SECURITY COMPLIANCE MADE EASY(ER): ENTERING THE SCAP RENAISSANCE
Slide 1

Slide 2
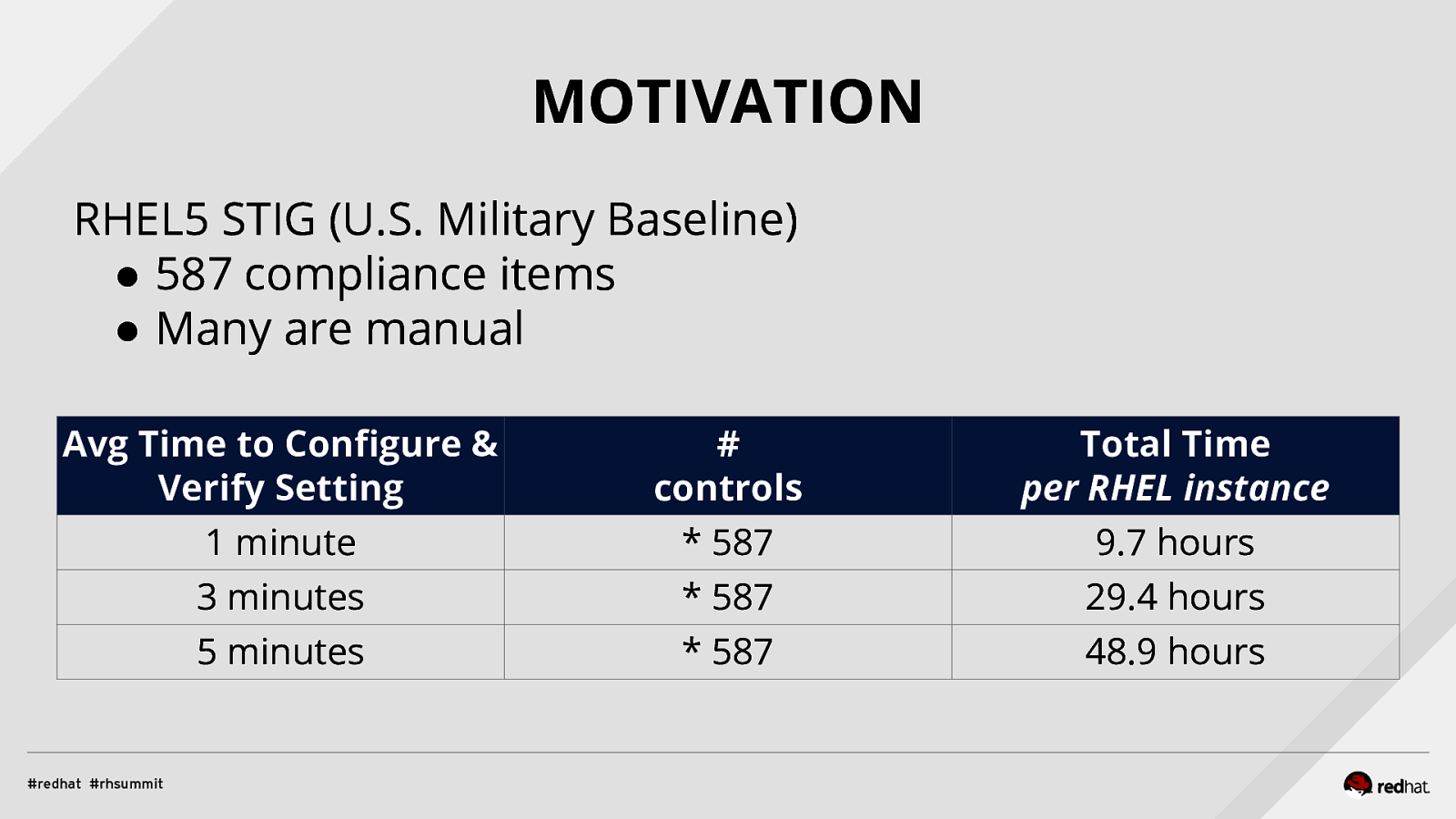
MOTIVATION RHEL5 STIG (U.S. Military Baseline) ● 587 compliance items ● Many are manual Avg Time to Configure & Verify Setting
controls
Total Time per RHEL instance 1 minute
- 587 9.7 hours 3 minutes
- 587 29.4 hours 5 minutes
- 587 48.9 hours
Slide 3
Slide 4
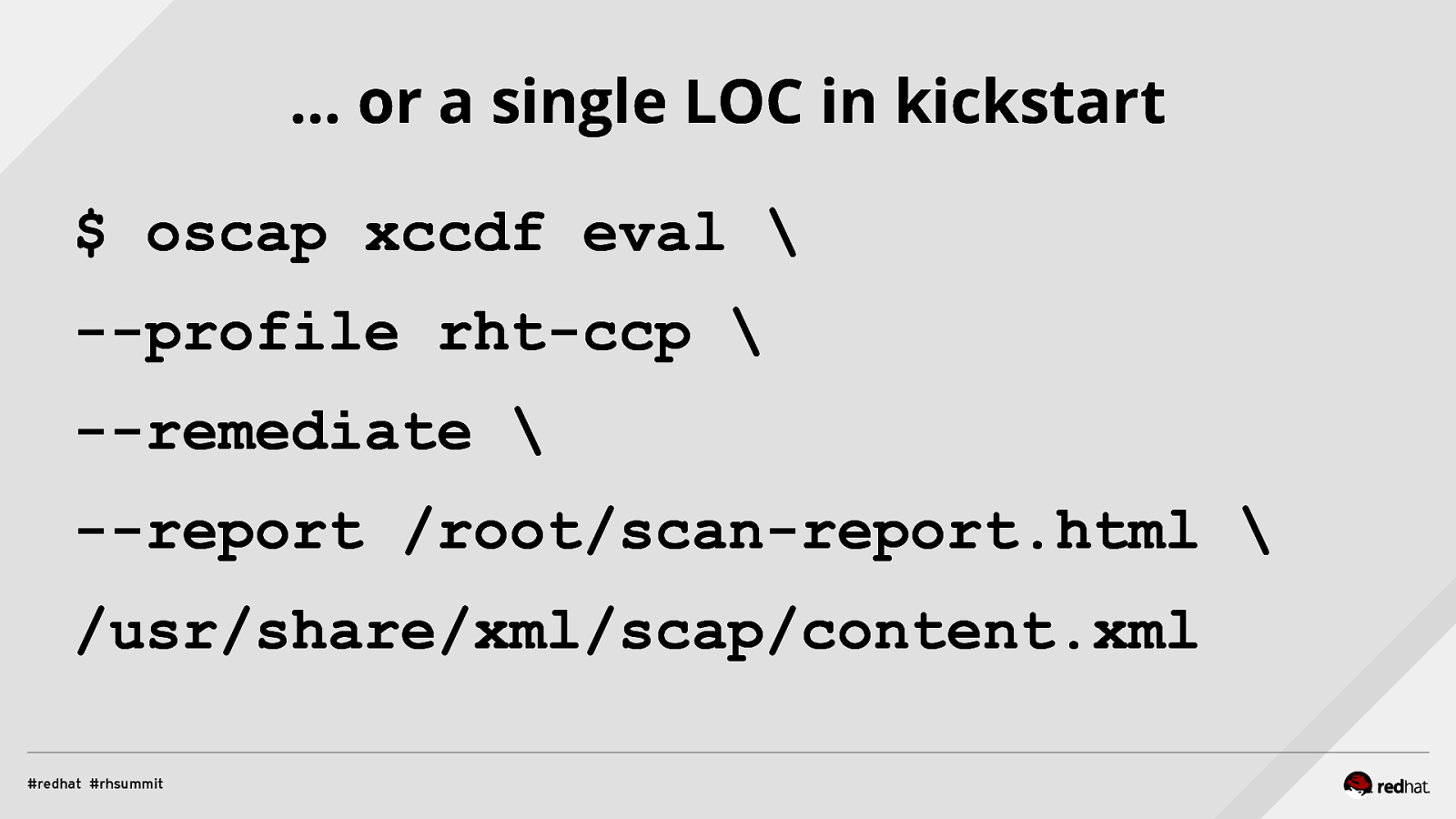
… or a single LOC in kickstart $ oscap xccdf eval \ —profile rht-ccp \ —remediate \ —report /root/scan-report.html \ /usr/share/xml/scap/content.xml
Slide 5
Slide 6

OUR (very ambitious) AGENDA 1. What’s the latest in the Security Automation space? a. Government & Commercial Initiatives b. Formal and Emerging SCAP Standards 2. What tools and content are available today? a. For enumerating (known) software vulnerabilities b. For assessing configuration 3. Use Case Story: Lockheed Martin and the Centralized Super Computing Facility
Slide 7

LIVE DEMOS 1. Install & Review SCAP profiles in RHEL 7 2. Performing a Compliance Scan 3. System Remediation 4. Creating Custom (derived) Configuration Baselines with SCAP Workbench 5. RHEL 7 “Easy Button” Installations
Slide 8

SPEAKERS Shawn Wells Director, Innovation Programs Developer, OpenSCAP Content Red Hat
Slide 9

SPEAKERS Jeff Blank Technical Director, OS and Applications Division Information Assurance Directorate National Security Agency
Slide 10

