NEW ERA OF DIGITAL SECURITY Shawn Wells Chief Security Strategist U.S. Public Sector shawn@redhat.com || 443-534-0130
Slide 1

Slide 2
Technology for the Digital World 2
Slide 3
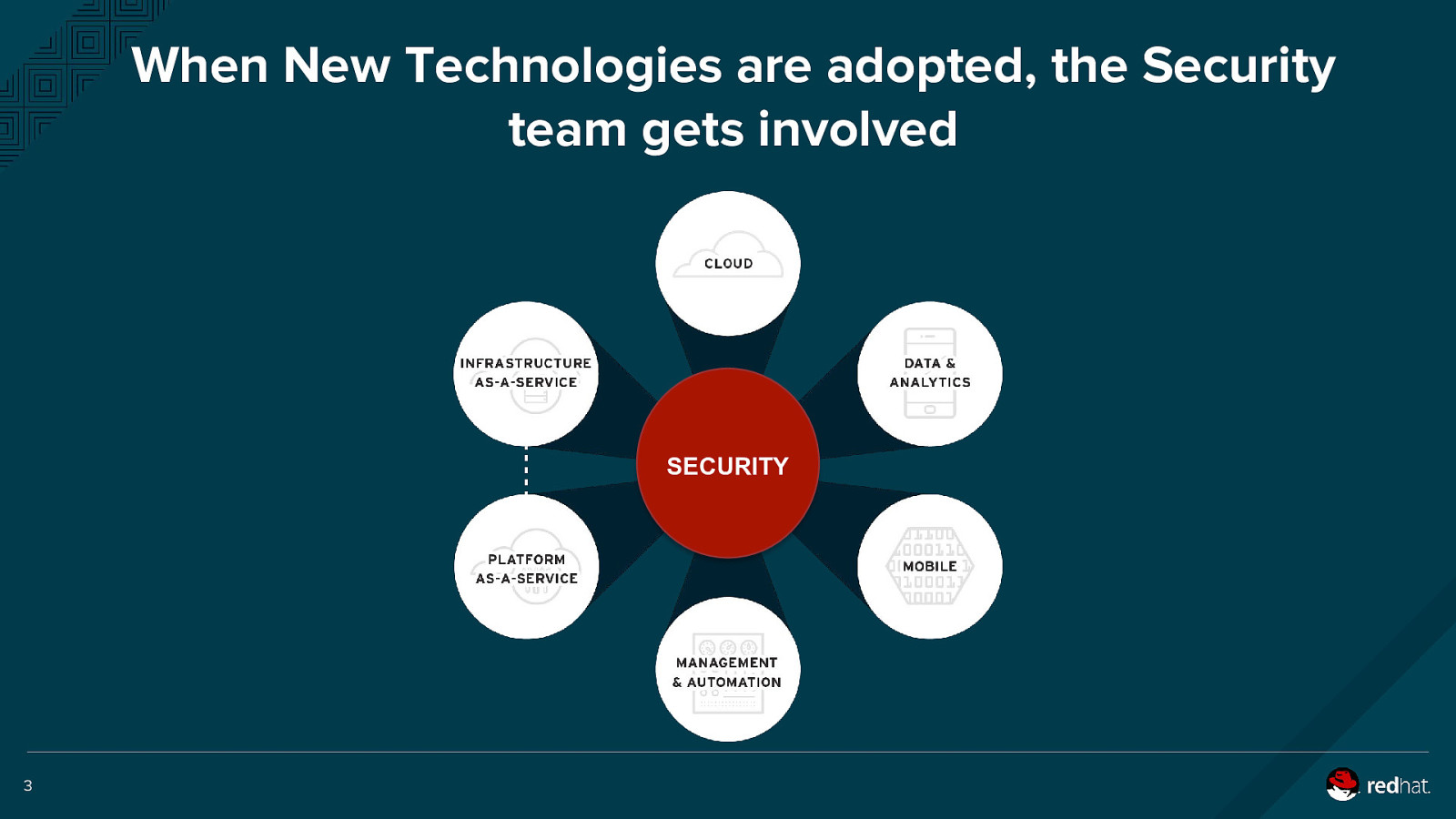
When New Technologies are adopted, the Security team gets involved SECURITY 3
Slide 4
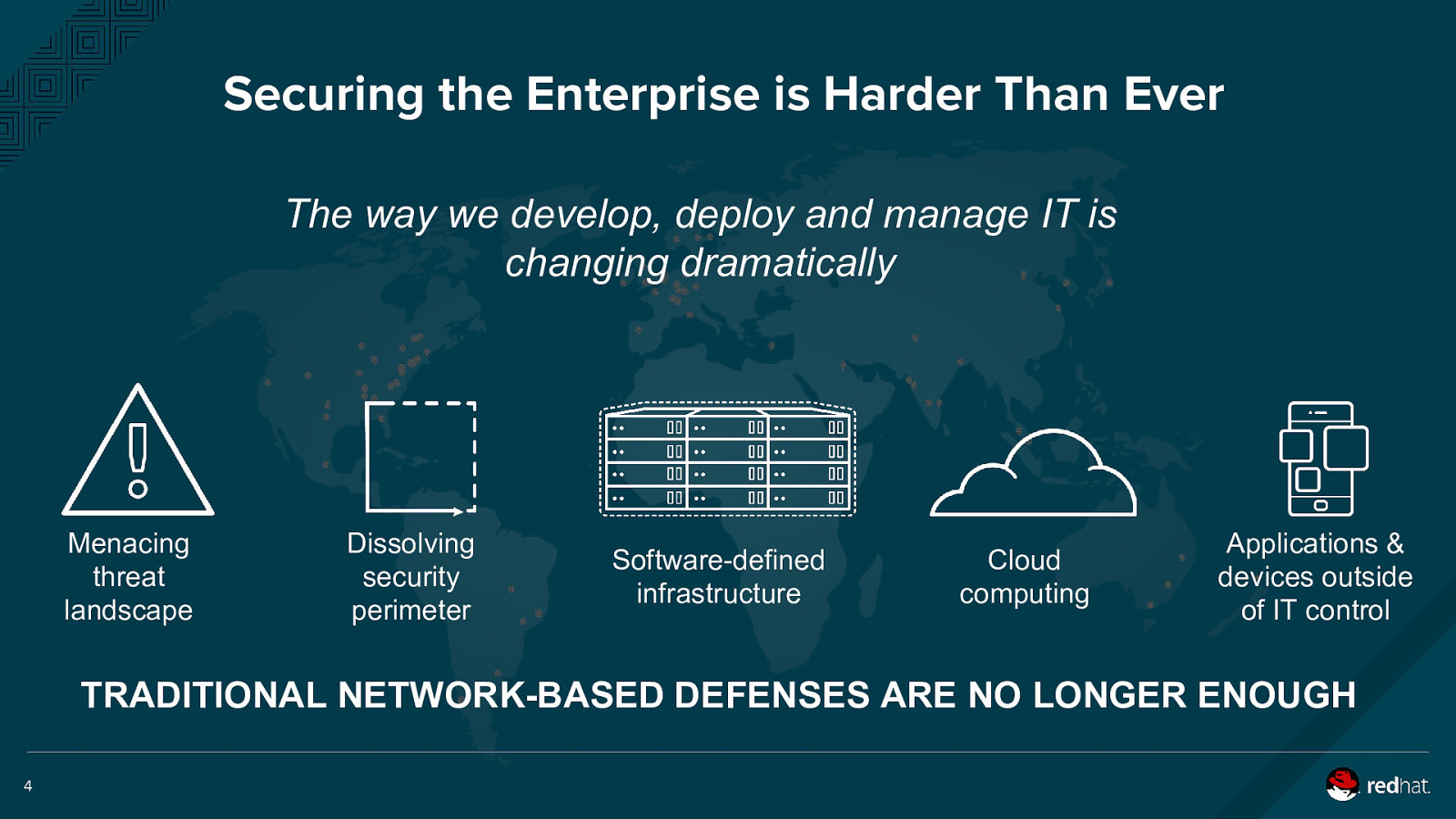
Securing the Enterprise is Harder Than Ever The way we develop, deploy and manage IT is changing dramatically Menacing threat landscape Dissolving security perimeter Software-defined infrastructure Cloud computing Applications & devices outside of IT control TRADITIONAL NETWORK-BASED DEFENSES ARE NO LONGER ENOUGH 4
Slide 5
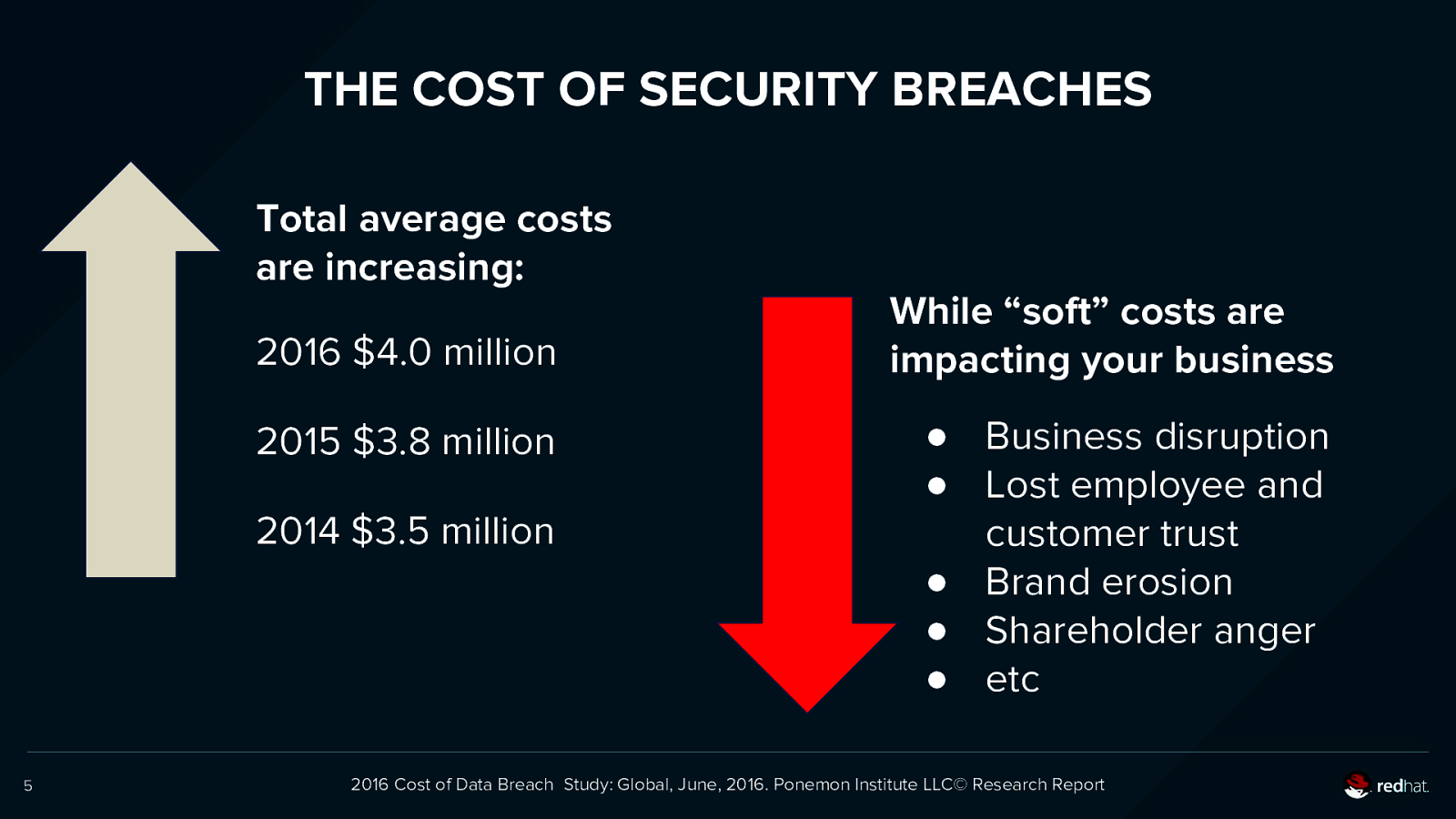
THE COST OF SECURITY BREACHES Total average costs are increasing: 2016 $4.0 million 2015 $3.8 million 2014 $3.5 million 5 While “soft” costs are impacting your business ● Business disruption ● Lost employee and customer trust ● Brand erosion ● Shareholder anger ● etc 2016 Cost of Data Breach Study: Global, June, 2016. Ponemon Institute LLC© Research Report
Slide 6
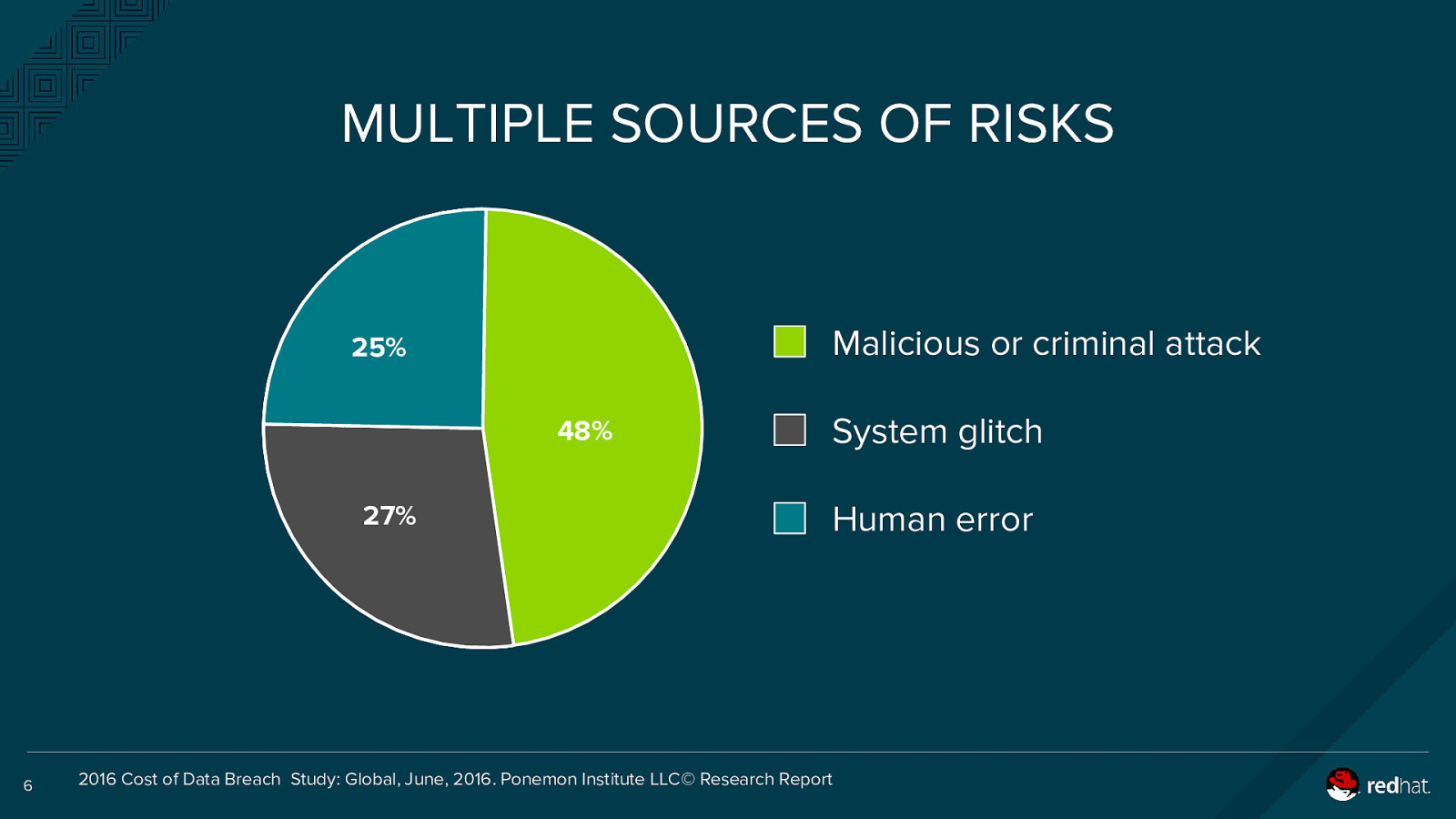
MULTIPLE SOURCES OF RISKS Malicious or criminal attack 25% 48% 27% 6 System glitch Human error 2016 Cost of Data Breach Study: Global, June, 2016. Ponemon Institute LLC© Research Report
Slide 7
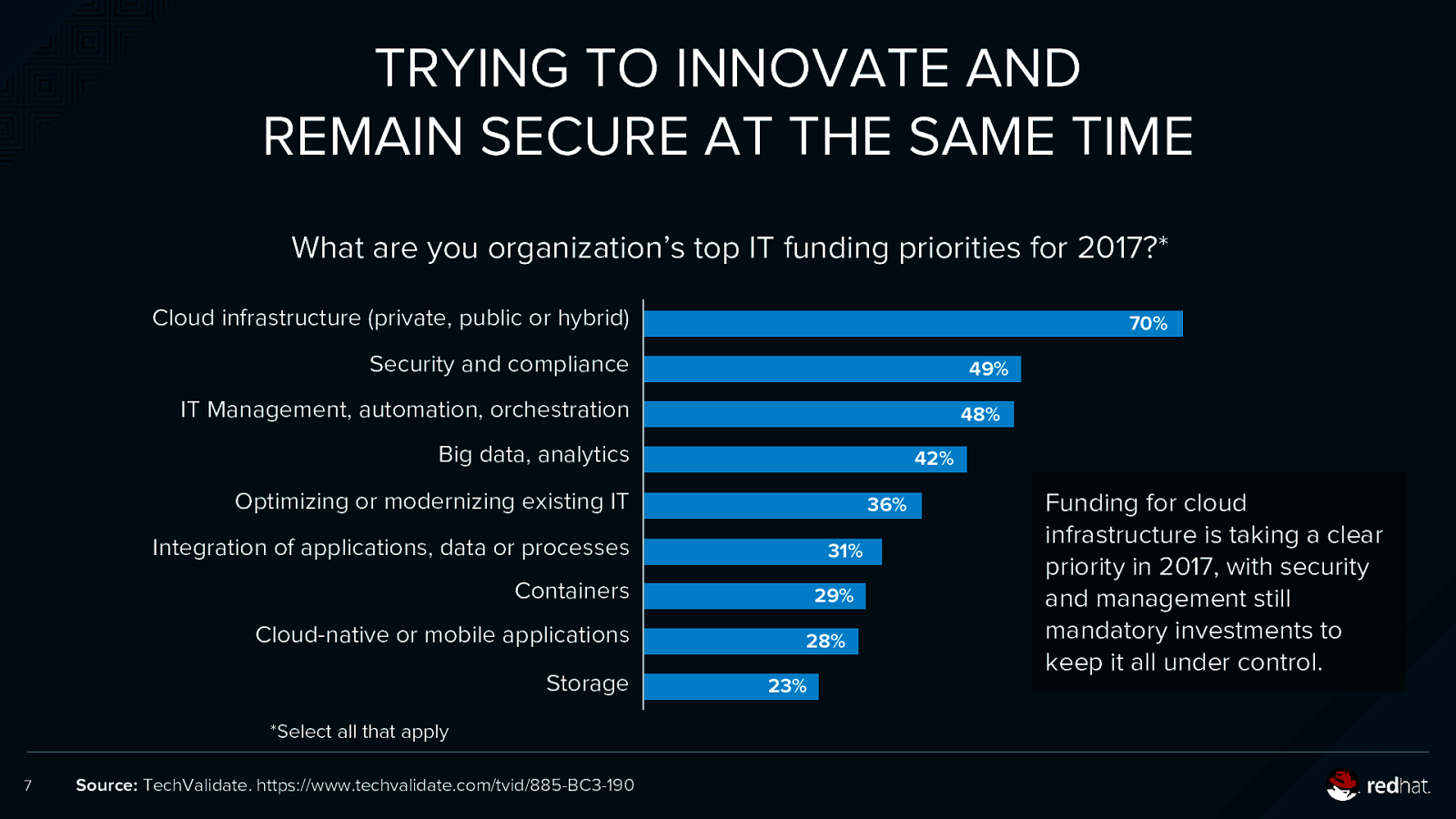
TRYING TO INNOVATE AND REMAIN SECURE AT THE SAME TIME What are you organization’s top IT funding priorities for 2017?* Cloud infrastructure (private, public or hybrid) 70% Security and compliance 49% IT Management, automation, orchestration 48% Big data, analytics 42% Optimizing or modernizing existing IT 36% Integration of applications, data or processes 31% Containers Cloud-native or mobile applications Storage *Select all that apply 7 Source: TechValidate. https://www.techvalidate.com/tvid/885-BC3-190 29% 28% 23% Funding for cloud infrastructure is taking a clear priority in 2017, with security and management still mandatory investments to keep it all under control.
