OpenShift Security
A presentation at Worldwide Technology (WWT) Security Day in in Denver, CO, USA by Shawn Wells

OpenShift Security SHAWN WELLS Chief Information Security Officer U.S. Public Sector unclass: shawn@redhat.com JWICS: sdwell2@nsa.ic.gov (+1) 443-534-0130 UNCLASSIFIED 1

45 MINUTES, 3 GOALS 1. Review OpenShift Security Framework • sVirt • MCS & Type Enforcement 2. 3. 2

45 MINUTES, 3 GOALS 1. Review OpenShift Security Framework • sVirt • MCS & Type Enforcement 2. Review compliance tech + initiatives • Upstream: SCAP Security Guide (SSG) • Downstream: NSA SNAC Guides & STIGs 3. 3

45 MINUTES, 3 GOALS 1. Review OpenShift Security Framework • sVirt • MCS & Type Enforcement 2. Review compliance tech + initiatives • Upstream: SCAP Security Guide (SSG) • Downstream: NSA SNAC Guides & STIGs 3. SCAP Demo • OpenSCAP + SSG • C&A Document Generation 4
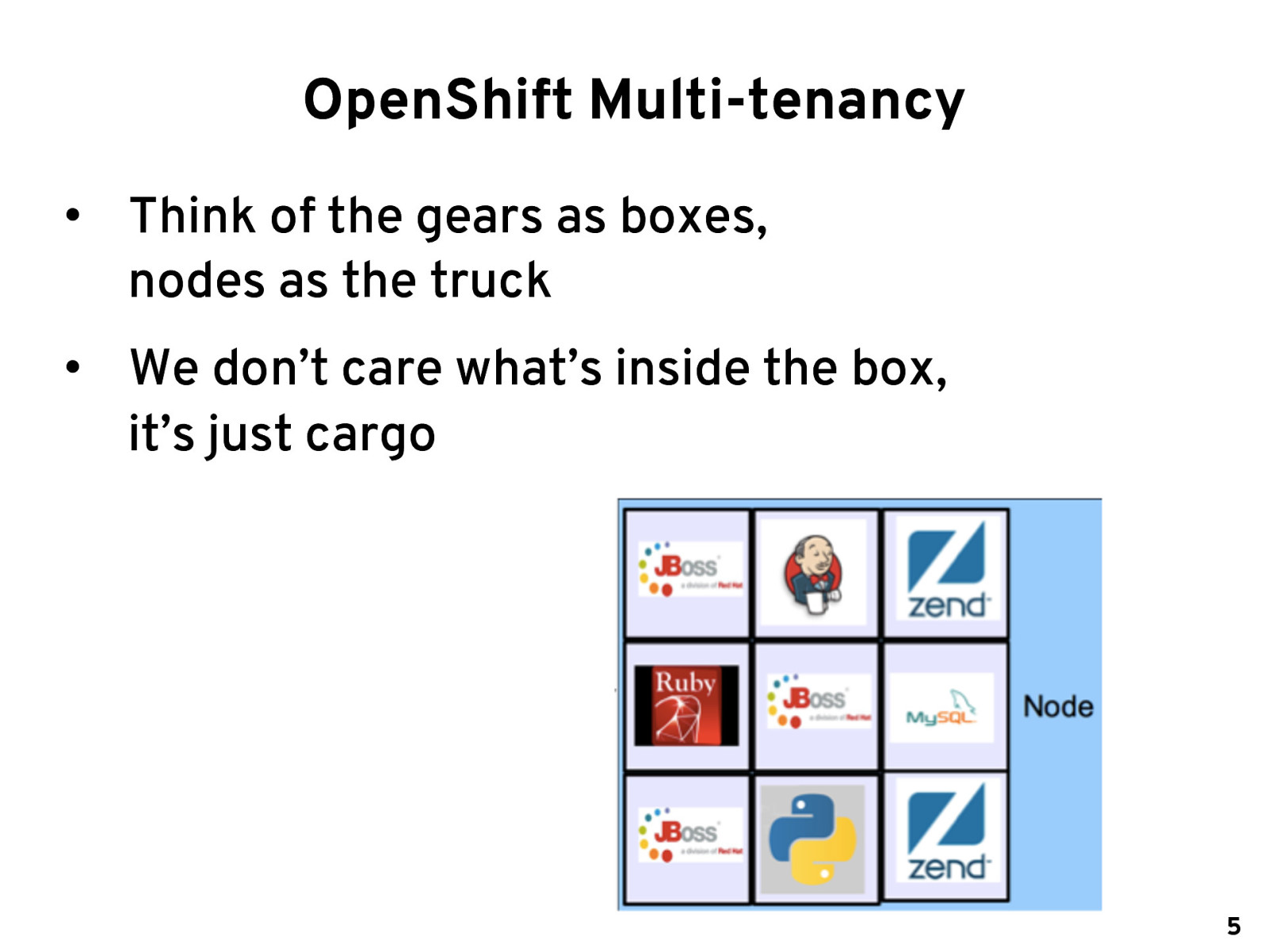
OpenShift Multi-tenancy • Think of the gears as boxes, nodes as the truck • We don’t care what’s inside the box, it’s just cargo 5
