Changing the Open Hybrid Cloud Game: Deploying OpenShift to Azure
A presentation at GovLoop Webinar by Shawn Wells
Changing the Open Hybrid Cloud Game Deploying OpenShift to Azure Harold Wong Cloud Architect Commercial Software Engineering harold.wong@microsoft.com ADD NAME (View > Master > Slide master)
Red Hat OpenShift Container Platform ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)

ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
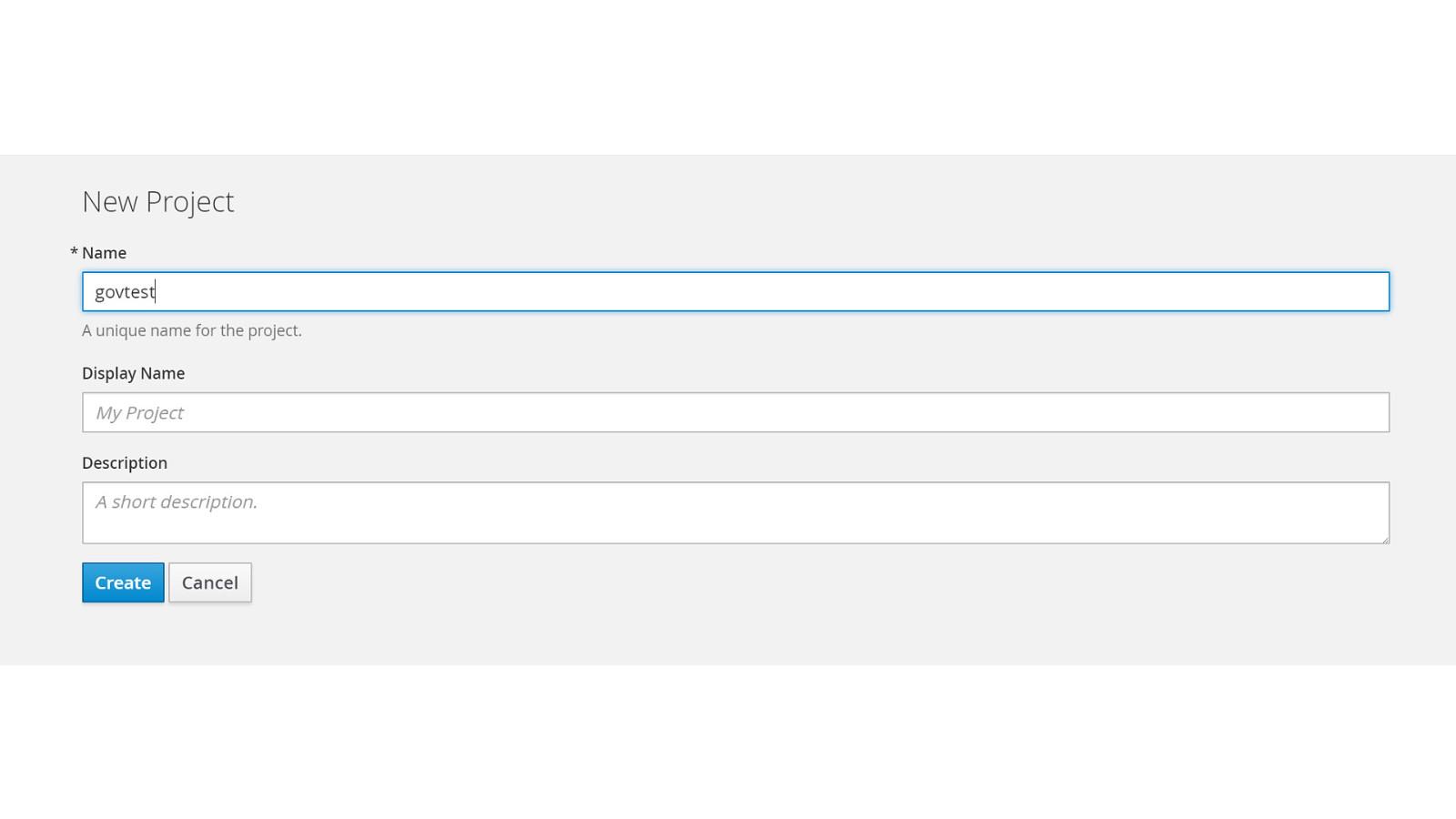
ADD NAME (View > Master > Slide master)
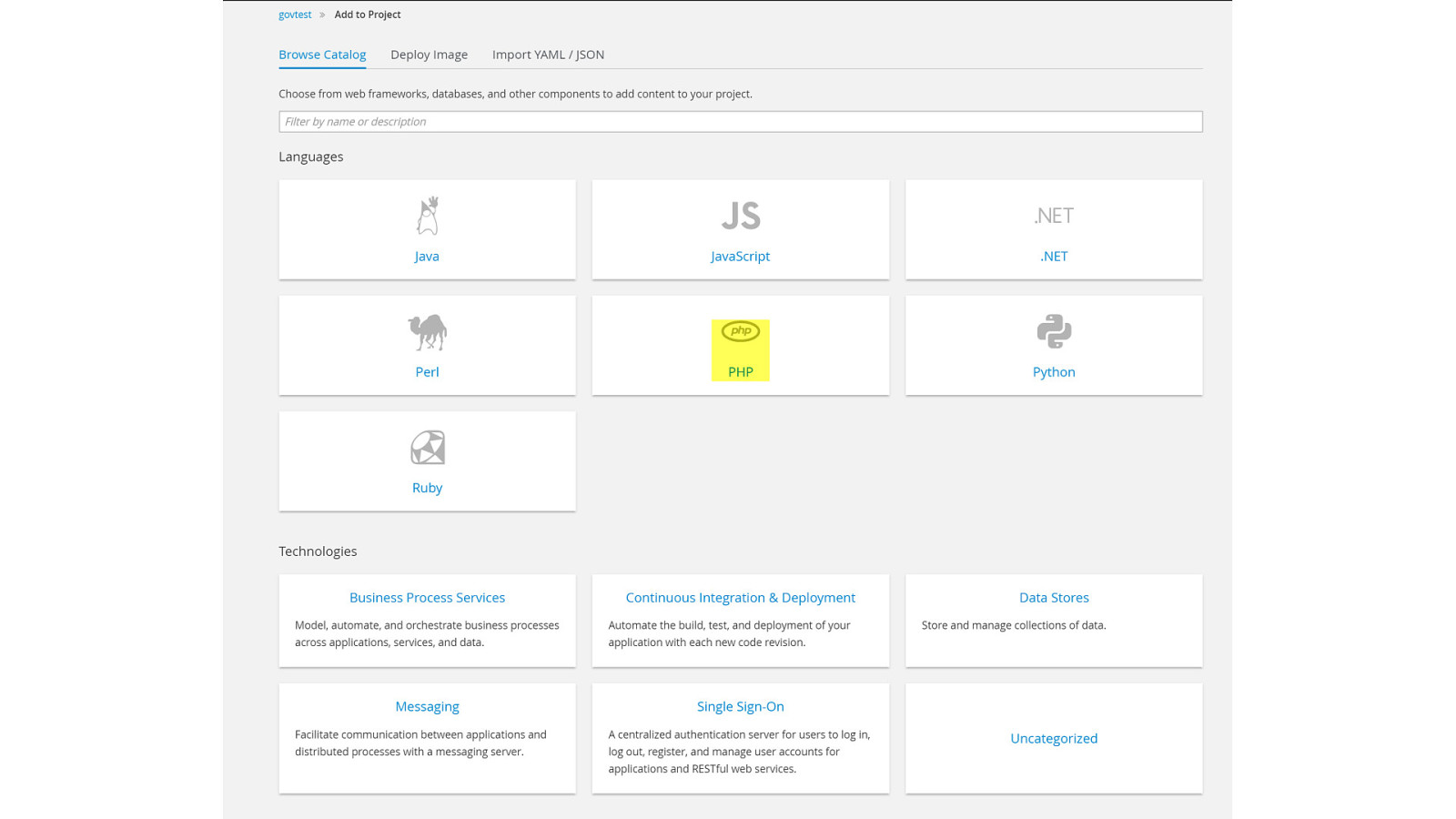
ADD NAME (View > Master > Slide master)
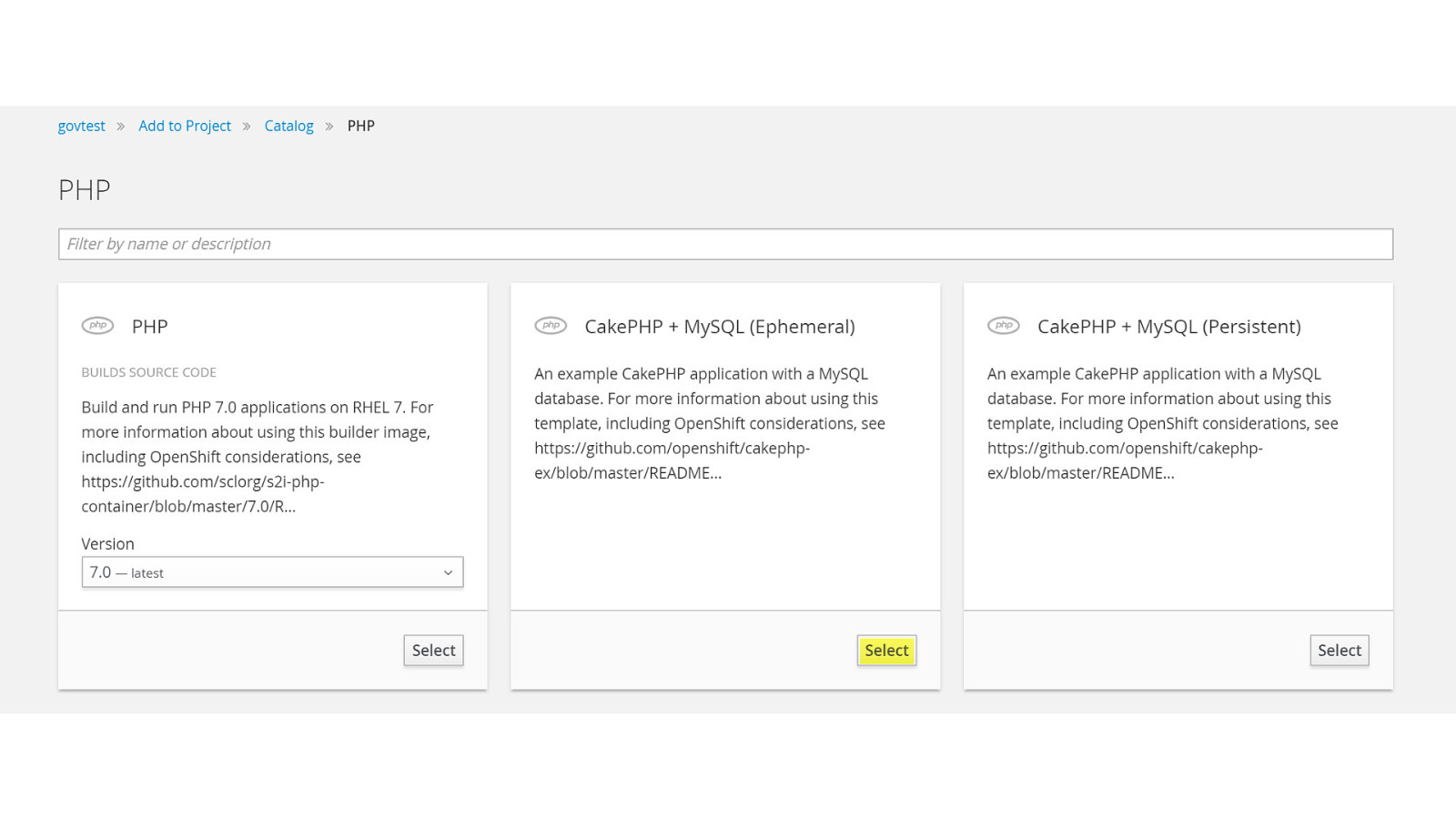
ADD NAME (View > Master > Slide master)
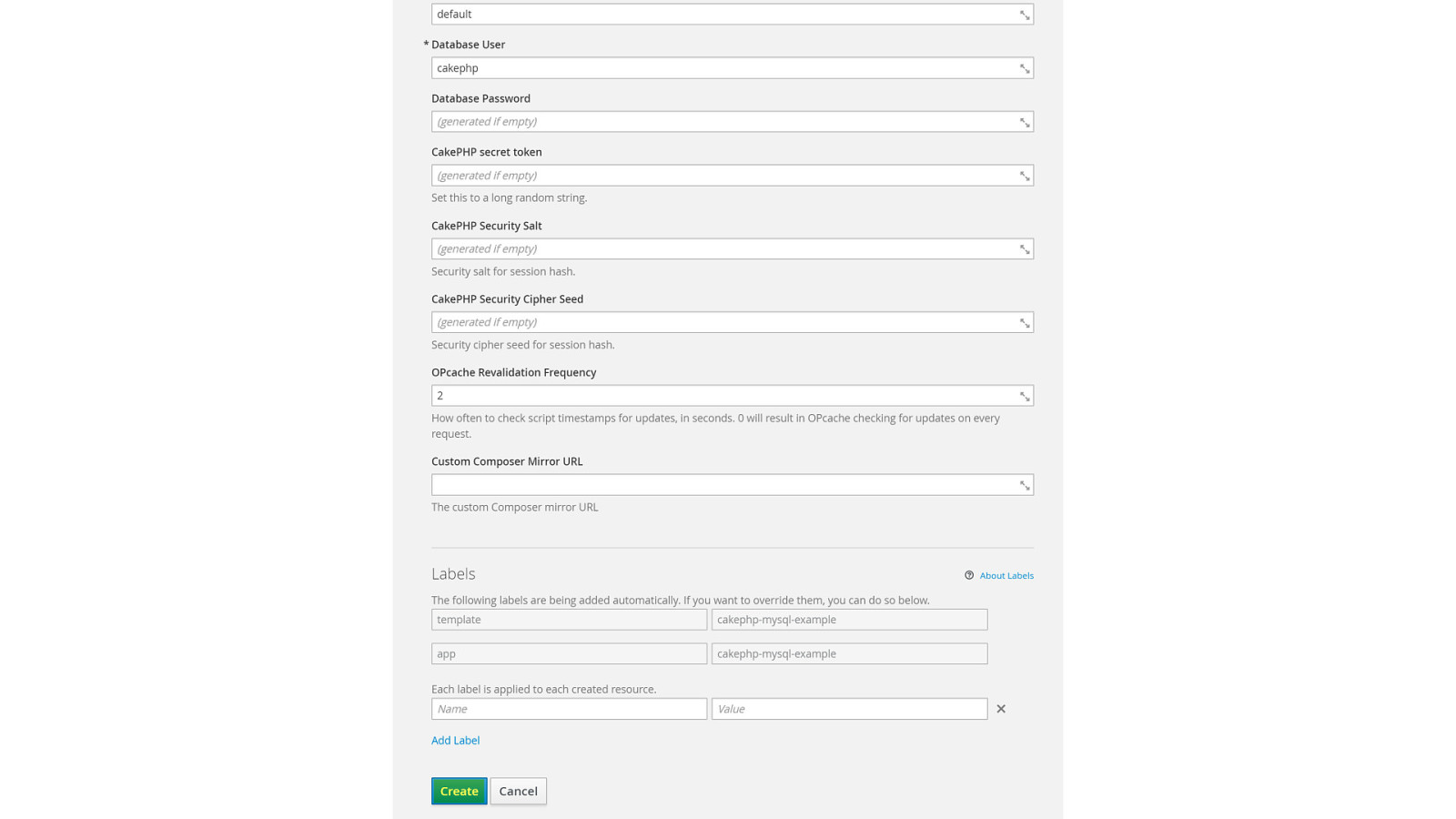
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)
ADD NAME (View > Master > Slide master)

Accrediting OpenShift On Azure Shawn Wells Office of the Chief Technologist U.S. Public Sector shawn@redhat.com || 443-534-0130 ADD NAME (View > Master > Slide master)
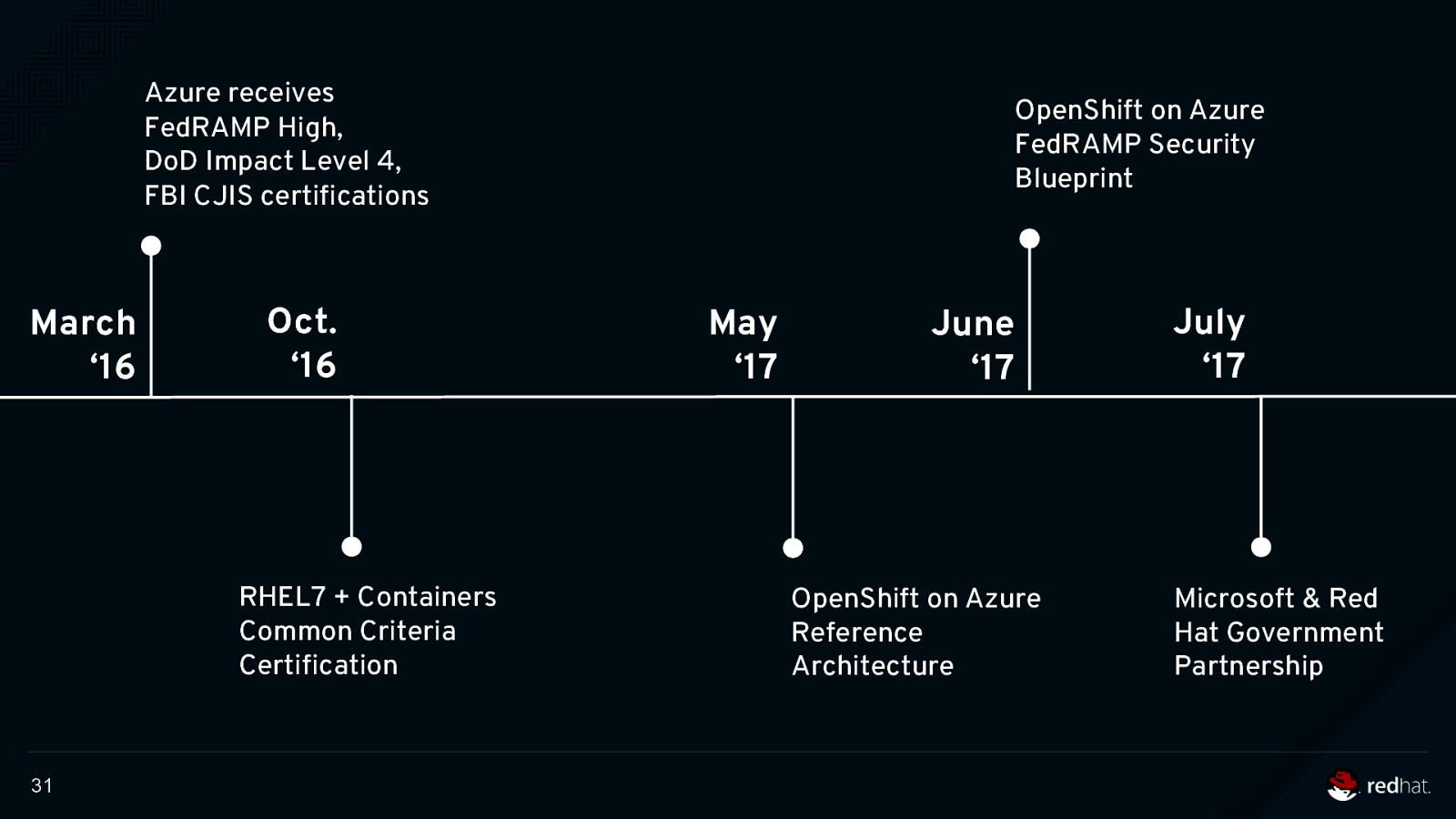
Azure receives FedRAMP High, DoD Impact Level 4, FBI CJIS certifications March ‘16 Oct. ‘16 RHEL7 + Containers Common Criteria Certification 31 OpenShift on Azure FedRAMP Security Blueprint May ‘17 June ‘17 OpenShift on Azure Reference Architecture July ‘17 Microsoft & Red Hat Government Partnership

Azure for Government Certifications DoD Impact Level 4 ITAR Readiness FedRAMP High ● Allows all DoD and mission partners to leverage Azure for “Controlled Unclassified Information” ● aka “FOUO” 32

Azure for Government Certifications DoD Impact Level 4 ITAR Readiness FedRAMP High 33 ● Store and process regulated data. ● Azure facilities and personnel US-based.