Slide 8
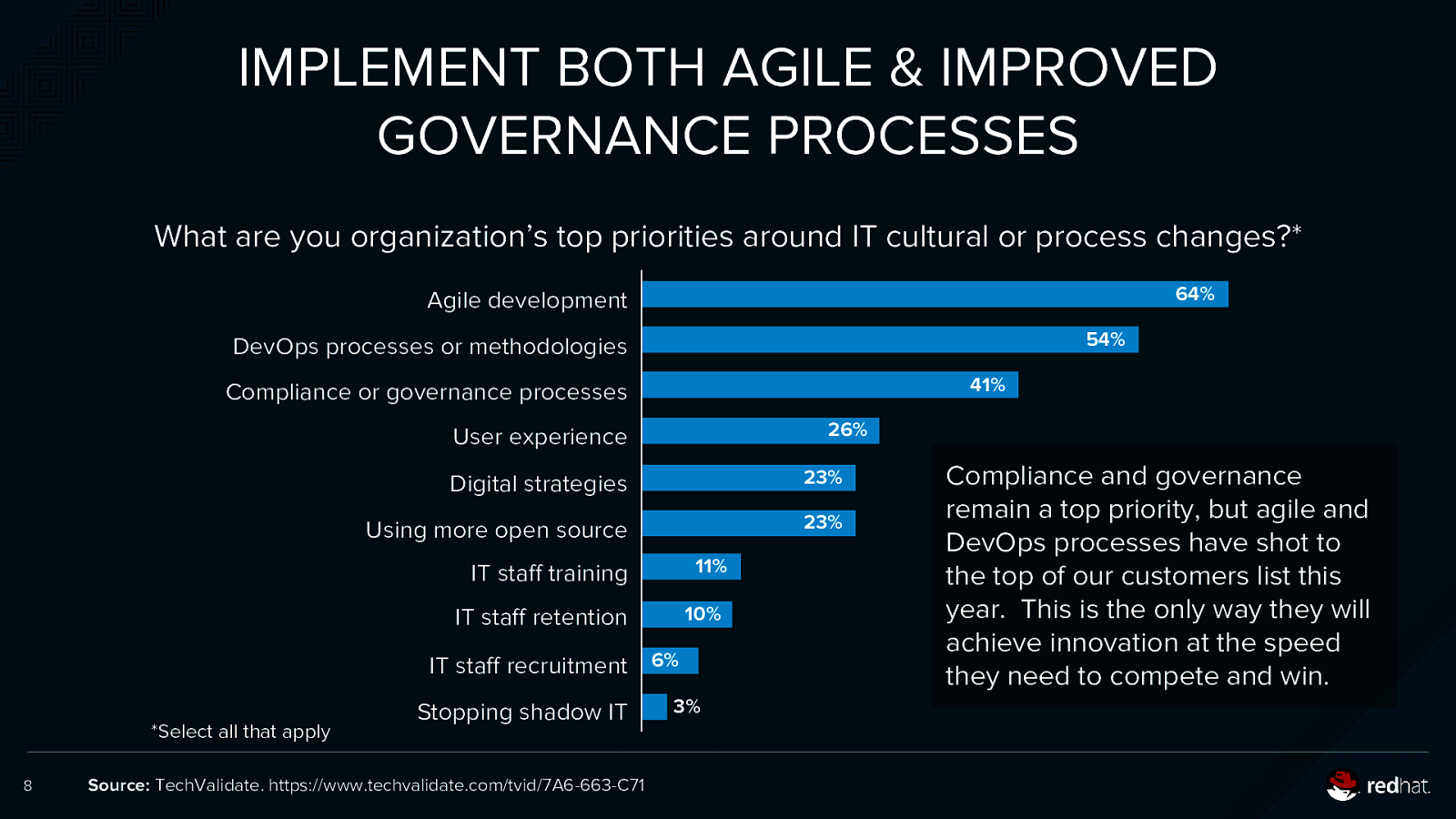
IMPLEMENT BOTH AGILE & IMPROVED GOVERNANCE PROCESSES What are you organization’s top priorities around IT cultural or process changes?* 64% Agile development 54% DevOps processes or methodologies 41% Compliance or governance processes 26% User experience Digital strategies 23% Using more open source 23% 11% IT staff training 10% IT staff retention IT staff recruitment 6% *Select all that apply 8 Stopping shadow IT Source: TechValidate. https://www.techvalidate.com/tvid/7A6-663-C71 3% Compliance and governance remain a top priority, but agile and DevOps processes have shot to the top of our customers list this year. This is the only way they will achieve innovation at the speed they need to compete and win.
Slide 9
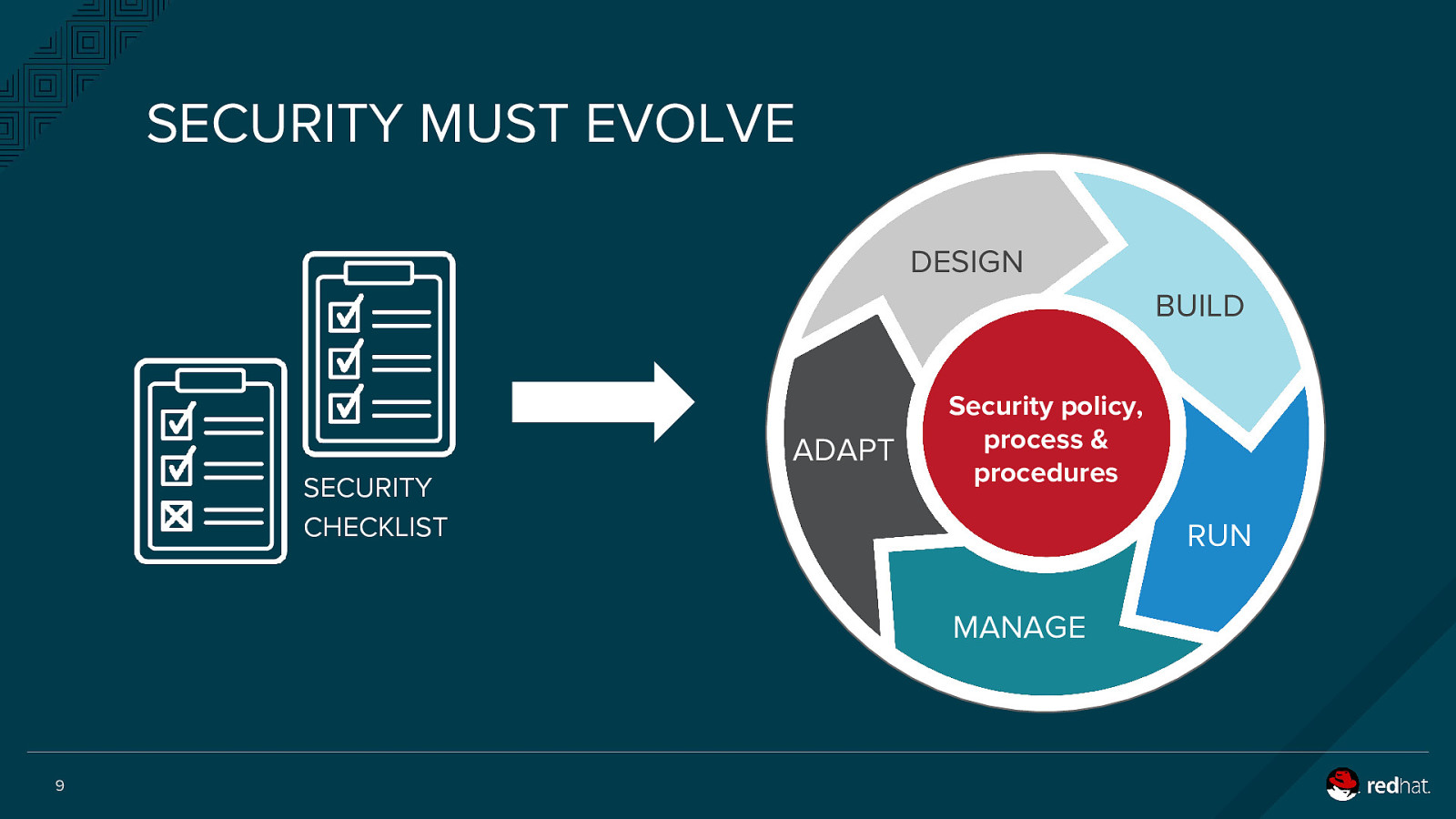
SECURITY MUST EVOLVE DESIGN BUILD ADAPT SECURITY CHECKLIST Security policy, process & procedures RUN MANAGE 9
Slide 10
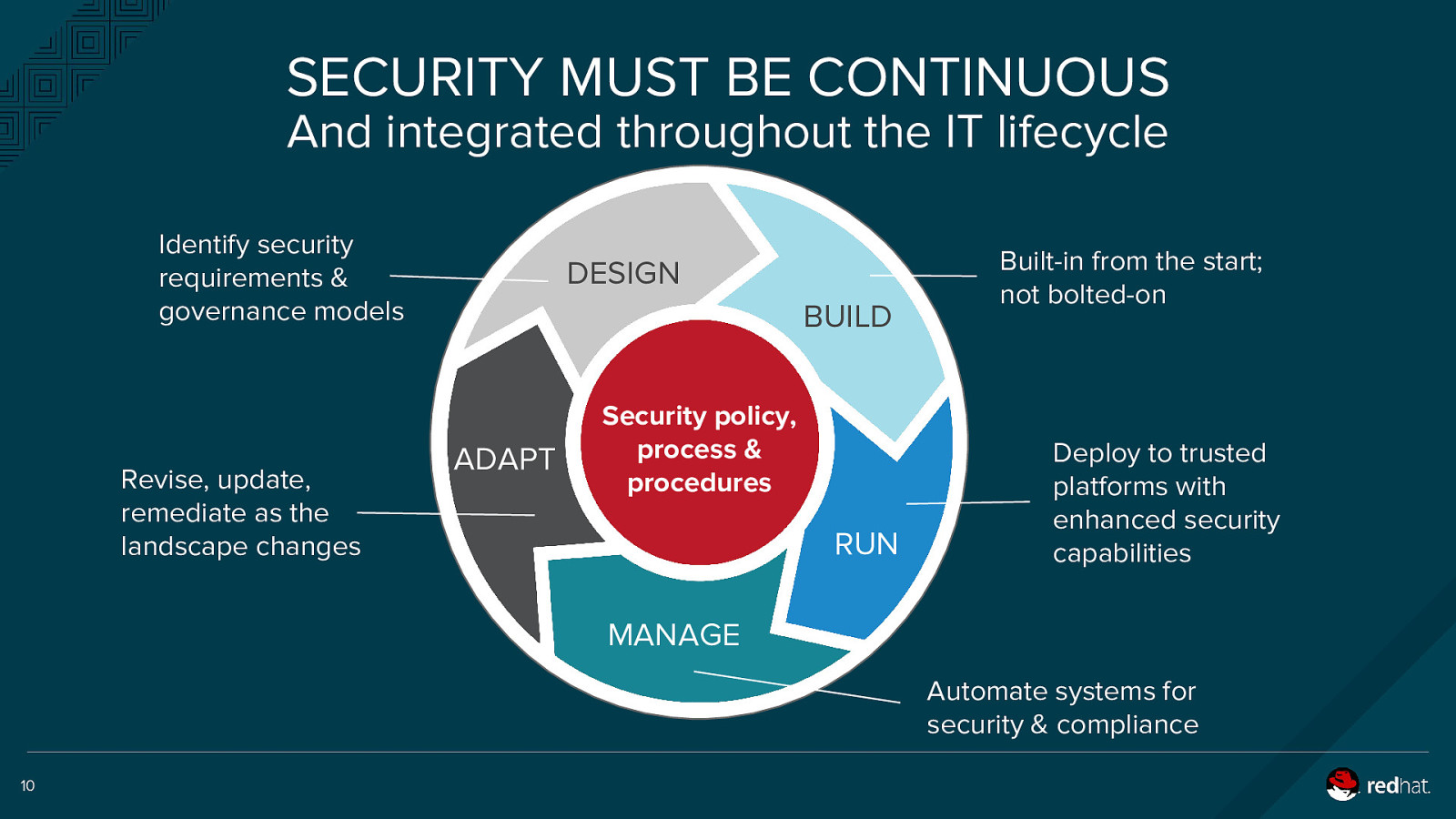
SECURITY MUST BE CONTINUOUS And integrated throughout the IT lifecycle Identify security requirements & governance models Revise, update, remediate as the landscape changes DESIGN