AFS Zero Trust Strategy and Roadmap Partner Messaging Workshop
Slide 1

Slide 2
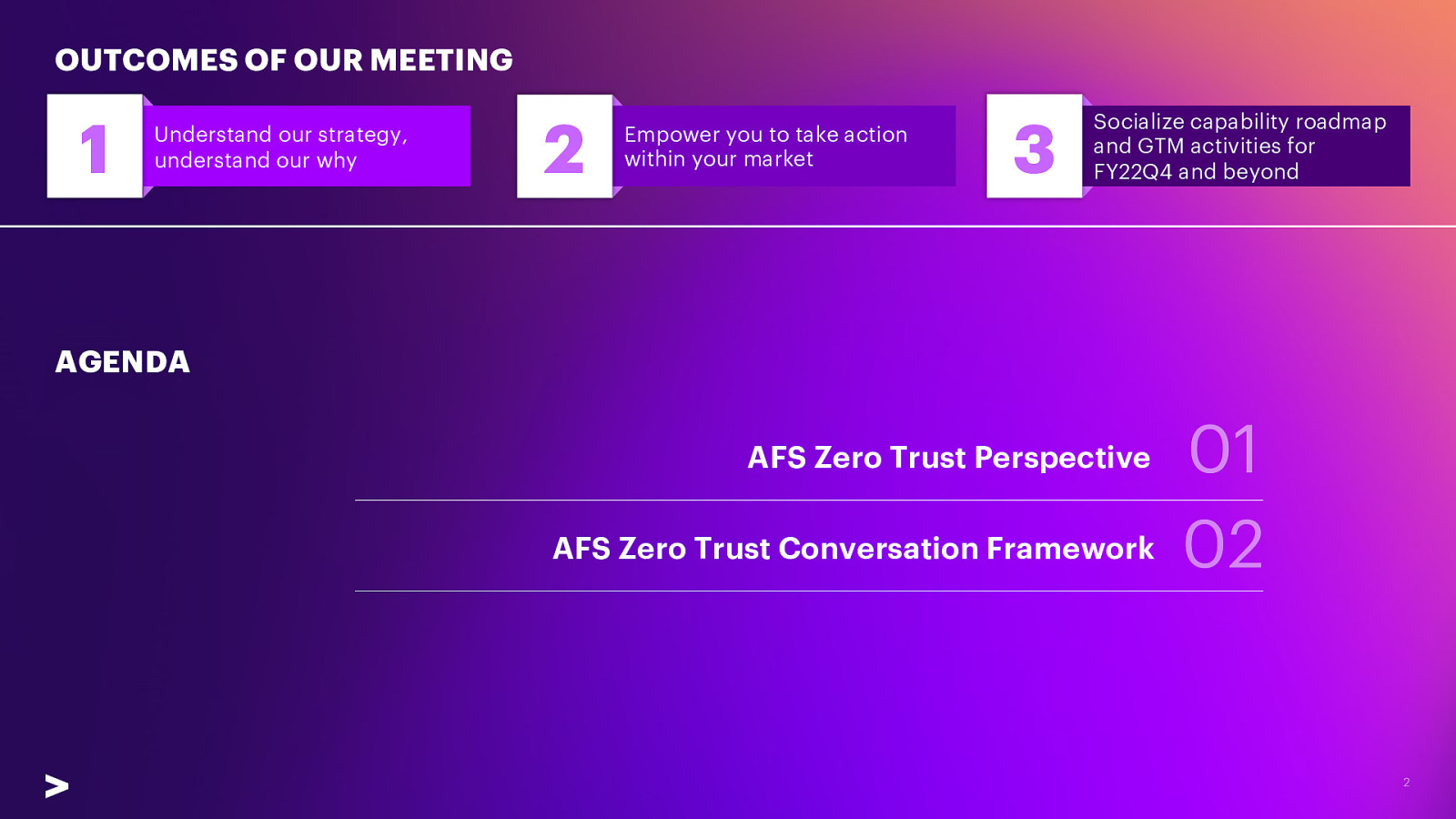
OUTCOMES OF OUR MEETING 1 Understand our strategy, understand our why 2 Empower you to take action within your market 3 Socialize capability roadmap and GTM activities for FY22Q4 and beyond AGENDA AFS Zero Trust Perspective AFS Zero Trust Conversation Framework
Slide 3
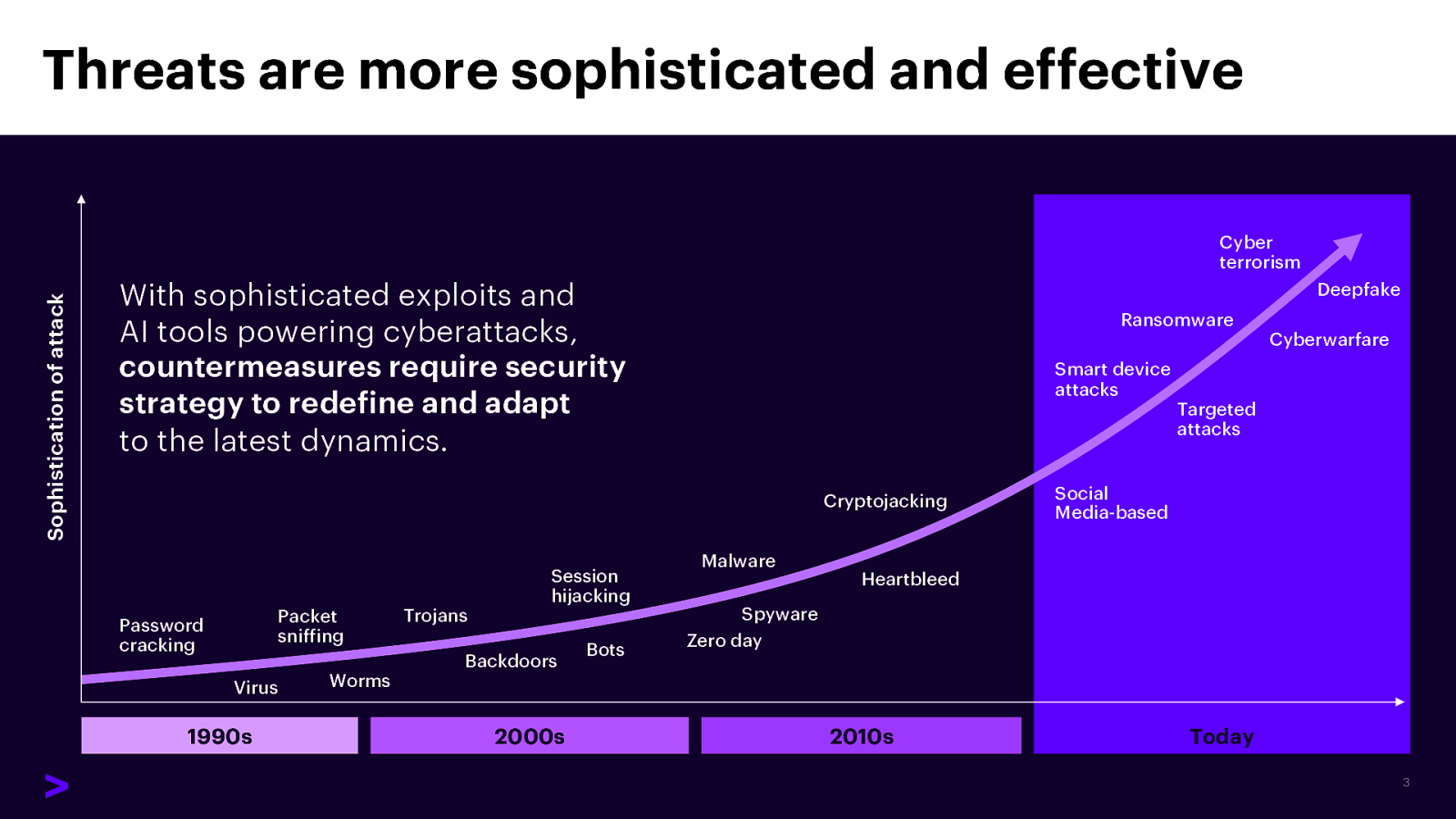
Threats are more sophisticated and effective Sophistication of attack Cyber terrorism With sophisticated exploits and AI tools powering cyberattacks, countermeasures require security strategy to redefine and adapt to the latest dynamics. Deepfake Ransomware Cyberwarfare Smart device attacks Targeted attacks Cryptojacking Session hijacking Packet sniffing Password cracking Trojans Backdoors Virus 1990s Bots Social Media-based Malware Heartbleed Spyware Zero day Worms 2000s 2010s Today
Slide 4

Security models cannot be static and must assume a threat actors are always present New Assumptions New Principles Intruders are omnipresent: A bad actor is always present, so we must reduce the potential “attack surface” Operate in real-time: Use dynamic threat analyses of multiple threat vectors Endpoints: Devices can be friendly one moment and hostile the next, even internal