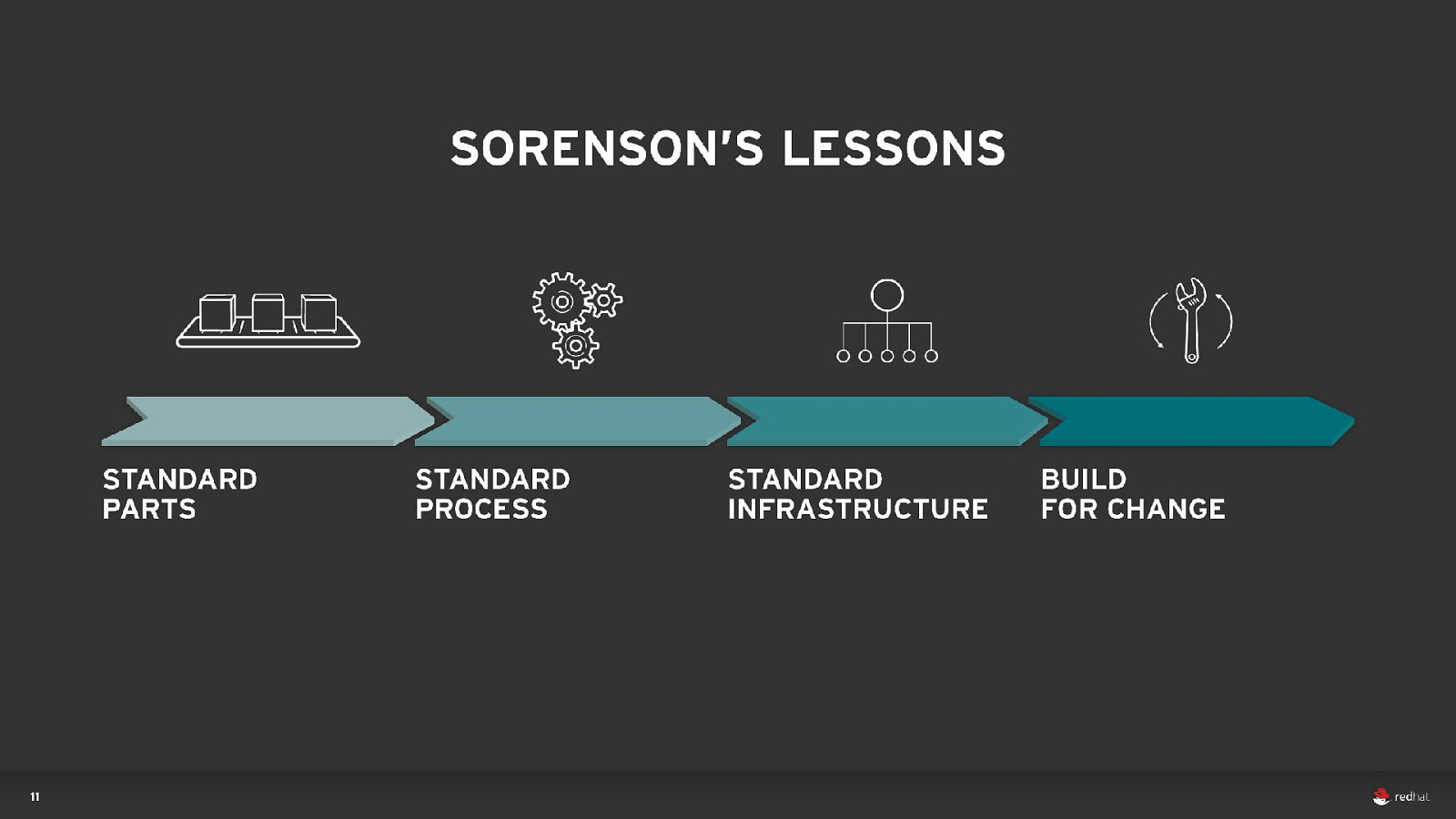
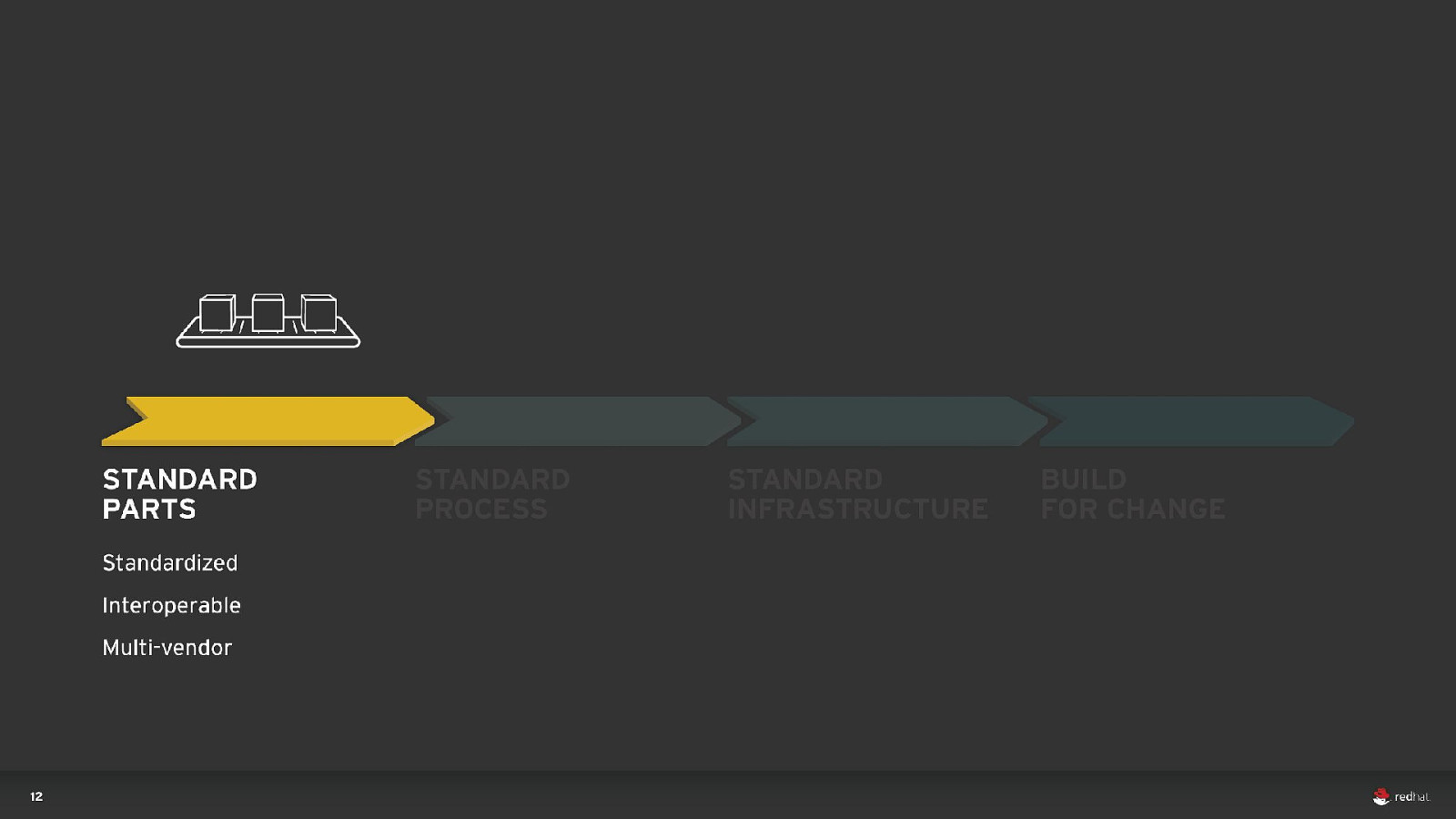
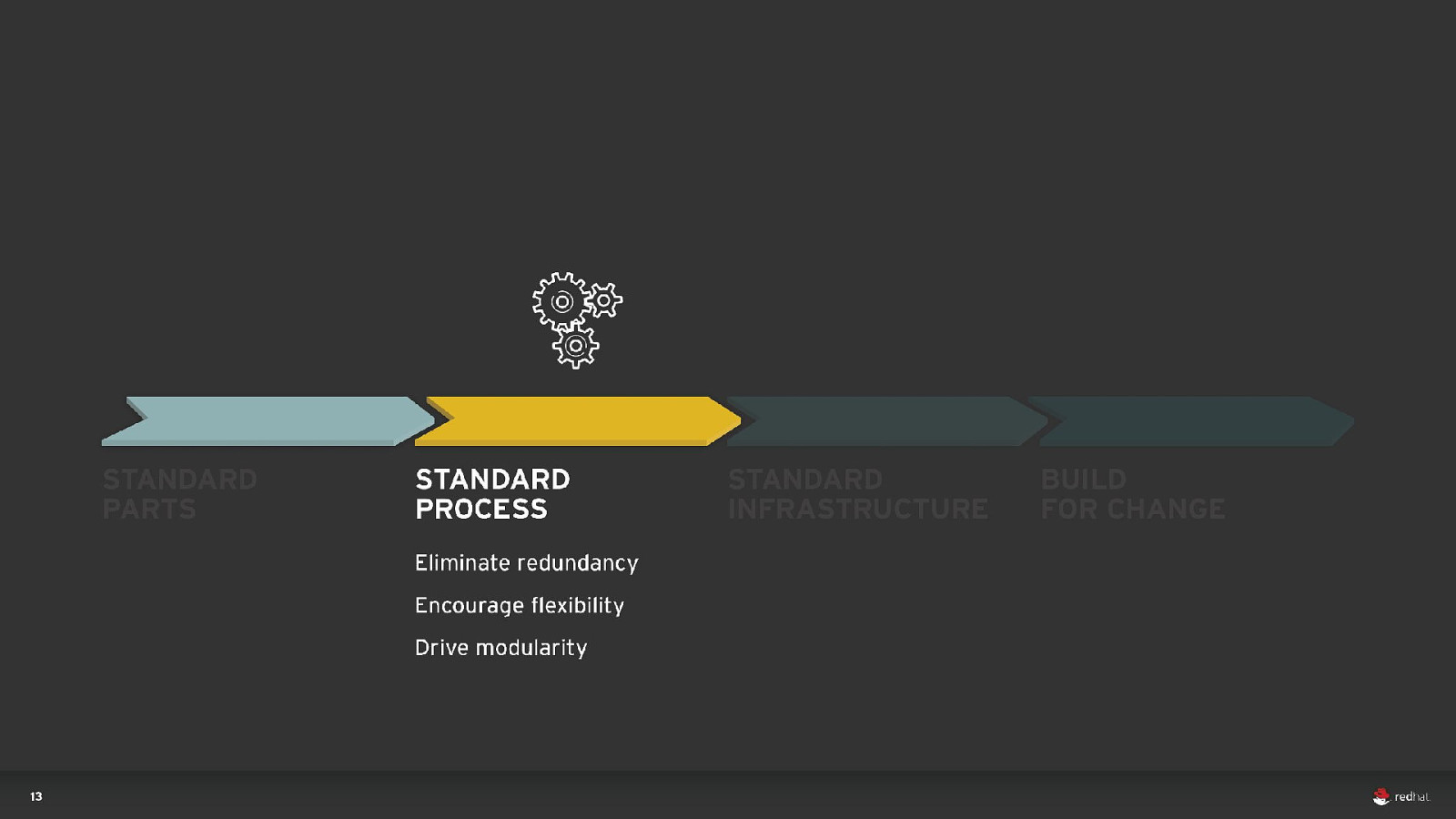
DEVOPS 40 Everything as code Application monitoring Automate everything Rapid feedback Continuous Integration/Delivery Rebuild vs. Repair Application is always “releaseable” Delivery pipeline
