Red Hat Security Seminar Shawn D. Wells (swells@redhat.com) Solutions Architect, Federal Team
Slide 1

Slide 2

Agenda Start: 10:30 am End: 1:00 pm, ish Red Hat Emerging Technologies Red Hat Security Summary & Close 2
Slide 3

Hands On & Labs 3
Slide 4
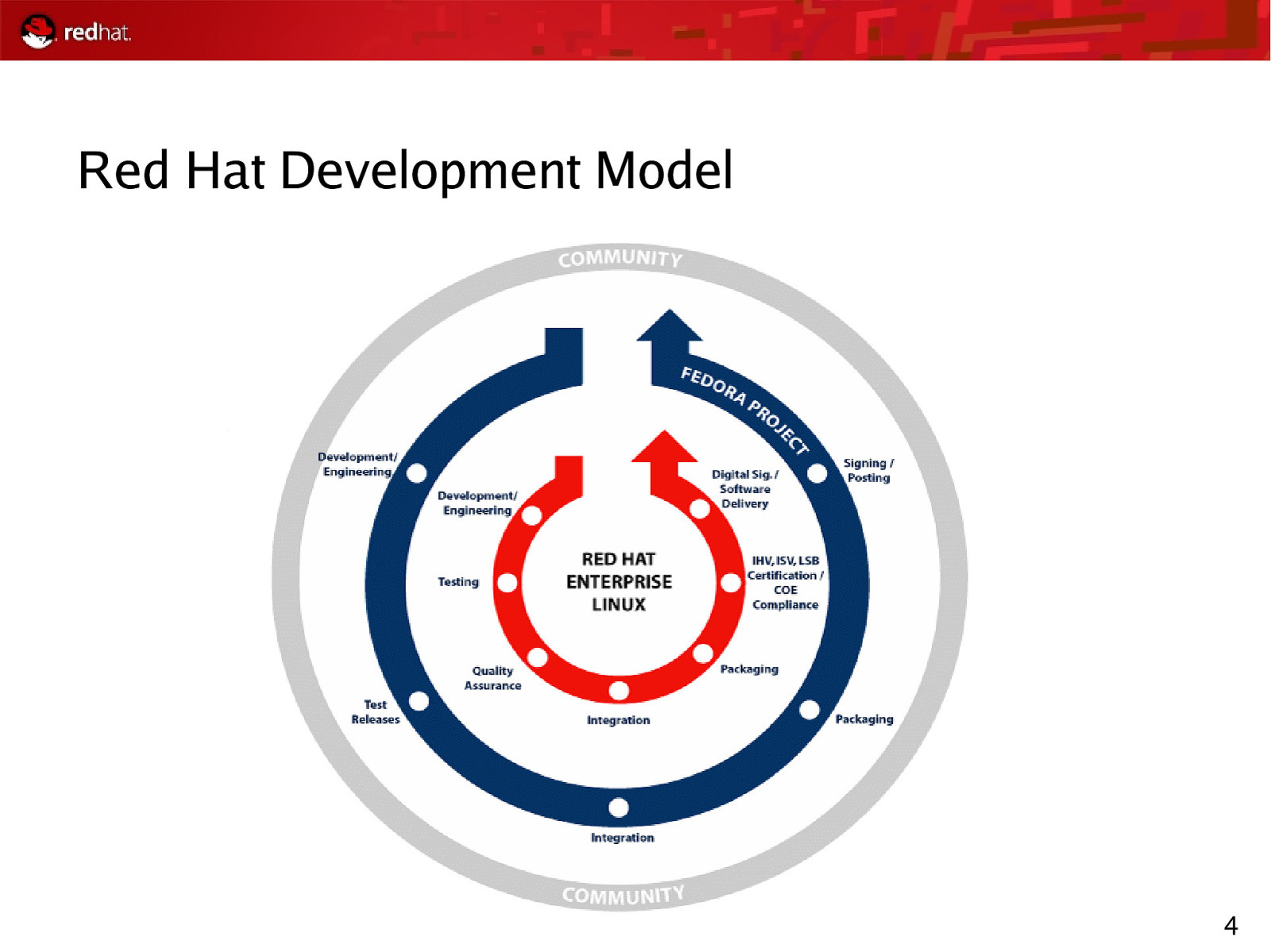
Red Hat Development Model 4
Slide 5
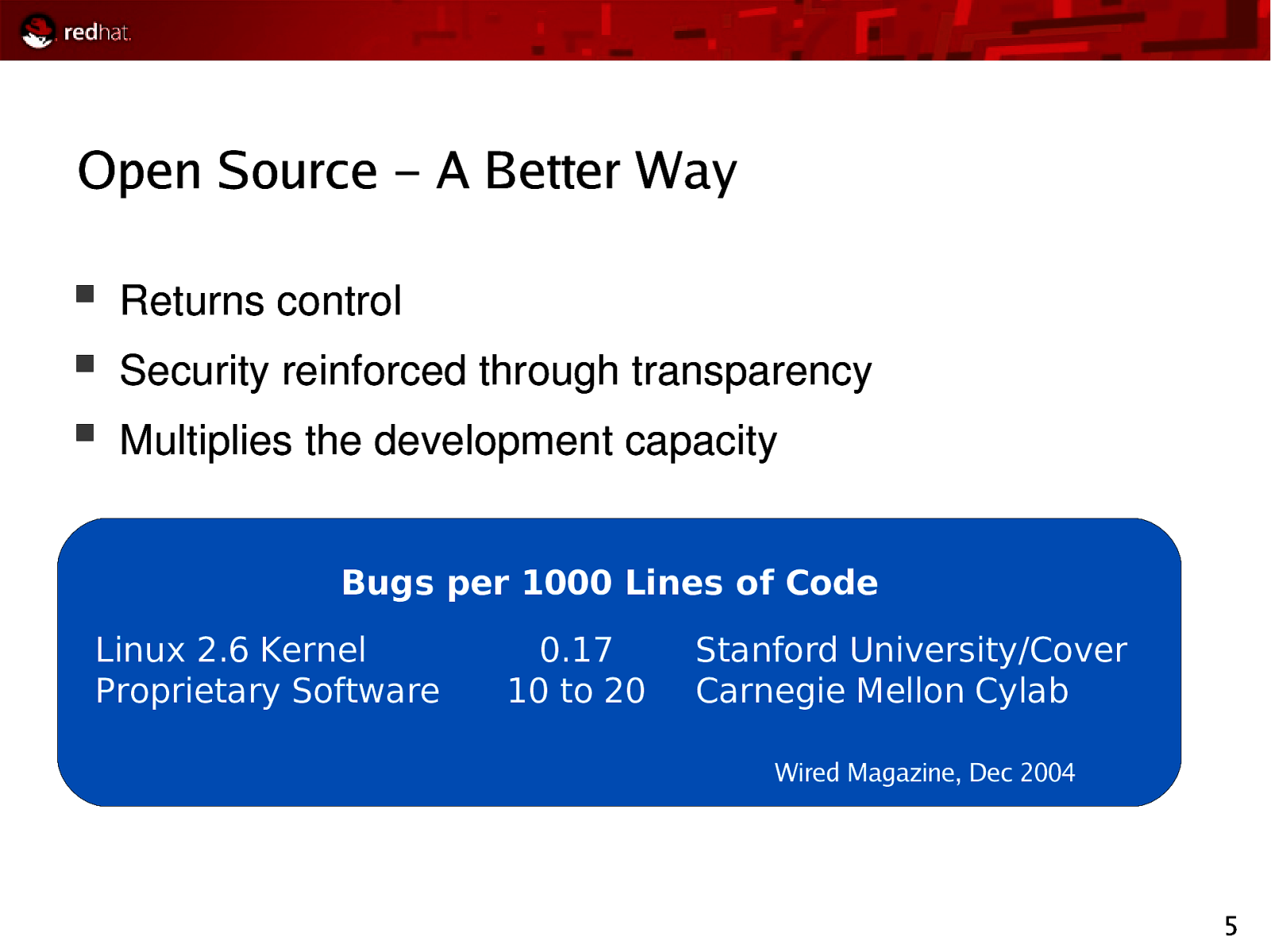
Open Source – A Better Way Returns control Security reinforced through transparency Multiplies the development capacity Bugs per 1000 Lines of Code Linux 2.6 Kernel Proprietary Software 0.17 10 to 20 Stanford University/Coverity Carnegie Mellon Cylab Wired Magazine, Dec 2004 5
Slide 6
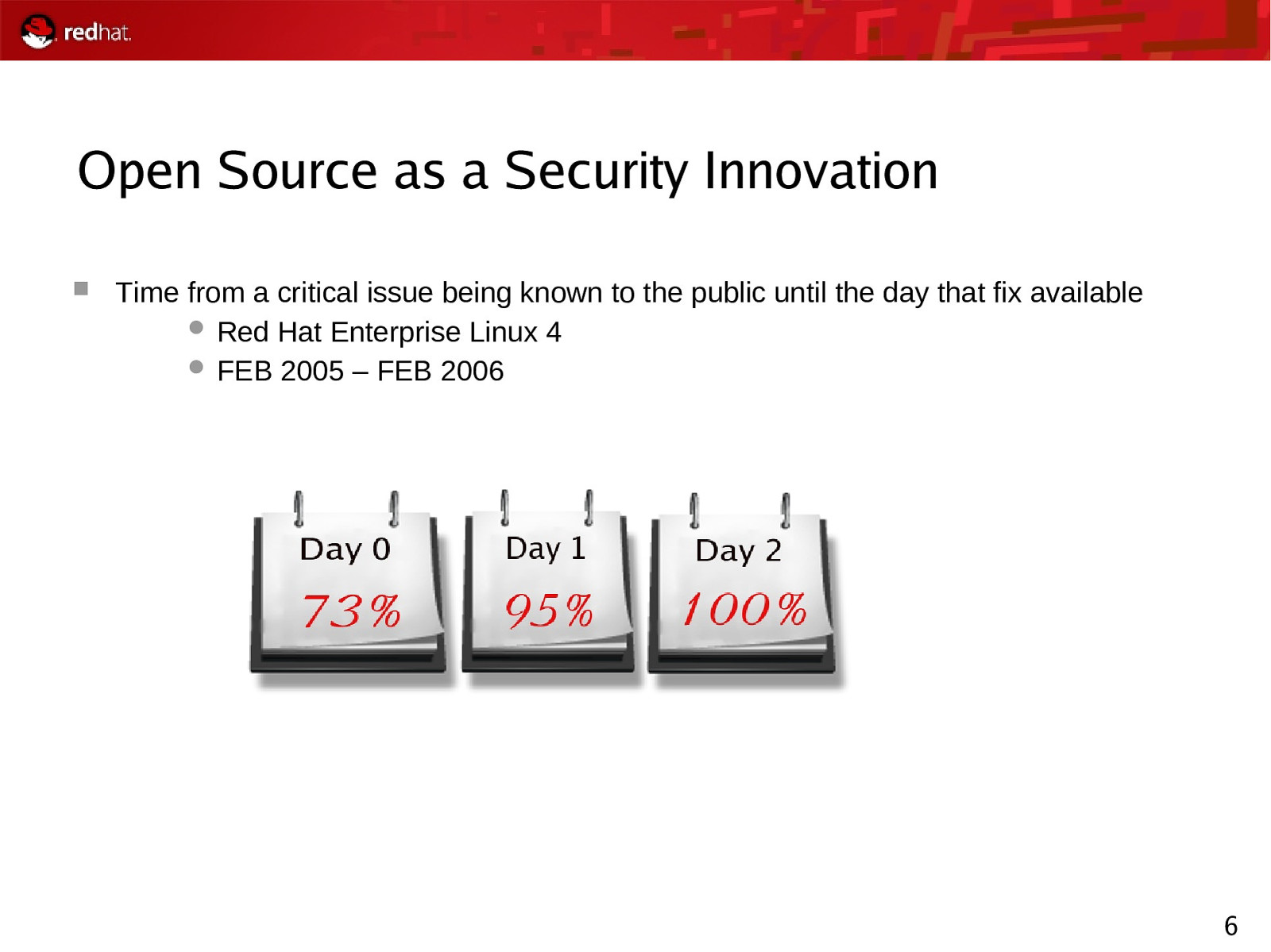
Open Source as a Security Innovation Time from a critical issue being known to the public until the day that fix available Red Hat Enterprise Linux 4 FEB 2005 – FEB 2006 6
Slide 7
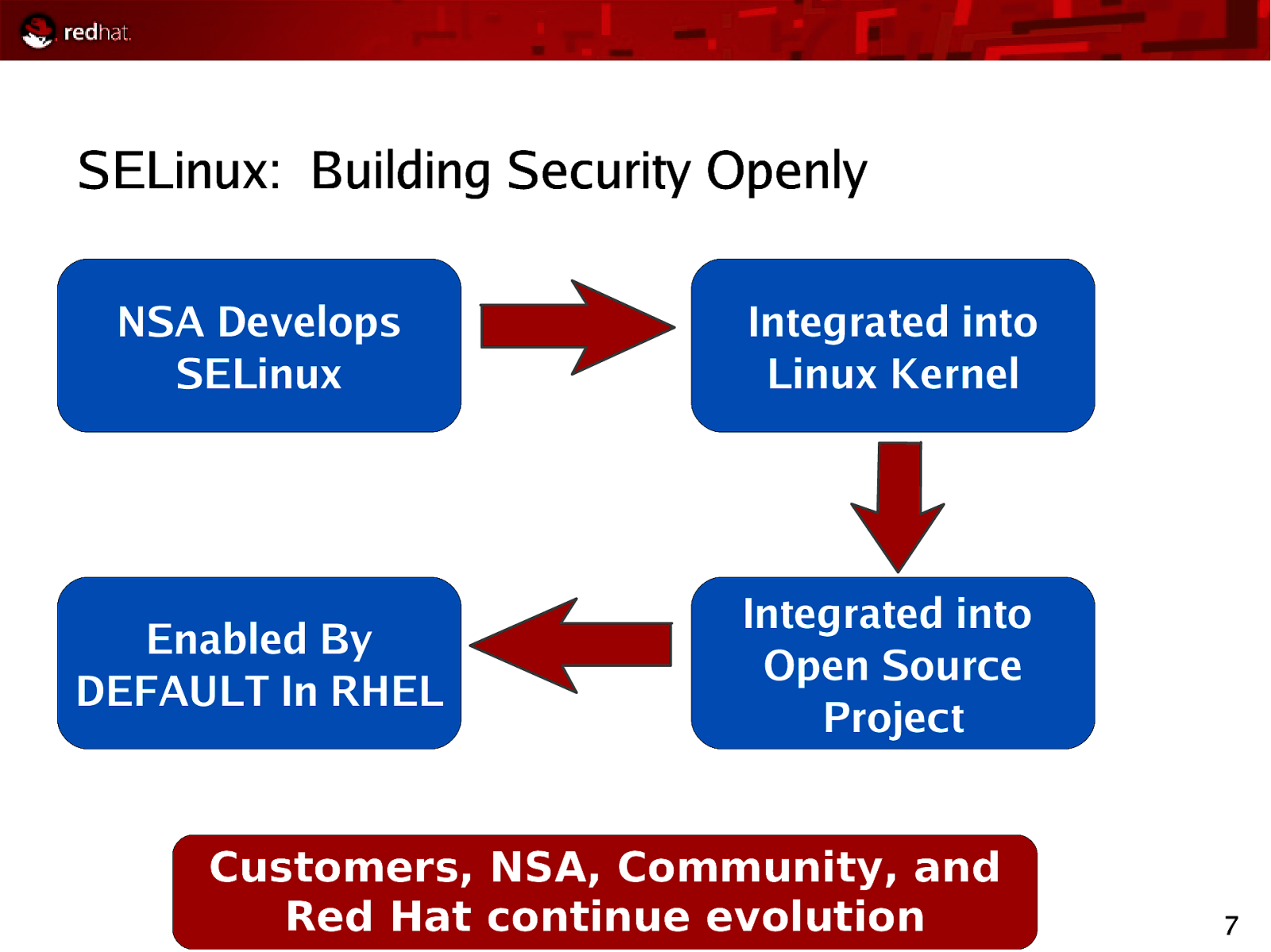
SELinux: Building Security Openly NSA Develops SELinux Integrated into Linux Kernel Enabled By DEFAULT In RHEL Integrated into Open Source Project Customers, NSA, Community, and Red Hat continue evolution 7
Slide 8