BUILD ADAPT Security policy, process & procedures RUN Built-in from the start; not bolted-on Deploy to trusted platforms with enhanced security capabilities MANAGE Automate systems for security & compliance 10
Slide 11
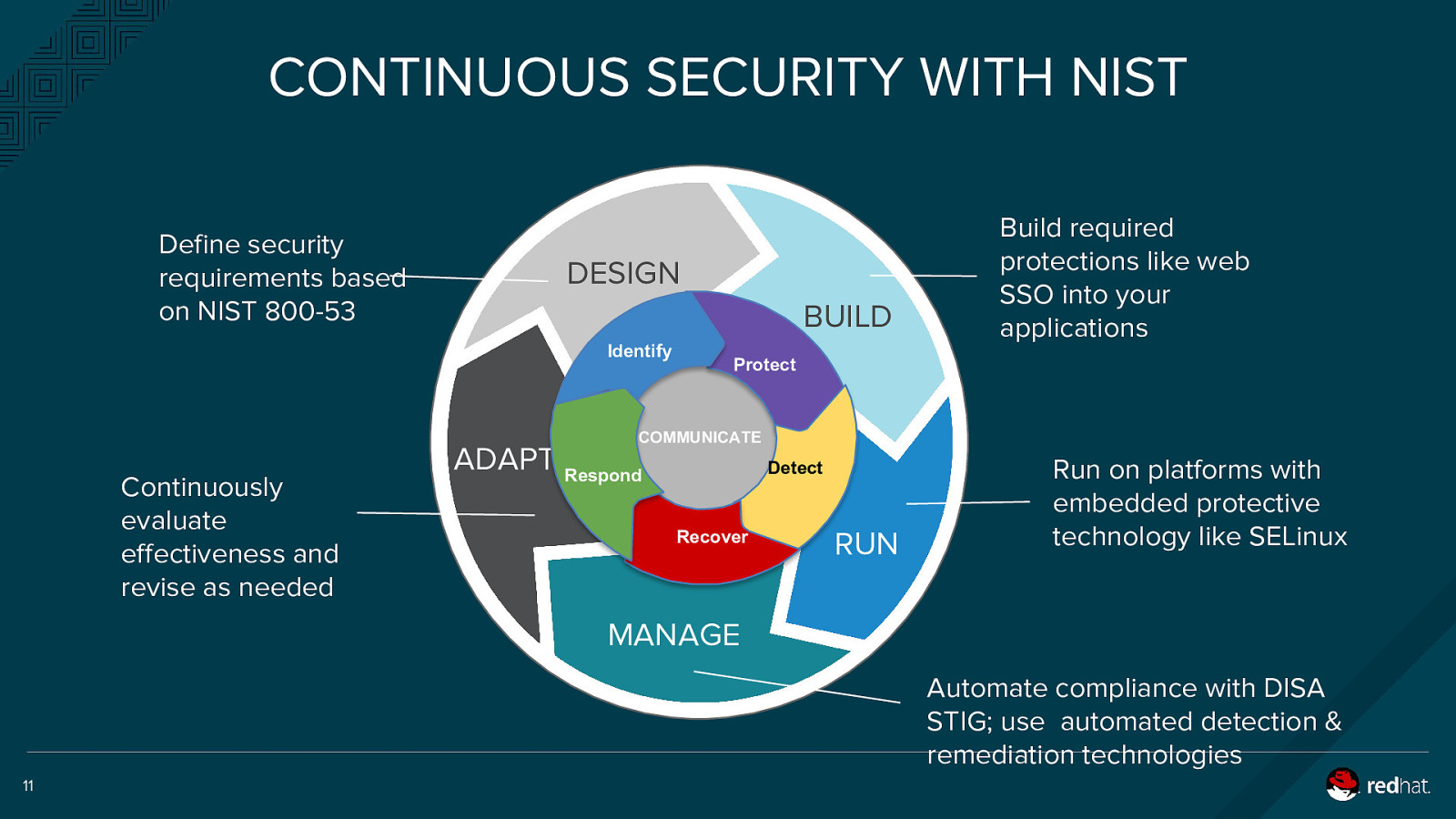
CONTINUOUS SECURITY WITH NIST Define security requirements based on NIST 800-53 DESIGN BUILD Identify Build required protections like web SSO into your applications Protect COMMUNICATE Continuously evaluate effectiveness and revise as needed ADAPT Respond Detect Recover RUN Run on platforms with embedded protective technology like SELinux MANAGE Automate compliance with DISA STIG; use automated detection & remediation technologies 11
Slide 12
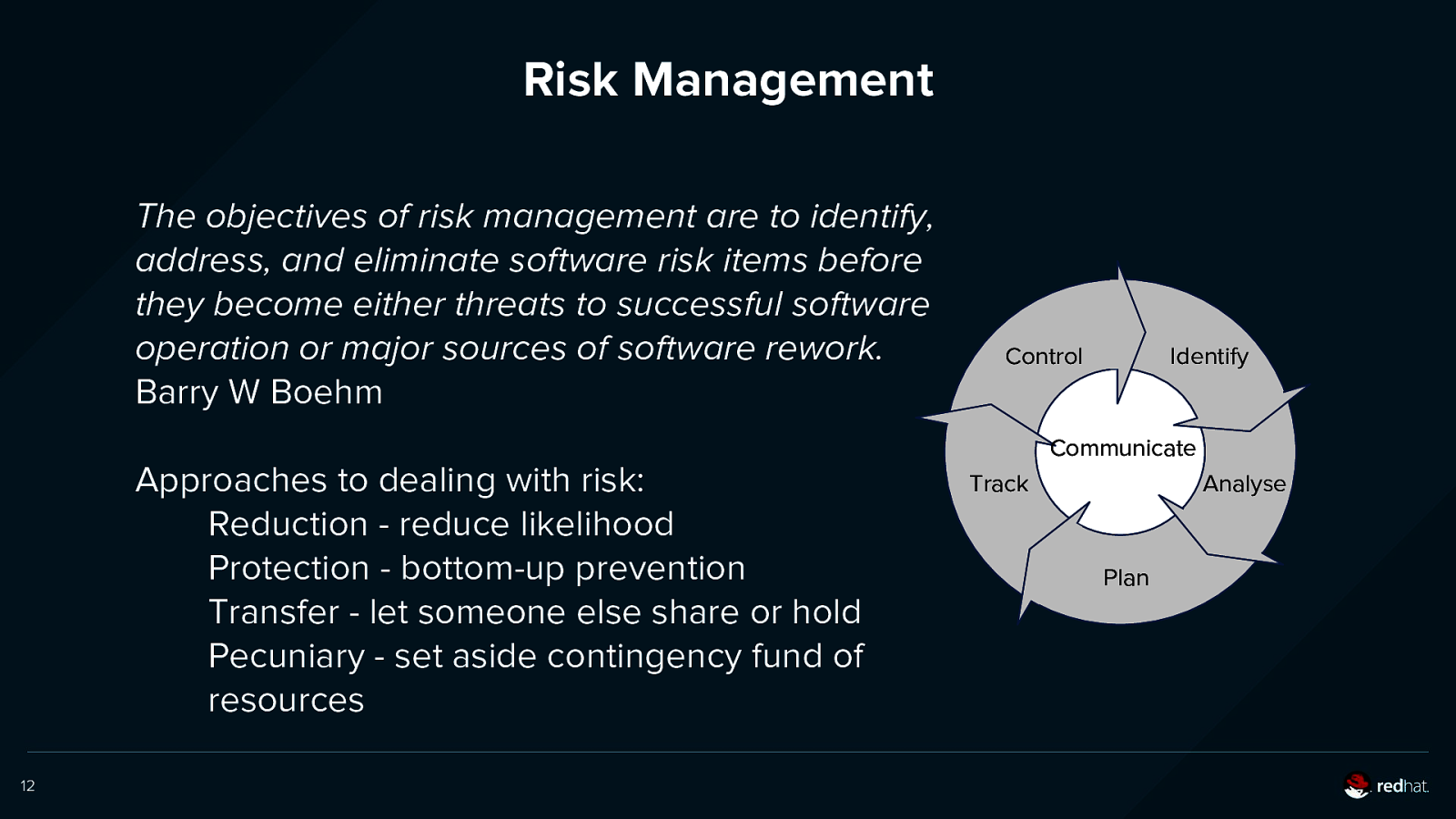
Risk Management The objectives of risk management are to identify, address, and eliminate software risk items before they become either threats to successful software operation or major sources of software rework. Barry W Boehm Control Identify Communicate Approaches to dealing with risk: Reduction - reduce likelihood Protection - bottom-up prevention Transfer - let someone else share or hold Pecuniary - set aside contingency fund of resources 12 Track Analyse Plan
