OpenSCAP Workshop: Hands-on Labs to explore Scanning, Reporting, Remediation
A presentation at OpenSCAP Workshop in in McLean, VA, USA by Shawn Wells

OpenSCAP Workshop Hands-on Labs to explore Scanning, Reporting, Remediation Shawn Wells shawn@redhat.com || 443-534-0130 (US EST) ADD NAME (View > Master > Slide master)

1.What’s the latest in the Linux Security Automation space? a. Government & Commercial Initiatives b.Formal and Emerging SCAP Standards 2.What tools and content are available today? a. For enumerating (known) software vulnerabilities b.For assessing configuration
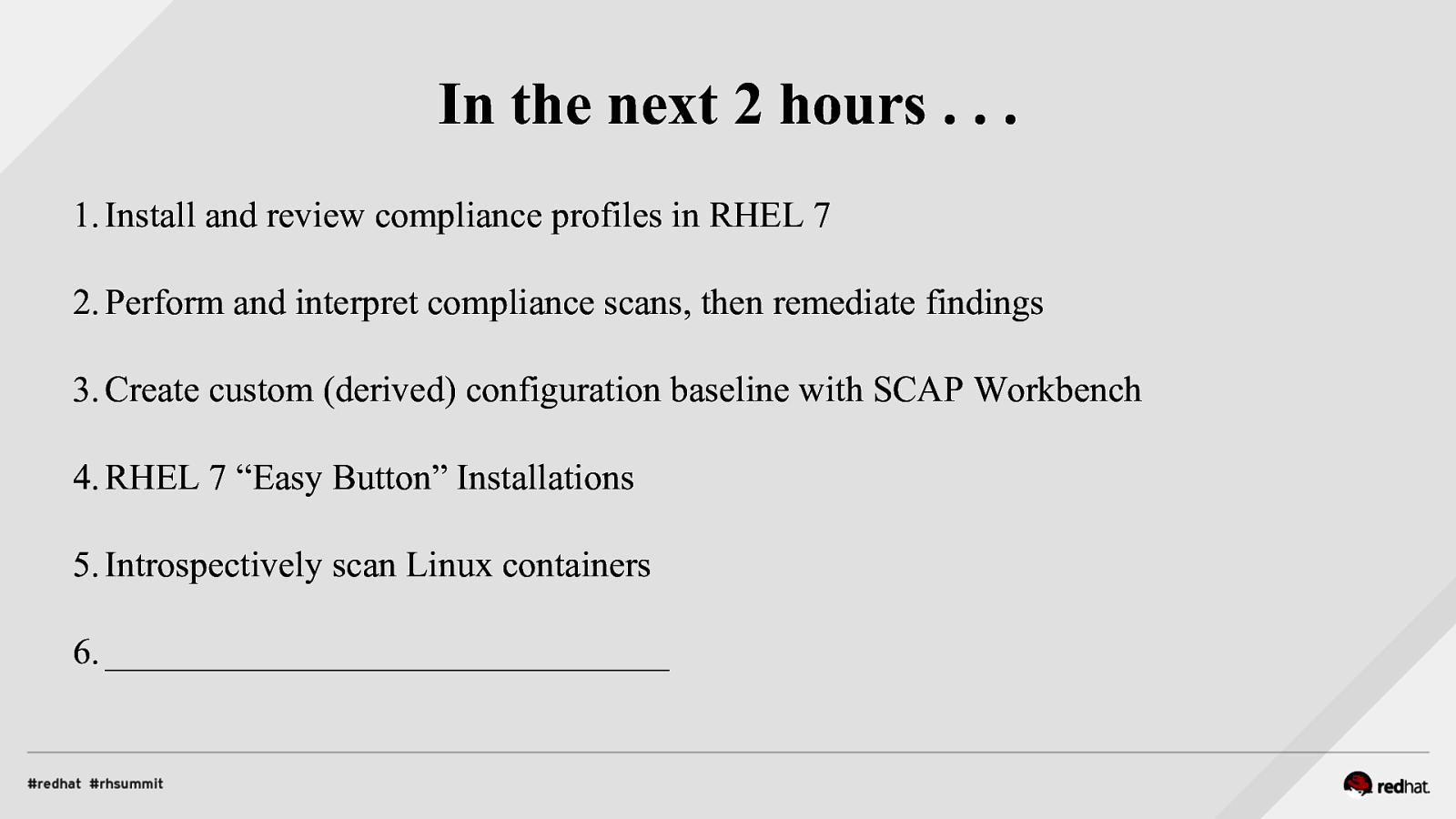
In the next 2 hours … 1. Install and review compliance profiles in RHEL 7 2. Perform and interpret compliance scans, then remediate findings 3. Create custom (derived) configuration baseline with SCAP Workbench 4. RHEL 7 “Easy Button” Installations 5. Introspectively scan Linux containers 6. _______________________________
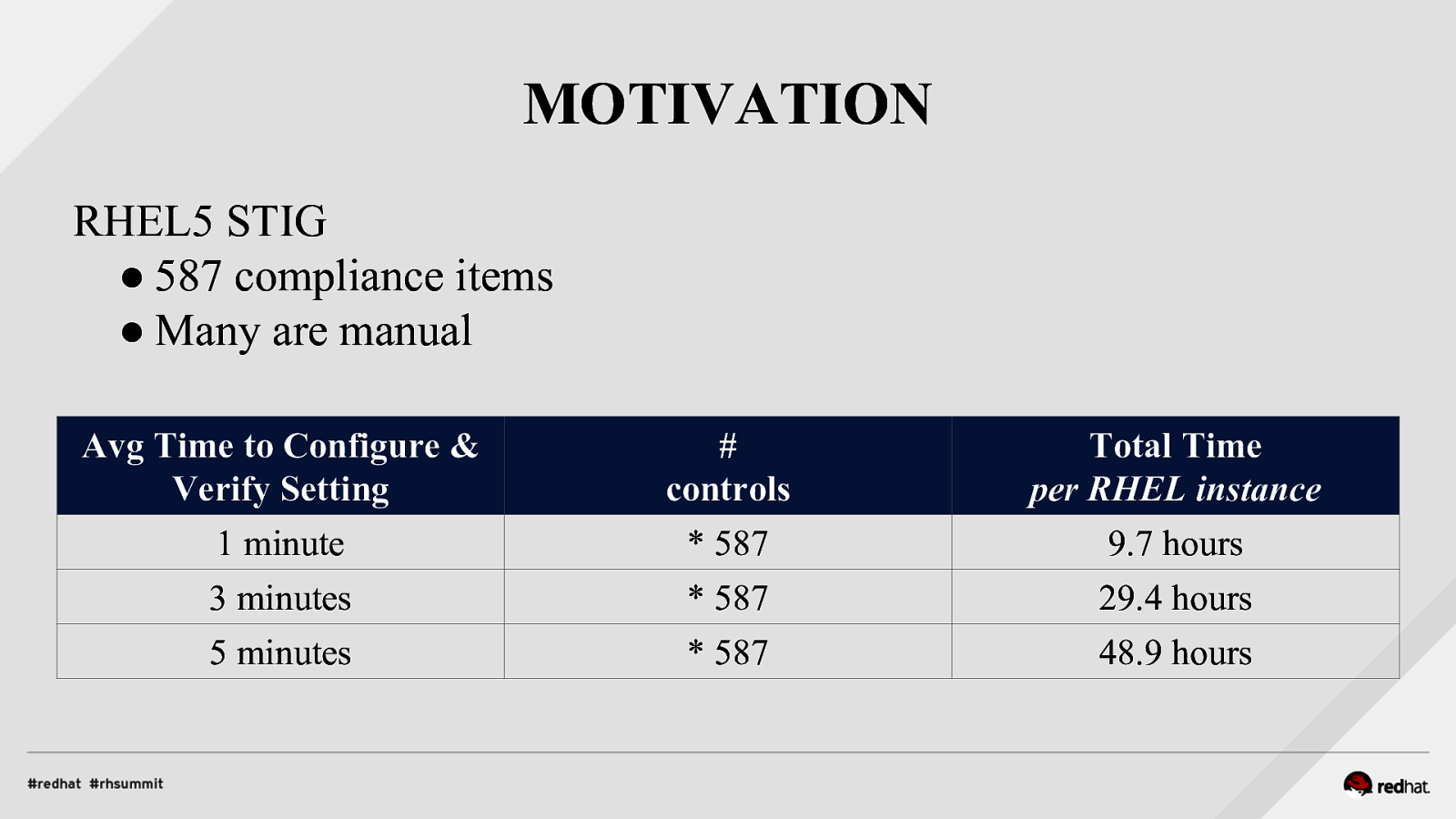
MOTIVATION RHEL5 STIG ● 587 compliance items ● Many are manual Avg Time to Configure & Verify Setting 1 minute 3 minutes 5 minutes
controls * 587 * 587 * 587
Total Time per RHEL instance 9.7 hours 29.4 hours 48.9 hours
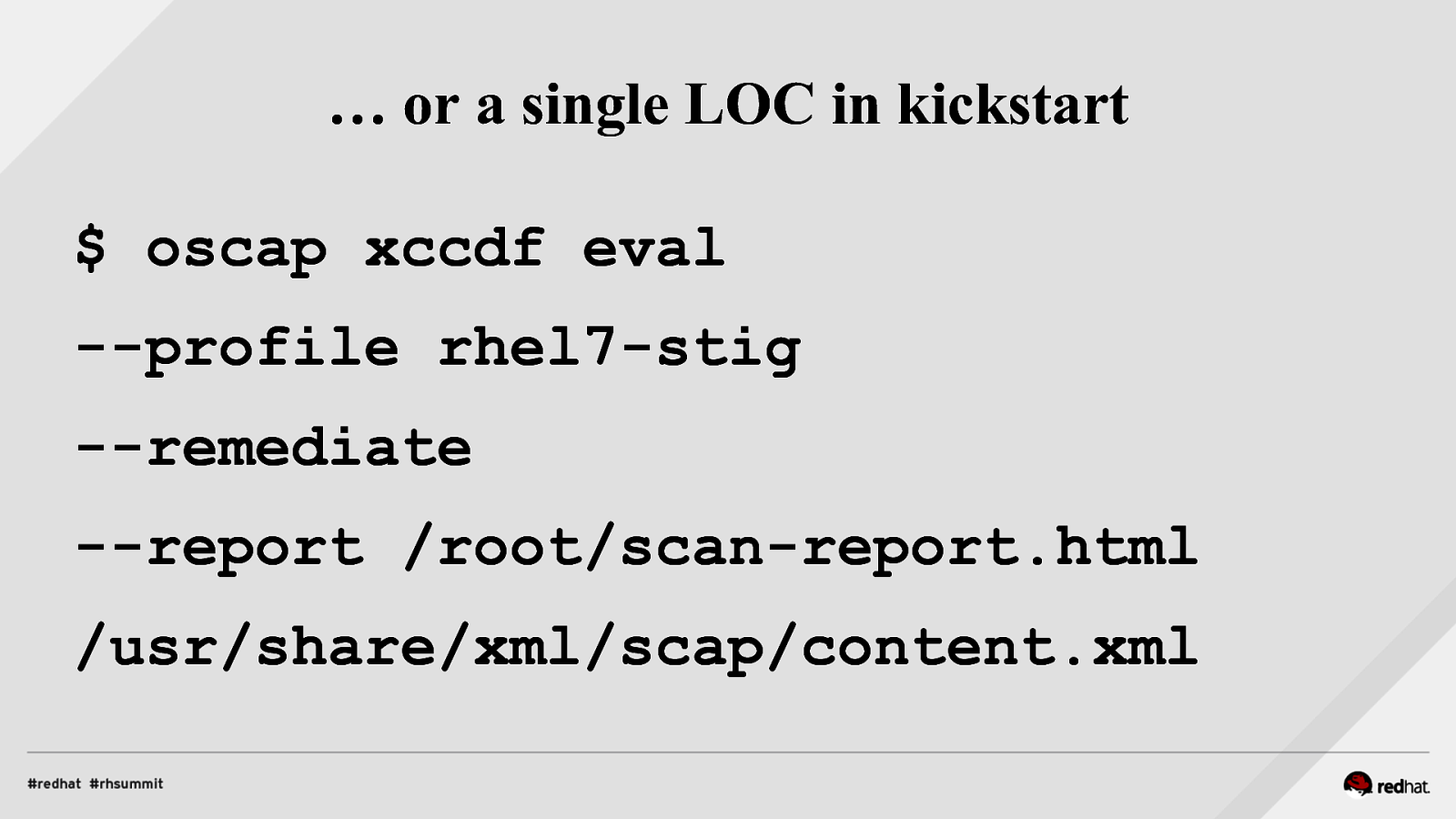
… or a single LOC in kickstart $ oscap xccdf eval —profile rhel7-stig —remediate —report /root/scan-report.html /usr/share/xml/scap/content.xml

