The Linux Audit Subsystem Deep Dive SHARE Denver Colorado Convention Center, Korbel 4b 24-Aug 2009 1100-Noon Shawn Wells swells@redhat.com Red Hat, Inc
Slide 1

Slide 2

Session Themes Why is Linux Auditing needed? What can it do for me? How does it work? How do events get audited? How do I make sense of all the data? Yes, I work for Red Hat. Yes, the demos & examples are on RHEL. But we’re SHAREing here, and everything is applicable to SuSE as well. 2
Slide 3
Demos / Examples 3
Slide 4
Why is Linux Auditing needed? What can it do for me? Taken from a customers INFOSEC policy (GEN002720: CAT II) The SA will configure the auditing system to audit logon (unsuccessful and successful) and logout (successful) (GEN002760: CAT II) The SA will configure the auditing system to audit unauthorized access attempts to files (unsuccessful) (GEN002780: CAT II) The SA will configure the auditing system to audit use of privileged commands (unsuccessful and successful) (GEN002840: CAT II) The SA will configure the auditing system to audit all security personnel actions (GEN002820: CAT II) The SA will configure the auditing system to audit all system administration actions 4
Slide 5

Why is Linux Auditing needed? What can it do for me? Some of the design requirements for the audit system: Shall be able to record at least the following Date and time of event, type of event, subject identity, outcome Sensitivity labels of subjects and objects Be able to associate event with identity of user causing it All modifications to audit configuration and attempted access to logs All use of authentication mechanisms Changes to any trusted database Attempts to import/export information Be able to include/exclude events based on user identity, subject/object, labels, other attributes 5
Slide 6

