SECURING INTELLIGENCE IN AN OPEN HYBRID CLOUD Stories from the DoD and IC Shawn Wells Chief Security Strategist U.S. Public Sector shawn@redhat.com 24 August 2016
Slide 1

Slide 2

FOUNDATIONAL BLOCKING & TACKLING Key infrastructure themes from Jennifer Kron’s presentation: • Functional testing for identity & access management, data protection, audit • Perform continuous diagnostics and monitoring • Must have consistent measurements across multiple environments • Standardized implementations • Baselines? • Service Catalogs? • Platform as a Service (PaaS)?
Slide 3

FEDERATED DATA ACCESS Key data themes from Jennifer Kron’s presentation: • “Build to Share, BUT securely” • How do we ensure data contains attributes and security labels/tags, and build access restrictions from this metedata?
Slide 4

SECURITY AUTOMATION + TOOLING FOR HYBRID CLOUDS
Slide 5

PROJECT • Deliver practical security guidance, baselines, and associated validation mechanisms using Secure Content Automation Protocol (SCAP) • Current upstream source for NSA, NIST, and Red Hat Configuration Guides – DISA JBoss Enterprise Application Platform STIG – DISA Red Hat Enterprise Linux 6 & 7 STIGs – Department of Justice CJIS Baselines – National Security Agency SNAC Guide
Slide 6

PROJECT CONTRIBUTORS
Slide 7

PROJECT • Maps specific security tests to formalized policies – NIST 800-53 rev4 – DISA Operating System SRG – NIST CCE • Delivering DoD and IC Automated Baselines today! • DoD STIG: Joint development with NSA, DISA FSO • C2S: Developed for CIA C2S Linux images • CS2: Developed with NSA TS for GOVCLOUD systems • CJIS: FBI criminal justice systems