ones Data is the priority: What we’re really protecting is our intellectual property and data The network is insecure: The network is not be considered a security control for protection Streamline the security environment: Ensure our complex security environment is more manageable and organized This is known as the zero-trust security model
Slide 5
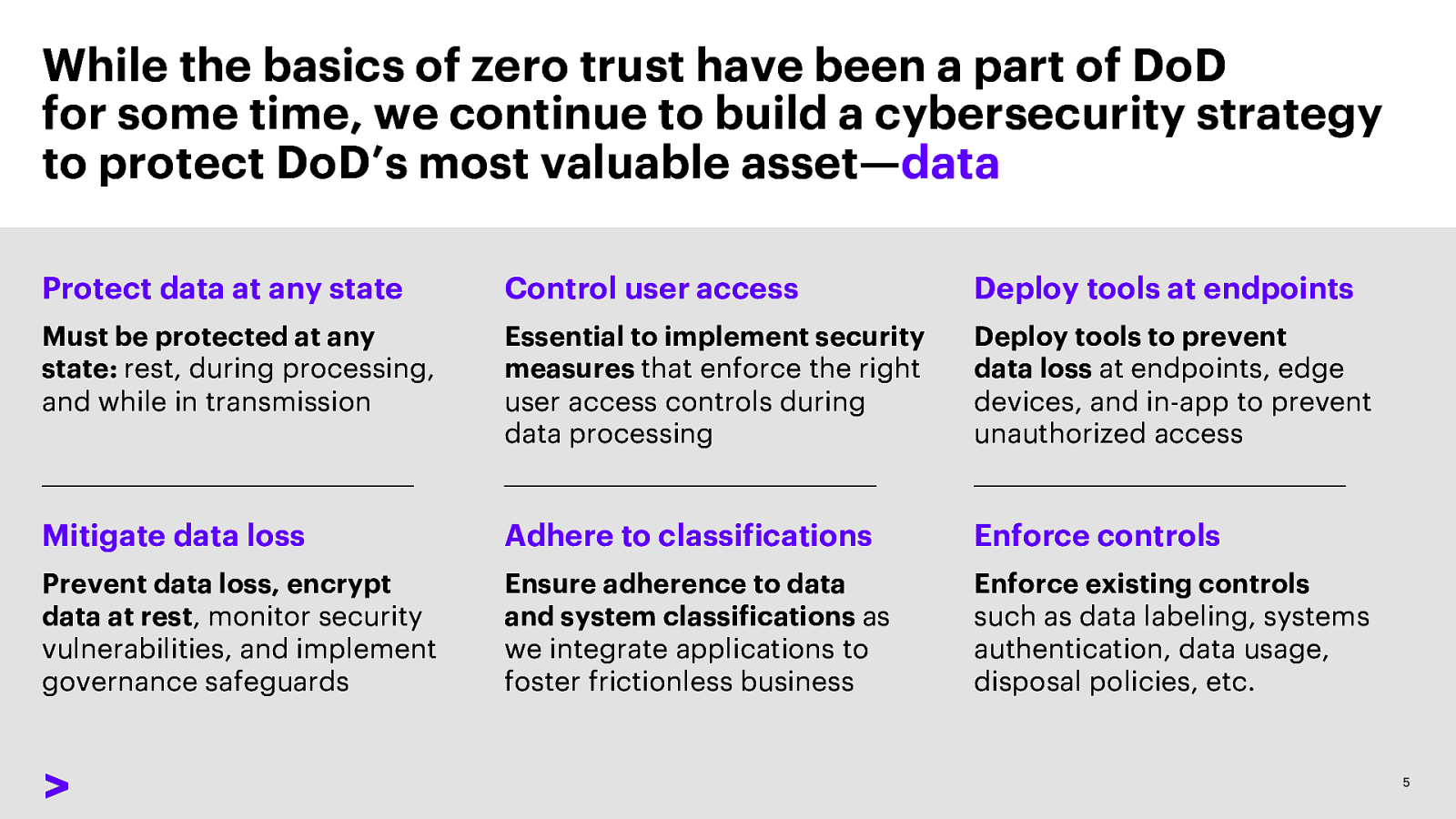
While the basics of zero trust have been a part of DoD for some time, we continue to build a cybersecurity strategy to protect DoD’s most valuable asset—data Protect data at any state Control user access Deploy tools at endpoints Must be protected at any state: rest, during processing, and while in transmission Essential to implement security measures that enforce the right user access controls during data processing Deploy tools to prevent data loss at endpoints, edge devices, and in-app to prevent unauthorized access Mitigate data loss Adhere to classifications Enforce controls Prevent data loss, encrypt data at rest, monitor security vulnerabilities, and implement governance safeguards Ensure adherence to data and system classifications as we integrate applications to foster frictionless business Enforce existing controls such as data labeling, systems authentication, data usage, disposal policies, etc.