SPEAKERS Sarah Storms Josh Koontz Engineering, Lockheed Martin
Slide 11

COMPLIANCE BIG PICTURE: PRODUCTS AND SYSTEMS
Slide 12
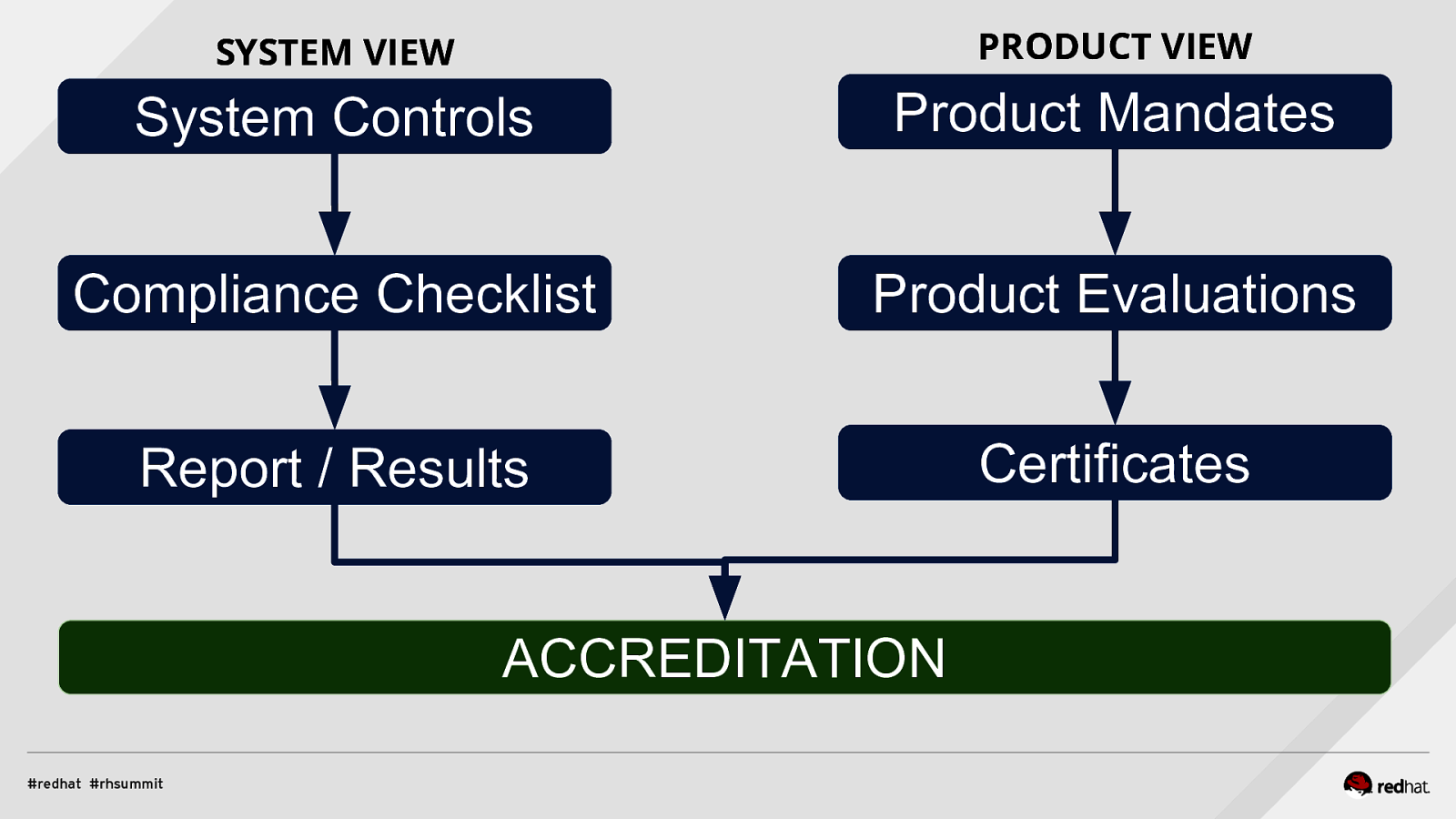
SYSTEM VIEW PRODUCT VIEW System Controls Product Mandates Compliance Checklist Product Evaluations Report / Results Certificates ACCREDITATION
Slide 13
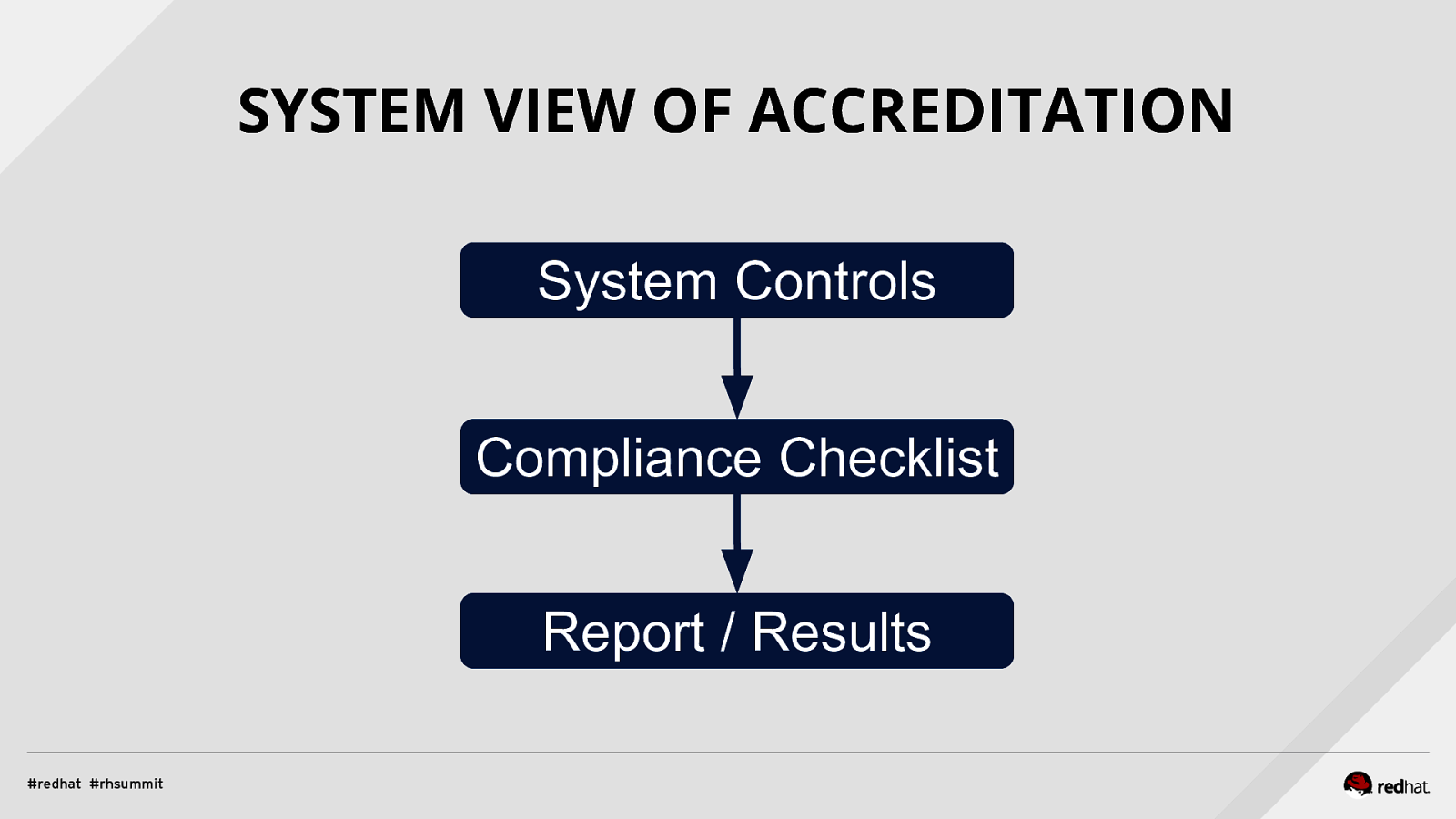
SYSTEM VIEW OF ACCREDITATION System Controls Compliance Checklist Report / Results
Slide 14
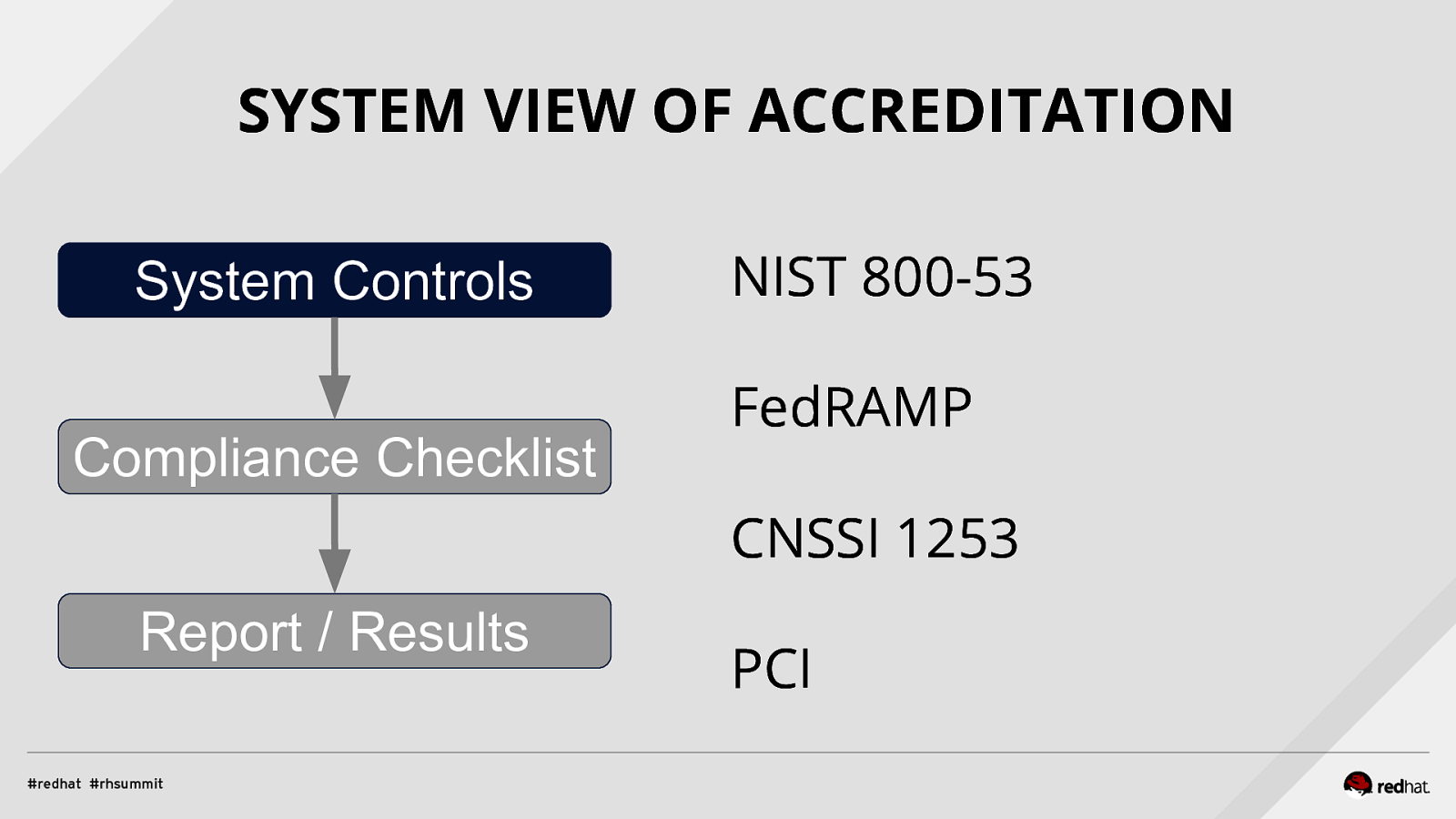
SYSTEM VIEW OF ACCREDITATION System Controls Compliance Checklist NIST 800-53 FedRAMP CNSSI 1253 Report / Results PCI
Slide 15