Intro to SCAP ADD NAME (View > Master > Slide master)
First, an SCAP Primer ● A family of specifications managed by NIST ● Really a bunch of XML schema ○ which are data formats ○ so not a protocol at all, it turns out ○ openly defined, community developed, and evolving

First, an SCAP Primer ● Defines standardized formats ● Because you’ll get: ○ Standardized inputs (e.g. a compliance baseline) ○ Standardized outputs (e.g. compliance report) ● Provides the enterprise liberty with regard to product choices ○ Avoid vendor lock-in ○ Federal procurement language starting to require SCAP

TOOLS vs CONTENT

U.S. Gov SCAP Validation Program https://scap.nist.gov/validation/ ● Automated test suites to verify interpreters, like OpenSCAP ● Mandated by US Gov: The U.S. Office of Management and Budget has required, in the August 11, 2008, M-08-22 memorandum to Federal CIOs, that “Both industry and government information technology providers must use SCAP validated tools with FDCC Scanner capability to certify their products operate correctly with FDCC configurations and do not alter FDCC settings. Agencies will use SCAP tools to scan for both FDCC configurations and configuration deviations approved by department or agency accrediting authority. Agencies must also use these tools when monitoring use of these configurations as part of FISMA continuous monitoring.” ● Required by GSA for vulnerability and configuration management products
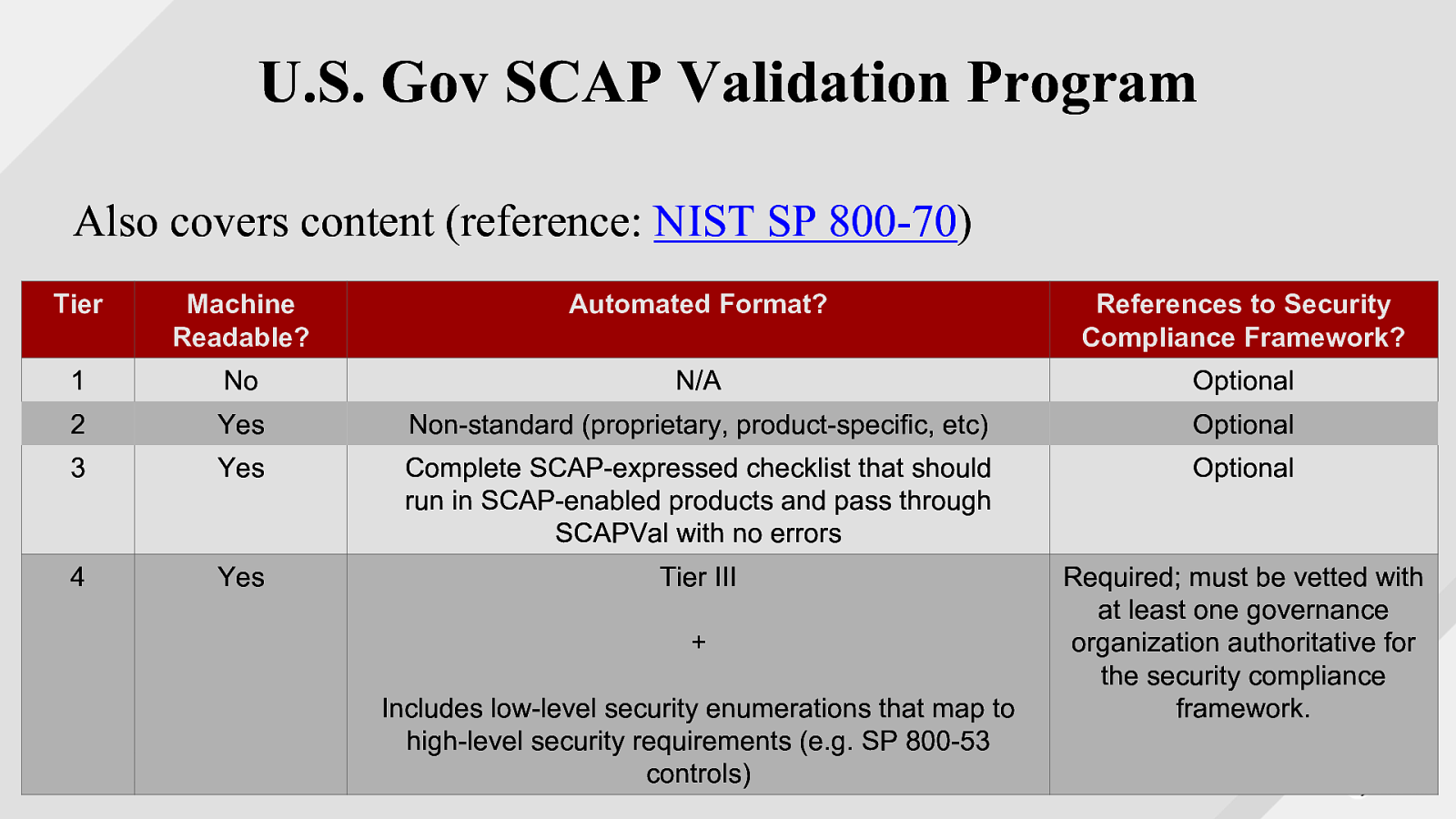
U.S. Gov SCAP Validation Program Also covers content (reference: NIST SP 800-70) Tier Machine Readable? Automated Format? References to Security Compliance Framework? 1 No N/A Optional 2 Yes Non-standard (proprietary, product-specific, etc) Optional 3 Yes Complete SCAP-expressed checklist that should run in SCAP-enabled products and pass through SCAPVal with no errors Optional 4 Yes Tier III Required; must be vetted with at least one governance organization authoritative for the security compliance framework.
- Includes low-level security enumerations that map to high-level security requirements (e.g. SP 800-53 controls)