Slide 6
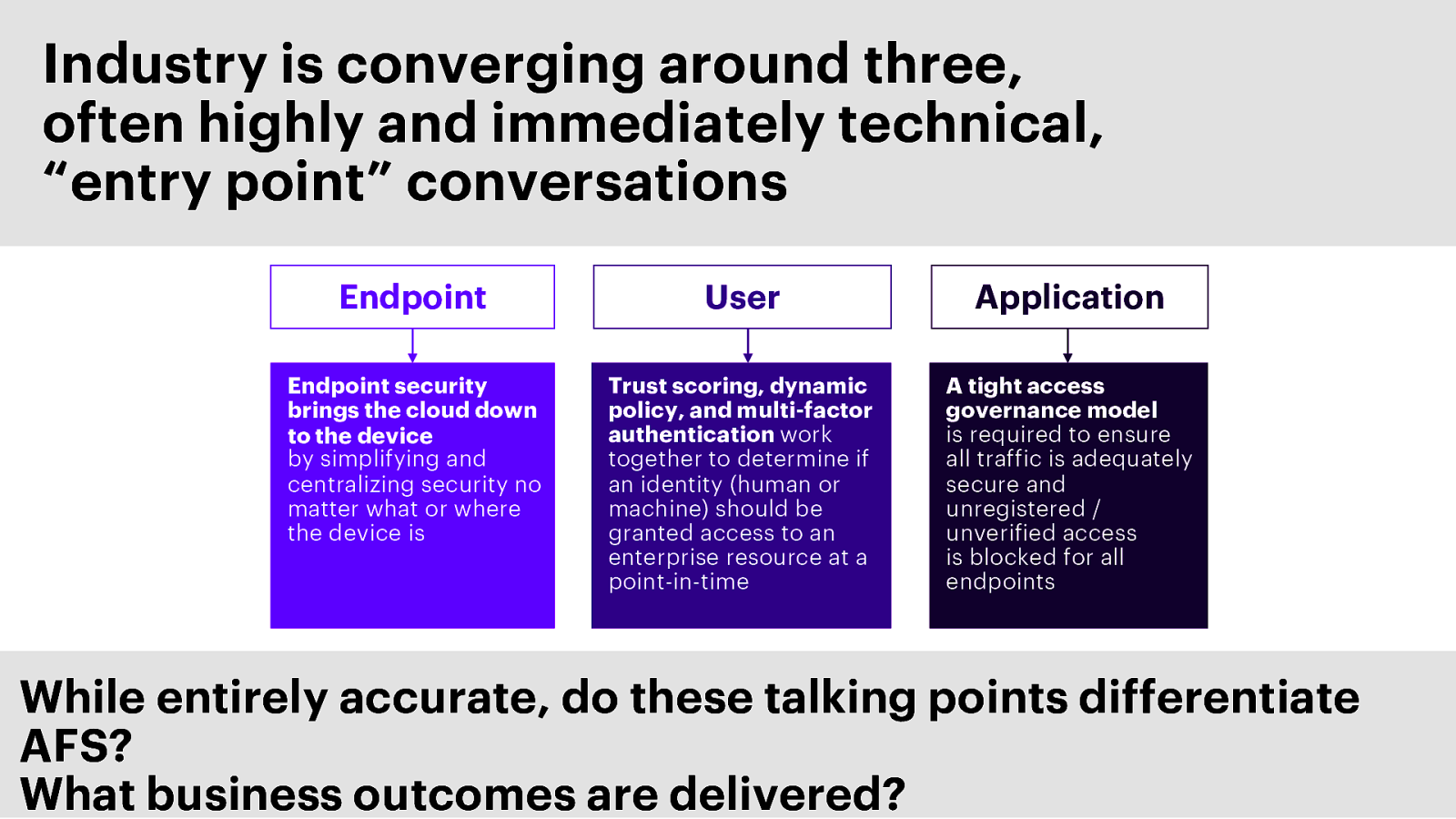
Industry is converging around three, often highly and immediately technical, “entry point” conversations Endpoint User Application Endpoint security brings the cloud down to the device by simplifying and centralizing security no matter what or where the device is Trust scoring, dynamic policy, and multi-factor authentication work together to determine if an identity (human or machine) should be granted access to an enterprise resource at a point-in-time A tight access governance model is required to ensure all traffic is adequately secure and unregistered / unverified access is blocked for all endpoints While entirely accurate, do these talking points differentiate AFS? What business outcomes are delivered?
Slide 7
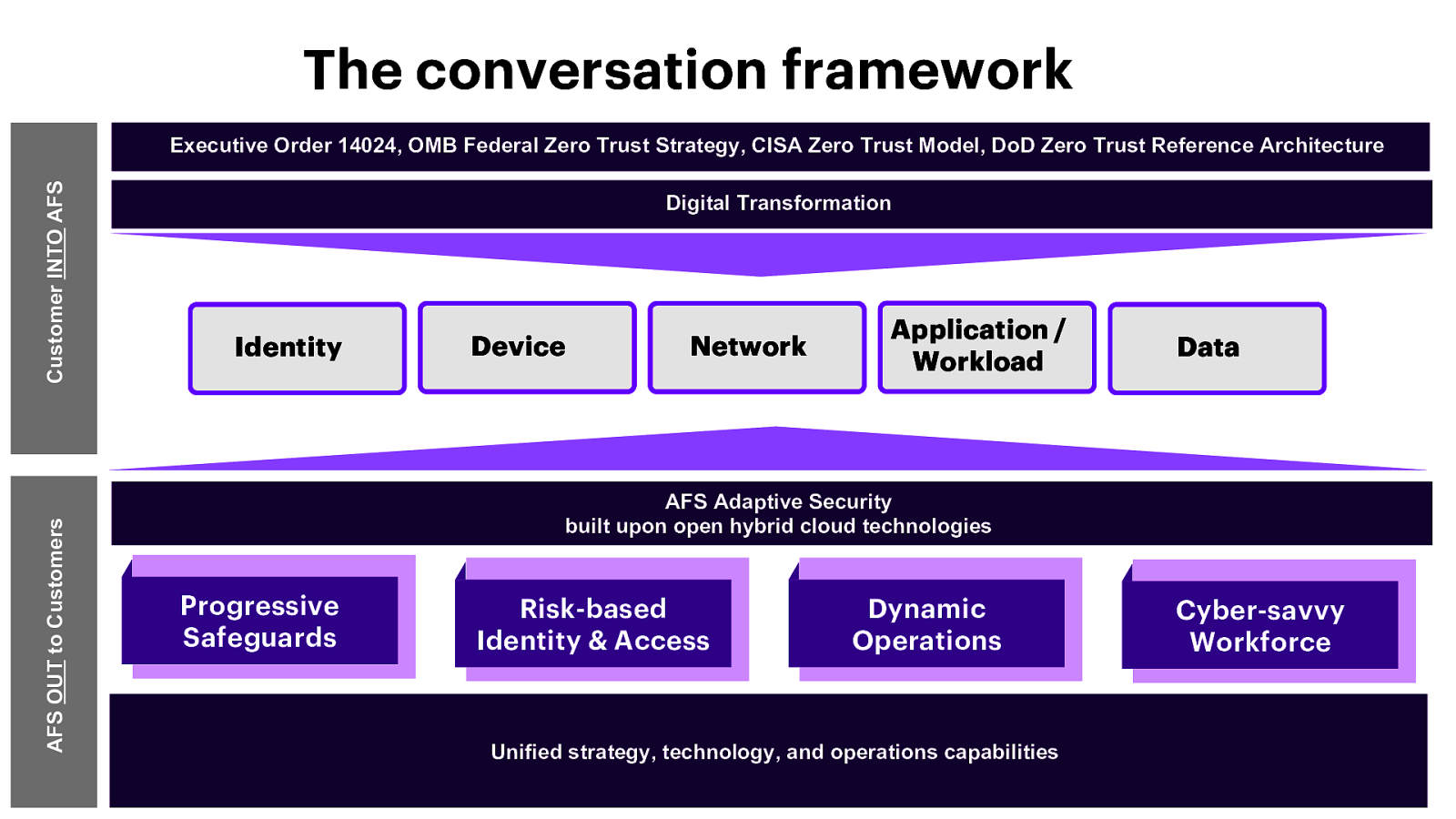
The conversation framework AFS OUT to Customers Customer INTO AFS Executive Order 14024, OMB Federal Zero Trust Strategy, CISA Zero Trust Model, DoD Zero Trust Reference Architecture Digital Transformation Identity Device Network Application / Workload Data AFS Adaptive Security built upon open hybrid cloud technologies Progressive Safeguards Risk-based Identity & Access Dynamic Operations Unified strategy, technology, and operations capabilities Cyber-savvy Workforce
Slide 8
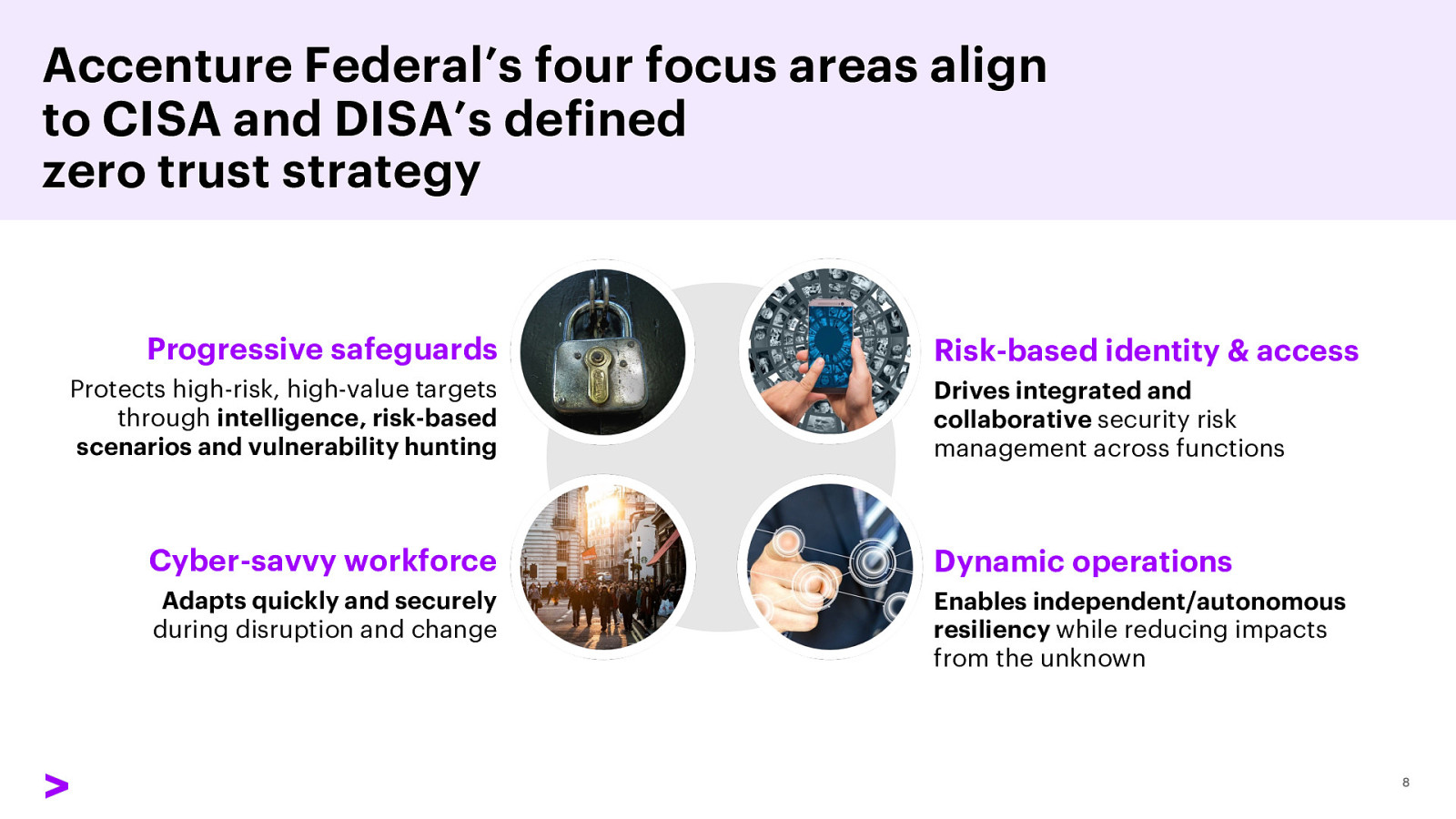
