Consumer to Collaborator: Re-imaging the US Government’s role in Open Source
A presentation at DevOpsDays DC in in Washington, DC, USA by Shawn Wells
Greg Elin, Founder, GovReady PBC (@gregelin)
Fen Labalme, Engineer, CivicActions
Shawn Wells, Director, Innovation Programs, Red Hat
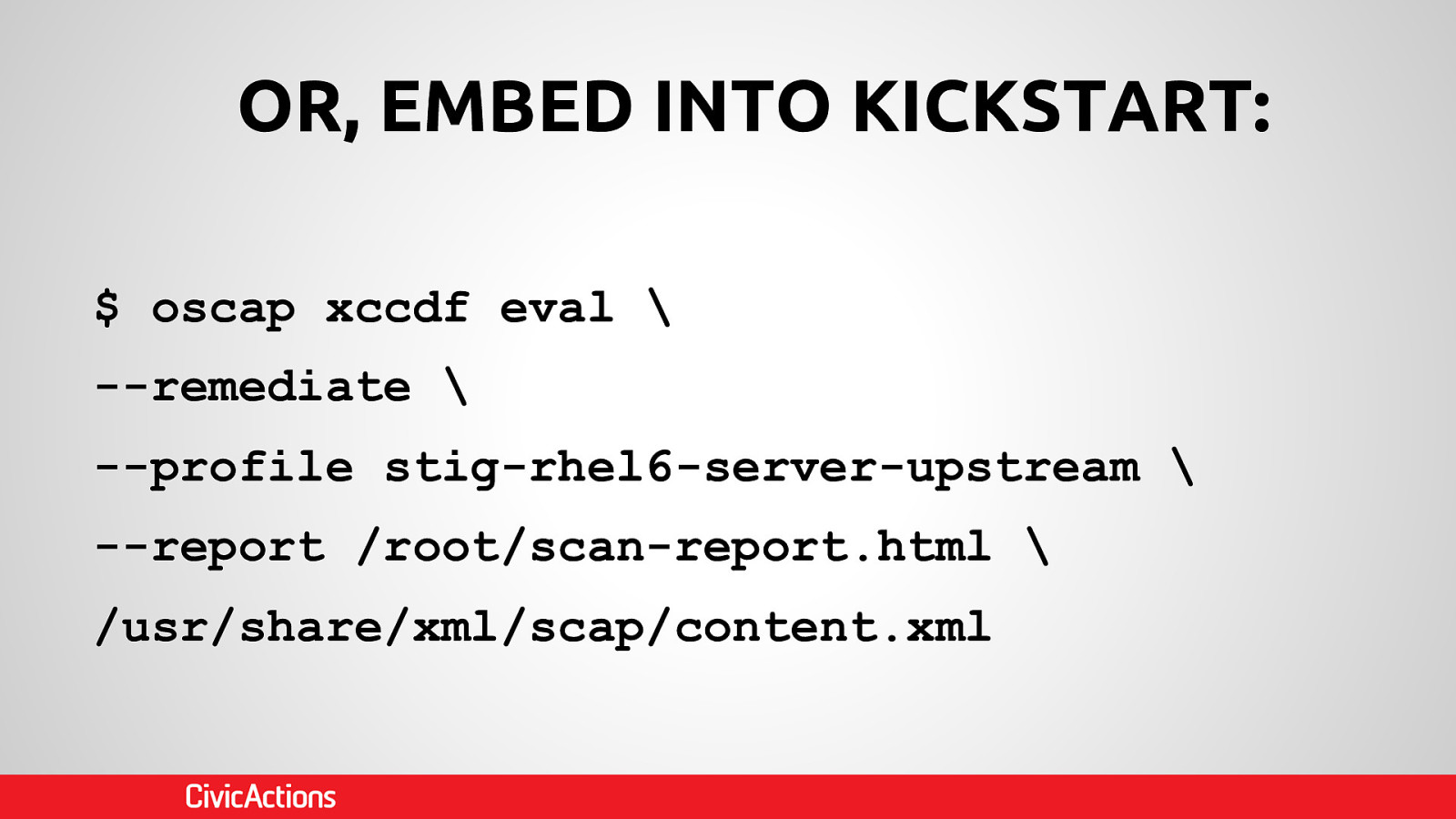