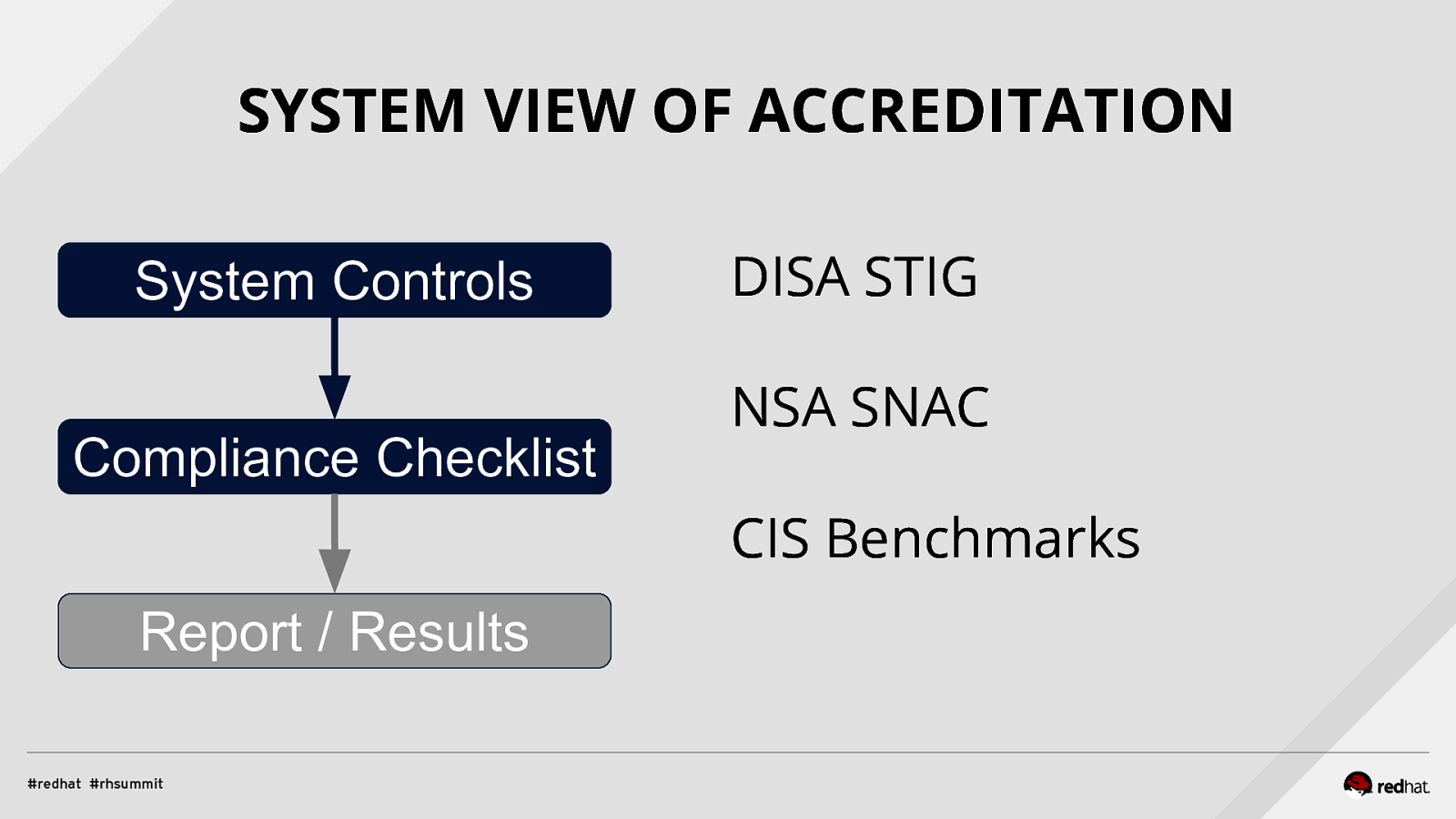
SYSTEM VIEW OF ACCREDITATION System Controls Compliance Checklist DISA STIG NSA SNAC CIS Benchmarks Report / Results
Slide 16
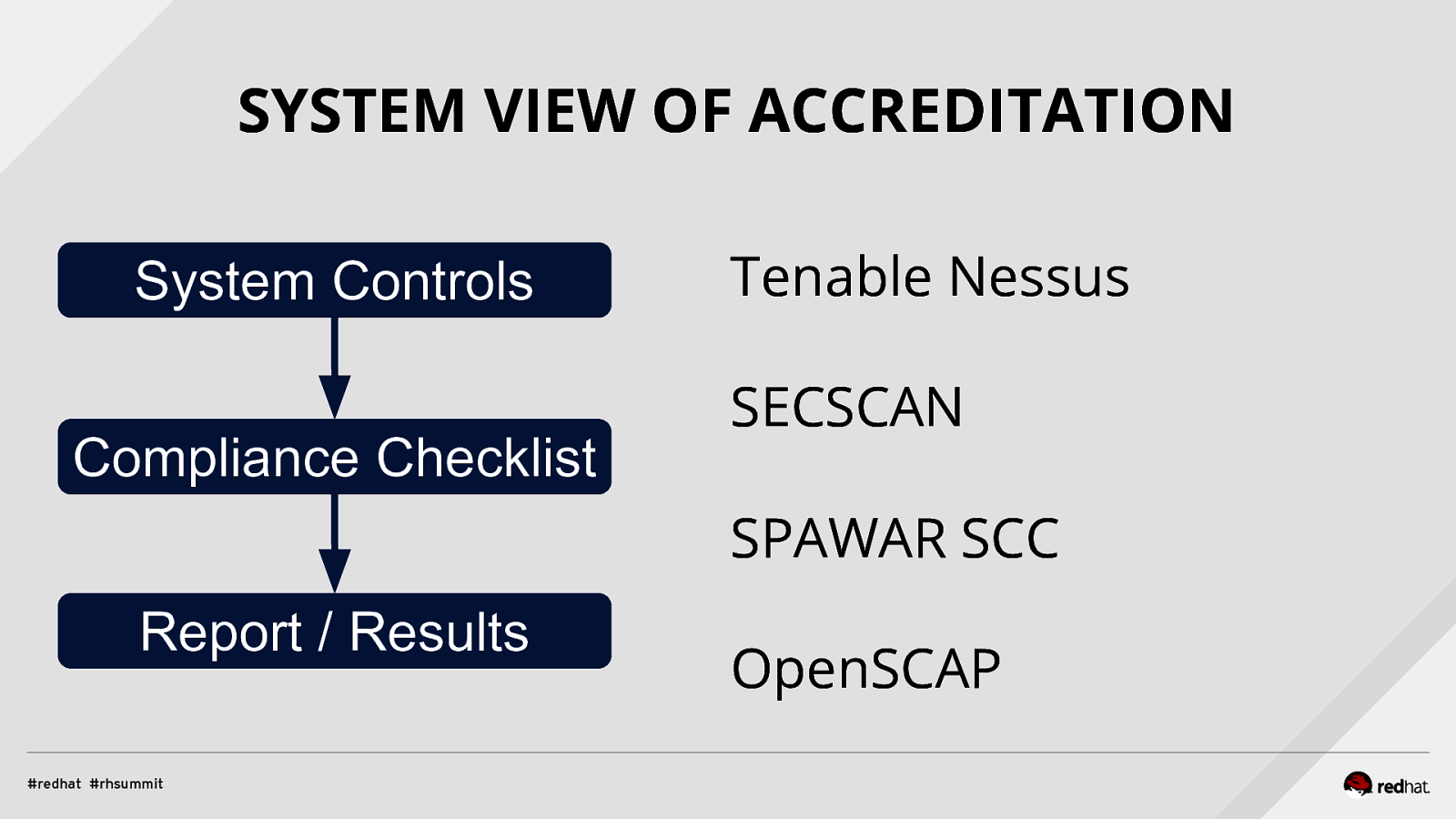
SYSTEM VIEW OF ACCREDITATION System Controls Compliance Checklist Tenable Nessus SECSCAN SPAWAR SCC Report / Results OpenSCAP
Slide 17
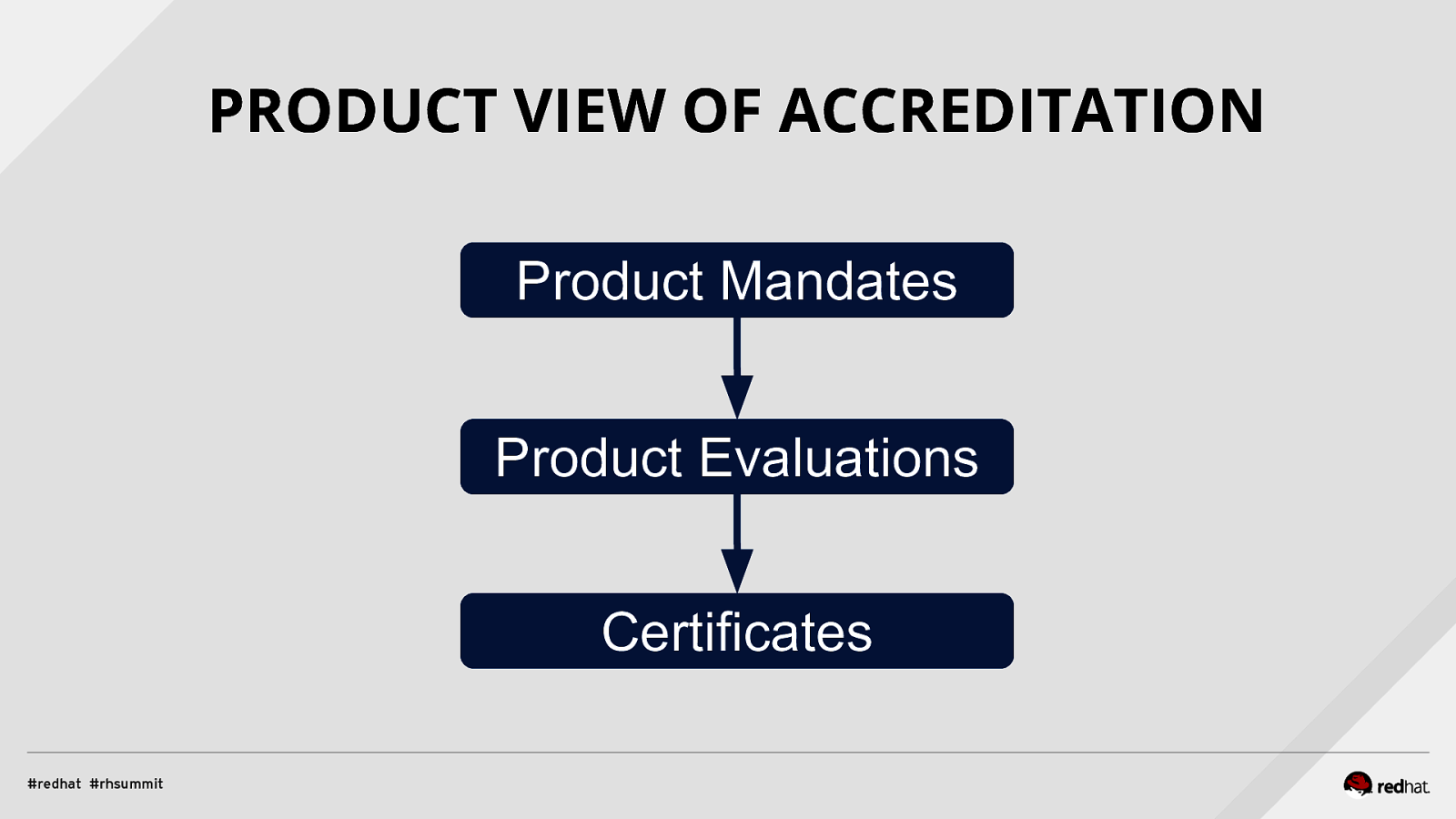
PRODUCT VIEW OF ACCREDITATION Product Mandates Product Evaluations Certificates
Slide 18
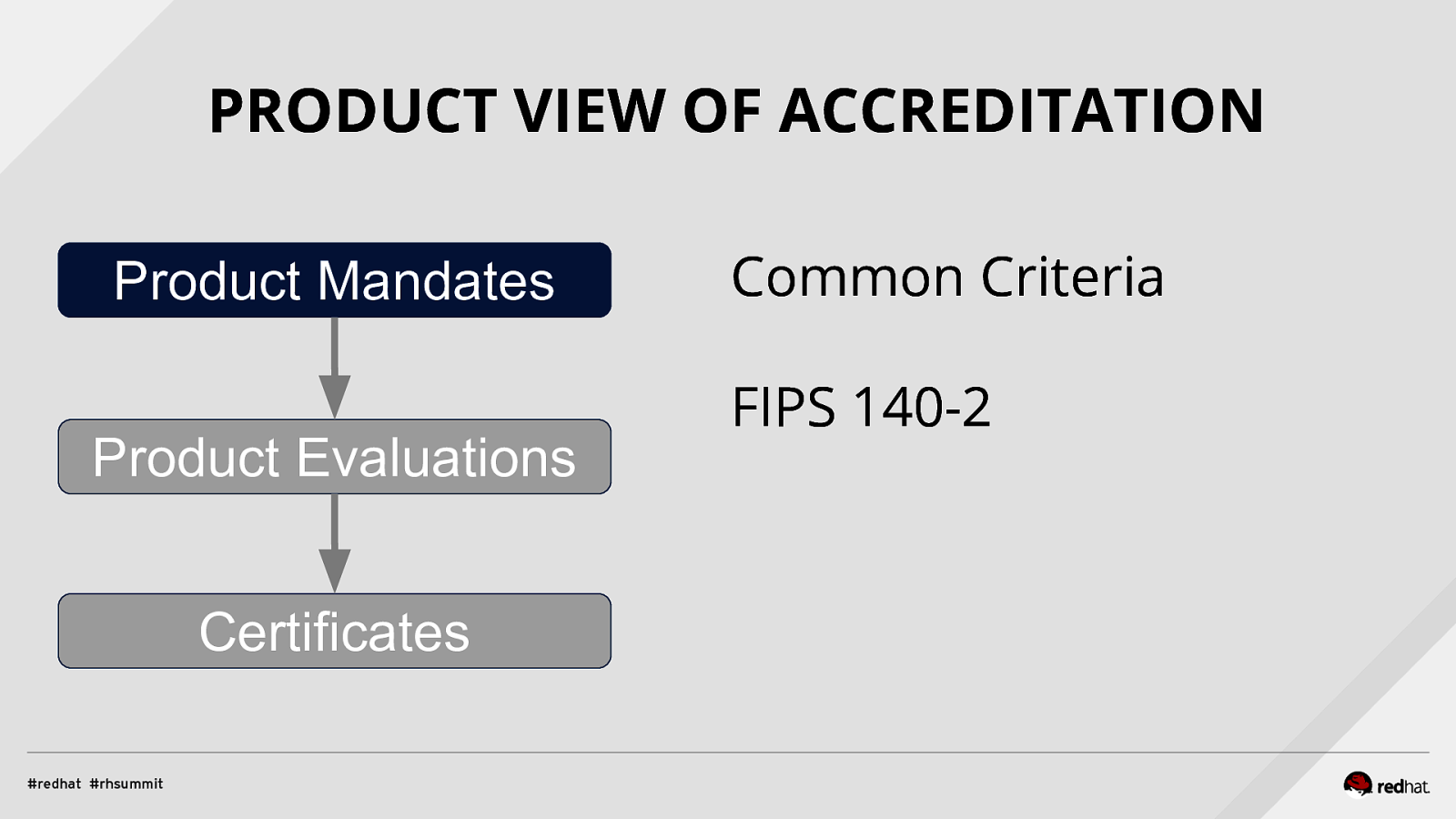
PRODUCT VIEW OF ACCREDITATION Product Mandates Product Evaluations Certificates Common Criteria FIPS 140-2
Slide 19