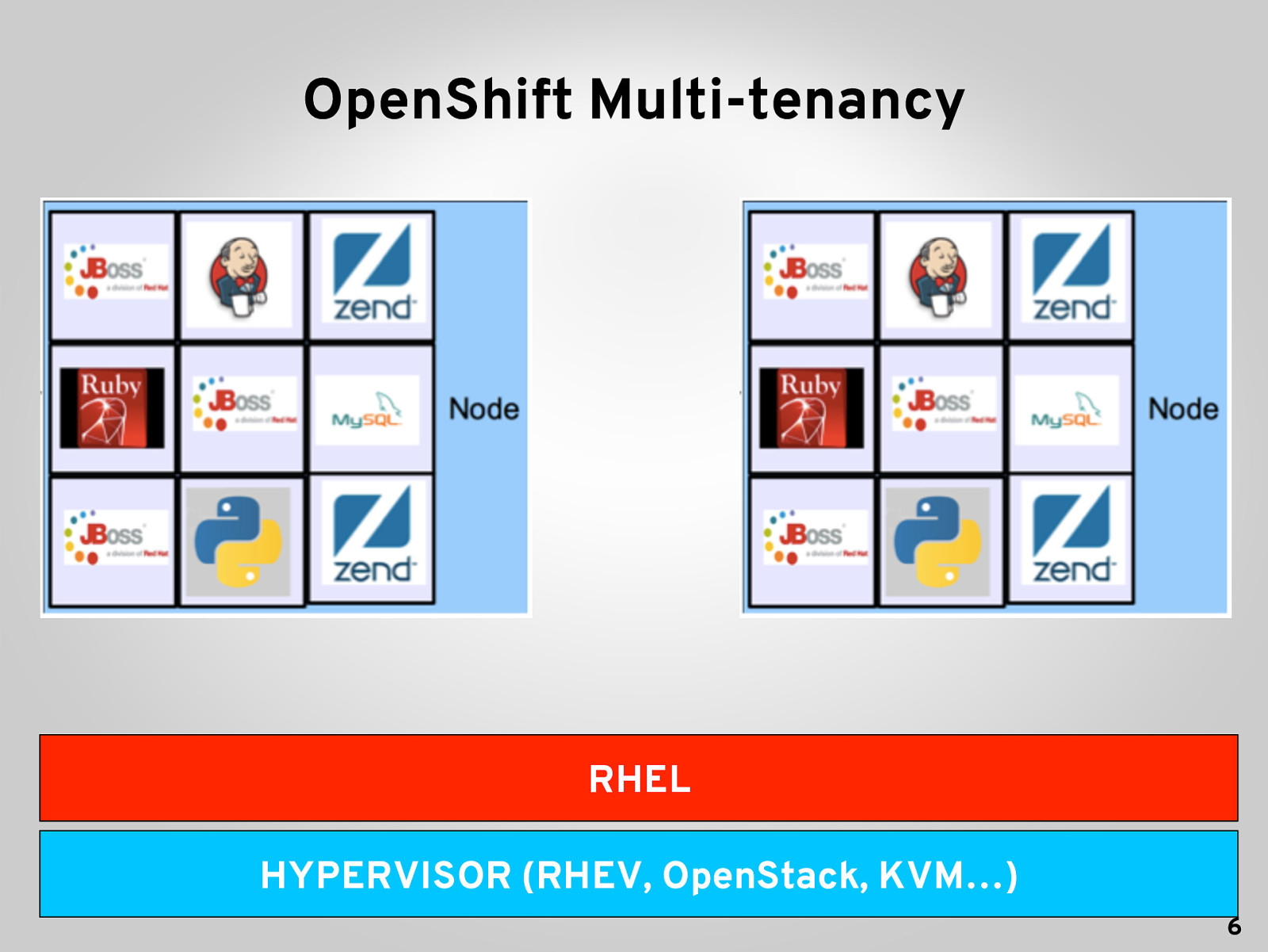
OpenShift Multi-tenancy RHEL HYPERVISOR (RHEV, OpenStack, KVM…) 6
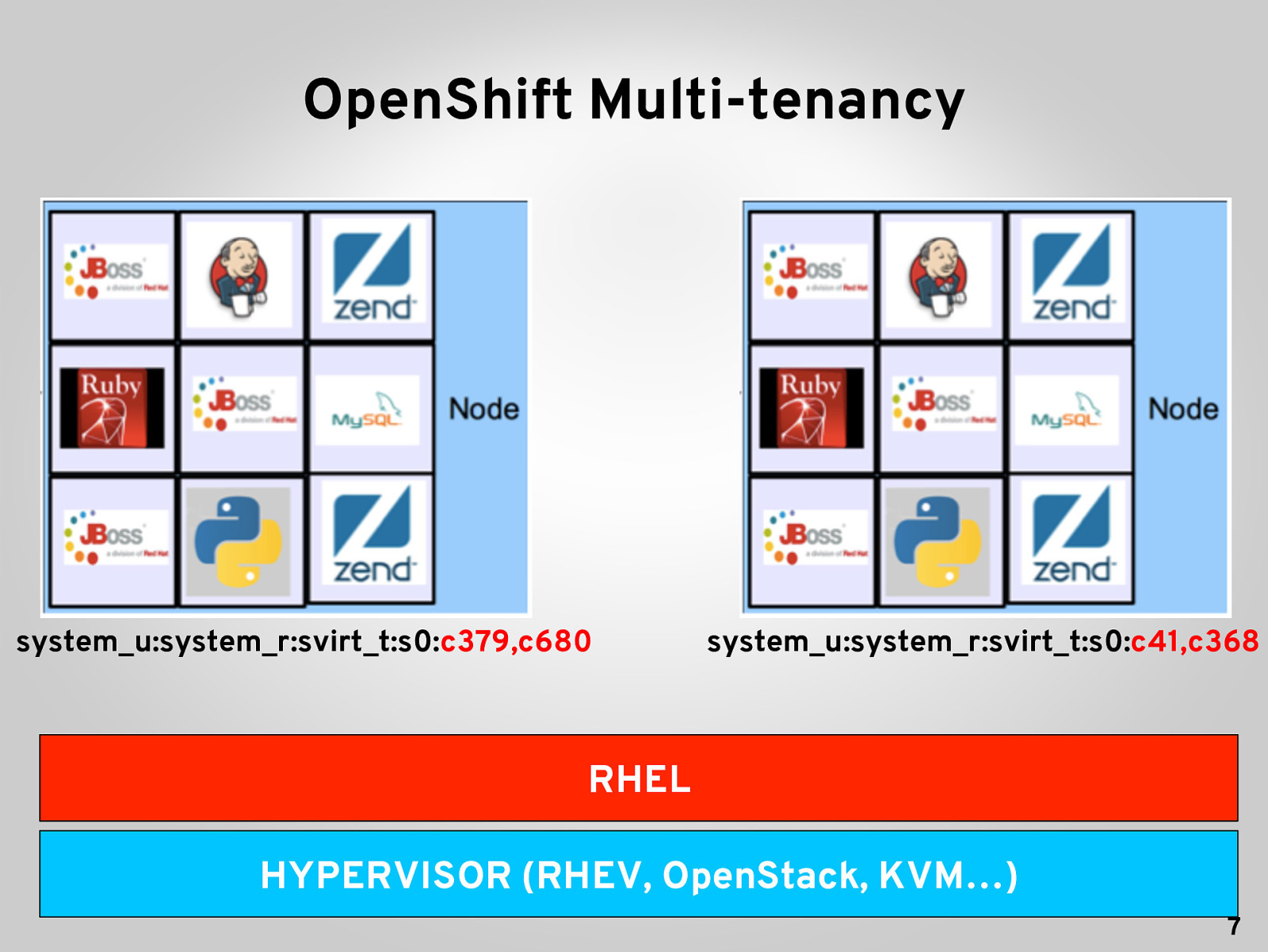
OpenShift Multi-tenancy system_u:system_r:svirt_t:s0:c379,c680 system_u:system_r:svirt_t:s0:c41,c368 RHEL HYPERVISOR (RHEV, OpenStack, KVM…) 7
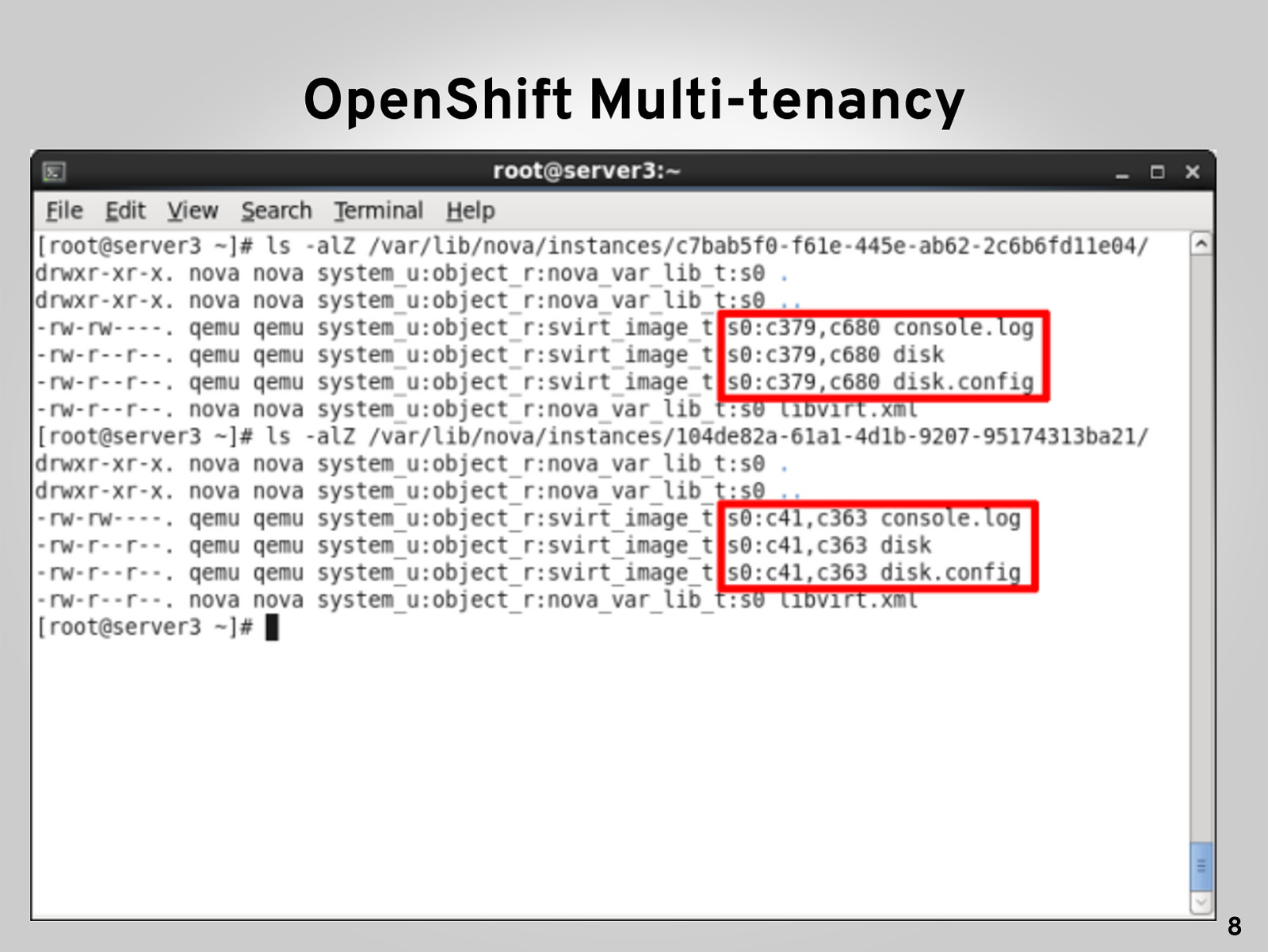
OpenShift Multi-tenancy 8
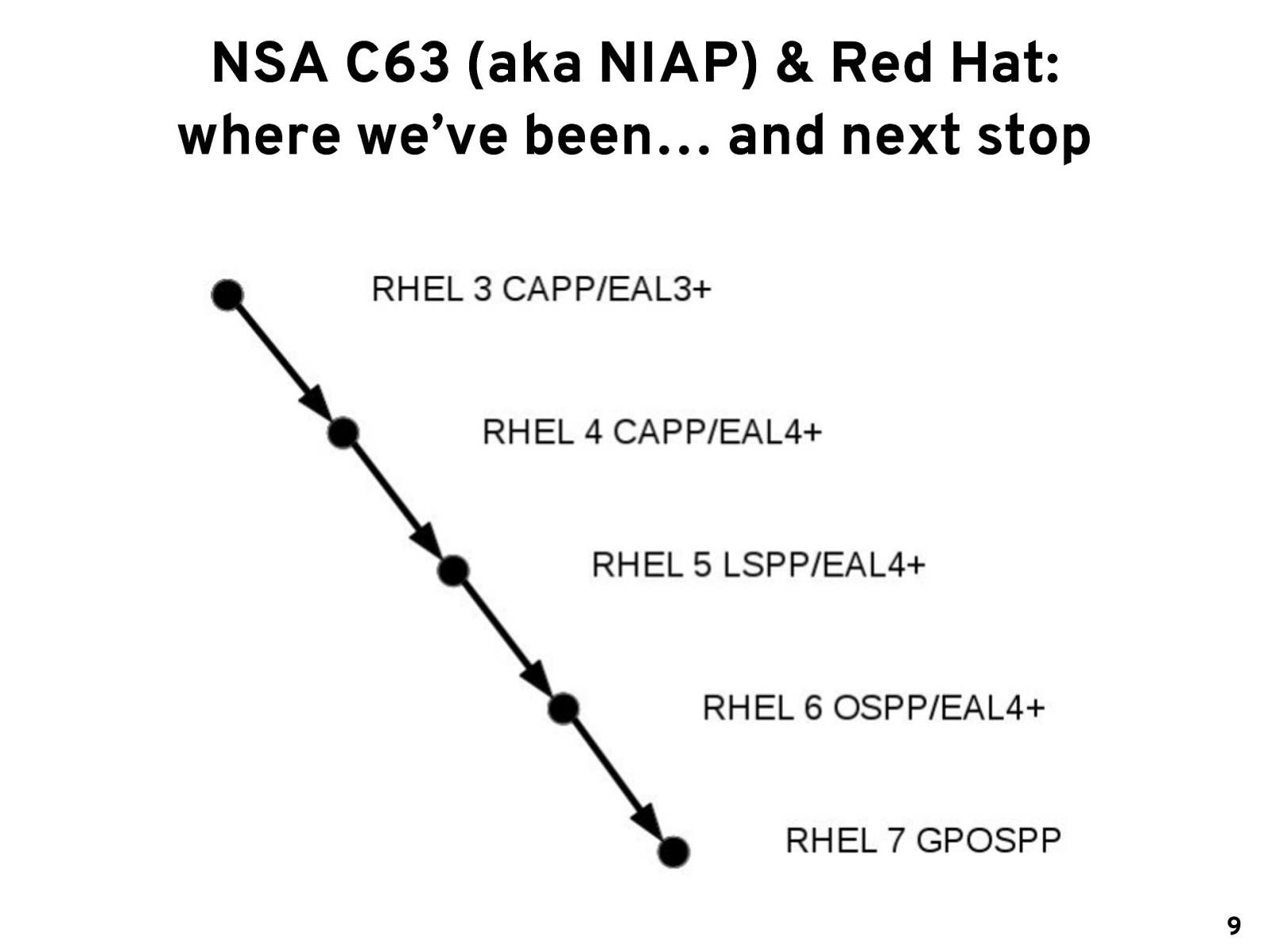
NSA C63 (aka NIAP) & Red Hat: where we’ve been… and next stop 9
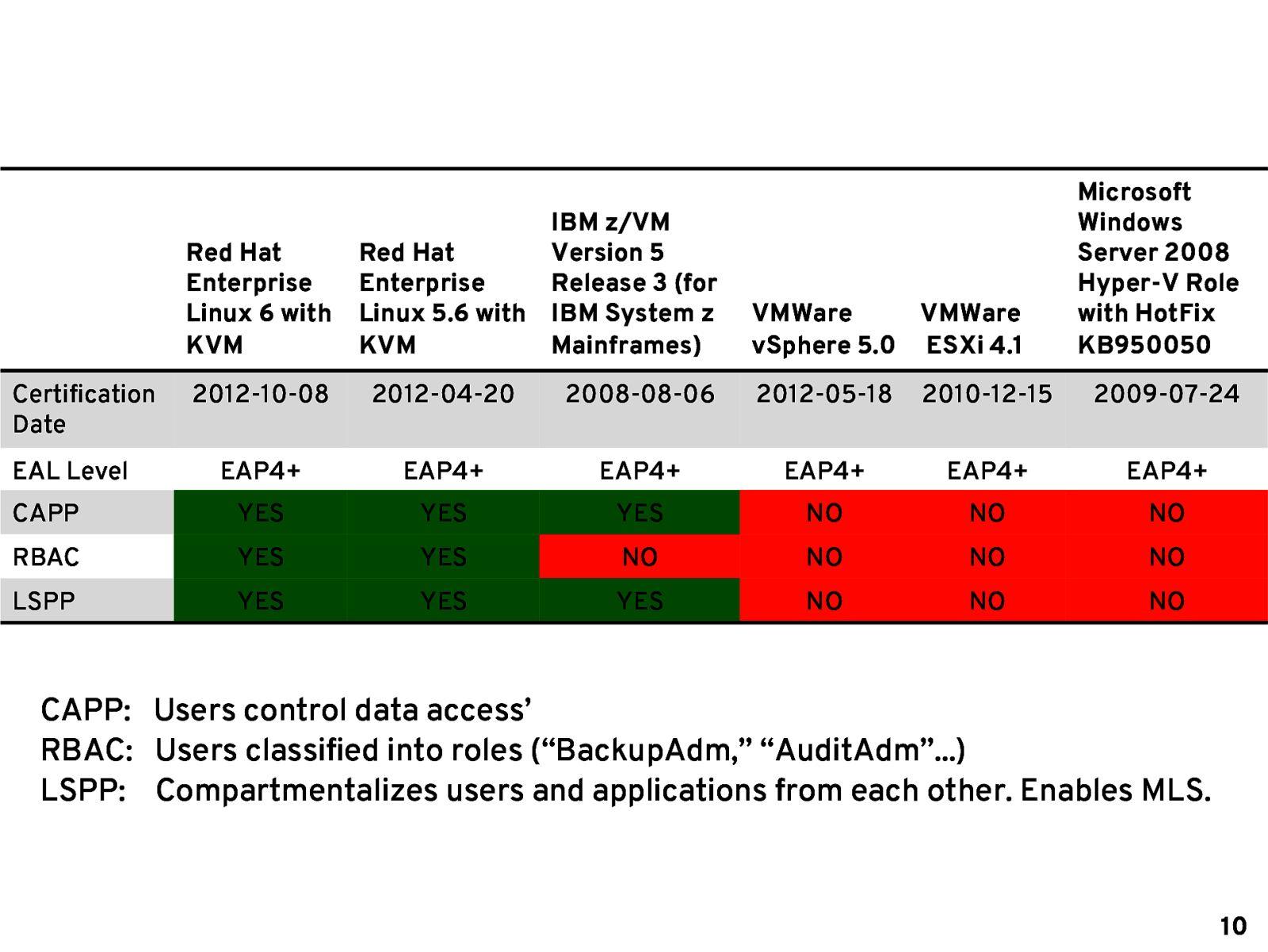