Why is Linux Auditing needed? What can it do for me? Linux Audit is a system to Collect information regarding events occurring on the system(s) Kernel events (syscall events) User events (audit-enabled programs) Form a log recording and describing each event (/var/log/audit/audit.log) Components to assist analysing the log 6
Slide 7

7
Slide 8
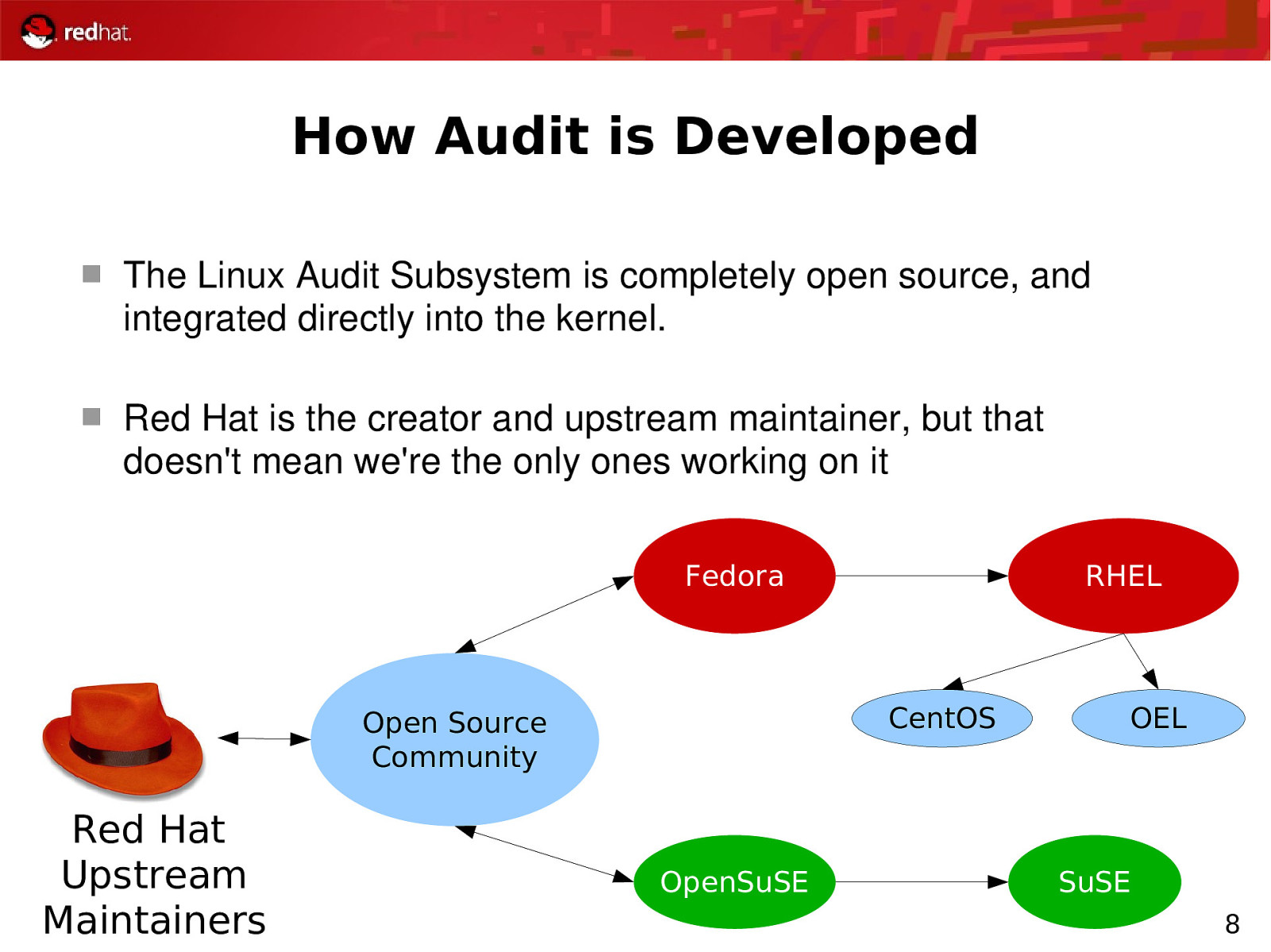
How Audit is Developed The Linux Audit Subsystem is completely open source, and integrated directly into the kernel. Red Hat is the creator and upstream maintainer, but that doesn’t mean we’re the only ones working on it Fedora CentOS Open Source Community Red Hat Upstream Maintainers RHEL OpenSuSE OEL SuSE 8
Slide 9
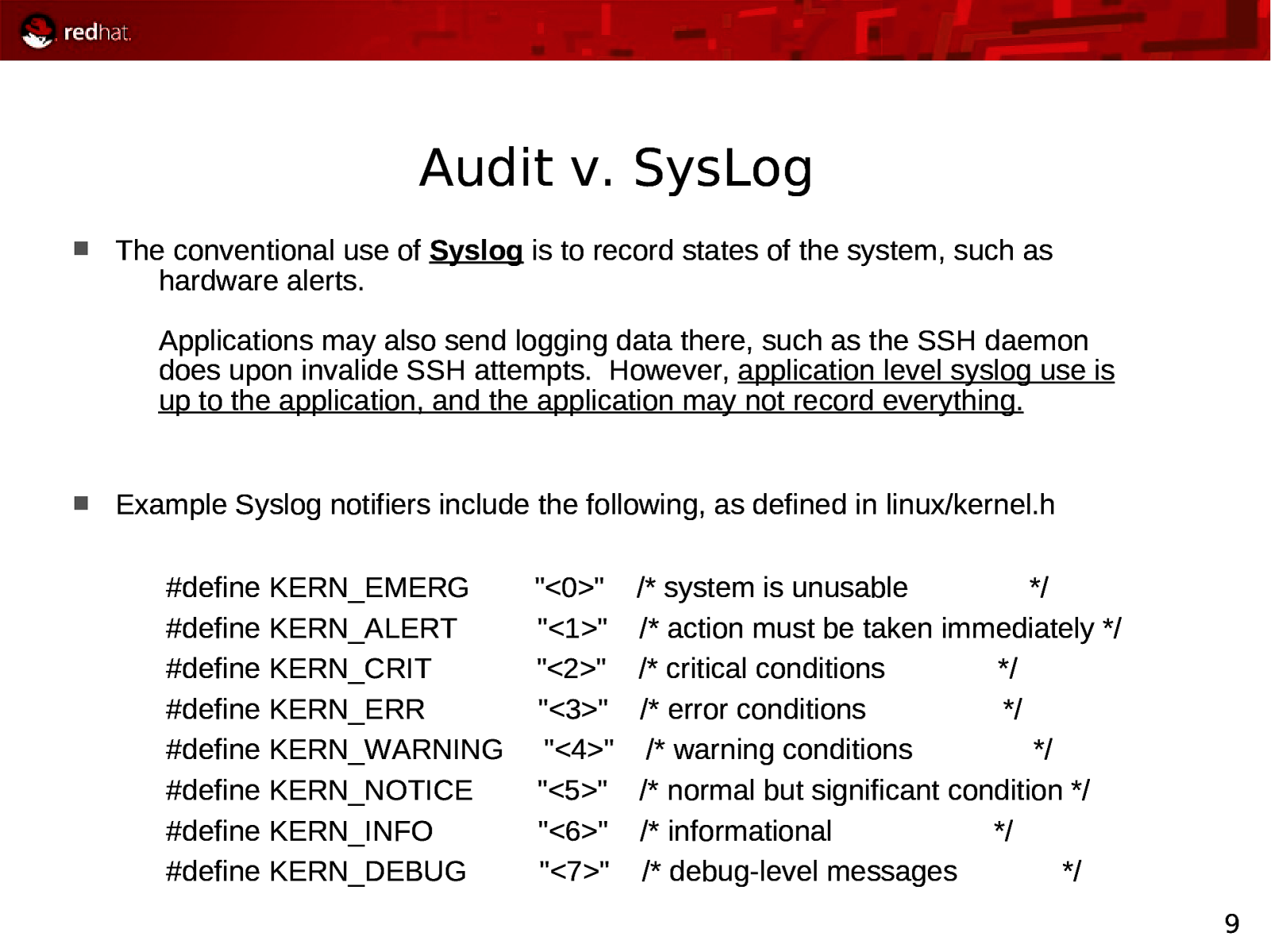
Audit v. SysLog The conventional use of Syslog is to record states of the system, such as hardware alerts. Applications may also send logging data there, such as the SSH daemon does upon invalide SSH attempts. However, application level syslog use is up to the application, and the application may not record everything. Example Syslog notifiers include the following, as defined in linux/kernel.h #define KERN_EMERG #define KERN_ALERT #define KERN_CRIT #define KERN_ERR #define KERN_WARNING #define KERN_NOTICE #define KERN_INFO #define KERN_DEBUG “<0>” “<1>” “<2>” “<3>” “<4>” “<5>” “<6>” “<7>” /* system is unusable / / action must be taken immediately / / critical conditions / / error conditions / / warning conditions / / normal but significant condition / / informational / / debug-level messages */ 9
Slide 10
Audit v. SysLog Since there is no assurance that applications will completely log all user actions, we offloaded that responsibility to the Linux kernel. Thus, the Linux Audit subsystem was born. When audit is defined, every single system call will pass through the Audit subsystem, which has rules defined at /etc/audit/audit.rules Audit has the ability to log BEFORE and AFTER an action: this is extremely useful. 10
Slide 11