Slide 8
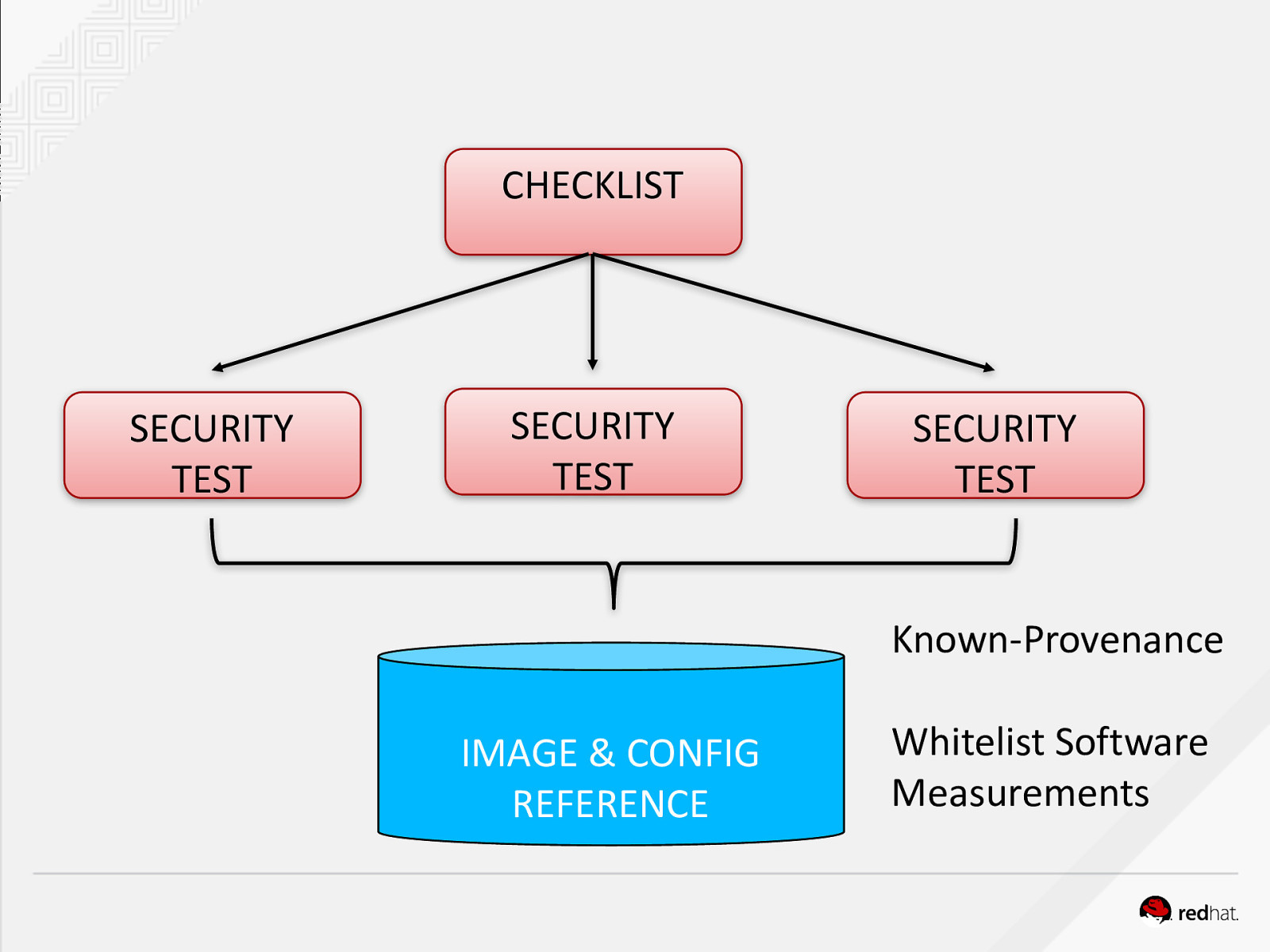
CHECKLIST SECURITY TEST SECURITY TEST SECURITY TEST Known-Provenance IMAGE & CONFIG REFERENCE Whitelist Software Measurements
Slide 9
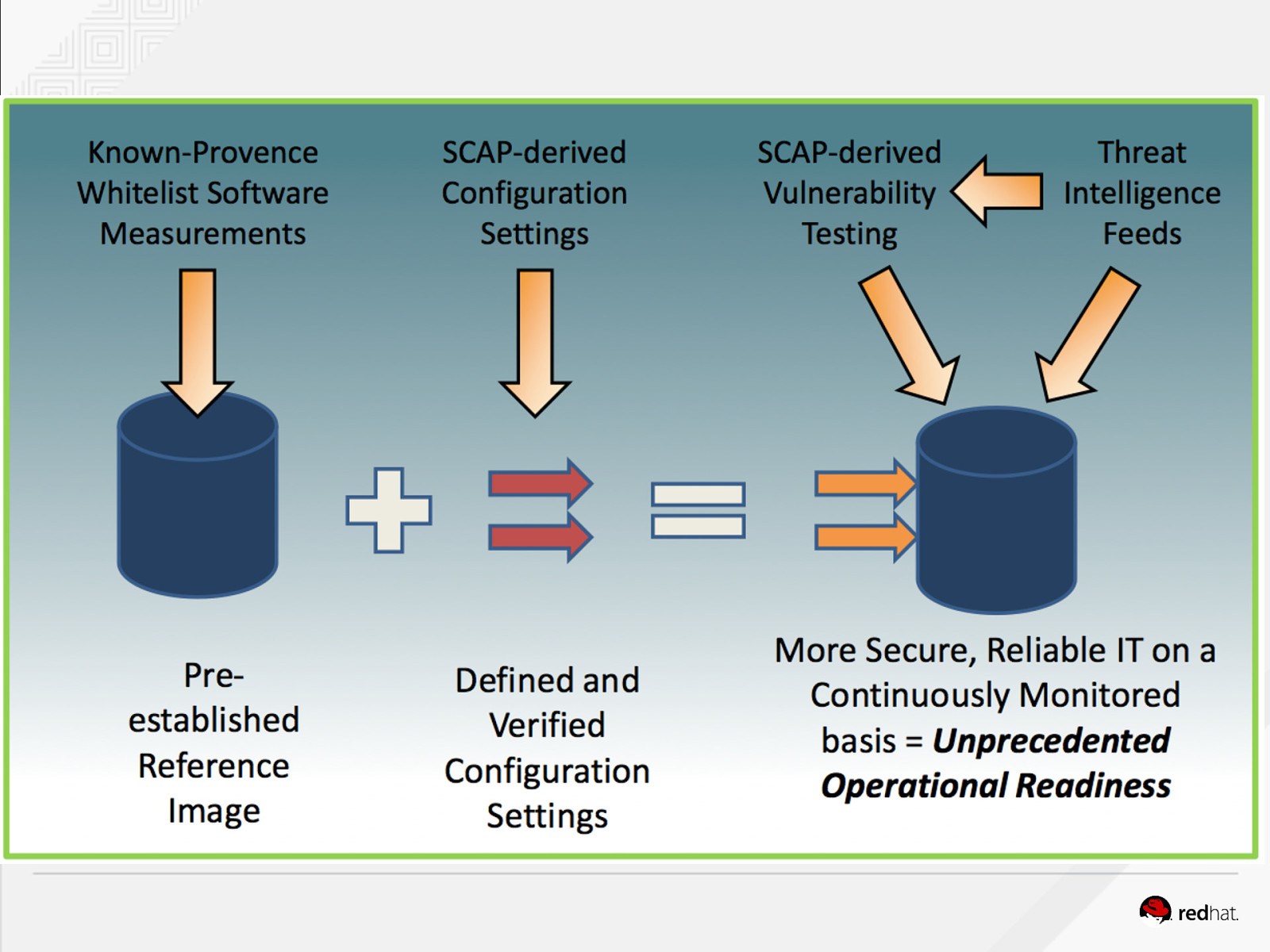
Slide 10

STRUCTURED DATA SERVICES ACROSS HYBRID CLOUDS
Slide 11
Slide 12
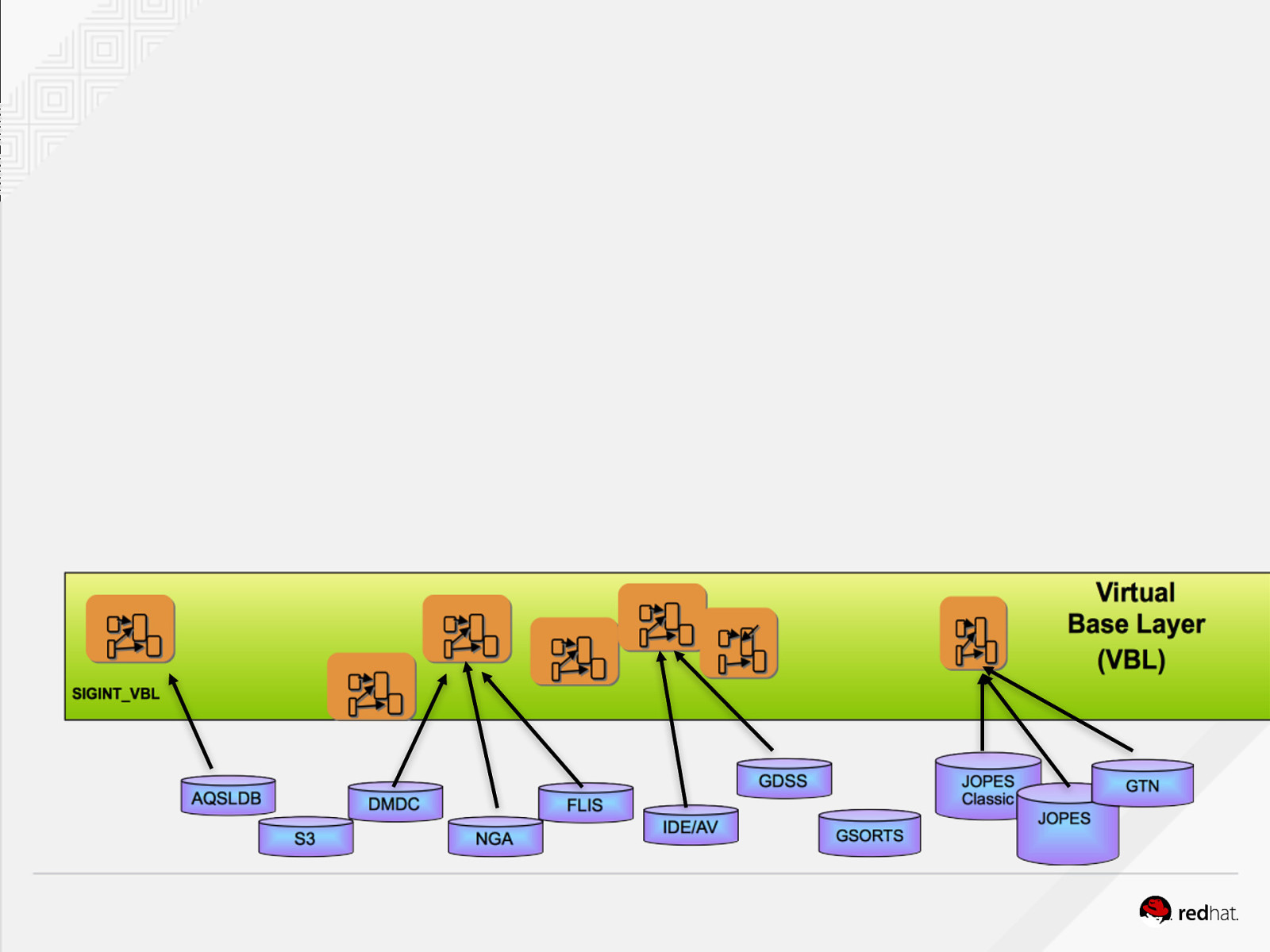
Slide 13
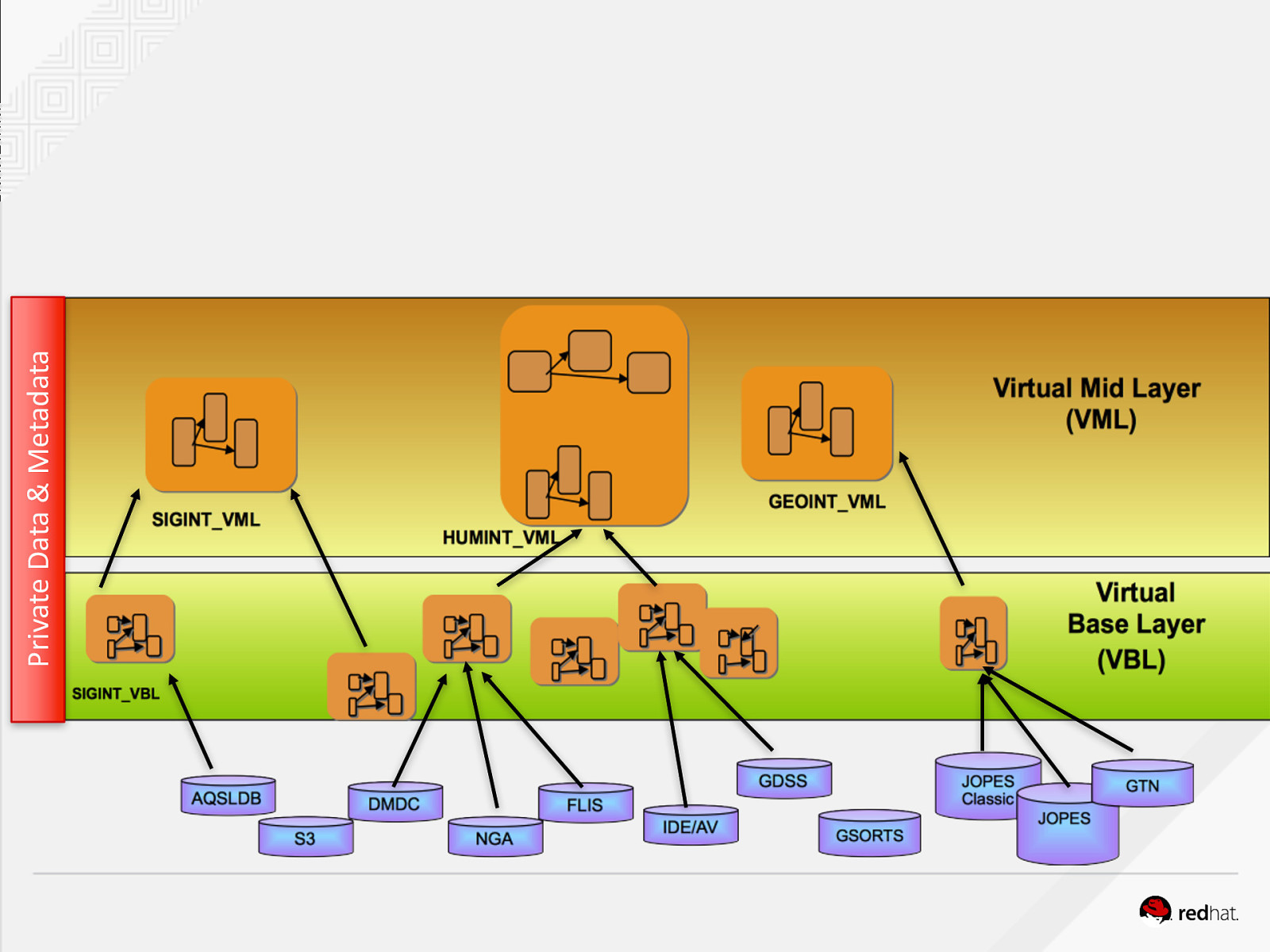
Private Data & Metadata
Slide 14
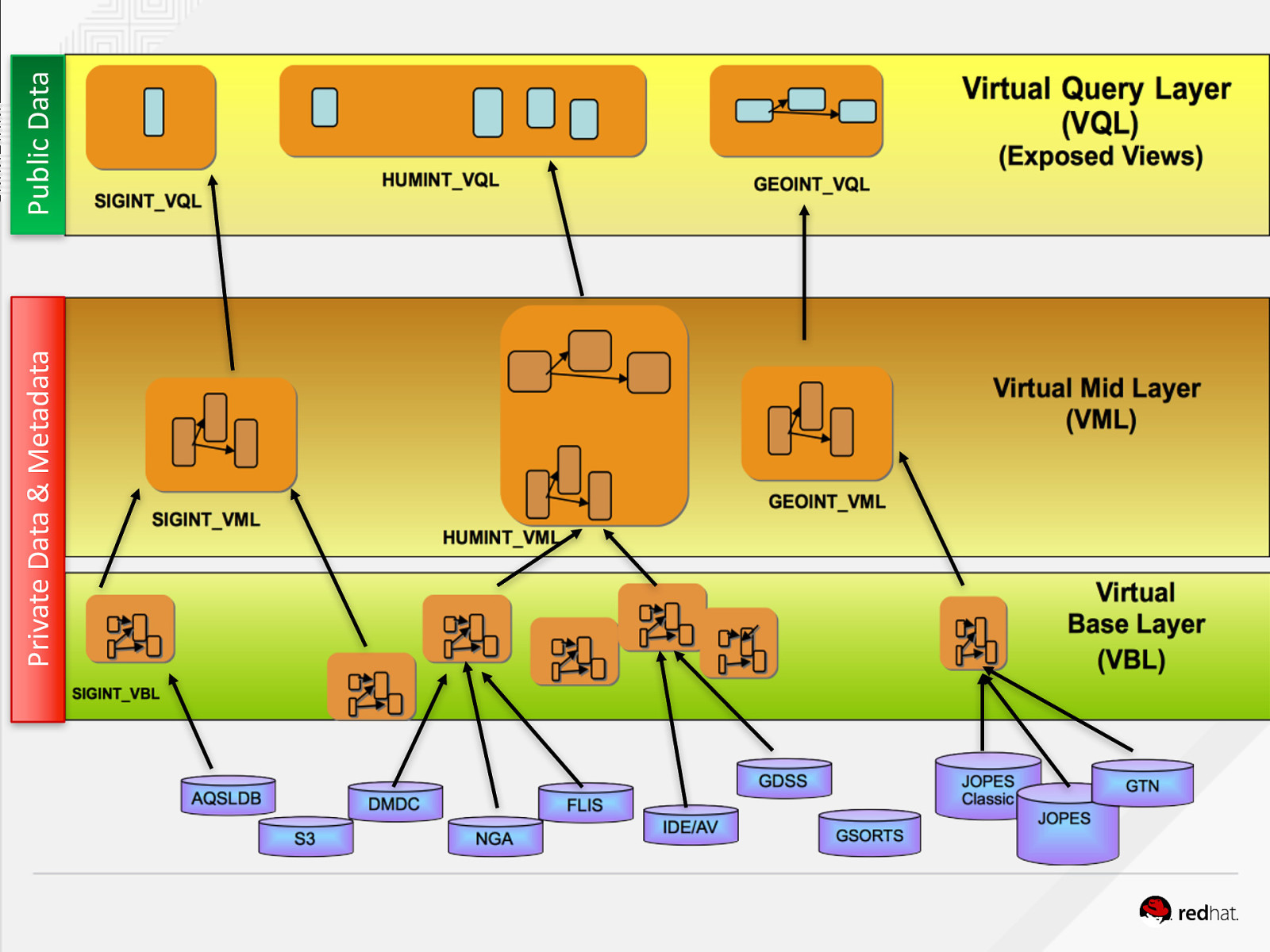