A Solution Adopting a container strategy will allow applications to be easily shared and deployed. 41
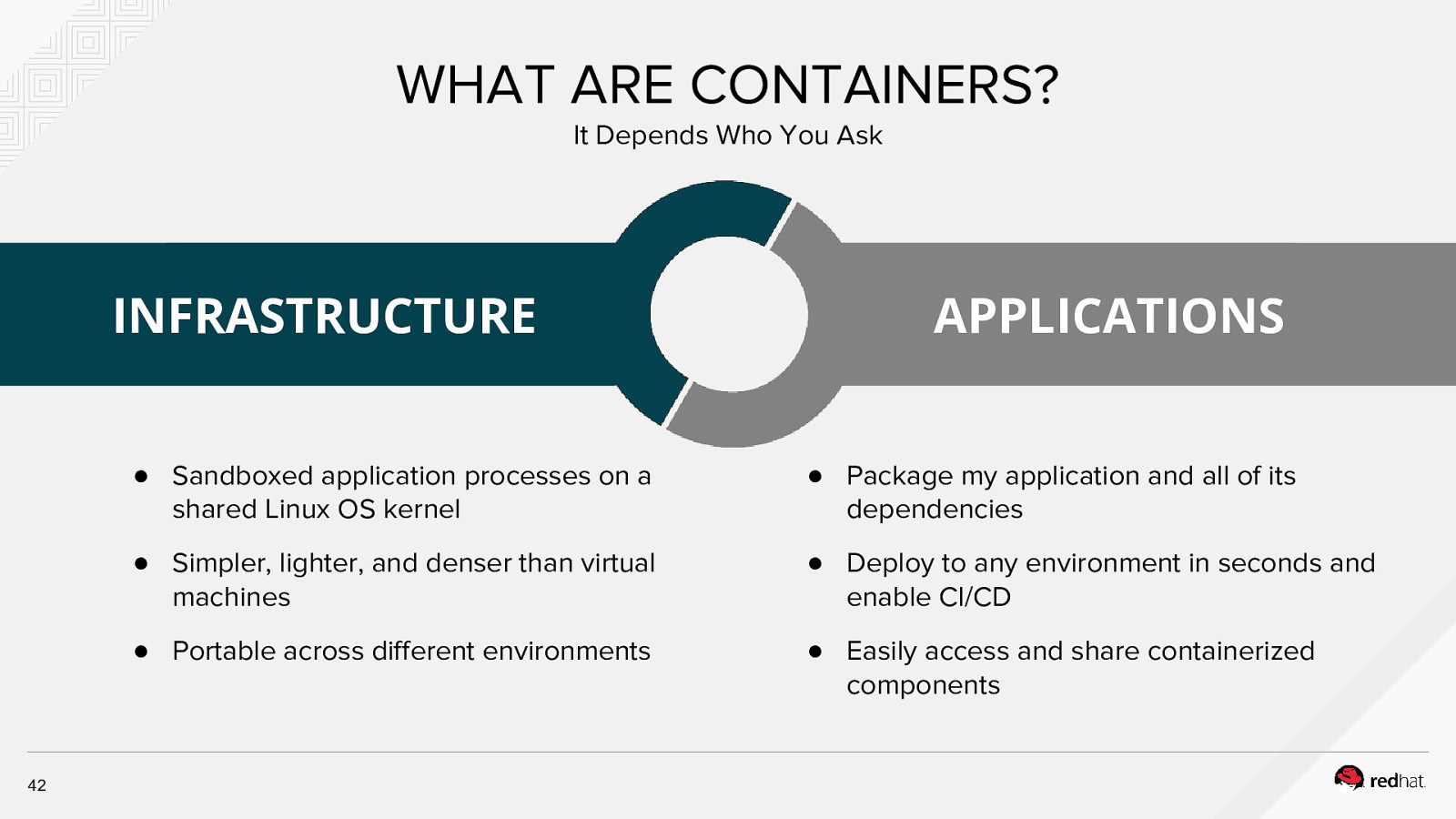
WHAT ARE CONTAINERS? It Depends Who You Ask INFRASTRUCTURE 42 APPLICATIONS ● Sandboxed application processes on a