How does it work?
Slide 12

Why is Linux Auditing needed? What can it do for me? (GEN002760: CAT II) The SA will configure the auditing system to audit unauthorized access attempts to files (unsuccessful) But How? 12
Slide 13
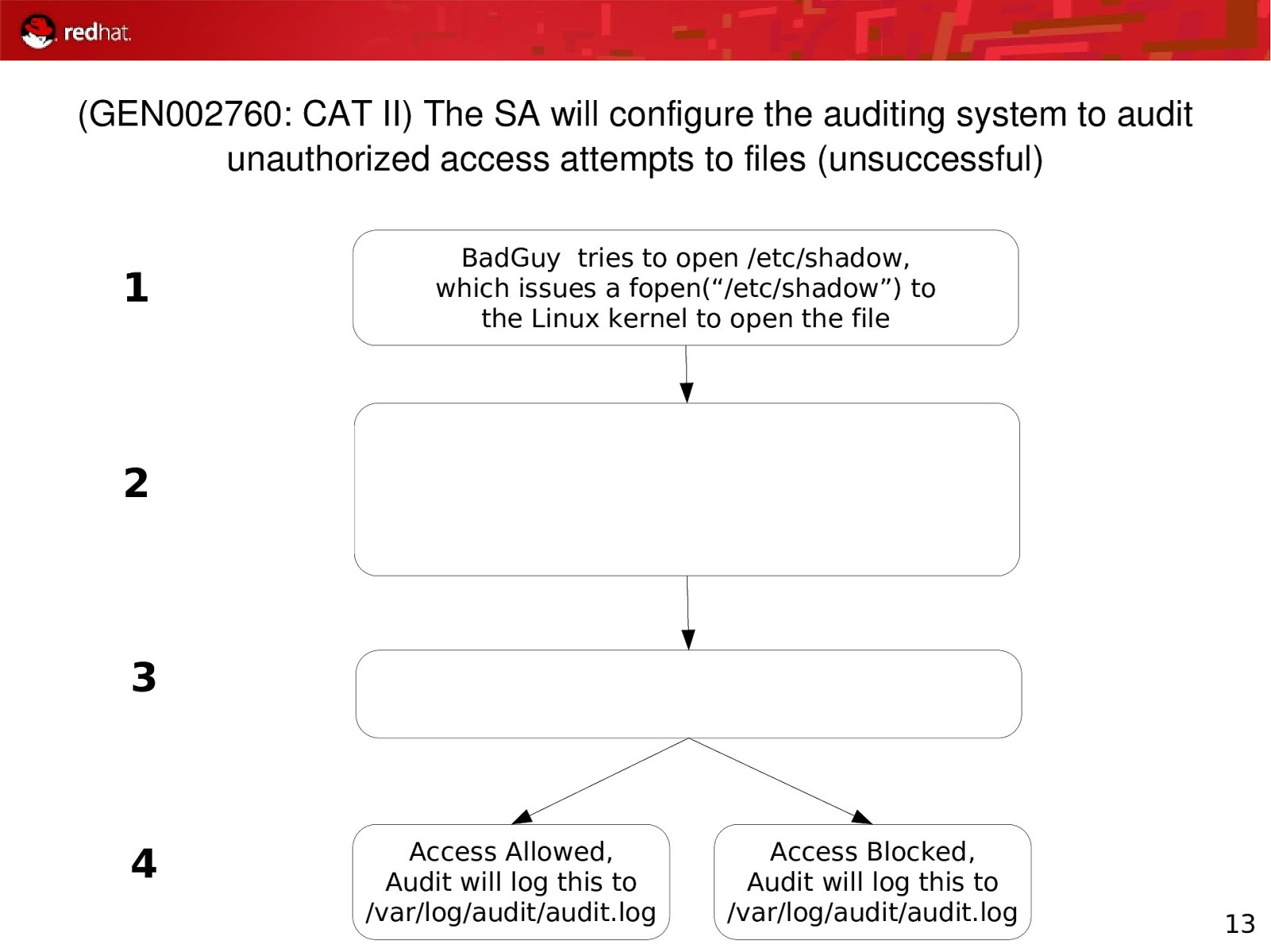
(GEN002760: CAT II) The SA will configure the auditing system to audit unauthorized access attempts to files (unsuccessful) 1 BadGuy tries to open /etc/shadow, which issues a fopen(“/etc/shadow”) to the Linux kernel to open the file 2 3 4 Access Allowed, Audit will log this to /var/log/audit/audit.log Access Blocked, Audit will log this to /var/log/audit/audit.log 13
Slide 14
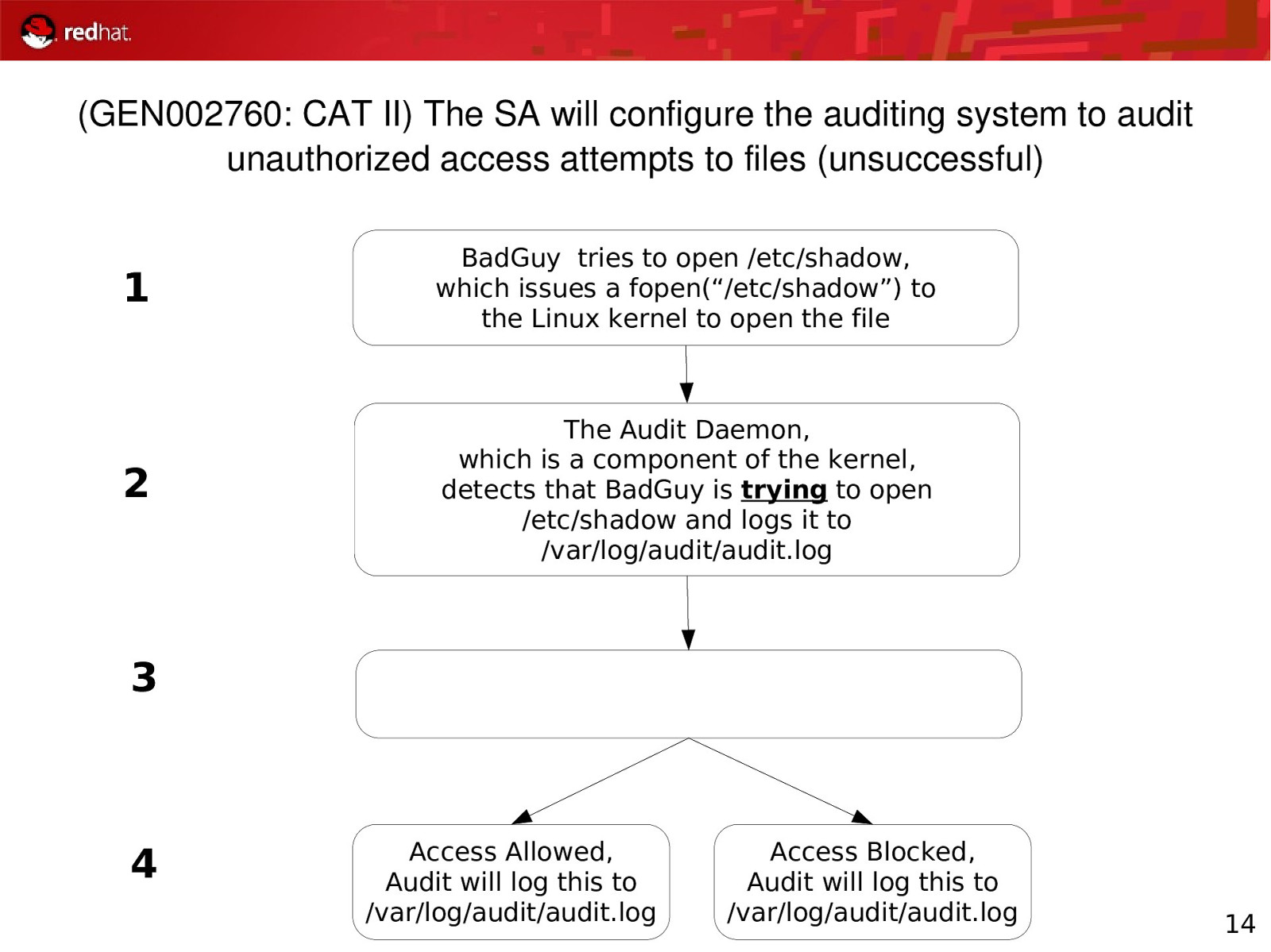
(GEN002760: CAT II) The SA will configure the auditing system to audit unauthorized access attempts to files (unsuccessful) 1 BadGuy tries to open /etc/shadow, which issues a fopen(“/etc/shadow”) to the Linux kernel to open the file 2 The Audit Daemon, which is a component of the kernel, detects that BadGuy is trying to open /etc/shadow and logs it to /var/log/audit/audit.log 3 4 Access Allowed, Audit will log this to /var/log/audit/audit.log Access Blocked, Audit will log this to /var/log/audit/audit.log 14