Private Data & Metadata Public Data
Slide 15
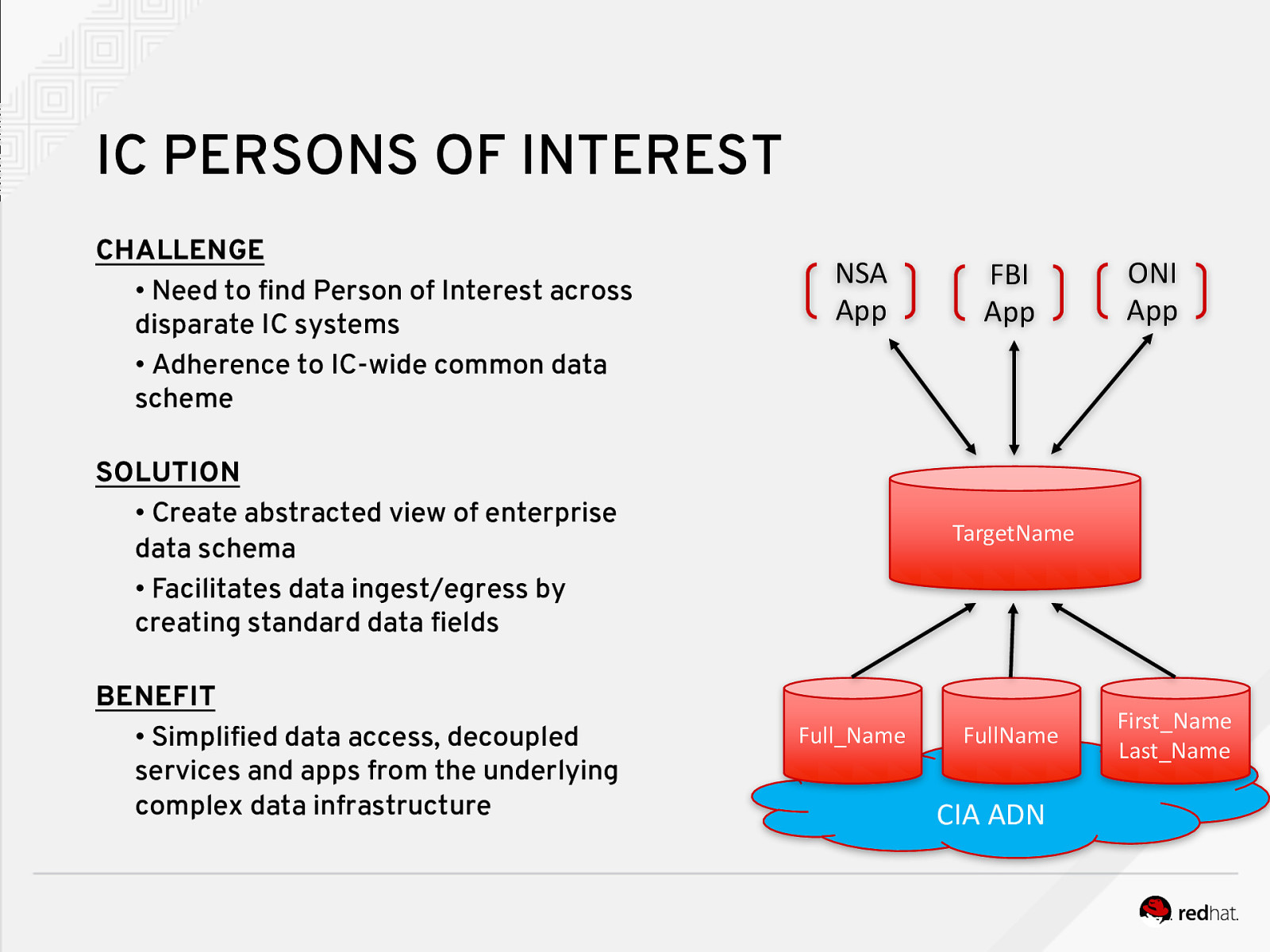
IC PERSONS OF INTEREST CHALLENGE • Need to find Person of Interest across disparate IC systems • Adherence to IC-wide common data scheme NSA App SOLUTION • Create abstracted view of enterprise data schema • Facilitates data ingest/egress by creating standard data fields BENEFIT • Simplified data access, decoupled services and apps from the underlying complex data infrastructure FBI App ONI App TargetName Full_Name FullName CIA ADN First_Name Last_Name