Azure for Government Certifications DoD Impact Level 4 ITAR Readiness FedRAMP High 34 ● Focus for today. ● GSA-estimated 50% of $80B Federal IT budget falls under ‘FedRAMP High’

Red Hat Certifications Common Criteria ● RHEL 7.1 certified to EAL4+. ● 3rd party lab verifies security functionality. ● Certified multi-tenancy capabilities. 35
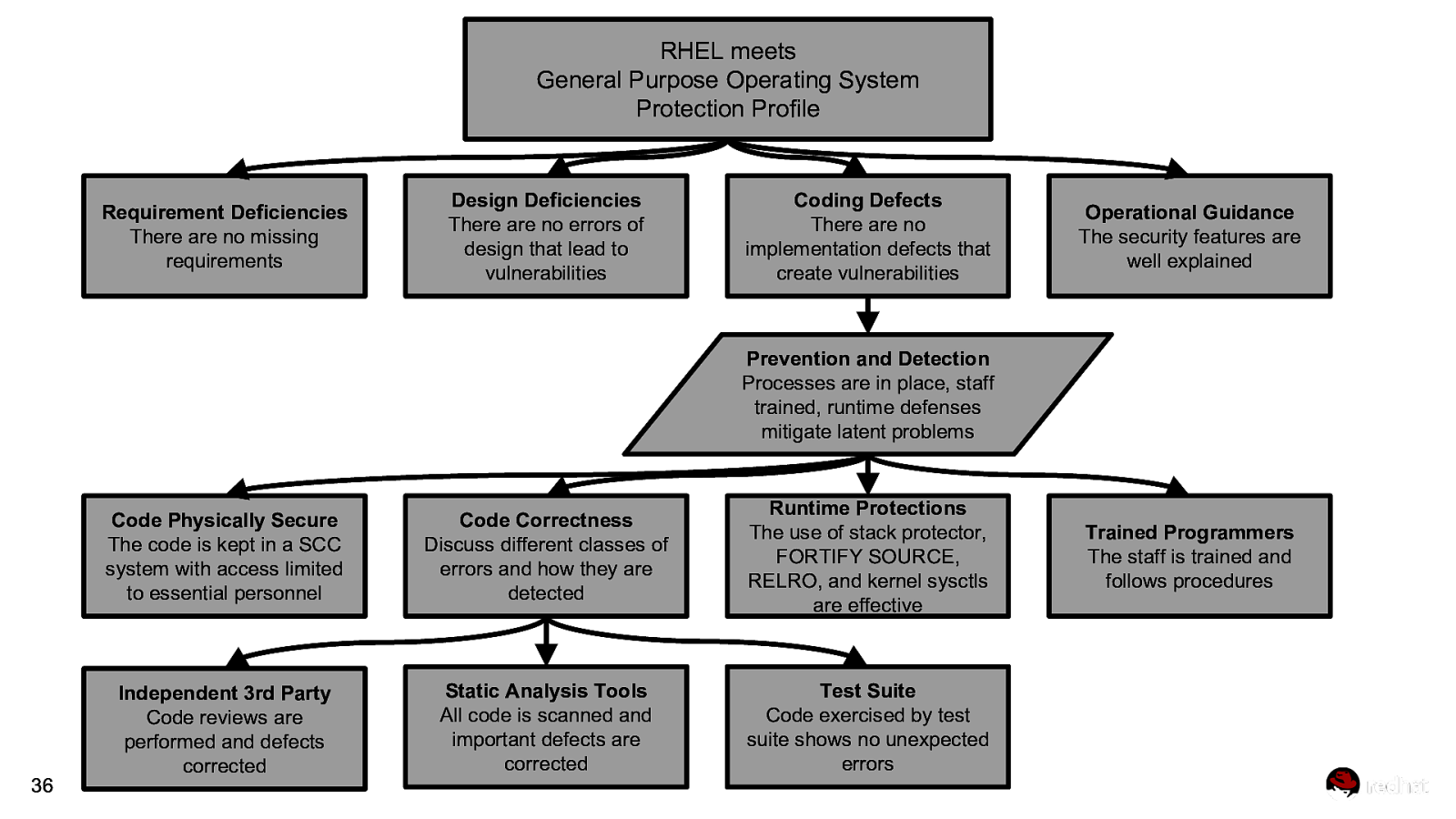
RHEL meets General Purpose Operating System Protection Profile Requirement Deficiencies There are no missing requirements Design Deficiencies There are no errors of design that lead to vulnerabilities Coding Defects There are no implementation defects that create vulnerabilities Operational Guidance The security features are well explained Prevention and Detection Processes are in place, staff trained, runtime defenses mitigate latent problems 36 Code Physically Secure The code is kept in a SCC system with access limited to essential personnel Code Correctness Discuss different classes of errors and how they are