Red Hat Security Certifications NIAP/Common Criteria: The most evaluated operating system platform ● Red Hat Enterprise Linux 2.1 – EAL 2 (Completed: February 2004) ● Red Hat Enterprise Linux 3 EAL 3+/CAPP (Completed: August 2004) ● Red Hat Enterprise Linux 4 EAL 4+/CAPP (Completed: February 2006) ● Red Hat Enterprise Linux 5 EAL4+/CAPP/LSPP/RBAC (Completed: June 2007) DII-COE ● Red Hat Enterprise Linux 3 (Self-Certification Completed: October 2004) ● Red Hat Enterprise Linux: First Linux platform certified by DISA DCID 6/3 ● Currently PL3/PL4: ask about kickstarts. ● Often a component in PL5 systems DISA SRRs / STIGs ● Ask about kickstarts. FIPS 140-2 ● Red Hat / NSS Cryptography Libraries certified Level 2 8
Slide 9
Security Standards Work Extensible Configuration Checklist Description Format (XCCDF) Enumeration for configuration requirements DISA FSO committed to deploying STIG as XCCDF Others working with NIST Security policy becomes one file Open Vulnerability & Assessment Language (OVAL) Machine-readable versions of security advisories Common Vulnerability and Exposures (CVE) Compatibility Trace a vulnerability through multiple vendors 9
Slide 10