Slide 15
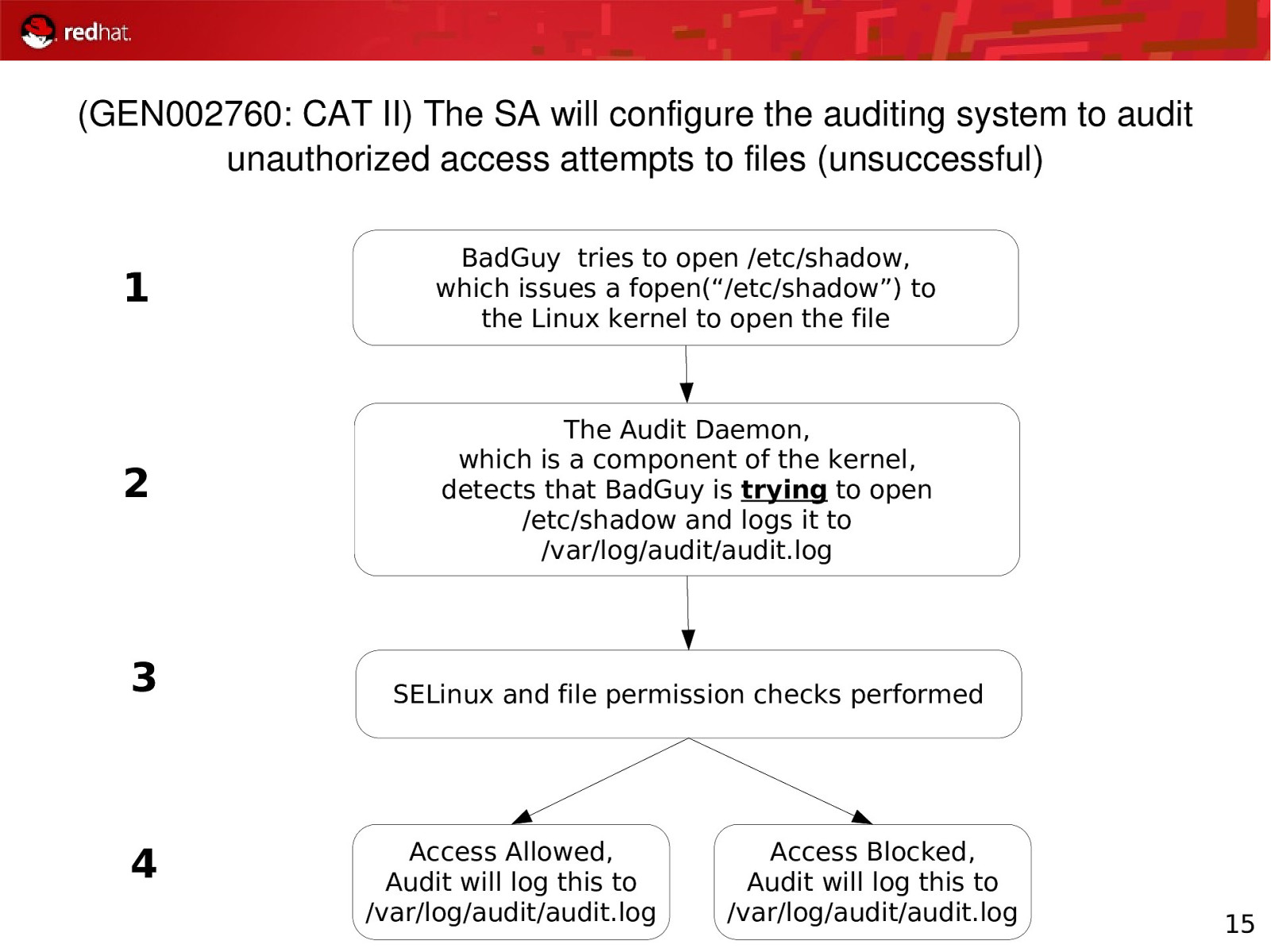
(GEN002760: CAT II) The SA will configure the auditing system to audit unauthorized access attempts to files (unsuccessful) 1 BadGuy tries to open /etc/shadow, which issues a fopen(“/etc/shadow”) to the Linux kernel to open the file 2 The Audit Daemon, which is a component of the kernel, detects that BadGuy is trying to open /etc/shadow and logs it to /var/log/audit/audit.log 3 4 SELinux and file permission checks performed Access Allowed, Audit will log this to /var/log/audit/audit.log Access Blocked, Audit will log this to /var/log/audit/audit.log 15
Slide 16
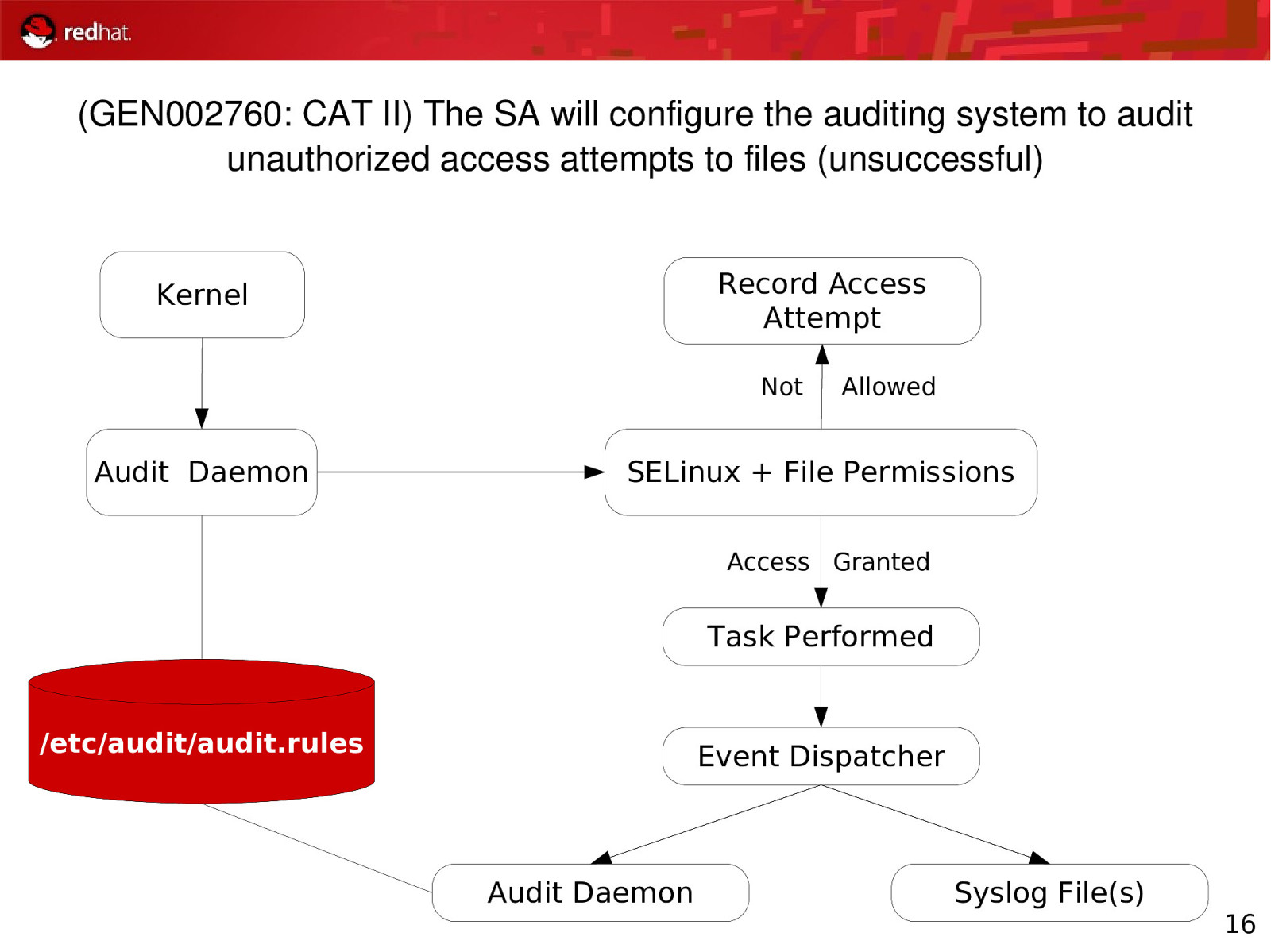
(GEN002760: CAT II) The SA will configure the auditing system to audit unauthorized access attempts to files (unsuccessful) Record Access Attempt Kernel Not Audit Daemon Allowed SELinux + File Permissions Access Granted Task Performed /etc/audit/audit.rules Event Dispatcher Audit Daemon Syslog File(s) 16
Slide 17