detected Runtime Protections The use of stack protector, FORTIFY SOURCE, RELRO, and kernel sysctls are effective Independent 3rd Party Code reviews are performed and defects corrected Static Analysis Tools All code is scanned and important defects are corrected Test Suite Code exercised by test suite shows no unexpected errors Trained Programmers The staff is trained and follows procedures
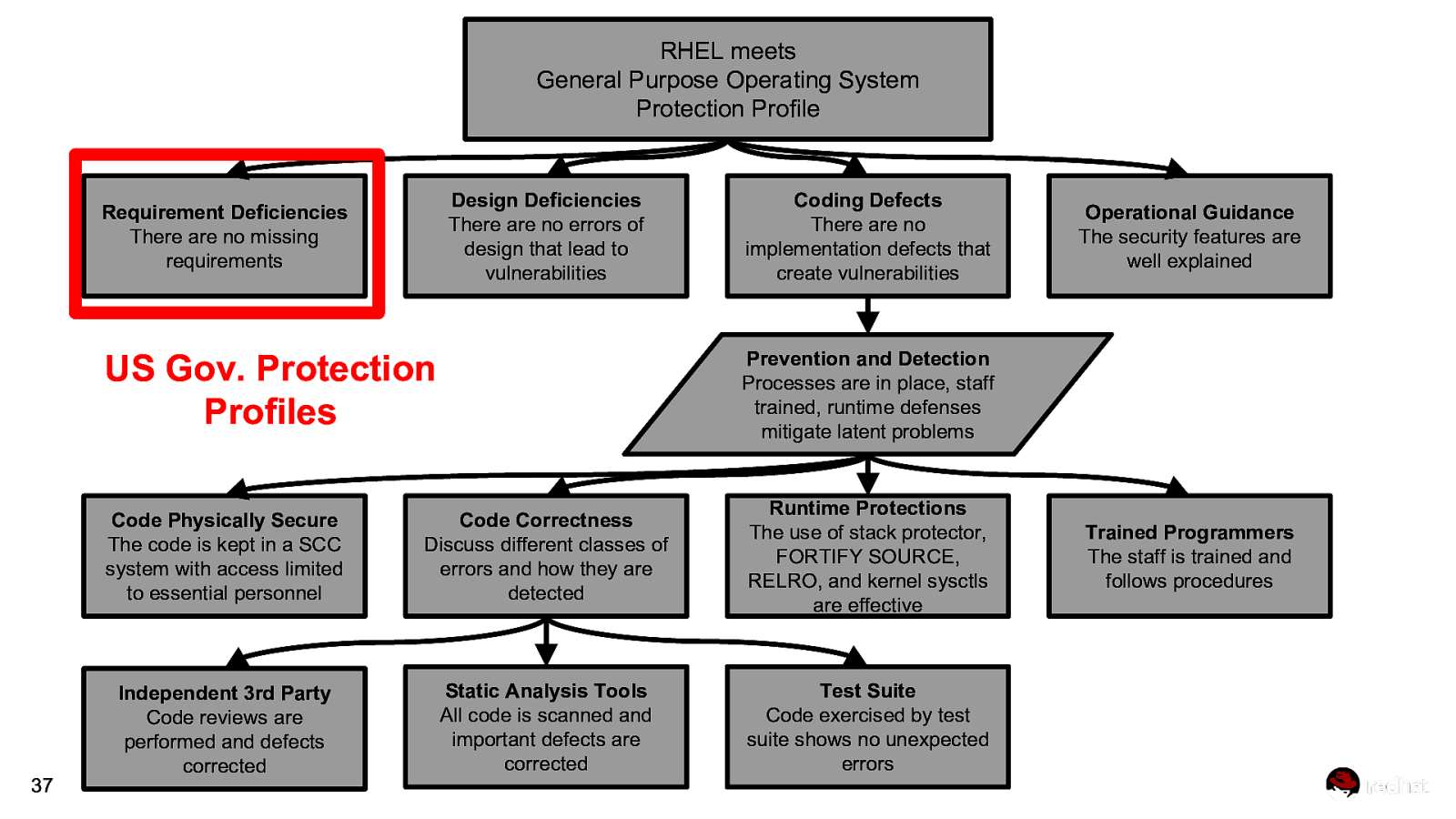
RHEL meets General Purpose Operating System Protection Profile Design Deficiencies There are no errors of design that lead to vulnerabilities Requirement Deficiencies There are no missing requirements 37 Coding Defects There are no implementation defects that create vulnerabilities US Gov. Protection Profiles Prevention and Detection Processes are in place, staff trained, runtime defenses mitigate latent problems Code Physically Secure The code is kept in a SCC system with access limited to essential personnel Code Correctness Discuss different classes of errors and