ACRONYM BREAKDOWN ADD NAME (View > Master > Slide master)
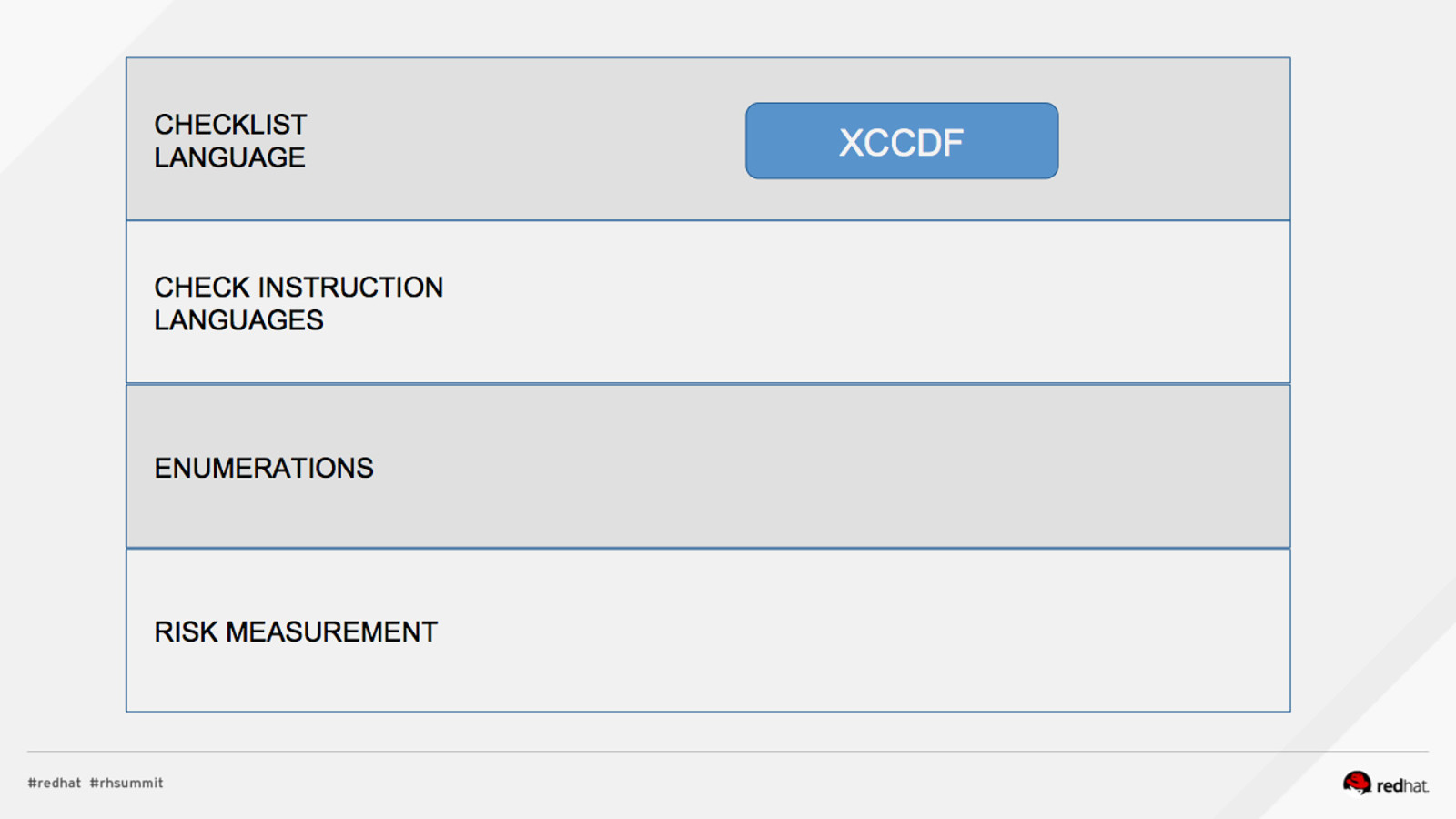
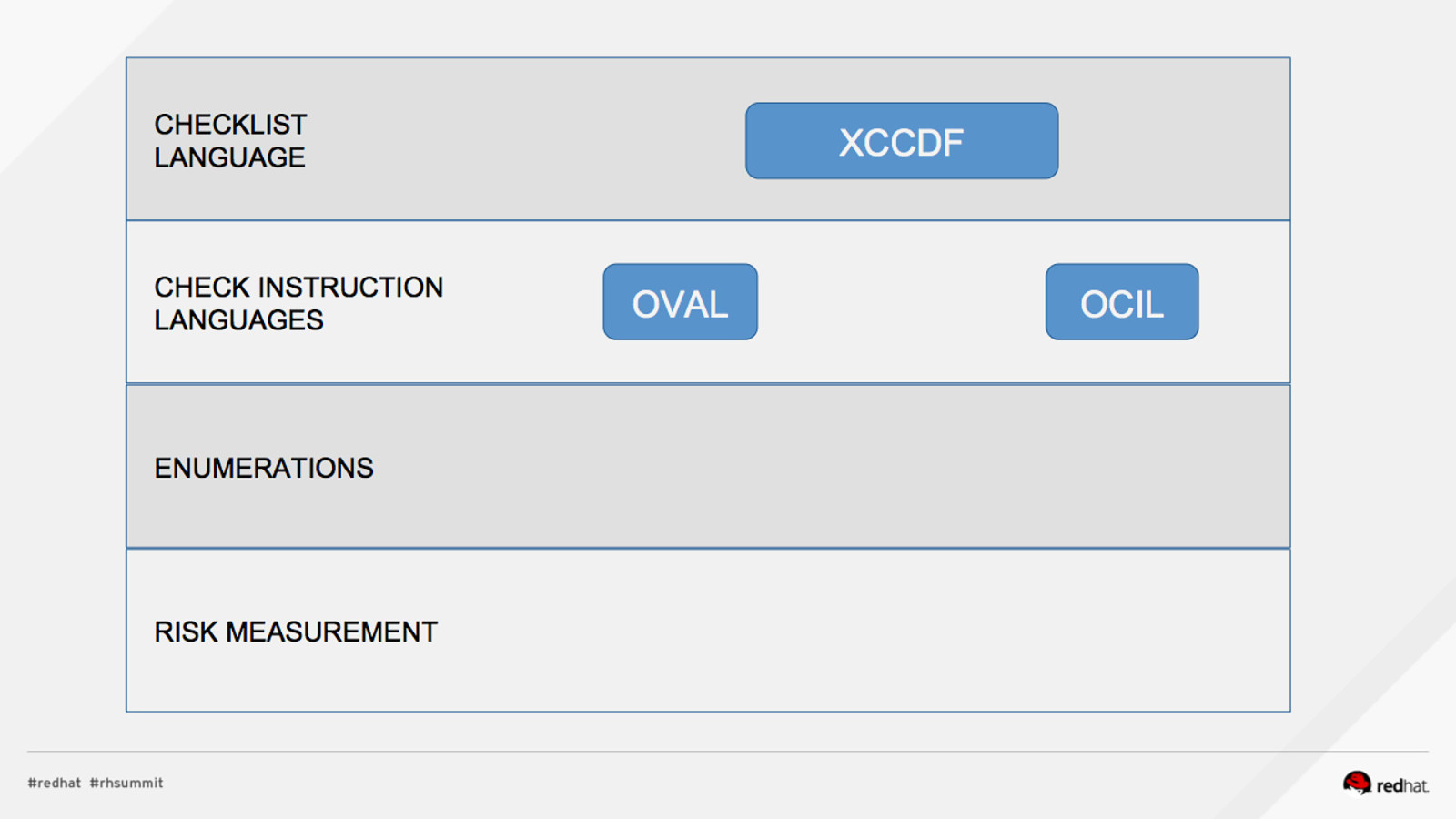
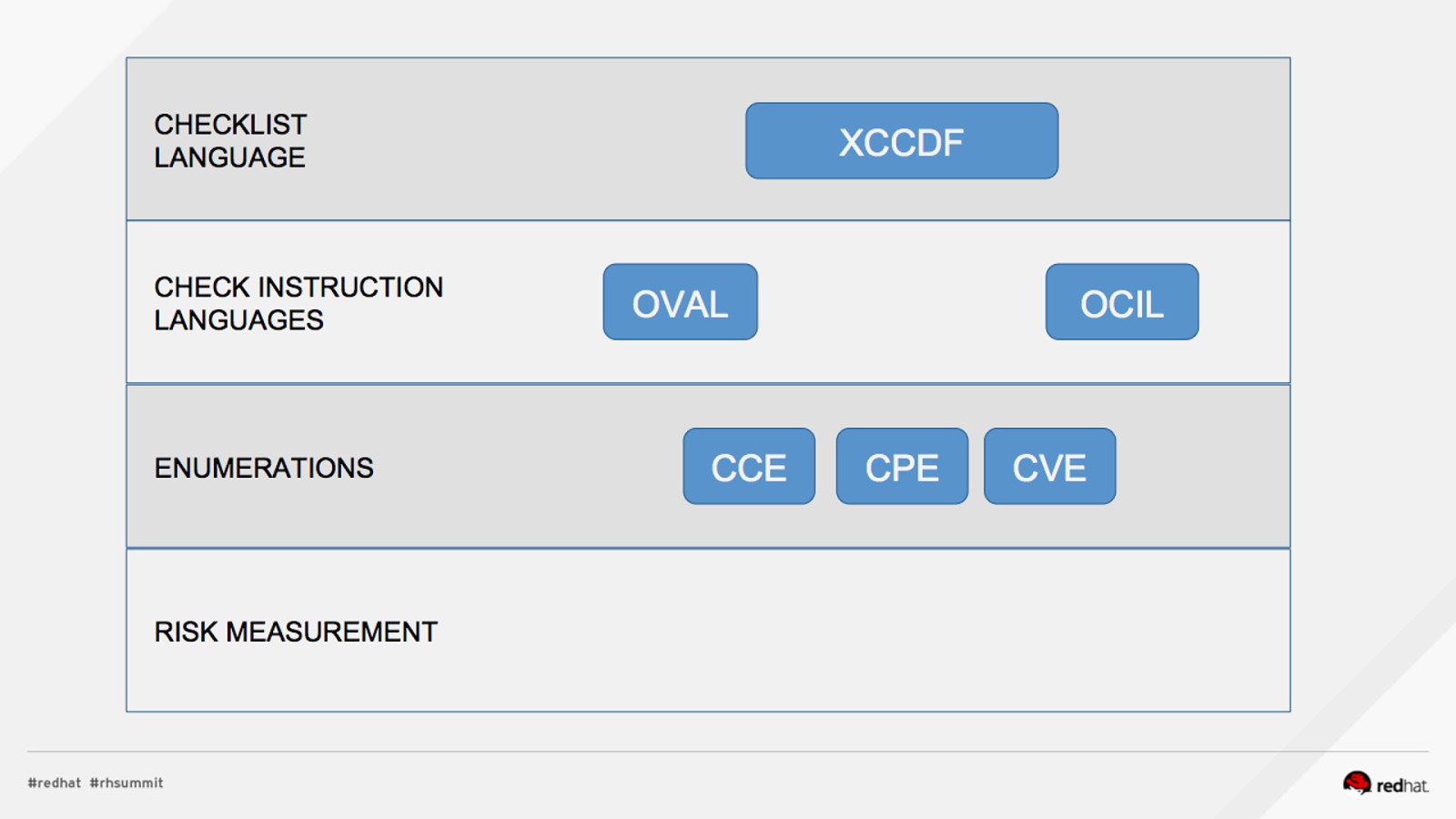
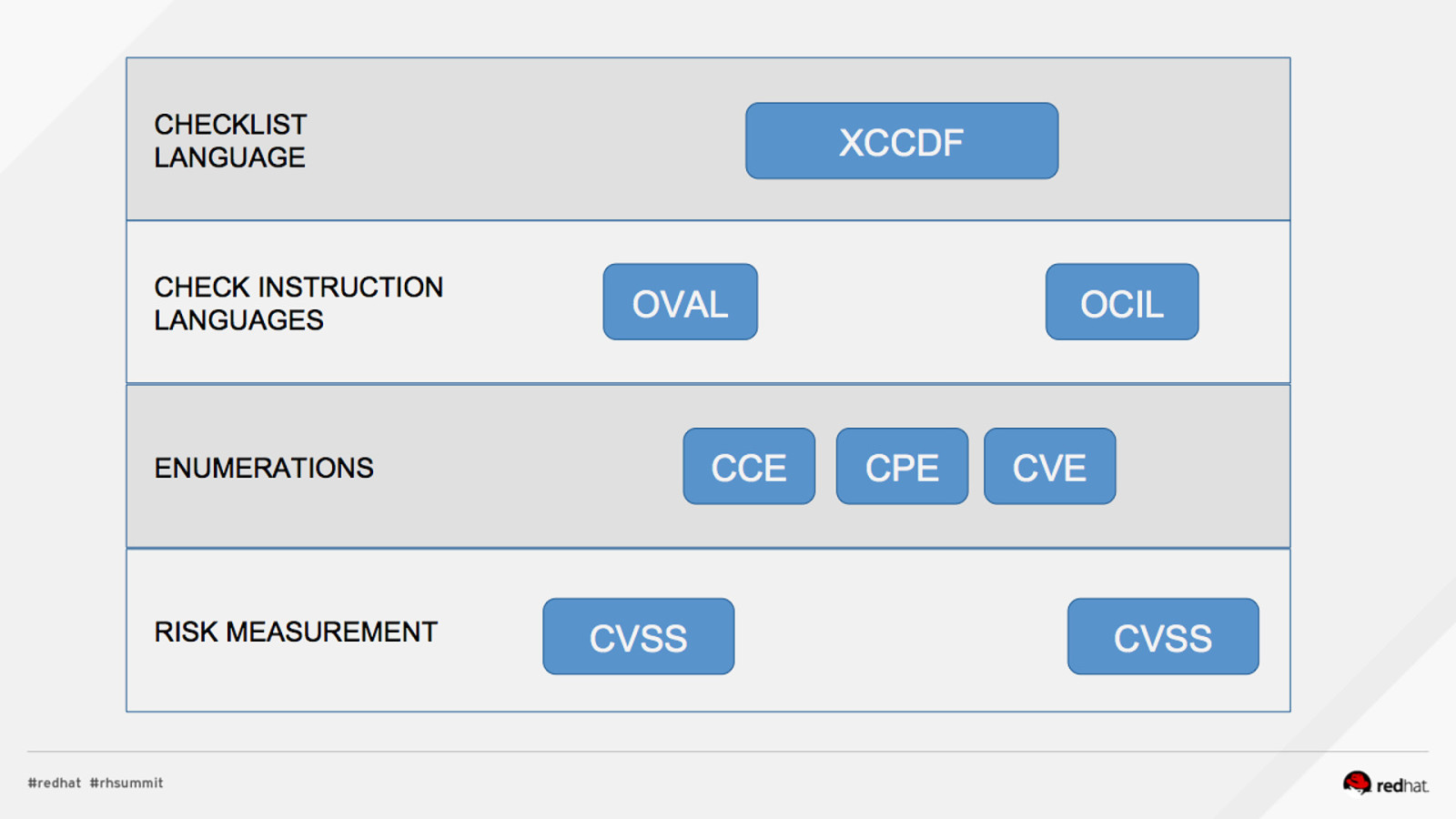