Red Hat Enterprise Linux 6 with KVM Certification Date IBM z/VM Red Hat Version 5 Enterprise Release 3 (for Linux 5.6 with IBM System z KVM Mainframes) VMWare VMWare vSphere 5.0 ESXi 4.1 Microsoft Windows Server 2008 Hyper-V Role with HotFix KB950050 2012-10-08 2012-04-20 2008-08-06 2012-05-18 2010-12-15 2009-07-24 EAP4+ EAP4+ EAP4+ EAP4+ EAP4+ EAP4+ CAPP YES YES YES NO NO NO RBAC YES YES NO NO NO NO LSPP YES YES YES NO NO NO EAL Level CAPP: Users control data access’ RBAC: Users classified into roles (“BackupAdm,” “AuditAdm”…) LSPP: Compartmentalizes users and applications from each other. Enables MLS. 10
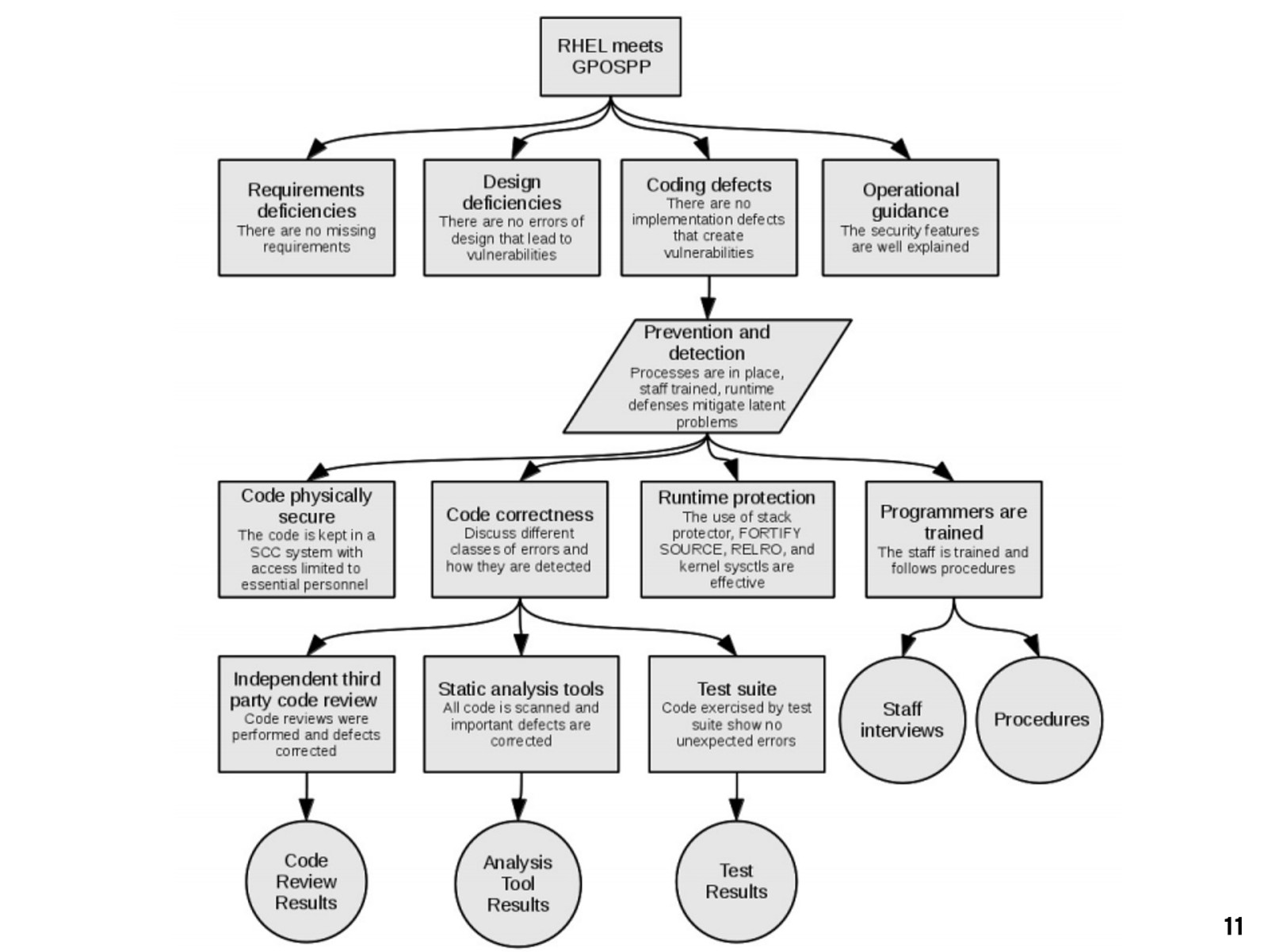
11
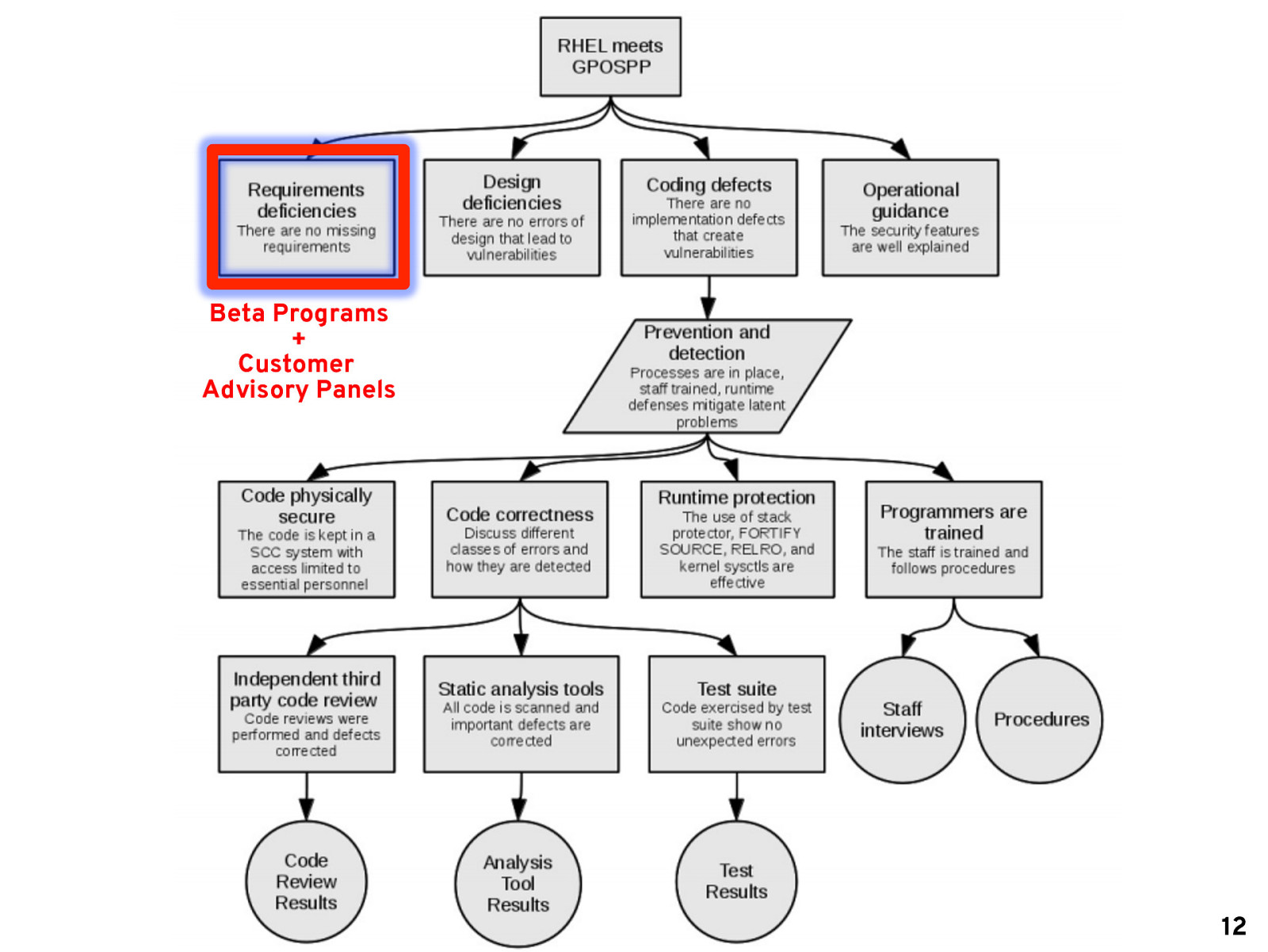
Beta Programs + Customer Advisory Panels 12
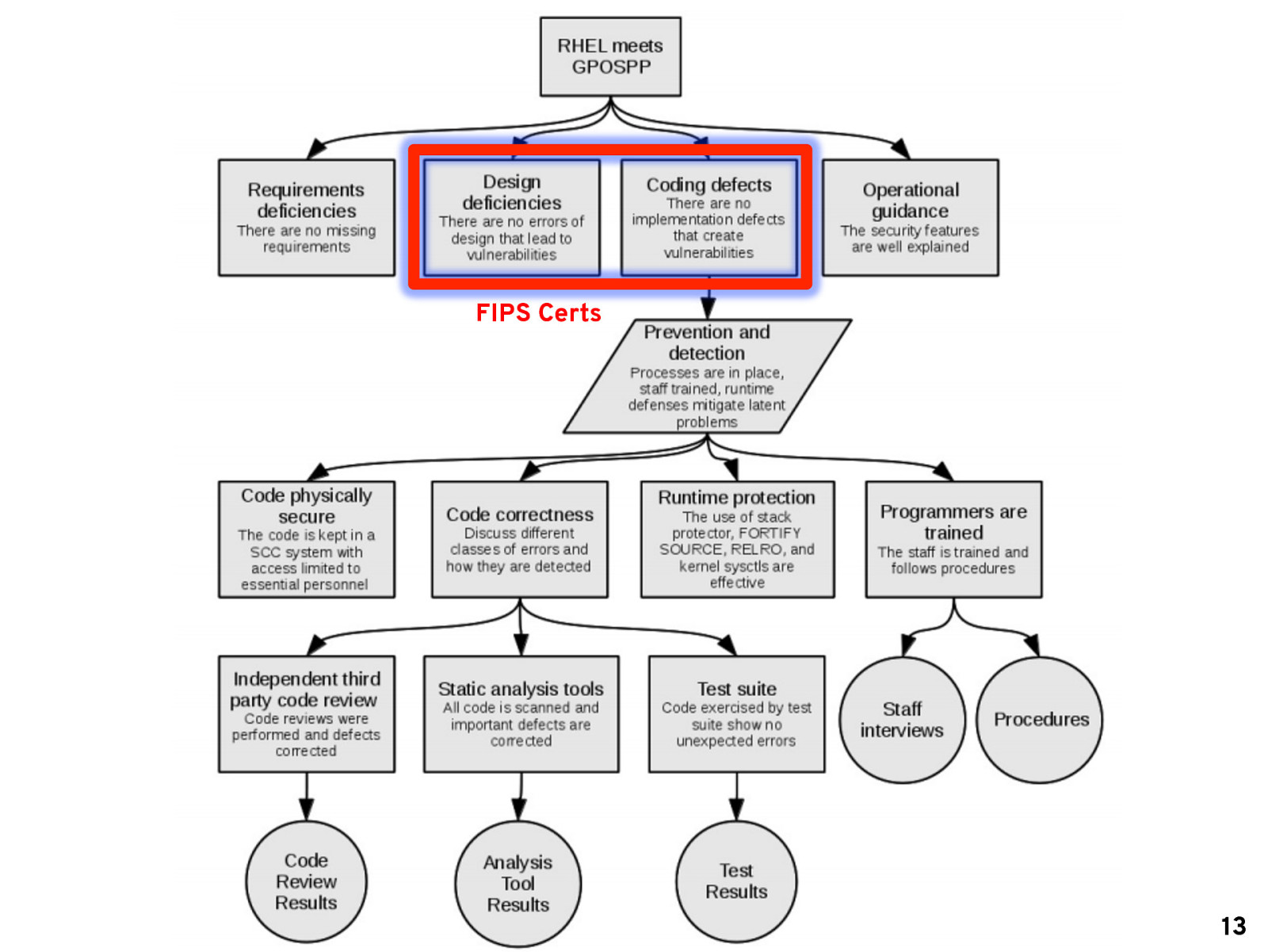
FIPS Certs 13
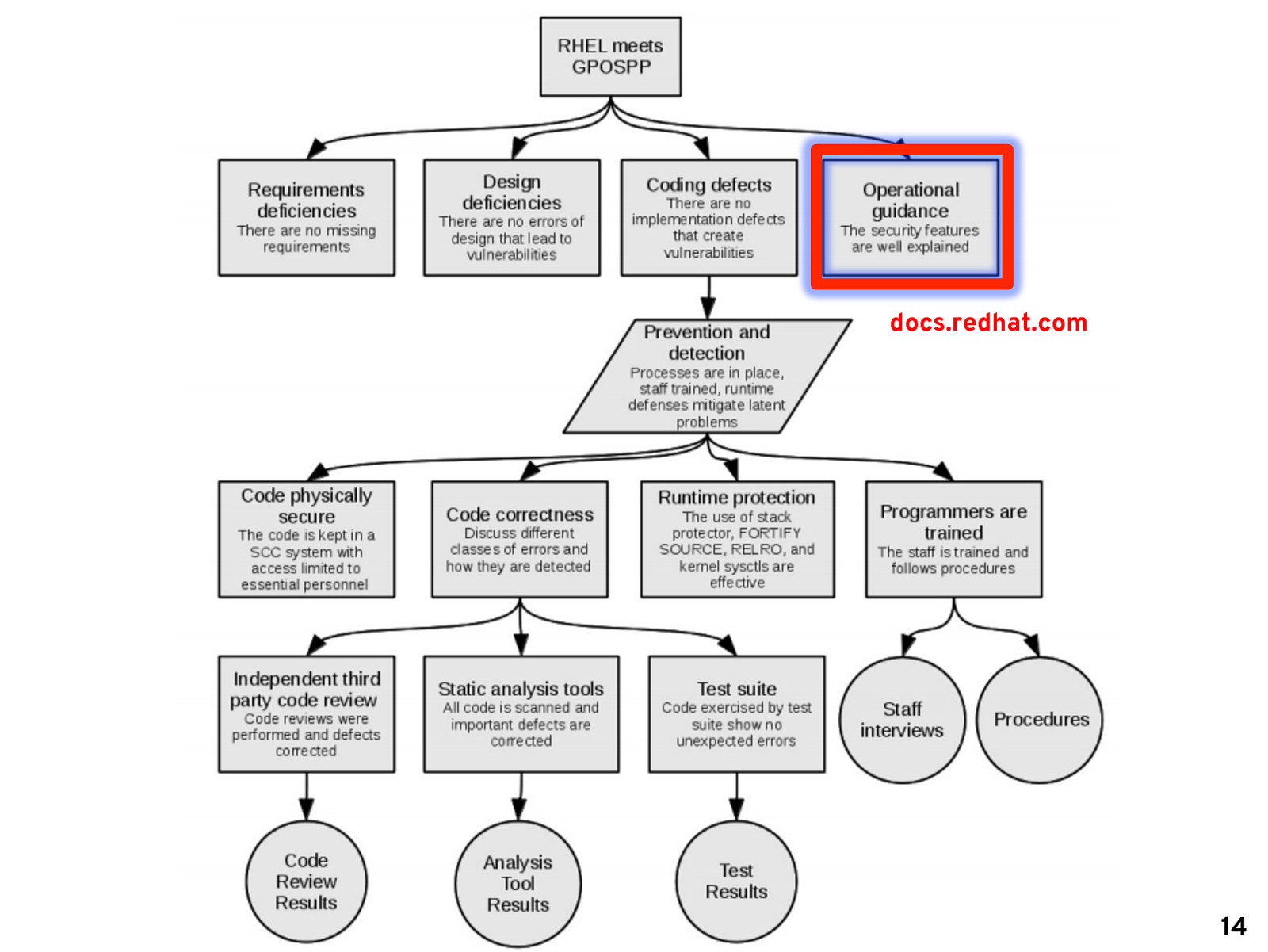
docs.redhat.com 14
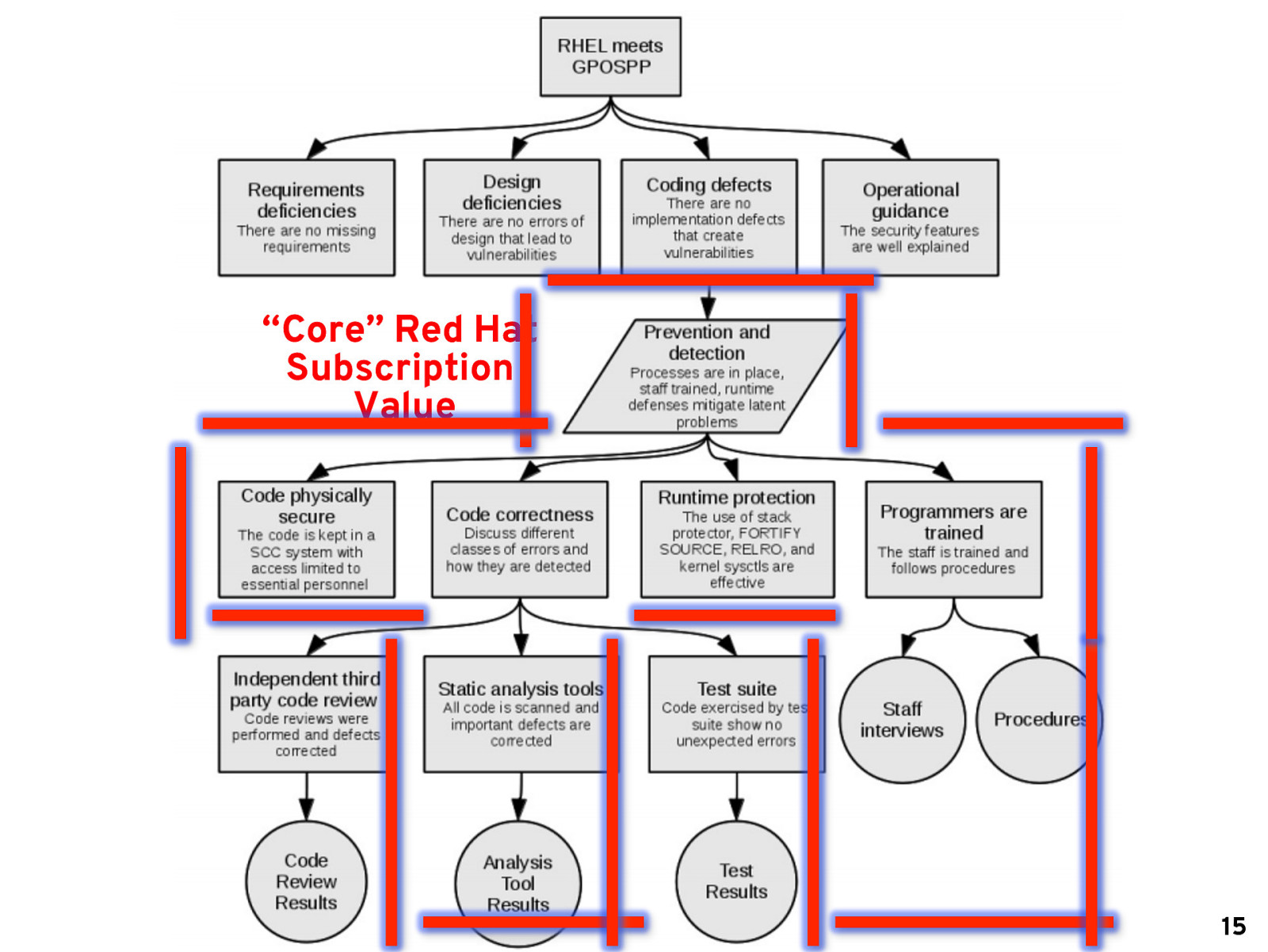
“Core” Red Hat Subscription Value 15
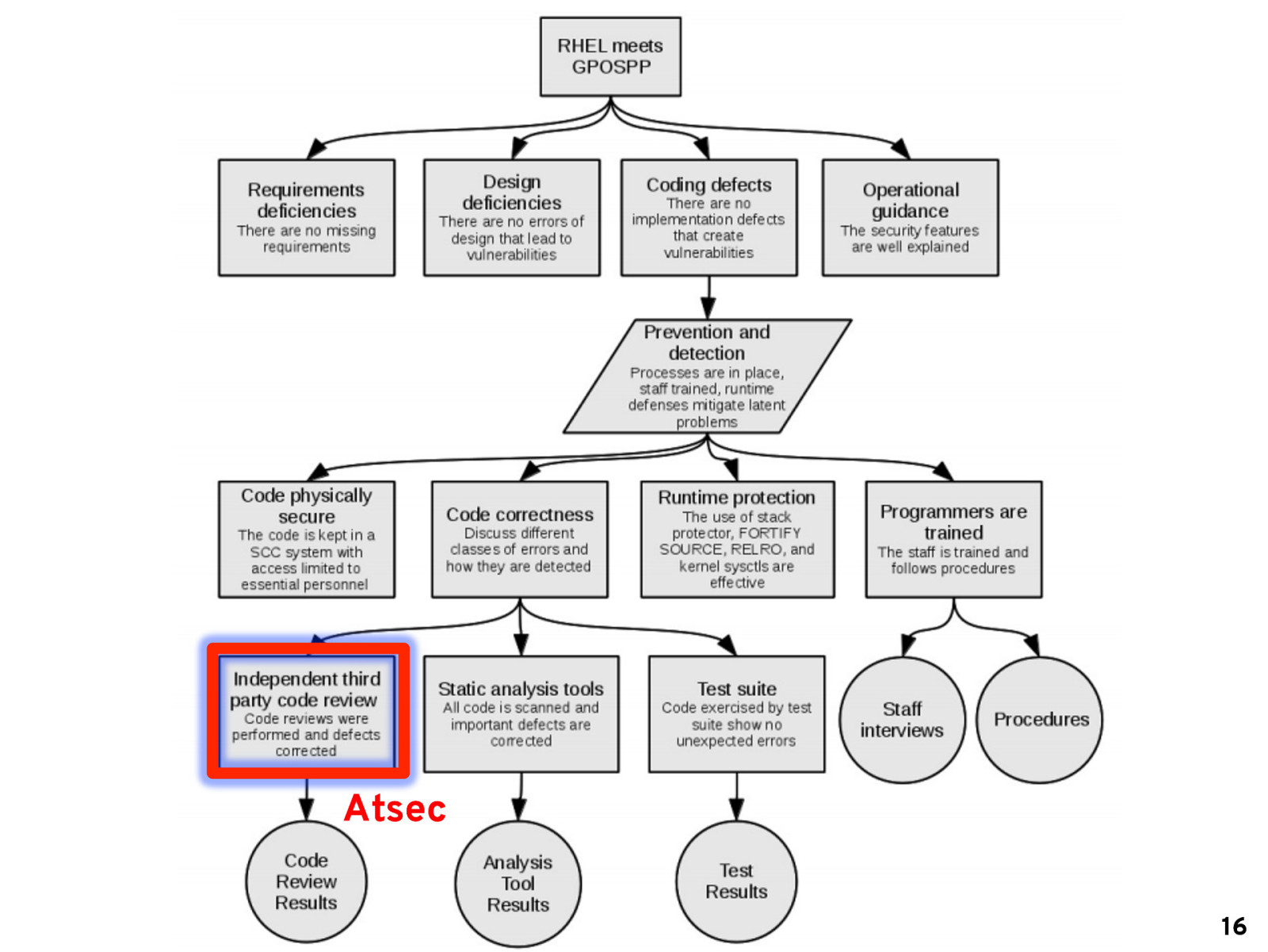
Atsec 16

Common Criteria != Compliance Policy 17