how they are detected Runtime Protections The use of stack protector, FORTIFY SOURCE, RELRO, and kernel sysctls are effective Independent 3rd Party Code reviews are performed and defects corrected Static Analysis Tools All code is scanned and important defects are corrected Test Suite Code exercised by test suite shows no unexpected errors Operational Guidance The security features are well explained Trained Programmers The staff is trained and follows procedures
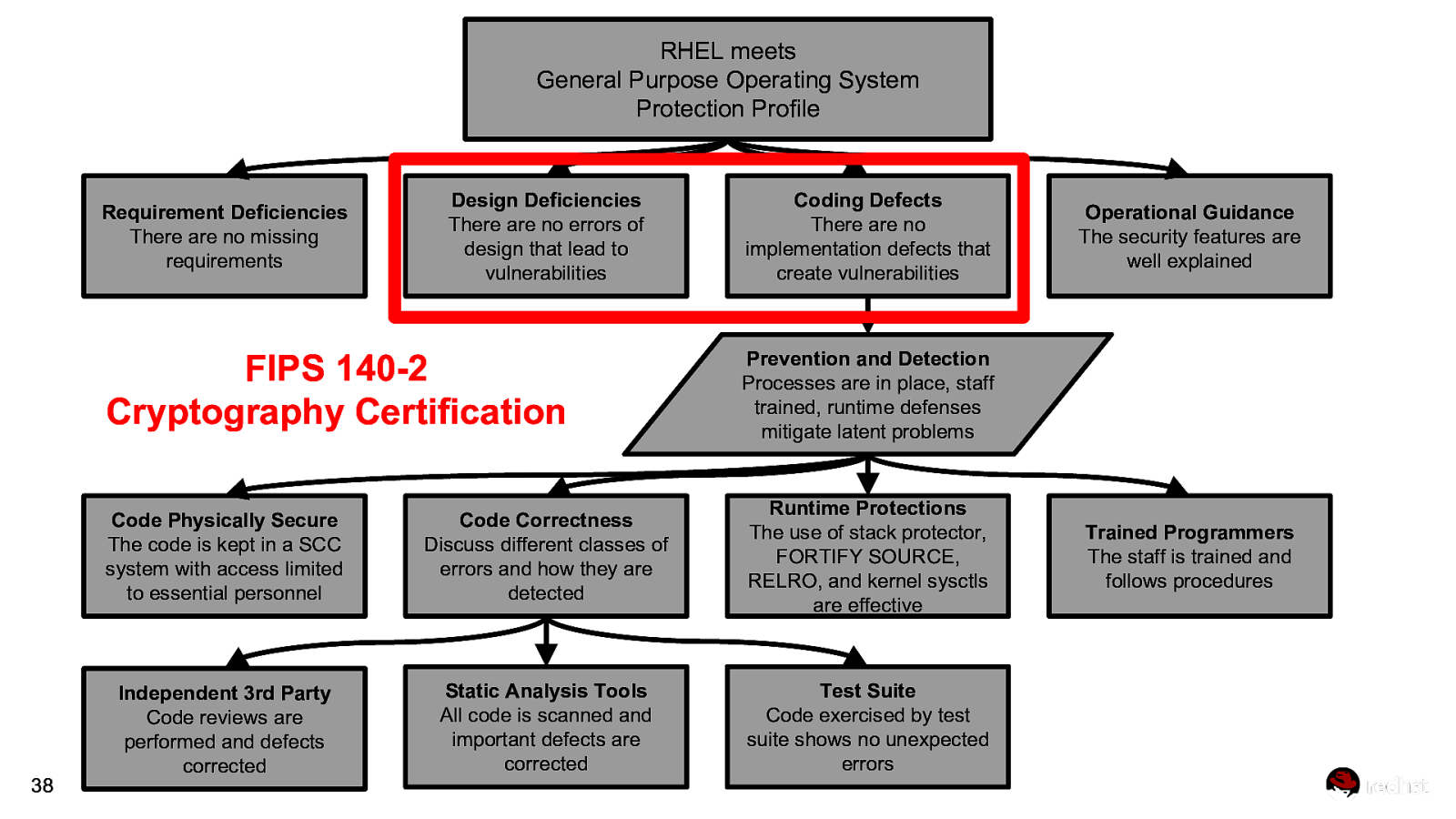
RHEL meets General Purpose Operating System Protection Profile Requirement Deficiencies There are no missing requirements 38 Design Deficiencies There are no errors of design that lead to vulnerabilities Coding Defects There are no implementation defects that create vulnerabilities FIPS 140-2 Cryptography Certification Prevention and Detection Processes are in place, staff trained, runtime defenses mitigate latent problems Code Physically Secure The code is kept in a SCC system with access