…. wait… what’s COMMON CRITERIA? - international framework for specifying and testing security functional and assurance requirements in IT products - through the use of Protection Profiles (PPs) - vendors can then implement and/or make claims about the security attributes of their products, and testing laboratories can evaluate the products to determine if they actually meet the claims.
Slide 20
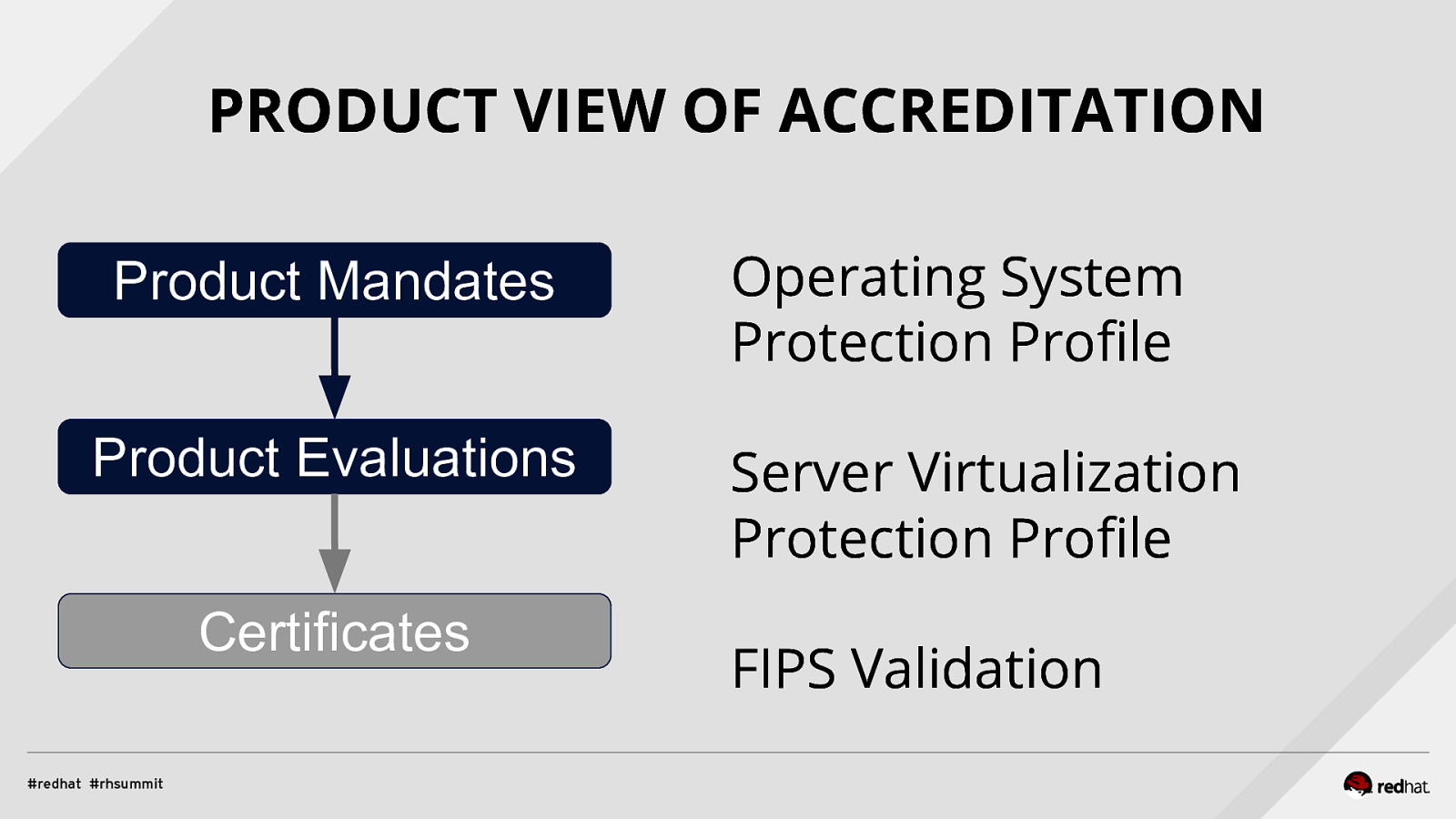
PRODUCT VIEW OF ACCREDITATION Product Mandates Product Evaluations Certificates Operating System Protection Profile Server Virtualization Protection Profile FIPS Validation
Slide 21
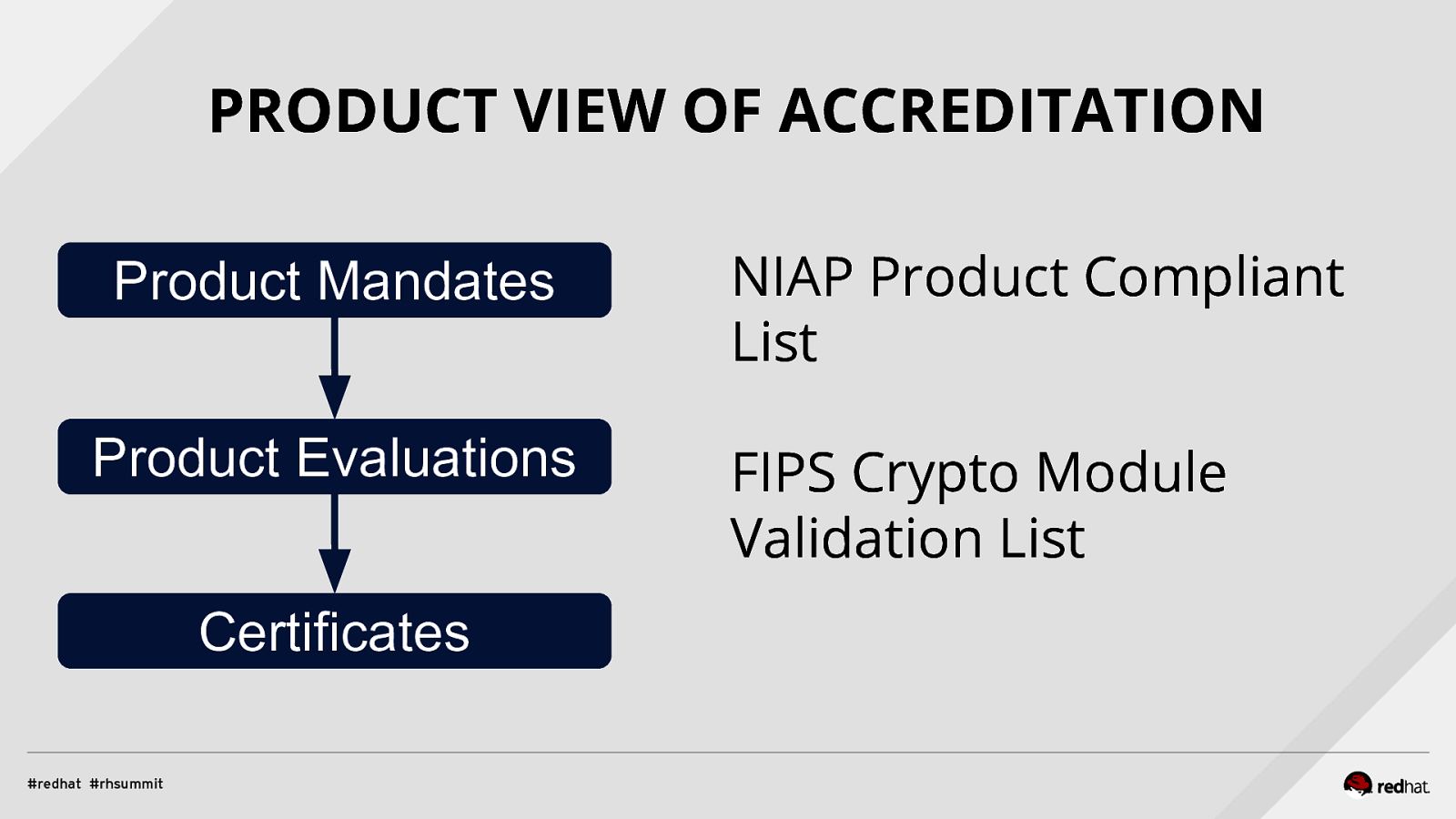
PRODUCT VIEW OF ACCREDITATION Product Mandates Product Evaluations Certificates NIAP Product Compliant List FIPS Crypto Module Validation List
Slide 22
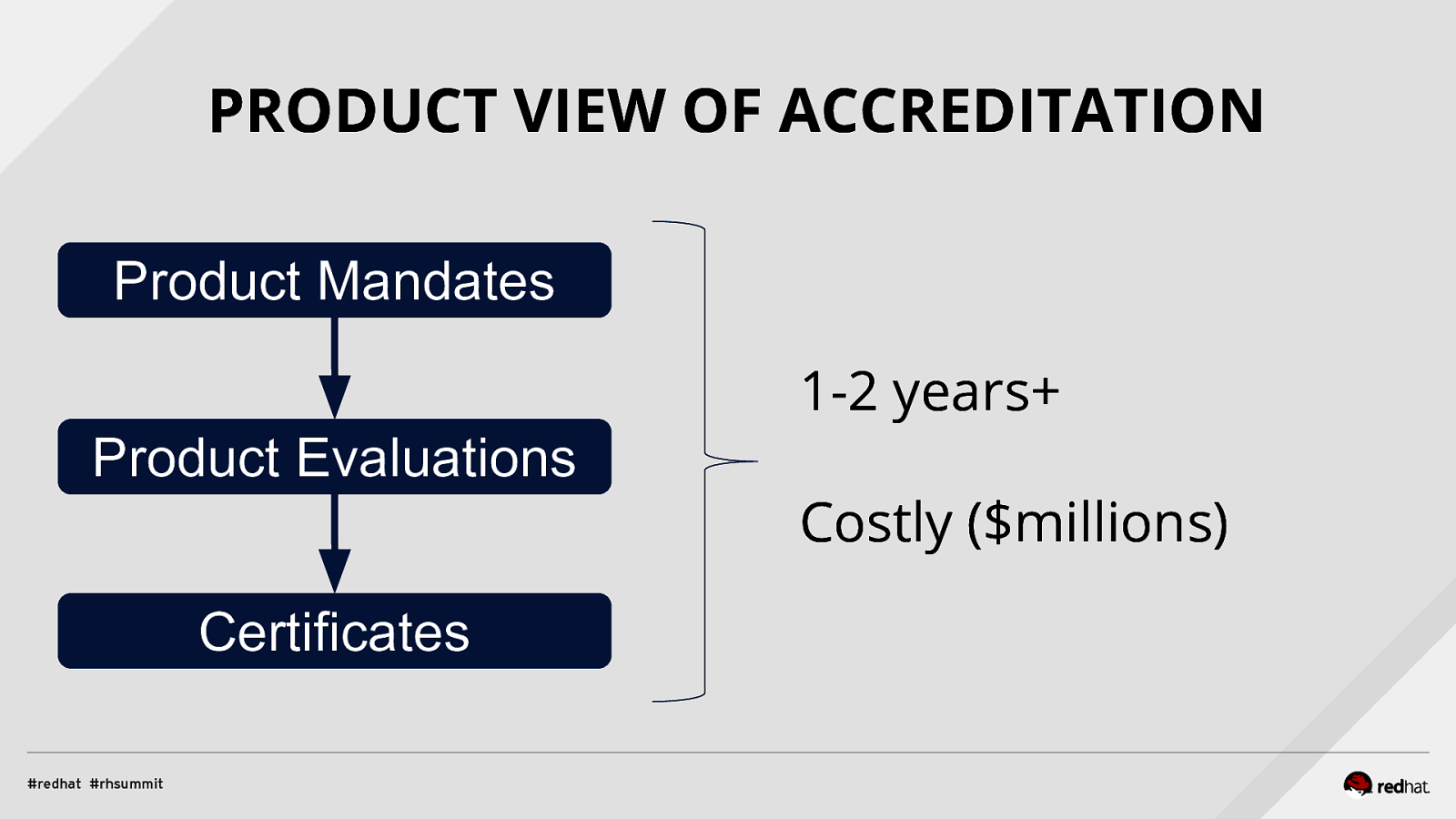
PRODUCT VIEW OF ACCREDITATION Product Mandates 1-2 years+ Product Evaluations Costly ($millions) Certificates
Slide 23