Slide 13
WHY OPEN SOURCE?
Slide 14
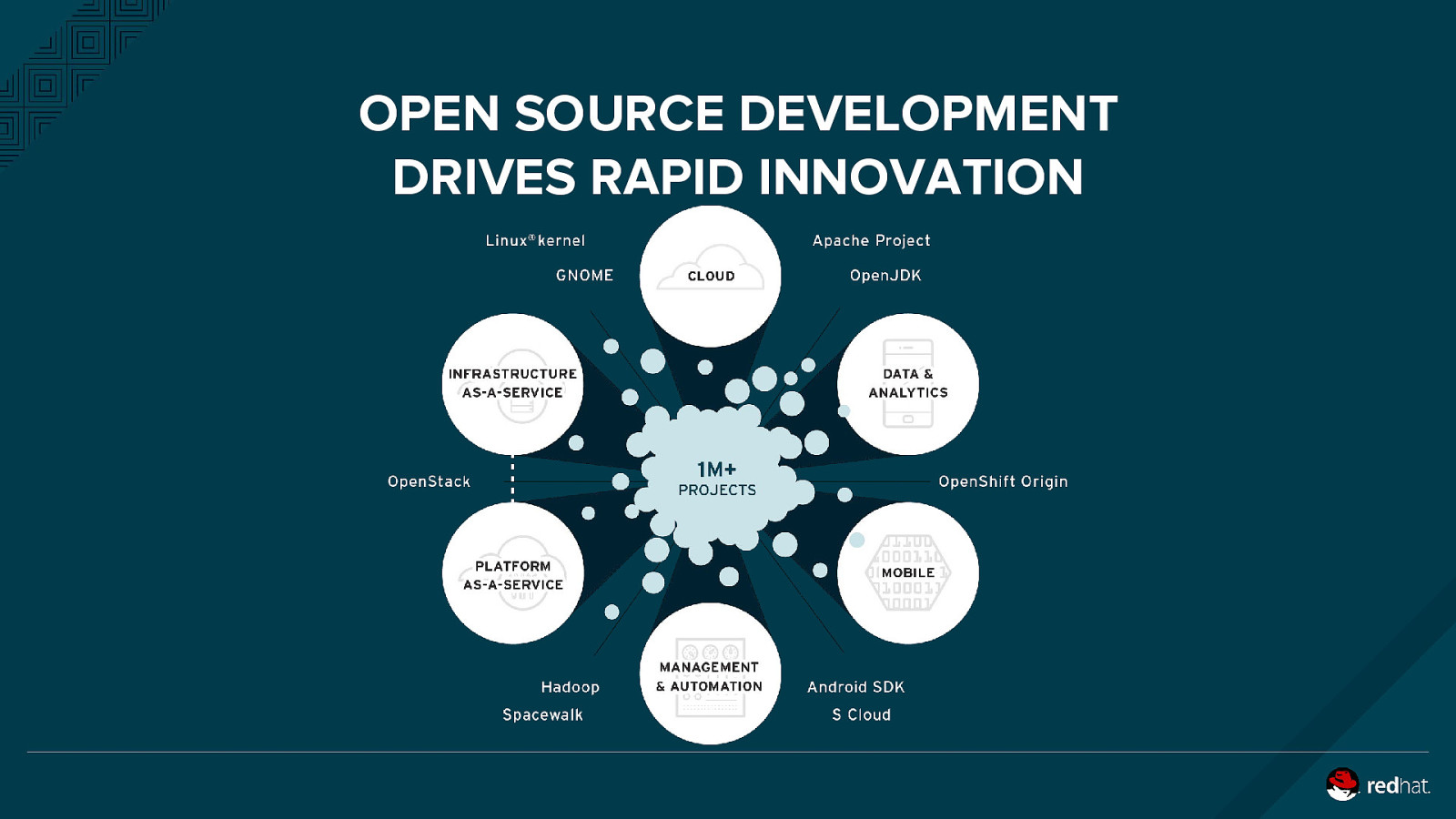
OPEN SOURCE DEVELOPMENT DRIVES RAPID INNOVATION
Slide 15
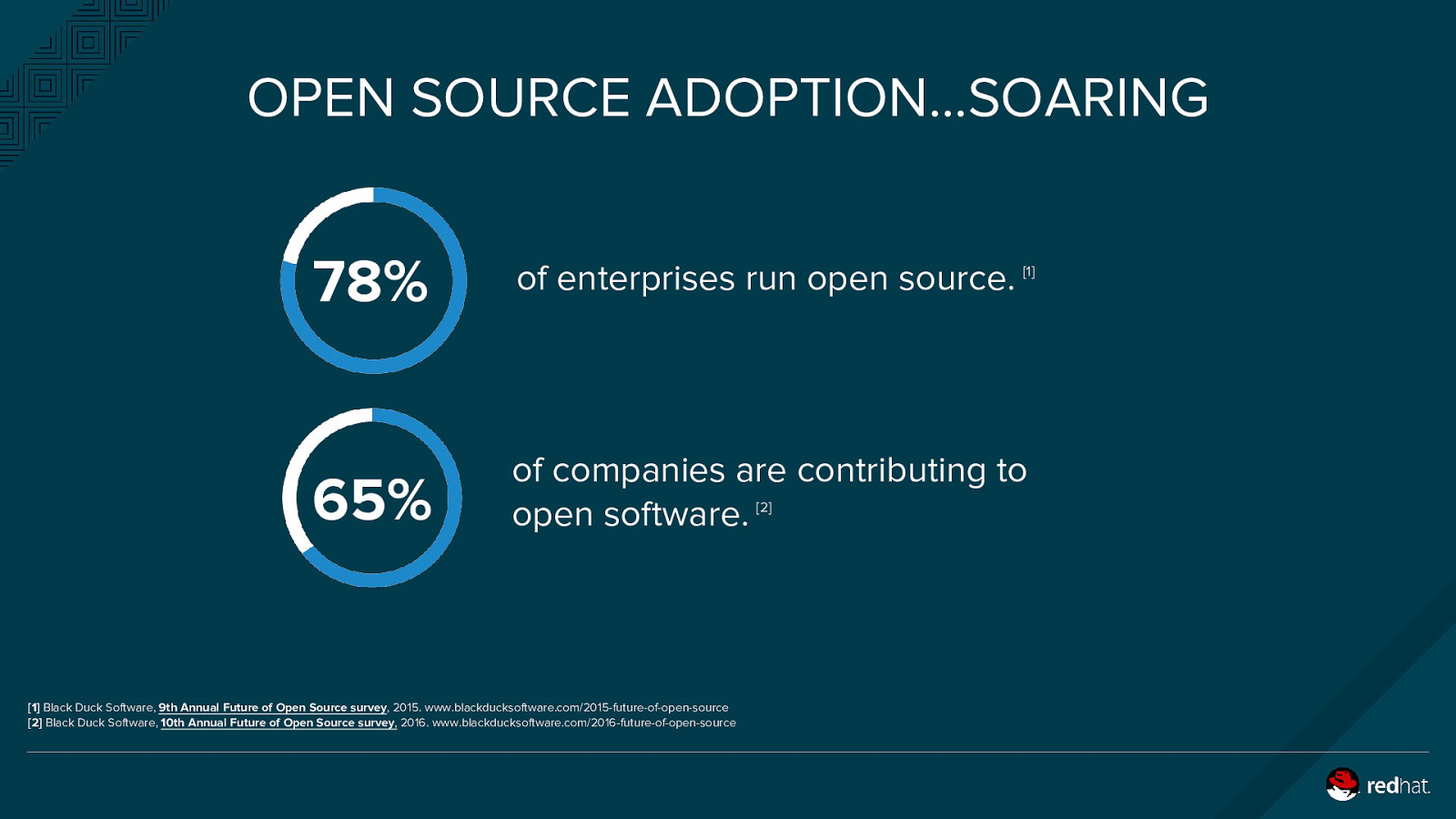
OPEN SOURCE ADOPTION…SOARING 78% of enterprises run open source. 65% of companies are contributing to open software. [1] Black Duck Software, 9th Annual Future of Open Source survey, 2015. www.blackducksoftware.com/2015-future-of-open-source [2] Black Duck Software, 10th Annual Future of Open Source survey, 2016. www.blackducksoftware.com/2016-future-of-open-source [2] [1]
Slide 16
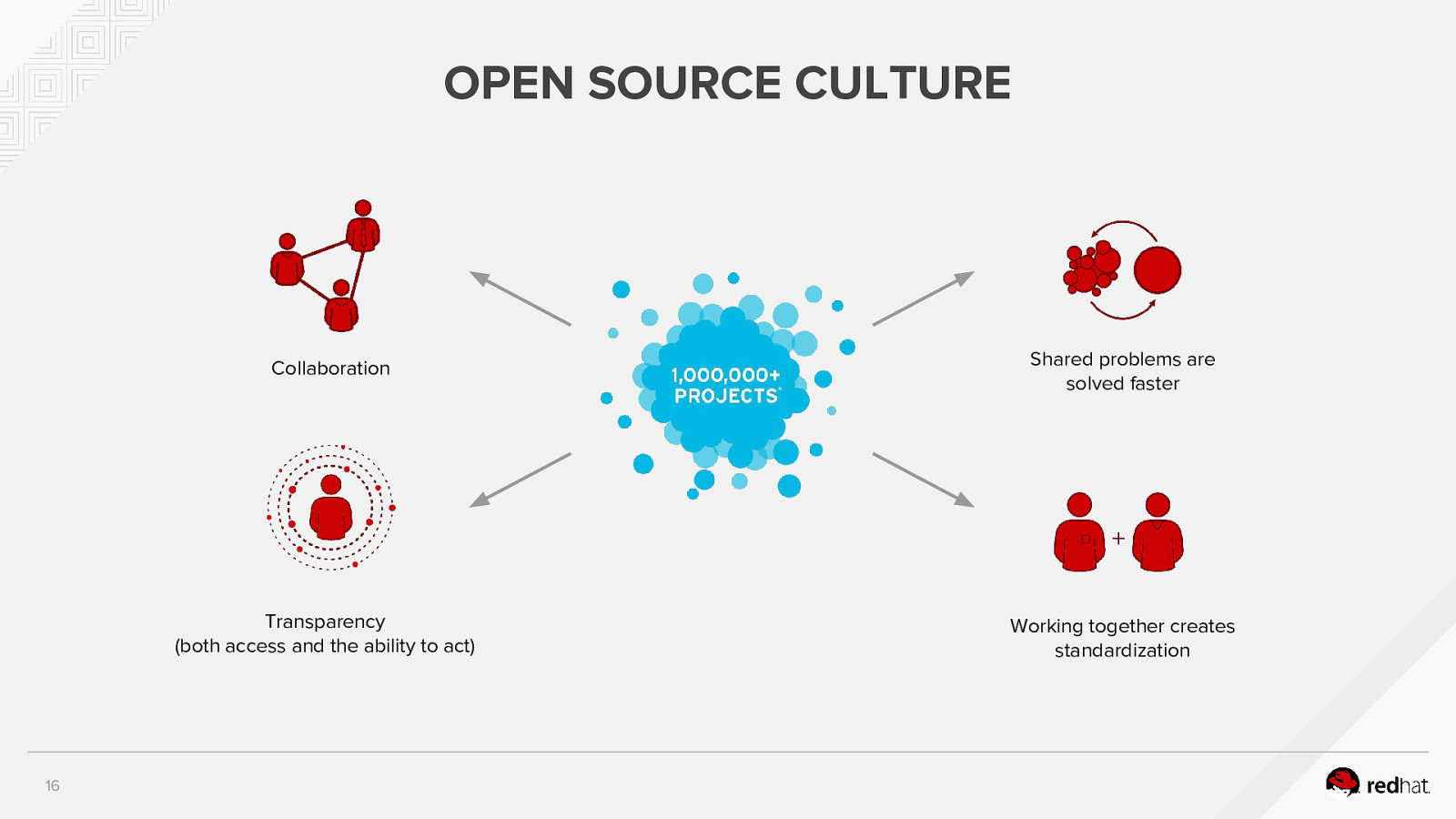
OPEN SOURCE CULTURE Collaboration * Transparency (both access and the ability to act) 16 Shared problems are solved faster Working together creates standardization
Slide 17

AGILITY, WITH SECURITY
Slide 18
The Problem Applications require complicated installation and integration every time they are deployed 18
Slide 19
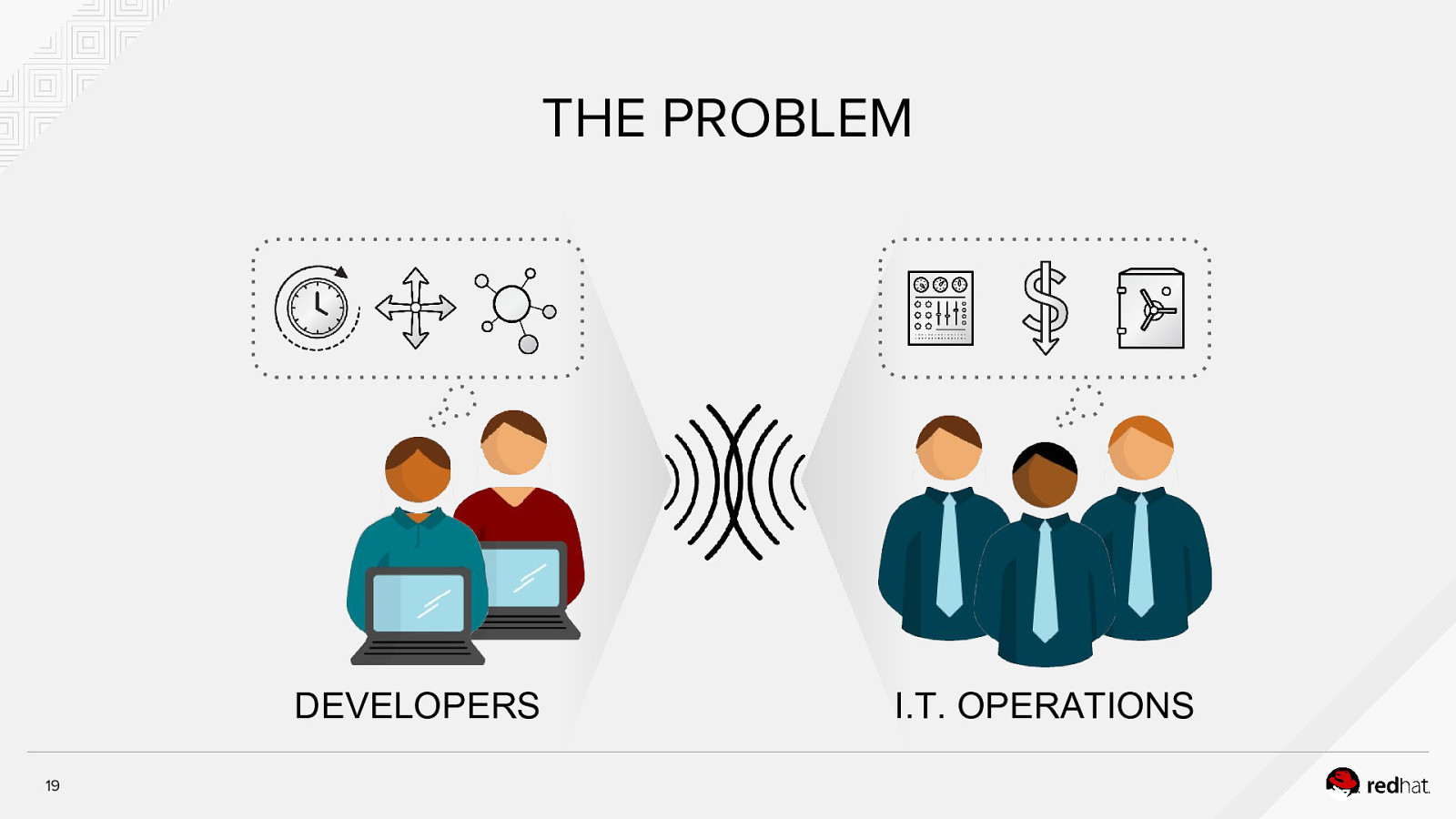
THE PROBLEM DEVELOPERS 19 I.T. OPERATIONS
Slide 20
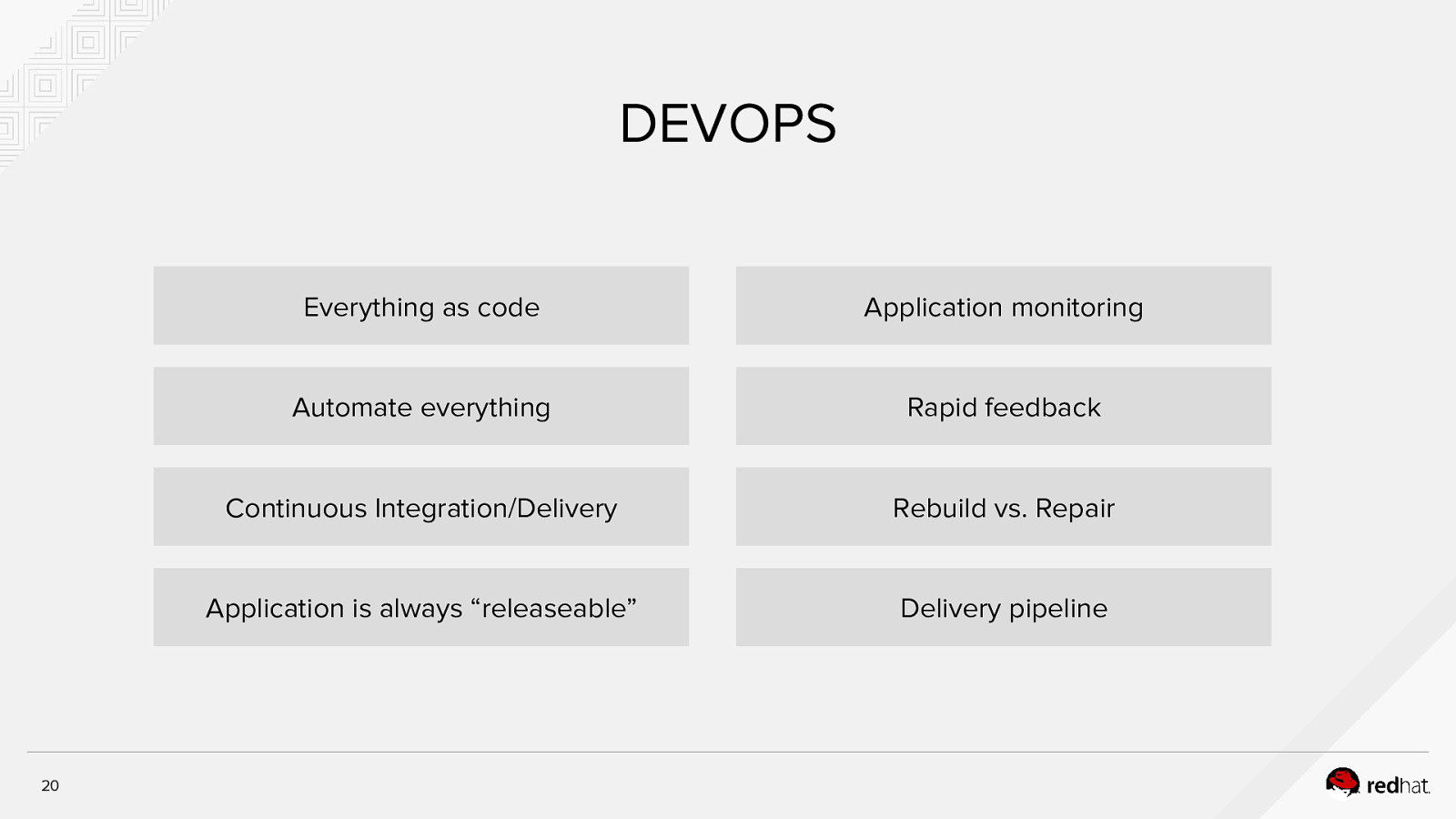