STIG == Compliance Policy 18
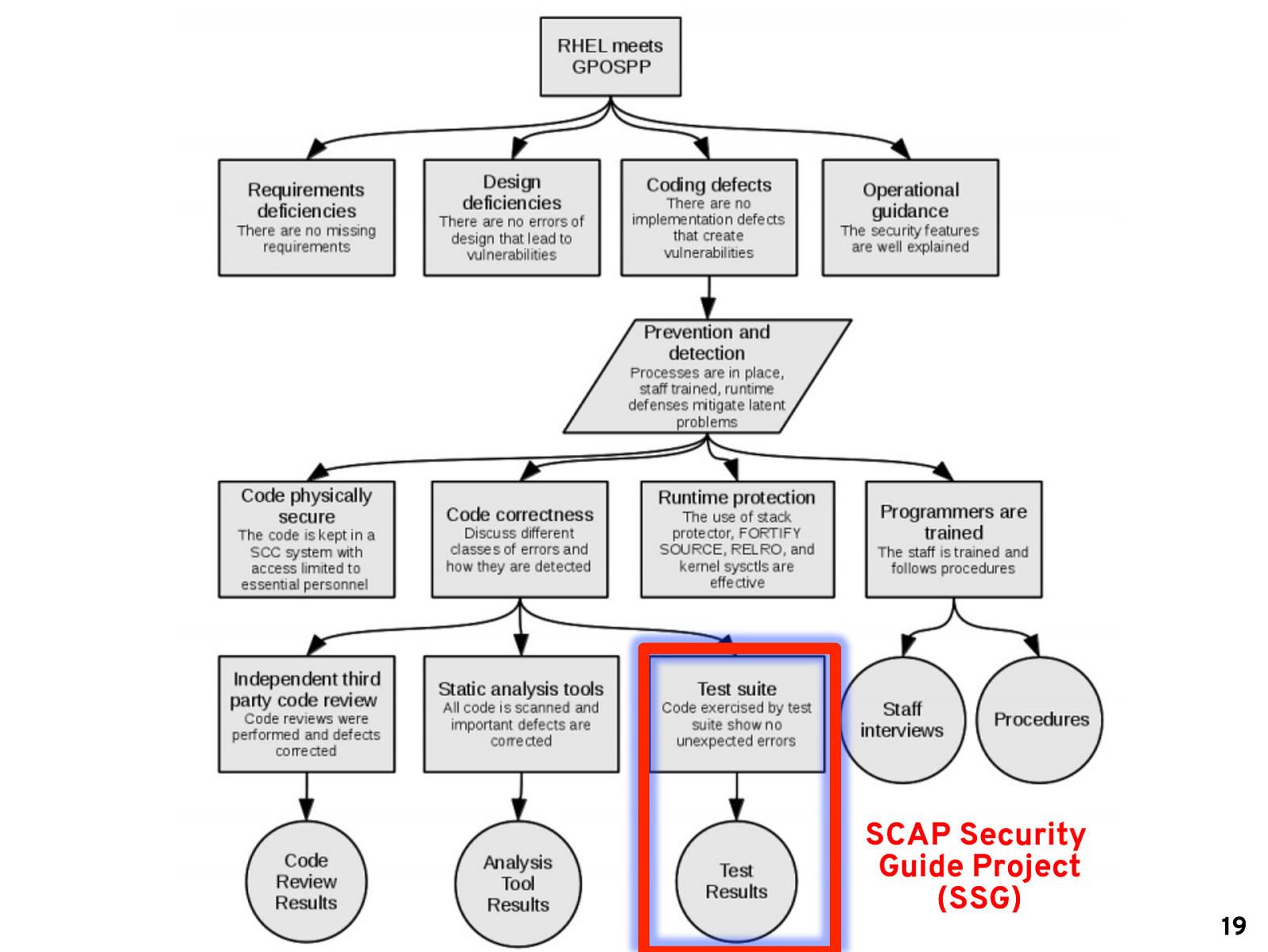
SCAP Security Guide Project (SSG) 19

SCAP Security Guide 20
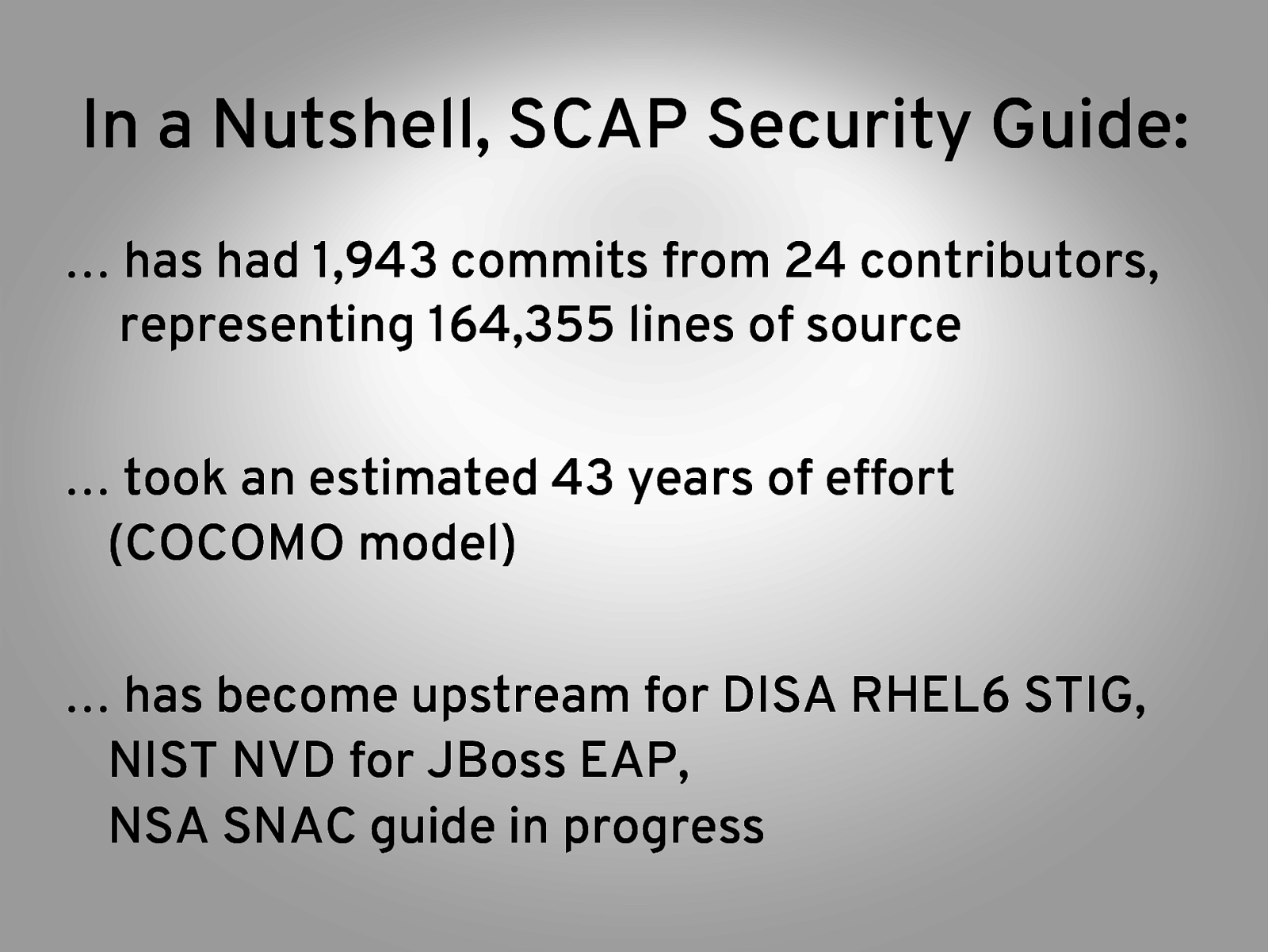
In a Nutshell, SCAP Security Guide: … has had 1,943 commits from 24 contributors, representing 164,355 lines of source … took an estimated 43 years of effort (COCOMO model) … has become upstream for DISA RHEL6 STIG, NIST NVD for JBoss EAP, NSA SNAC guide in progress

RHEL5 STIG Delay: 1,988 days 22
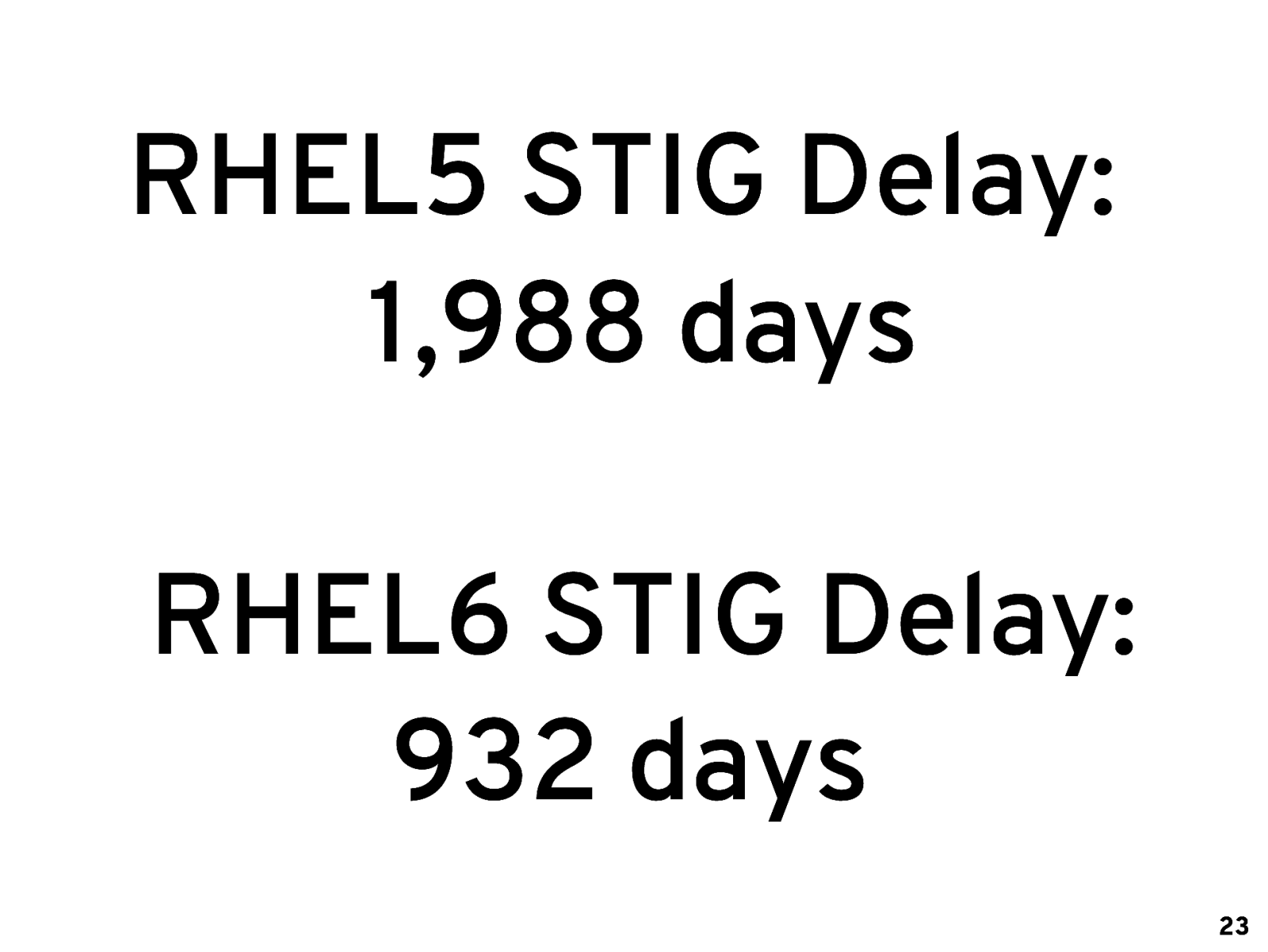