Slide 24
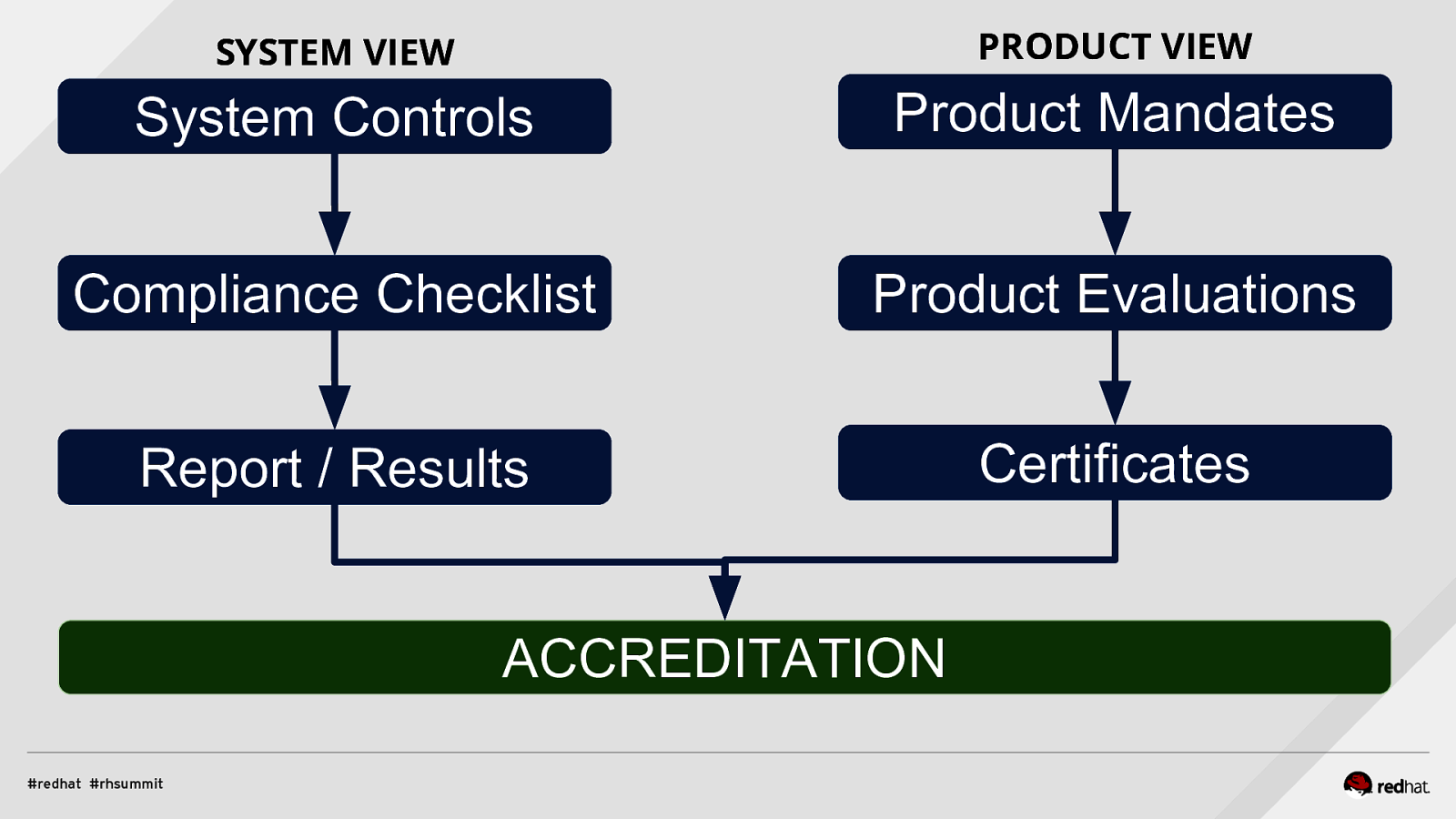
SYSTEM VIEW PRODUCT VIEW System Controls Product Mandates Compliance Checklist Product Evaluations Report / Results Certificates ACCREDITATION
Slide 25