tail -F /var/log/audit/audit.log $ cat /etc/shadow [as non-root] 17
Slide 18

Configuration via auditctl auditctl is a command line utility to control the behavior, get status, and add or delete rules Useful for kickstarts / system automation Useful for making non-persistent changes Reminder: use auditctl, then update audit.rules to be persistent Arguments to familiarize yourself with -k {key} Sets a filter on an audit rule, which you can query against via the ausearch utility -F arch={b32 , b64} -w {file} Selects the architecture libraries to use when logging Watches for edits to a file, such as a user modifying /etc/shadow All arguments are in the man page (man auditctl) 18
Slide 19

LSPP, CAPP, NISPOM example rules with auditctl 19
Slide 20
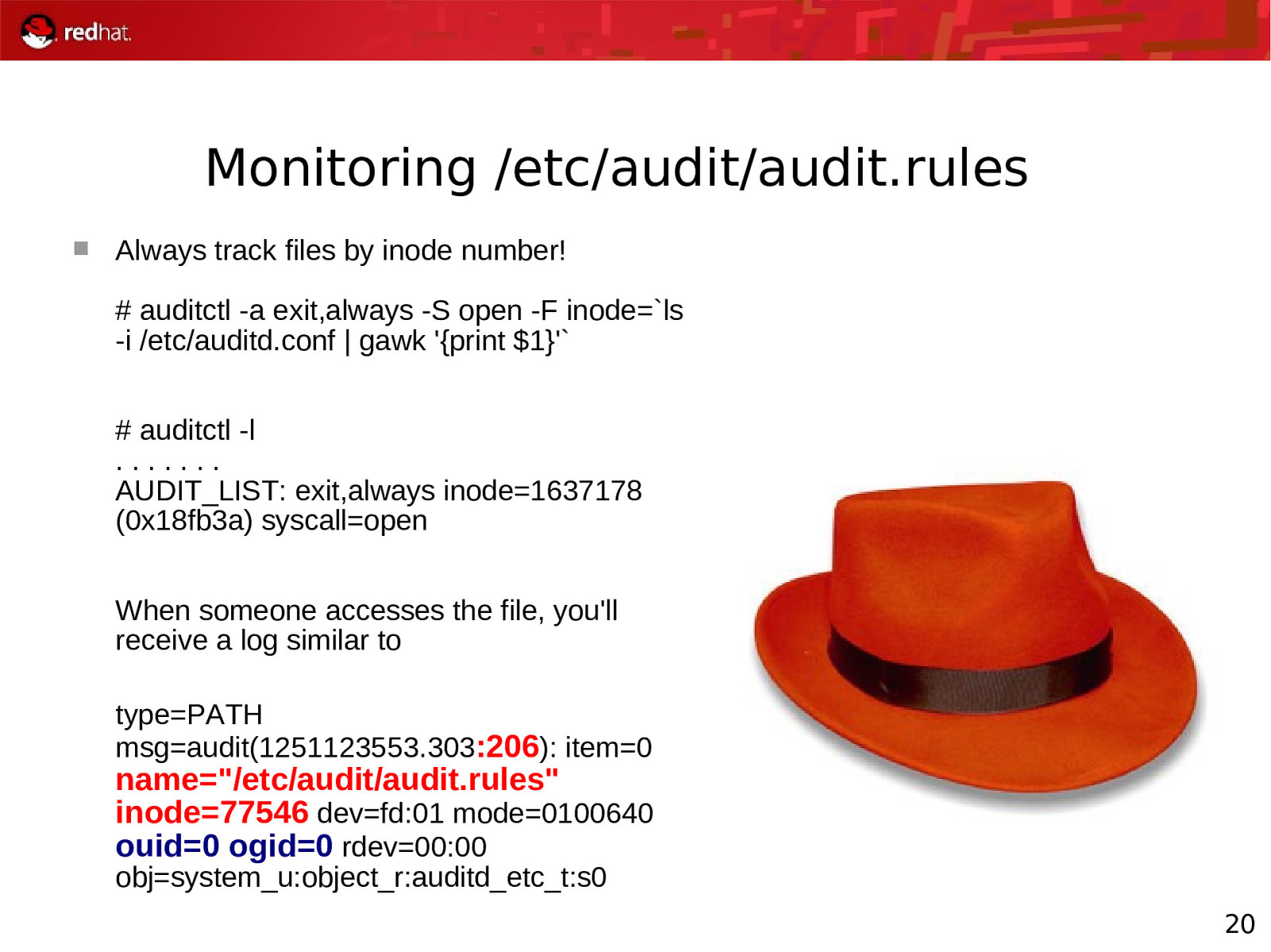
Monitoring /etc/audit/audit.rules
Always track files by inode number! # auditctl -a exit,always -S open -F inode=ls -i /etc/auditd.conf | gawk '{print $1}' # auditctl -l ……. AUDIT_LIST: exit,always inode=1637178 (0x18fb3a) syscall=open When someone accesses the file, you’ll receive a log similar to type=PATH msg=audit(1251123553.303:206): item=0
name=”/etc/audit/audit.rules” inode=77546 dev=fd:01 mode=0100640 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:auditd_etc_t:s0
20
Slide 21