limited to essential personnel Code Correctness Discuss different classes of errors and how they are detected Runtime Protections The use of stack protector, FORTIFY SOURCE, RELRO, and kernel sysctls are effective Independent 3rd Party Code reviews are performed and defects corrected Static Analysis Tools All code is scanned and important defects are corrected Test Suite Code exercised by test suite shows no unexpected errors Operational Guidance The security features are well explained Trained Programmers The staff is trained and follows procedures
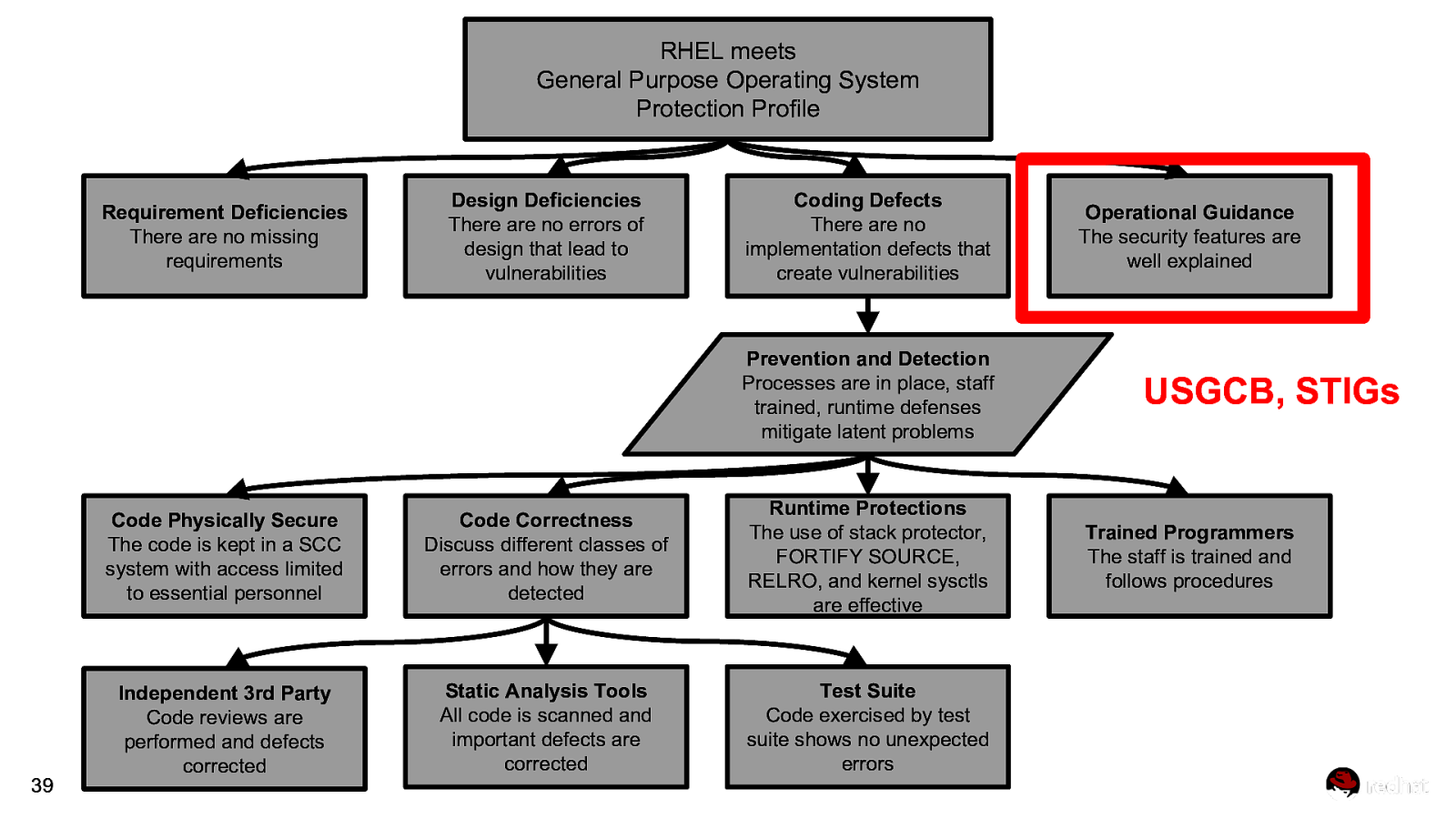
RHEL meets General Purpose Operating System Protection Profile Requirement Deficiencies There are no missing requirements Design Deficiencies There are no errors of design that lead to vulnerabilities Coding Defects There are no implementation defects that create vulnerabilities Prevention and Detection Processes are in place, staff trained, runtime defenses mitigate latent problems 39 Code Physically Secure