Accenture Federal’s four focus areas align to CISA and DISA’s defined zero trust strategy Progressive safeguards Protects high-risk, high-value targets through intelligence, risk-based scenarios and vulnerability hunting Risk-based identity & access Drives integrated and collaborative security risk management across functions Cyber-savvy workforce Dynamic operations Adapts quickly and securely during disruption and change Enables independent/autonomous resiliency while reducing impacts from the unknown
Slide 9
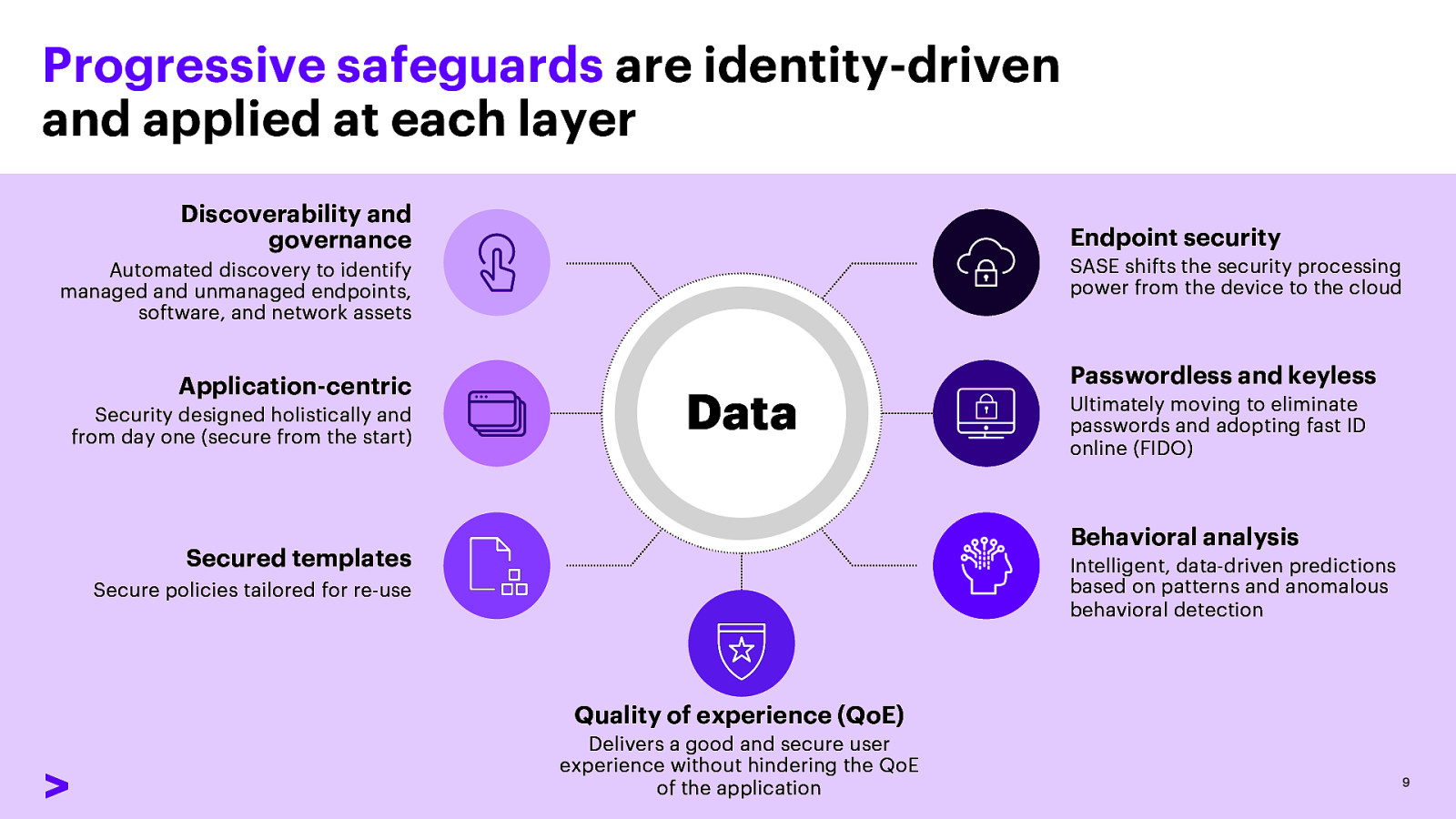
Progressive safeguards are identity-driven and applied at each layer Discoverability and governance Endpoint security SASE shifts the security processing power from the device to the cloud Automated discovery to identify managed and unmanaged endpoints, software, and network assets Application-centric Security designed holistically and from day one (secure from the start) Passwordless and keyless Data Ultimately moving to eliminate passwords and adopting fast ID online (FIDO) Behavioral analysis Secured templates Intelligent, data-driven predictions based on patterns and anomalous behavioral detection Secure policies tailored for re-use Quality of experience (QoE) Delivers a good and secure user experience without hindering the QoE of the application
Slide 10
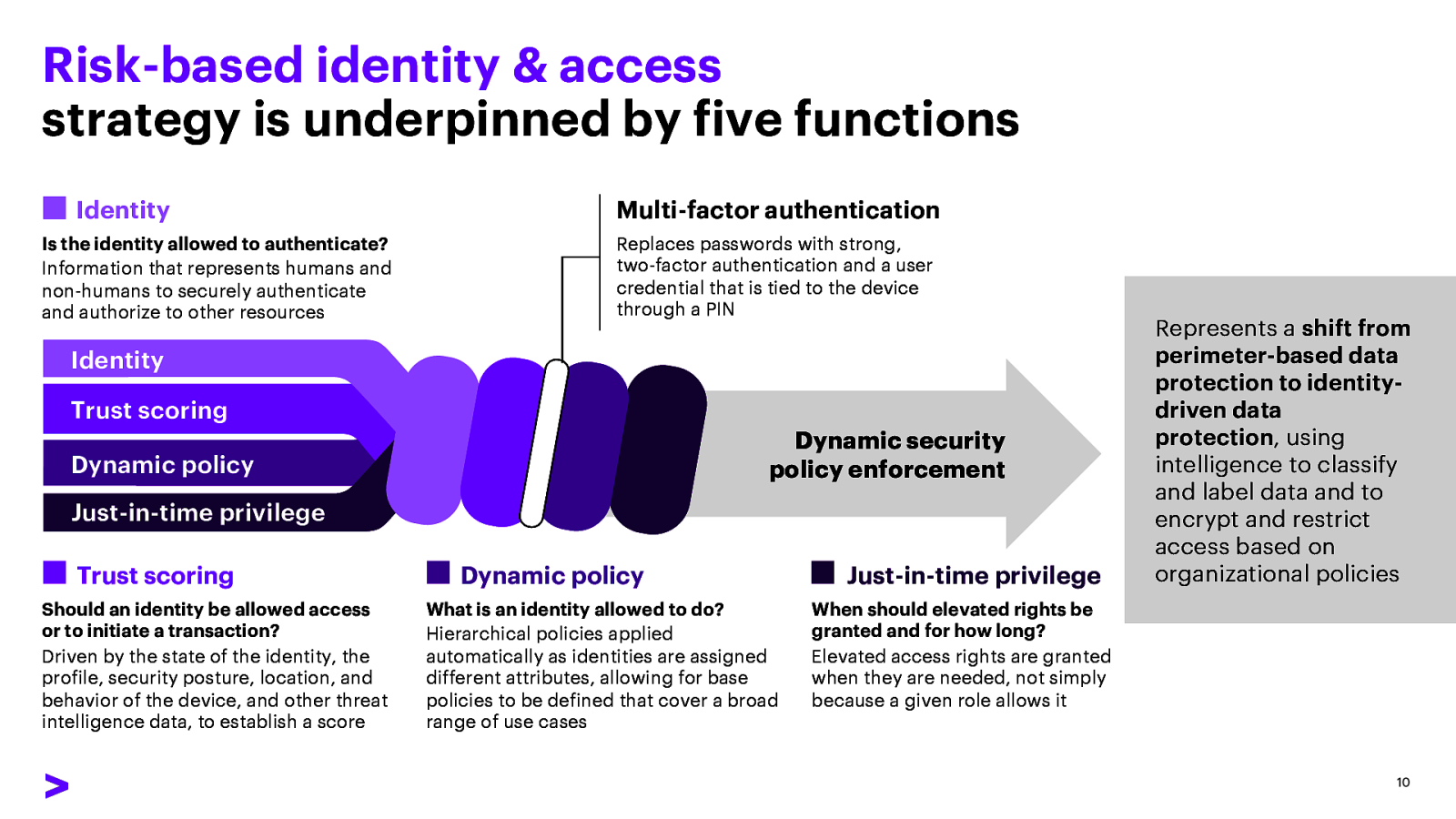