Configuration via system-config-audit 21
Slide 22

How do I make sense of the data?
Slide 23

Usage of ausearch Ausearch is a command-line utility to query your audit logs ausearch -f <file> ausearch -ui <user> 23
Slide 24

ausearch Example (1/3) auditctl -l | grep shadow LIST_RULES: exit,always watch=/etc/gshadow perm=wa key=auth LIST_RULES: exit,always watch=/etc/shadow perm=wa key=auth sudo -u sdw cat /etc/shadow cat: /etc/shadow: Permission denied 24
Slide 25

ausearch Example (2/3) aureport -r Summary Report ====================== Range of time in logs: 06/21/2009 14:43:44.362 - 08/24/2009 10:29:29.498 Selected time for report: 06/21/2009 14:43:44 - 08/24/2009 10:29:29.498 Number of changes in configuration: 164 Number of changes to accounts, groups, or roles: 32 Number of logins: 2 Number of failed logins: 6 Number of failed syscalls: 290 25
Slide 26
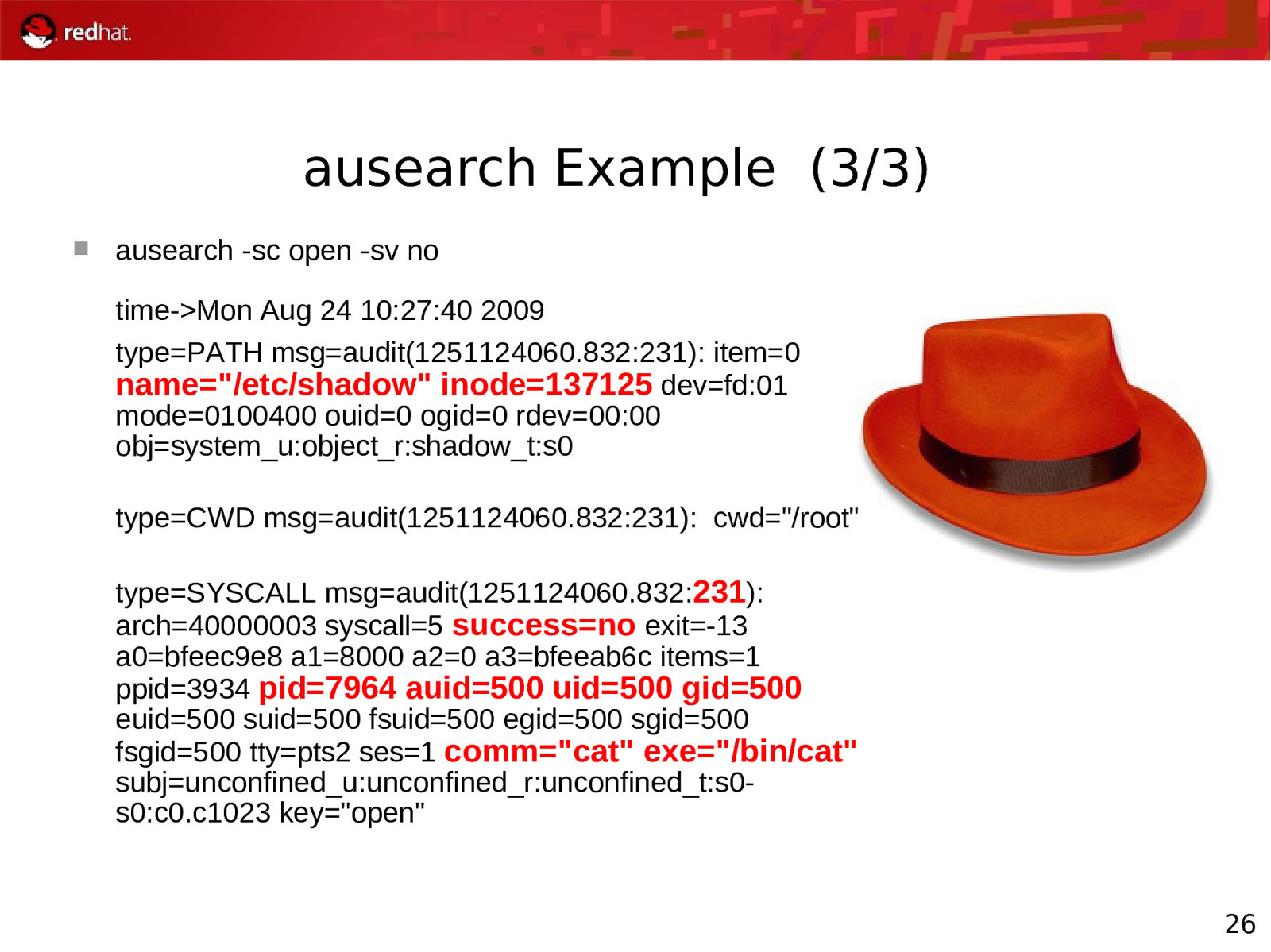
ausearch Example (3/3) ausearch -sc open -sv no time->Mon Aug 24 10:27:40 2009 type=PATH msg=audit(1251124060.832:231): item=0 name=”/etc/shadow” inode=137125 dev=fd:01 mode=0100400 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:shadow_t:s0 type=CWD msg=audit(1251124060.832:231): cwd=”/root” type=SYSCALL msg=audit(1251124060.832:231): arch=40000003 syscall=5 success=no exit=-13 a0=bfeec9e8 a1=8000 a2=0 a3=bfeeab6c items=1 ppid=3934 pid=7964 auid=500 uid=500 gid=500 euid=500 suid=500 fsuid=500 egid=500 sgid=500 fsgid=500 tty=pts2 ses=1 comm=”cat” exe=”/bin/cat” subj=unconfined_u:unconfined_r:unconfined_t:s0s0:c0.c1023 key=”open” 26
Slide 27
Usage of autrace autrace is similar to strace This command deletes all audit rules prior to executing the target program and after executing it. As a safety precaution, it will not run unless all rules are deleted with auditctl prior to use. 27
Slide 28

autrace Example (1/2) autrace /bin/ls /etc/audit/auditd.conf autrace cannot be run with rules loaded. Please delete all rules using ‘auditctl -D’ if you really wanted to run this command auditctl -D No rules autrace /bin/ls /etc/audit/auditd.conf Waiting to execute: /bin/ls /etc/audit/auditd.conf Cleaning up… Trace complete. You can locate the records with ‘ausearch -i -p 8031’ 28
Slide 29

autrace Example (2/2) Autrace -i -p 8031 —-type=SYSCALL msg=audit(08/24/2009 10:38:09.251:382) : arch=i386 syscall=write success=yes exit=23 a0=1 a1=b7fc0000 a2=17 a3=17 items=0 ppid=8029 pid=8031 auid=sdw uid=root gid=root euid=root suid=root fsuid=root egid=root sgid=root fsgid=root tty=pts2 ses=1 comm=ls exe=/bin/ls subj=unconfined_u:unconfined_r:unconfined_t:s0s0:c0.c1023 key=(null) —-type=SYSCALL msg=audit(08/24/2009 10:38:09.251:383) : arch=i386 syscall=close success=yes exit=0 a0=1 a1=0 a2=930ff4 a3=9314c0 items=0 ppid=8029 pid=8031 auid=sdw uid=root gid=root euid=root suid=root fsuid=root egid=root sgid=root fsgid=root tty=pts2 ses=1 comm=ls exe=/bin/ls subj=unconfined_u:unconfined_r:unconfined_t:s0s0:c0.c1023 key=(null) —— 29
Slide 30