OPEN SOURCE CONFRONTS THE C&A CHALLENGE: PRODUCT CERTIFICATION
Slide 26
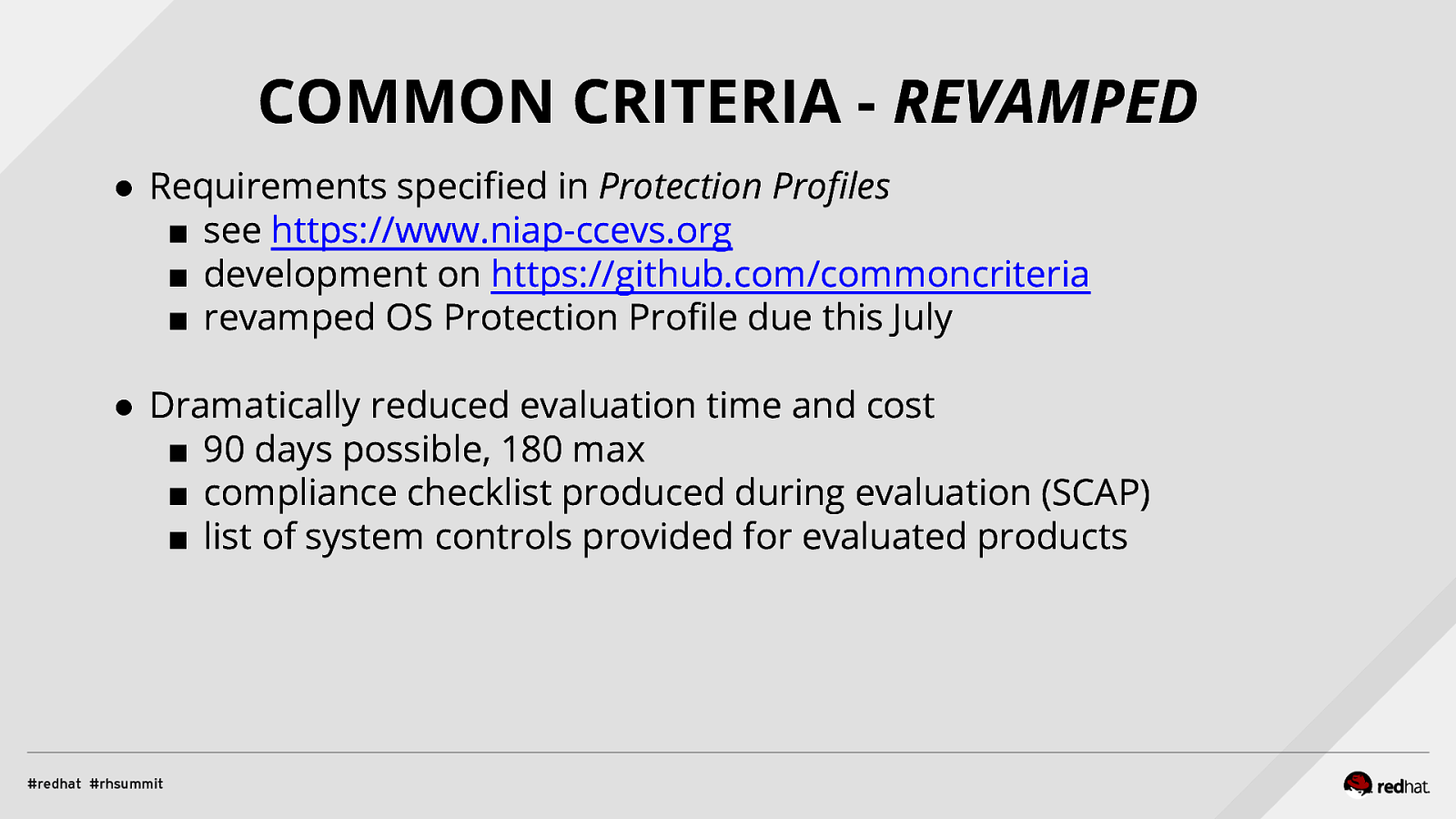
COMMON CRITERIA - REVAMPED ● Requirements specified in Protection Profiles ■ see https://www.niap-ccevs.org ■ development on https://github.com/commoncriteria ■ revamped OS Protection Profile due this July ● Dramatically reduced evaluation time and cost ■ 90 days possible, 180 max ■ compliance checklist produced during evaluation (SCAP) ■ list of system controls provided for evaluated products
Slide 27
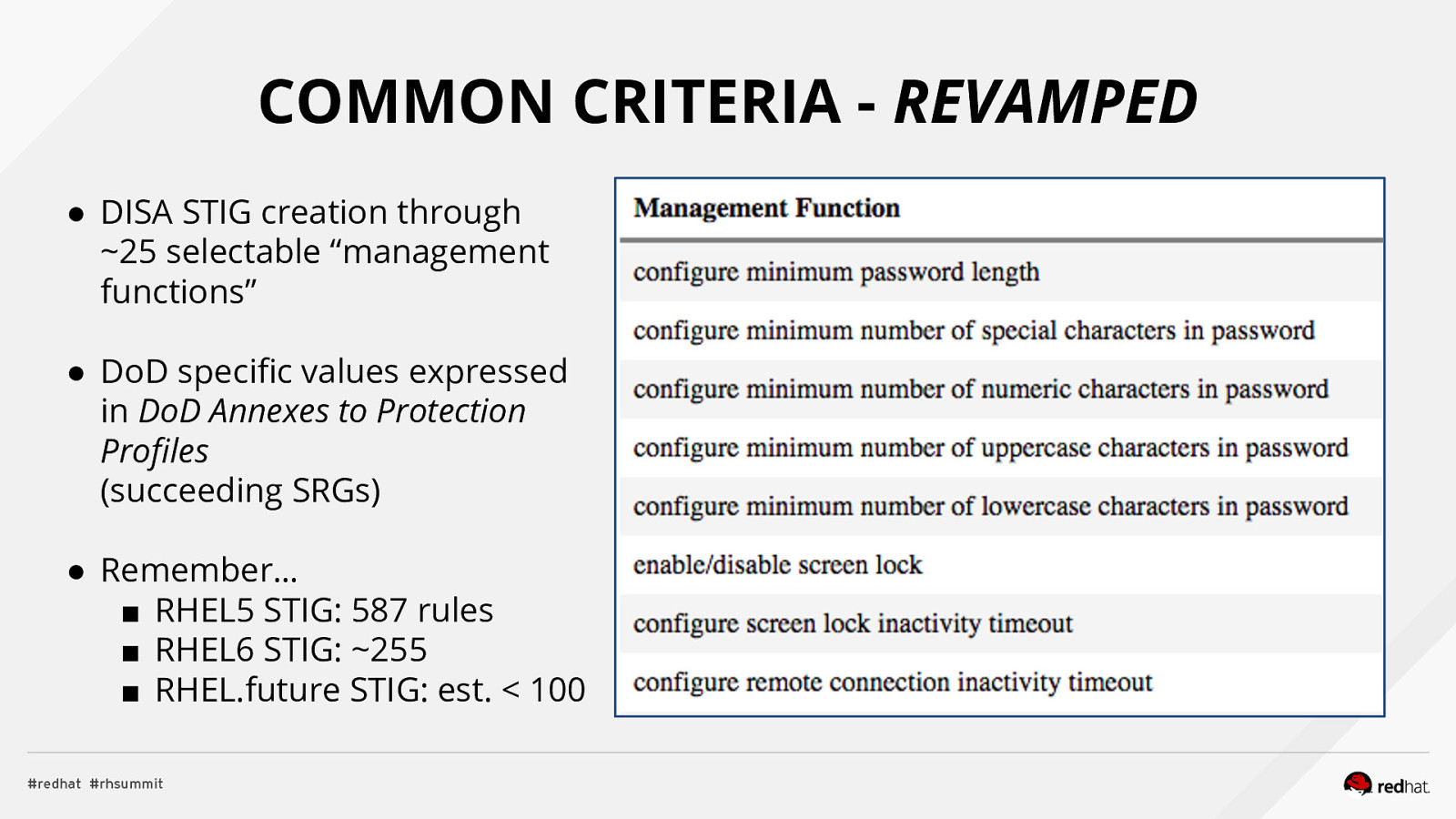
COMMON CRITERIA - REVAMPED ● DISA STIG creation through ~25 selectable “management functions” ● DoD specific values expressed in DoD Annexes to Protection Profiles (succeeding SRGs) ● Remember… ■ RHEL5 STIG: 587 rules ■ RHEL6 STIG: ~255 ■ RHEL.future STIG: est. < 100
Slide 28