Risk-based identity & access strategy is underpinned by five functions Identity Is the identity allowed to authenticate? Information that represents humans and non-humans to securely authenticate and authorize to other resources Multi-factor authentication Replaces passwords with strong, two-factor authentication and a user credential that is tied to the device through a PIN Identity Trust scoring Dynamic security policy enforcement Dynamic policy Just-in-time privilege Trust scoring Should an identity be allowed access or to initiate a transaction? Driven by the state of the identity, the profile, security posture, location, and behavior of the device, and other threat intelligence data, to establish a score Dynamic policy What is an identity allowed to do? Hierarchical policies applied automatically as identities are assigned different attributes, allowing for base policies to be defined that cover a broad range of use cases Just-in-time privilege When should elevated rights be granted and for how long? Elevated access rights are granted when they are needed, not simply because a given role allows it Represents a shift from perimeter-based data protection to identitydriven data protection, using intelligence to classify and label data and to encrypt and restrict access based on organizational policies
Slide 11
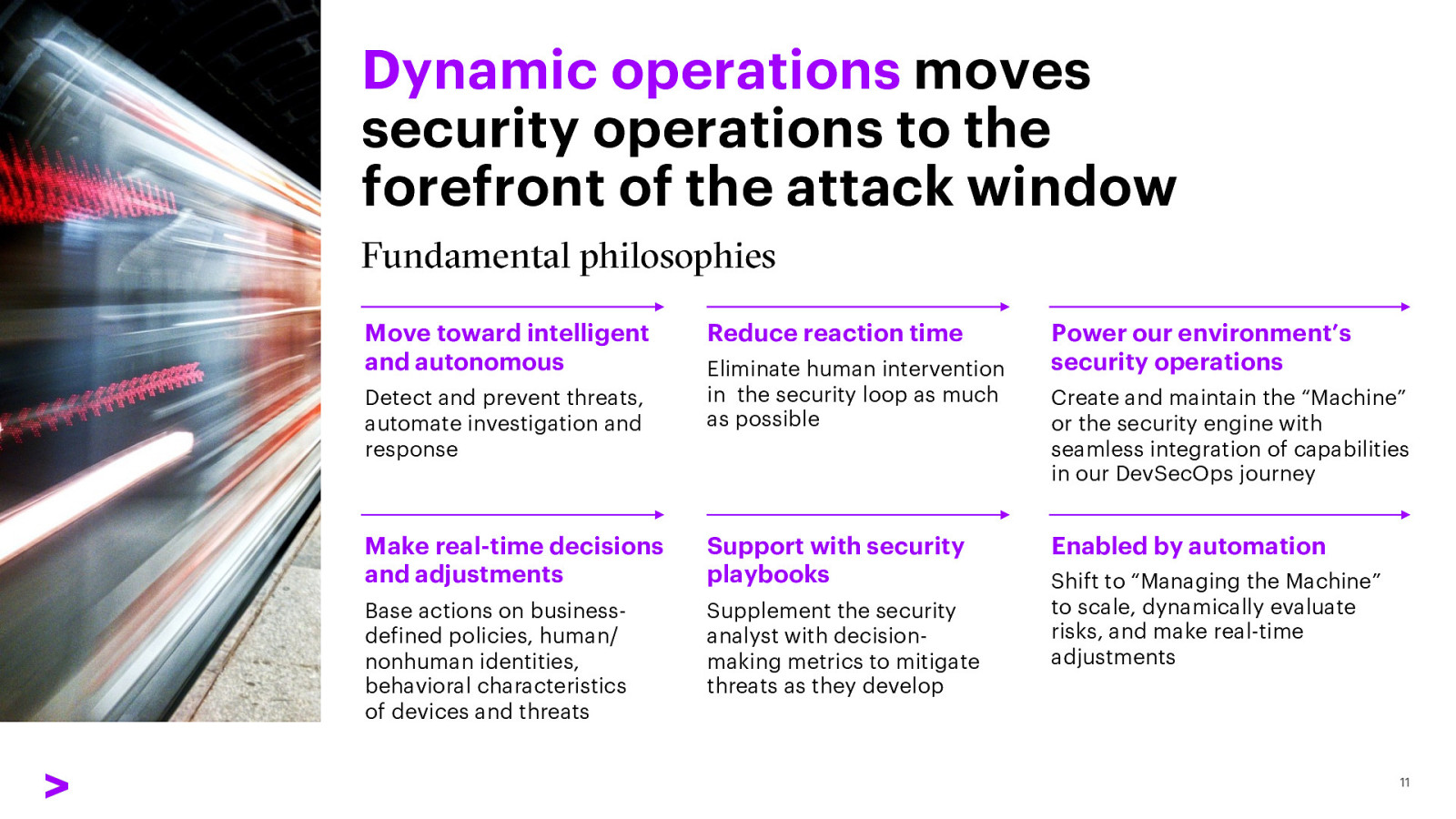