DEVOPS 20 Everything as code Application monitoring Automate everything Rapid feedback Continuous Integration/Delivery Rebuild vs. Repair Application is always “releaseable” Delivery pipeline
Slide 21
A Solution Adopting a container strategy will allow applications to be easily shared and deployed. 21
Slide 22
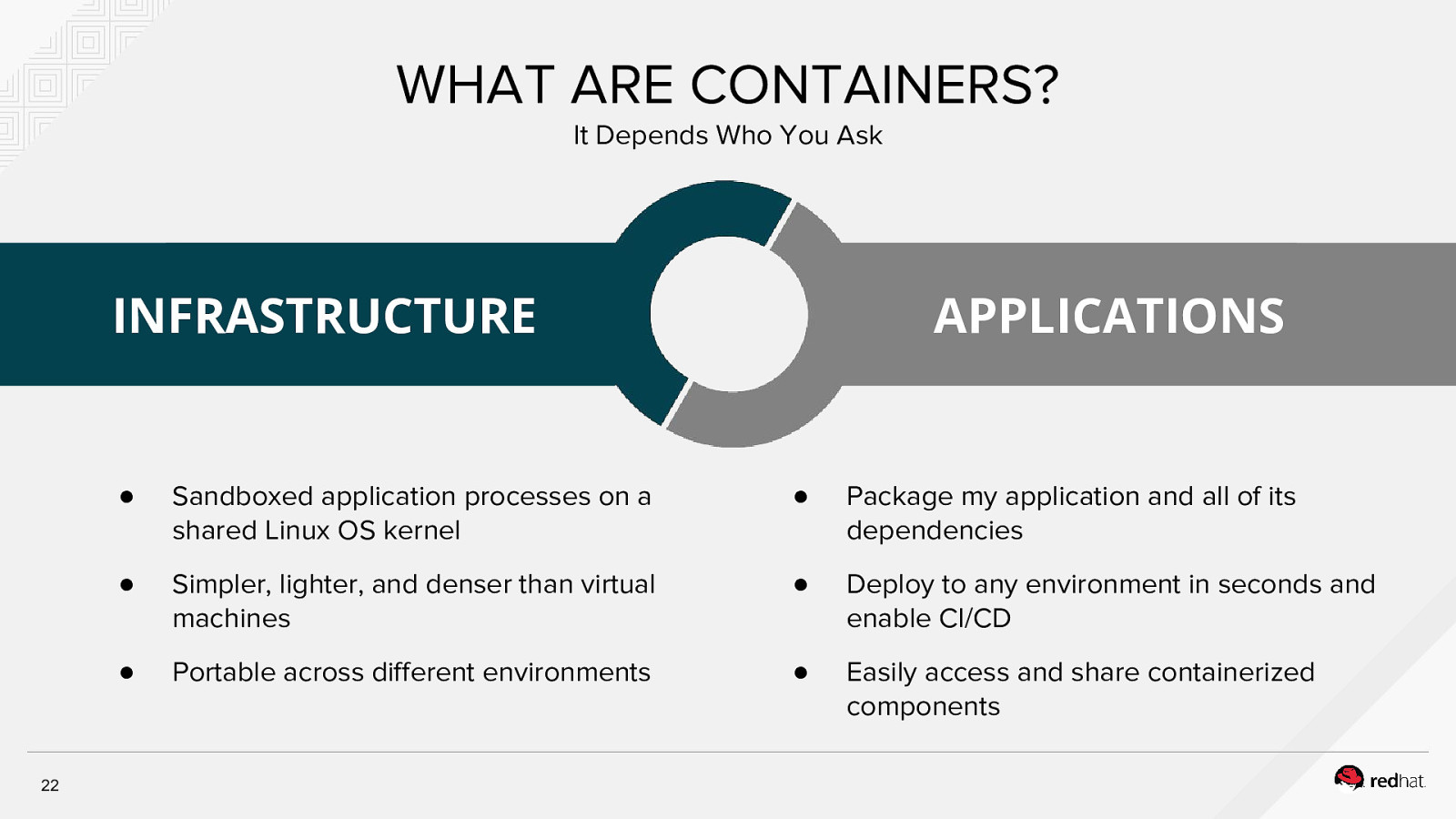
WHAT ARE CONTAINERS? It Depends Who You Ask APPLICATIONS INFRASTRUCTURE 22 ● Sandboxed application processes on a shared Linux OS kernel ● Package my application and all of its dependencies ● Simpler, lighter, and denser than virtual machines ● Deploy to any environment in seconds and enable CI/CD ● Portable across different environments ● Easily access and share containerized components
Slide 23
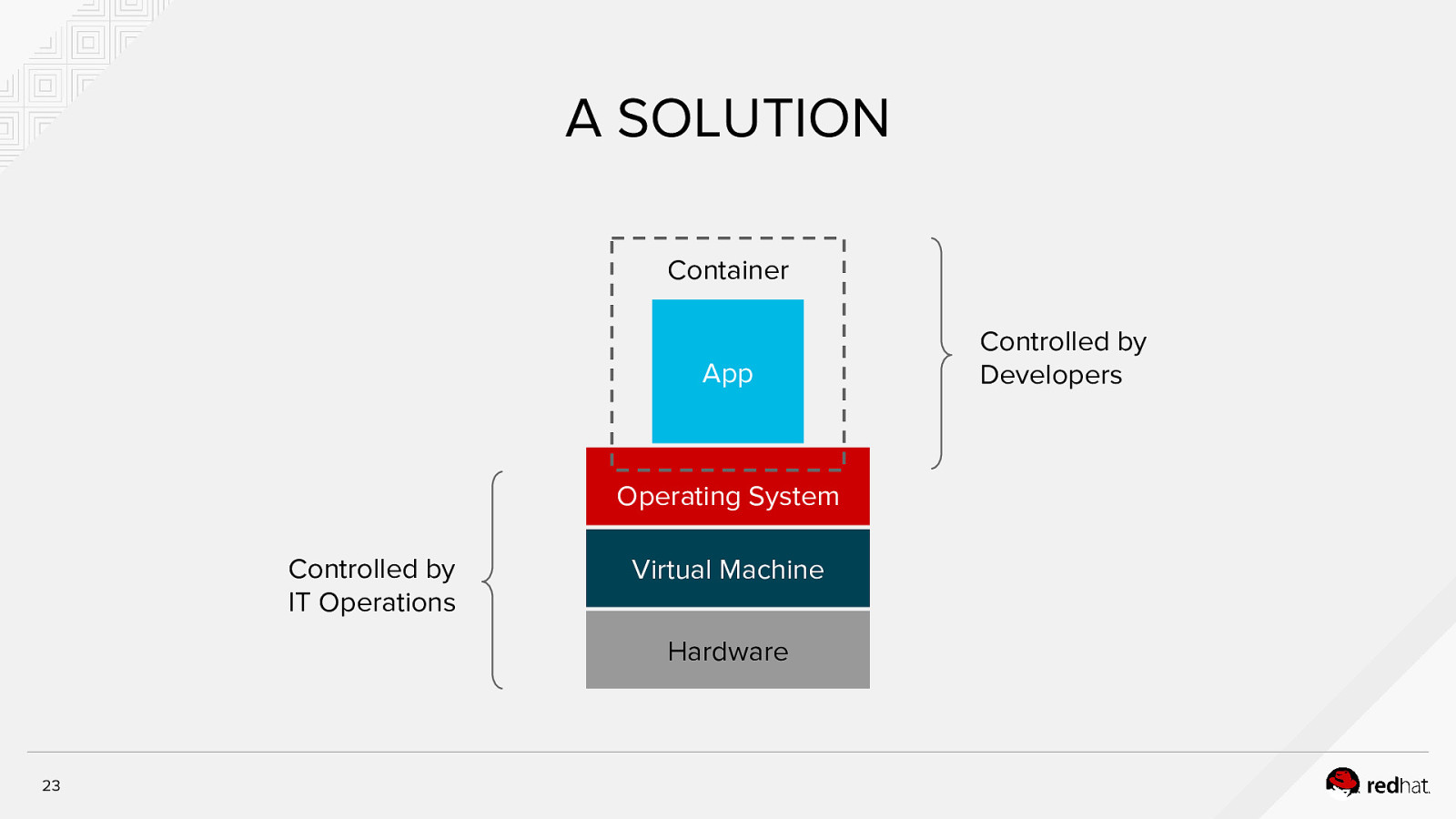
A SOLUTION Container App Operating System Controlled by IT Operations Virtual Machine Hardware 23 Controlled by Developers
Slide 24
A SOLUTION DEVELOPERS 24 I.T. OPERATIONS
Slide 25
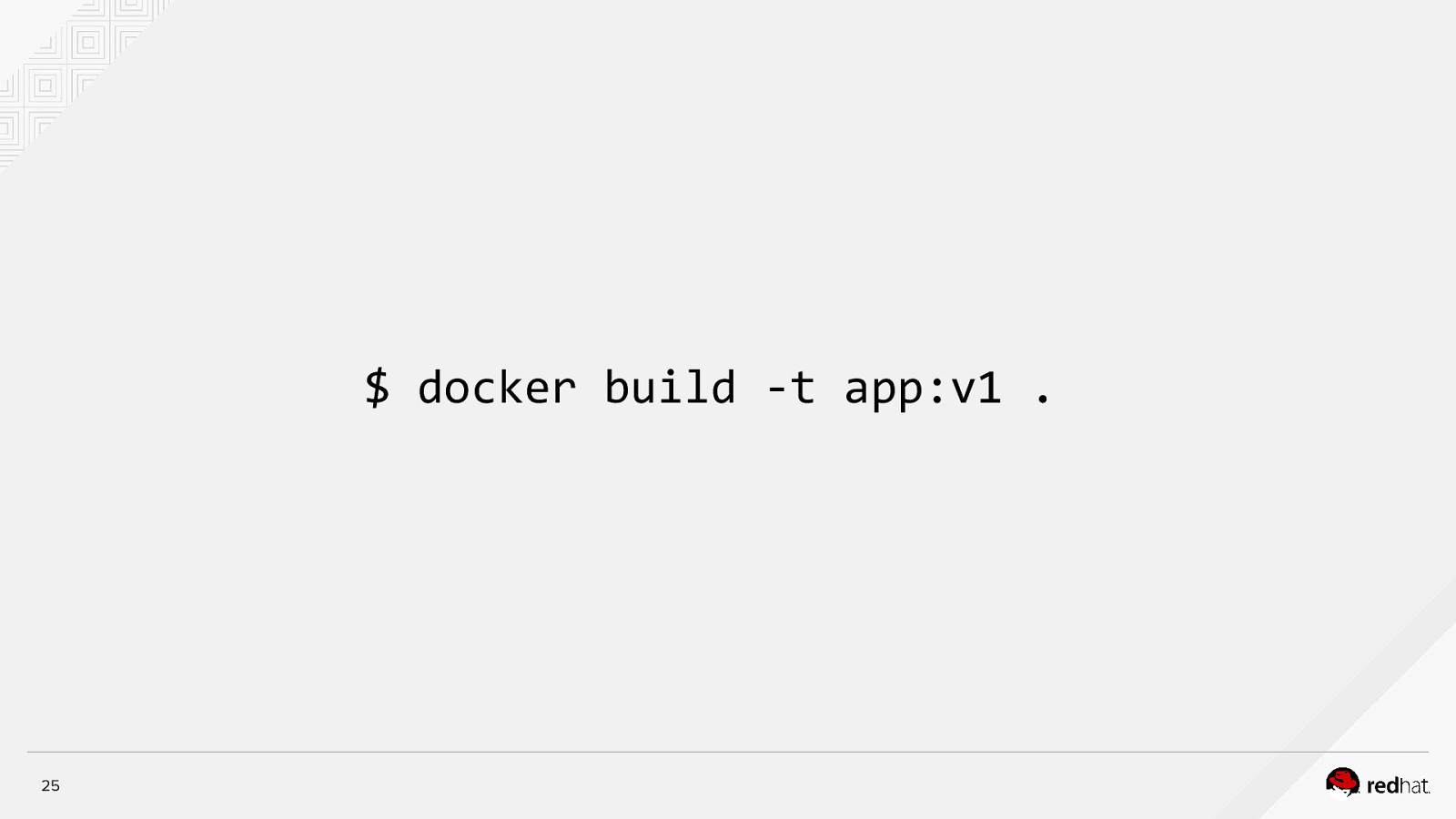
$ docker build -t app:v1 . 25
Slide 26
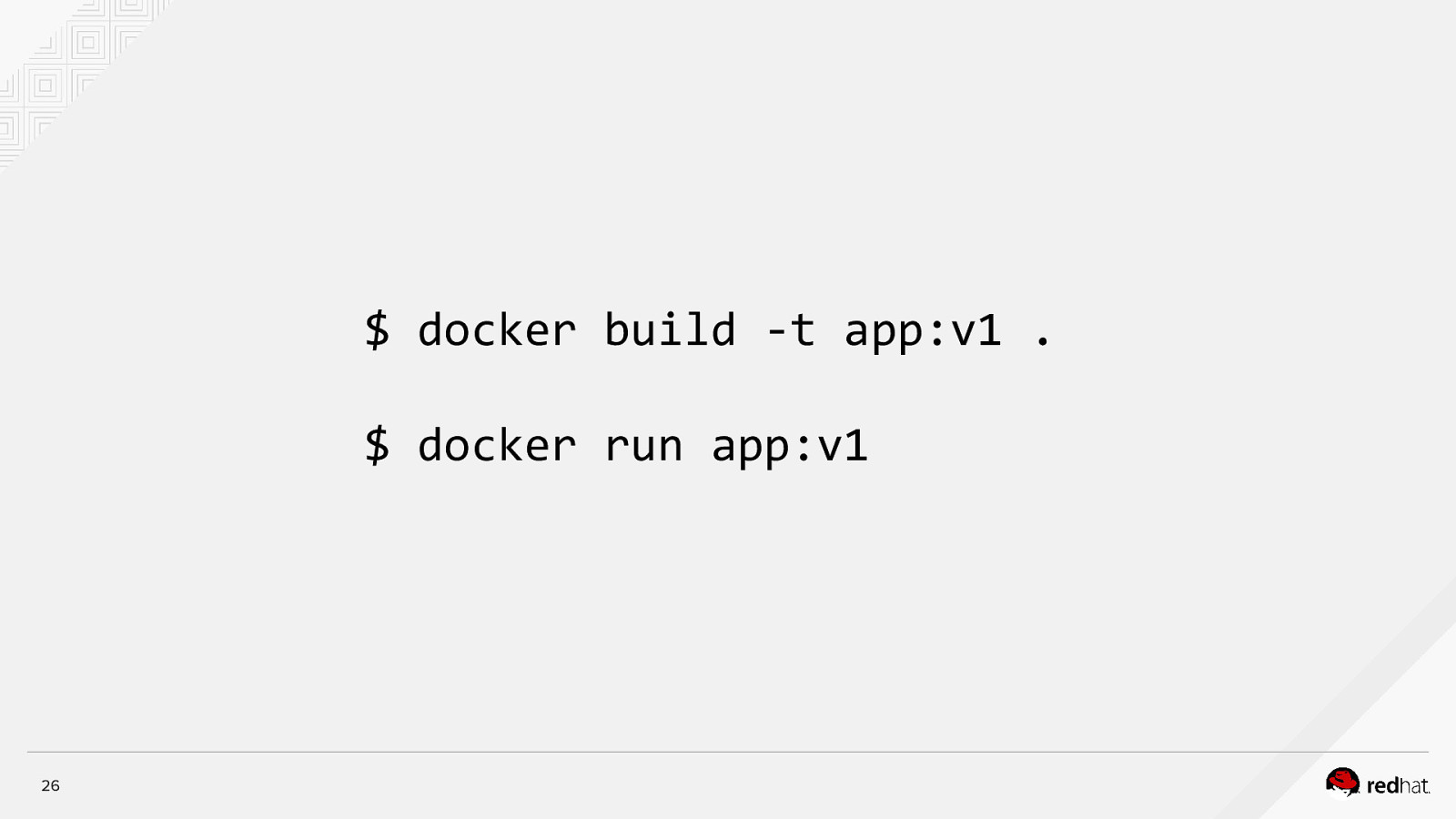
$ docker build -t app:v1 . $ docker run app:v1 26
Slide 27
physical virtual private cloud public cloud 27