OPEN SOURCE CONFRONTS THE C&A CHALLENGE: SYSTEM COMPLIANCE
Slide 29

Community created portfolio of tools and content to assess systems for known vulnerabilities. https://github.com/OpenSCAP
Slide 30
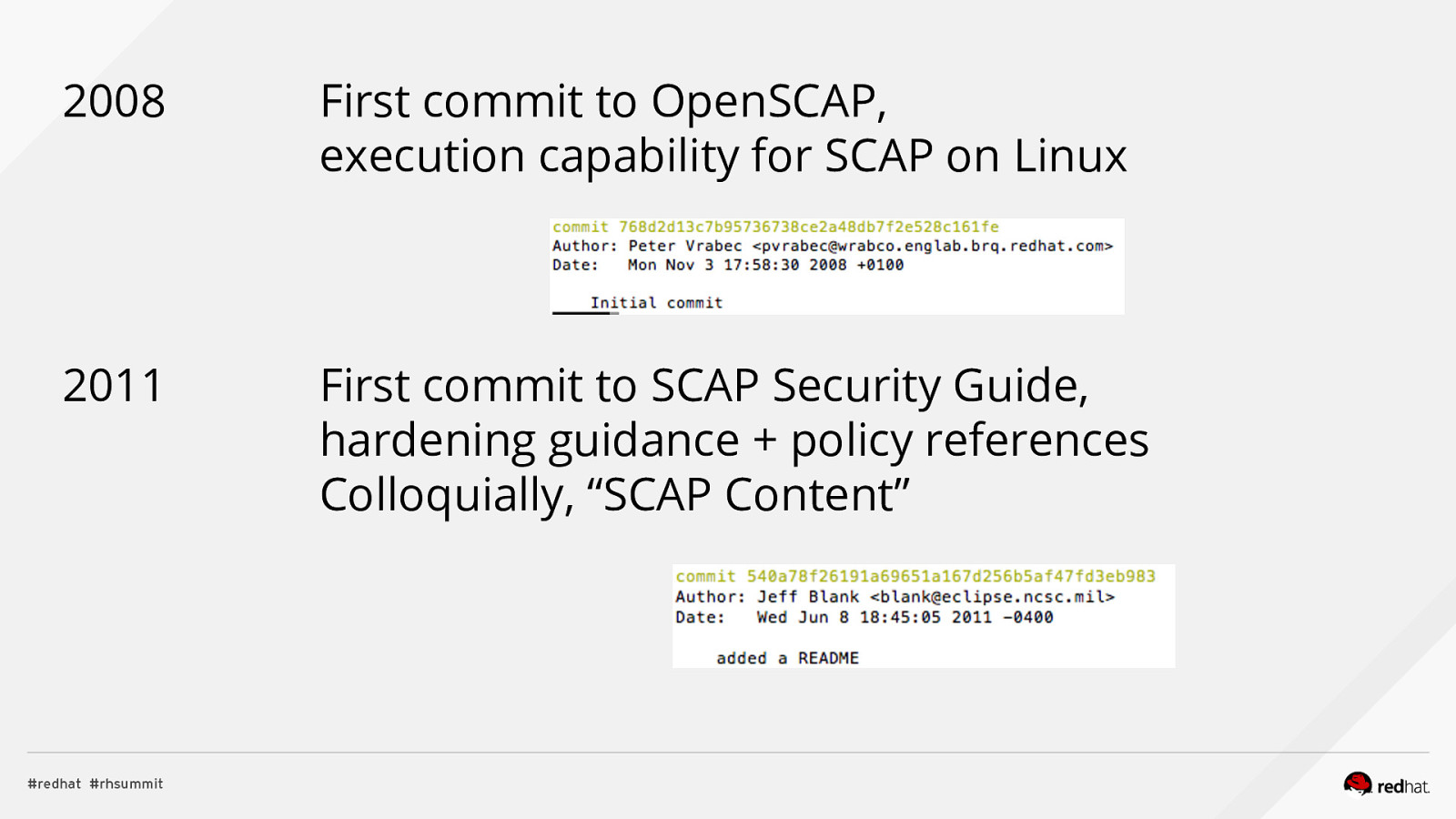
2008 First commit to OpenSCAP, execution capability for SCAP on Linux 2011 First commit to SCAP Security Guide, hardening guidance + policy references Colloquially, “SCAP Content”
Slide 31

Slide 32

Slide 33

Slide 34

DEMO #1: INSTALL, REVIEW PROFILES Install OpenSCAP and SCAP Content $ sudo yum install openscap-scanner scap-security-guide What default profiles exist? $ oscap info /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml …. Profiles: pci-dss rht-ccp common stig-rhel7-server-upstream ….
Slide 35

DEMO #2: REVIEW HARDENING GUIDES Review manpage $ man scap-security-guide Review HTML gudes $ ls -l /usr/share/doc/scap-security-guide/rhel7-guide.html
Slide 36