Data Visualization
Slide 31
Audit Data Visualization http://people.redhat.com/sgrubb/audit/visualize/index.html Steve Grub, the maintainer of the Linux Audit subsystem, has written an excellent paper + utilities for visualizing audit data. There are two utilities, mkbar and mkgraph, which perform functions as indicated in the name The mkgraph script can be downloaded from: http://people.redhat.com/sgrubb/audit/visualize/mkgraph The mkbar script can be downloaded from: http://people.redhat.com/sgrubb/audit/visualize/mkbar Note that these scripts have absolutely no vendor support, they’re simply utilities we thought others would get use from 31
Slide 32
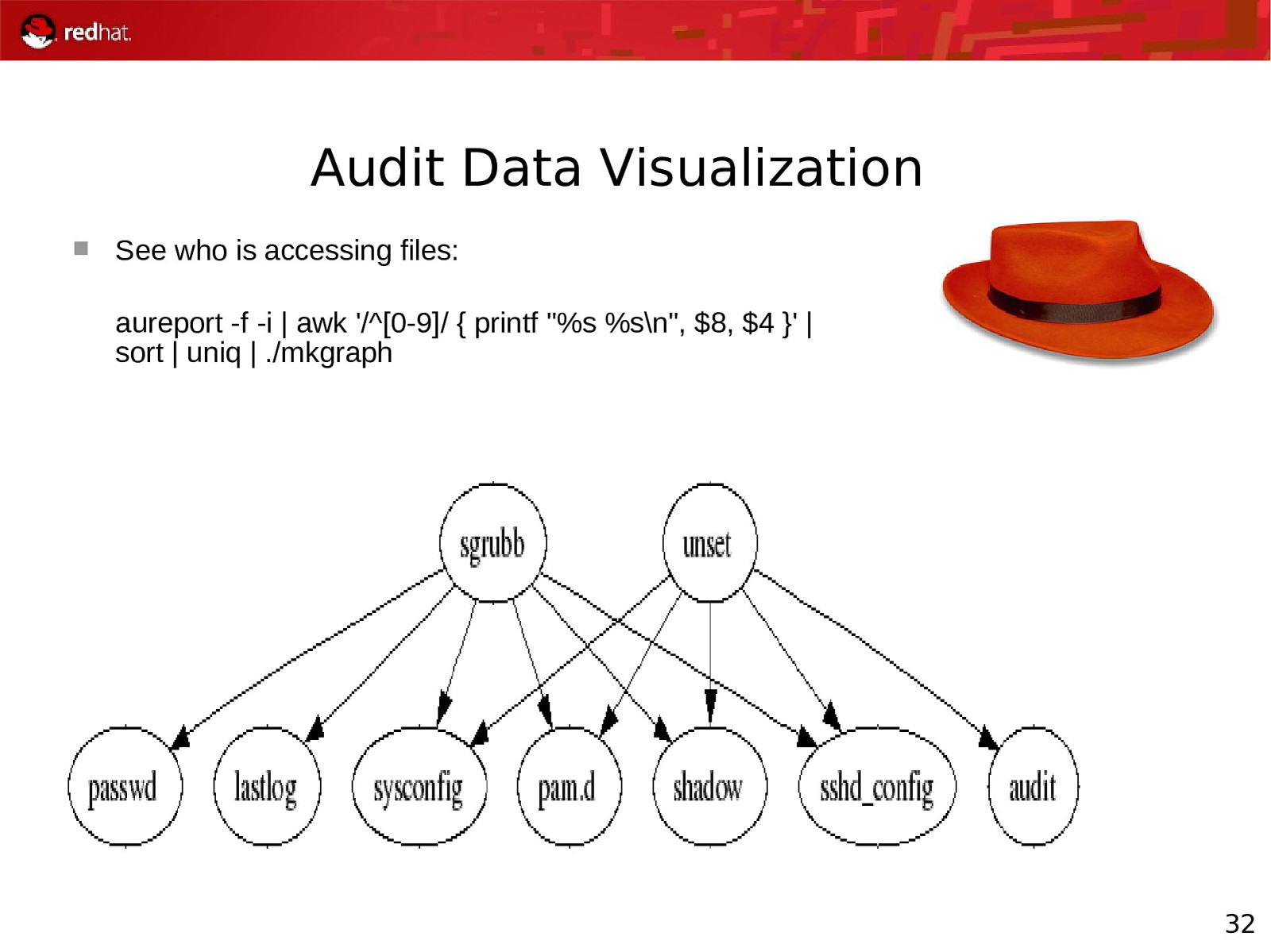
Audit Data Visualization See who is accessing files: aureport -f -i | awk ‘/^[0-9]/ { printf “%s %s\n”, $8, $4 }’ | sort | uniq | ./mkgraph 32