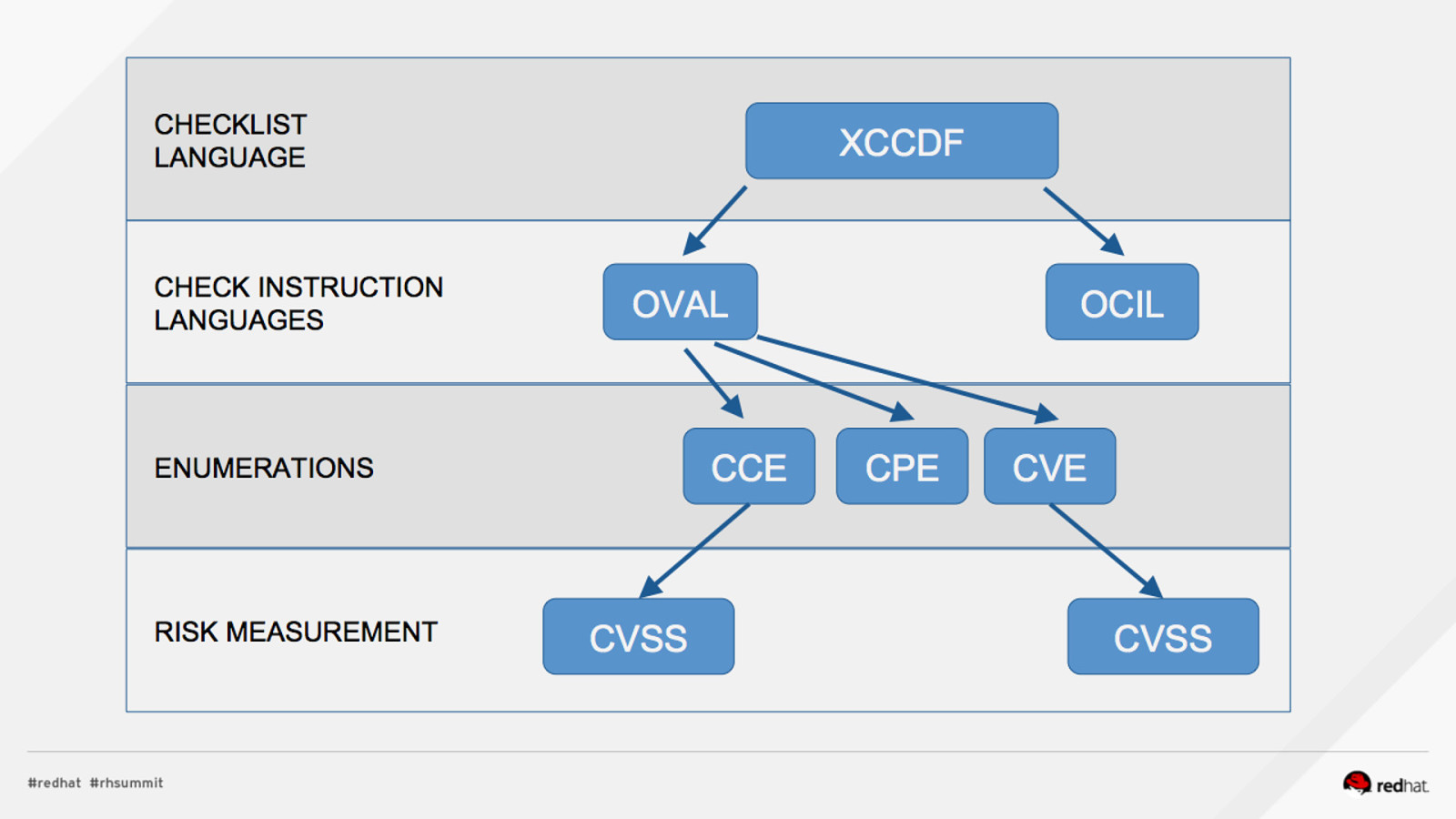
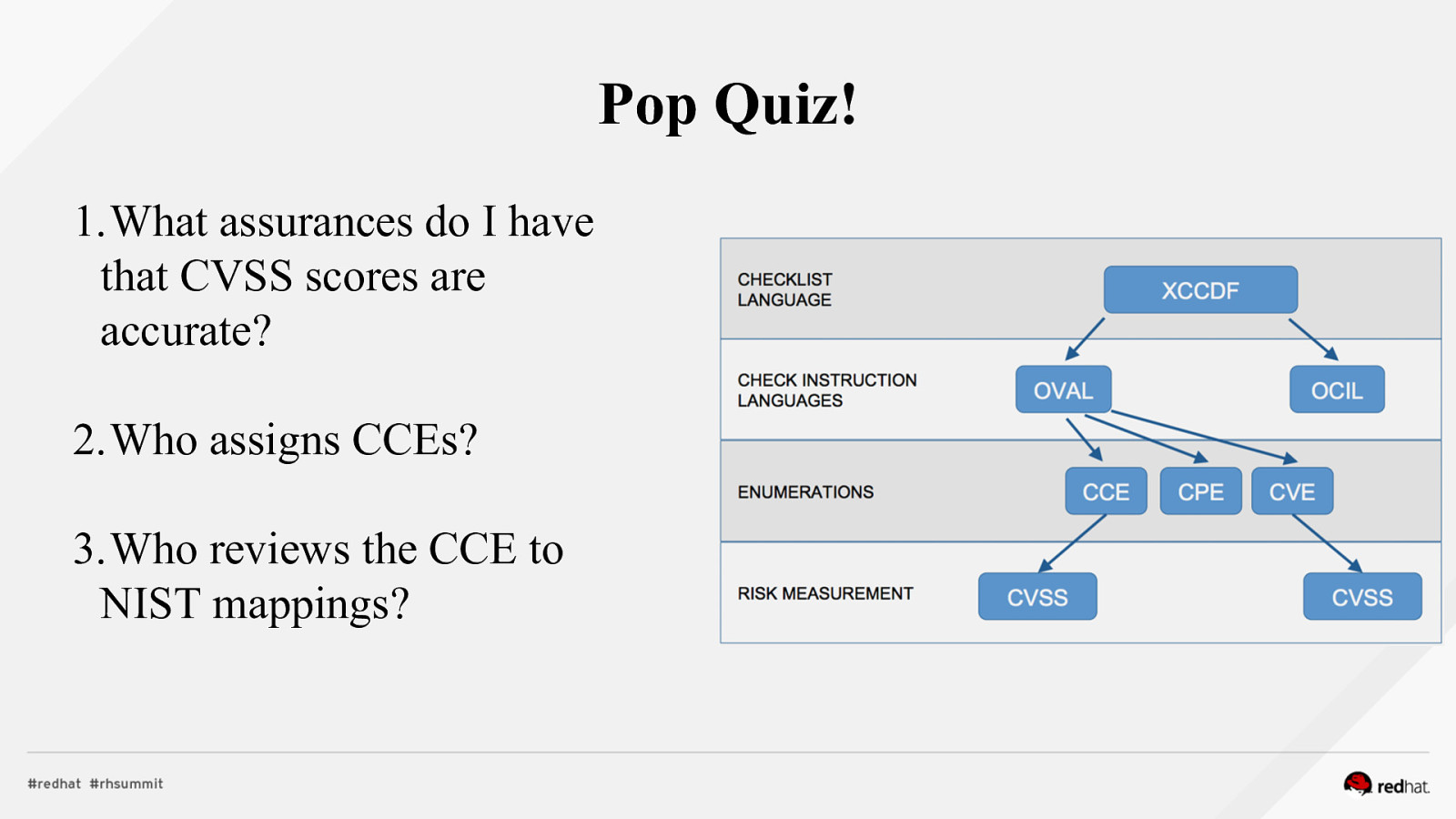
Pop Quiz! 1.What assurances do I have that CVSS scores are accurate? 2.Who assigns CCEs? 3.Who reviews the CCE to NIST mappings?