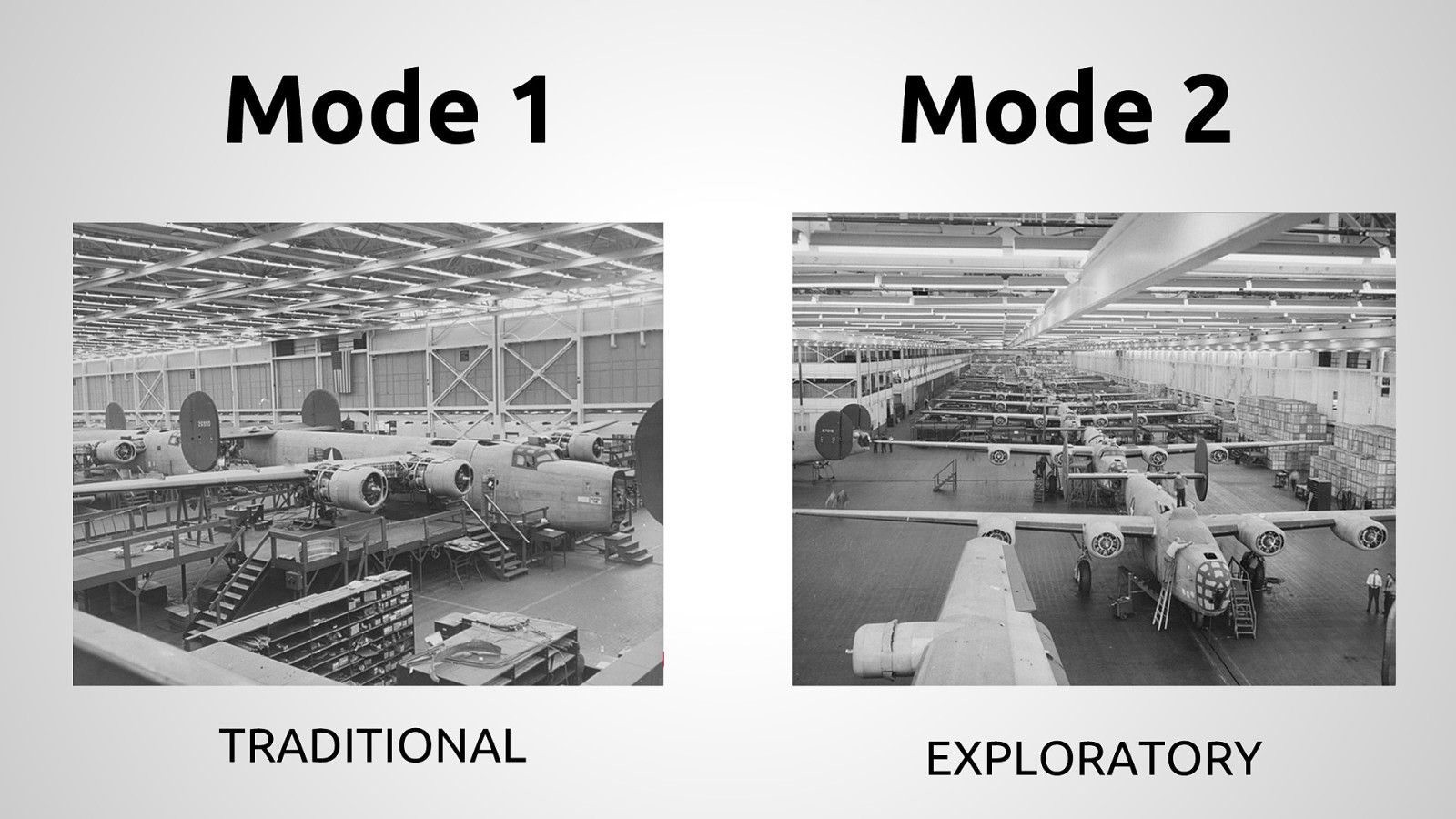
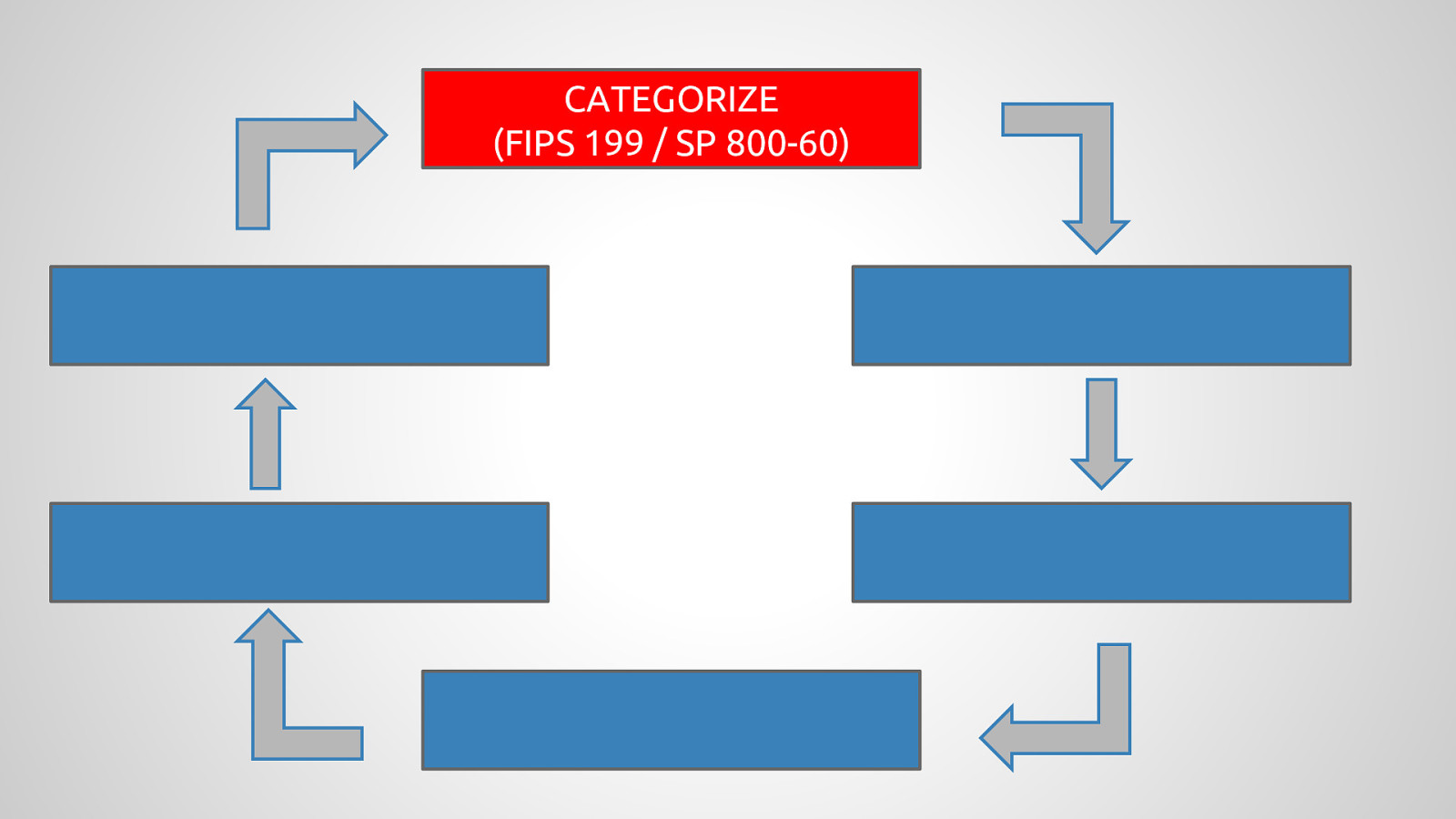
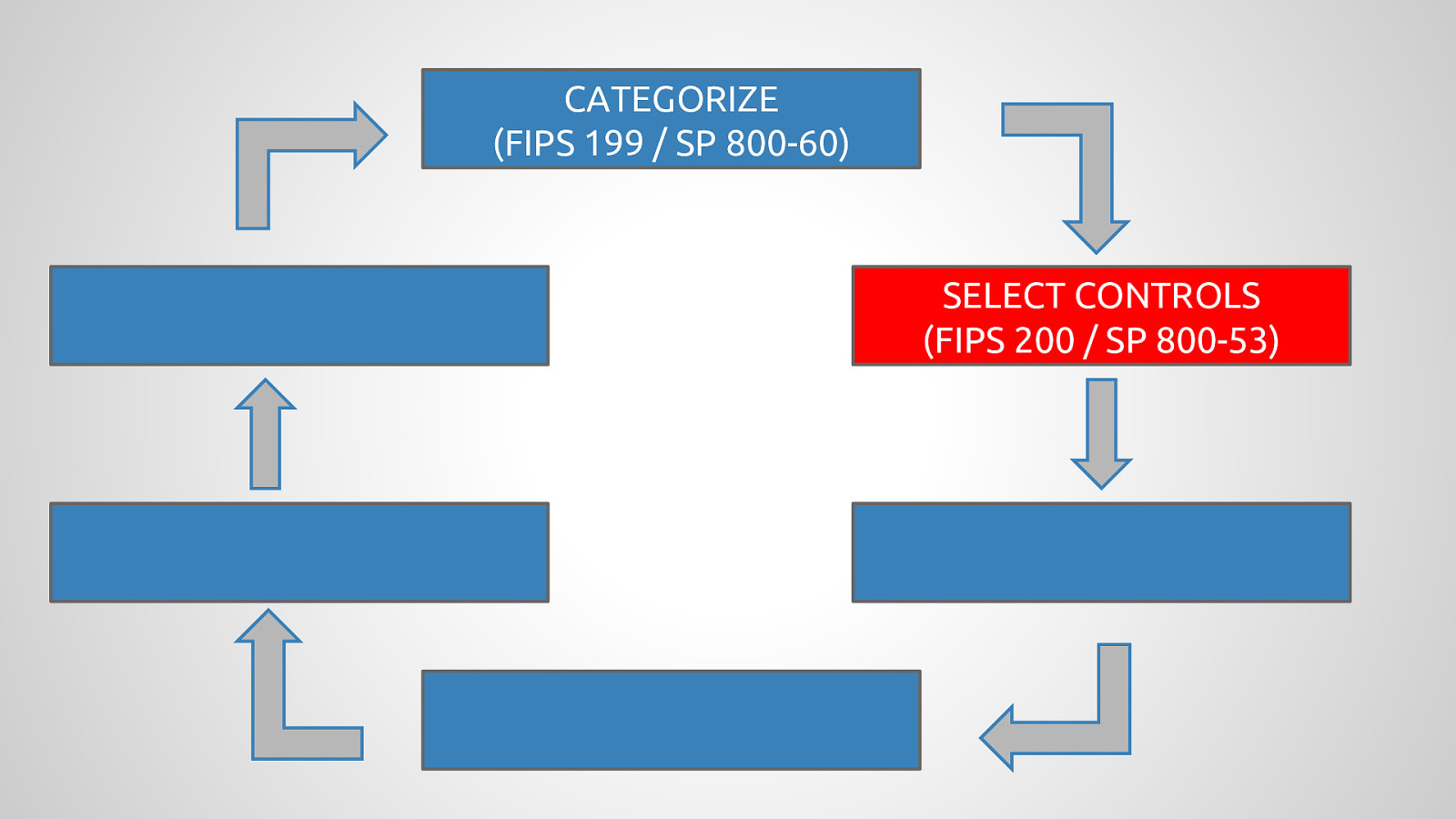
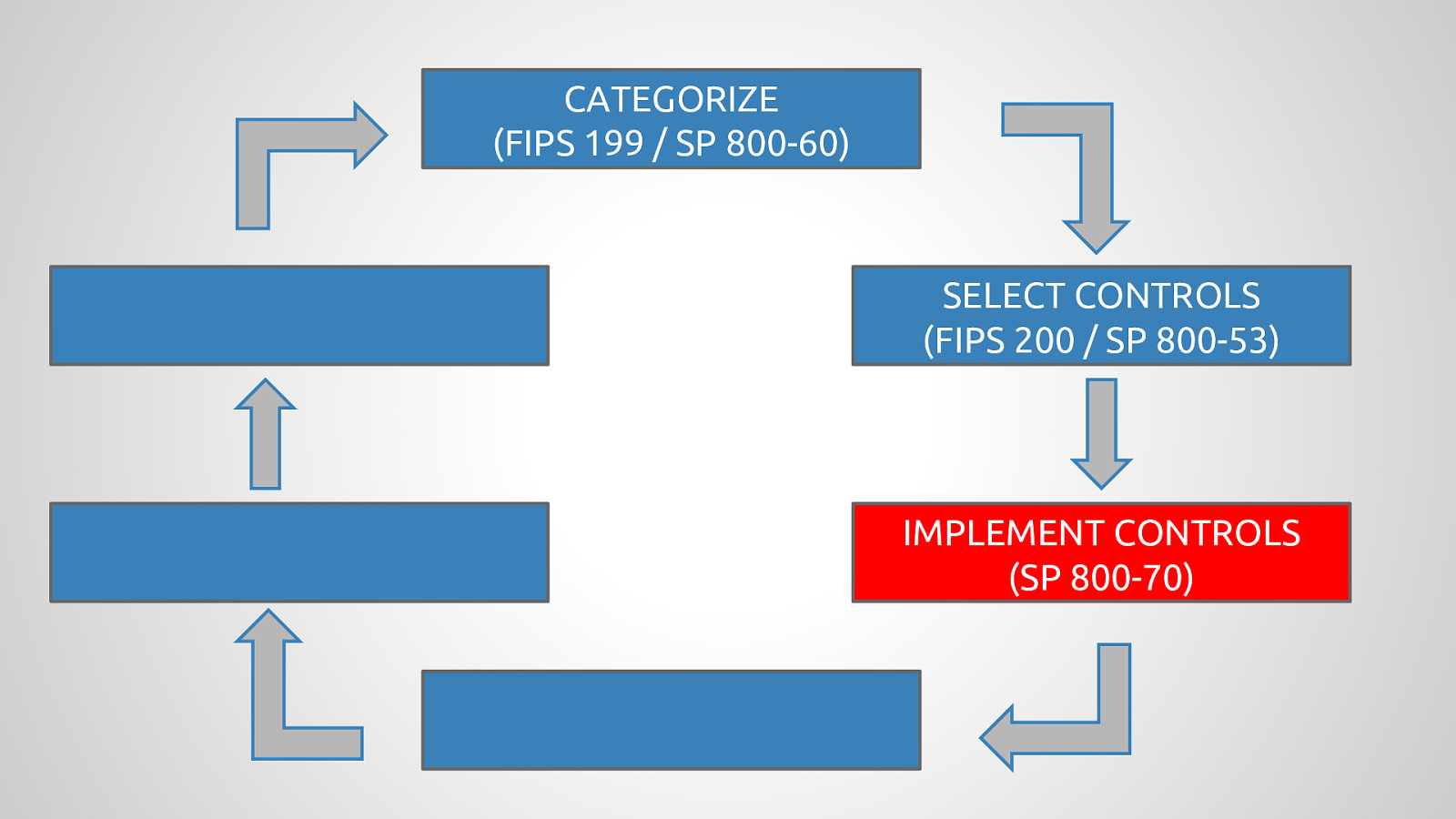
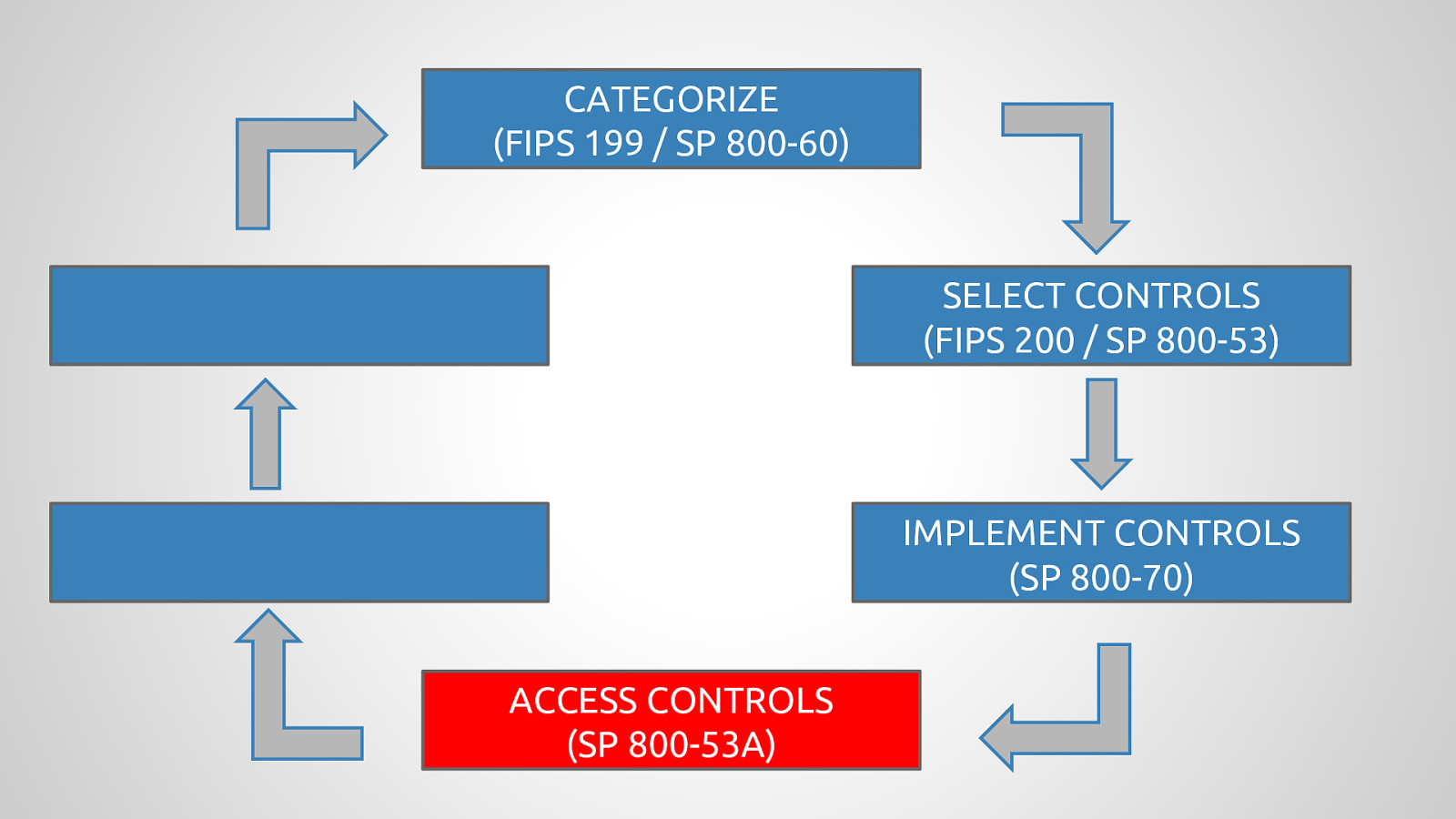
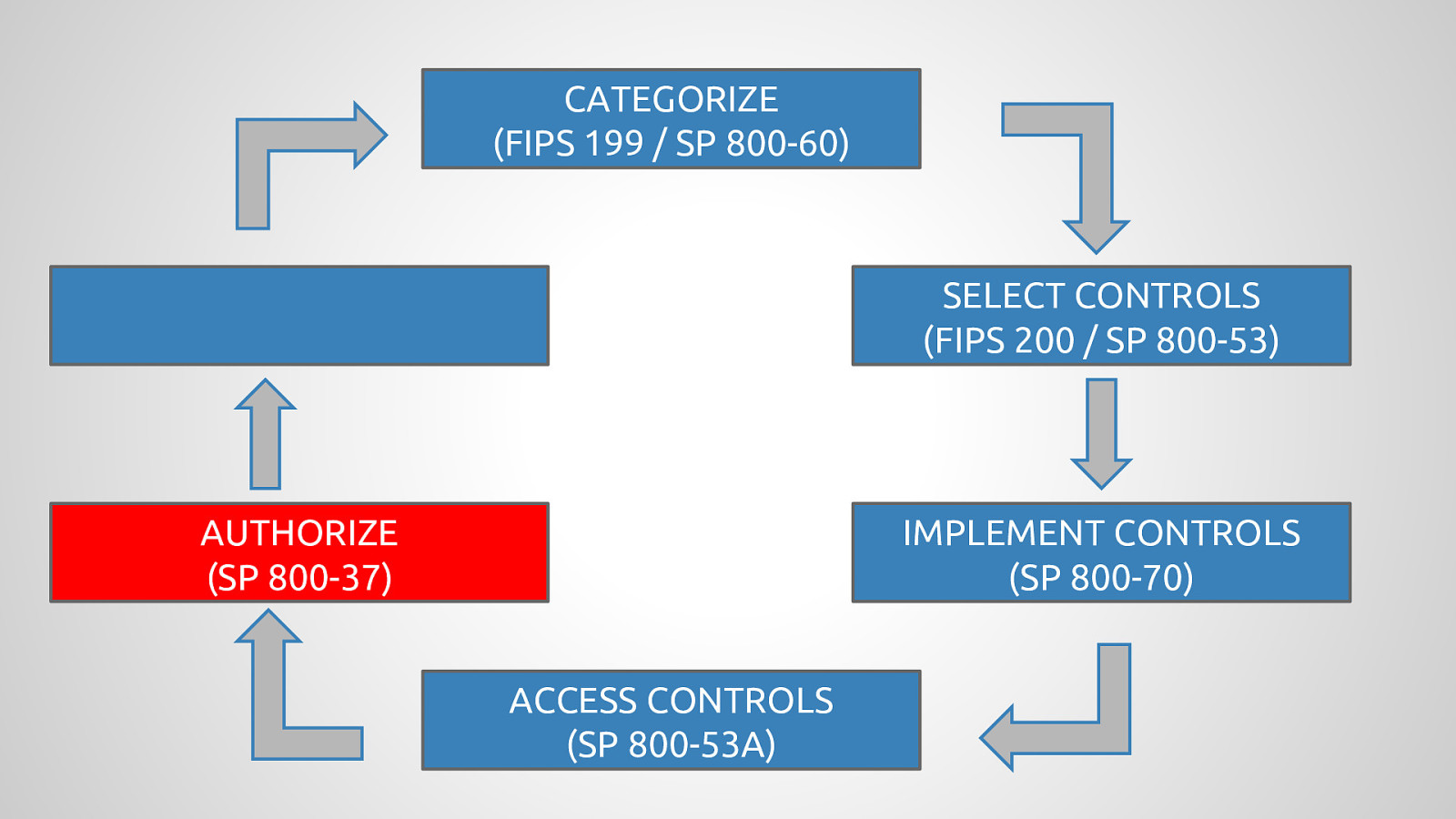
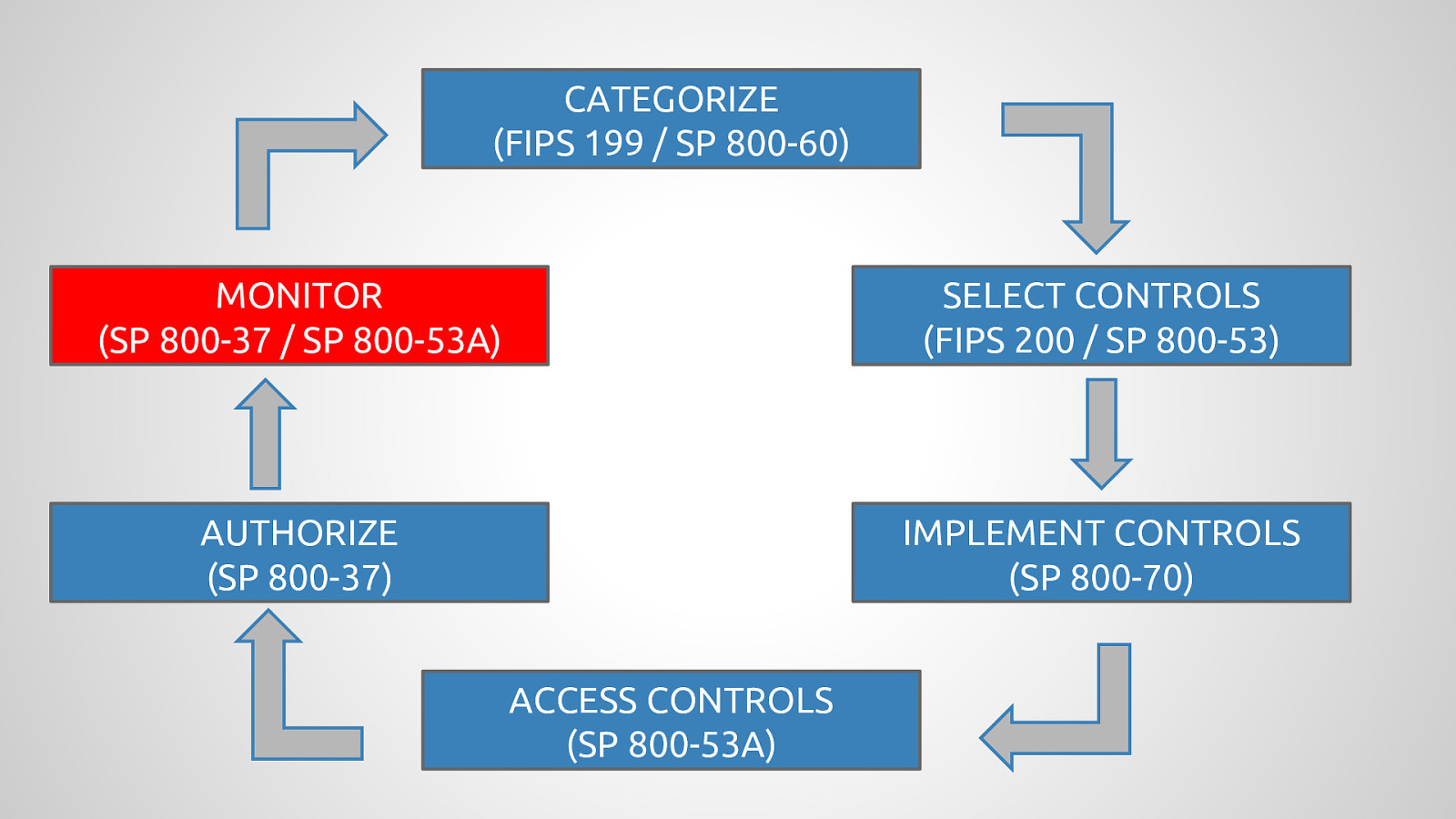