Questions? 10
Slide 11

Red Hat Emerging Technologies
Slide 12
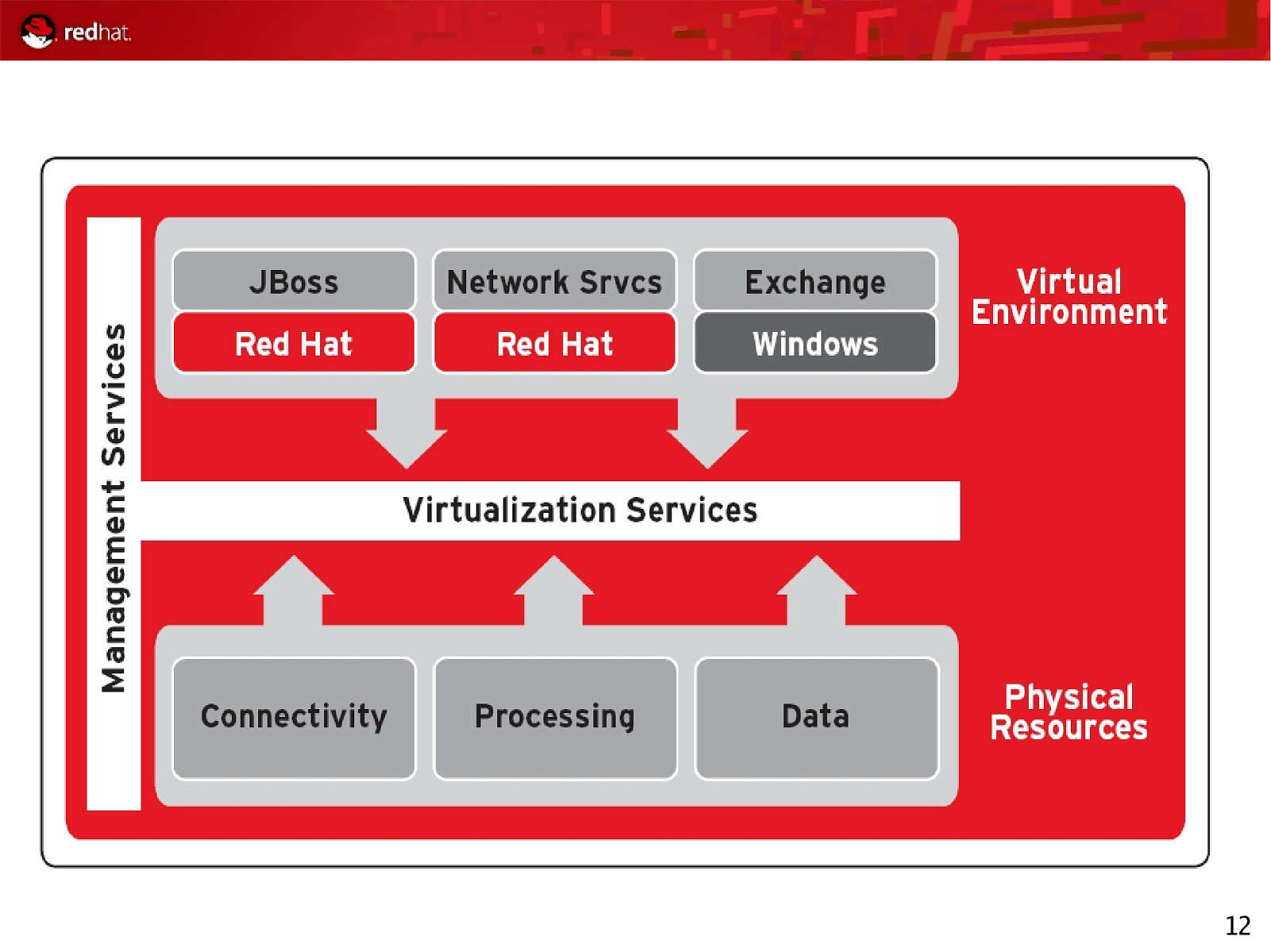
12
Slide 13
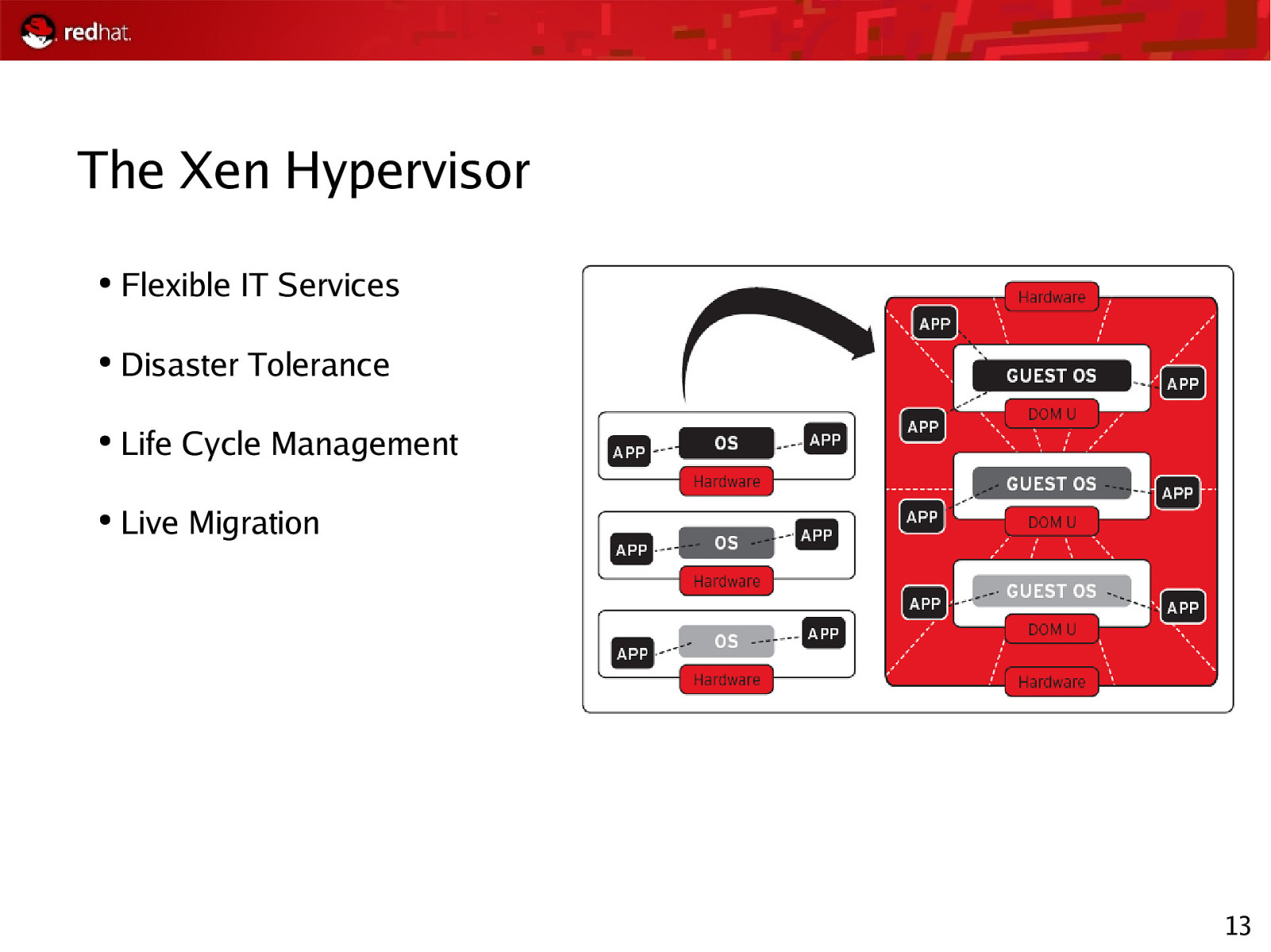
The Xen Hypervisor ● Flexible IT Services ● Disaster Tolerance ● Life Cycle Management ● Live Migration 13
Slide 14
Introduction to libvirt API Hypervisor agnostic Stable API for tool/app development CIM providers; Python, C bindings, scriptable Allows authenticated/encrypted sessions to remote hypervisors Current support for Xen Hypervisor KVM Hypervisor QEMU Hypervisor 14
Slide 15
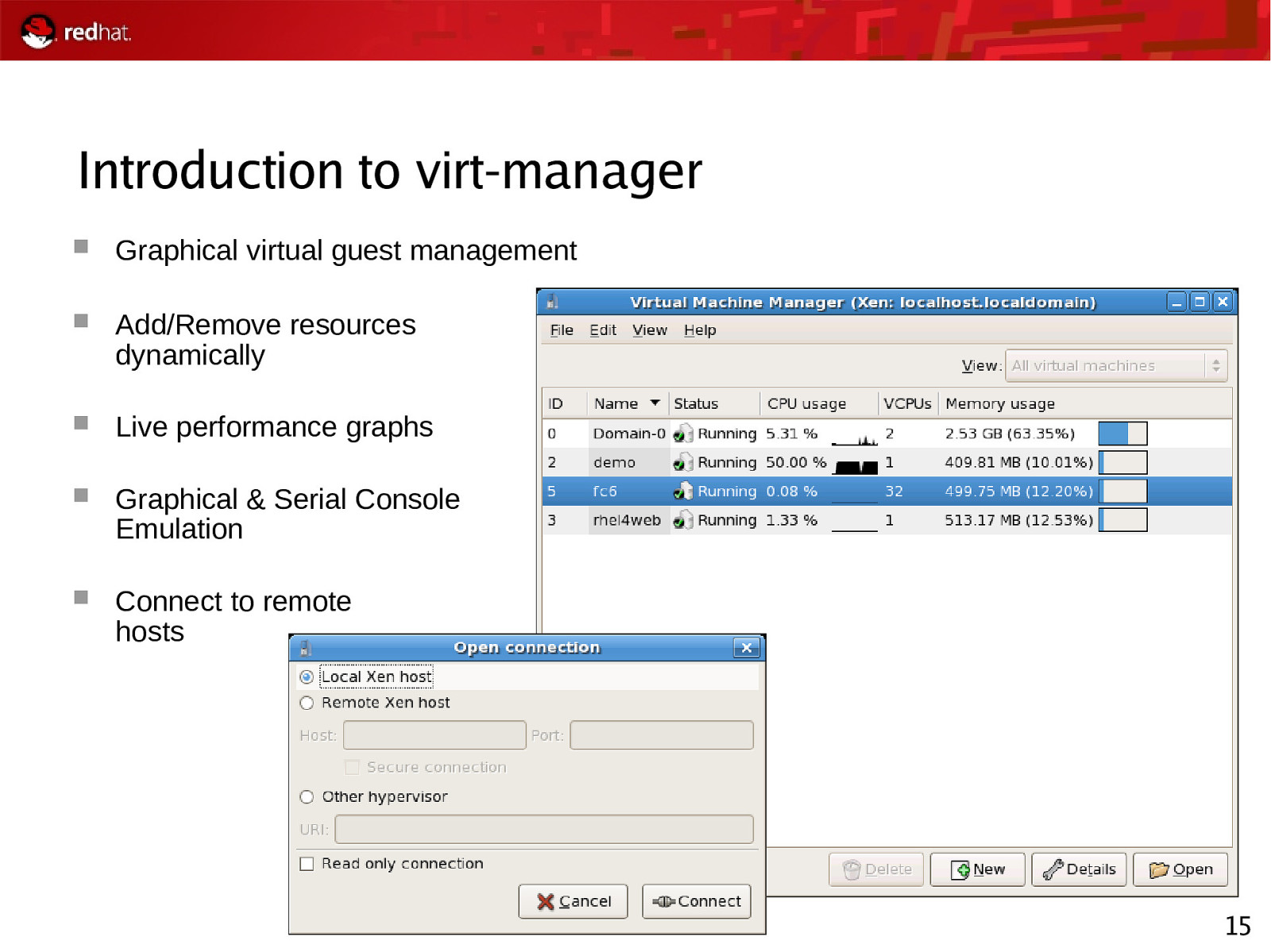
Introduction to virt-manager Graphical virtual guest management Add/Remove resources dynamically Live performance graphs Graphical & Serial Console Emulation Connect to remote hosts 15
Slide 16
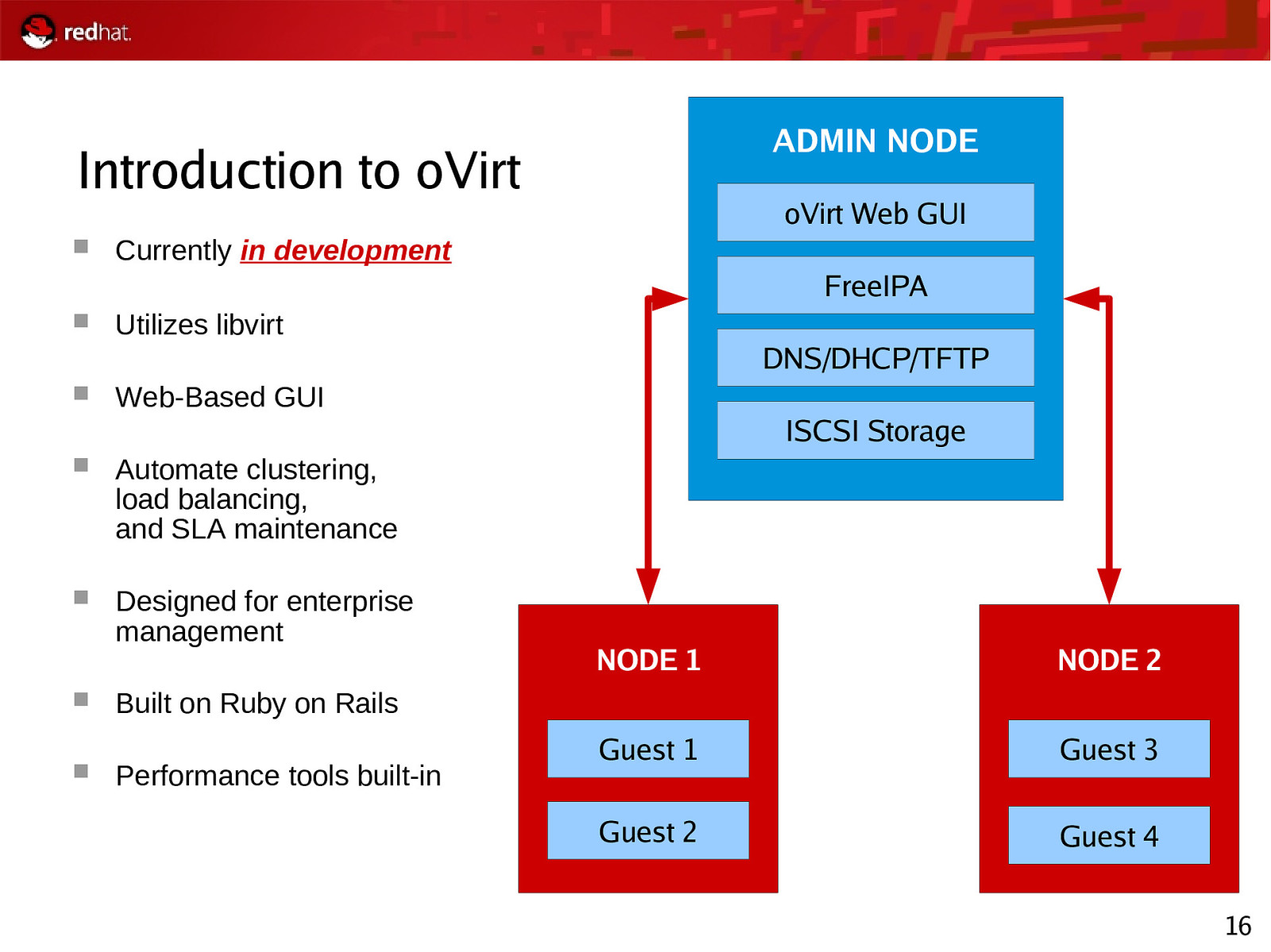
ADMIN NODE Introduction to oVirt oVirt Web GUI Currently in development FreeIPA Utilizes libvirt Web-Based GUI Automate clustering, load balancing, and SLA maintenance Designed for enterprise management DNS/DHCP/TFTP ISCSI Storage NODE 1 NODE 2 Guest 1 Guest 3 Guest 2 Guest 4 Built on Ruby on Rails Performance tools built-in 16
Slide 17
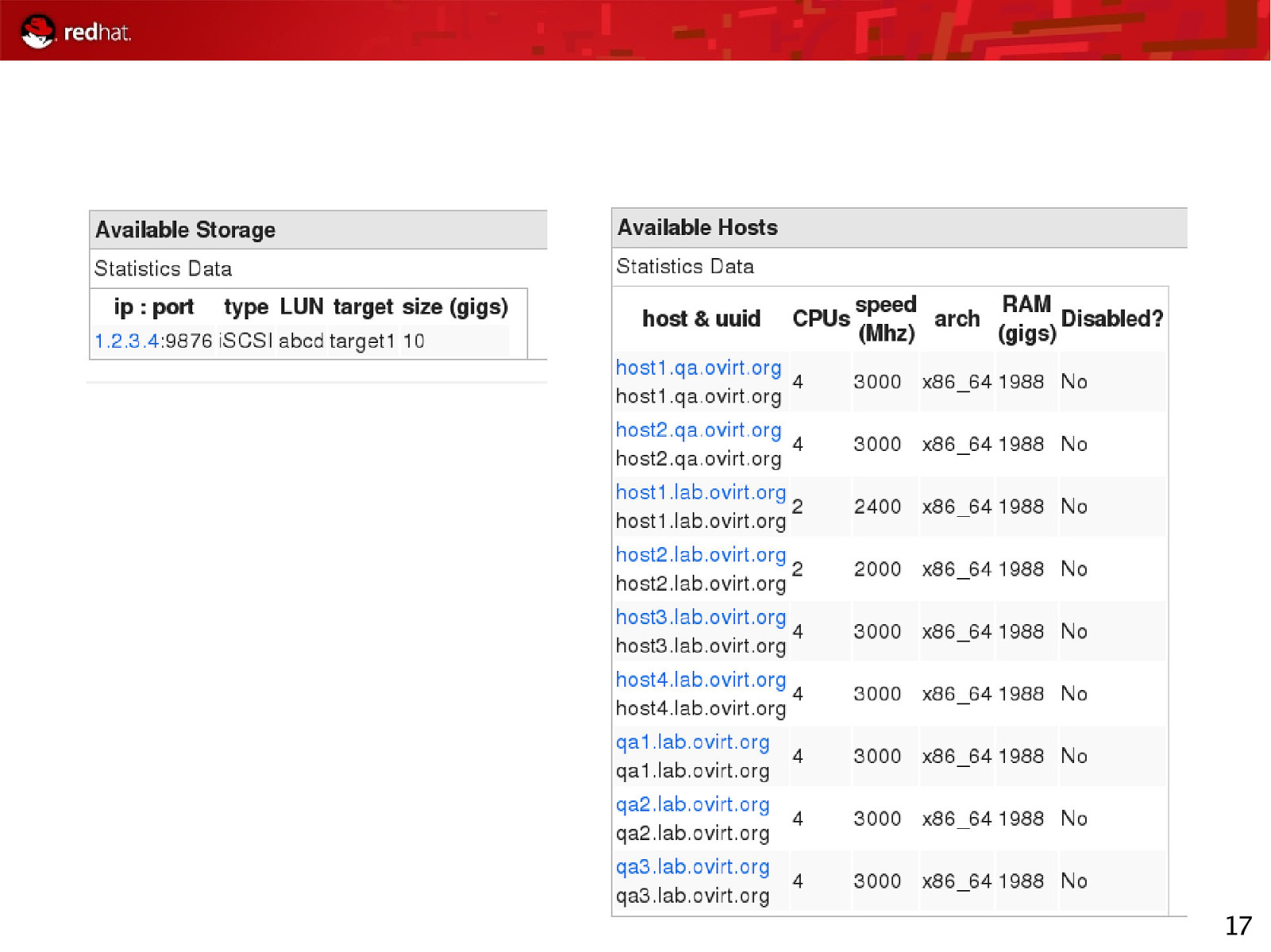
17
Slide 18
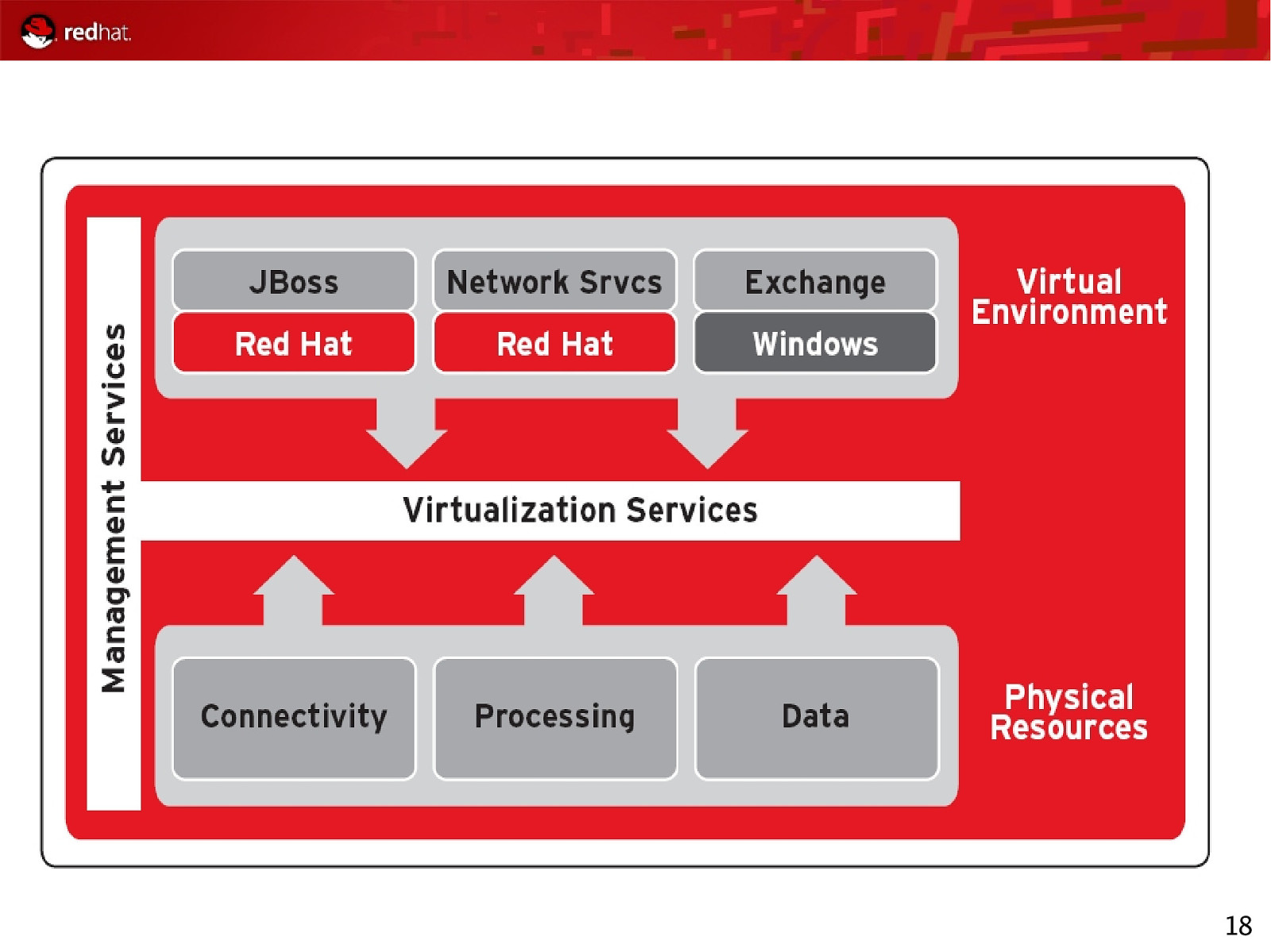
18
Slide 19
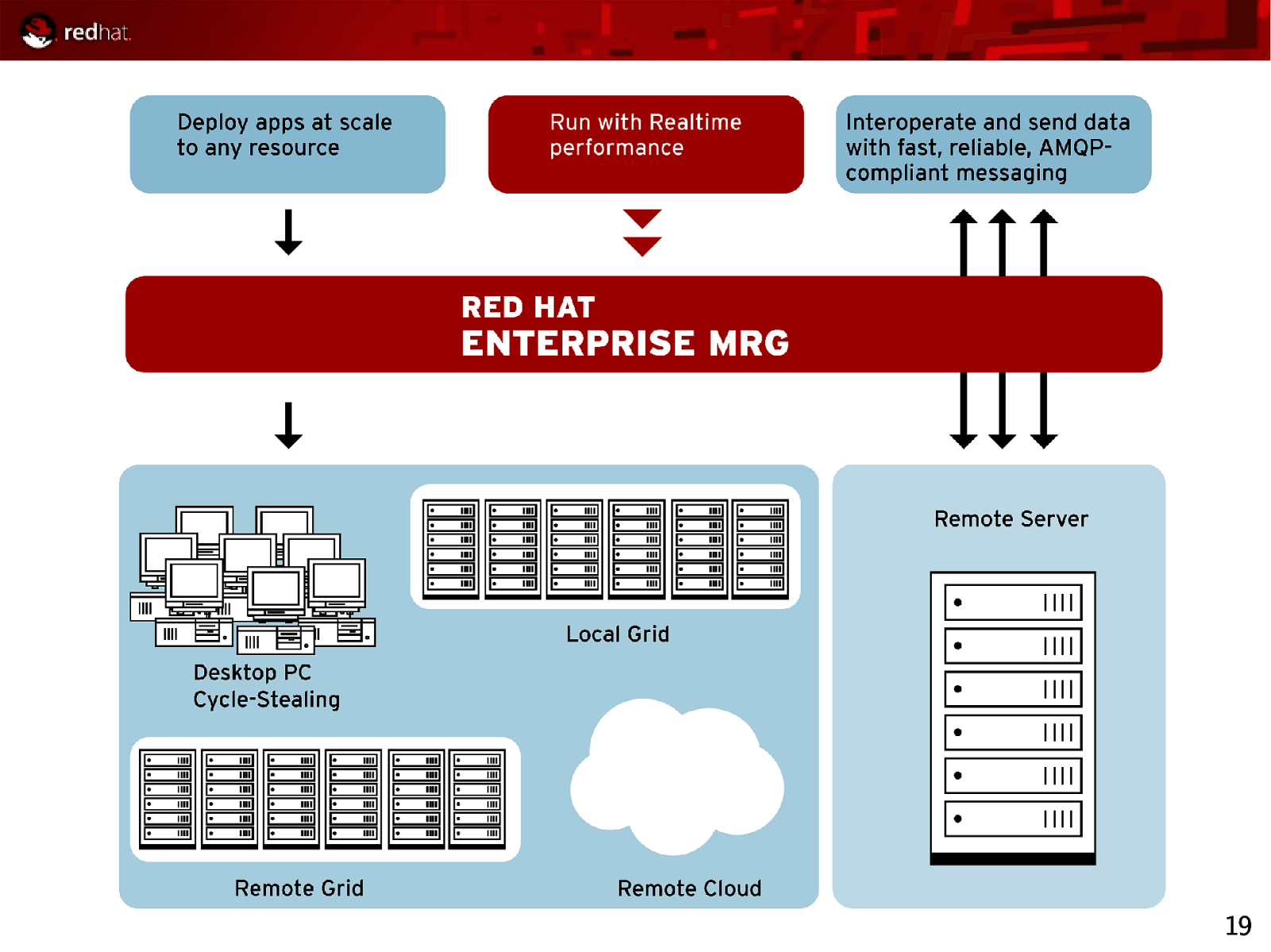
19
Slide 20