Slide 16
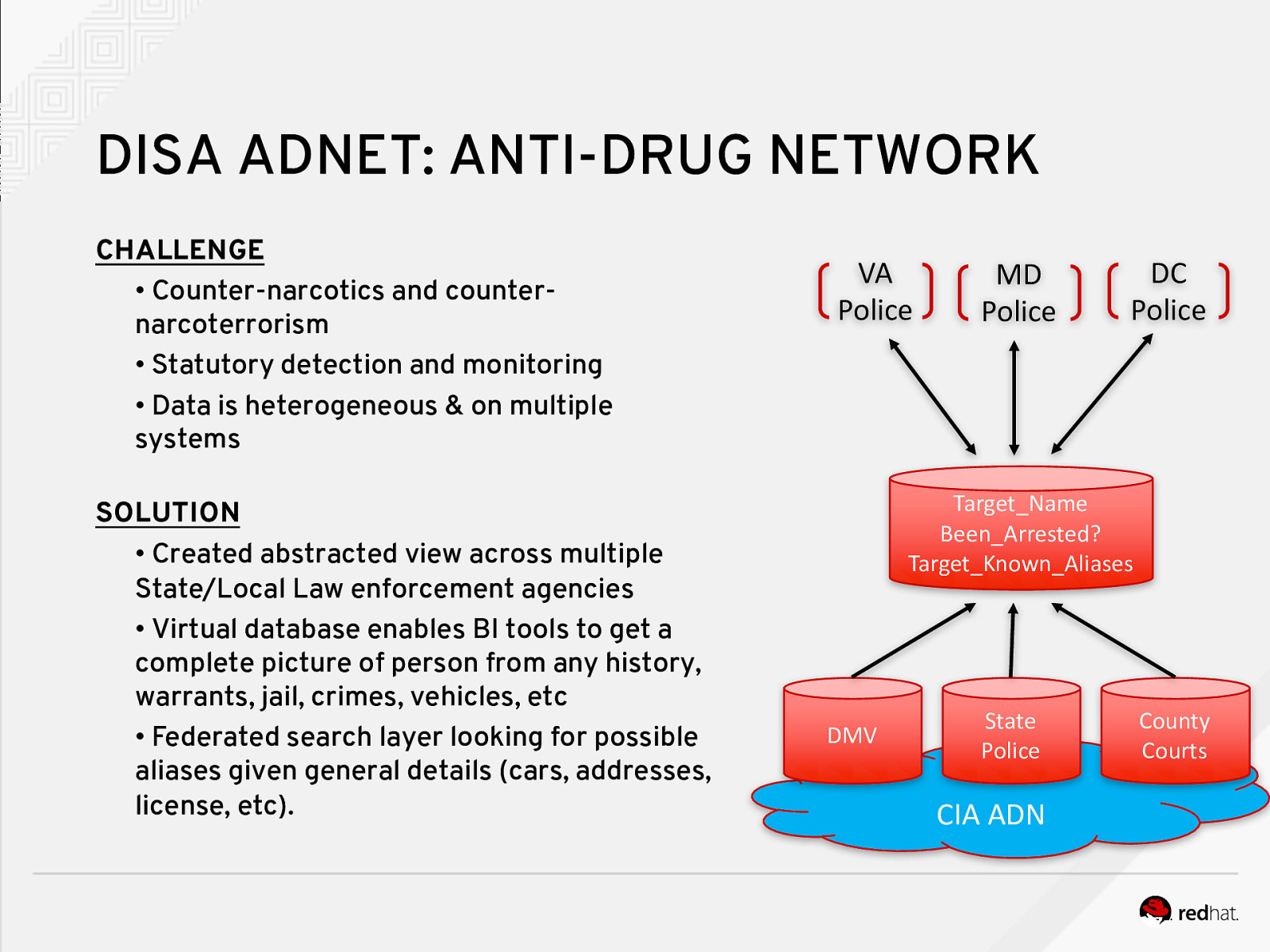
DISA ADNET: ANTI-DRUG NETWORK CHALLENGE • Counter-narcotics and counternarcoterrorism • Statutory detection and monitoring • Data is heterogeneous & on multiple systems SOLUTION • Created abstracted view across multiple State/Local Law enforcement agencies • Virtual database enables BI tools to get a complete picture of person from any history, warrants, jail, crimes, vehicles, etc • Federated search layer looking for possible aliases given general details (cars, addresses, license, etc). VA Police MD Police DC Police Target_Name Been_Arrested? Target_Known_Aliases DMV State Police CIA ADN County Courts
Slide 17

BUILDING YOUR OPEN HYBRID CLOUD
Slide 18

EVERYONE IS A TECHNOLOGY COMPANY TODAY.
Slide 19

WHEN EVERYONE IS A TECH COMPANY, I.T. CAN BE A SOURCE OF COMPETITIVE ADVANTAGE.
Slide 20
THESE TECHNOLOGIES ARE DRIVEN BY OPEN SOURCE OPEN SOURCE MEANS COMMUNITY MEMBERS CAN SEE, LEARN FROM, IMPROVE, MODIFY, AND SHARE THE SOURCE CODE TO SOLVE CHALLENGES AND MEET NEEDS.