shared Linux OS kernel ● Package my application and all of its dependencies ● Simpler, lighter, and denser than virtual machines ● Deploy to any environment in seconds and enable CI/CD ● Portable across different environments ● Easily access and share containerized components
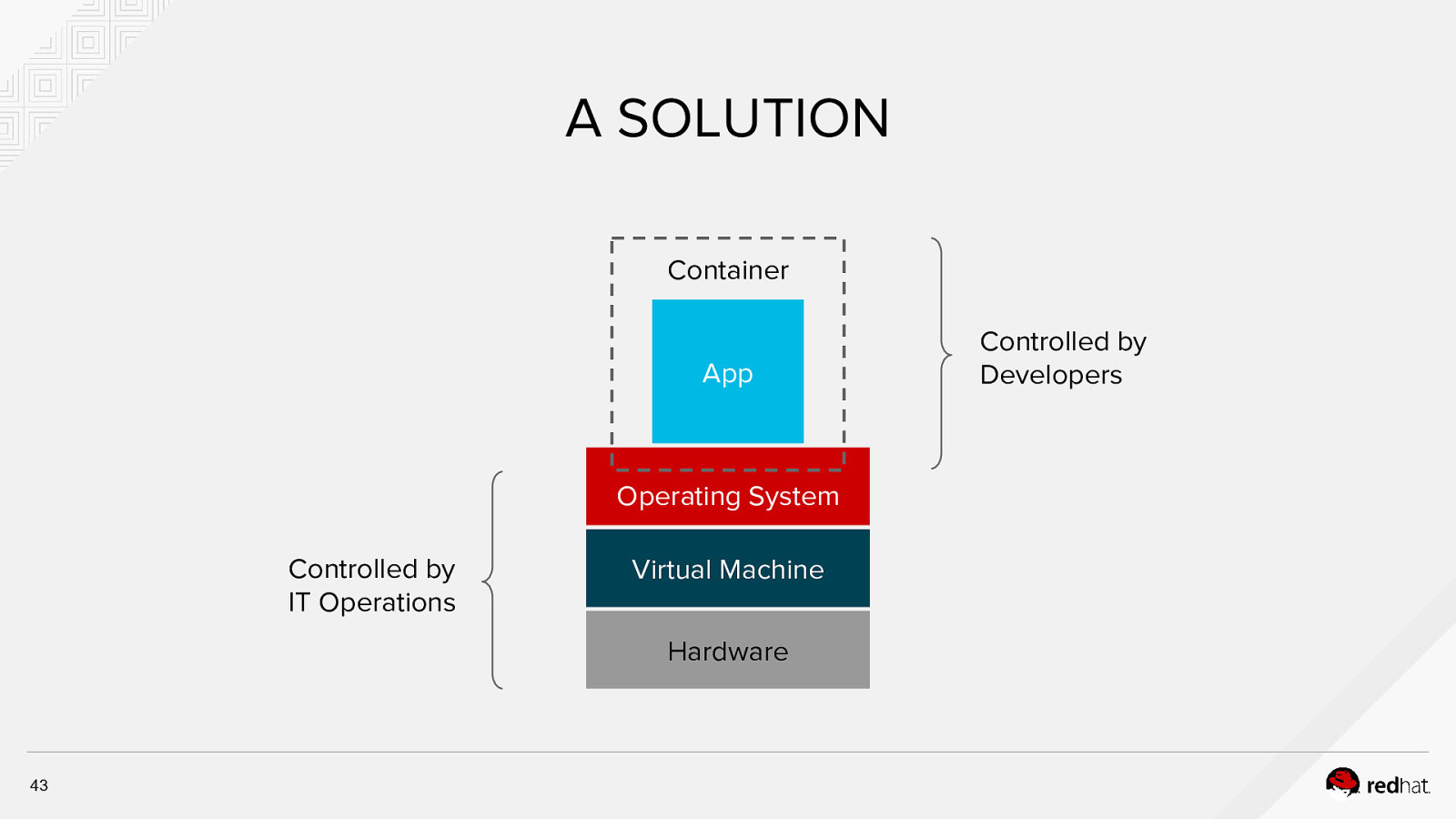
A SOLUTION Container App Operating System Controlled by IT Operations Virtual Machine Hardware 43 Controlled by Developers
A SOLUTION DEVELOPERS 44 I.T. OPERATIONS
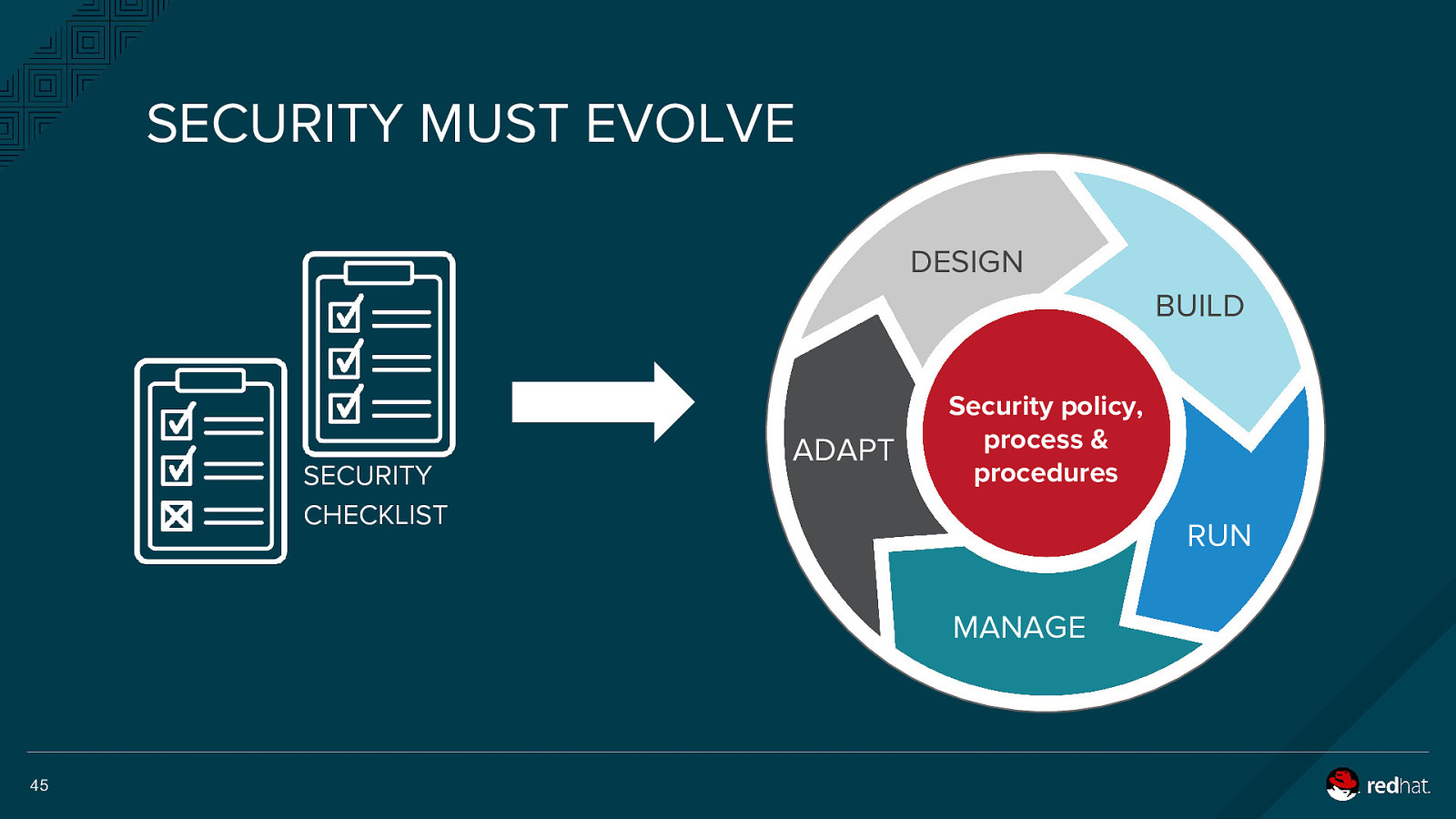
SECURITY MUST EVOLVE DESIGN BUILD SECURITY