MRG: Messaging Provides messaging that is up to 100-fold faster than before Spans fast messaging, reliable messaging, large-file messaging Implements AMQP, the industry’s first open messaging standard, for unprecedented interoperability that is cross-language, cross-platform, multivendor, spans hardware and software, and extends down to the wire level Uses Linux-specific optimizations to achieve optimal performance on Red Hat Enterprise Linux and MRG Realtime ● Takes advantage of RHEL clustering, IO, kernel, and more ● Includes new high-performance AIO Journal for durable messaging ● Provides native infiniband support for transient messaging 20
Slide 21

About AMQP AMQP is an open specification for messaging ● It is a complete specification ● Anyone may use the AMQP specification to create useful implementations without being charged for the IP rights to do so AMQP aims to be technology and language-neutral ● Available in C, C++, Java, JMS, .NET, C#, Ruby, Python, etc. ● Requires IP, and can be used with TCP, UDP, SCTP, Infiniband, etc. Products complying with AMQP are inter-operable ● AMQP is a Wire-Level protocol based on the ubiquitous IP ● Wire-level compatibility means it can be embedded in the network ● Applications written to Product X will plug into servers running Product Y Red Hat is a founding member of the AMQP Working Group 21
Slide 22
MRG Realtime Determinism Ability to schedule high priority tasks predictably and consistently Priority Ensure that highest priority applications are not blocked by low priority Quality Of Service (QoS) Trustworthy, consistent response times Proven results Average of 38% improvement over stock RHEL5 Timer event precision enhanced to μ s level, rather than ms 22
Slide 23
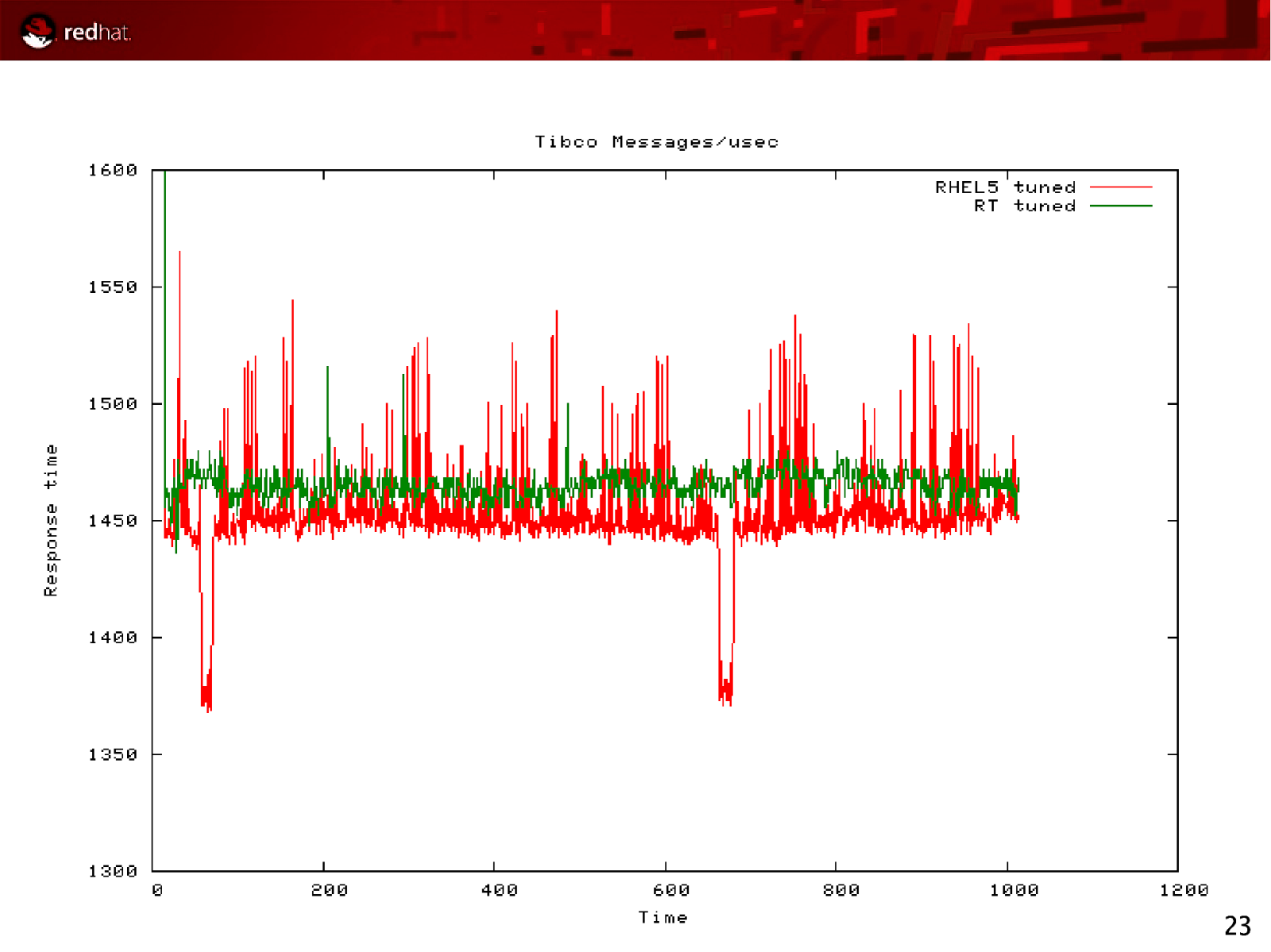
23
Slide 24