OPEN SOURCE CONFRONTS THE C&A CHALLENGE: OpenSCAP ADD NAME (View > Master > Slide master)

Community created portfolio of tools and content to assess systems for known vulnerabilities. https://github.com/OpenSCAP
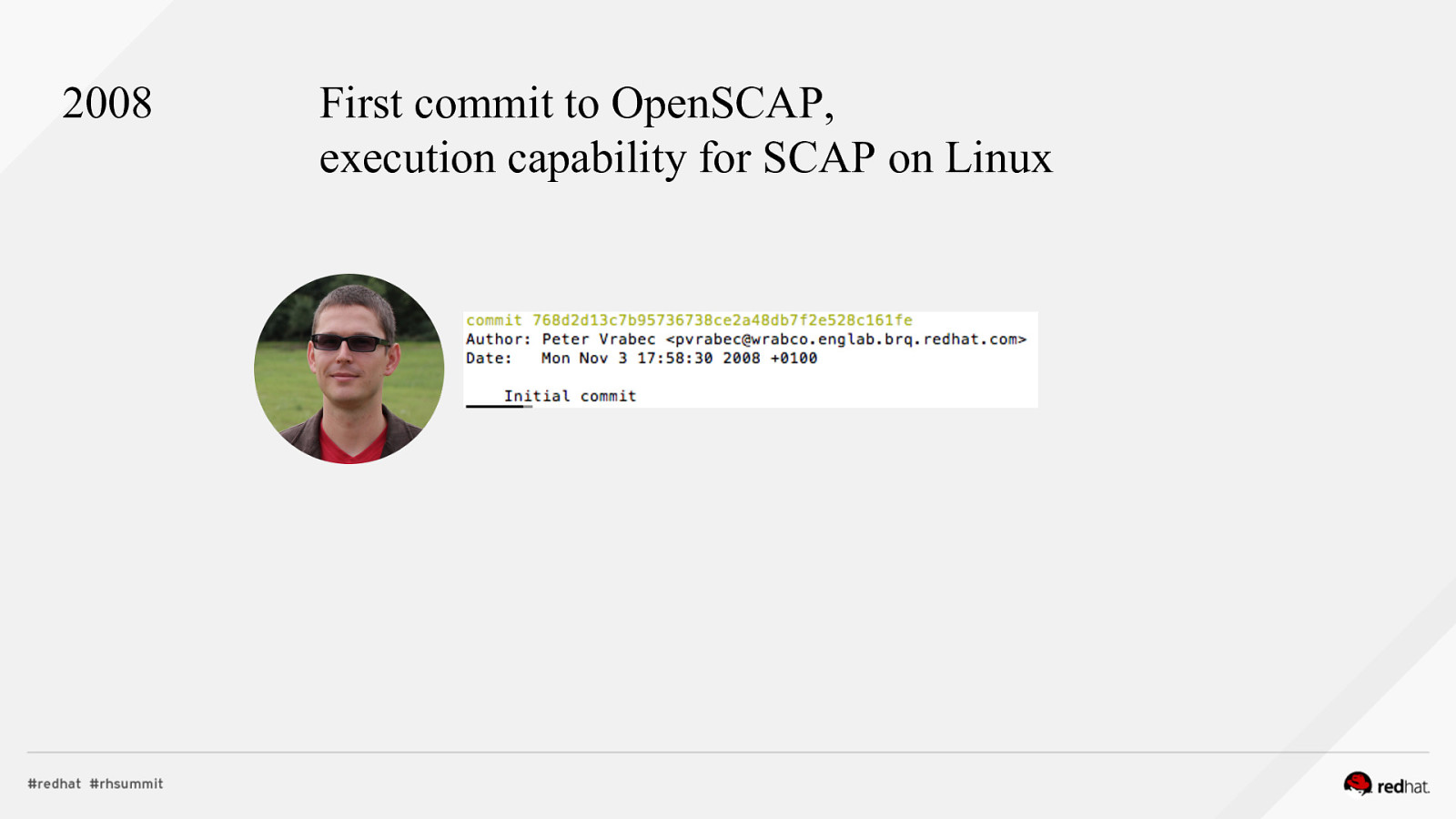
2008 First commit to OpenSCAP, execution capability for SCAP on Linux
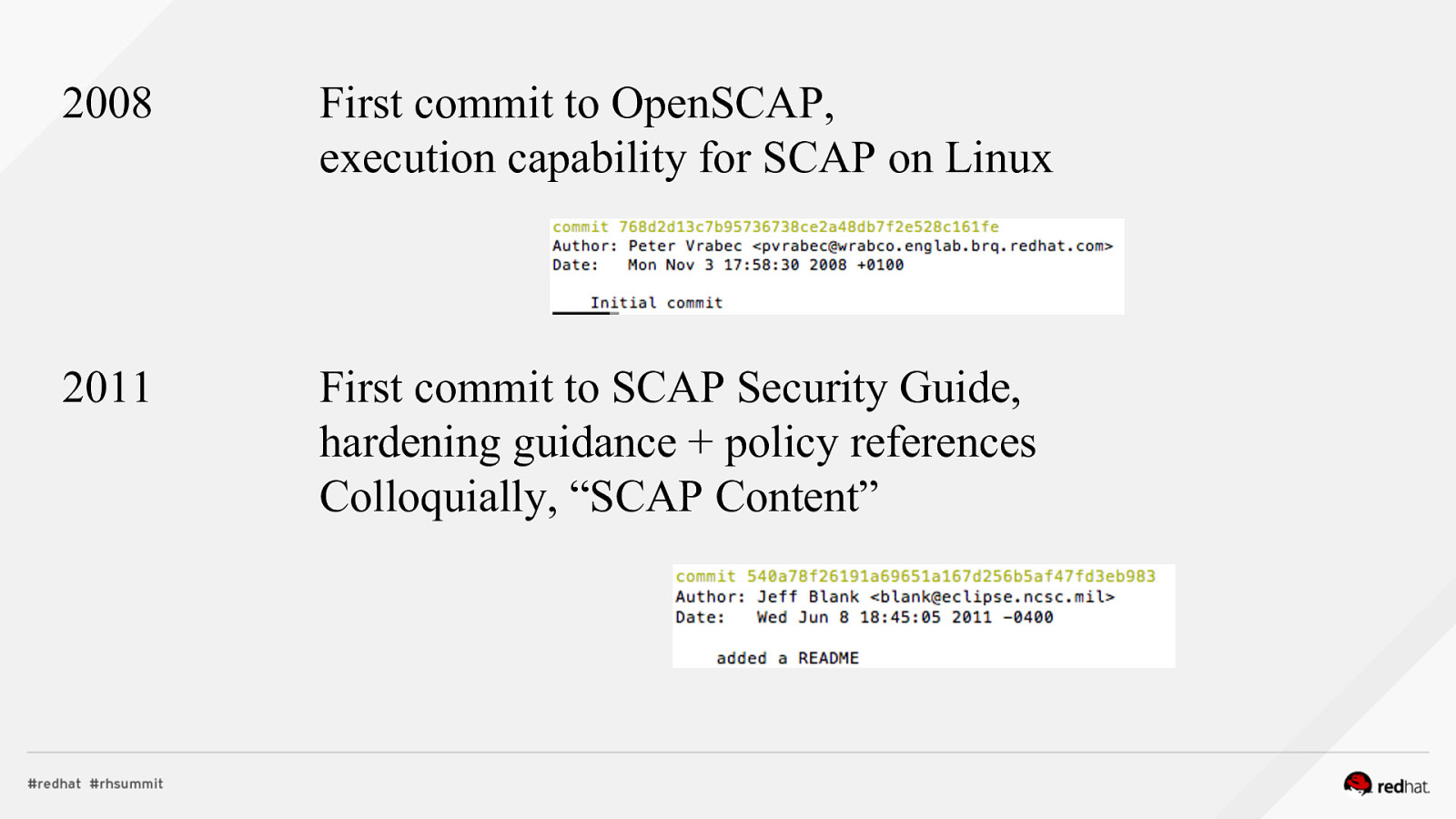
2008 First commit to OpenSCAP, execution capability for SCAP on Linux 2011 First commit to SCAP Security Guide, hardening guidance + policy references Colloquially, “SCAP Content”