The code is kept in a SCC system with access limited to essential personnel Code Correctness Discuss different classes of errors and how they are detected Runtime Protections The use of stack protector, FORTIFY SOURCE, RELRO, and kernel sysctls are effective Independent 3rd Party Code reviews are performed and defects corrected Static Analysis Tools All code is scanned and important defects are corrected Test Suite Code exercised by test suite shows no unexpected errors Operational Guidance The security features are well explained USGCB, STIGs Trained Programmers The staff is trained and follows procedures
PUTTING IT TOGETHER: OpenShift On Azure Reference Architecture + Security Blueprint
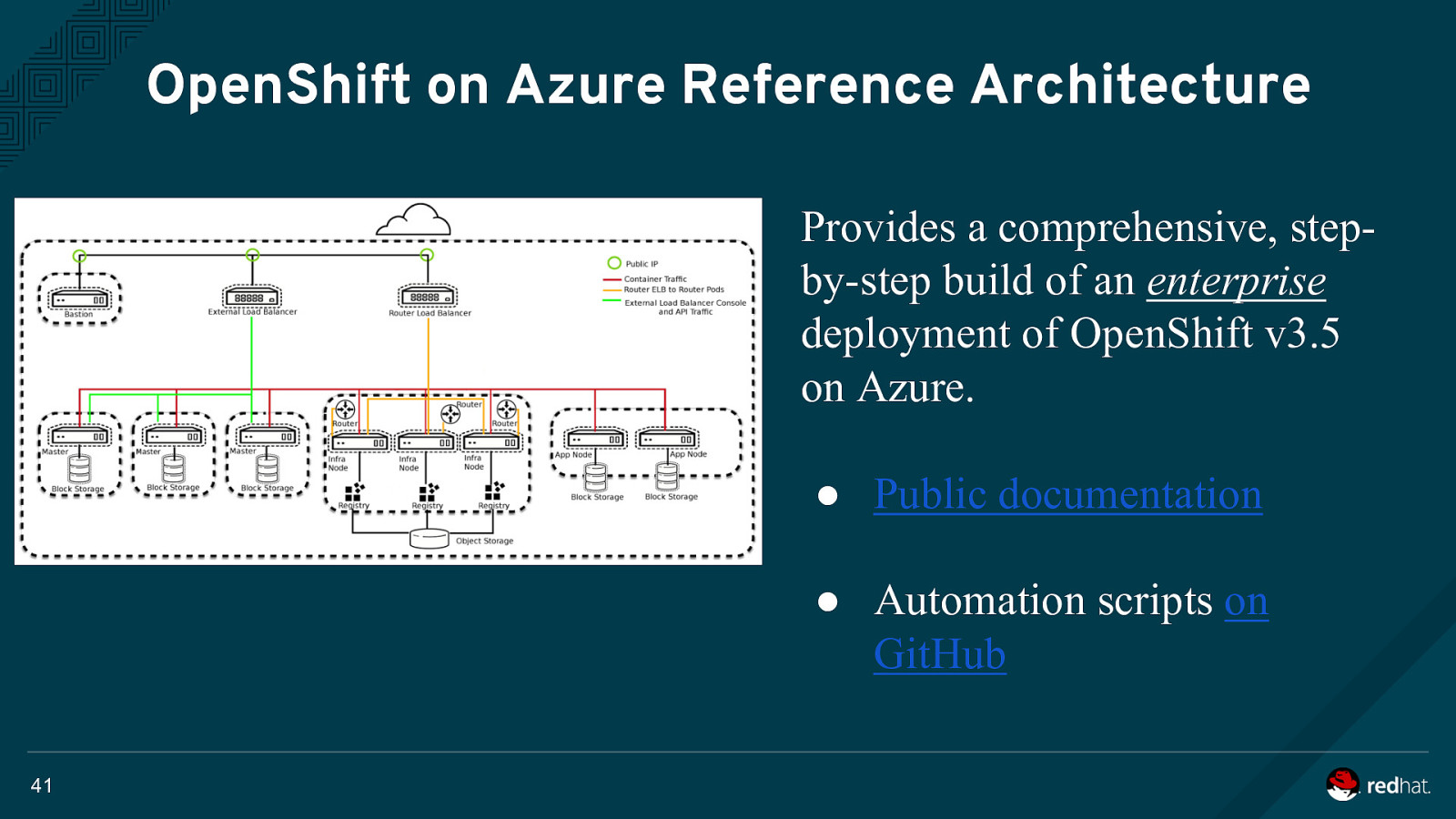
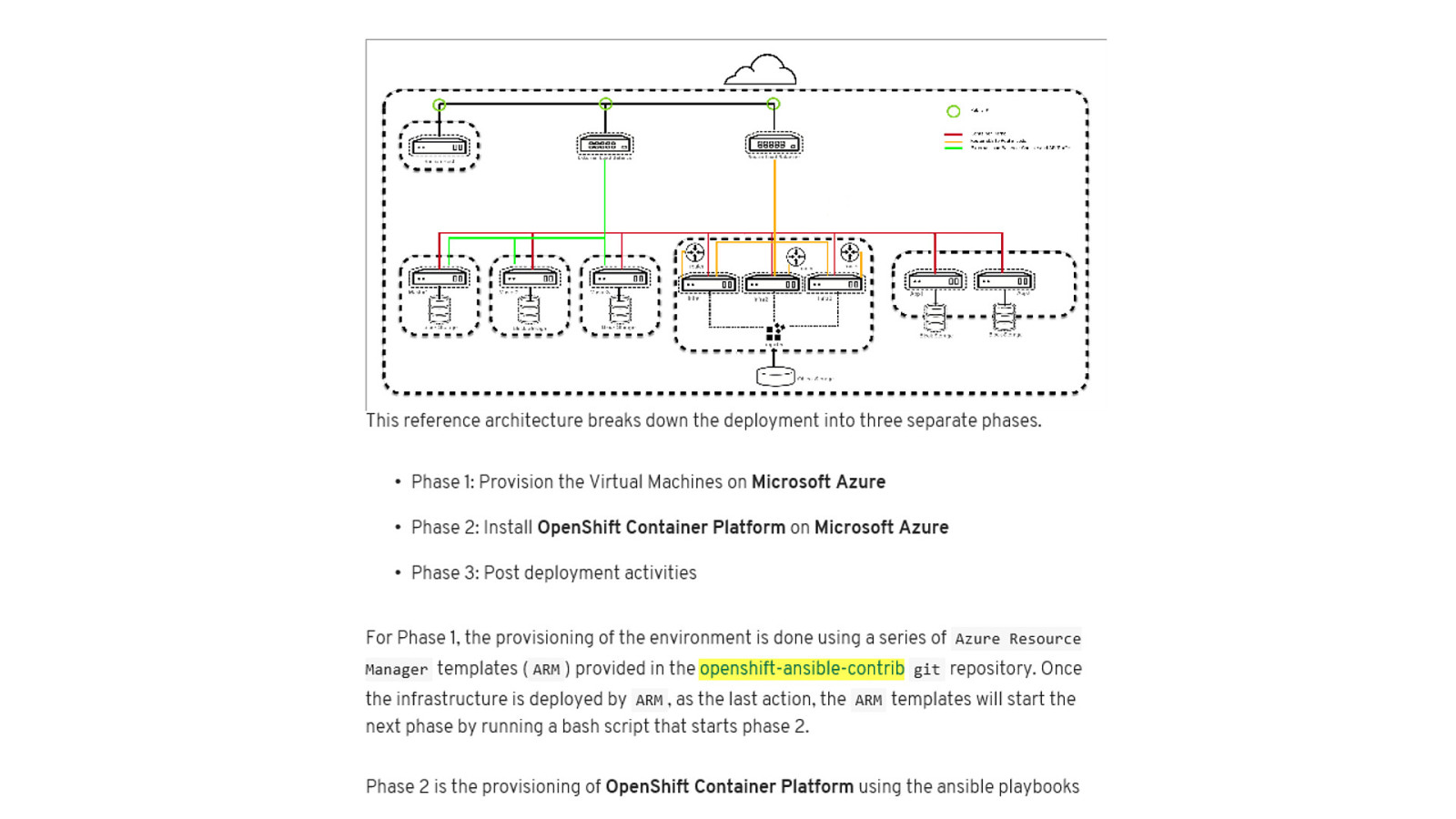
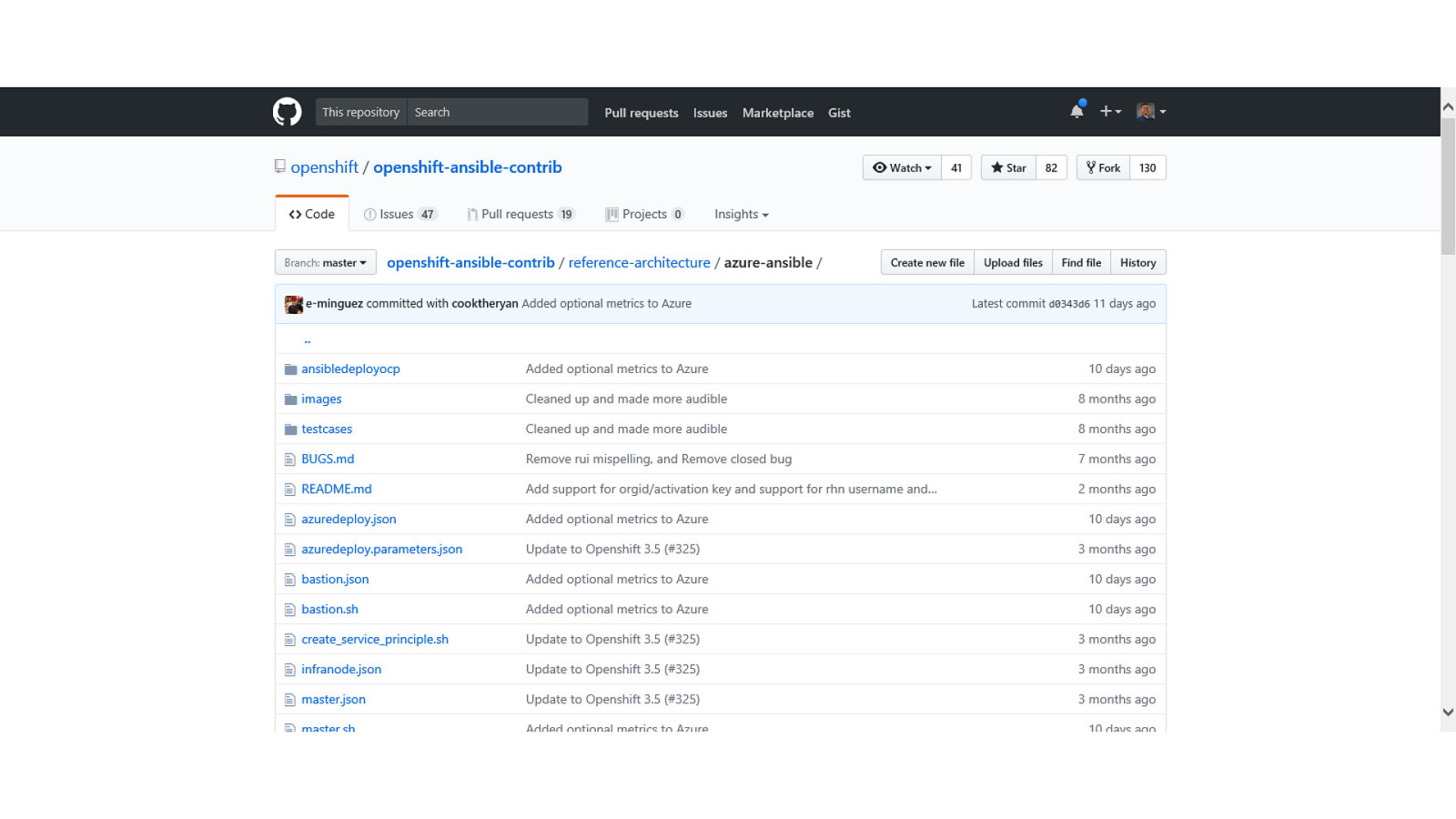
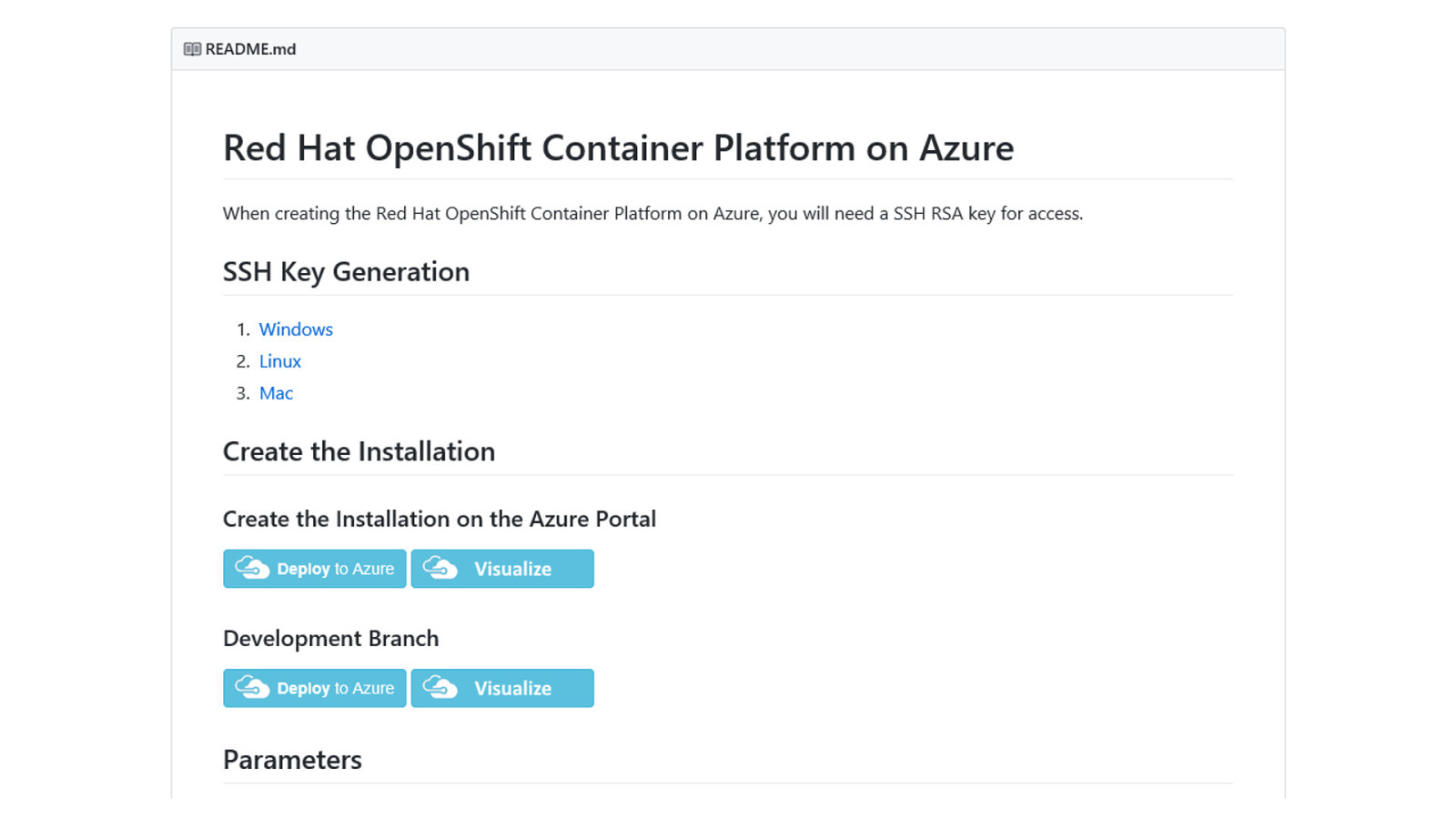
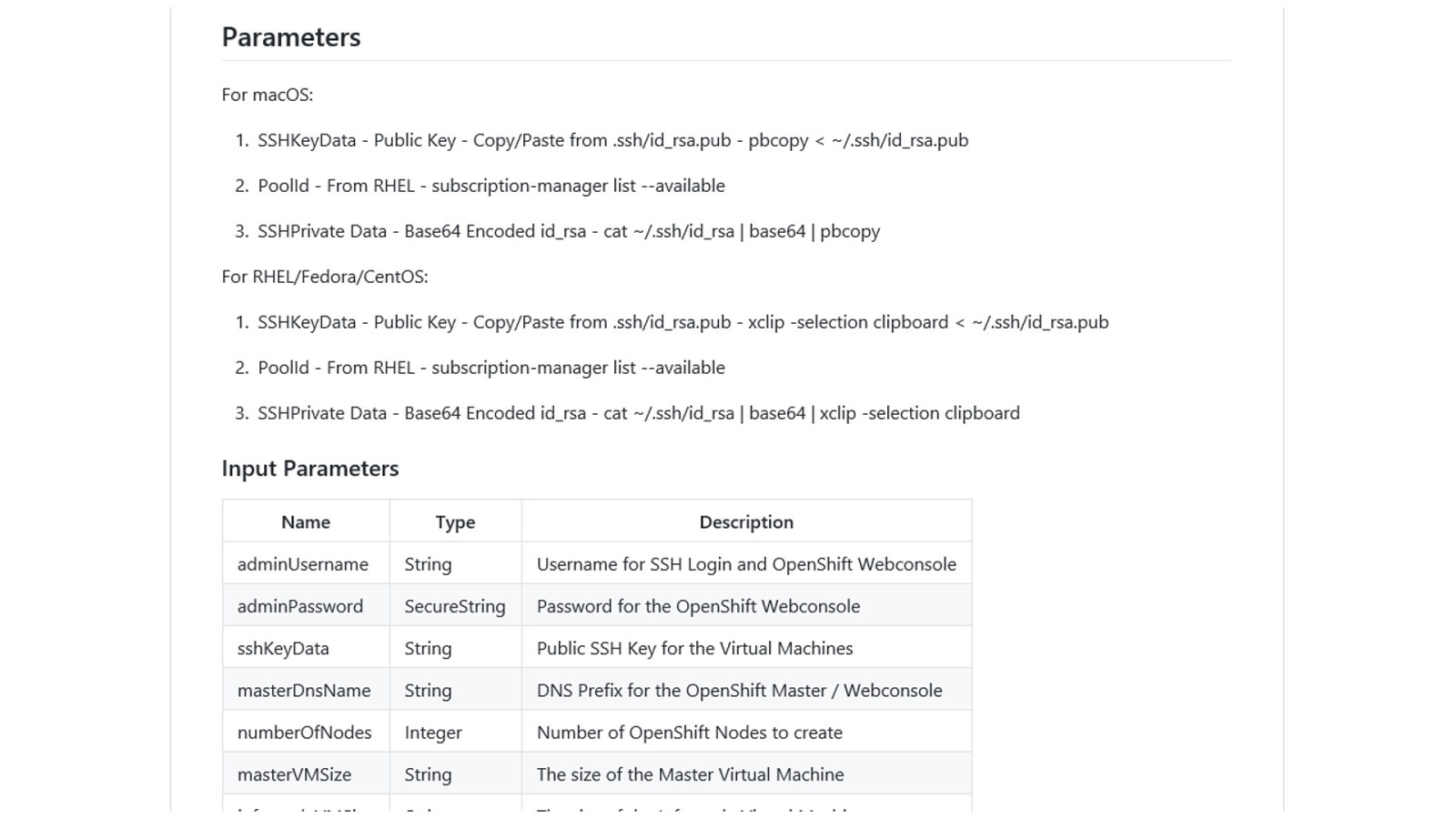
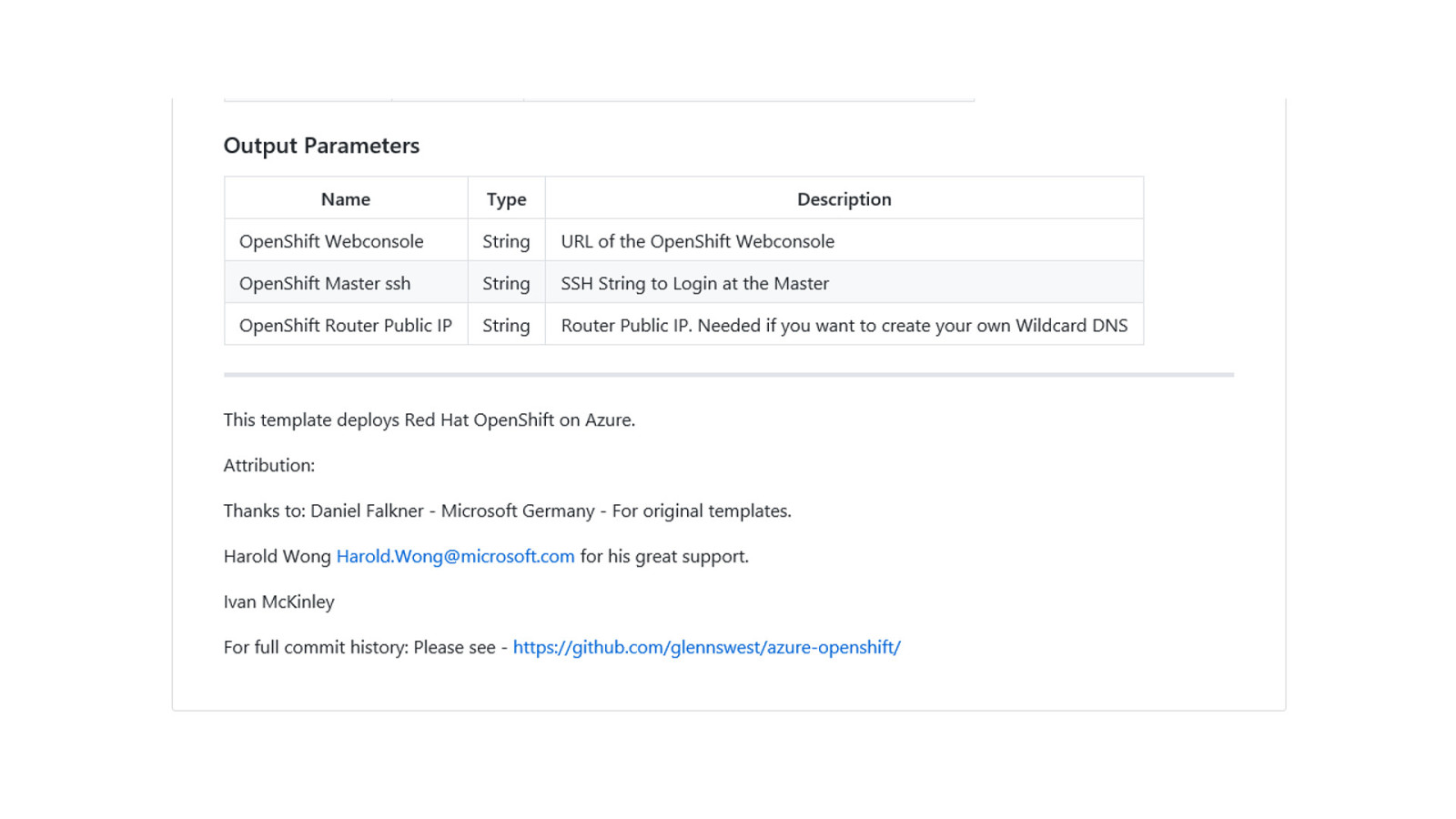
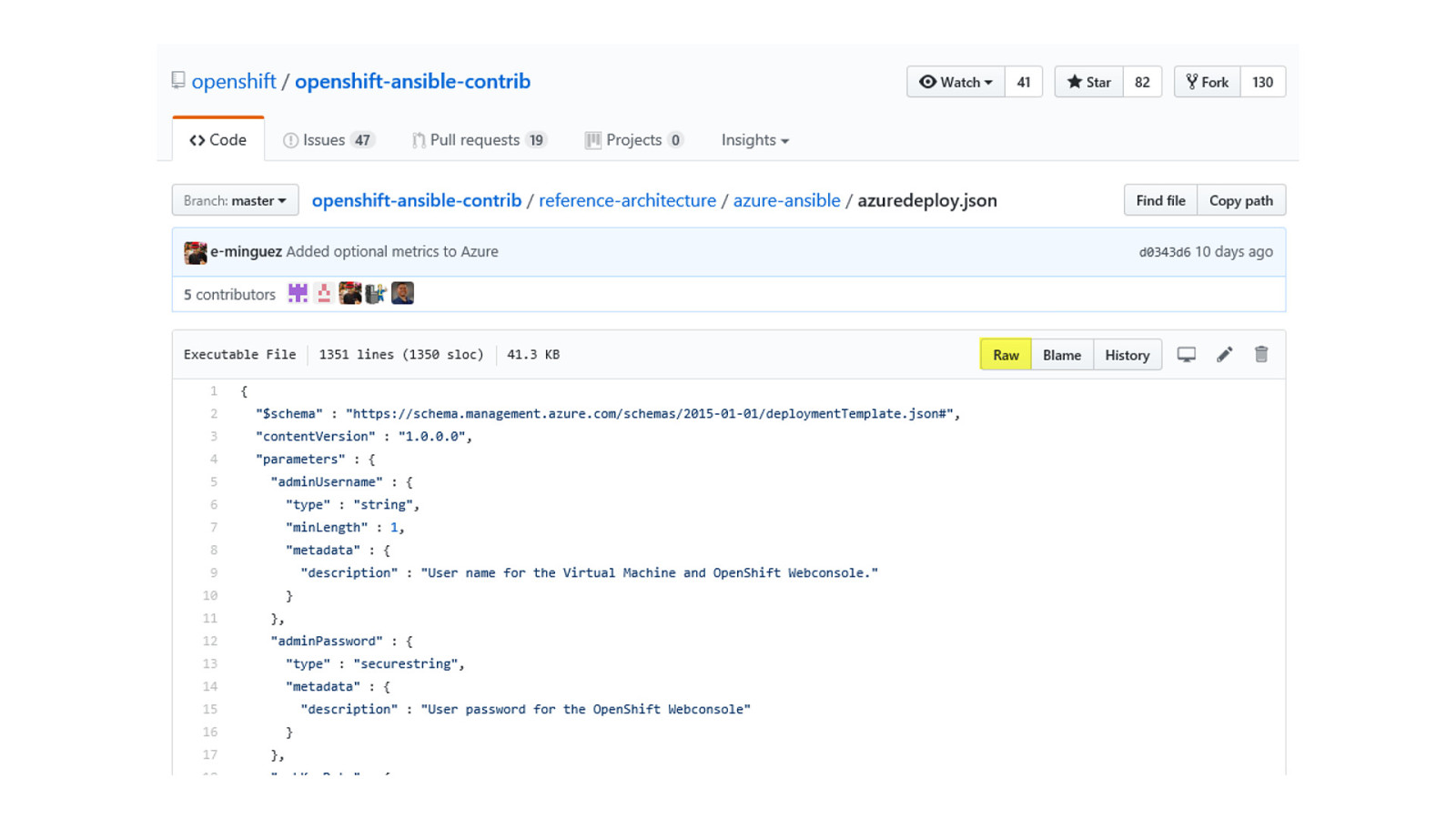