MRG: Grid Brings advantages of scale-out and flexible deployment to any application Delivers better asset utilization, allowing applications to to take advantage of all available computing resources Dynamically provisions additional peak capacity for “Christmas Rush”-like situations Executes across multiple platforms and in virtual machines Provides seamless and flexible High Throughput Computing (HTC) and High Performance Computing (HPC) across Local grids Remote grids Remote clouds (Amazon EC2) Cycle-stealing from desktop PCs 24
Slide 25

Project Open Source www.freeipa.org Started and contributed to by Red Hat Open to all IPA = Identity, Policy, Audit Big vision Start with centralized user identity management for UNIX/Linux Add robust, shared sense of machine, service and data identity Provide centrally managed admin access control for UNIX/Linux Give ability to externalize policy and add to it easily Add centralized audit With this you can enable flexible cross-enterprise policy and rational audit 25
Slide 26
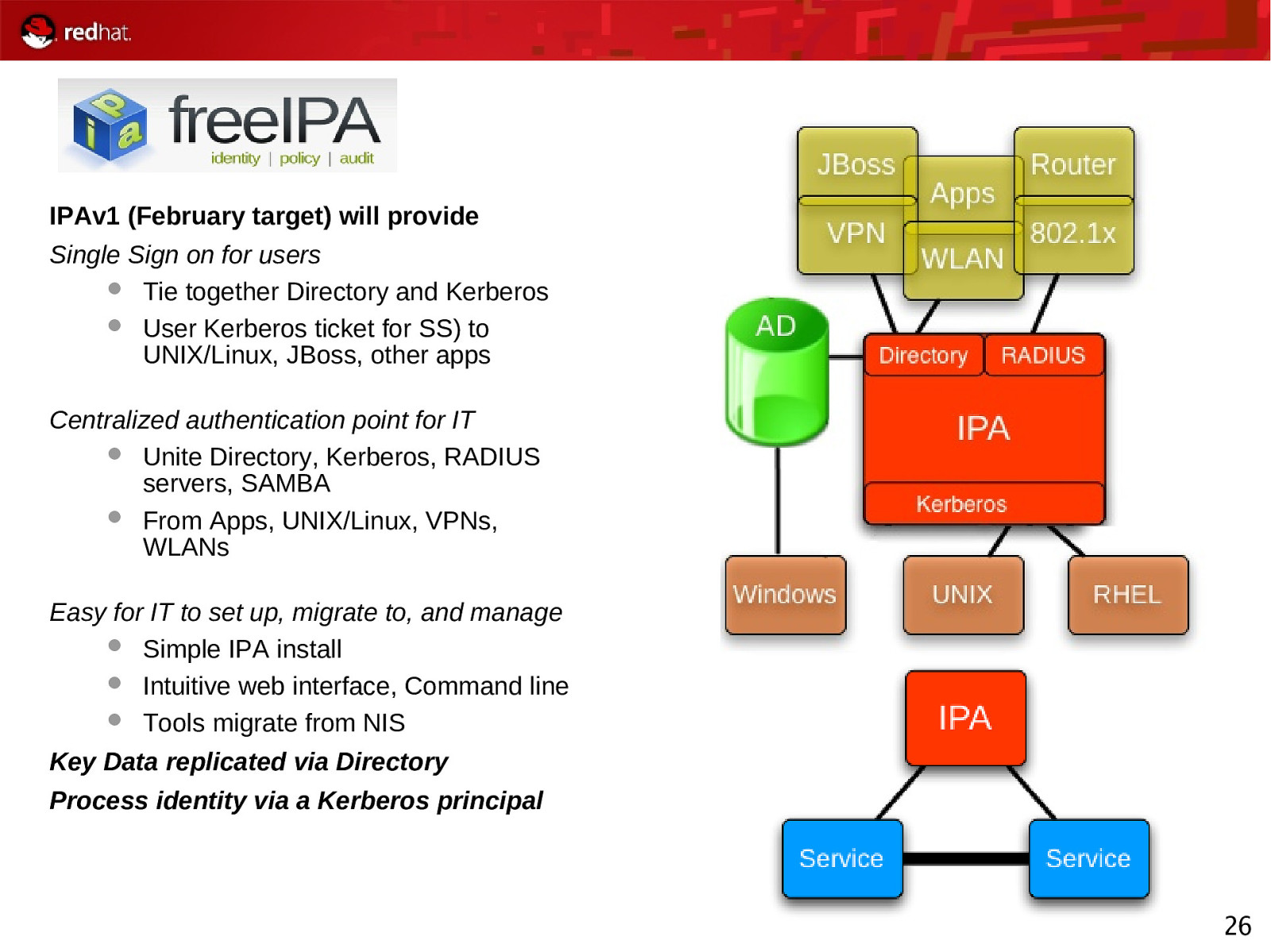
IPAv1 (February target) will provide Single Sign on for users Tie together Directory and Kerberos User Kerberos ticket for SS) to UNIX/Linux, JBoss, other apps Centralized authentication point for IT Unite Directory, Kerberos, RADIUS servers, SAMBA From Apps, UNIX/Linux, VPNs, WLANs Easy for IT to set up, migrate to, and manage Simple IPA install Intuitive web interface, Command line Tools migrate from NIS Key Data replicated via Directory Process identity via a Kerberos principal 26
Slide 27
IPAv2 (July target) will provide Identify and group machines, Vms, services Simplified service authentication and establishment of secure communication Machine identity via Kerberos, certificate Process identity via Kerberos principal Management of machine certificate Centrally managed access control Extensible policy framework Set policy of which users can access which apps on which machines Centrally managed scoped admin control Central audit database Centrally audit security event, logs, keystrokes (?), compliance with lockdown 27
Slide 28

RHEL5 Security: Smart Card Support 28
Slide 29

Questions? 29
Slide 30

SELinux A Wonderland of Obscure Subsystems
Slide 31

Access Control Mechanisms (ACMs) Control which users and processes can access different files, devices, interfaces, etc., in a computer system. This is a primary consideration when securing a computer system or network of any size. Discretionary Access Control (DAC) Access Control Lists (ACLs) SELinux Mandatory Access Control (MAC) RoleBased Access Control (RBAC) MultiLevel Security (MLS) 31
Slide 32
Discretionary Access Controls (DAC) Basic access controls for objects in a filesystem Typical access control provided by file permissions, sharing, etc Access is generally at the discretion of the owner of the object (file, directory, device, etc.).
ls -L /demos/Harris/
32
Slide 33
Access Control Lists (ACLs) Evolution of DAC Delegate access decisions to specific user/groups/subsets -rw-rw-r—+
sudo -u hr_worker cat HR_PayrollData # setfacl -m u:hr_worker:r HR_PayrollData # sudo -u hr_worker cat HR_PayrollData
33
Slide 34