Power of the Community ● RHEL7 STIG content, rebased in RHEL 7.3, reflects … ○ 6,180 commits from 95 people ○ 441,055 lines of code ● OpenSCAP interpreter contains … ○ 6,811 commits from 74 people ○ 157,775 lines of code ● “Security Button” in RHEL7 installer ○ 6 people, 90 days, 6,806 lines of code


Keyboard Time! ADD NAME (View > Master > Slide master)
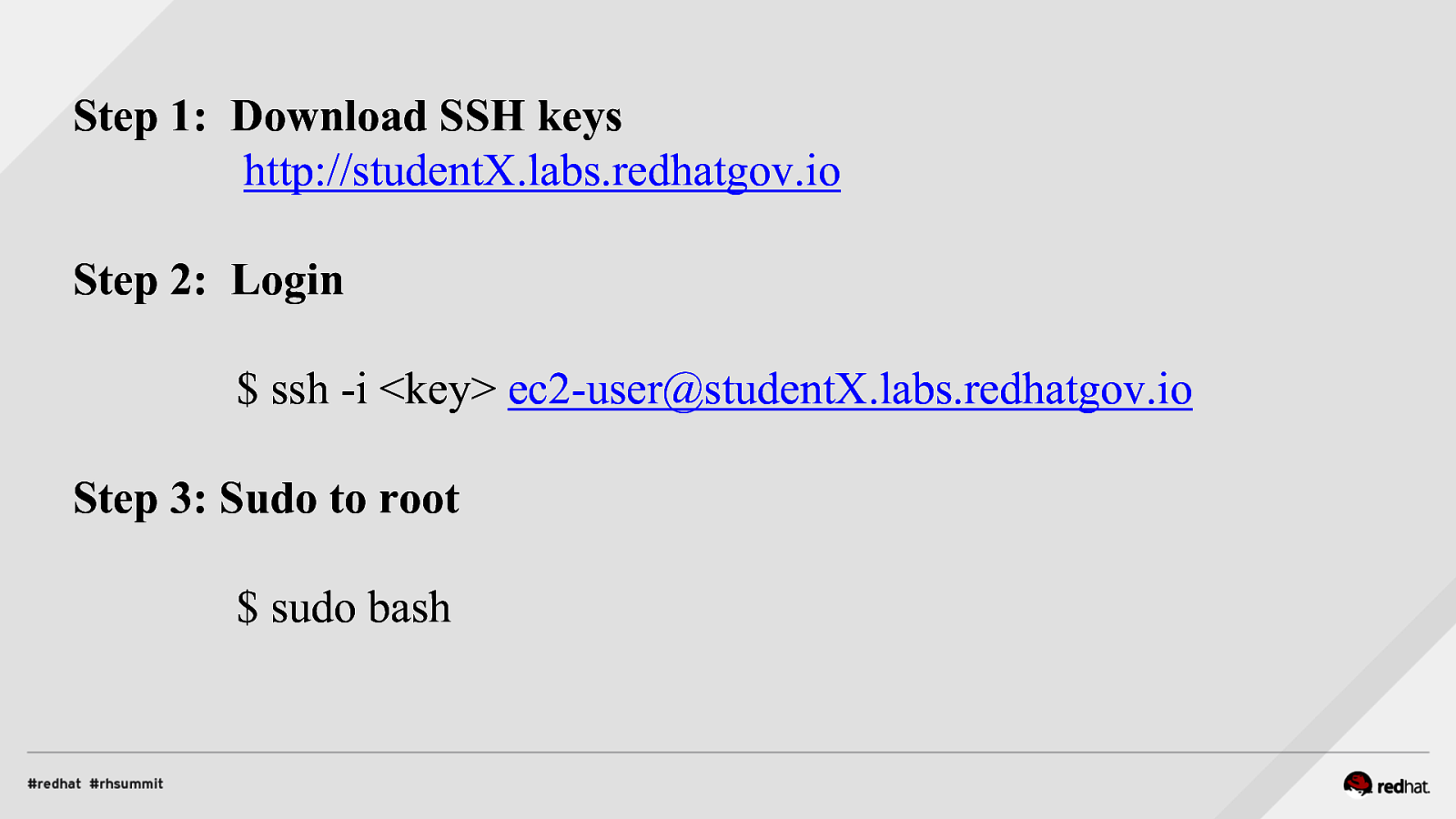
Step 1: Download SSH keys http://studentX.labs.redhatgov.io Step 2: Login $ ssh -i <key> ec2-user@studentX.labs.redhatgov.io Step 3: Sudo to root $ sudo bash
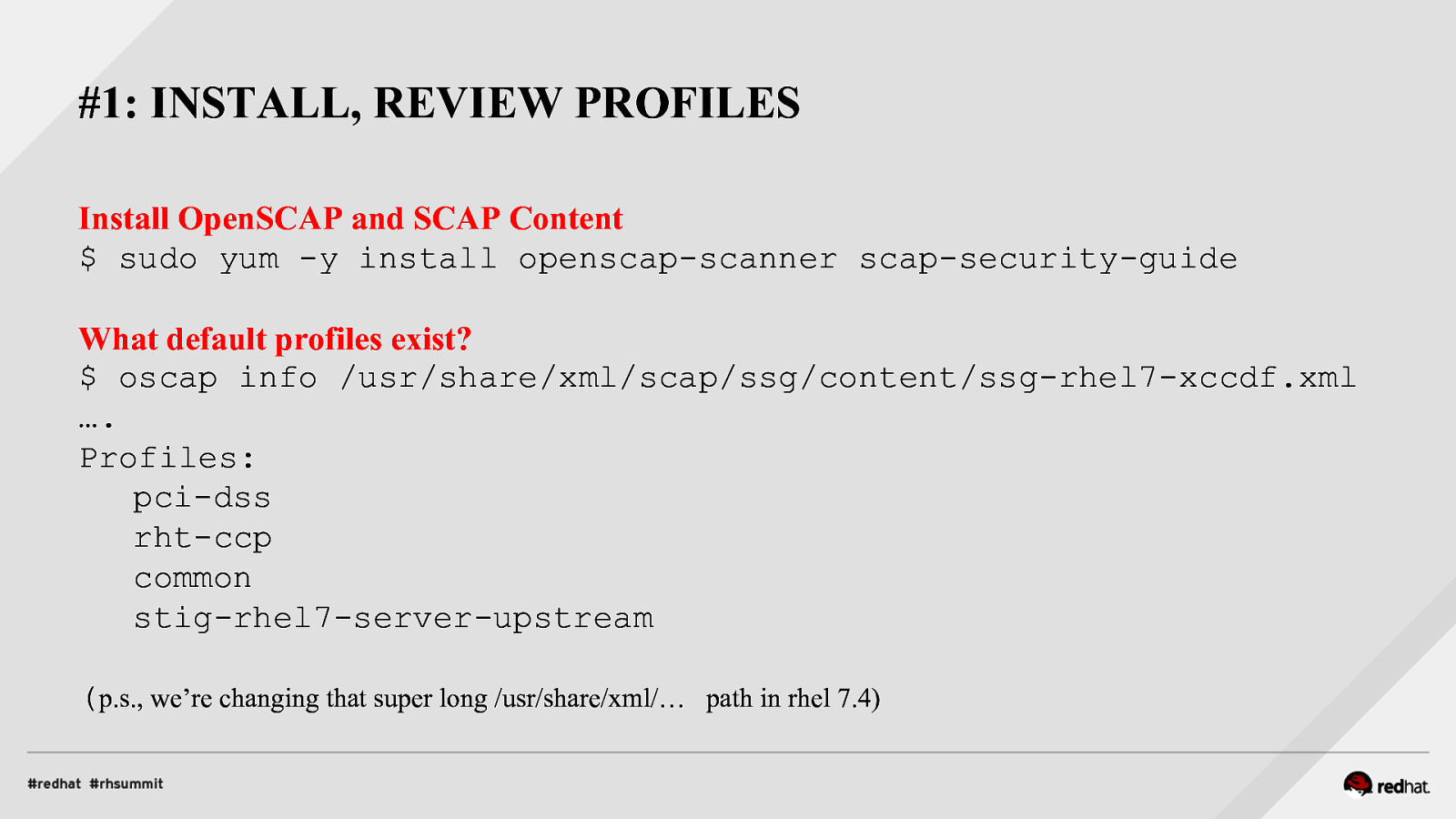
#1: INSTALL, REVIEW PROFILES Install OpenSCAP and SCAP Content $ sudo yum -y install openscap-scanner scap-security-guide What default profiles exist? $ oscap info /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml …. Profiles: pci-dss rht-ccp common stig-rhel7-server-upstream (p.s., we’re changing that super long /usr/share/xml/… path in rhel 7.4)
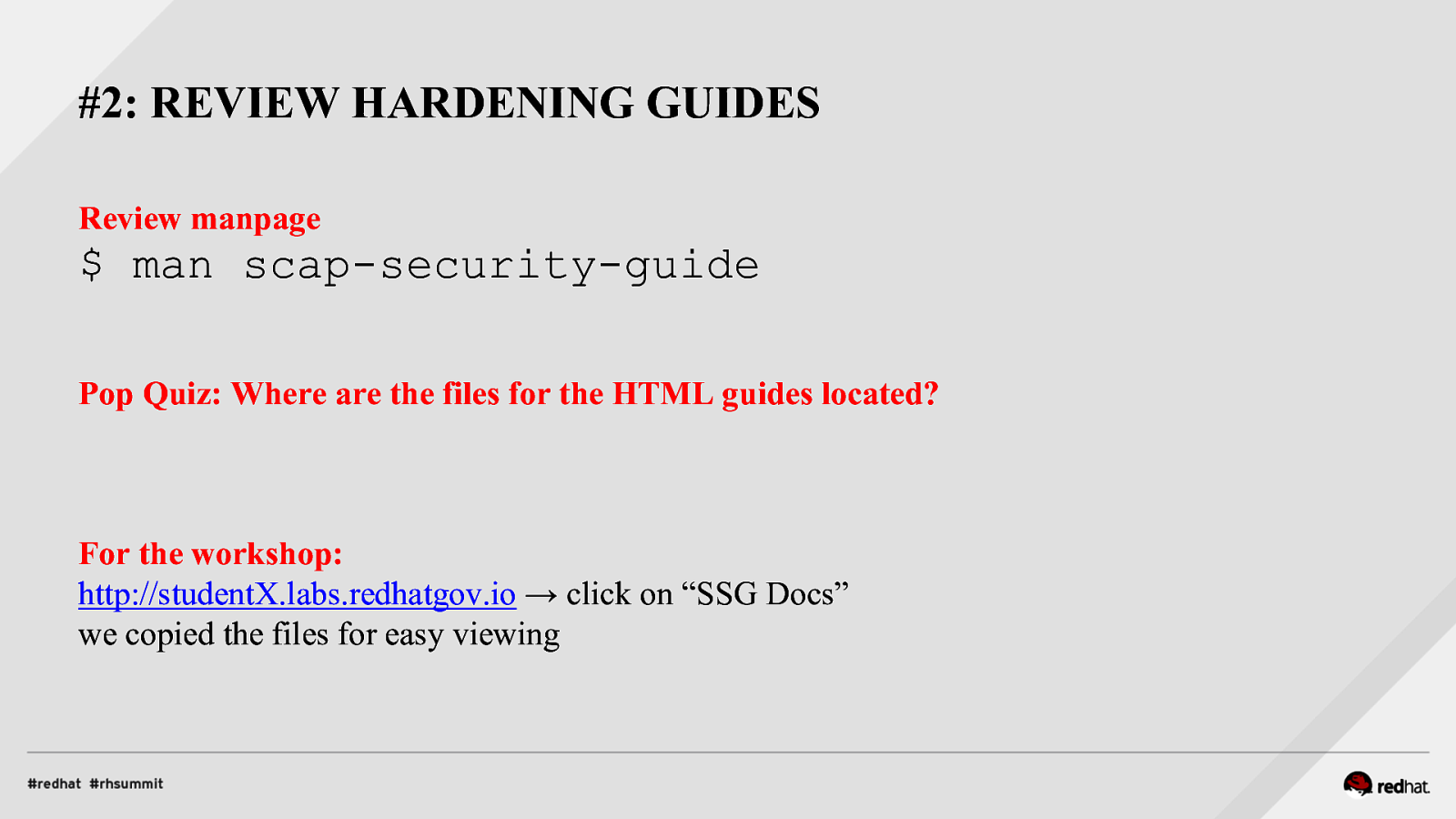
#2: REVIEW HARDENING GUIDES Review manpage $ man scap-security-guide Pop Quiz: Where are the files for the HTML guides located? For the workshop: http://studentX.labs.redhatgov.io → click on “SSG Docs” we copied the files for easy viewing
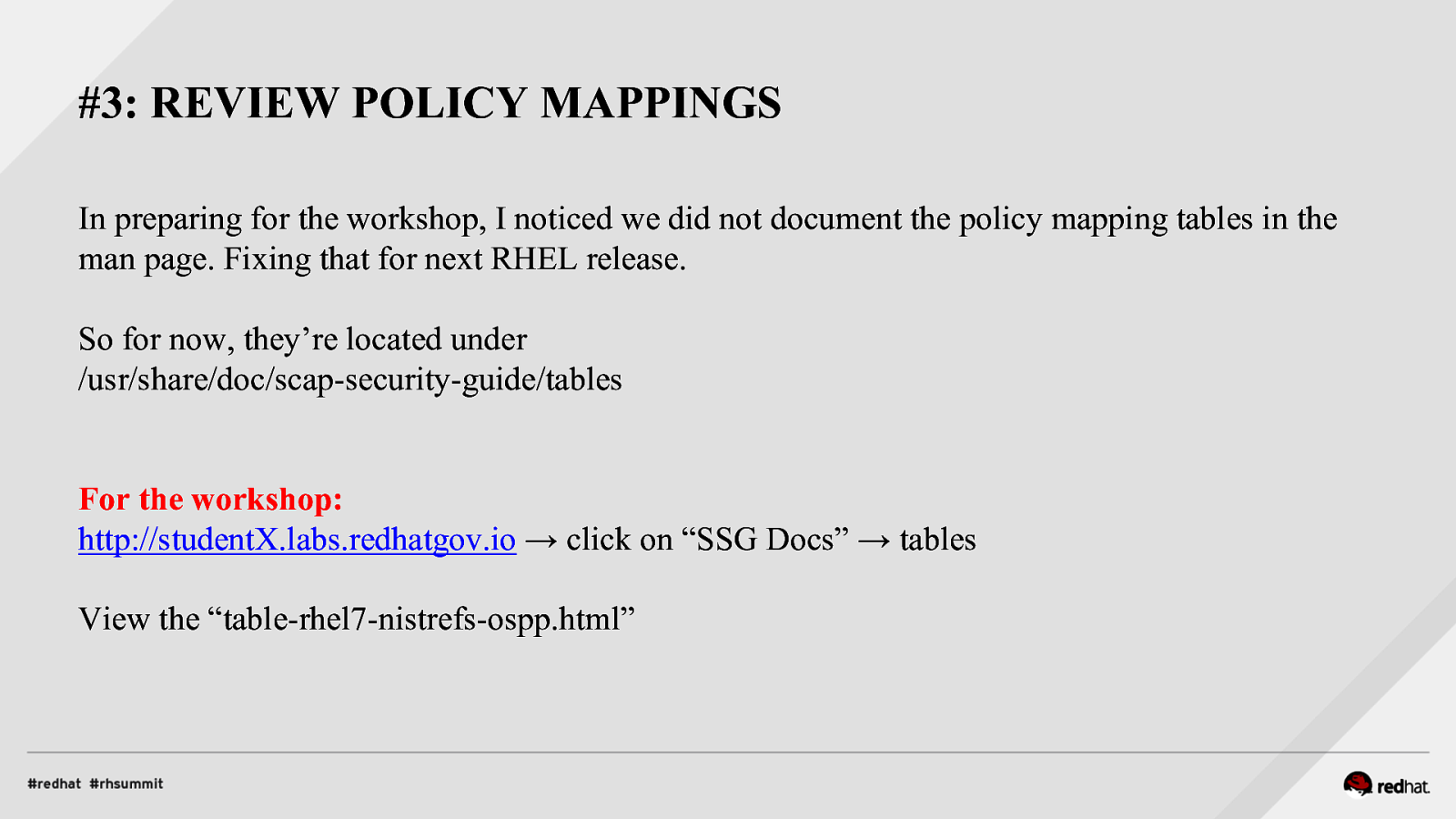
#3: REVIEW POLICY MAPPINGS In preparing for the workshop, I noticed we did not document the policy mapping tables in the man page. Fixing that for next RHEL release. So for now, they’re located under /usr/share/doc/scap-security-guide/tables For the workshop: http://studentX.labs.redhatgov.io → click on “SSG Docs” → tables View the “table-rhel7-nistrefs-ospp.html”
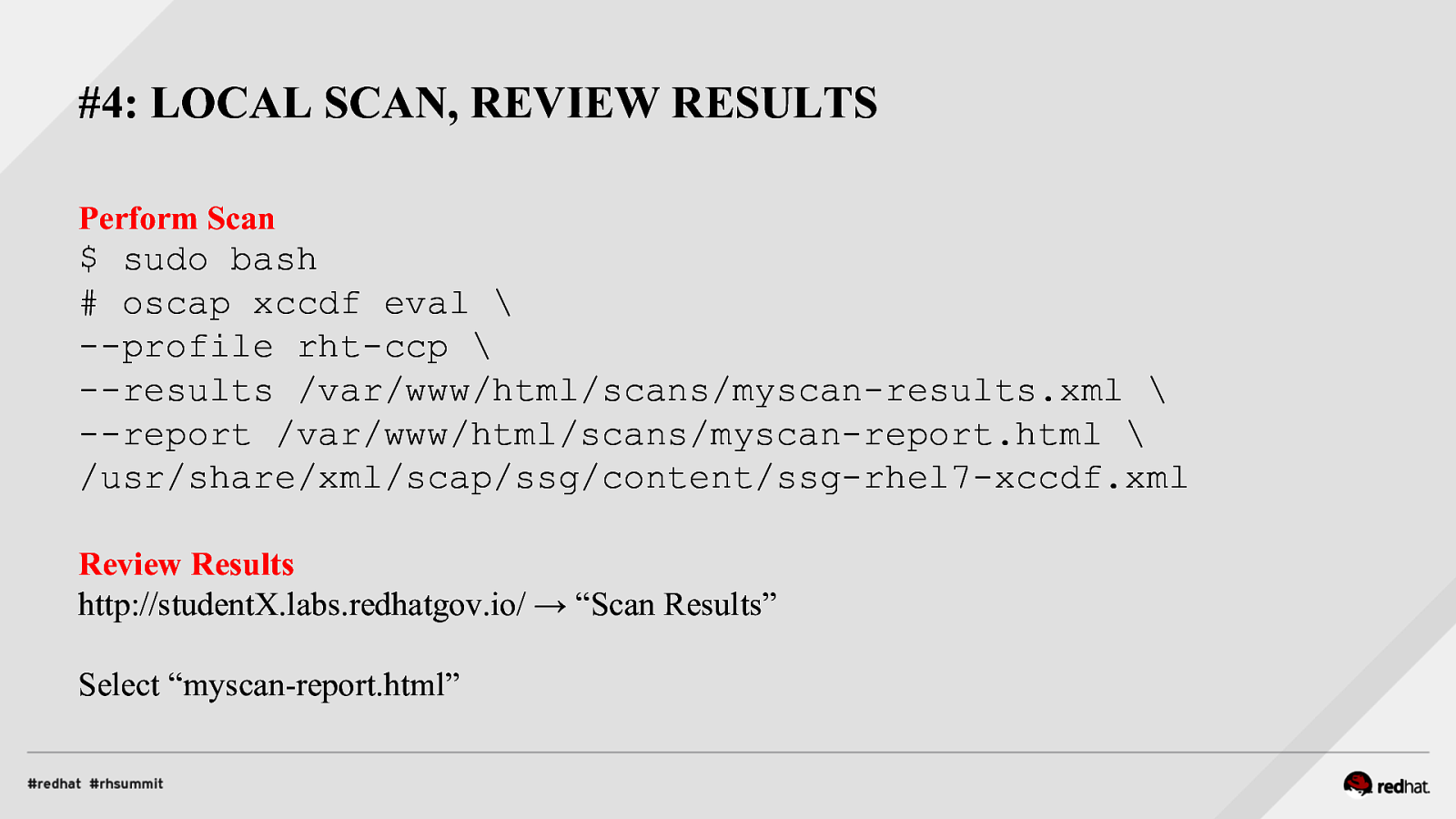
#4: LOCAL SCAN, REVIEW RESULTS Perform Scan $ sudo bash # oscap xccdf eval \ —profile rht-ccp \ —results /var/www/html/scans/myscan-results.xml \ —report /var/www/html/scans/myscan-report.html \ /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml Review Results http://studentX.labs.redhatgov.io/ → “Scan Results” Select “myscan-report.html”