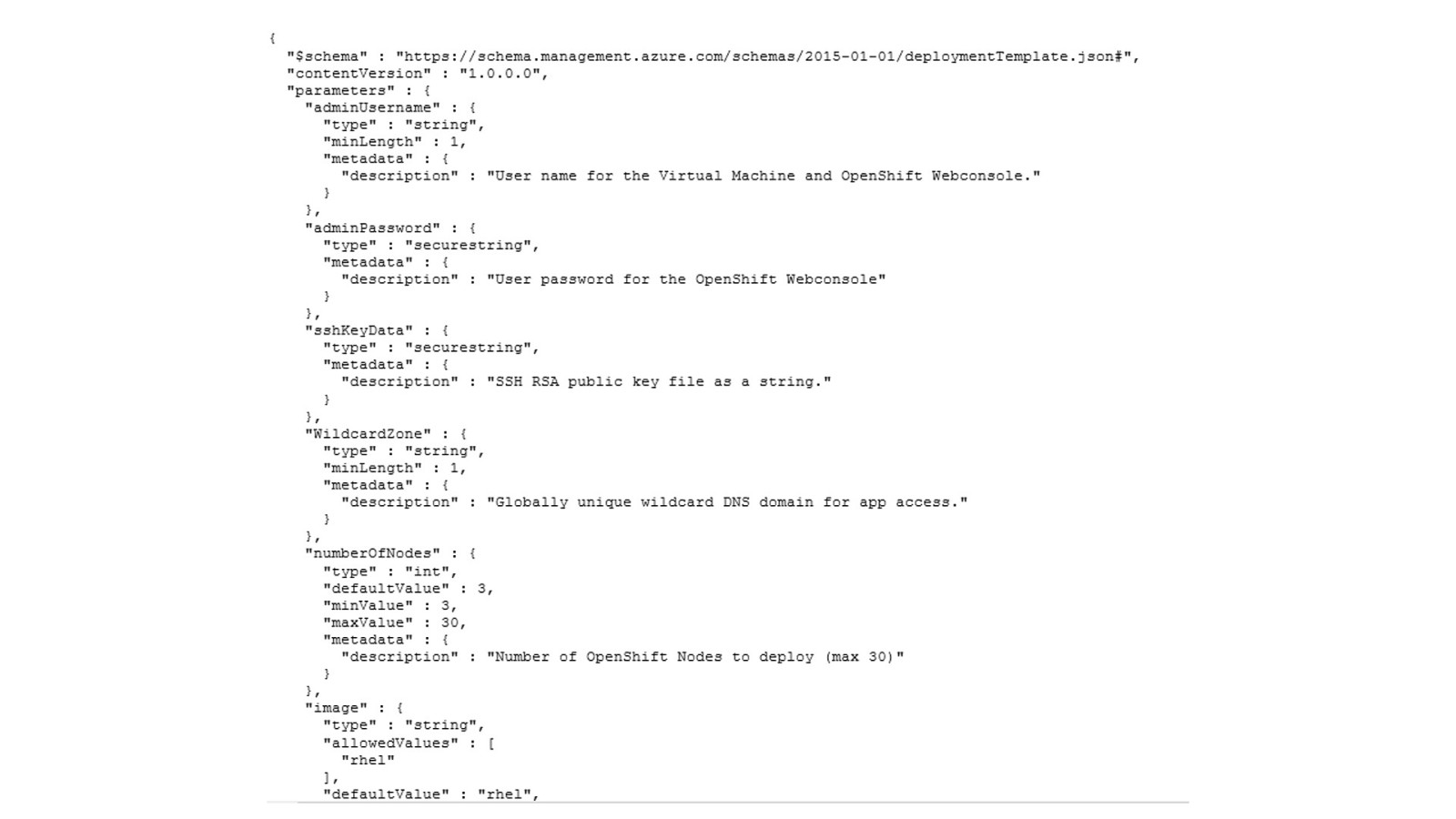
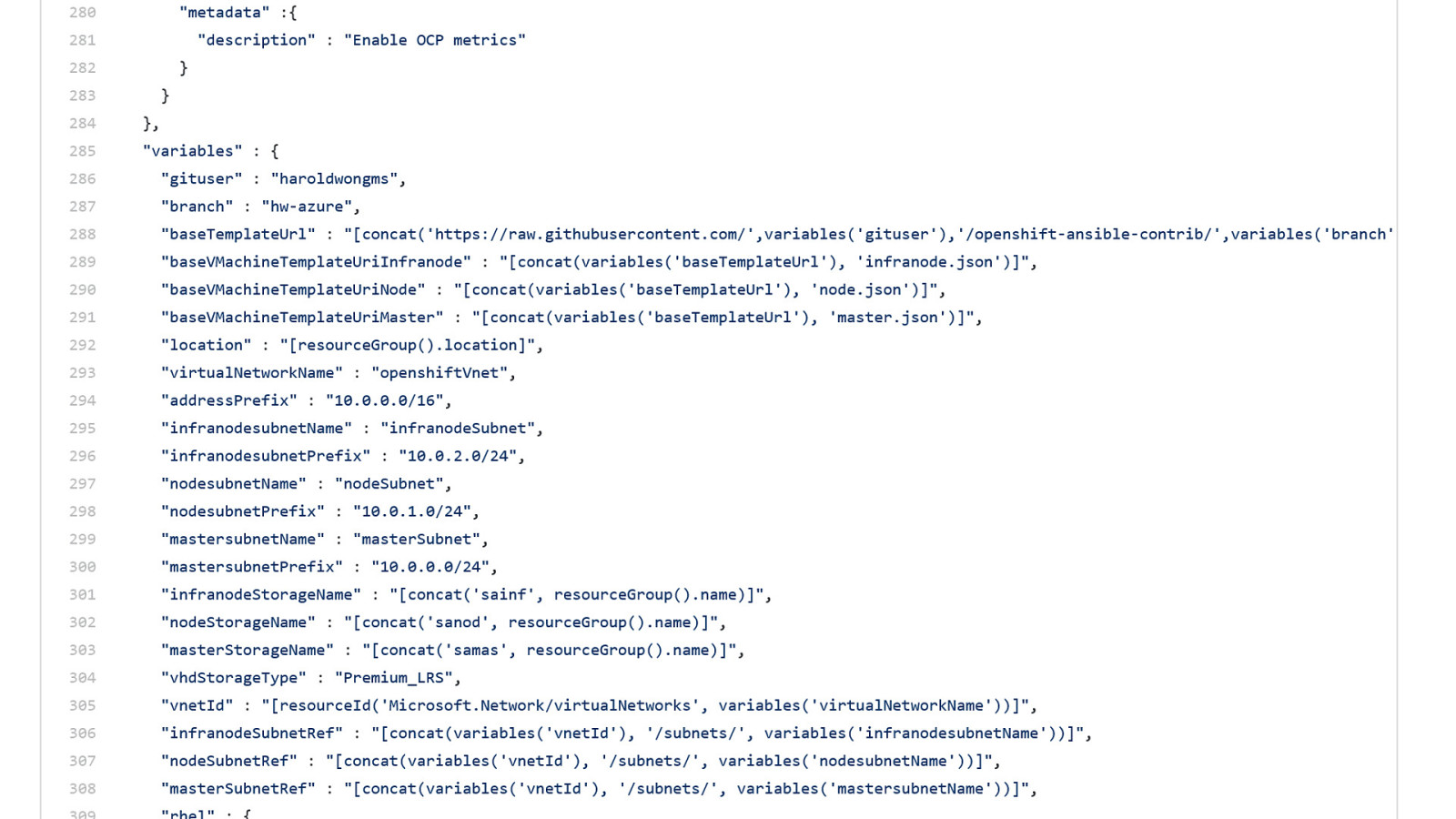
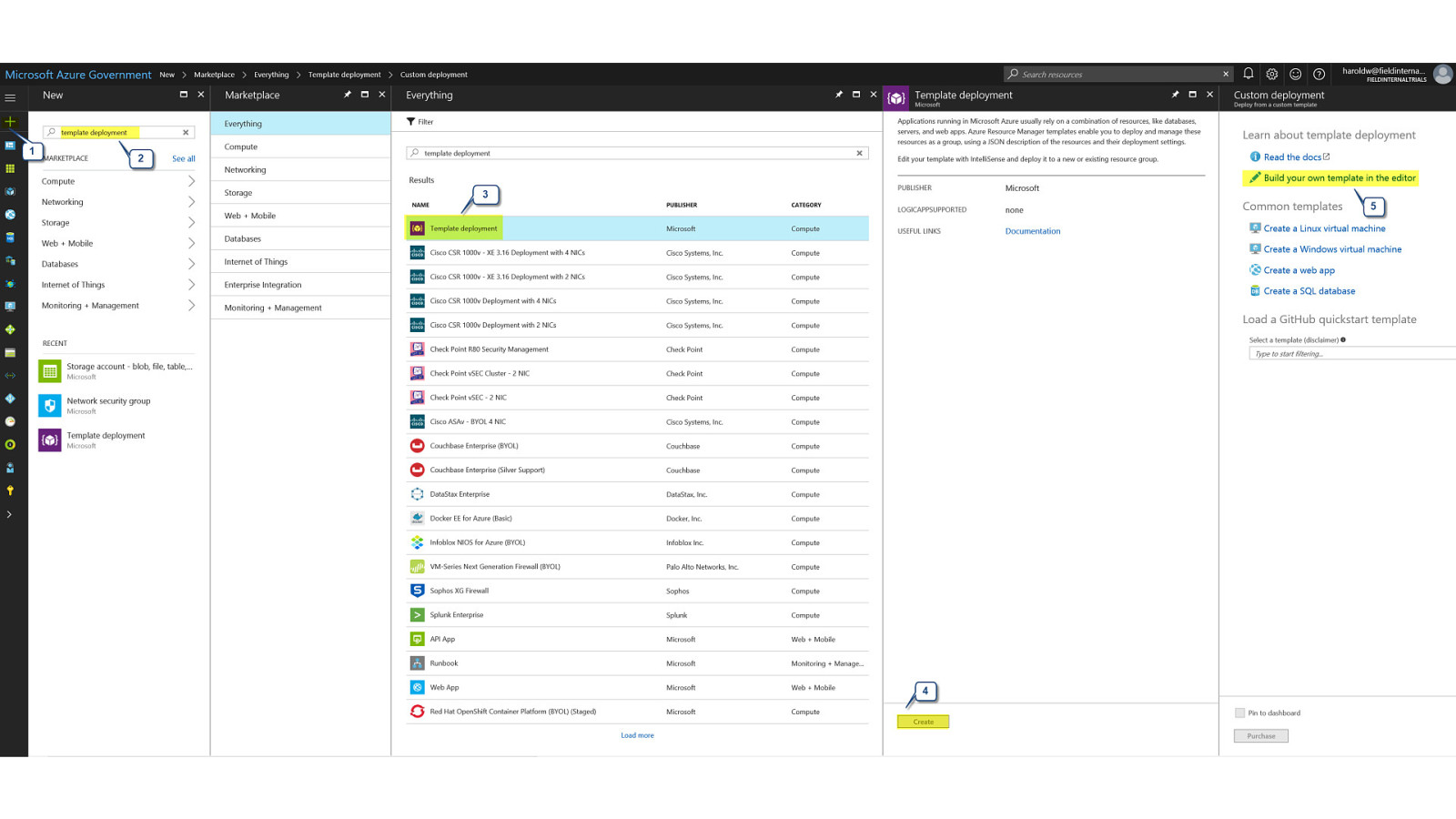
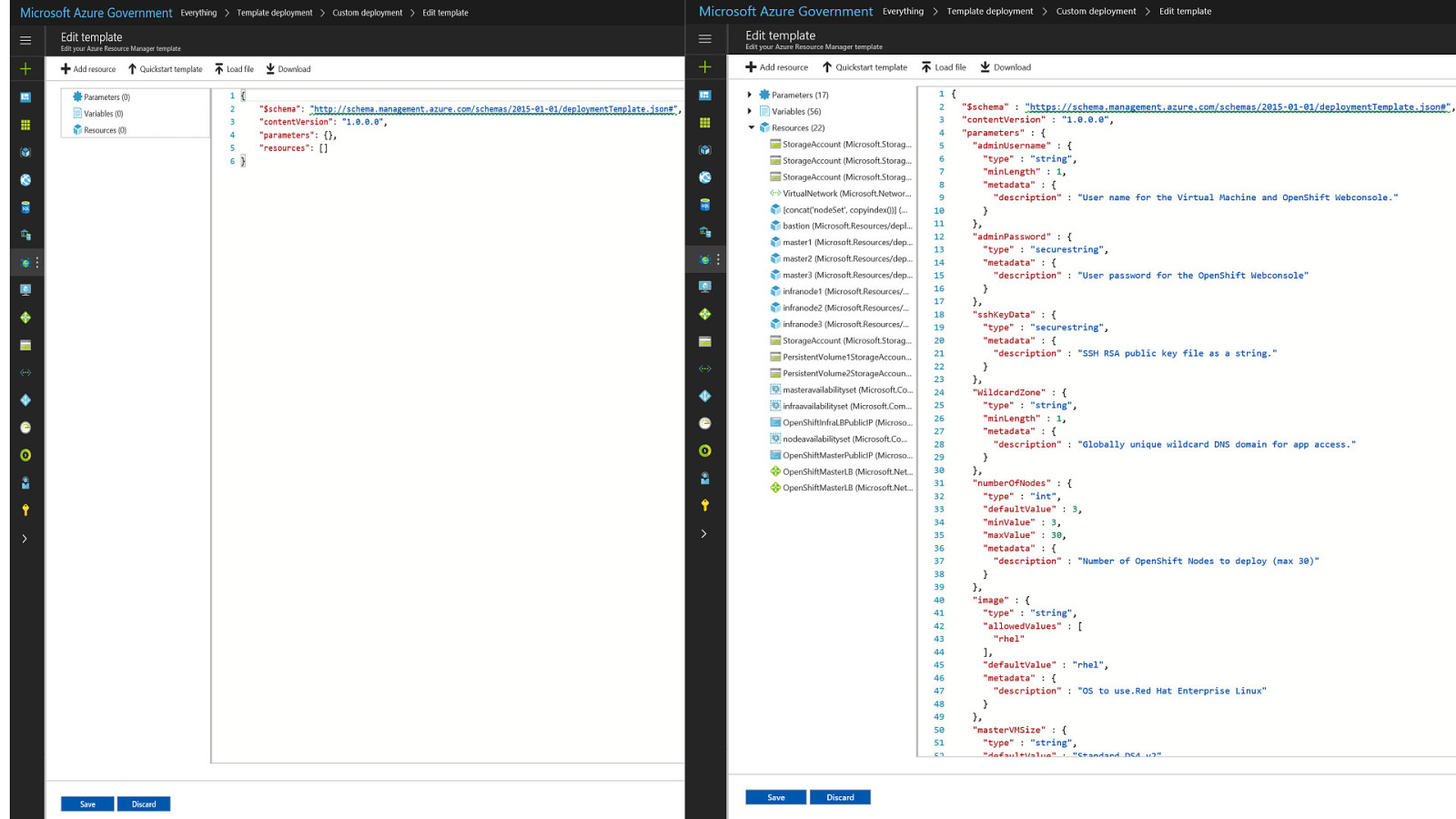
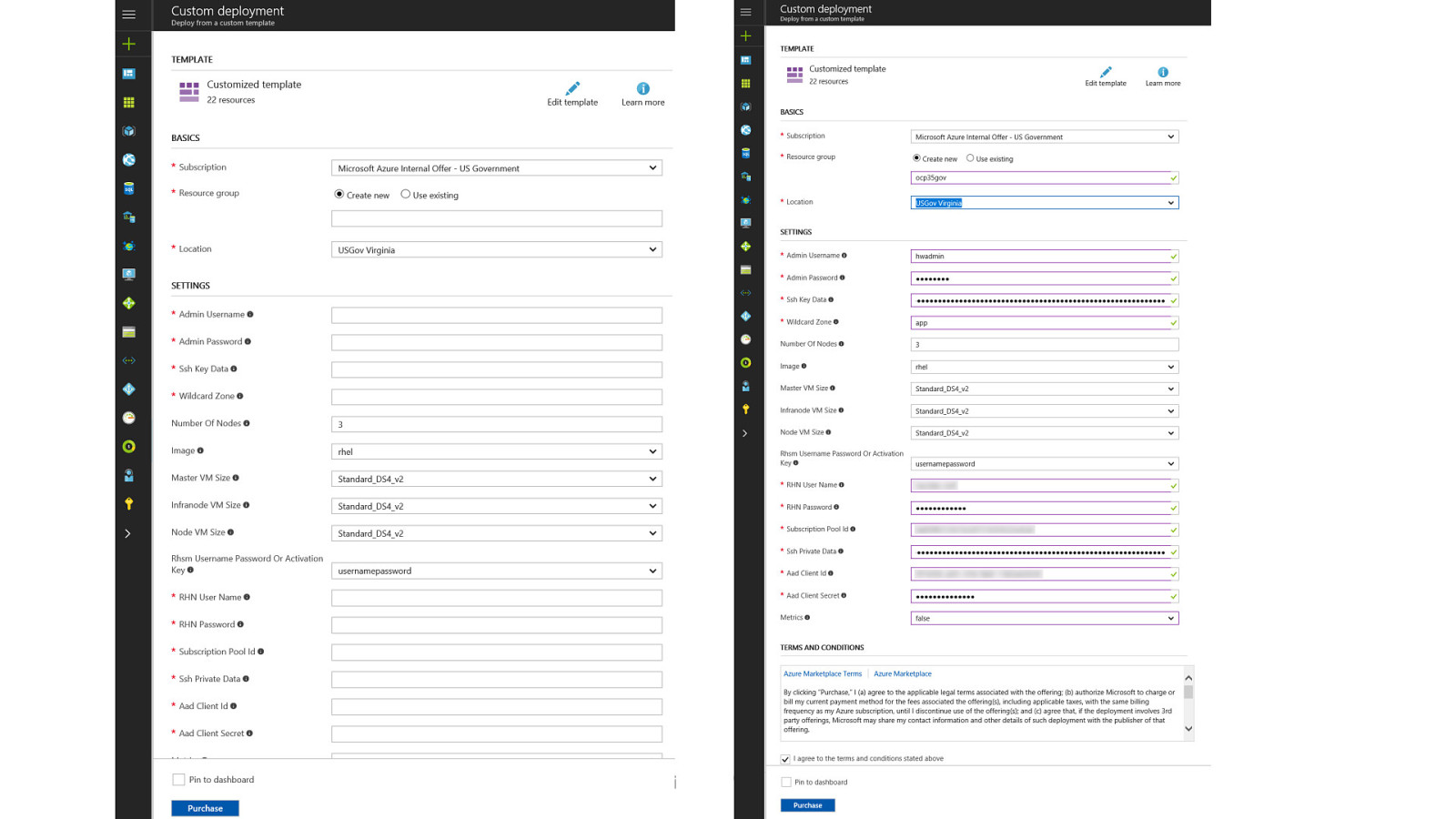
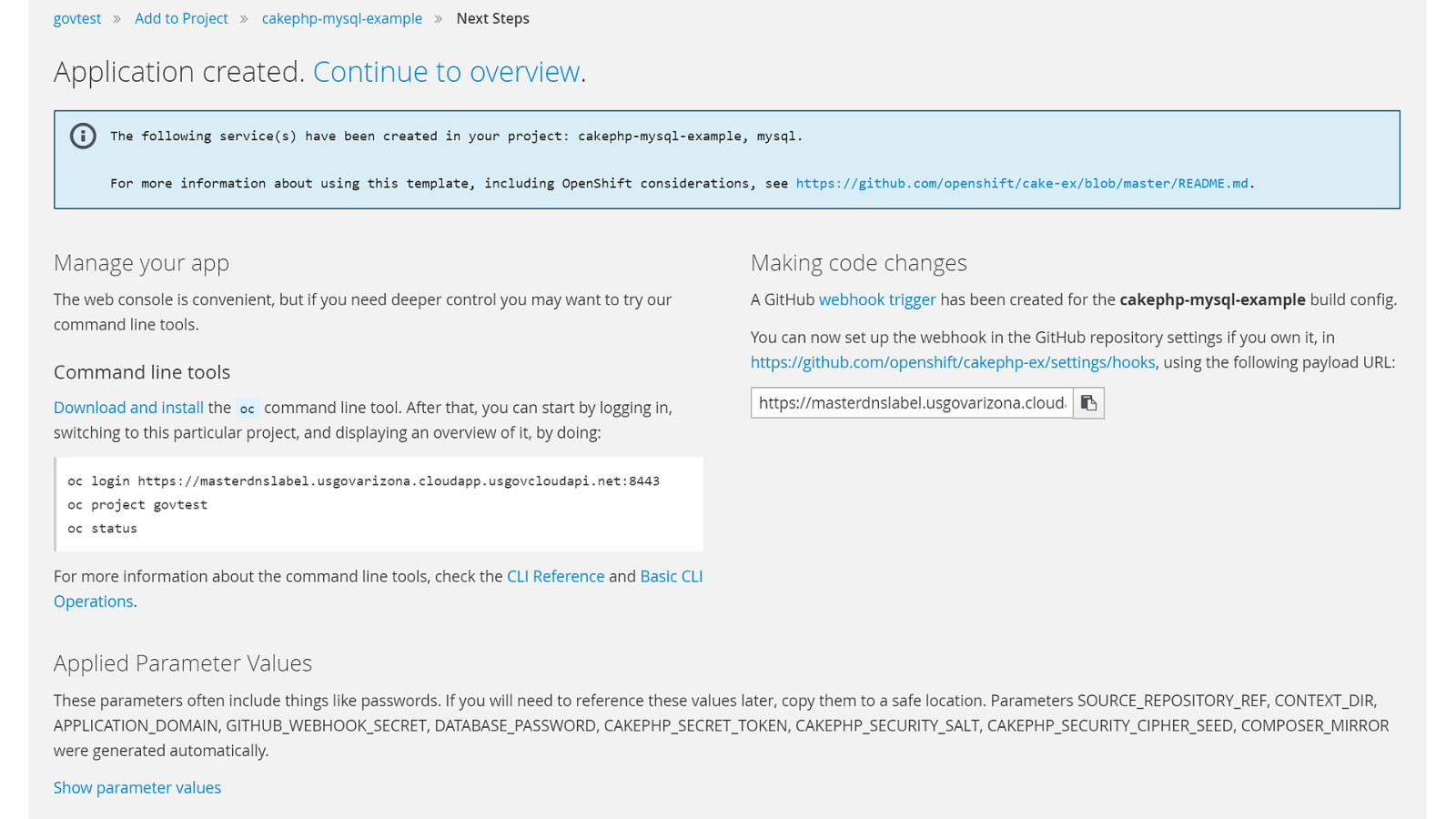
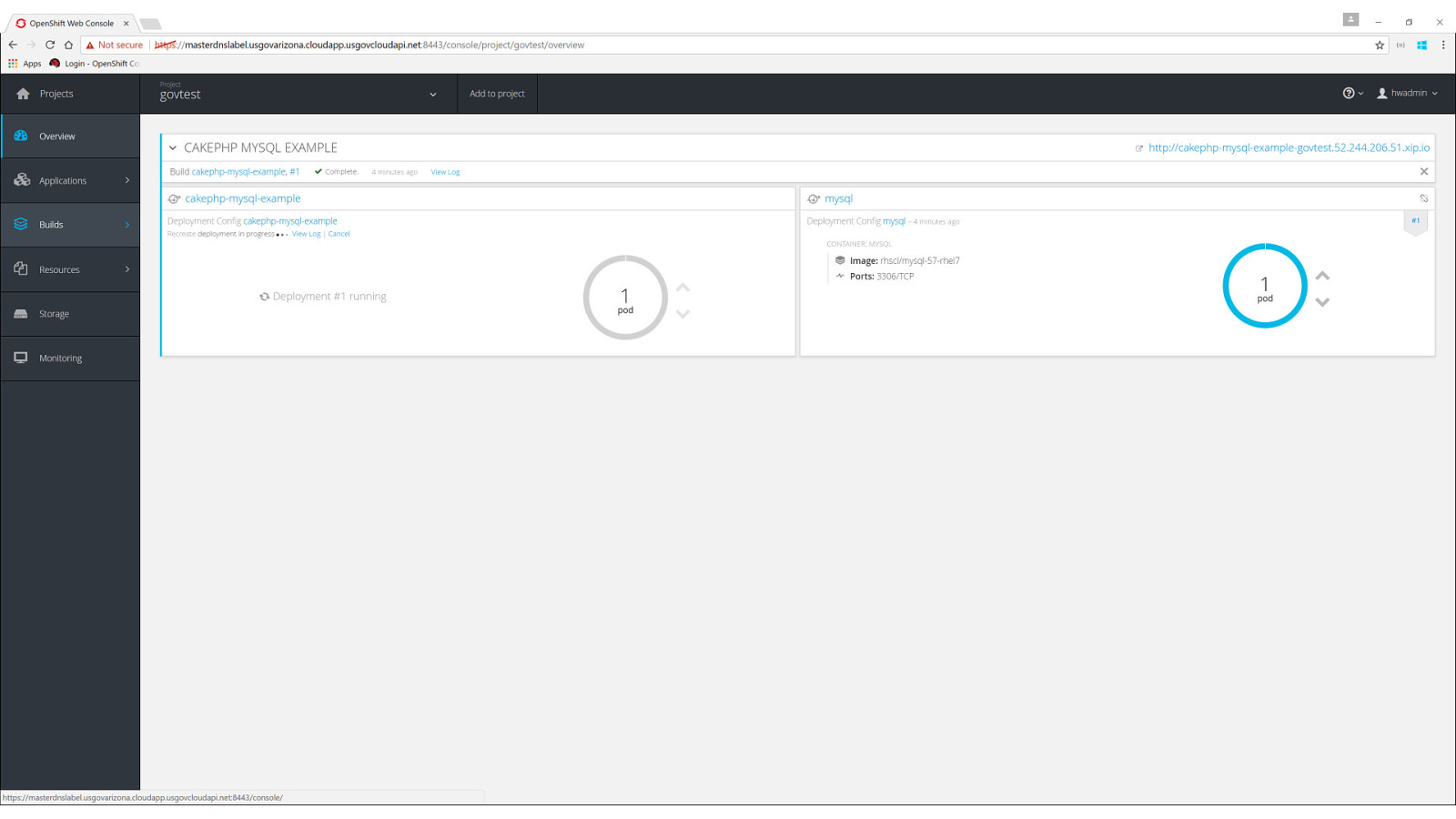
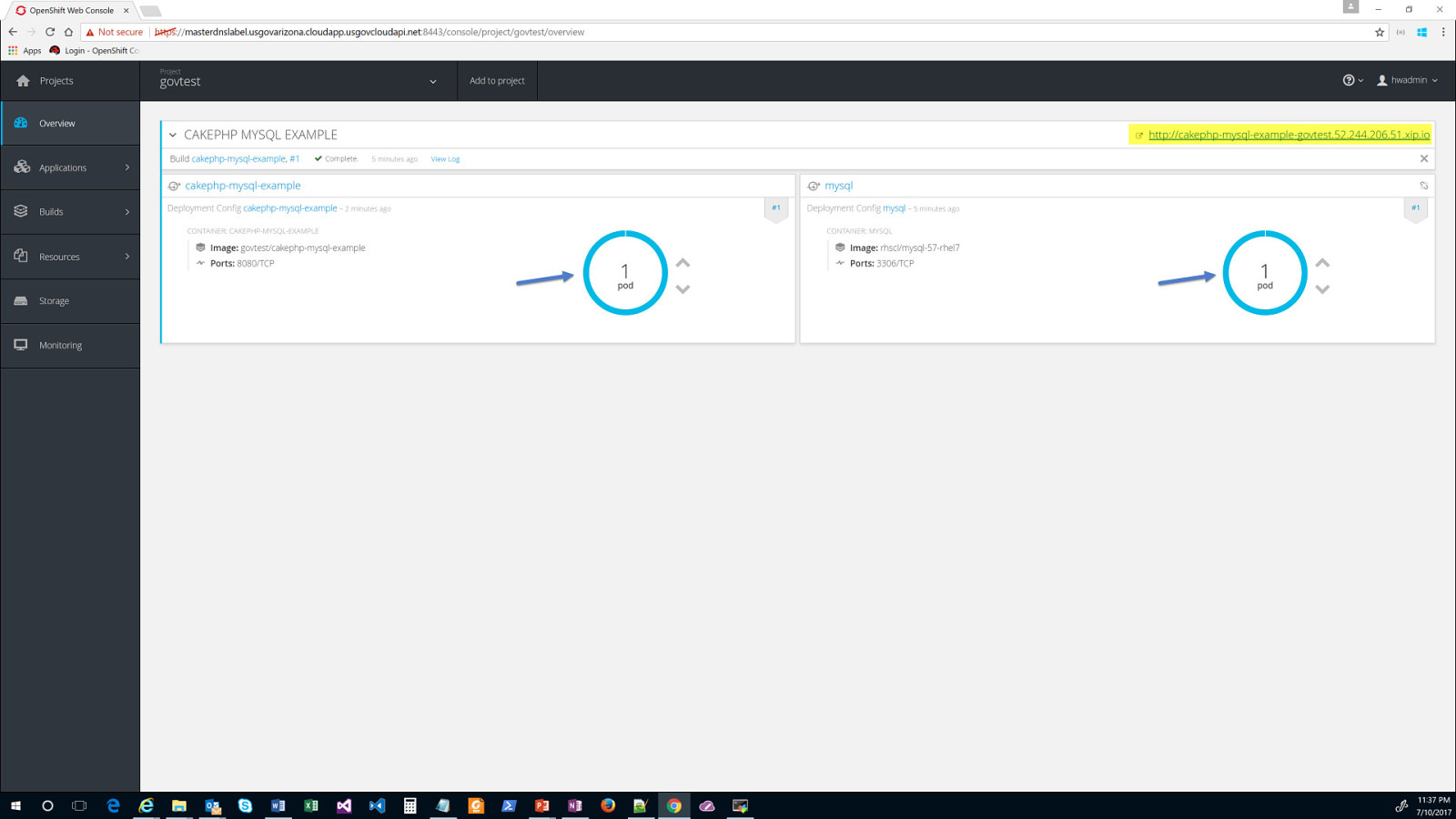
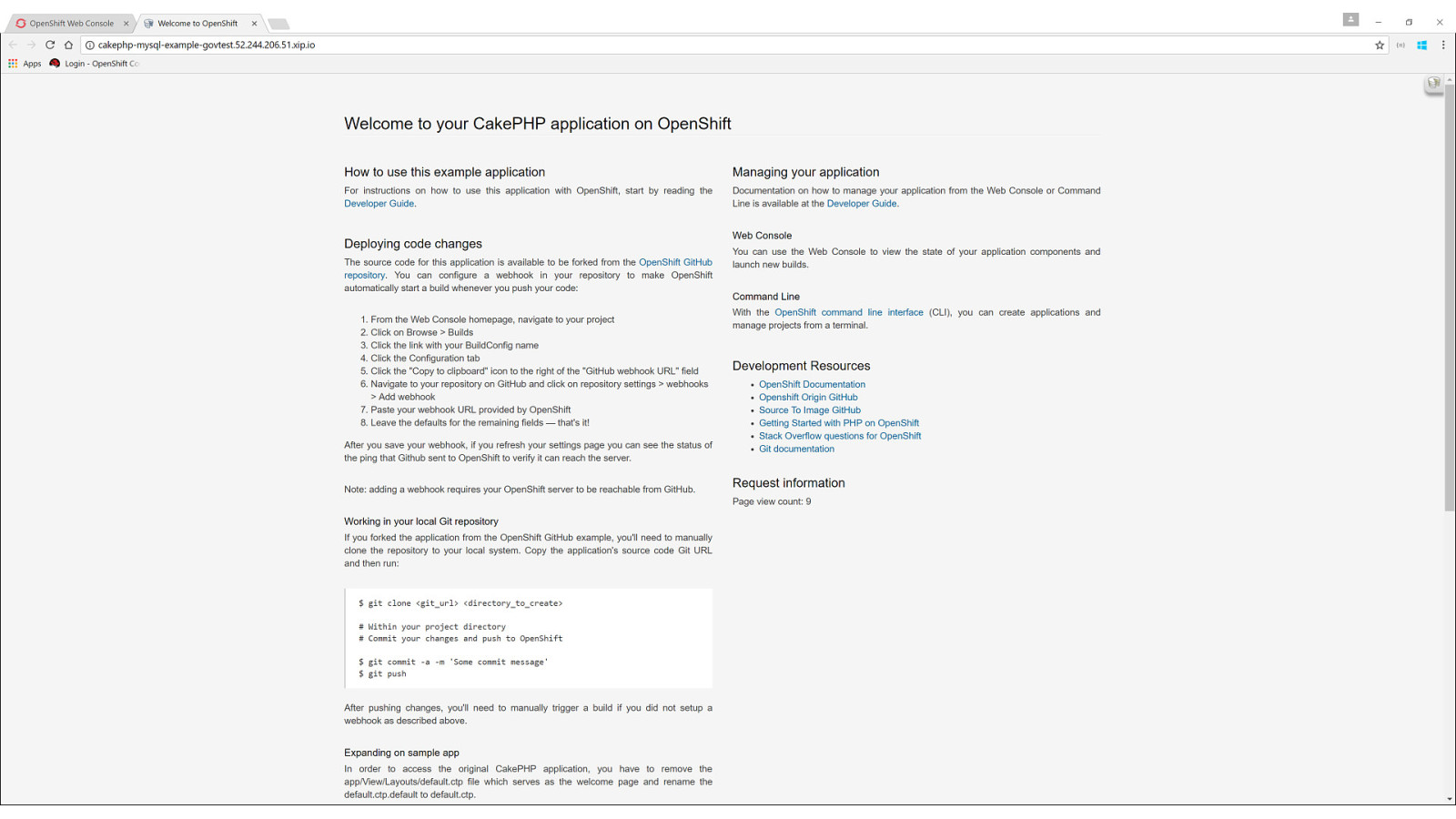
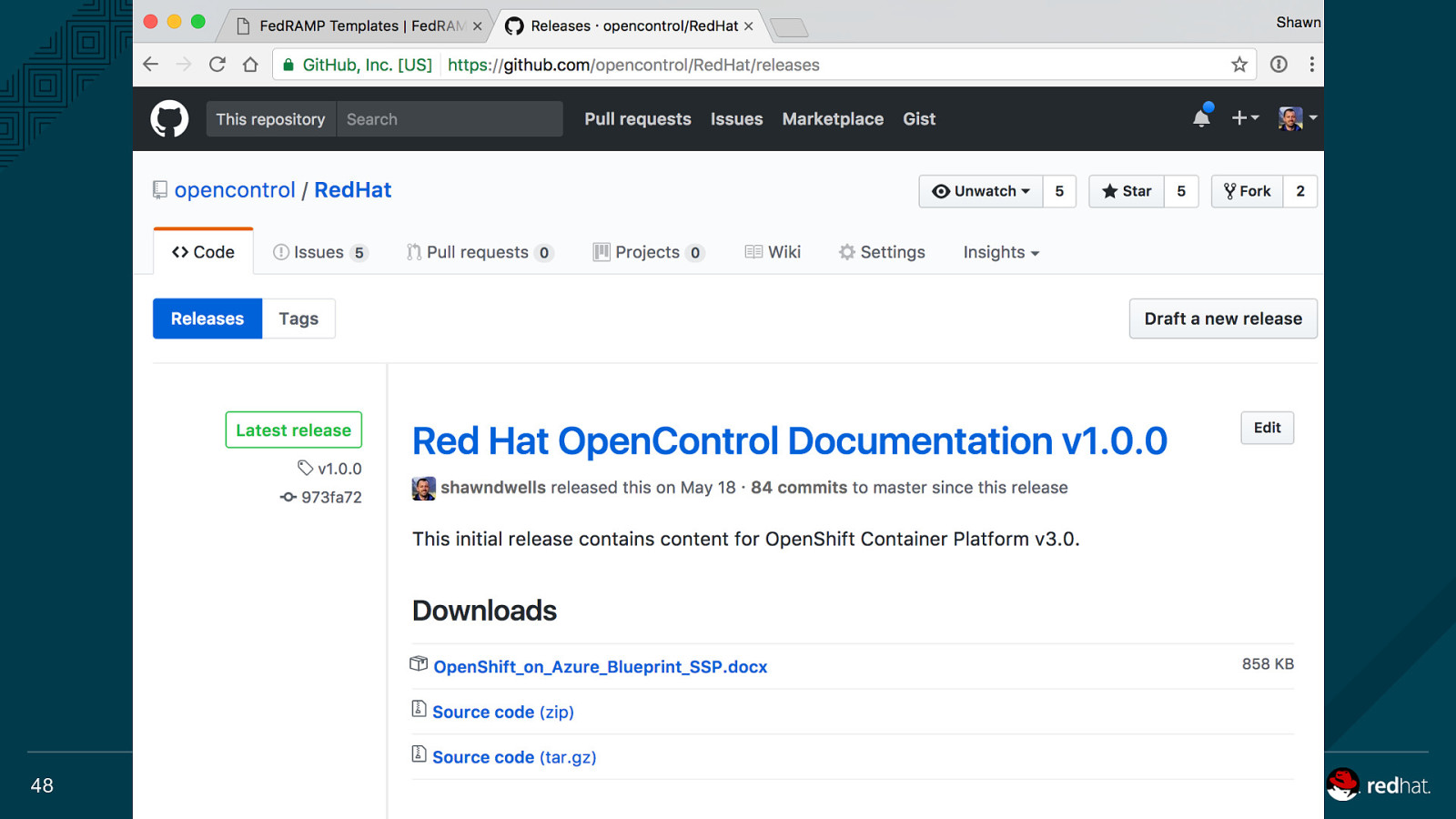
OpenShift on Azure Reference Architecture Provides a comprehensive, stepby-step build of an enterprise deployment of OpenShift v3.5 on Azure. ● Public documentation ● Automation scripts on GitHub 41
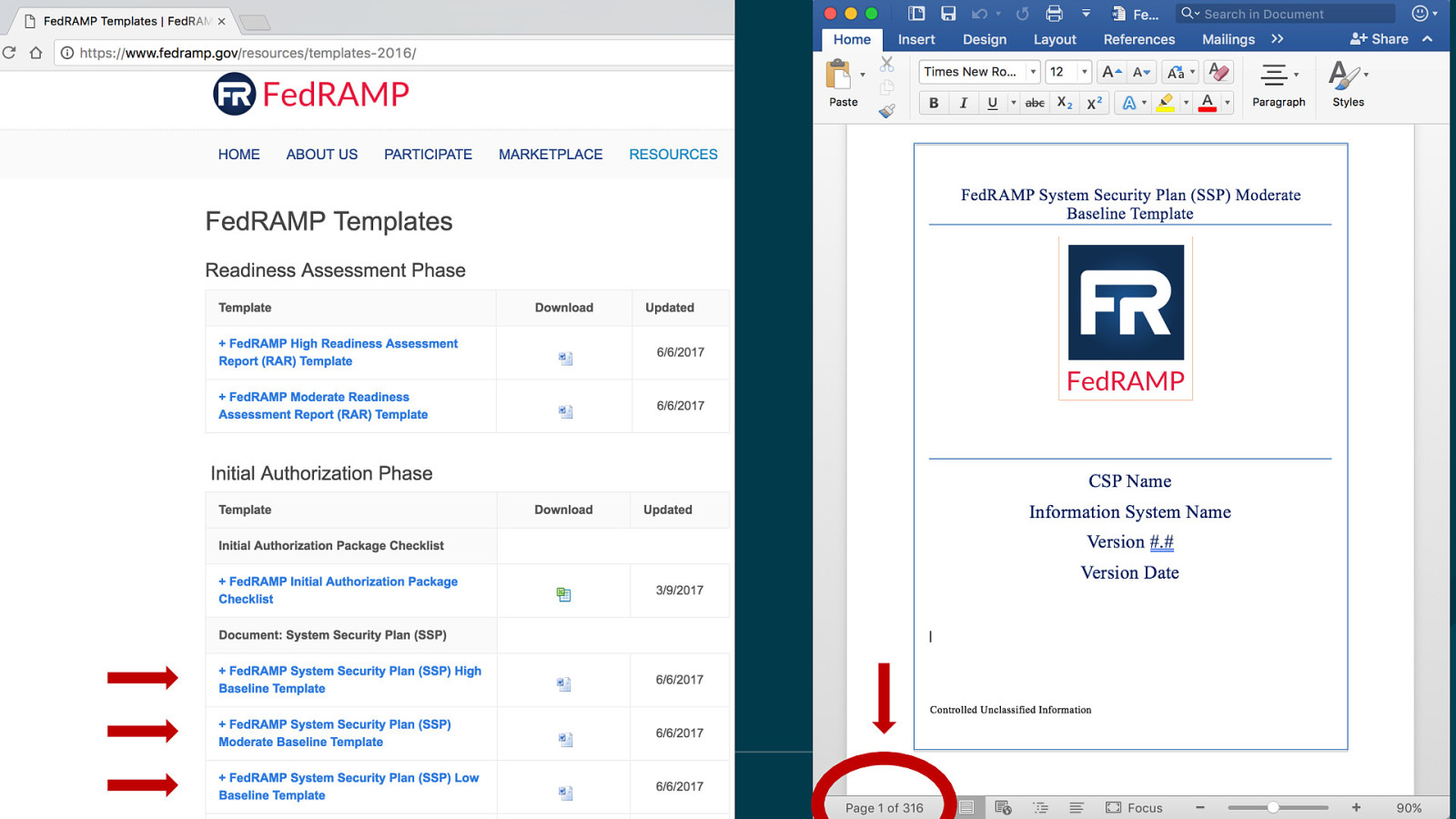
42
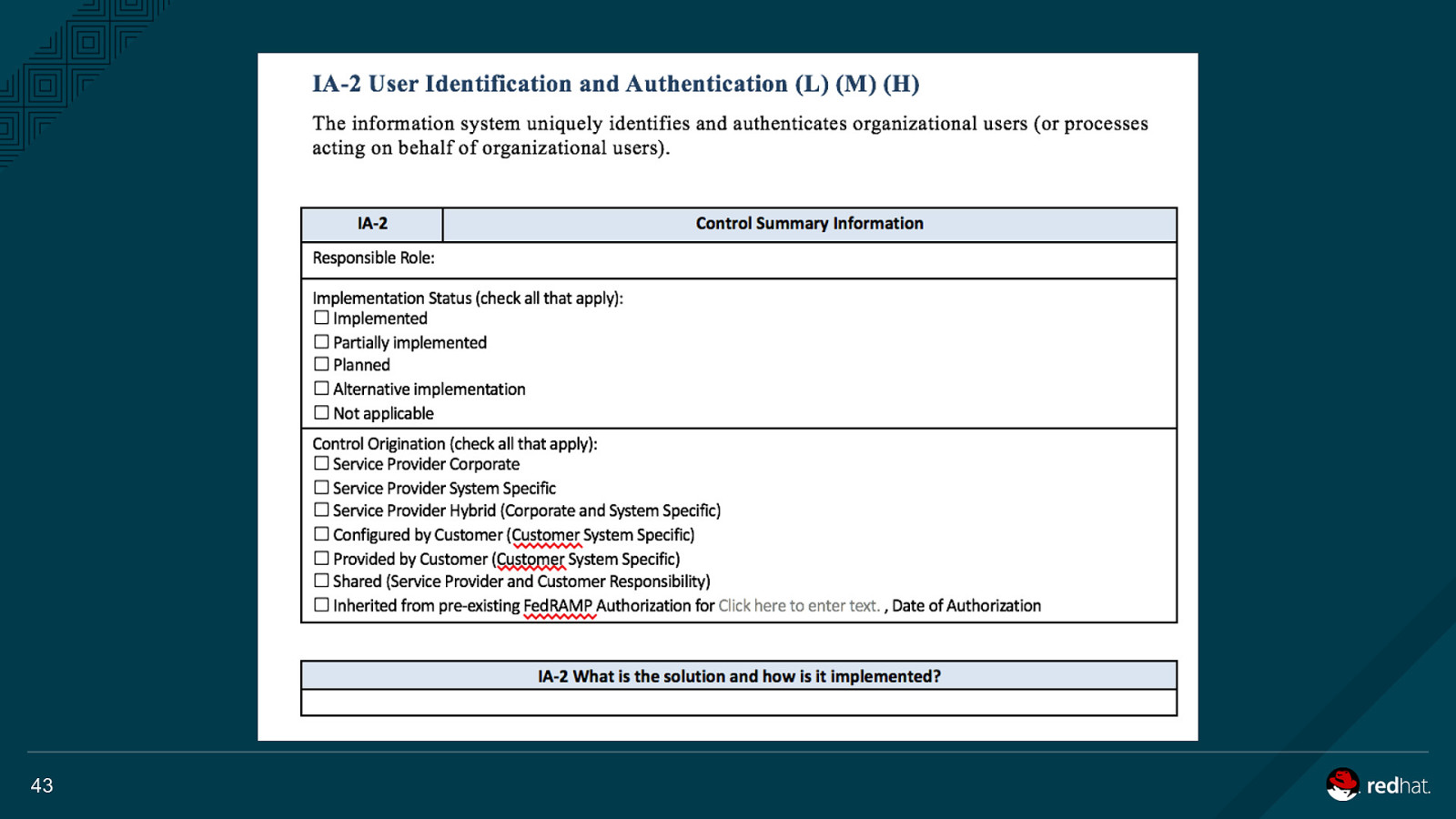
43
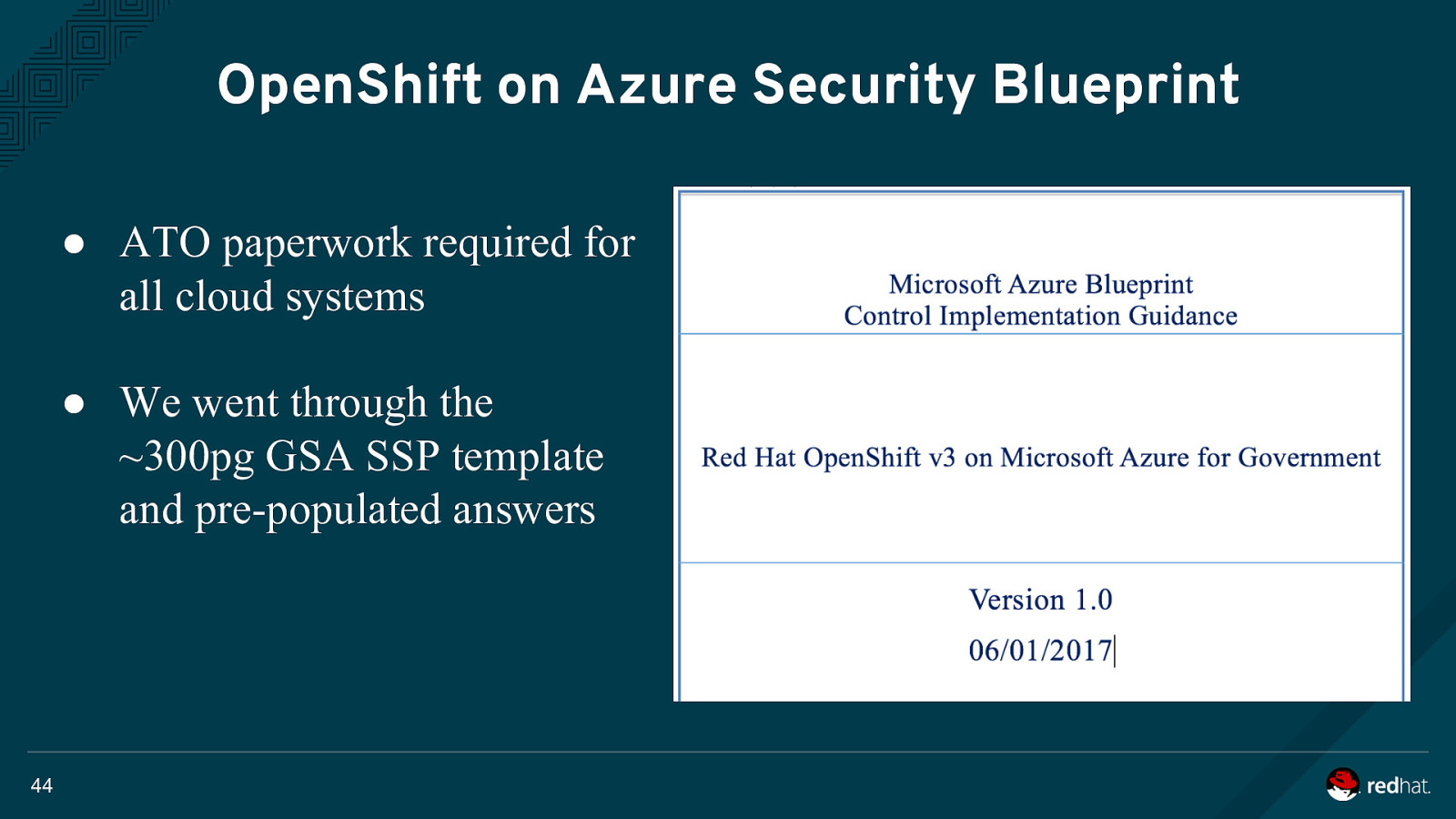
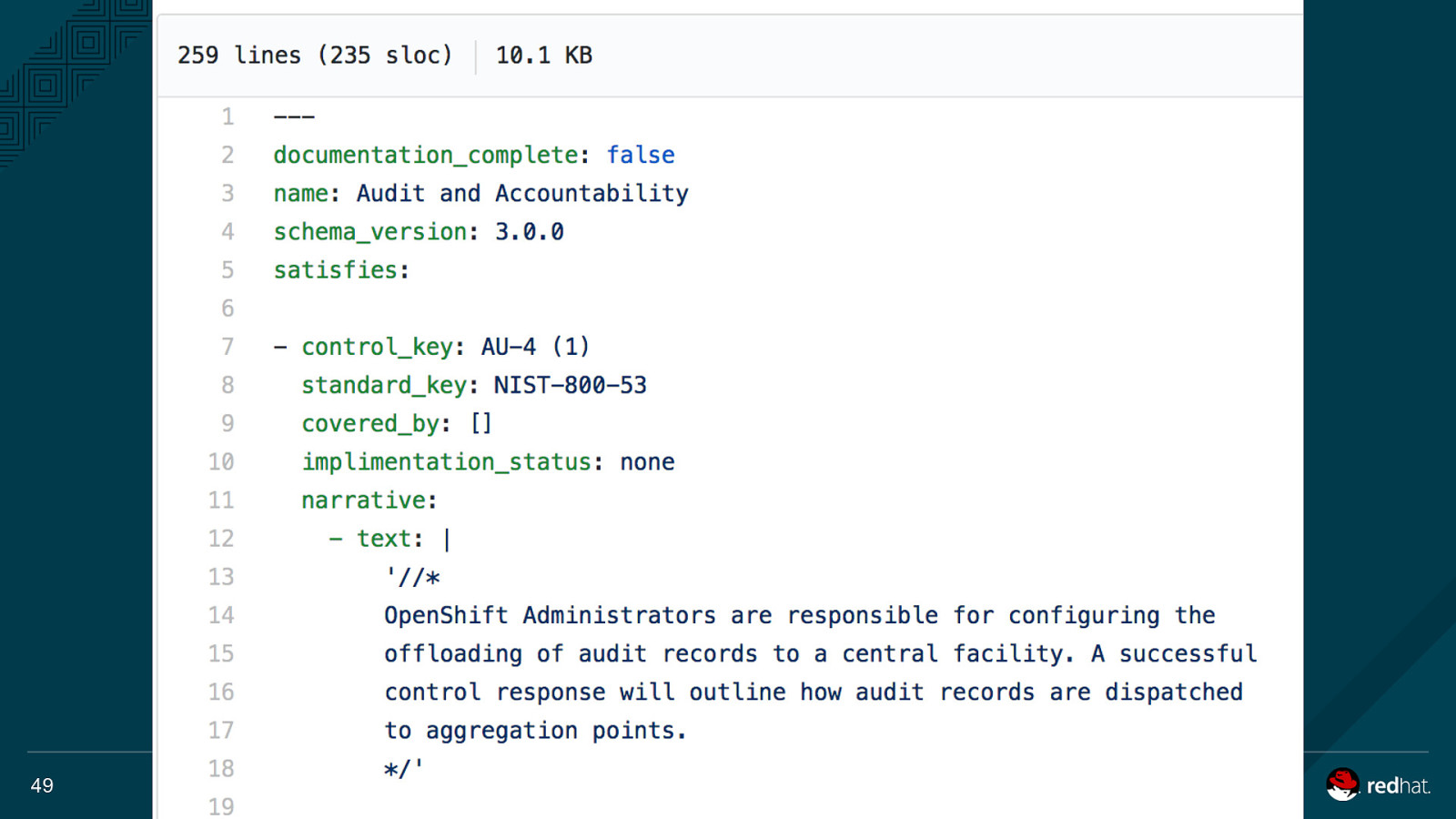
OpenShift on Azure Security Blueprint ● ATO paperwork required for all cloud systems ● We went through the ~300pg GSA SSP template and pre-populated answers 44
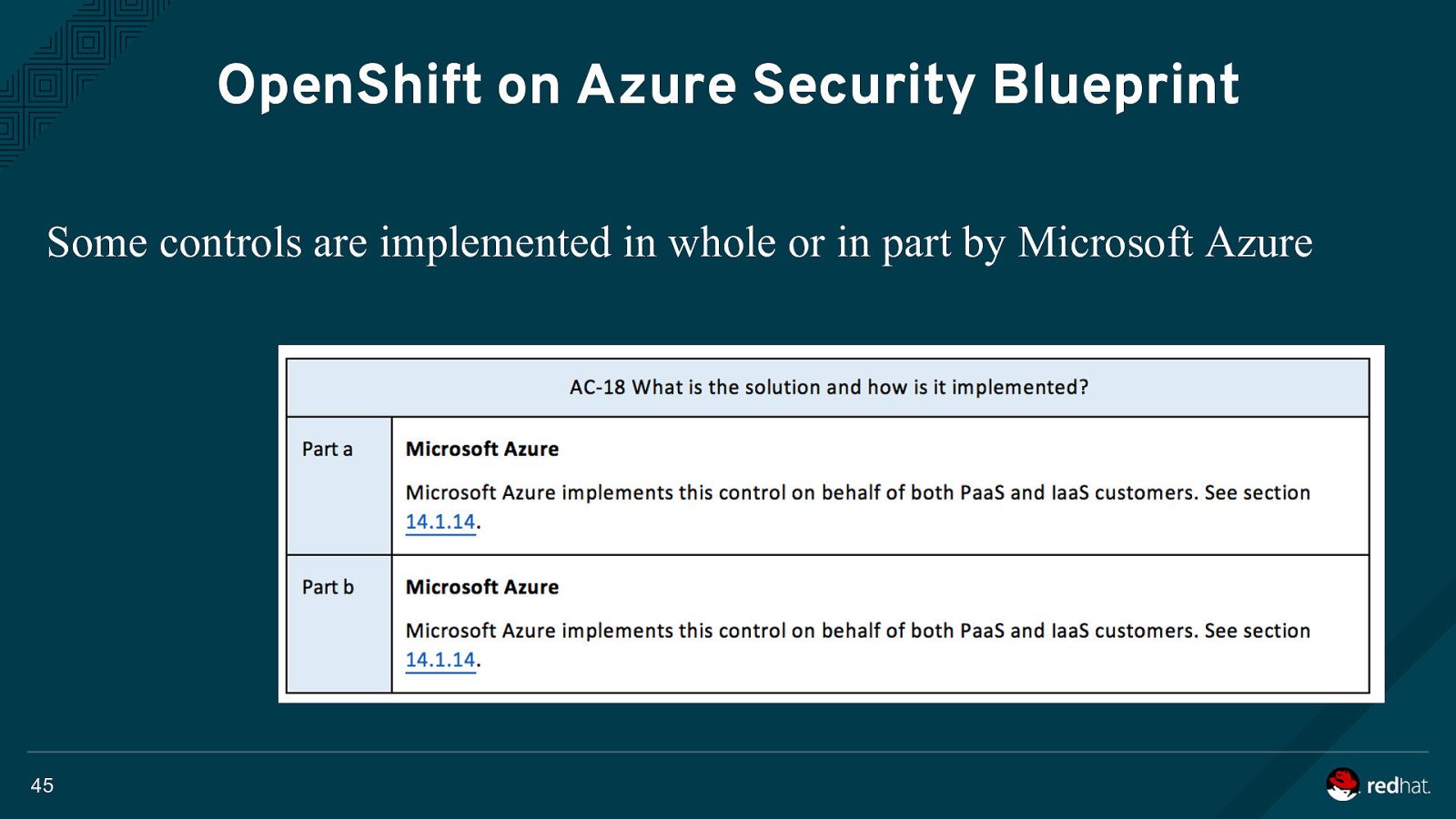