Dynamic operations moves security operations to the forefront of the attack window Fundamental philosophies Move toward intelligent and autonomous Detect and prevent threats, automate investigation and response Reduce reaction time Eliminate human intervention in the security loop as much as possible Make real-time decisions and adjustments Support with security playbooks Base actions on businessdefined policies, human/ nonhuman identities, behavioral characteristics of devices and threats Supplement the security analyst with decisionmaking metrics to mitigate threats as they develop Power our environment’s security operations Create and maintain the “Machine” or the security engine with seamless integration of capabilities in our DevSecOps journey Enabled by automation Shift to “Managing the Machine” to scale, dynamically evaluate risks, and make real-time adjustments
Slide 12
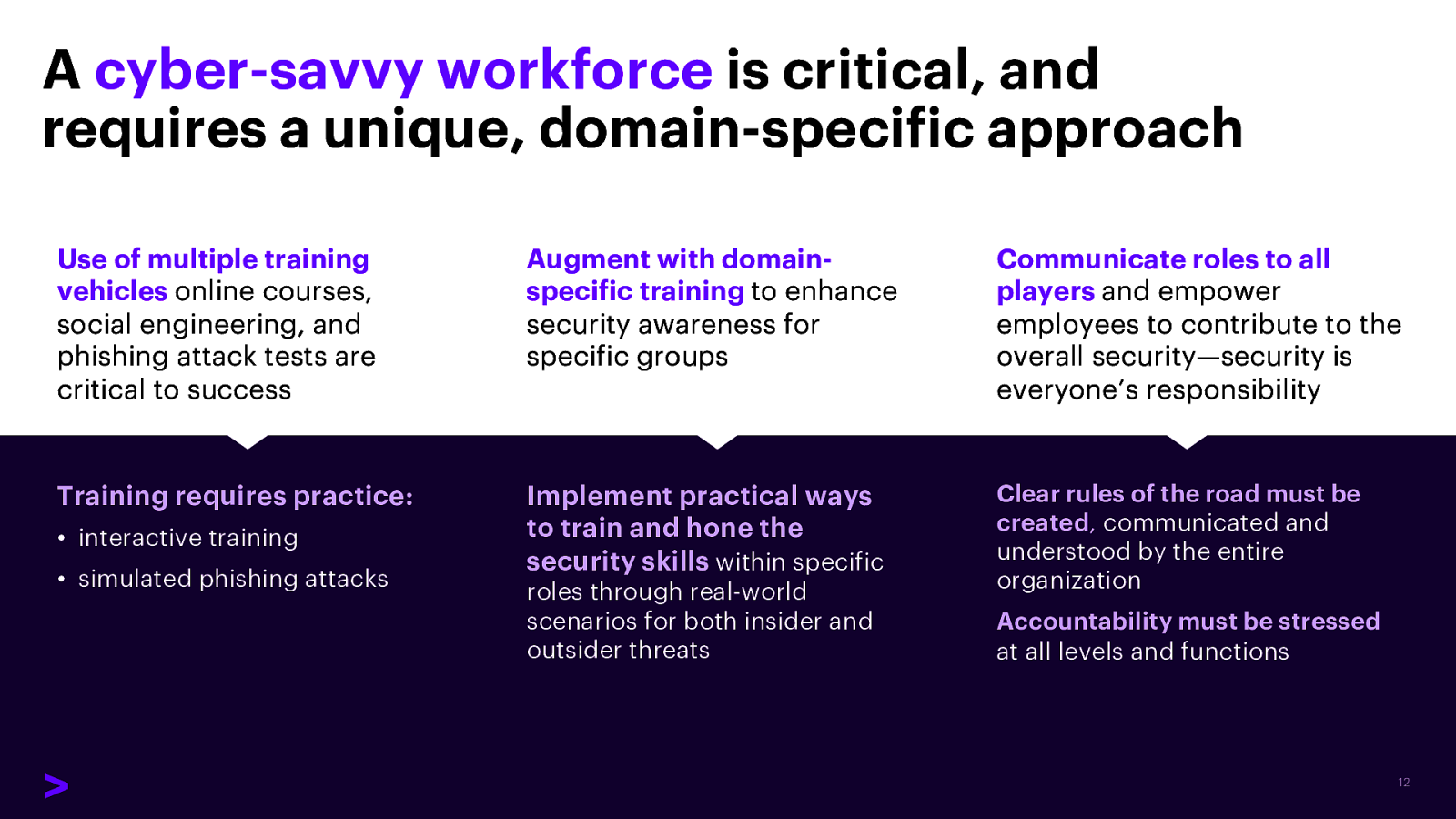
A cyber-savvy workforce is critical, and requires a unique, domain-specific approach Use of multiple training vehicles online courses, social engineering, and phishing attack tests are critical to success Augment with domainspecific training to enhance security awareness for specific groups Communicate roles to all players and empower employees to contribute to the overall security—security is everyone’s responsibility Training requires practice: Implement