Quick Review 1.If we forget the OpenSCAP CLI syntax, where can we look for a reminder? 2.How do I tell what profiles are available? a)What if I want to read through the profile prior to a scan? b)Help! My security officer is asking for NIST 800-53 and DISA STIG mappings! Where are they?
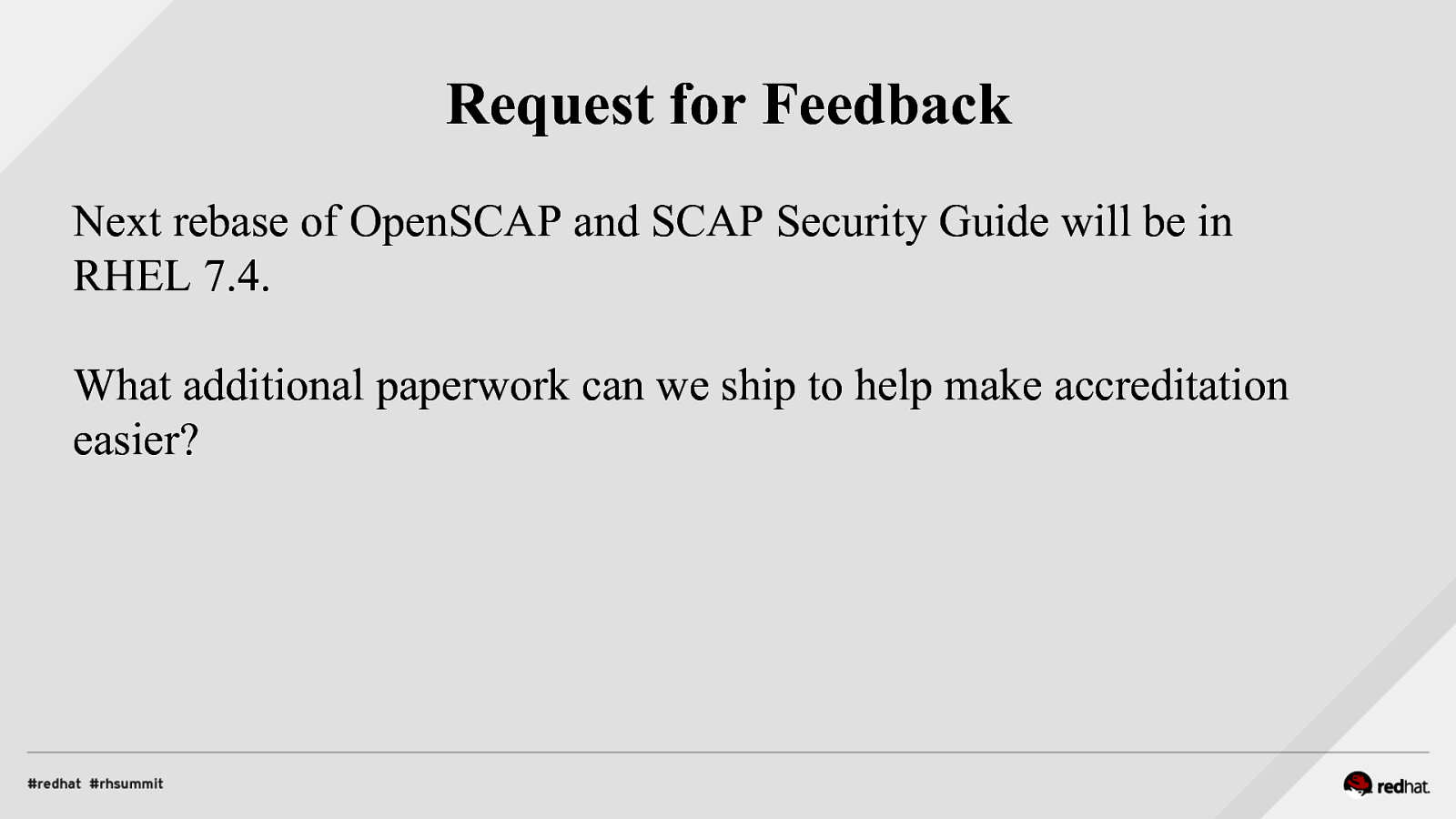
Request for Feedback Next rebase of OpenSCAP and SCAP Security Guide will be in RHEL 7.4. What additional paperwork can we ship to help make accreditation easier?

Remediation! ADD NAME (View > Master > Slide master)
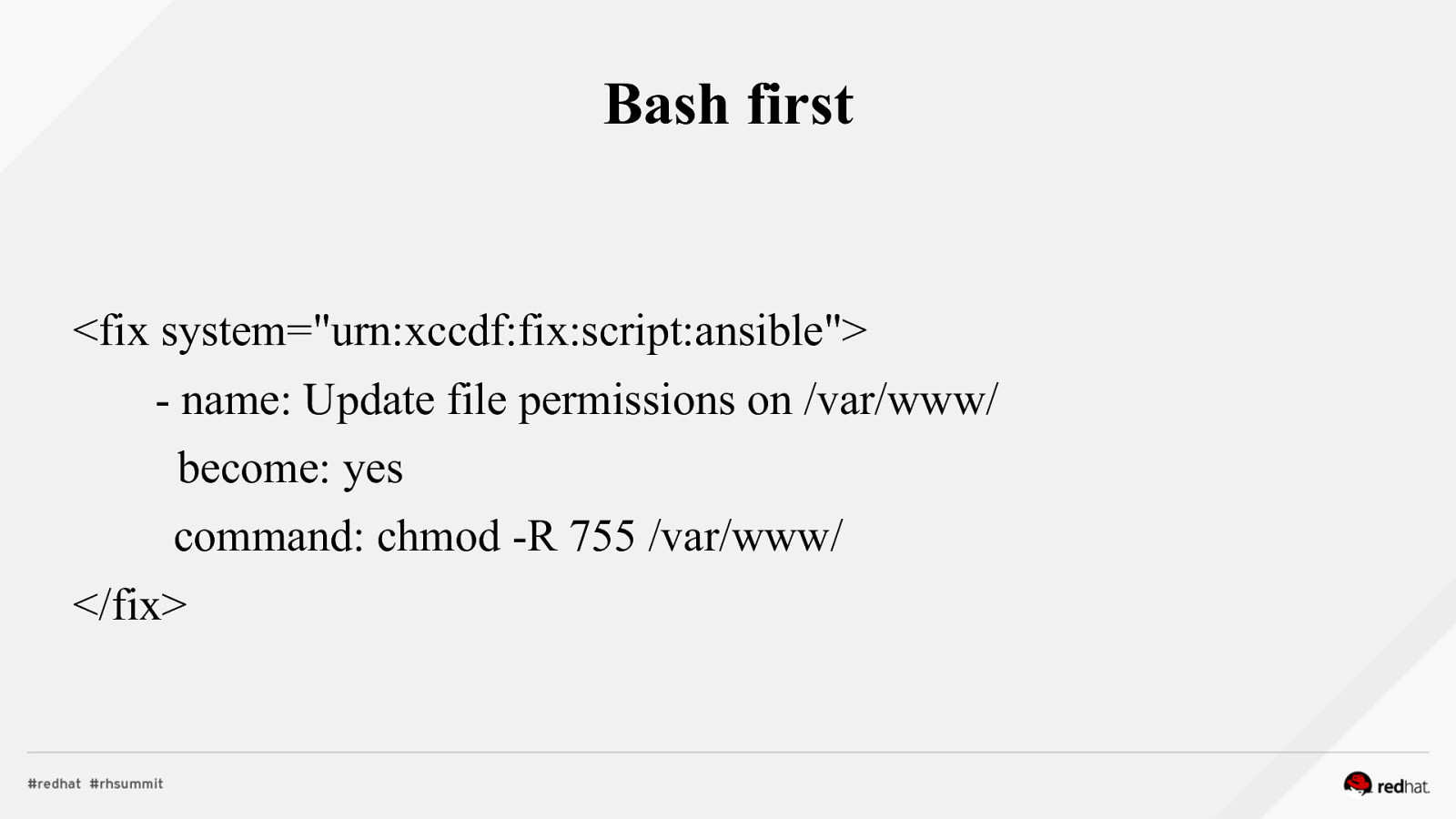
Bash first <fix system=”urn:xccdf:fix:script:ansible”> - name: Update file permissions on /var/www/ become: yes command: chmod -R 755 /var/www/ </fix>