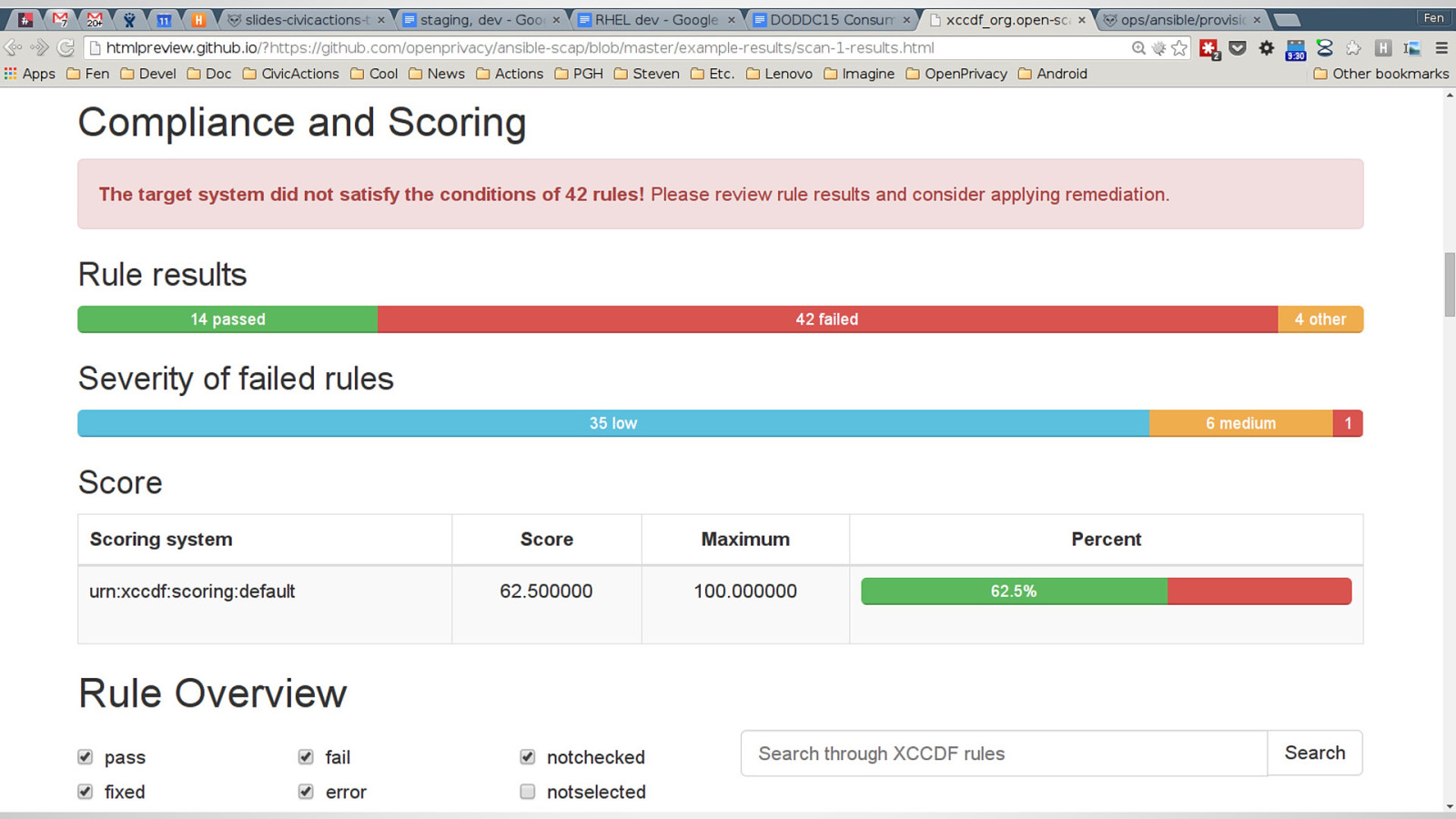
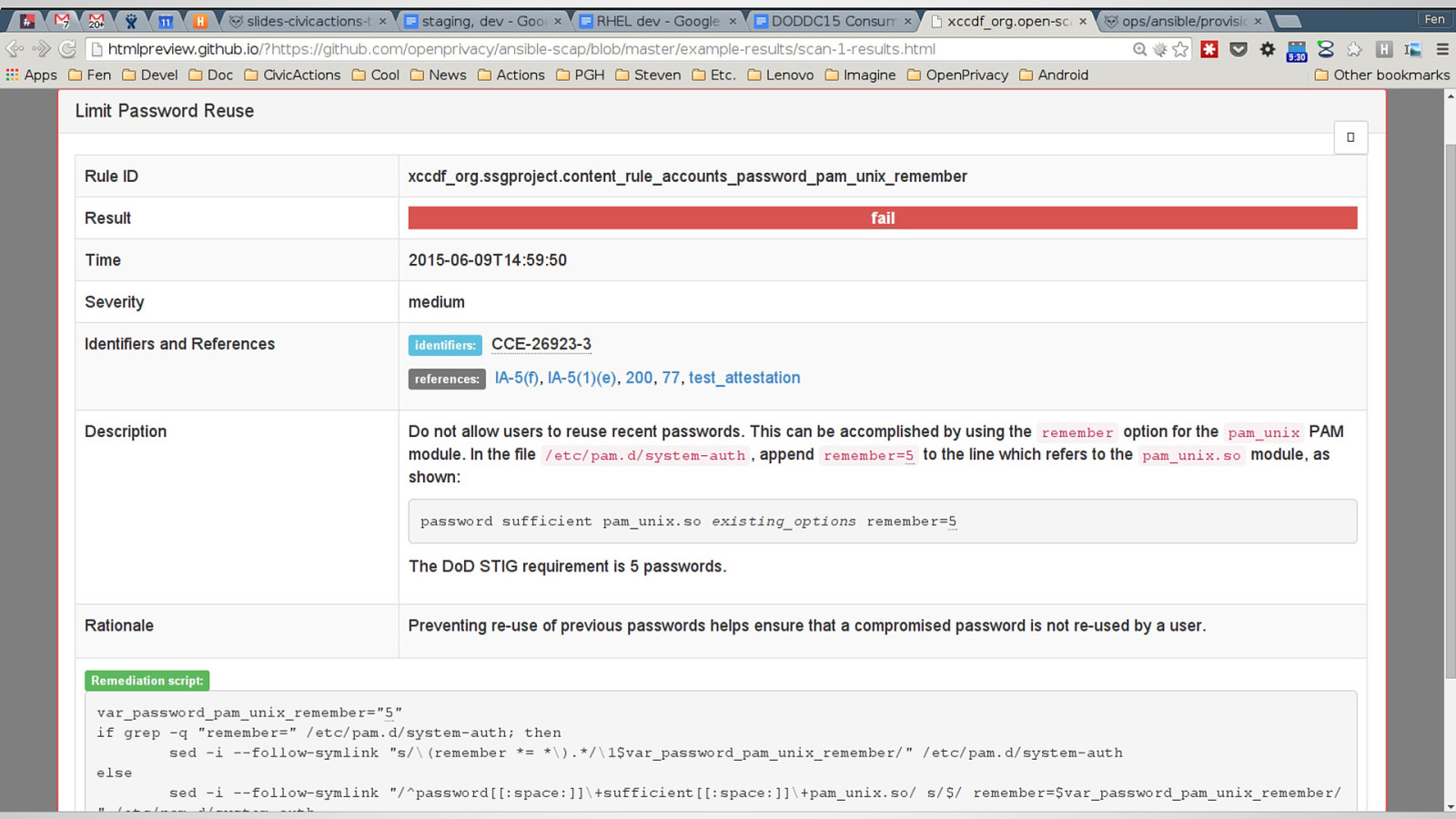
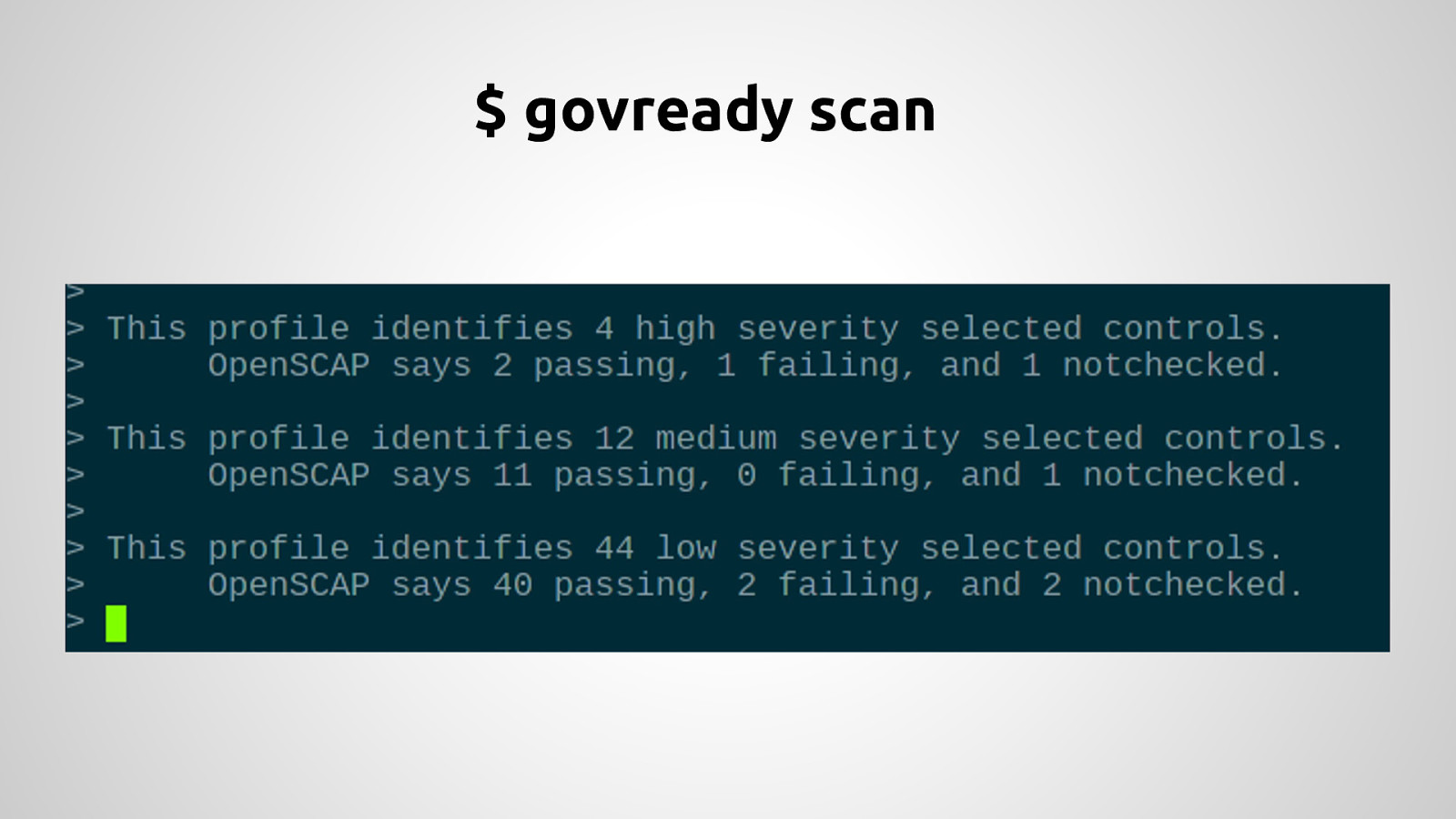
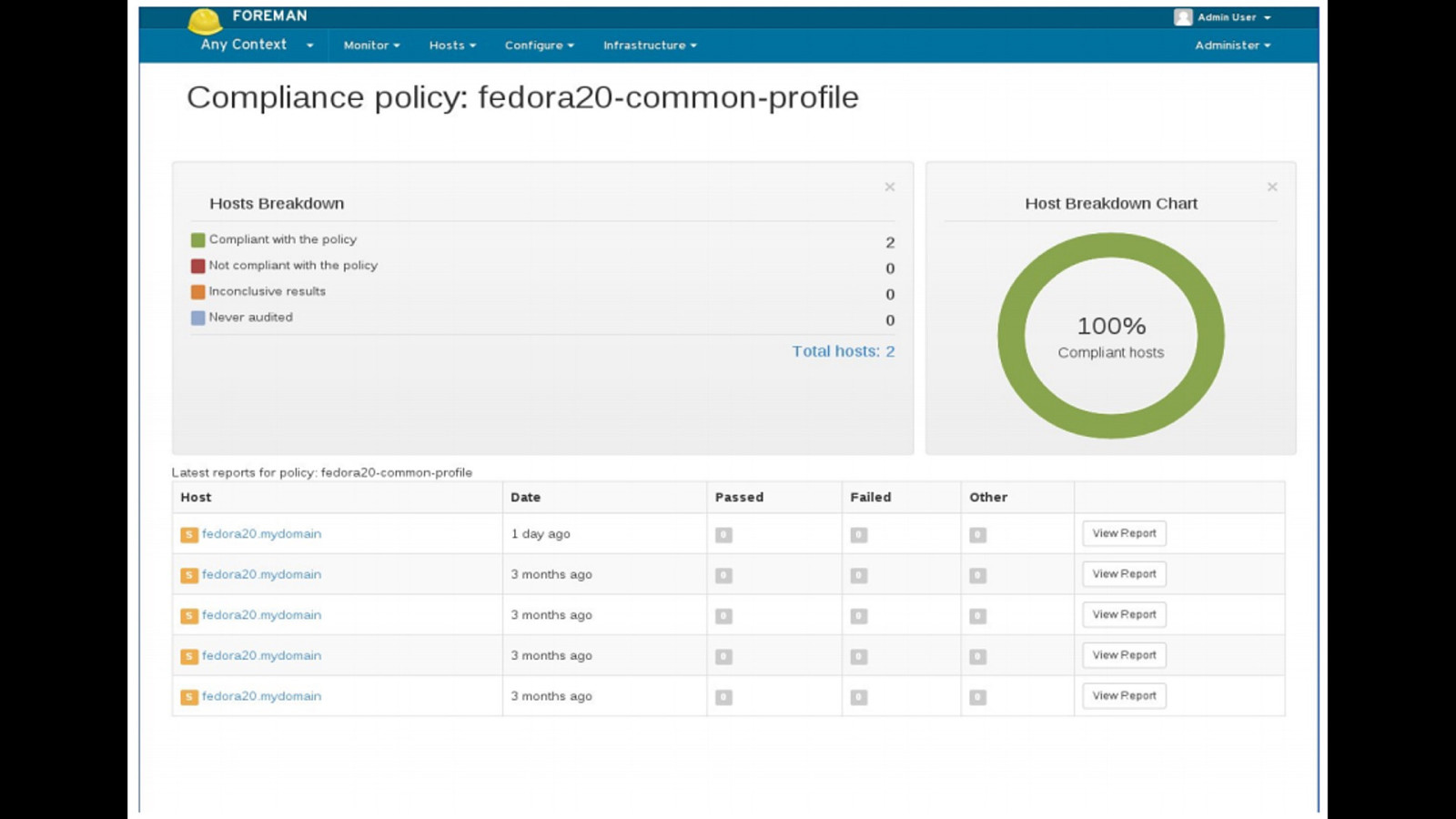
Government agencies are often hesitant to use open source tools out of concerns of security and compliance issues. This hesitancy to use open source deprives many government agencies from closely collaborating with others to create software that is finely tuned and widely available to scratch its own itch. The five-year old OpenSCAP community is helping to change that and re-imagining the US Governments role in open source through its NIST-Certified SCAP 1.2 scanning software and growing body of open source licensed SCAP content. By the OpenSCAP suite scanning and configuration management tools, government agencies looking to become high velocity organizations can automate the cumbersome process certifying a server has been properly hardened for production and begin to develop community resources for hardening of other popular open source tools. The OpenSCAP community is actively developing suite of software tools to make continuous monitoring in agile environments easier, especially for developers, who often do not realize they could be scanning their systems more collaboratively with Ops. OpenSCAP is not merely a secure piece of open source software, it is software that helps demonstrate security and compliance. The SCAP-Security-Guide Project is the only source of official configuration management SCAP and hardening content for Linux that is licensed open source and also directly reviewed by official government agencies. Initially started (and still significantly funded) by Red Hat, the OpenSCAP project has recently moved it’s repository from the the Fedora Project to GitHub and has seen an increase in the pace of development.