Slide 33
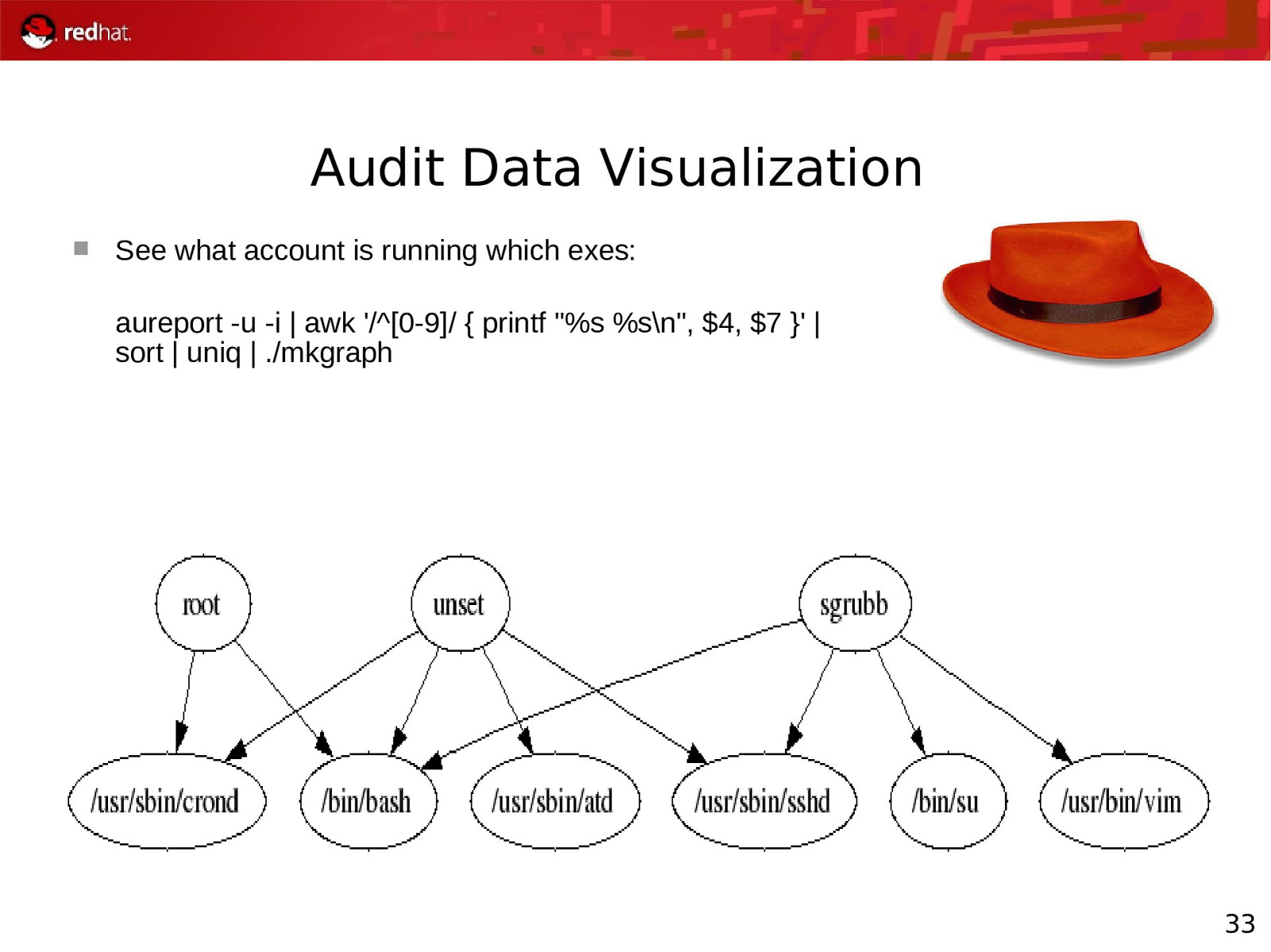
Audit Data Visualization See what account is running which exes: aureport -u -i | awk ‘/^[0-9]/ { printf “%s %s\n”, $4, $7 }’ | sort | uniq | ./mkgraph 33
Slide 34
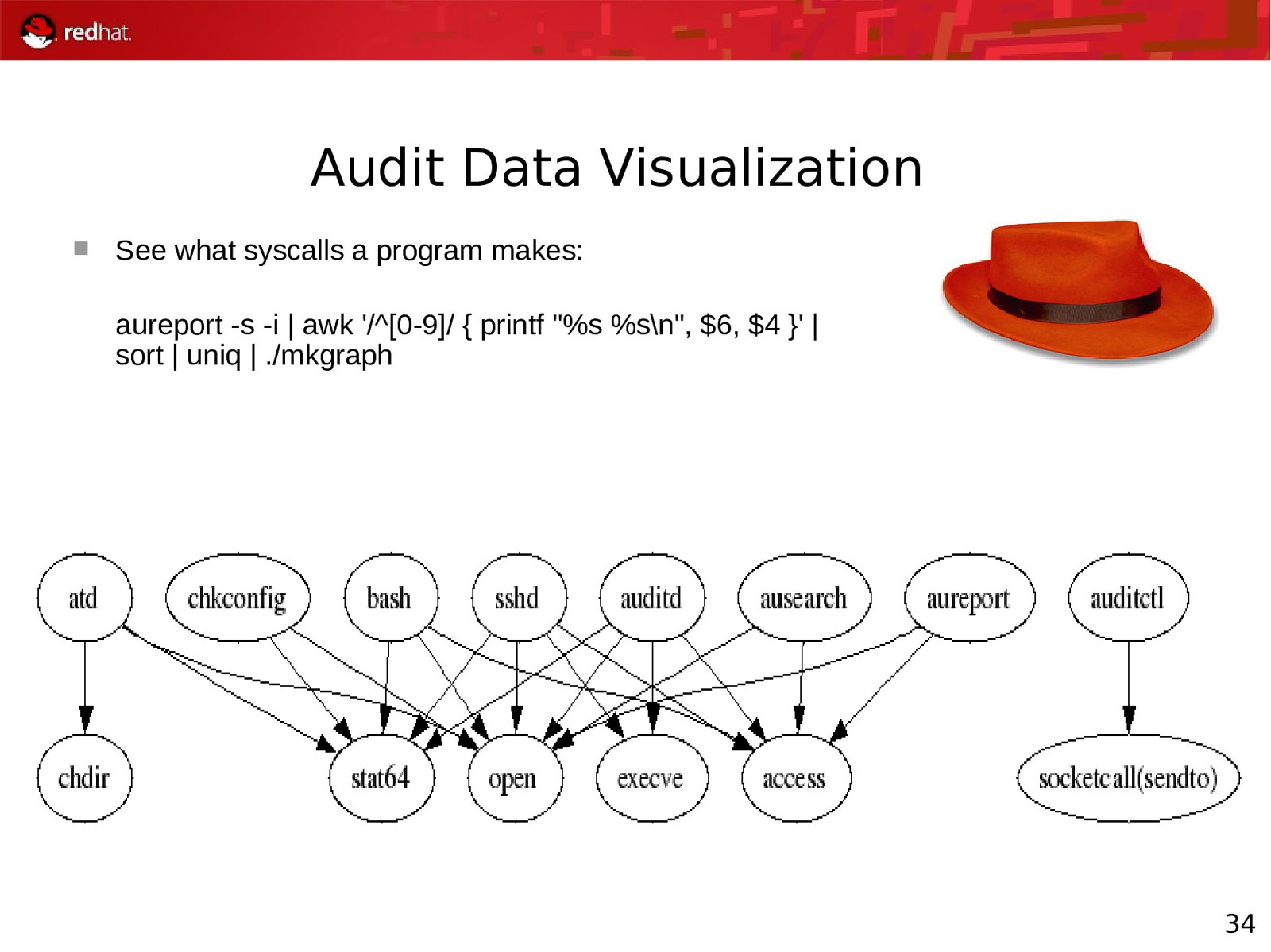
Audit Data Visualization See what syscalls a program makes: aureport -s -i | awk ‘/^[0-9]/ { printf “%s %s\n”, $6, $4 }’ | sort | uniq | ./mkgraph 34
Slide 35

Appendix
Slide 36
Appendix The Linux audit subsystem is generally available in the vanilla Linux kernel at http://www.kernel.org Audit userspace tools and daemon are available at: http://www.redhat.com/people/sgrubb/audit/ linux-audit mailing list (for all Audit, not just RHEL implementations) http://www.redhat.com/mailman/listinfo/linux-audit 36