practical ways to train and hone the security skills within specific Clear rules of the road must be created, communicated and understood by the entire organization • interactive training • simulated phishing attacks roles through real-world scenarios for both insider and outsider threats Accountability must be stressed at all levels and functions
Slide 13
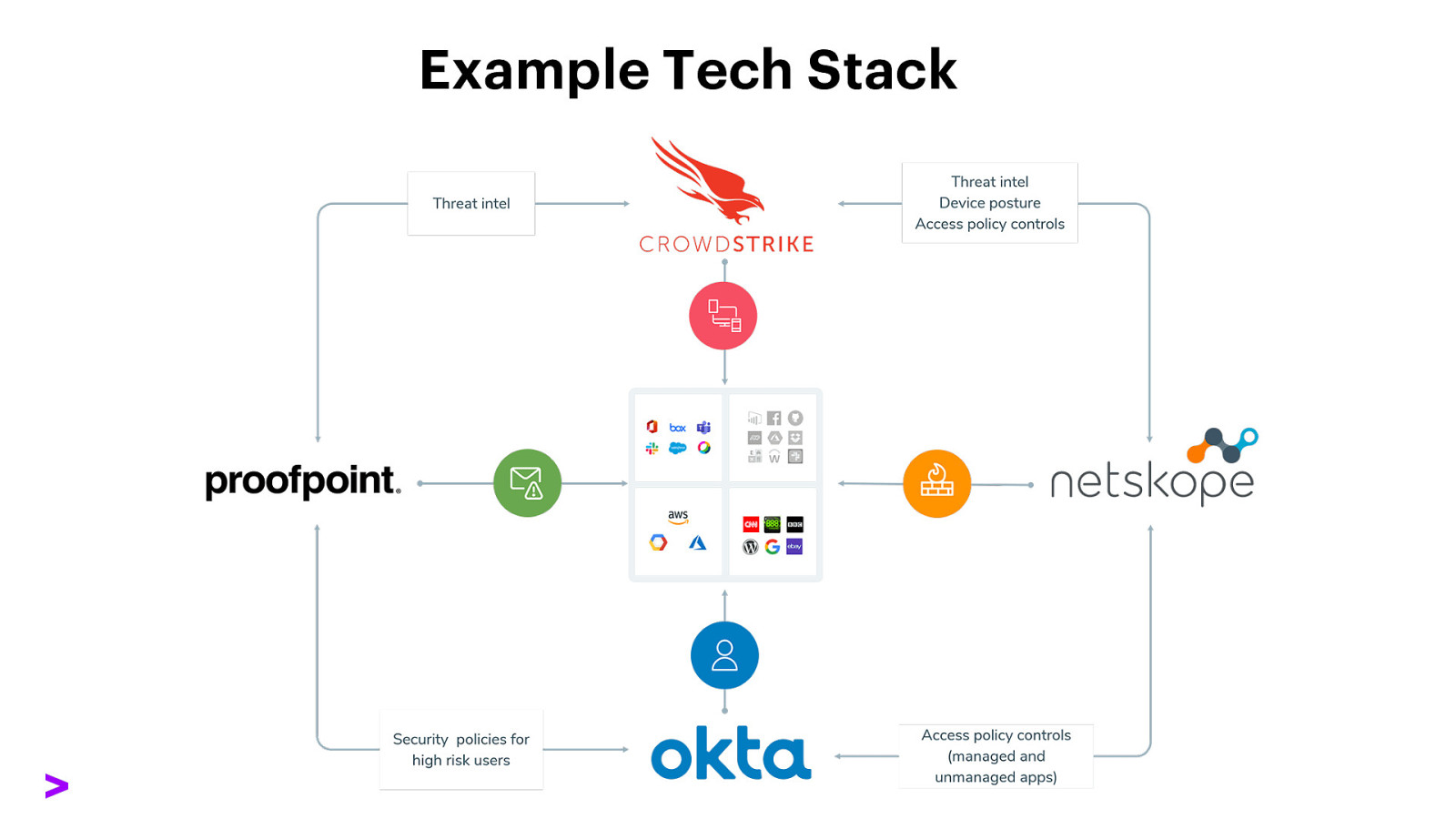
Example Tech Stack
Slide 14
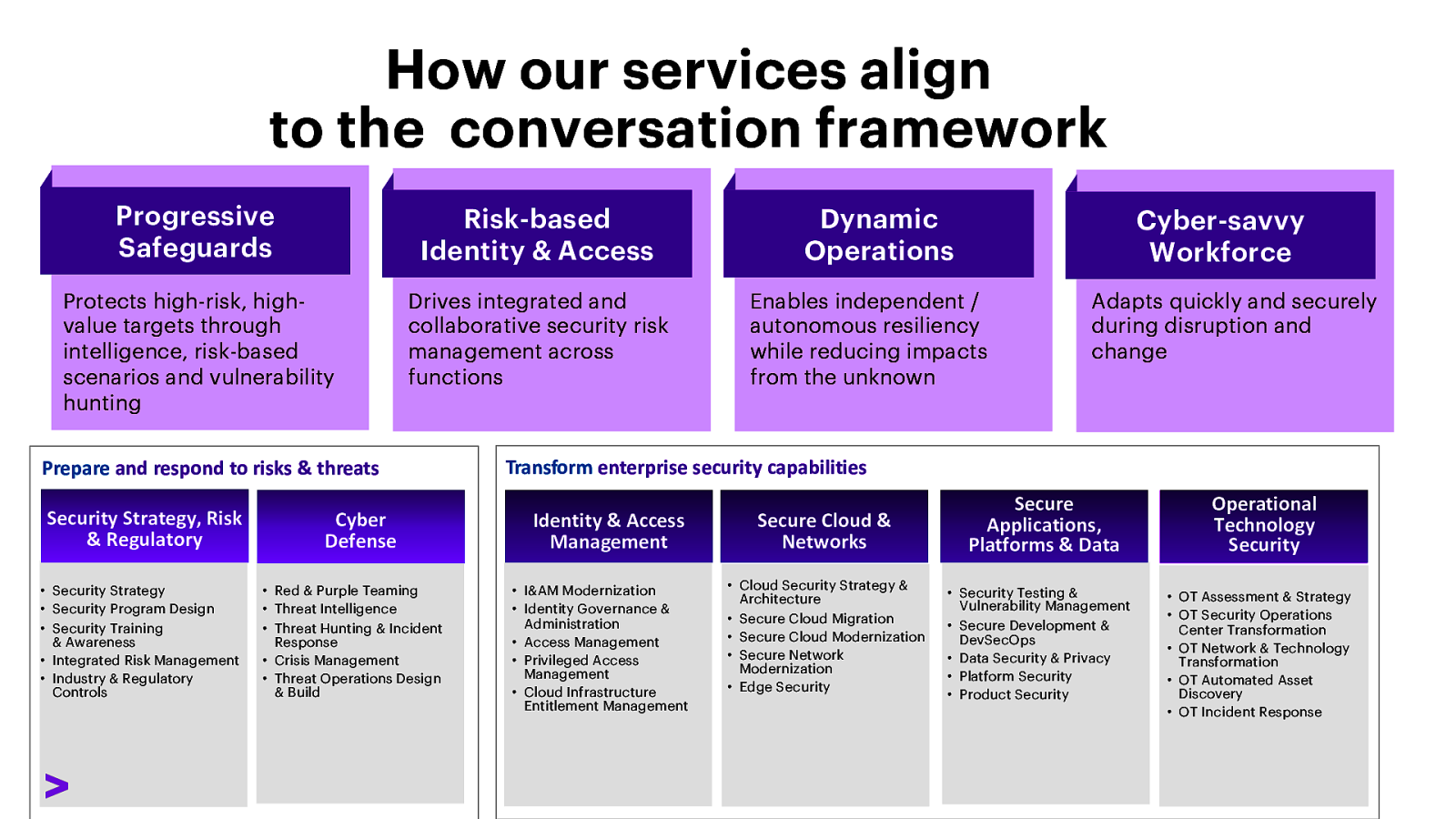
How our services align to the conversation framework Progressive Safeguards Risk-based Identity & Access Protects high-risk, highvalue targets through intelligence, risk-based scenarios and vulnerability hunting Drives integrated and collaborative security risk management across functions Prepare and respond to risks & threats Security Strategy, Risk & Regulatory • Security Strategy • Security Program Design • Security Training & Awareness • Integrated Risk Management • Industry & Regulatory Controls Cyber Defense • Red & Purple Teaming • Threat Intelligence • Threat Hunting & Incident Response • Crisis Management • Threat Operations Design & Build Dynamic Operations Cyber-savvy Workforce Enables independent / autonomous resiliency while reducing impacts from the unknown Adapts quickly and securely during disruption and change Transform enterprise security capabilities Identity & Access Management • I&AM Modernization • Identity Governance & Administration • Access Management • Privileged Access Management • Cloud Infrastructure Entitlement Management Secure Cloud & Networks • Cloud Security Strategy & Architecture • Secure Cloud Migration • Secure Cloud Modernization • Secure Network Modernization • Edge Security Secure Applications, Platforms & Data • Security Testing & Vulnerability Management • Secure Development & DevSecOps • Data Security & Privacy • Platform Security • Product Security Operational Technology Security • OT Assessment & Strategy • OT Security Operations Center Transformation • OT Network & Technology Transformation • OT Automated Asset Discovery • OT Incident Response
Slide 15

Questions or comments SHAWN WELLS Managing Director Cybersecurity Strategy & Technology shawn.wells@accenturefederal.com 443-534-0130 (Washington, D.C.)
Slide 16

Supplemental
Slide 17

Accenture’s DoD Zero Trust strategy is to fortify your cyber resilience, accelerate security innovation, and build elevated trust. To achieve this, we will help DoD continue to optimize against today’s threats, while being adaptive to an expanding and worsening threat landscape.
Slide 18

As the threat landscape continues to change and evolve, so must we. We not only need to respond to the new threats as they emerge, but we must anticipate them.