Slide 28
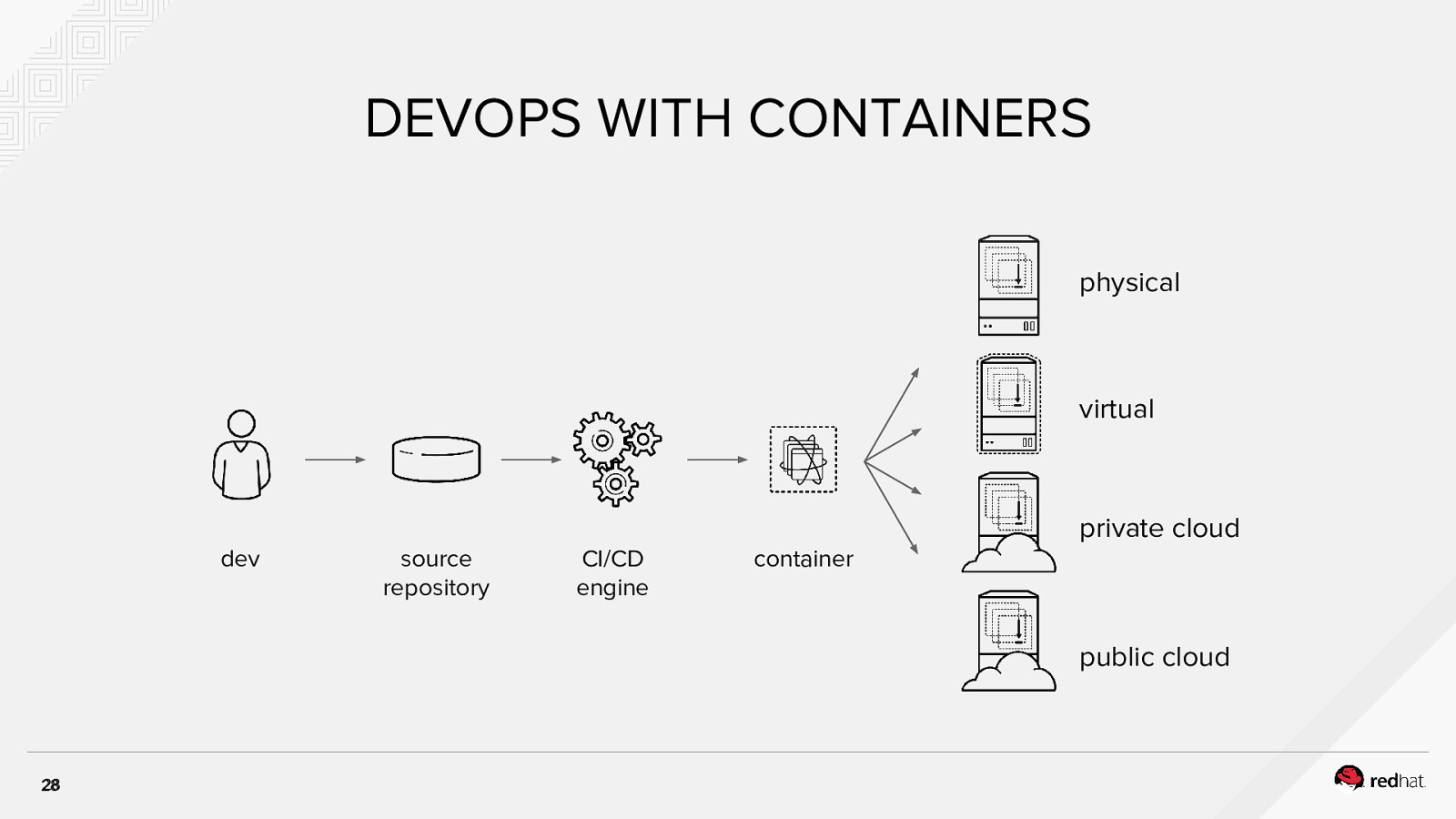
DEVOPS WITH CONTAINERS physical virtual private cloud dev source repository CI/CD engine container public cloud 28
Slide 29
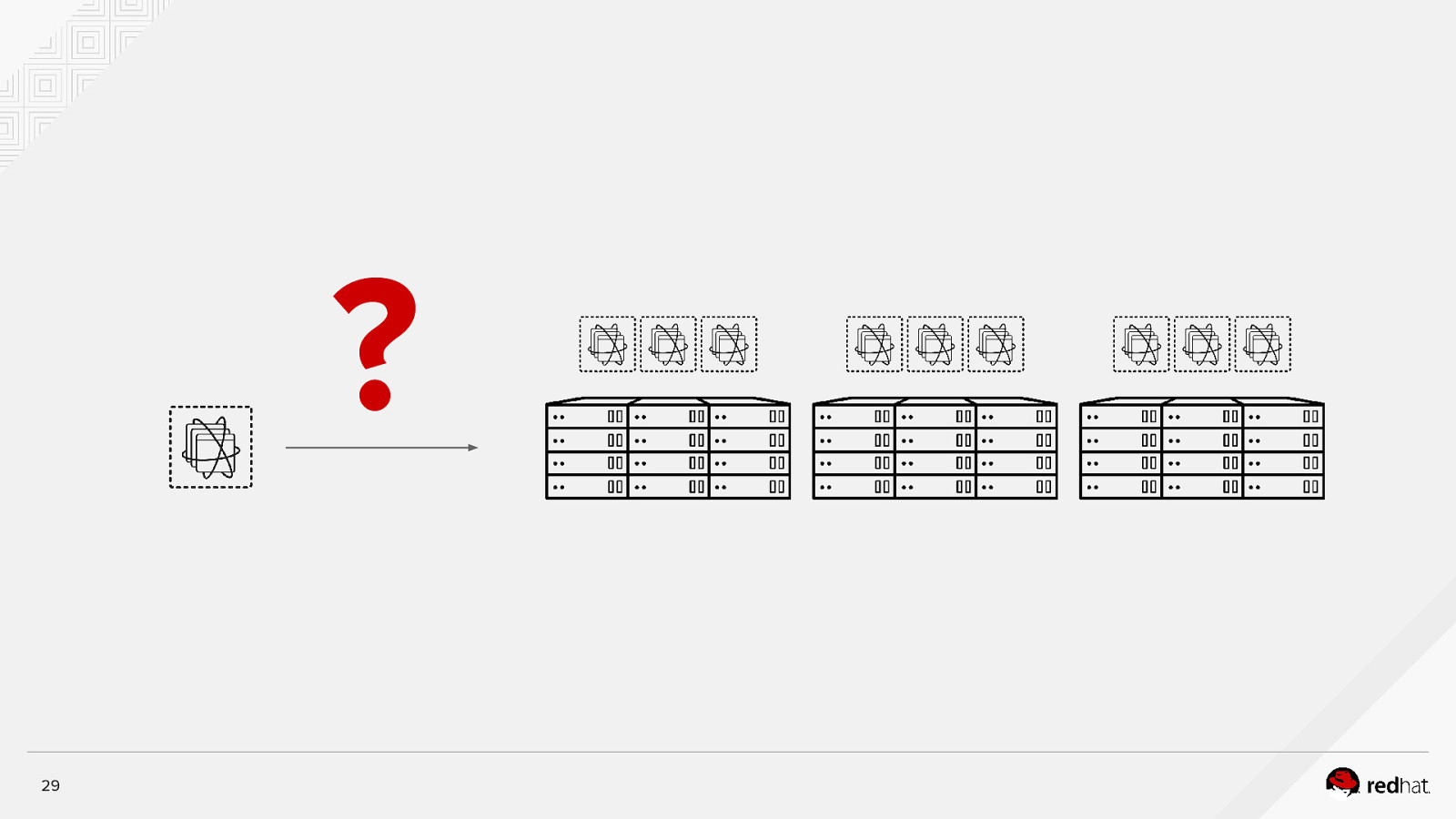
? 29
Slide 30
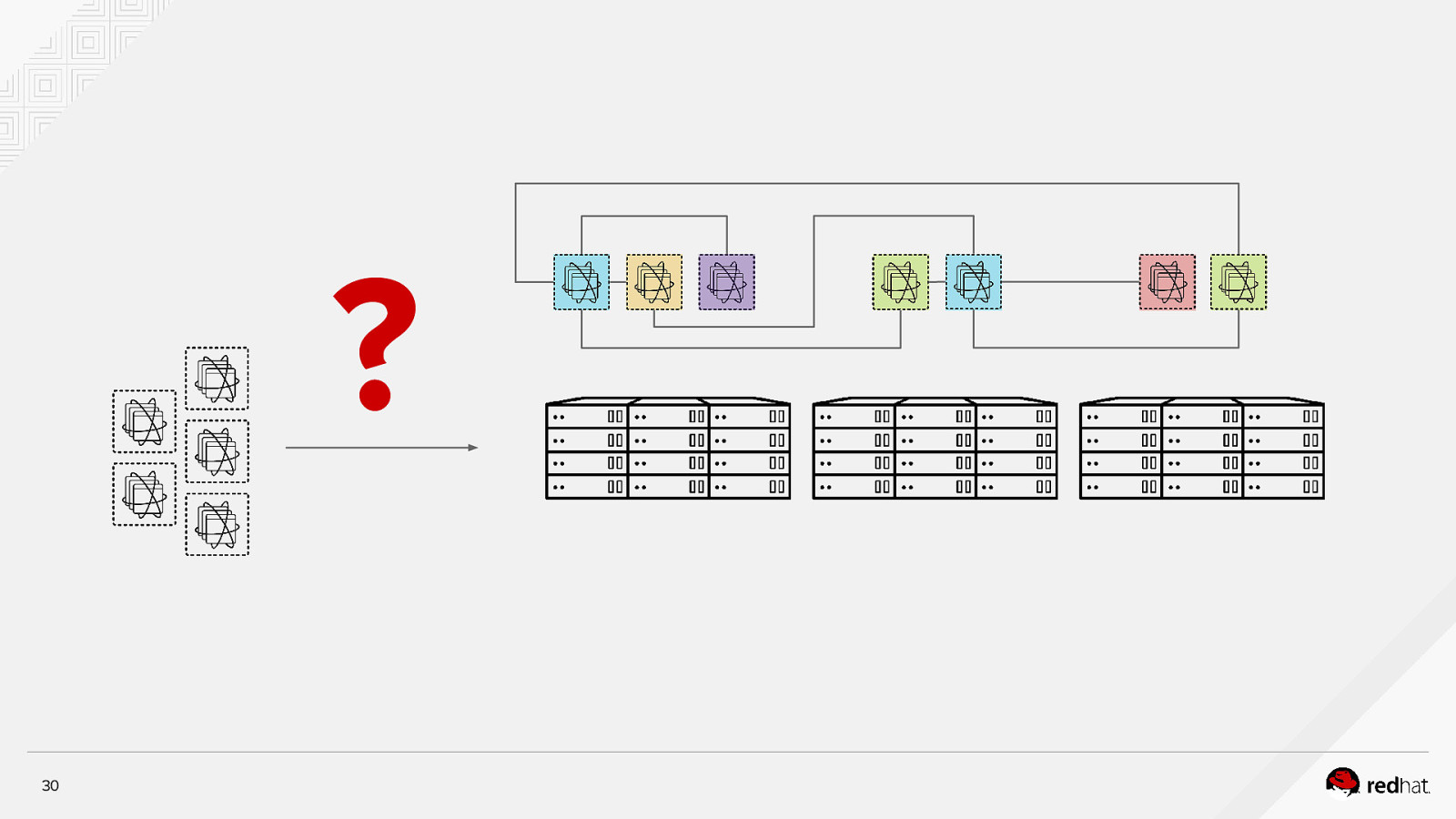
? 30
Slide 31

WE NEED MORE THAN JUST CONTAINERS 31 Scheduling Security Decide where to deploy containers Control who can do what Lifecycle and health Scaling Keep containers running despite failures Scale containers up and down Discovery Persistence Find other containers on the network Survive data beyond container lifecycle Monitoring Aggregation Visibility into running containers Compose apps from multiple containers
Slide 32

Kubernetes is an open-source system for automating deployment, operations, and scaling of containerized applications across multiple hosts kubernetes 32
Slide 33
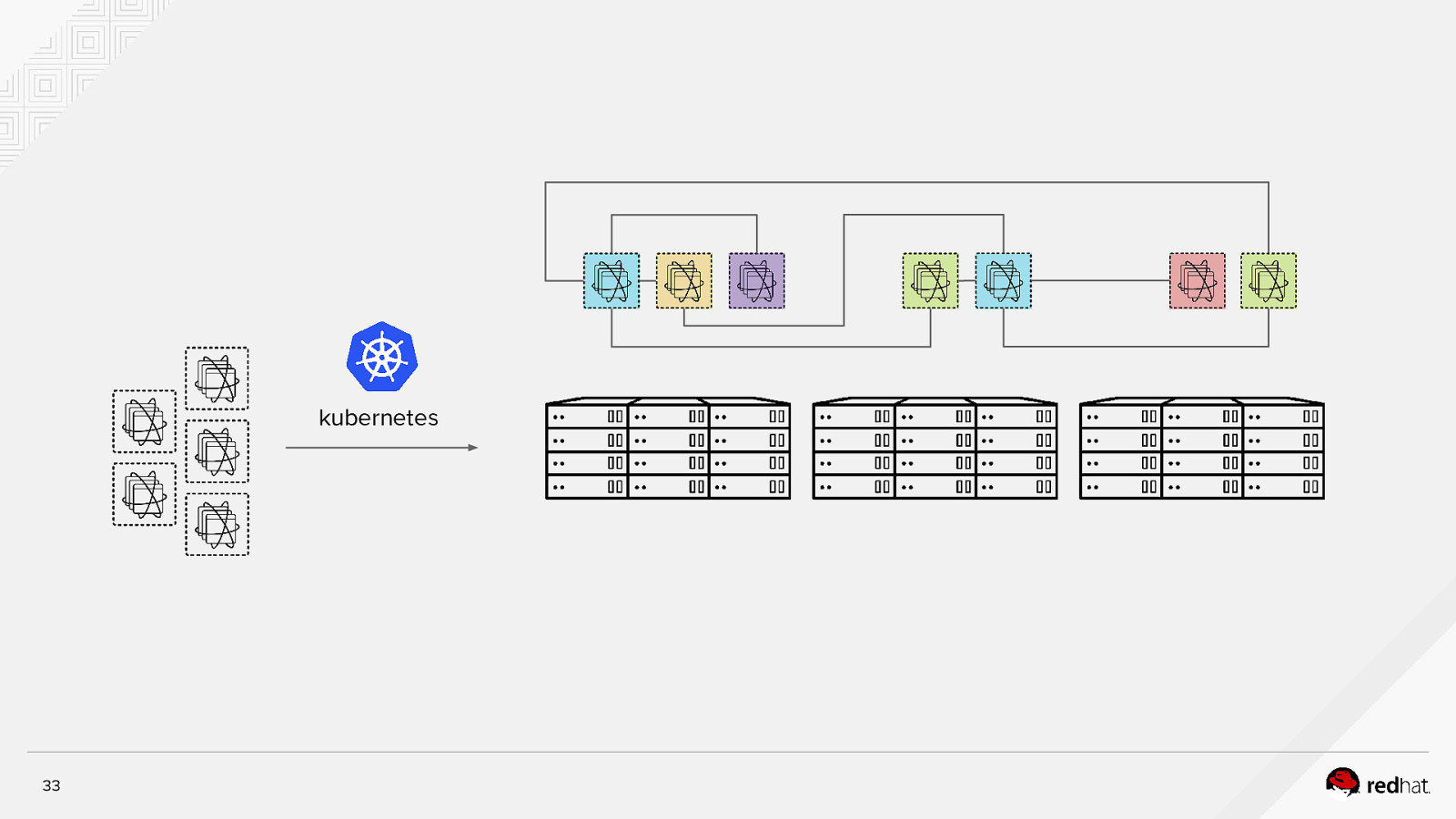
kubernetes 33
Slide 34
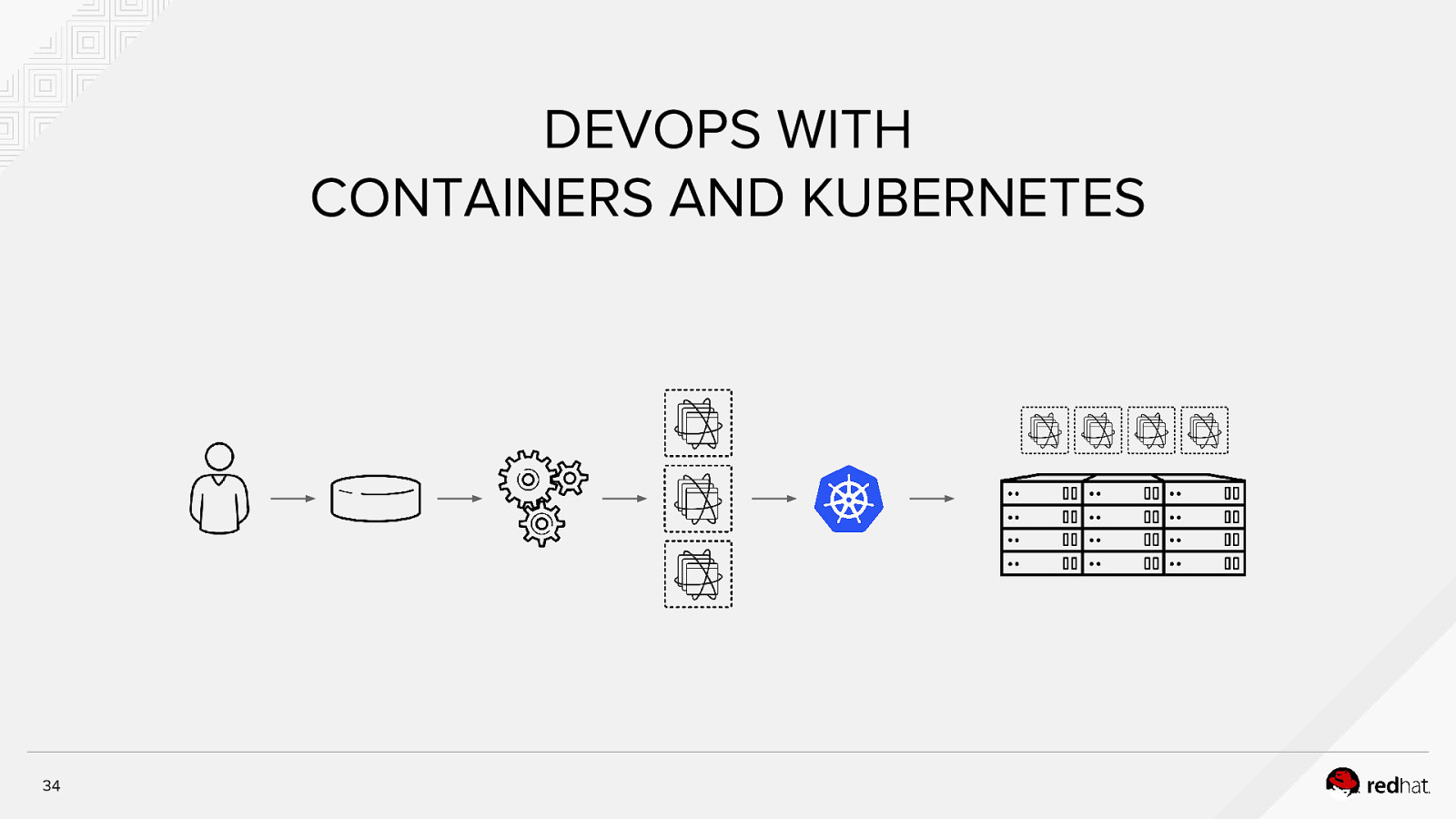
DEVOPS WITH CONTAINERS AND KUBERNETES 34
Slide 35

INDUSTRY CONVERGING ON KUBERNETES 35
Slide 36

INDUSTRY CONVERGING ON KUBERNETES 36
Slide 37