CHECKLIST ADAPT Security policy, process & procedures RUN MANAGE 45
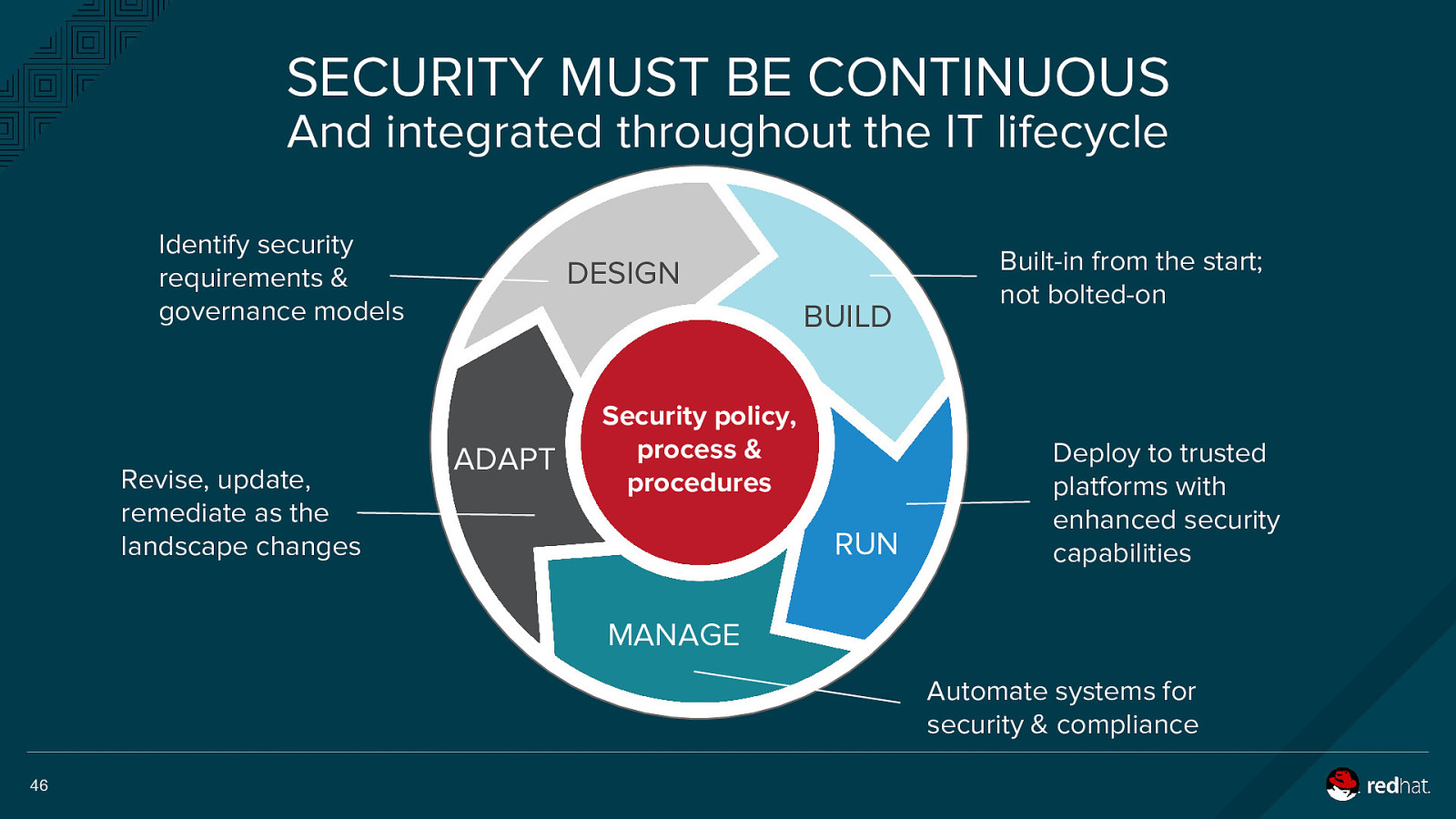
SECURITY MUST BE CONTINUOUS And integrated throughout the IT lifecycle Identify security requirements & governance models Revise, update, remediate as the landscape changes DESIGN BUILD ADAPT Security policy, process & procedures RUN Built-in from the start; not bolted-on Deploy to trusted platforms with enhanced security capabilities MANAGE Automate systems for security & compliance 46


We have to share to iterate quicker.
A cloud is sharing at run-time.
Open source is sharing at dev-time.
Agility is the capability.
You are the catalyst.

YOU ARE NOT AN IT CRAFTSMAN. YOU ARE AN IT MANUFACTURER.


Contact Info 56 LinkedIn: https://www.linkedin.com/in/shawndwells/ EMail: shawn@redhat.com Cell: 443-534-0130 (US EST) Blog: https://shawnwells.io