SELinux Basics: Goals Systems Must Be Tamperproof There must be no way for attackers or others on the system to intentionally or accidentally disable it or otherwise interfere with its operation Systems Must Be Nonbypassable There must be no way to gain access to system resources except through mechanisms that use the reference monitor to make access control decisions Access Must Be Verifiable There must be a way to convince third-party evaluators (i.e. Auditors) that the system will always enforce MLS correctly No Covert Channels Eliminate footprints of other processes on the system (process threads, resource utilization, disk activities, etc) 34
Slide 35
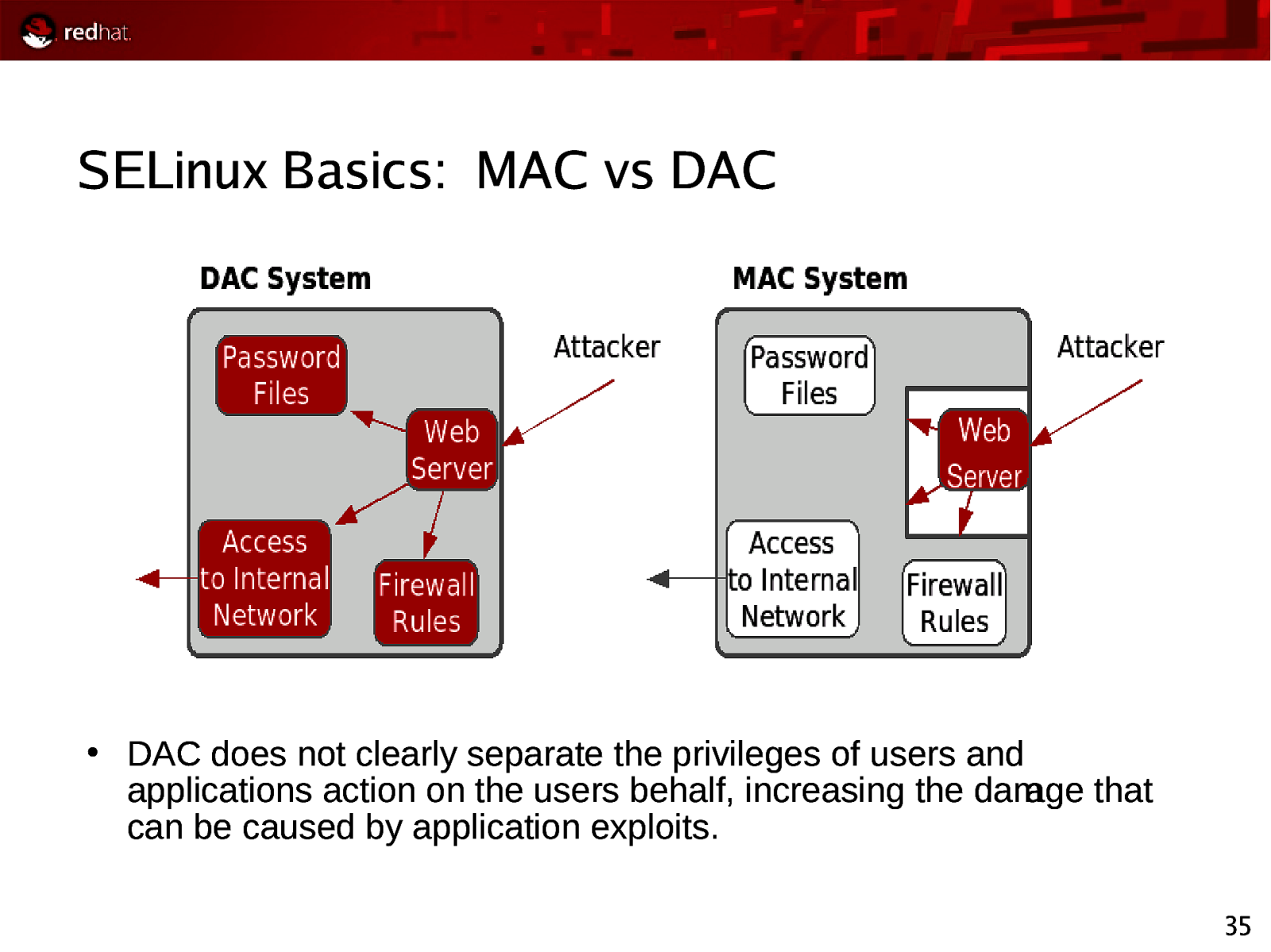
SELinux Basics: MAC vs DAC ● DAC does not clearly separate the privileges of users and applications action on the users behalf, increasing the damage that can be caused by application exploits. 35
Slide 36
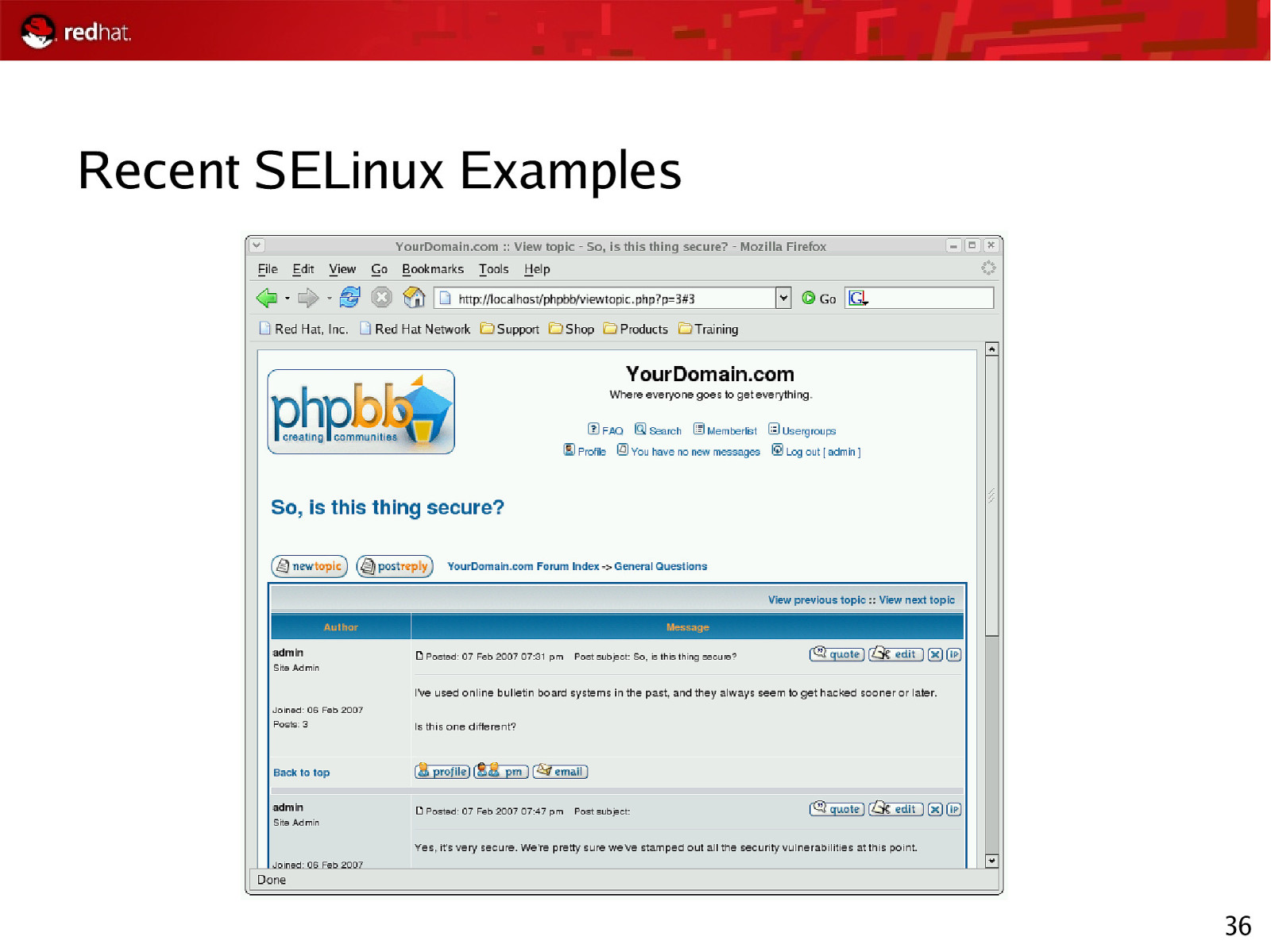
Recent SELinux Examples 36
Slide 37
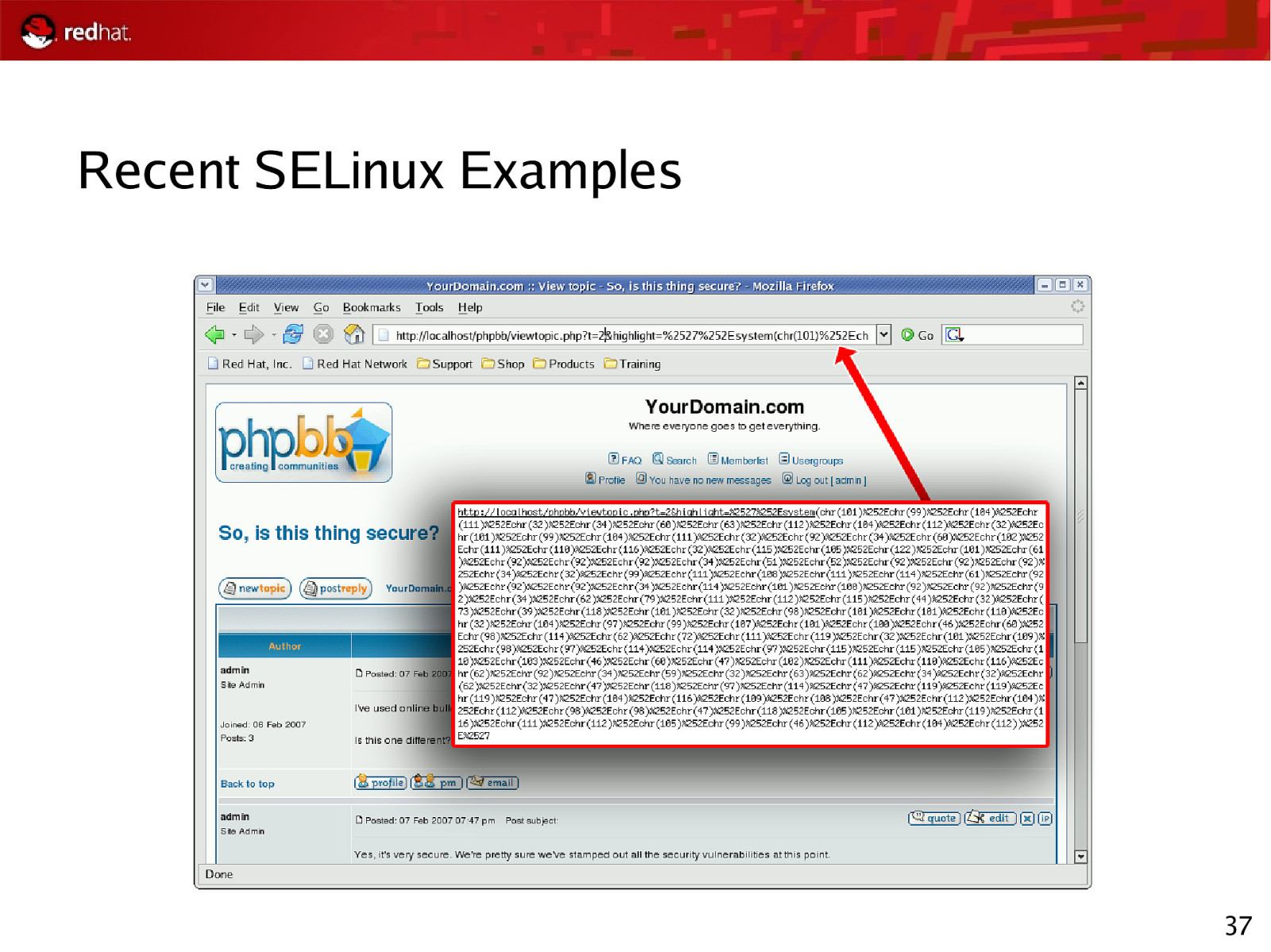
Recent SELinux Examples 37
Slide 38
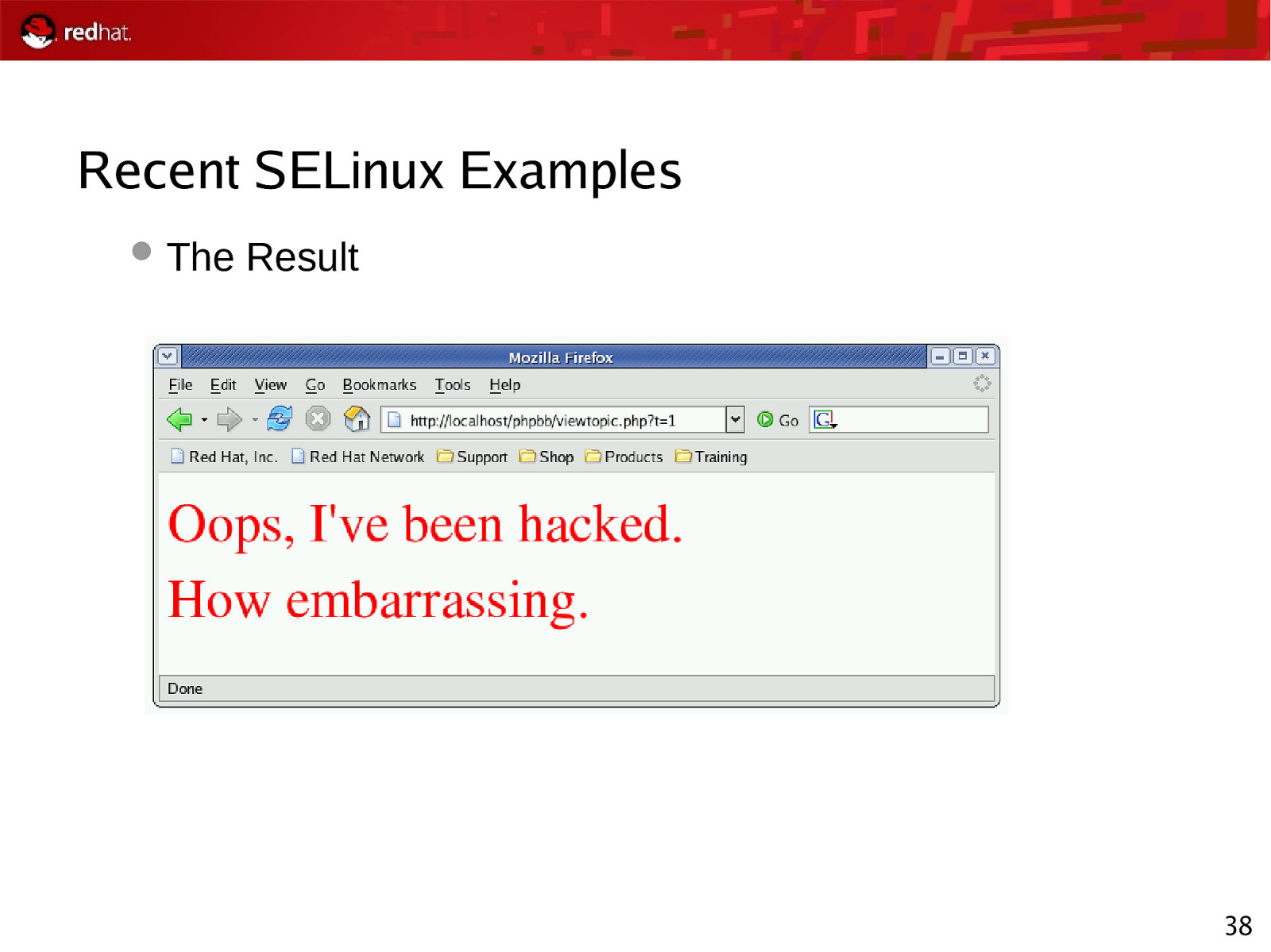
Recent SELinux Examples The Result 38
Slide 39
Using SELinux… Apache should not be allowed to overwrite content Therefore, Apache – and any program started by Apache – is not given write access to the data SELinux constrains the program, regardless of the user running executable The content is protected, even if the Apache PHP/CGI user owns the files When attacker uses the same exploit, with SELinux turned on: Mar 3 23:02:04 rhel4-u4-as kernel: audit(1170820924.171:108): avc: denied { write } for pid=26760 comm=”sh” name=”phpbb” dev=dm-0 ino=1114119 scontext=root:system_r:httpd_sys_script_t tcontext=root:object_r:httpd_sys_content_t tclass=dir 39
Slide 40