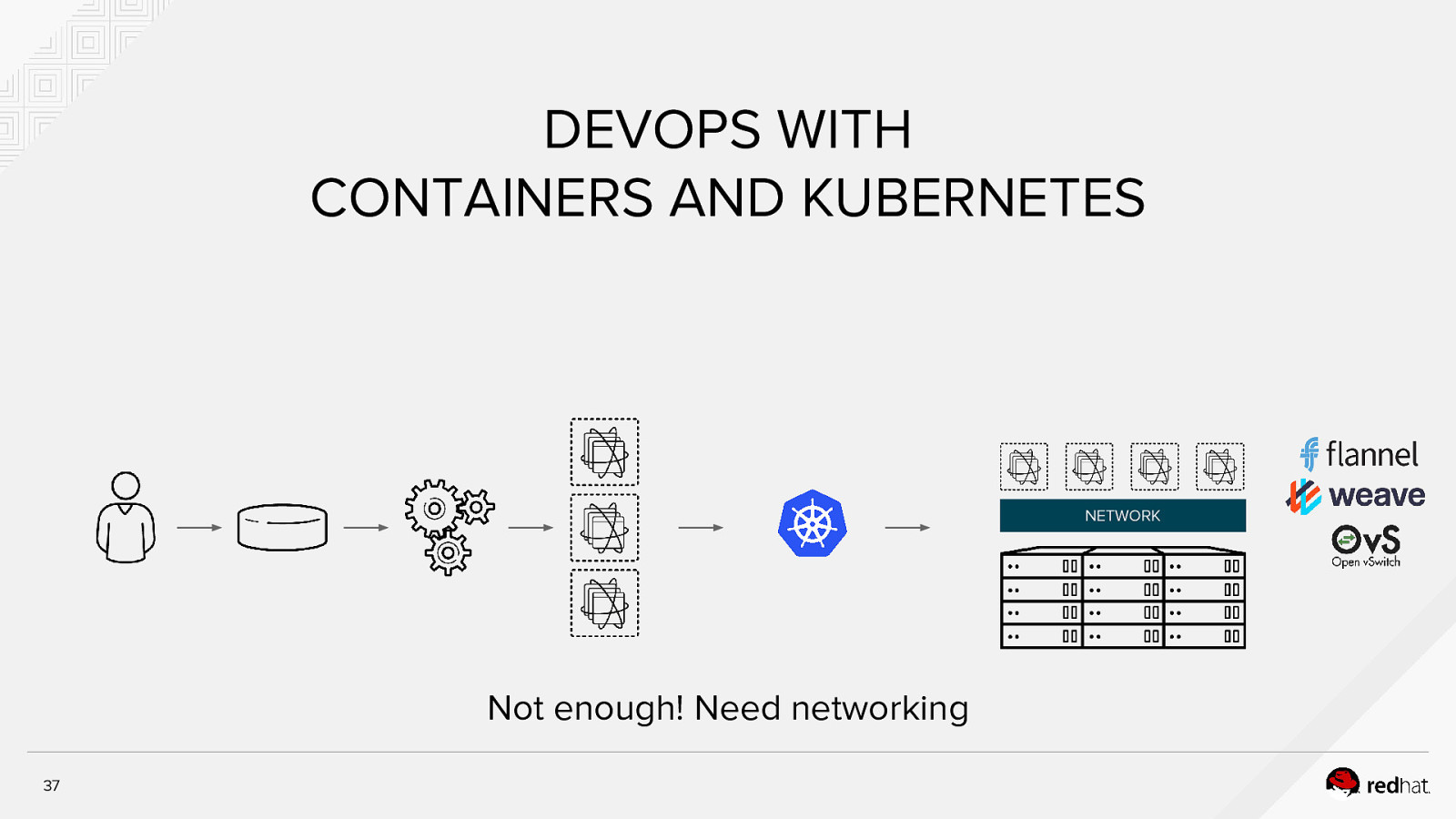
DEVOPS WITH CONTAINERS AND KUBERNETES NETWORK Not enough! Need networking 37
Slide 38
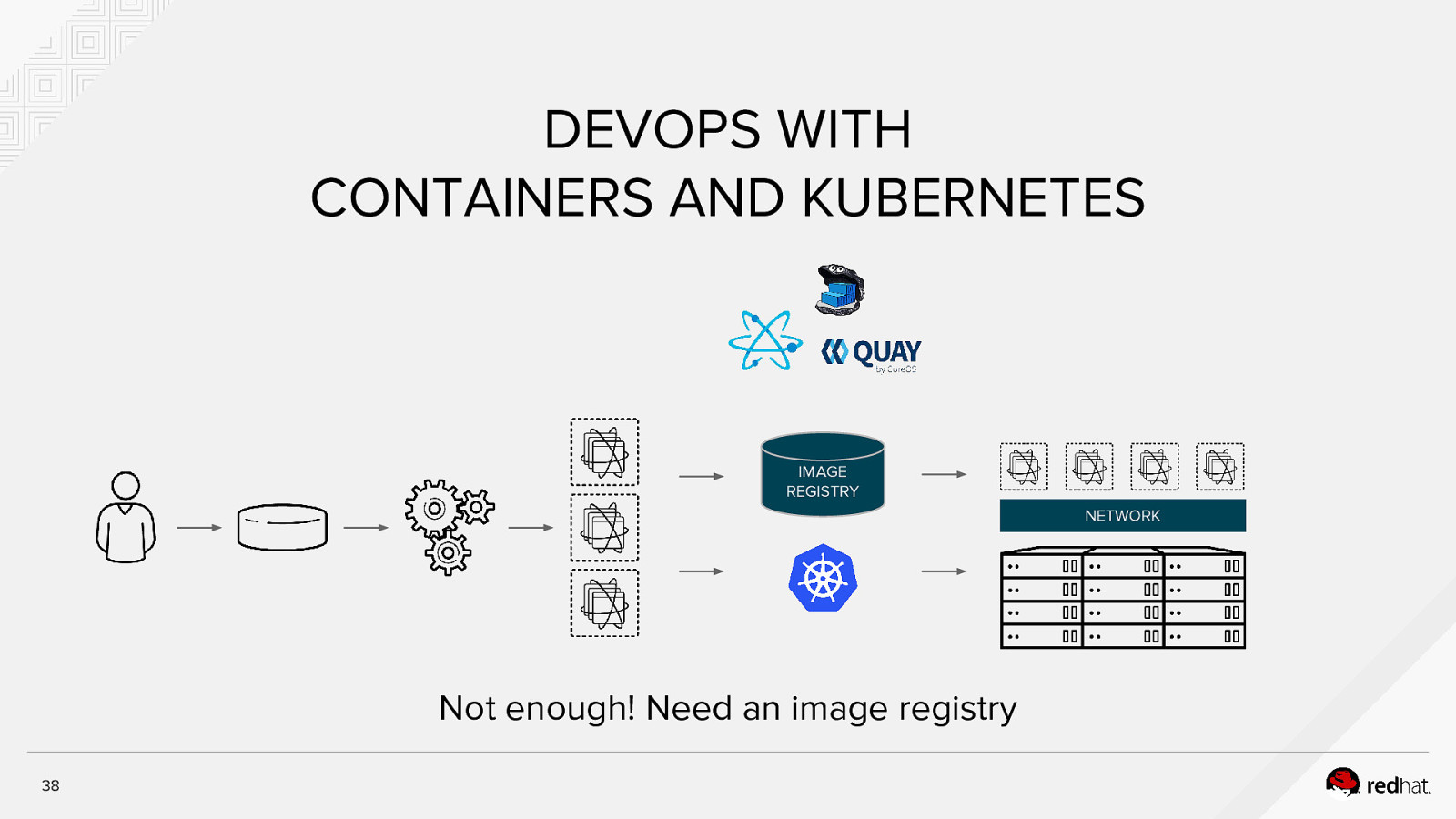
DEVOPS WITH CONTAINERS AND KUBERNETES IMAGE REGISTRY NETWORK Not enough! Need an image registry 38
Slide 39
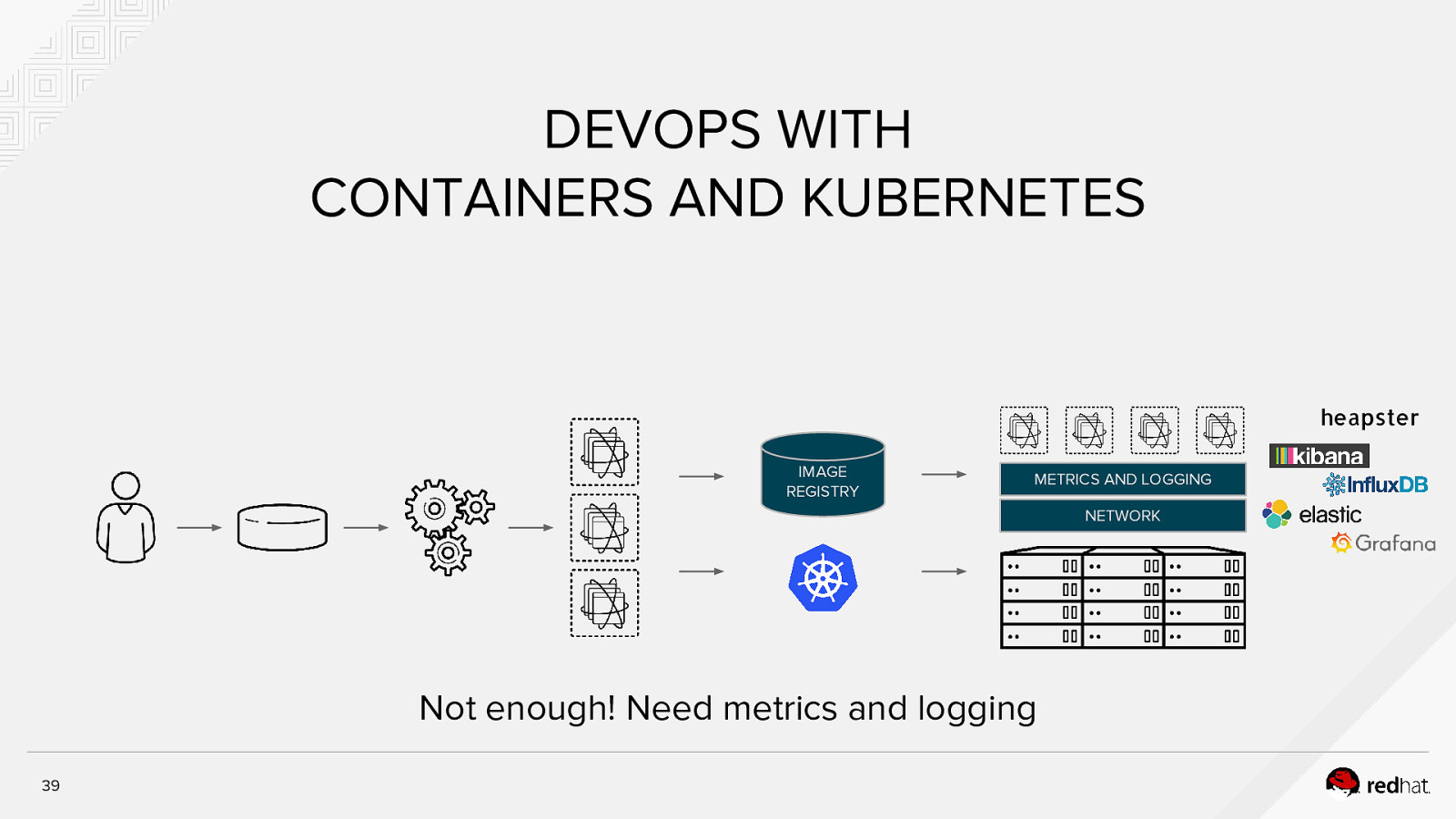
DEVOPS WITH CONTAINERS AND KUBERNETES heapster IMAGE REGISTRY METRICS AND LOGGING NETWORK Not enough! Need metrics and logging 39
Slide 40
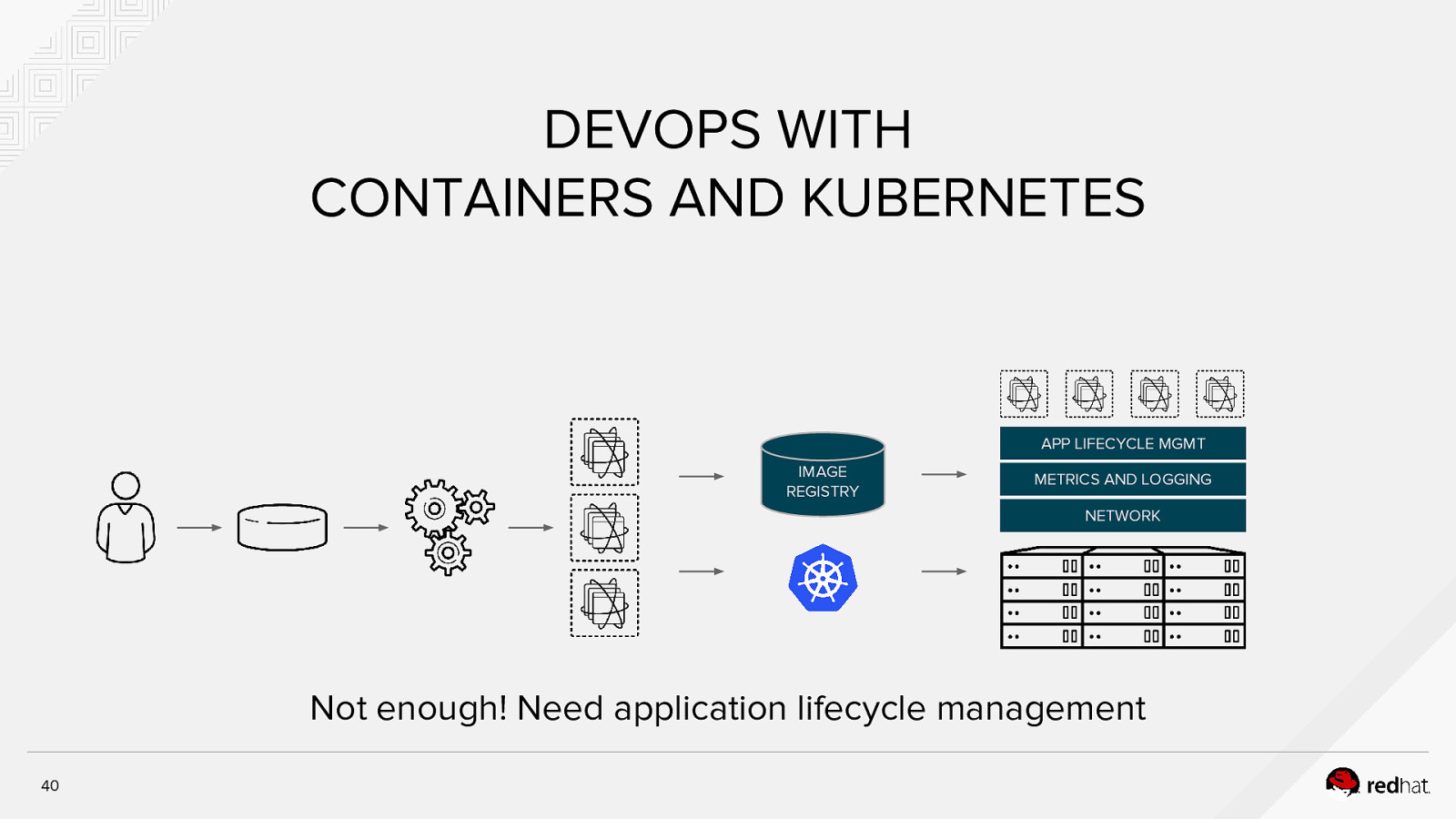
DEVOPS WITH CONTAINERS AND KUBERNETES APP LIFECYCLE MGMT IMAGE REGISTRY METRICS AND LOGGING NETWORK Not enough! Need application lifecycle management 40
Slide 41
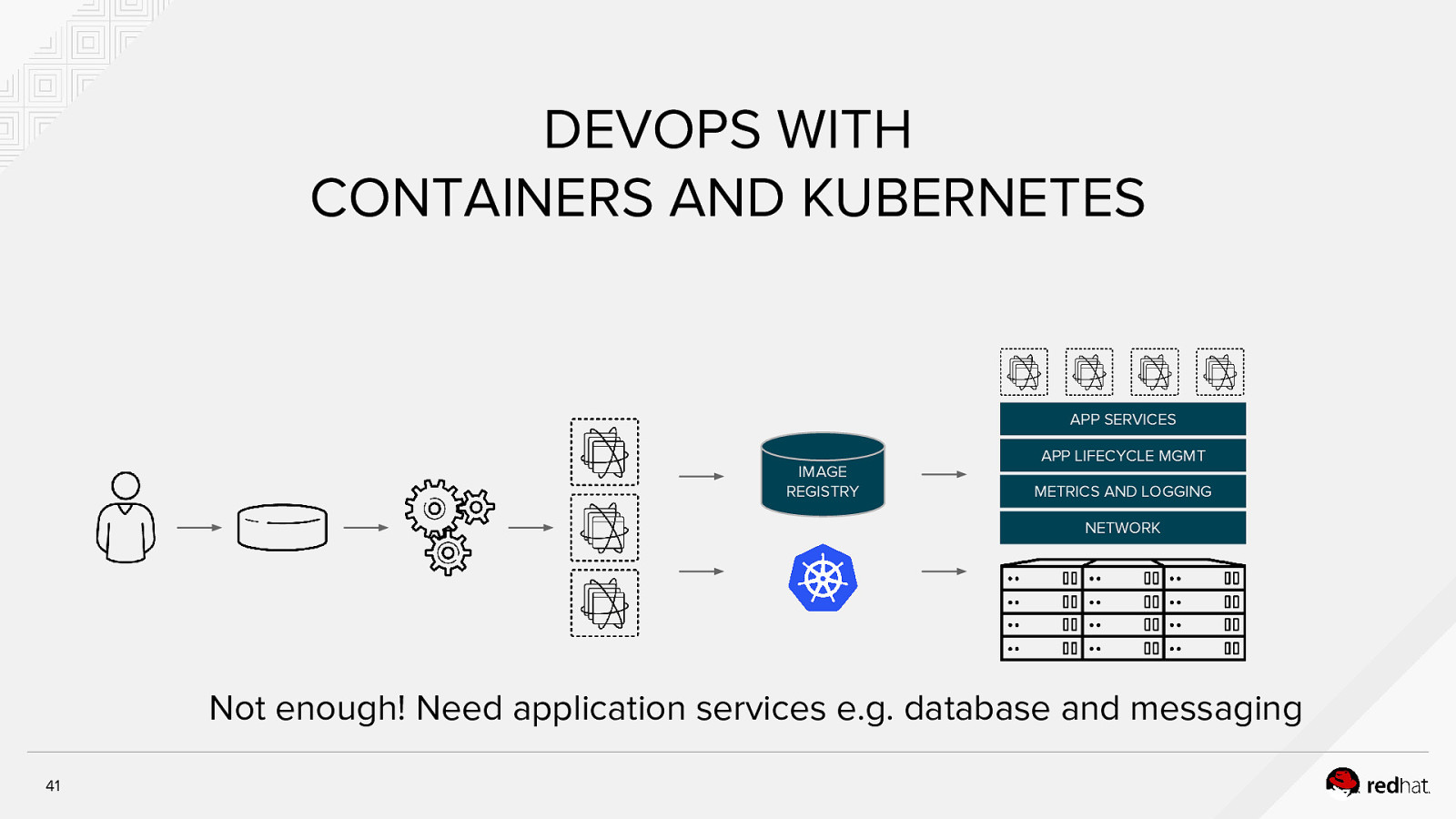
DEVOPS WITH CONTAINERS AND KUBERNETES APP SERVICES APP LIFECYCLE MGMT IMAGE REGISTRY METRICS AND LOGGING NETWORK Not enough! Need application services e.g. database and messaging 41
Slide 42
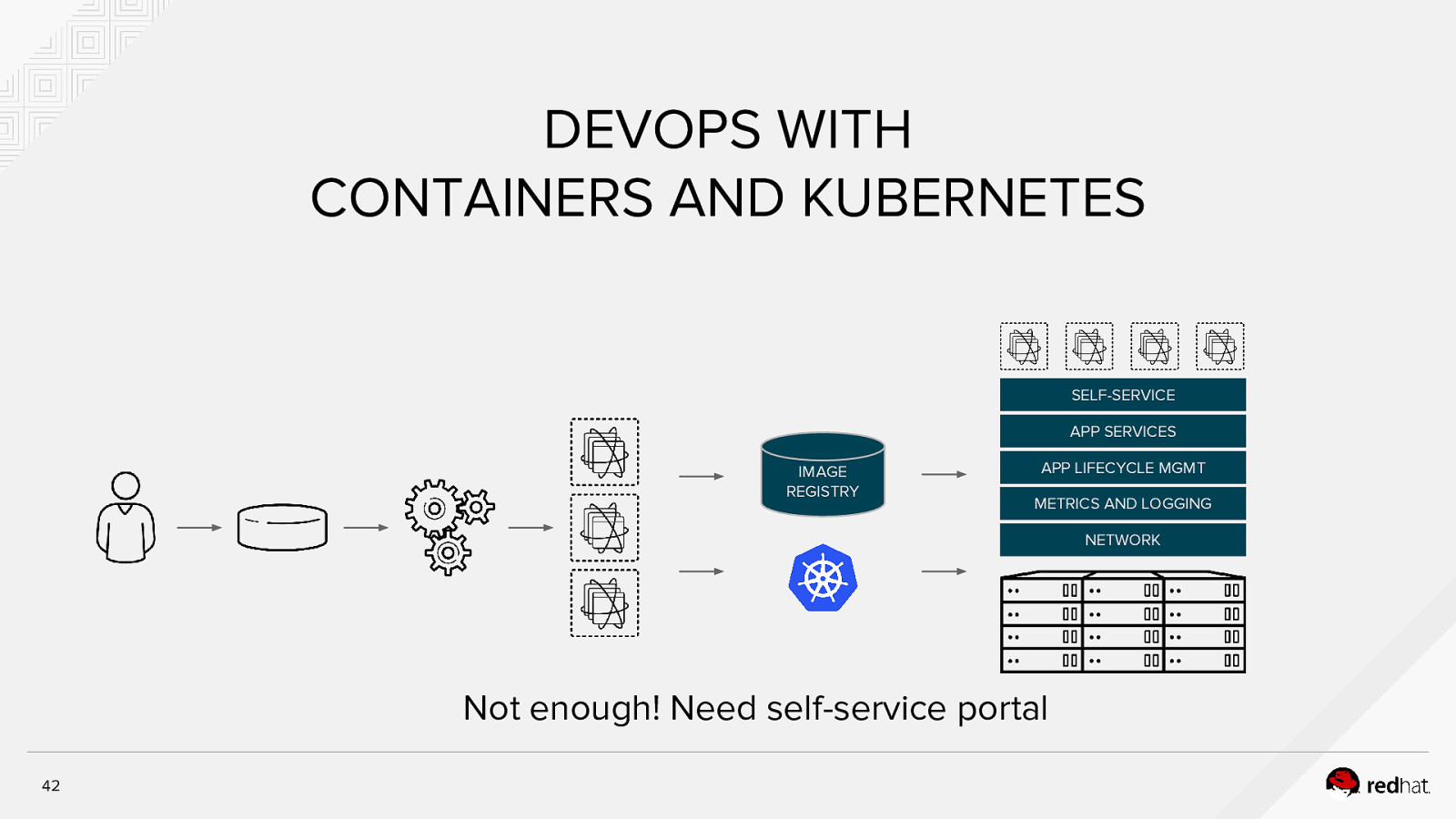
DEVOPS WITH CONTAINERS AND KUBERNETES SELF-SERVICE APP SERVICES IMAGE REGISTRY APP LIFECYCLE MGMT METRICS AND LOGGING NETWORK Not enough! Need self-service portal 42
Slide 43
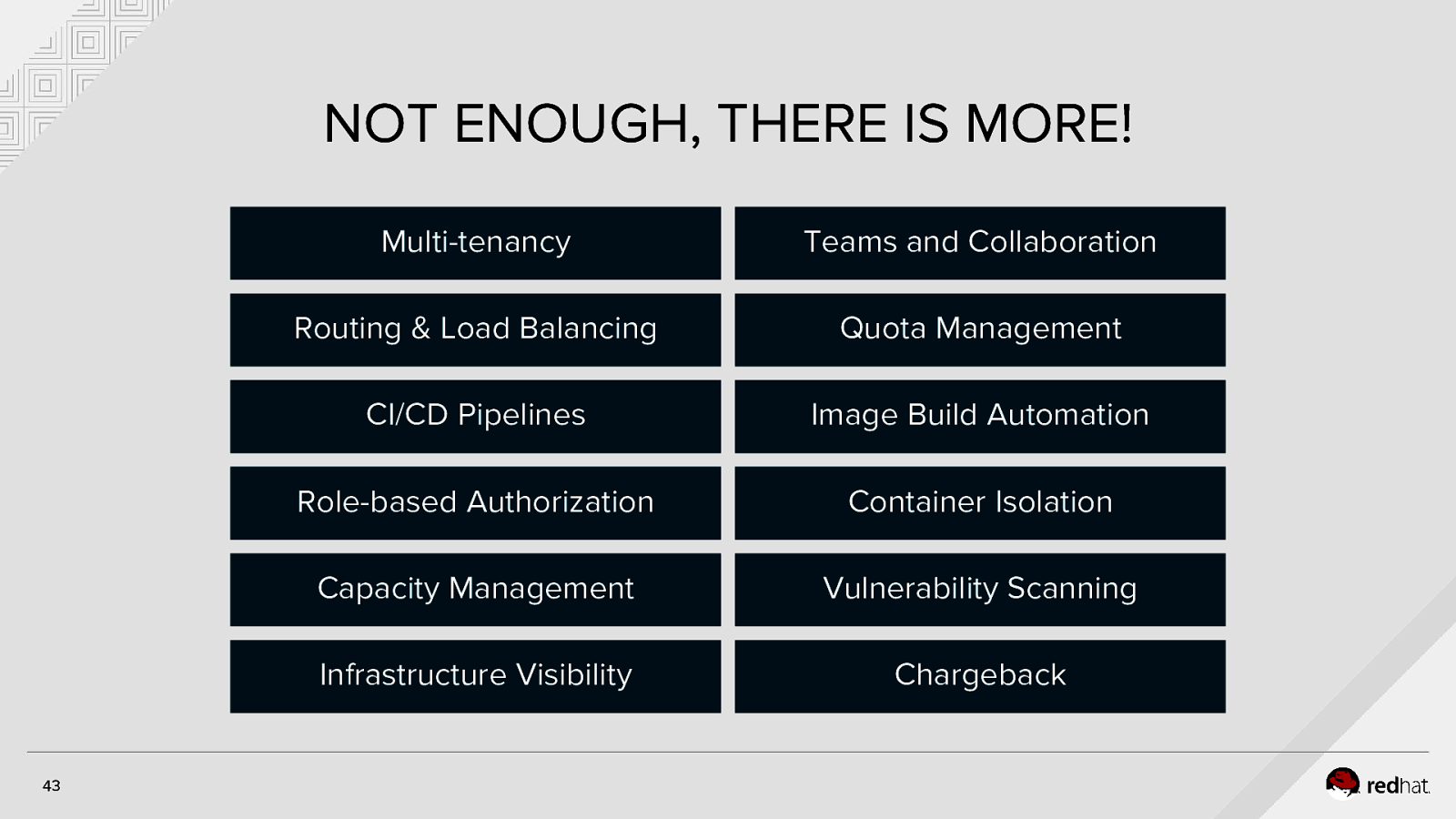