RHEL 7.3 + beyond Now has support for Ansible, but limited content. But we can show our upstream work (estimated RHEL 7.4 release)
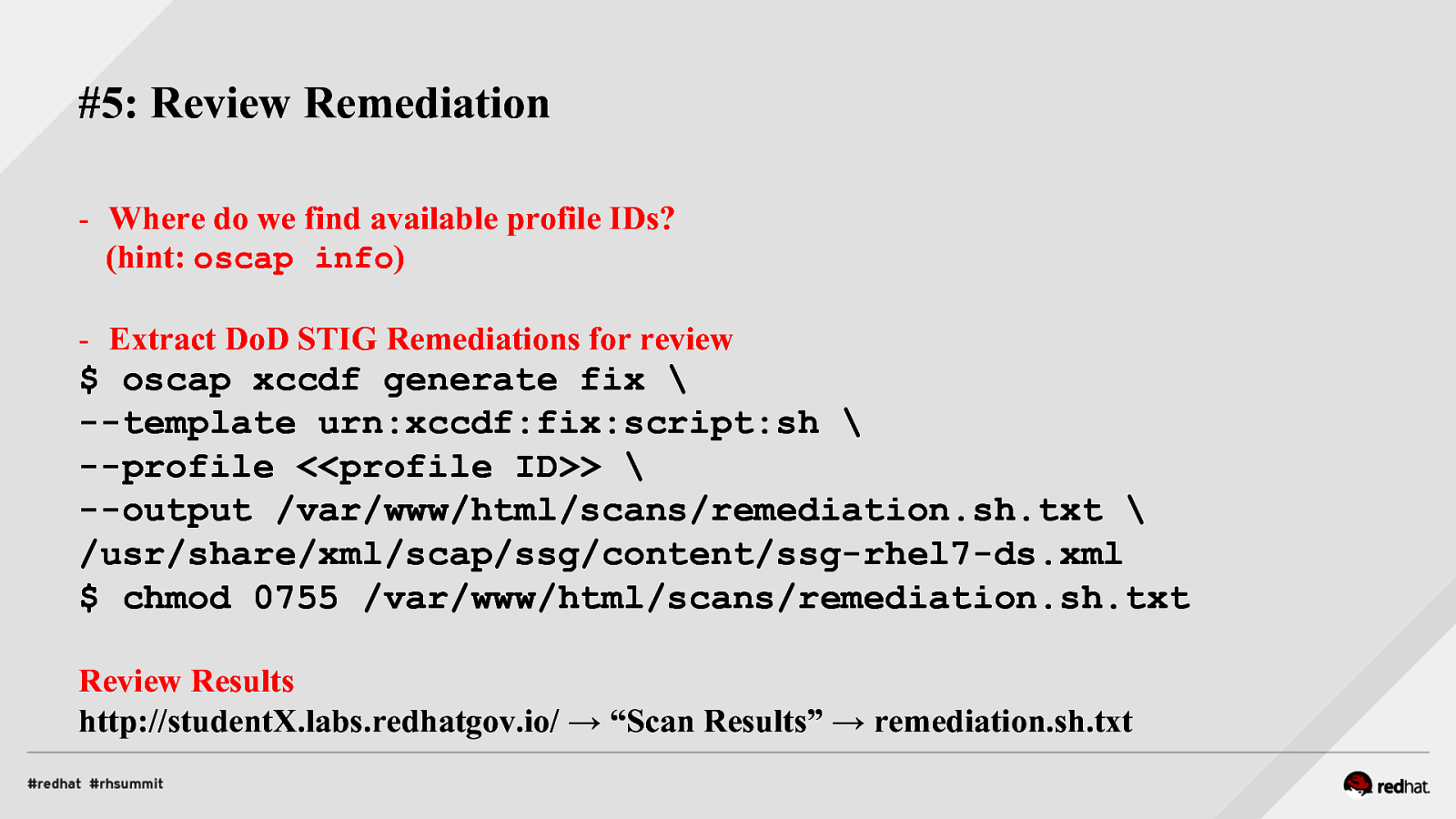
#5: Review Remediation - Where do we find available profile IDs? (hint: oscap info) - Extract DoD STIG Remediations for review $ oscap xccdf generate fix \ —template urn:xccdf:fix:script:sh \ —profile <<profile ID>> \ —output /var/www/html/scans/remediation.sh.txt \ /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xml $ chmod 0755 /var/www/html/scans/remediation.sh.txt Review Results http://studentX.labs.redhatgov.io/ → “Scan Results” → remediation.sh.txt
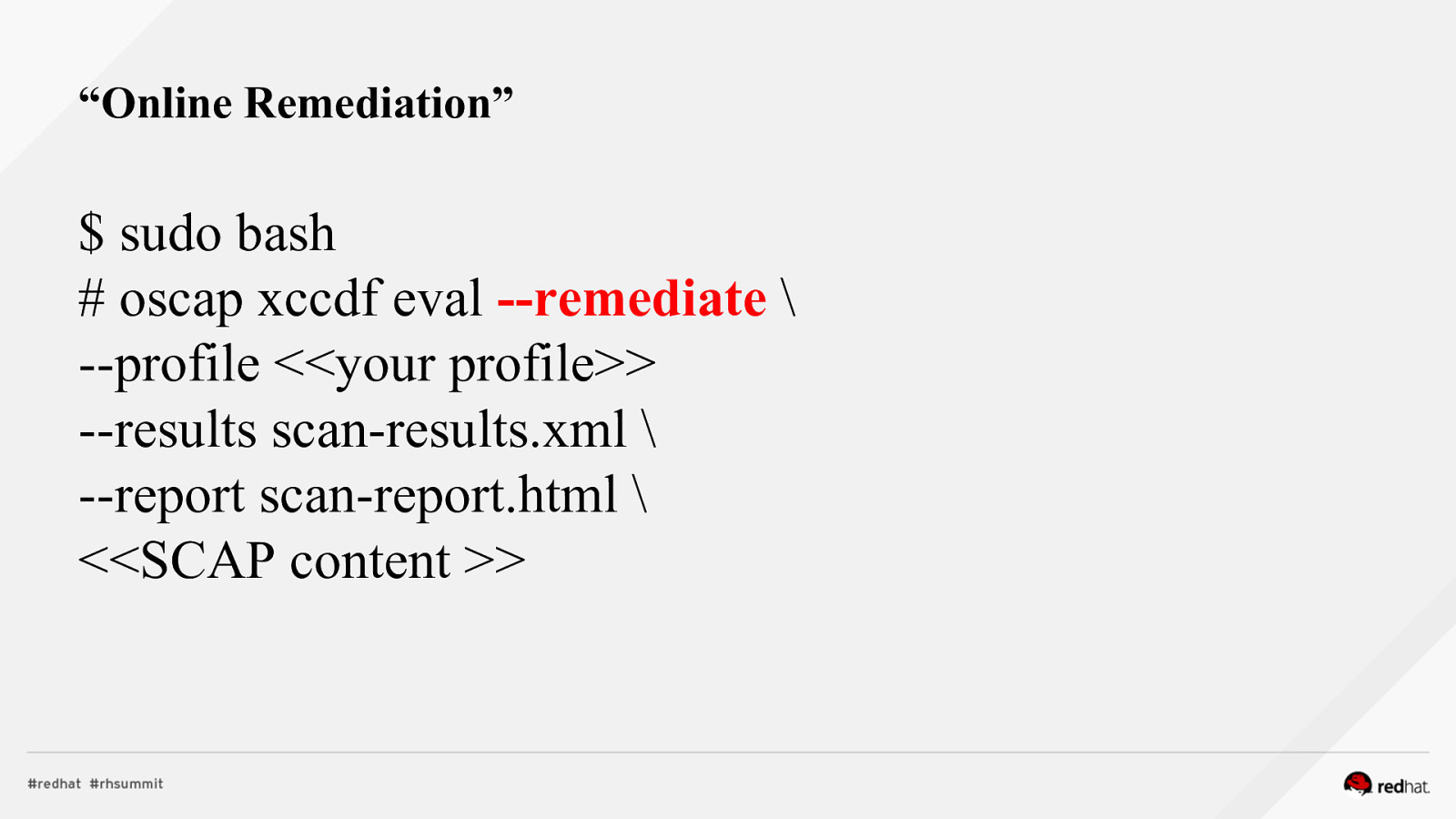
“Online Remediation” $ sudo bash # oscap xccdf eval —remediate \ —profile <<your profile>> —results scan-results.xml \ —report scan-report.html \ <<SCAP content >>
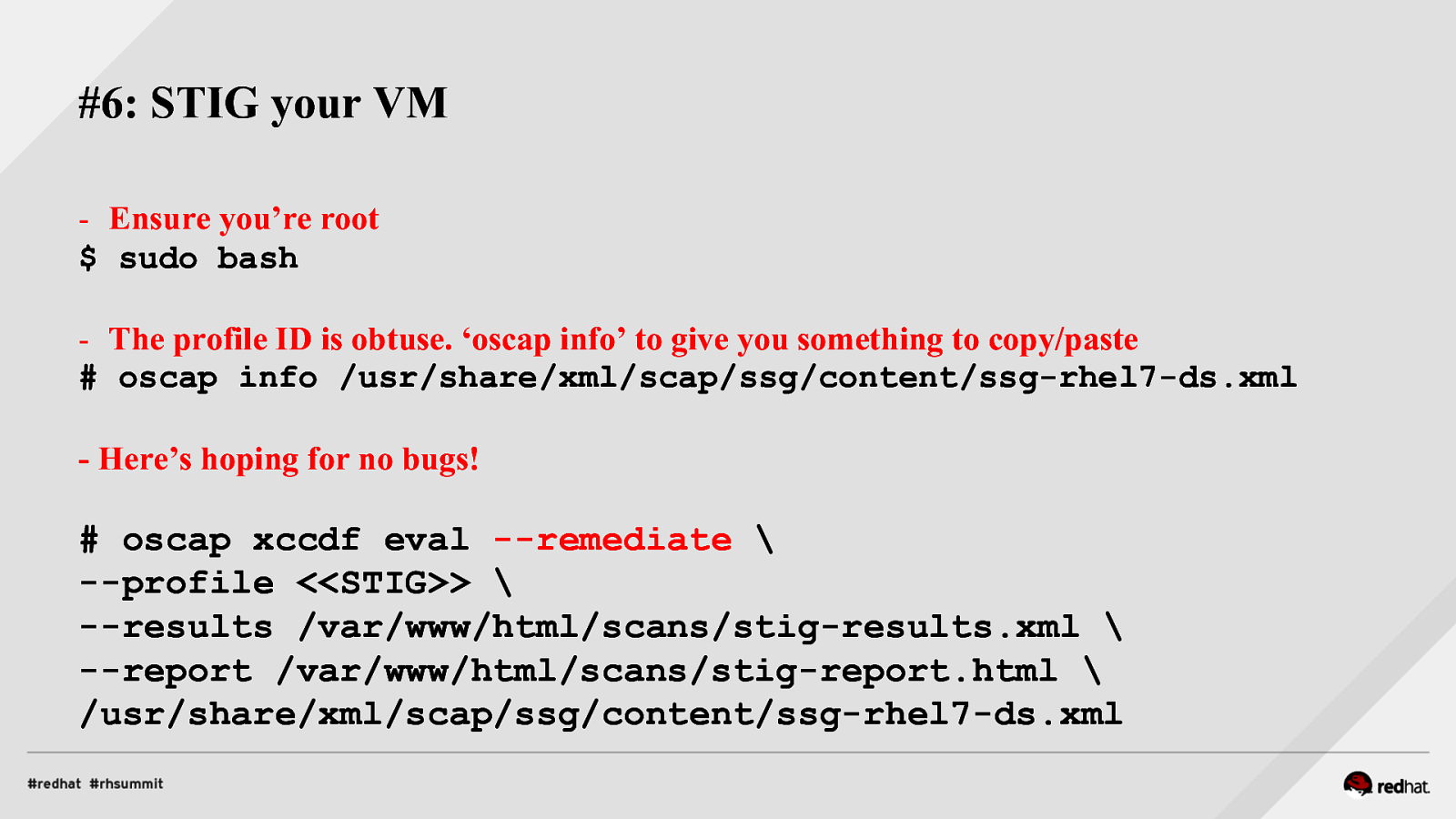
#6: STIG your VM - Ensure you’re root $ sudo bash - The profile ID is obtuse. ‘oscap info’ to give you something to copy/paste # oscap info /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xml - Here’s hoping for no bugs!
oscap xccdf eval —remediate \ —profile <<STIG>> \ —results /var/www/html/scans/stig-results.xml \ —report /var/www/html/scans/stig-report.html \ /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xml
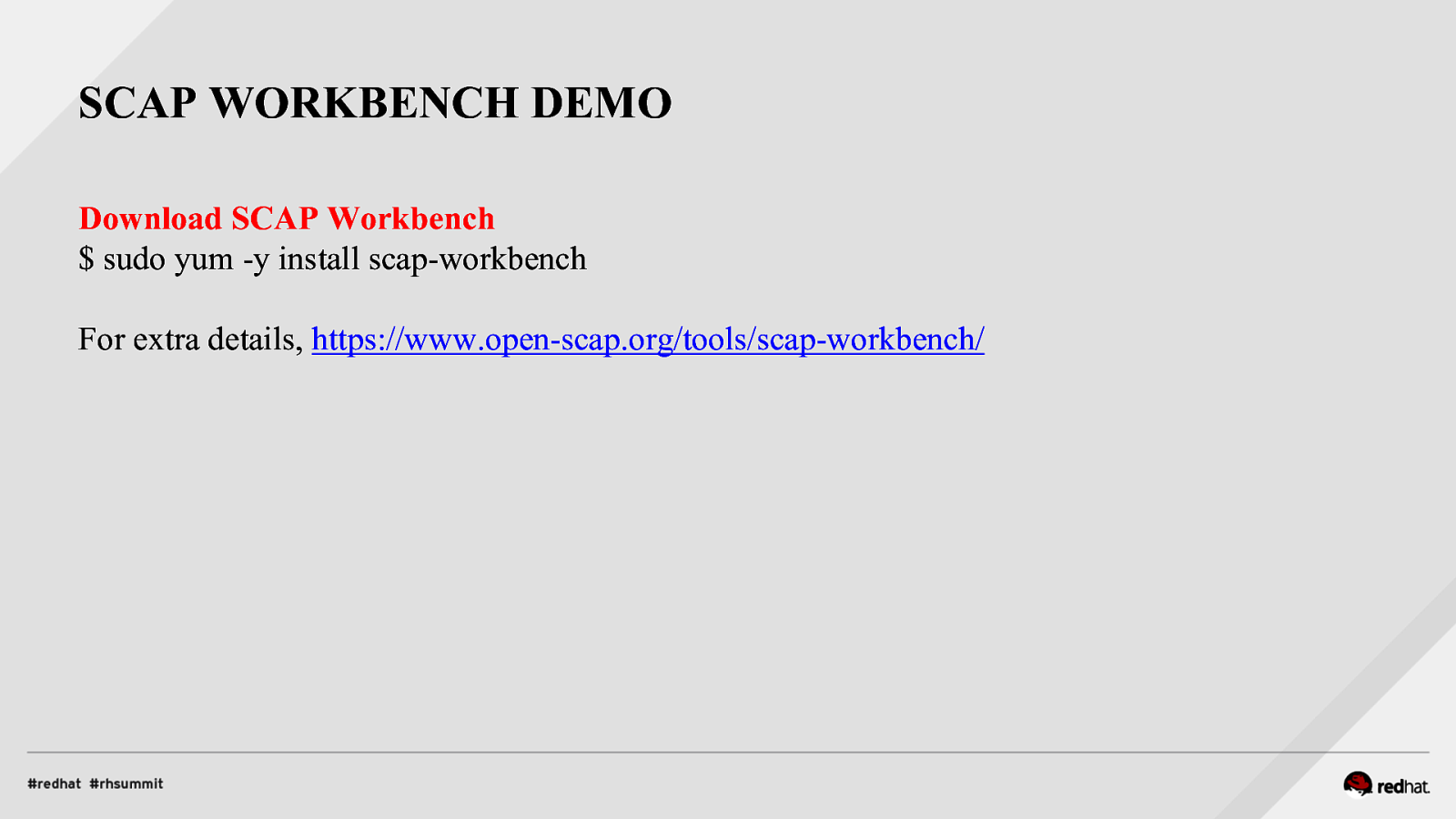
SCAP WORKBENCH DEMO Download SCAP Workbench $ sudo yum -y install scap-workbench For extra details, https://www.open-scap.org/tools/scap-workbench/

We’re done! Thank you! ADD NAME (View > Master > Slide master)
- What’s the latest in the Linux Security Automation space? A)Government & Commercial Initiatives B) Formal and Emerging SCAP Standards
2.What tools and content are available today? A) For enumerating (known) software vulnerabilities B) For assessing configuration