Key Points The attack would have been prevented simply by turning SELinux on, without any further configuration! SELinux implements comprehensive control over all resources, including files, directories, devices, sockets, networking, IPC, etc. SELinux and Linux DAC are orthogonal (both security checks must pass) 40
Slide 41
SELinux Basics: RHEL5 Improvements Expanded SELinux targeted policy coverage ● Provides coverage for all core system services, versus 11 in Red Hat Enterprise Linux 4 ● Includes support for Multi Level Security (MLS) enforcement model ● In addition to existing RBAC and TE models An additional level of protection against security exploits ● Fine-grained policies via kernel-enforced mandatory access controls ● Limits the scope of security vulnerabilities ● Beyond what any other general-purpose OS can deliver 41
Slide 42
SELinux Basics: RHEL5 Improvements, Cont Loadable Policy Modules ● In the past, all policy changes had to be made to the policy source ● Required the entire policy re-compiled ● Requiring a full set of policy development tools on production systems. ● ● Modules allow for the creation of self-contained policy modules ● Safely linked together to create system policies ● Add policy on the fly ● Remove policy on the fly Framework to allow ISV/OEM partners to ship their own modular SELinux policy Further Information ● http://sepolicy-server.sourceforge.net/index.php?page=moduleoverview 42
Slide 43
SELinux Basics: RHEL5 Improvements, Cont ExecShield Prevent any memory that was writable from becoming executable. Prevents an attacker from writing his code into memory and then executing it Stack Smashing protection (Canary values) Places a canary value at a randomized point above the stack. This canary value is verified during normal operation. If the stack has been smashed, the canary value will have been overwritten, indicating that the stack has been smashed. This is a method to detect buffer overflows early. 43
Slide 44
SELinux Basics: RHEL5 Improvements, Cont FORTIFY_SOURCE GCC option Compiler knows the size of a buffer Functions operate on the buffer to make sure it will not overflow at runtime. This works to help catch format string flaws as well as buffer overflows. Unconfined Memory Unconfined is a domain that was added to SELinux specifically to allow applications in this domain to run as if they were not running on an SELinux system. With RHEL5, memory protections have been added to the unconfined domain. 44
Slide 45

SELinux Compatible Applications ● ● ● SELinux can control all Linux applications. Since policy dictates how processes will access domains, all one needs to do is construct a policy for their application. Once the policy is constructed, it can be loaded, tested, and distributed with the application. 45
Slide 46
SELinux Basics: Policy Types Targeted Policy (Default) Applications run unconfined unless explicitly defined policy exists Strict Policy All application actions explicitly allowed through SELinux, else actions denied MLS Polyinstantiated file systems Allows for different “views” based on clearance level 46
Slide 47