RHEL5 STIG Delay: 1,988 days RHEL6 STIG Delay: 932 days 23

STIG Version 1, Release 2, Section 1.1: “The consensus content was developed using an open source project called SCAP Security Guide. The project’s website is https:// fedorahosted.org/scap-security-guide/. Except for differences in formatting to accommodate the DISA STIG publising process, the content of the RHEL6 STIG should mirror the SCAP Security Guide content with only minor divergences as updates from multiple sources work through the consensus process” 24
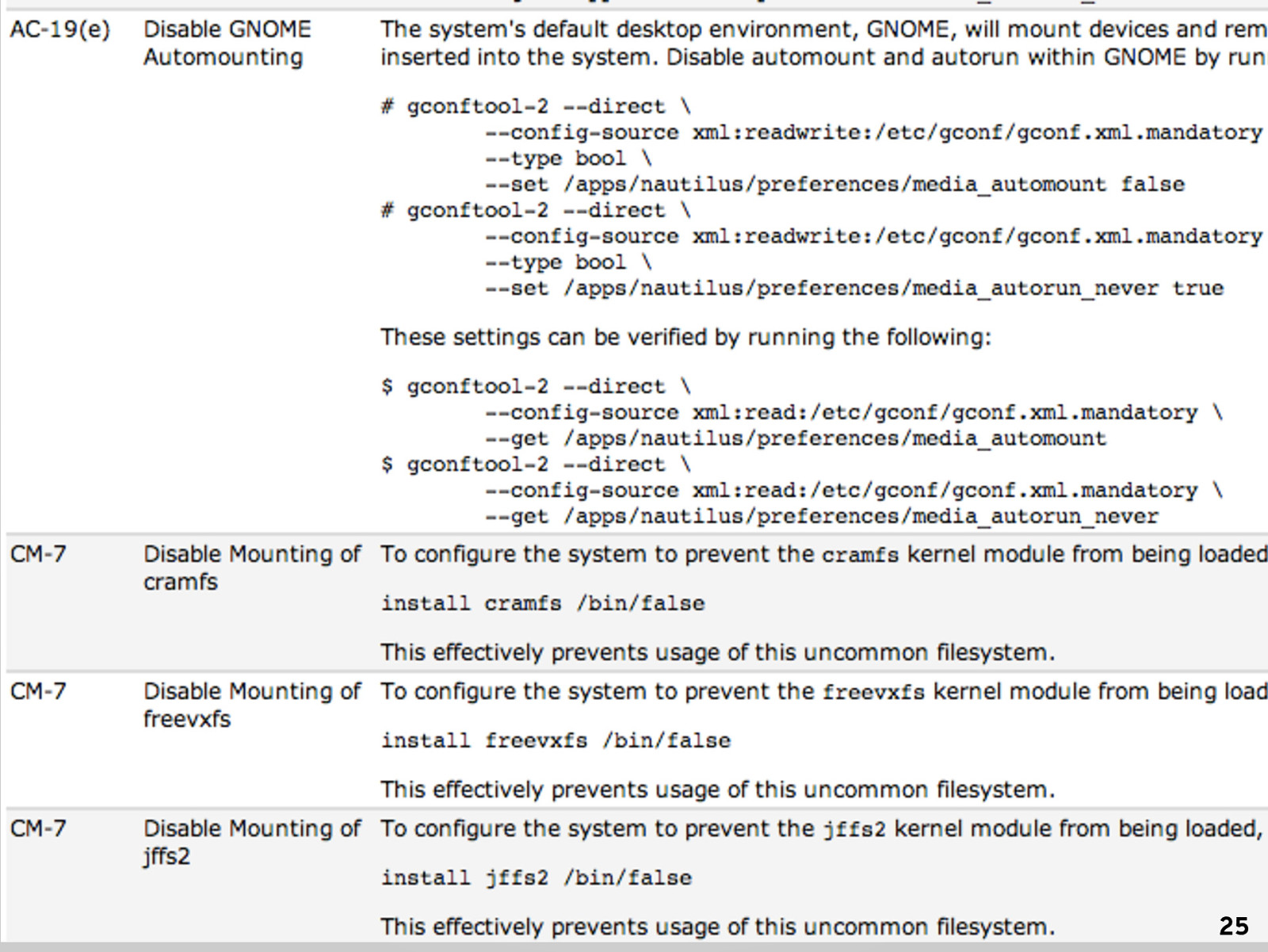
25
SCAP Security Guide • Guidance broken into profiles: • RHEL6 STIG • CS2 • NIST NVD (JBoss only) 26
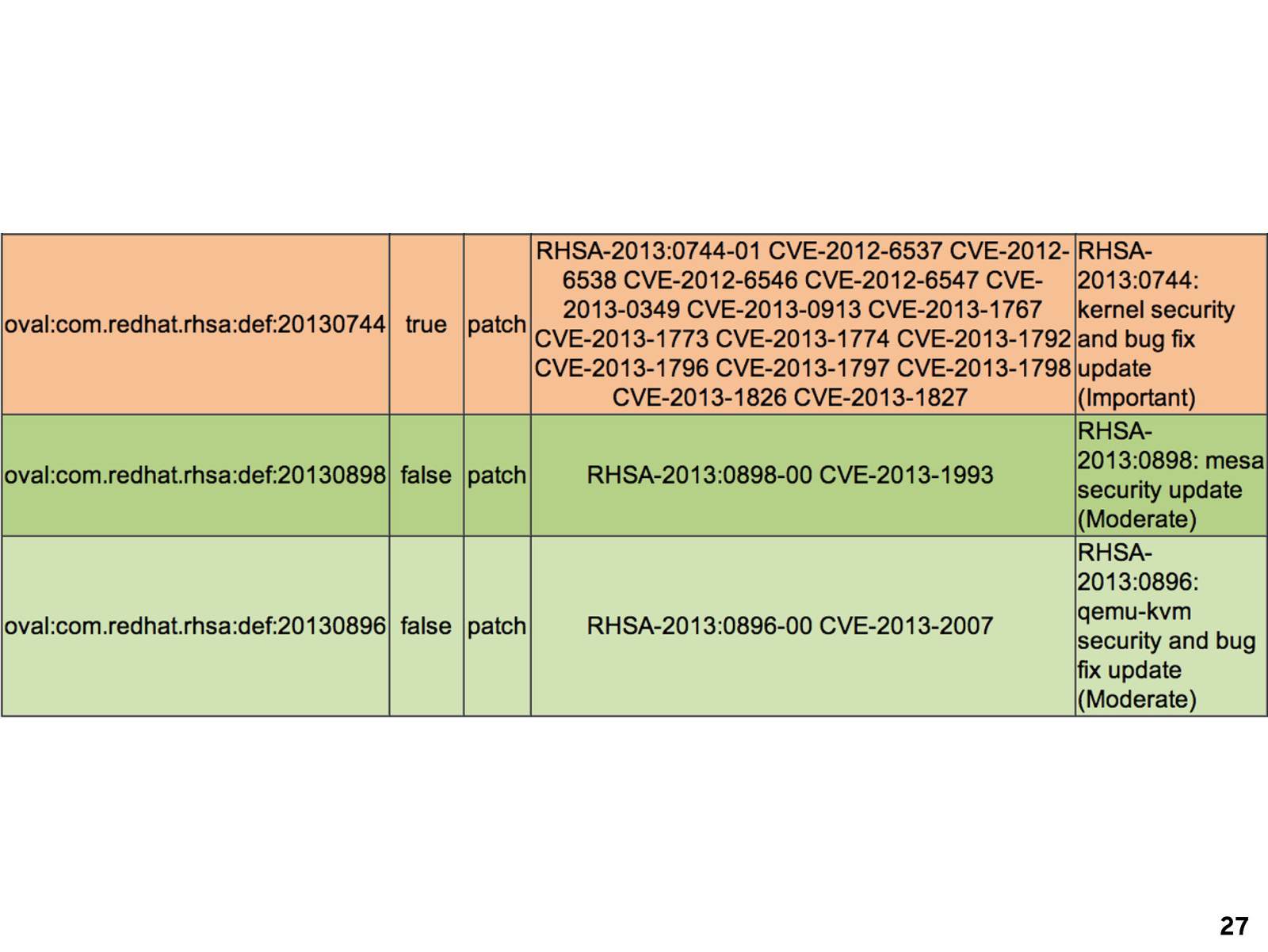
27
28

29
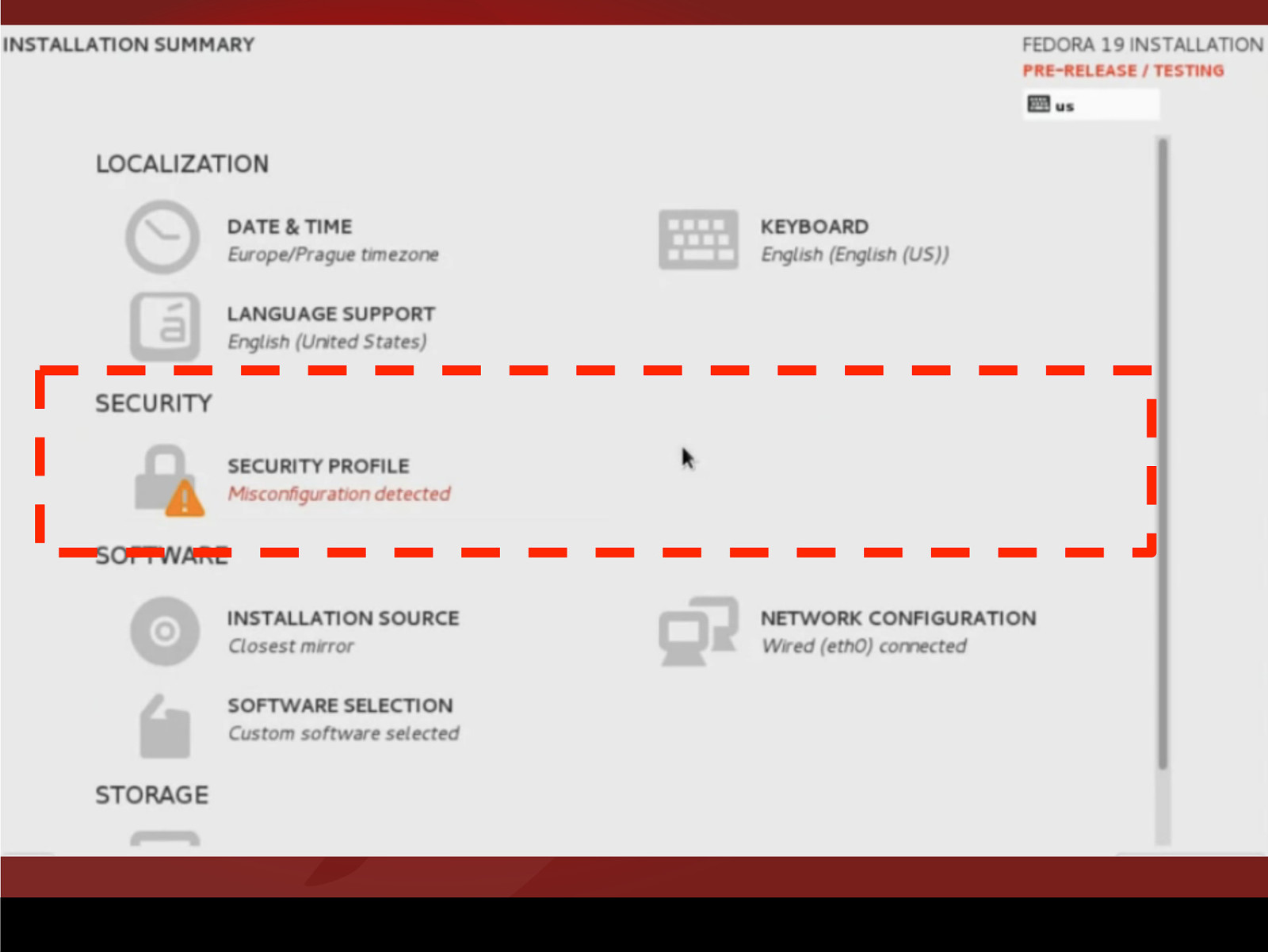
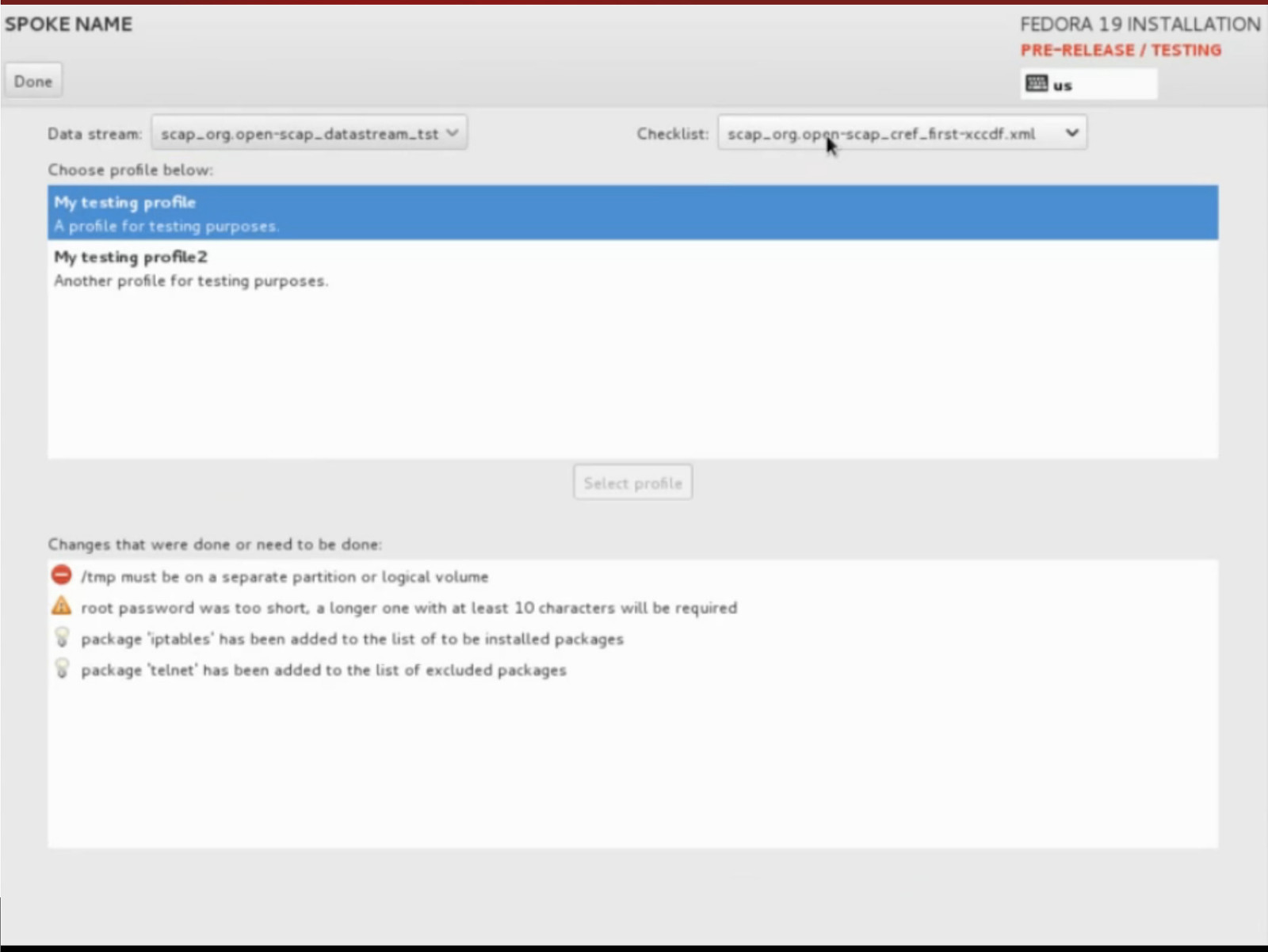
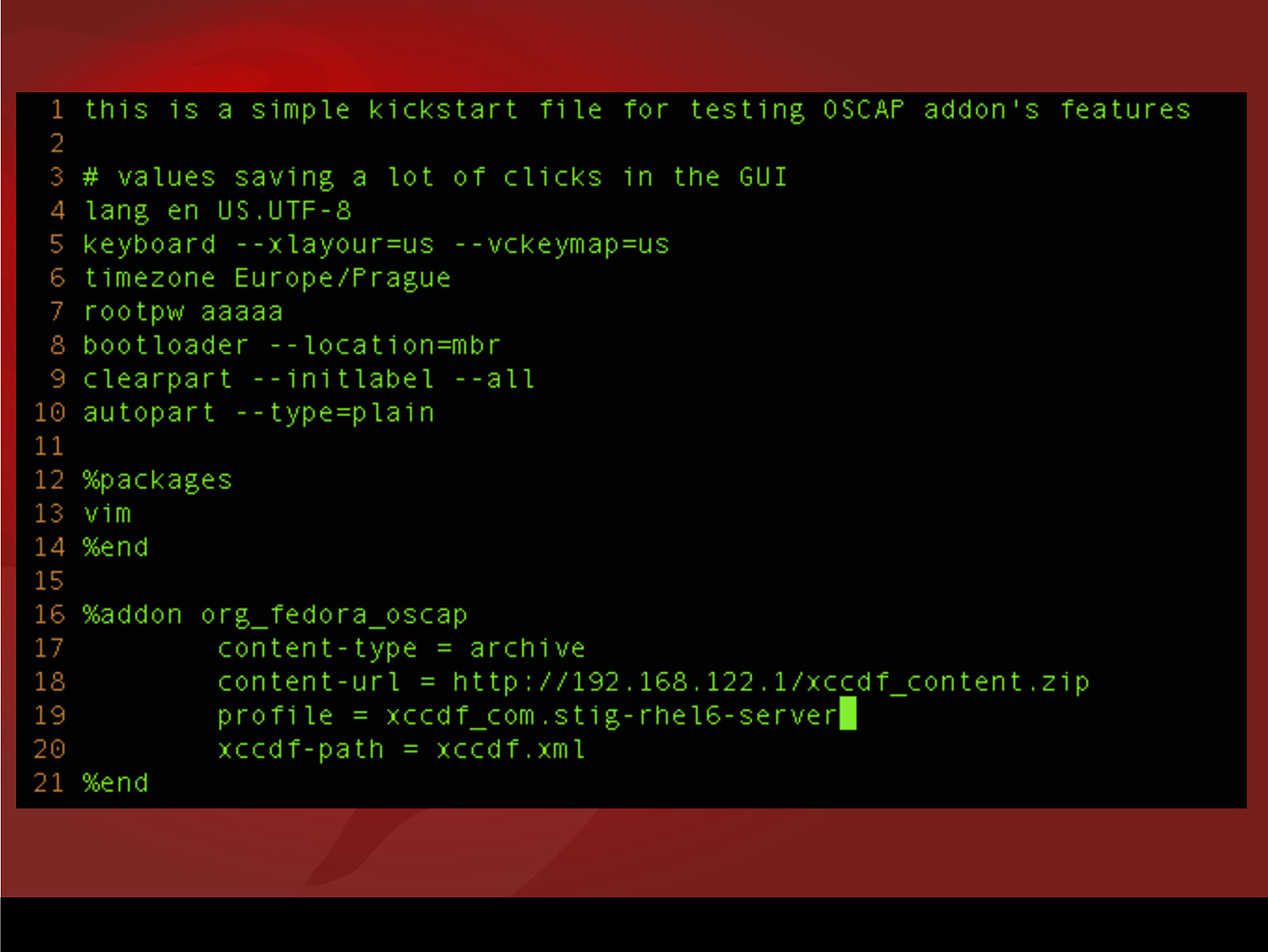
Remediation During Provisioning
Invited by channel partner WWT to review OpenShift Security Frameworks, and discuss compliance technology and initiatives across the US Government.