OpenShift on Azure Security Blueprint Some controls are implemented in whole or in part by Microsoft Azure 45
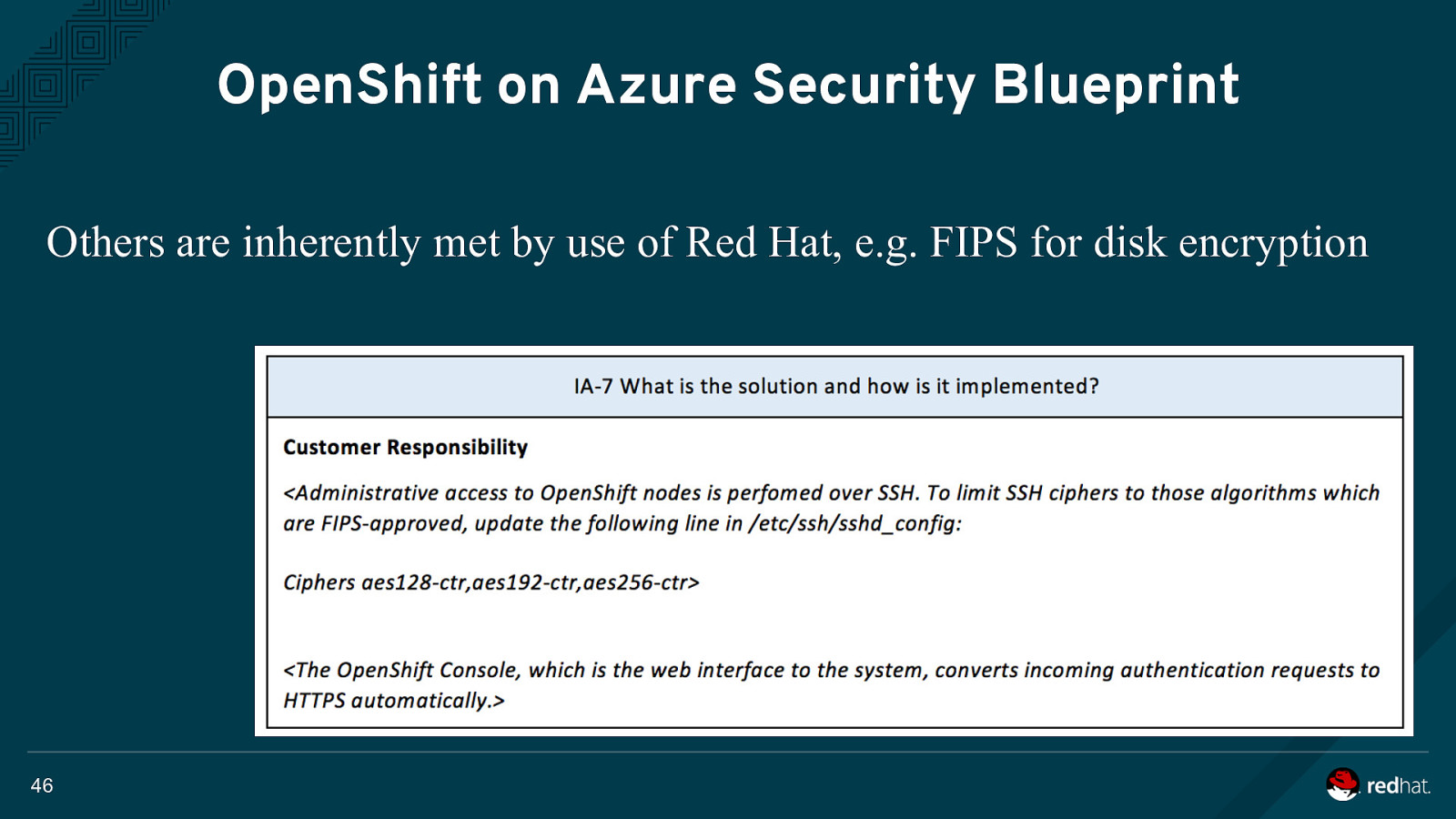
OpenShift on Azure Security Blueprint Others are inherently met by use of Red Hat, e.g. FIPS for disk encryption 46

OpenShift on Azure Security Blueprint For customer responsibilities, we documented what a successful response would be: 47
48
49
click 50

THANK YOU
Building secure environments and ensuring adherence to FedRAMP authorization requirements can be complex and cumbersome. Red Hat’s OpenShift Container Platform provides a secure, government-ready platform for containers and DevOps.
In GovLoop’s Gov Security in a Digital World Virtual Summit, Harold Wong, Cloud Architect at Microsoft and Shawn Wells, Chief Security Strategist in Red Hat’s Public Sector, teamed up to provide architectural guidance on deploying Red Hat OpenShift Container Platform in Azure Government, which is a hybrid cloud solution.
GovLoop landing site: https://www.govloop.com/changing-open-hybrid-cloud-game/