SELinux: Exploring Contexts ● All objects have a security context ● user:role:type[:sensitivity:category] ● Stored as extended attribute on the inode User ● ● Strict: audit_u, admin_u, etc. Targeted: root, system_u, user_u Role ● Targeted: files are object_r, processes are system_r Type ● ● ● Type v. domain: httpd_exec_t v. httpd_t Sensitivity: s0-s15, aka “SystemLow-SystemHigh” Category: c0-c1023 ● Set math! 47
Slide 48
SELinux: Exploring Contexts # ps -axZ Notice context of ntpd, versus bash # ls -Z /home Notice context of ntpd, versus bash Apache Example 48
Slide 49
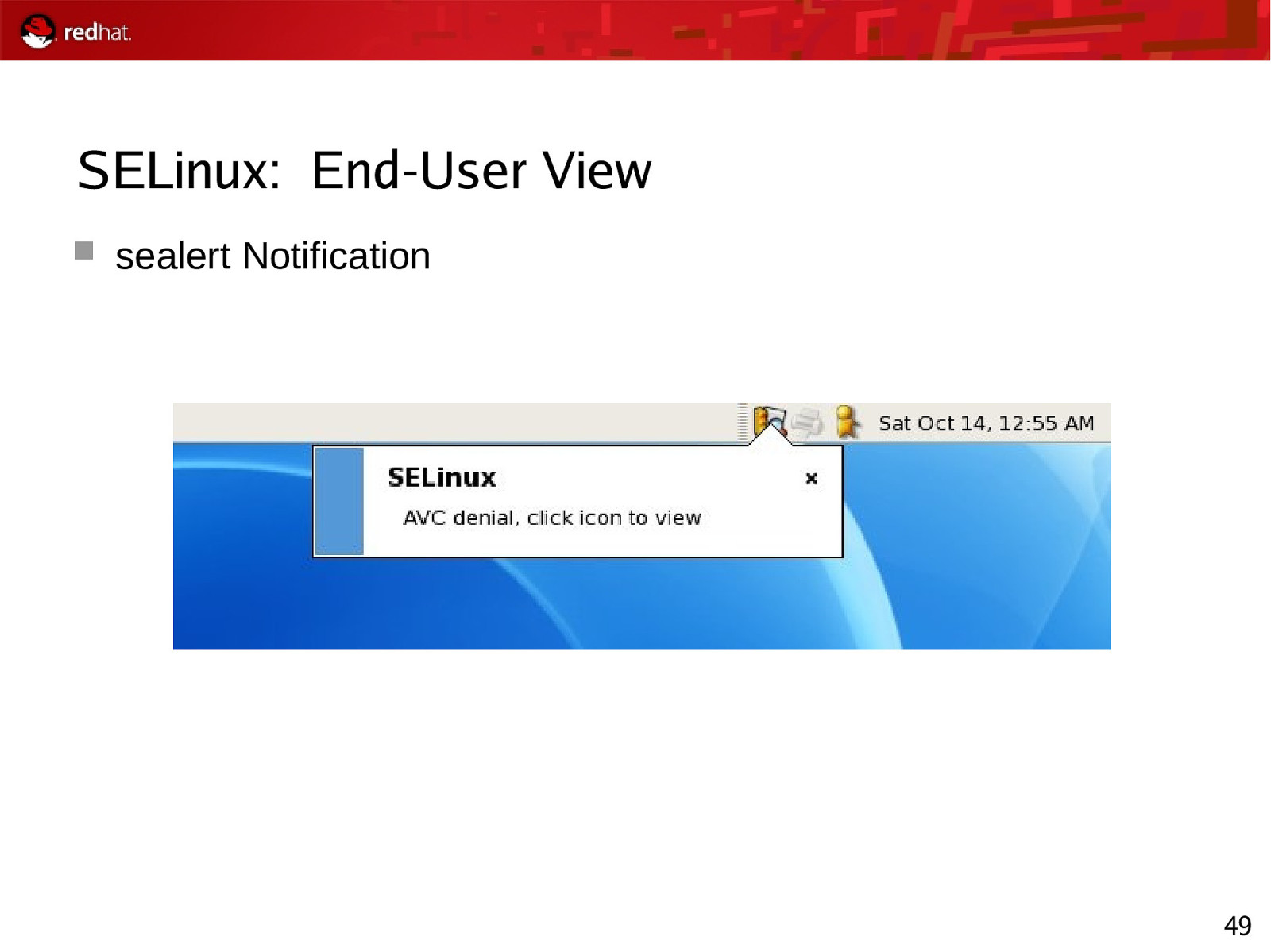
SELinux: End-User View sealert Notification 49
Slide 50
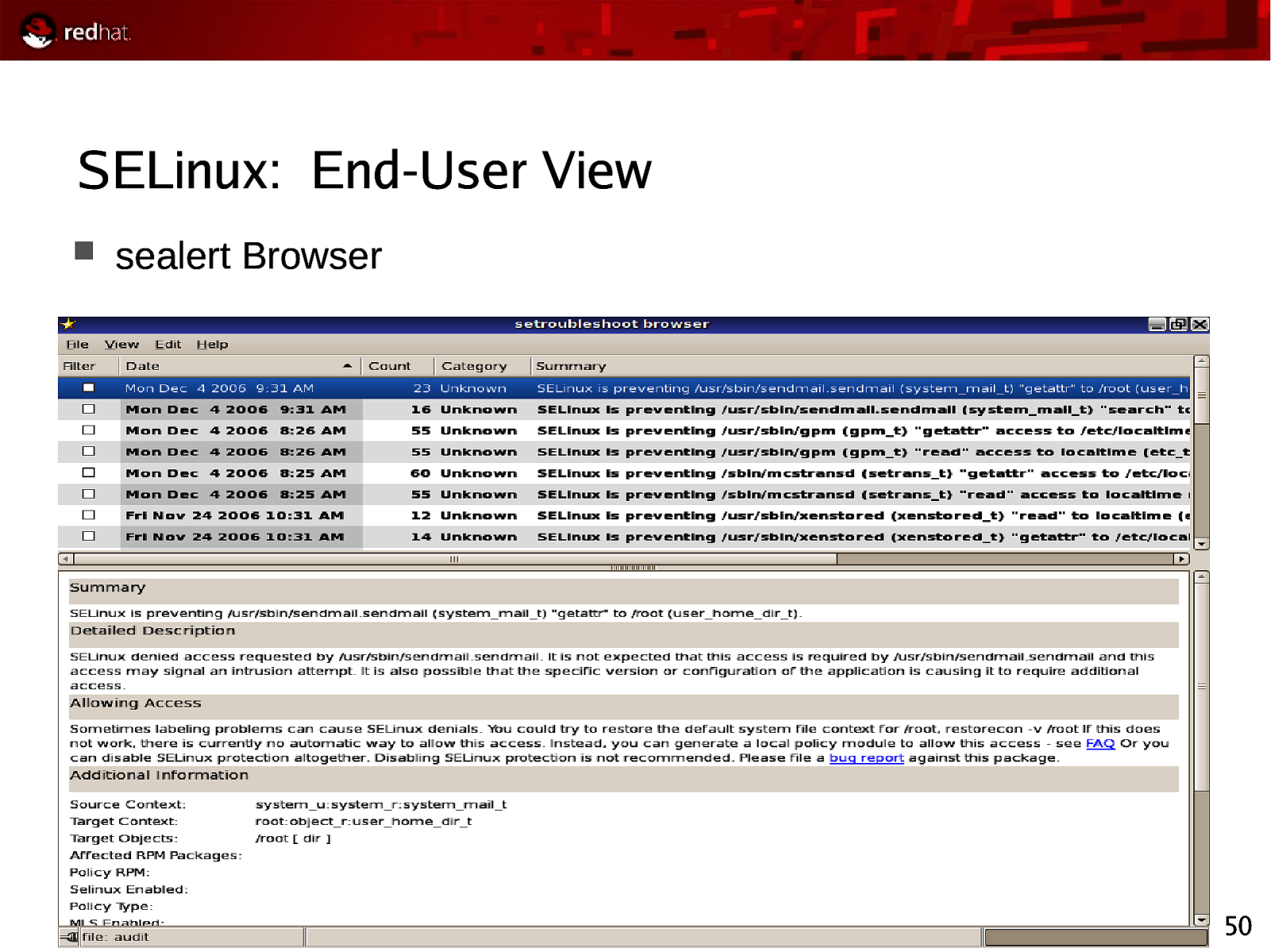
SELinux: End-User View sealert Browser 50
Slide 51
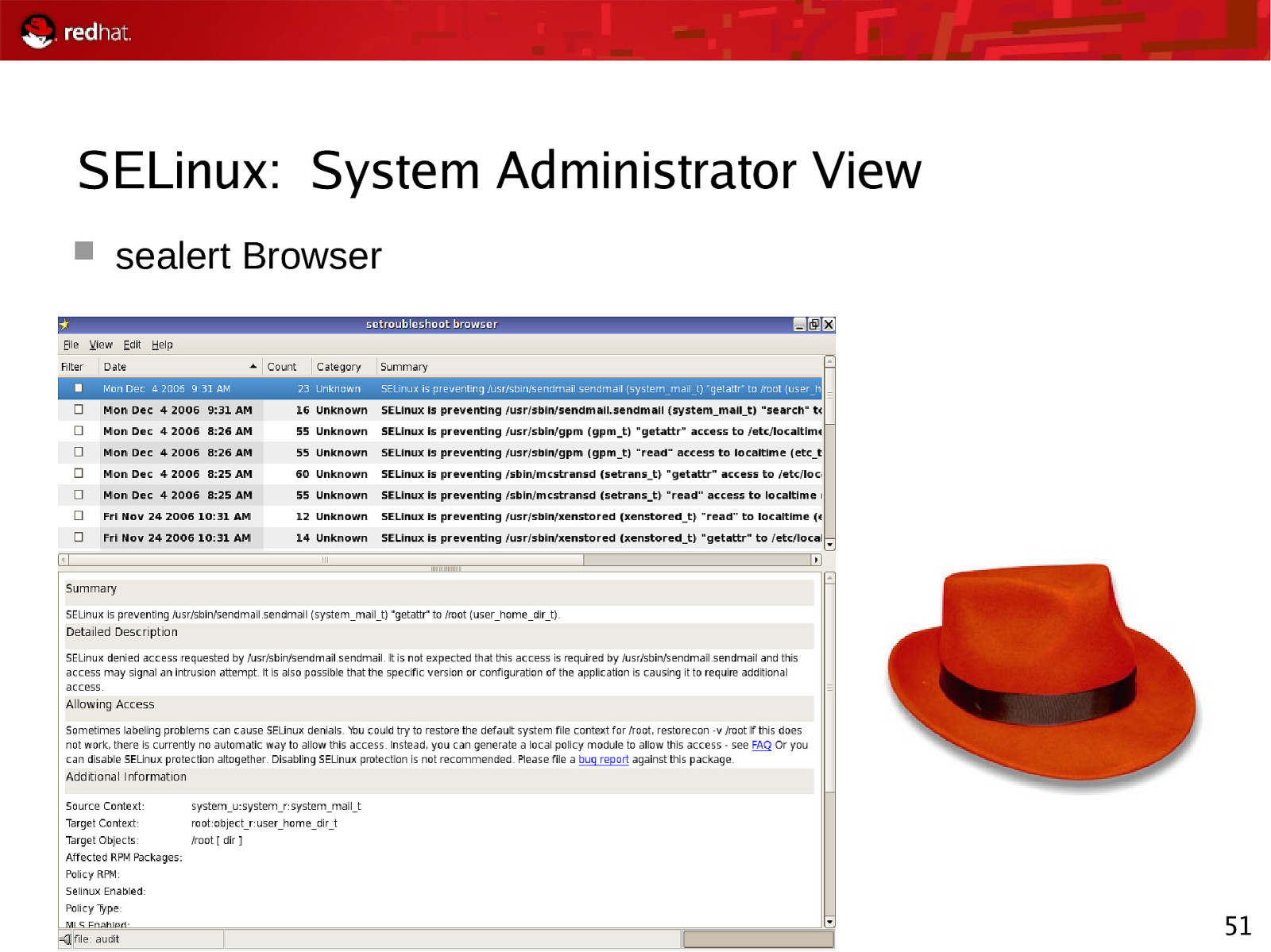
SELinux: System Administrator View sealert Browser 51
Slide 52
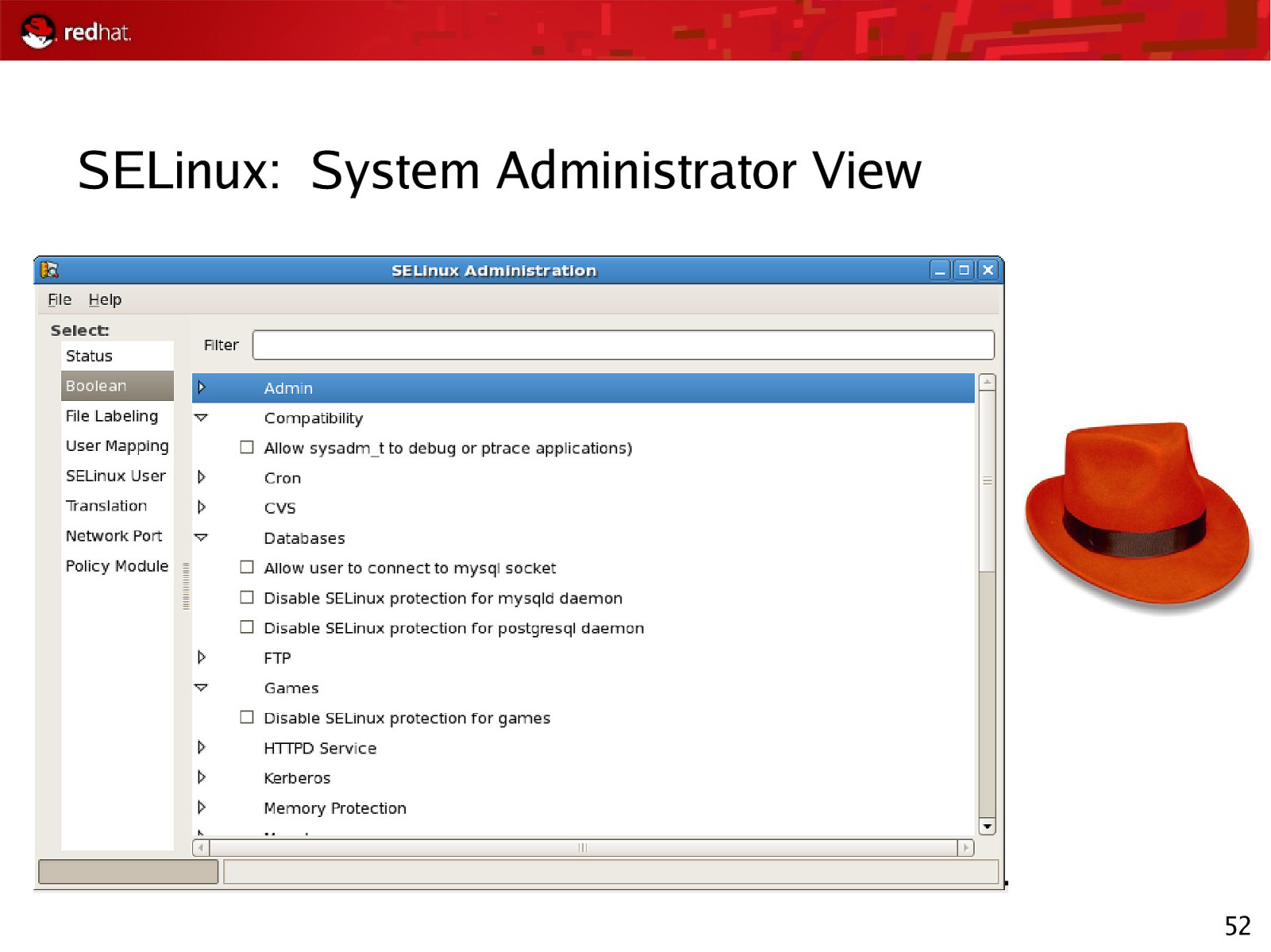
SELinux: System Administrator View 52
Slide 53
SELinux: System Administrator View Using audit2allow & semanage You are experiencing SELinux errors You know that these errors are blocking legitimate usage Be aware that changes to your SELinux policy could compromise the security of your system. 53
Slide 54
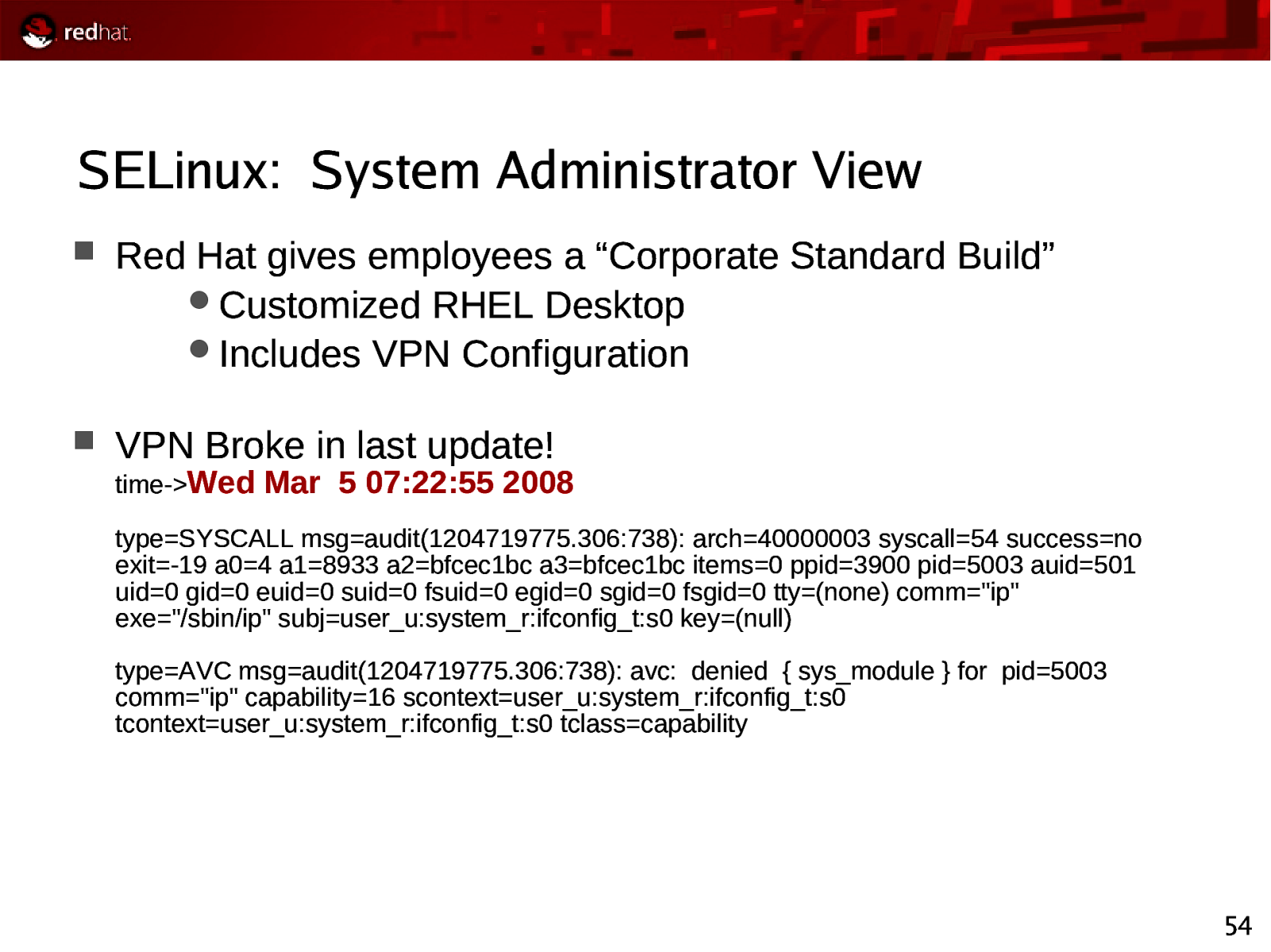
SELinux: System Administrator View Red Hat gives employees a “Corporate Standard Build” Customized RHEL Desktop Includes VPN Configuration VPN Broke in last update! time->Wed Mar 5 07:22:55 2008 type=SYSCALL msg=audit(1204719775.306:738): arch=40000003 syscall=54 success=no exit=-19 a0=4 a1=8933 a2=bfcec1bc a3=bfcec1bc items=0 ppid=3900 pid=5003 auid=501 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=(none) comm=”ip” exe=”/sbin/ip” subj=user_u:system_r:ifconfig_t:s0 key=(null) type=AVC msg=audit(1204719775.306:738): avc: denied { sys_module } for pid=5003 comm=”ip” capability=16 scontext=user_u:system_r:ifconfig_t:s0 tcontext=user_u:system_r:ifconfig_t:s0 tclass=capability 54
Slide 55
SELinux: System Administrator View <snip> …………. comm=”ip” exe=”/sbin/ip” subj=user_u:system_r:ifconfig_t:s0 key=(null) type=AVC msg=audit(1204719775.306:738): avc: denied { sys_module } for pid=5003 comm=”ip” capability=16 scontext=user_u:system_r:ifconfig_t:s0 tcontext=user_u:system_r:ifconfig_t:s0 tclass=capability …………. </snip>
ausearch -x “/sbin/ip” | audit2allow -M myVPNfix # semodule -i myVPNfix
55
Slide 56
SELinux: Auditor View Centralized Logging is a must! aureport # aureport –summary ausearch # ausearch -ul swells 56
Slide 57
aide Intrusion Detection program Ships with RHEL5
yum install aide # aide –init # chmod 777 /etc/hosts # aide - -check AIDE found differences between database and filesystem!! Changed files: changed:/etc/hosts Detailed information about changes: File: /etc/hosts Permissions: -rw-r—r— , -rwxrwxrwx 57
Slide 58
aide v auditd auditd built into RHEL Used in Common Criteria, DCID, STIG compliance -a exit,possible -S chmod -F arch=${ARCH} -F success=0 -F success!=0 -a exit,always -S open -S pipe -S mkdir -S creat -F arch=${ARCH} -F success=0 -a exit,always -S rename -F arch=${ARCH} -F success!=0 58