Slide 21
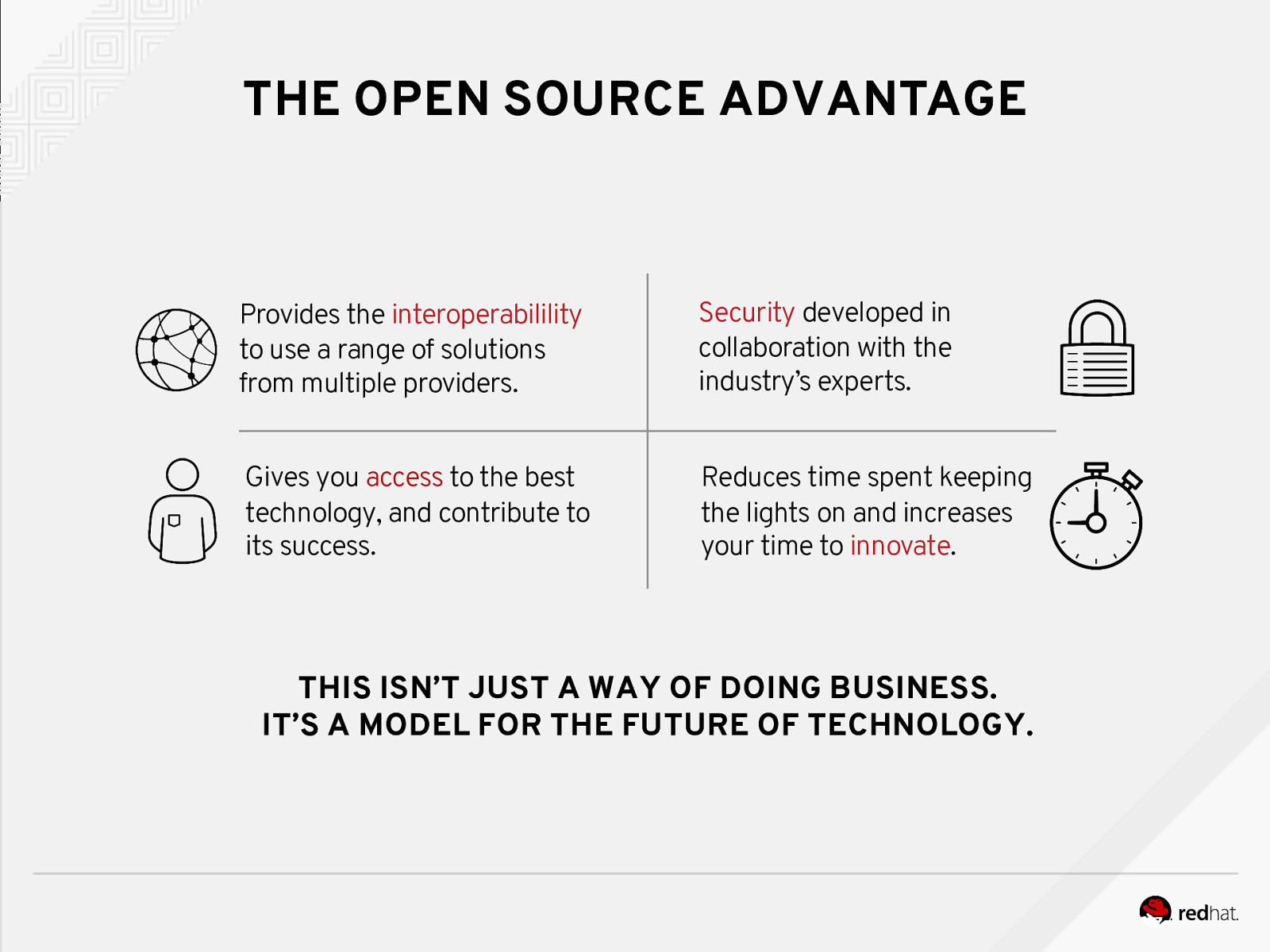
THE OPEN SOURCE ADVANTAGE Provides the interoperabilility to use a range of solutions from multiple providers. Security developed in collaboration with the industry’s experts. Gives you access to the best technology, and contribute to its success. Reduces time spent keeping the lights on and increases your time to innovate. THIS ISN’T JUST A WAY OF DOING BUSINESS. IT’S A MODEL FOR THE FUTURE OF TECHNOLOGY.
Slide 22

RED HAT MAKES OPEN SOURCE READY FOR THE ENTERPRISE RED HAT DELIVERS THE INNOVATION OF OPEN SOURCE PROJECTS AS PREDICTABLE, RELIABLE, AND SECURE PRODUCTS. COMMON CRITERIA – FIPS 140-2 – DoD STIGs – CNSSI 1253
Slide 23

THANK YOU! plus.google.com/+RedHat facebook.com/redhatinc linkedin.com/company/red-hat twitter.com/RedHatNews youtube.com/user/RedHatVideos