NOT ENOUGH, THERE IS MORE! 43 Multi-tenancy Teams and Collaboration Routing & Load Balancing Quota Management CI/CD Pipelines Image Build Automation Role-based Authorization Container Isolation Capacity Management Vulnerability Scanning Infrastructure Visibility Chargeback
Slide 44

Container application platform based on Docker and Kubernetes for building, distributing and running containers at scale 44
Slide 45
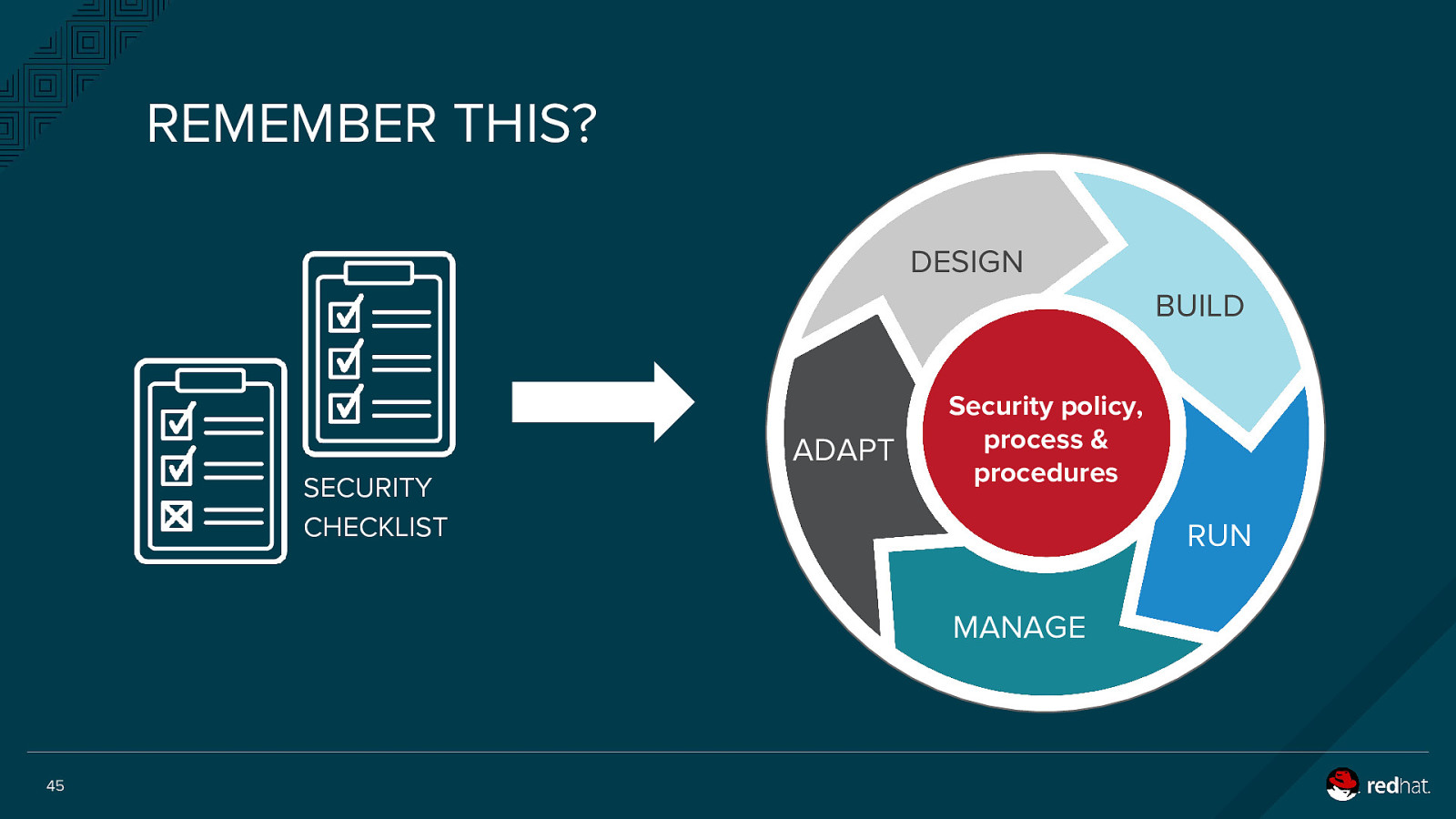
REMEMBER THIS? DESIGN BUILD ADAPT SECURITY CHECKLIST Security policy, process & procedures RUN MANAGE 45
Slide 46
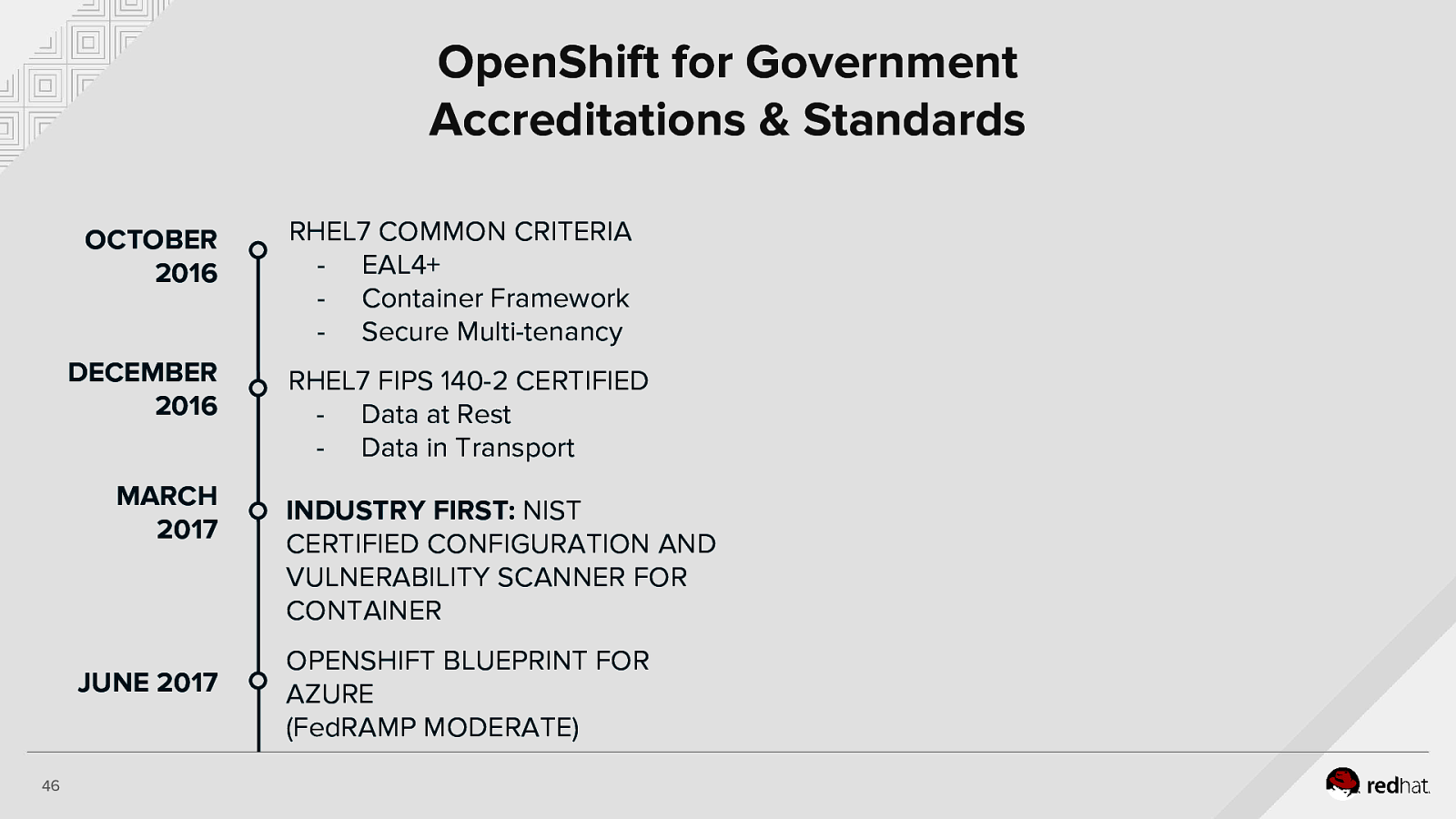
OpenShift for Government Accreditations & Standards OCTOBER 2016 DECEMBER 2016 MARCH 2017 JUNE 2017 46 RHEL7 COMMON CRITERIA - EAL4+ - Container Framework - Secure Multi-tenancy RHEL7 FIPS 140-2 CERTIFIED - Data at Rest - Data in Transport INDUSTRY FIRST: NIST CERTIFIED CONFIGURATION AND VULNERABILITY SCANNER FOR CONTAINER OPENSHIFT BLUEPRINT FOR AZURE (FedRAMP MODERATE)
Slide 47

WANT TO HEAR MORE? 47
Slide 48

Slide 49

THANK YOU plus.google.com/+RedHat facebook.com/redhatinc linkedin.com/company/red-hat twitter.com/RedHatNews youtube.com/user/RedHatVideos