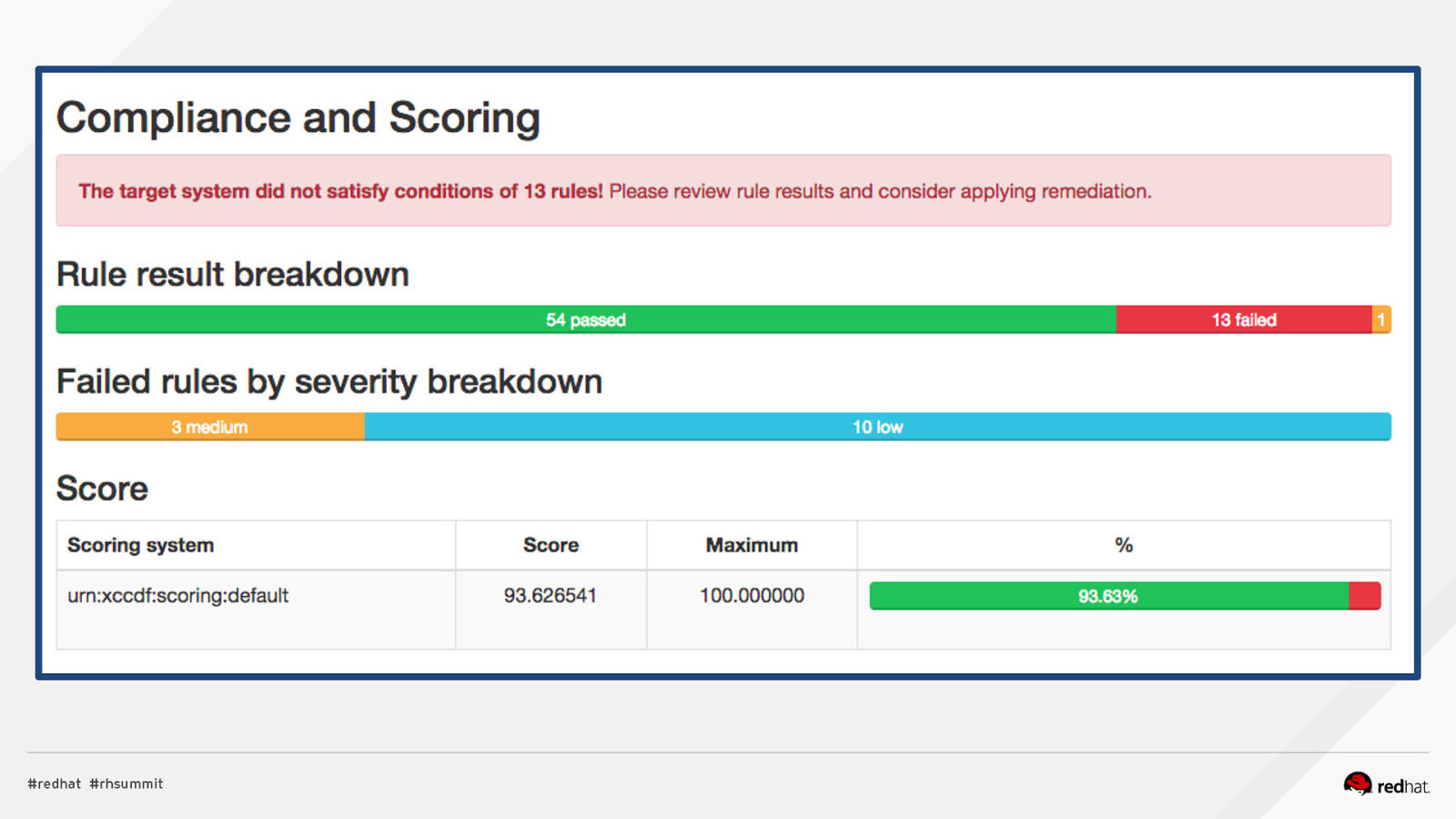
DEMO #3: LOCAL SCAN, REVIEW RESULTS Perform 1st Scan $ sudo oscap xccdf eval —profile rht-ccp \ —results /root/summit-results.html \ —report /root/summit-report.xml \ /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml Review Results $ ${web_browser} /root/summit-results.html
Slide 37
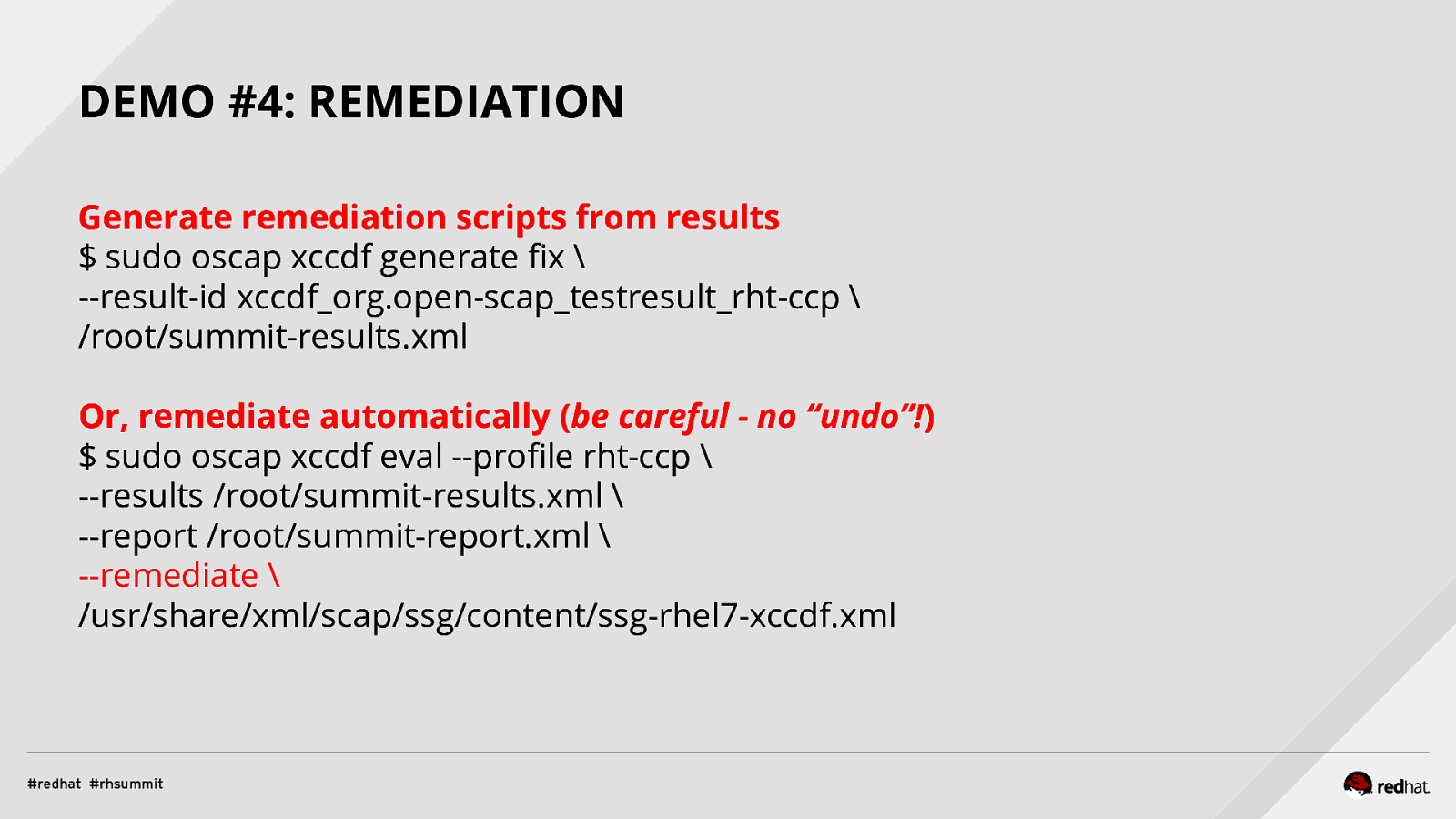
DEMO #4: REMEDIATION Generate remediation scripts from results $ sudo oscap xccdf generate fix \ —result-id xccdf_org.open-scap_testresult_rht-ccp \ /root/summit-results.xml Or, remediate automatically (be careful - no “undo”!) $ sudo oscap xccdf eval —profile rht-ccp \ —results /root/summit-results.xml \ —report /root/summit-report.xml \ —remediate \ /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml
Slide 38
DEMO #5: SCAP WORKBENCH Download SCAP Workbench $ sudo yum -y install scap-workbench Much of this demo is live. For extra details, https://open-scap.org
Slide 39
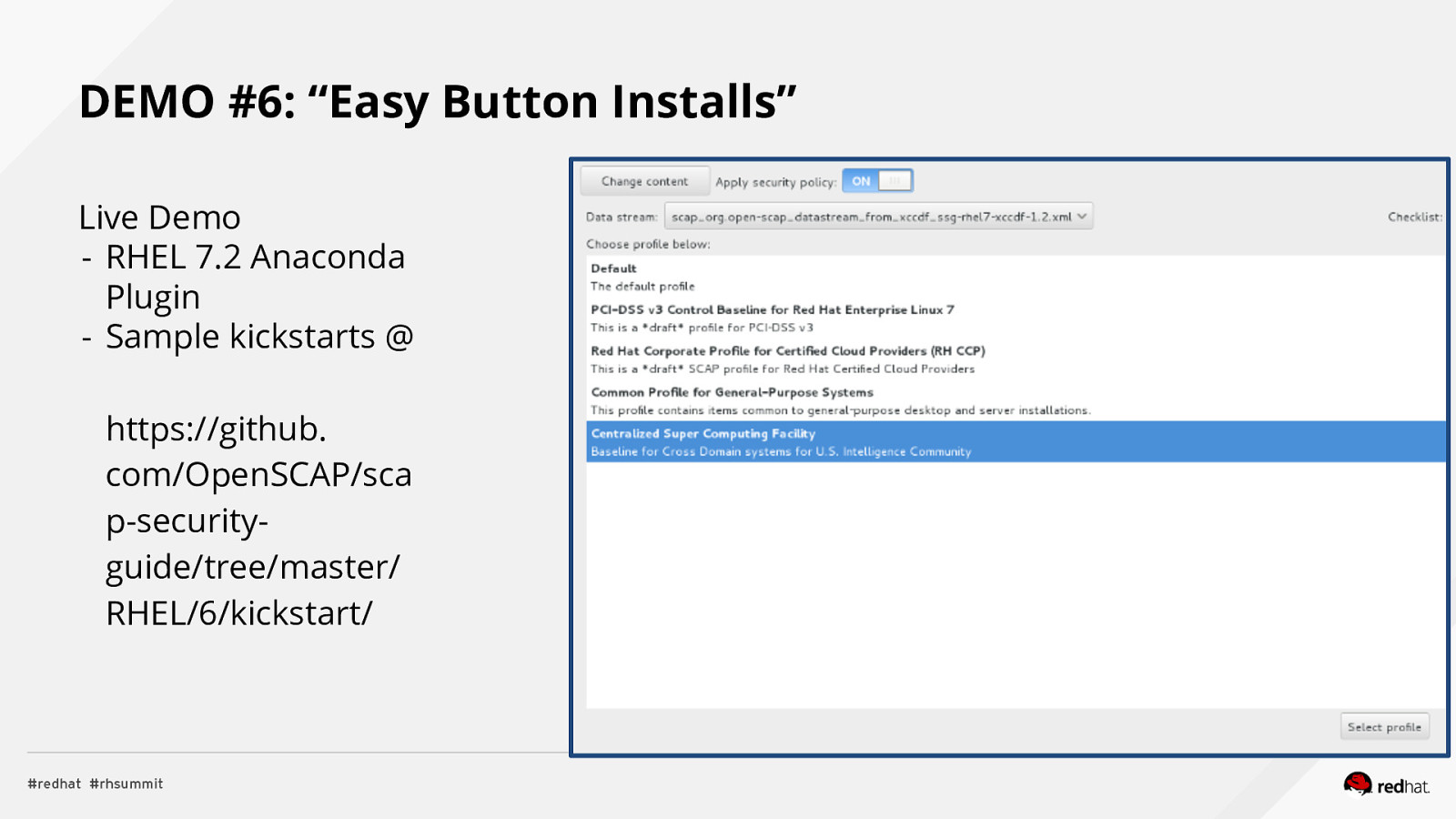
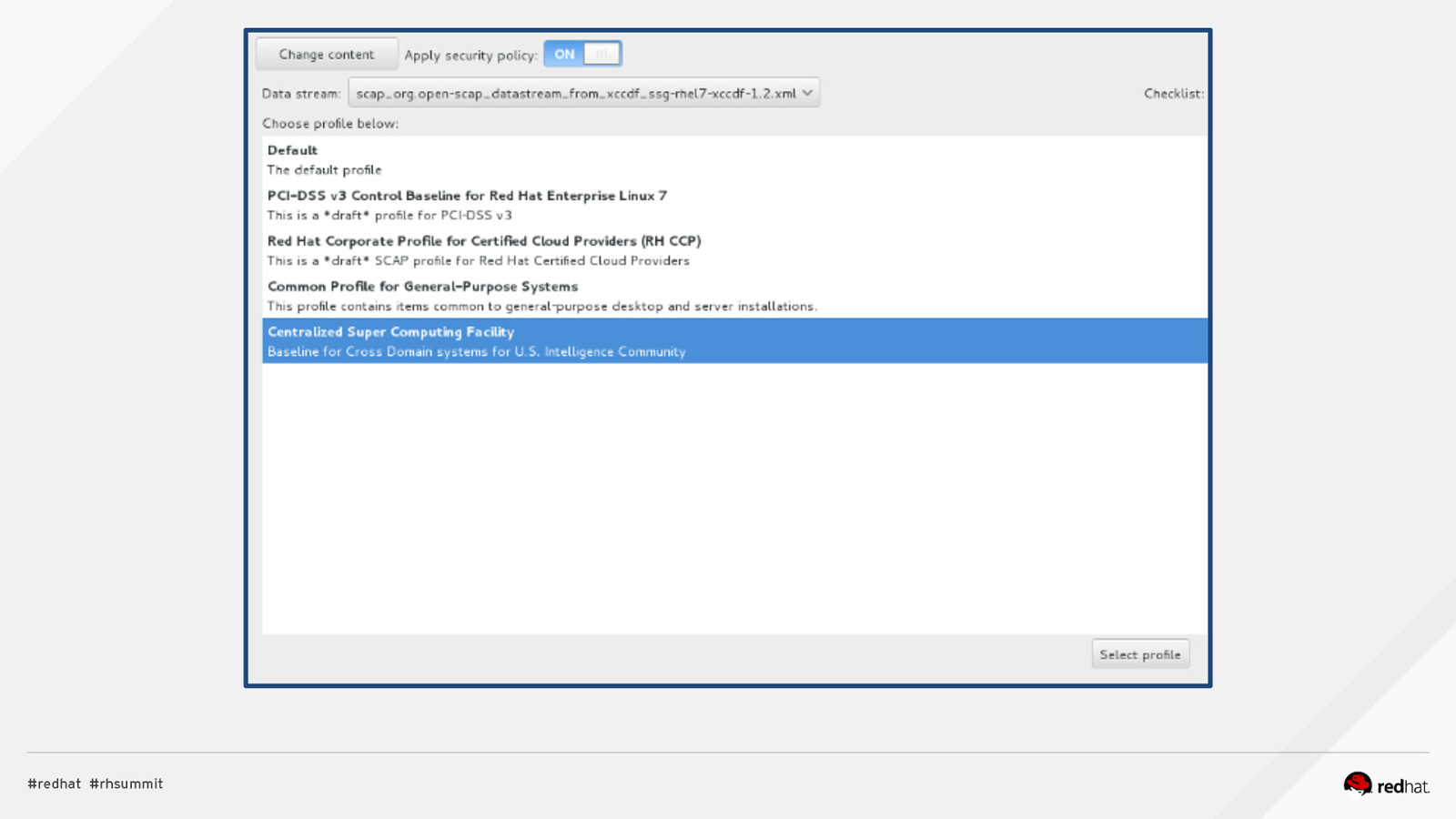
DEMO #6: “Easy Button Installs” Live Demo - RHEL 7.2 Anaconda Plugin - Sample kickstarts @ https://github. com/OpenSCAP/sca p-securityguide/tree/master/ RHEL/6/kickstart/
Slide 40

OpenSCAP IN ACTION Lockheed’s Use Case
Slide 41

Sarah Storms Project Engineer Lockheed Martin sarah.b.storms@lmco.com Joshua Koontz Systems Engineer Lockheed Martin joshua.koontz@lmco.com
Slide 42
WHAT WE DO The Centralized Super Computer Facility (CSCF) is an ICD 503 certified, cross-domain computing facility for U.S. Intelligence processing research and development. ALGORITHM PROESSING MULTI-TENANT DATA STORAGE CROSS DOMAIN DATA FUSION VIRTUALIZATION
Slide 43

CSCF BACKSTORY ● The CSCF program leverages MLS OS configurations for the last 20 years ○ Minimize hardware, licensing, OS configuration, manpower costs ○ Maximize flexibility, data fusion, system utilization ● MLS requires a full ecosystem to be truly useful ○ Certified products ○ OS configuration ○ Resource management ○ Direct and Network attached storage ○ Including long haul data sharing ○ System Monitoring including audit reduction ○ Databases
Slide 44
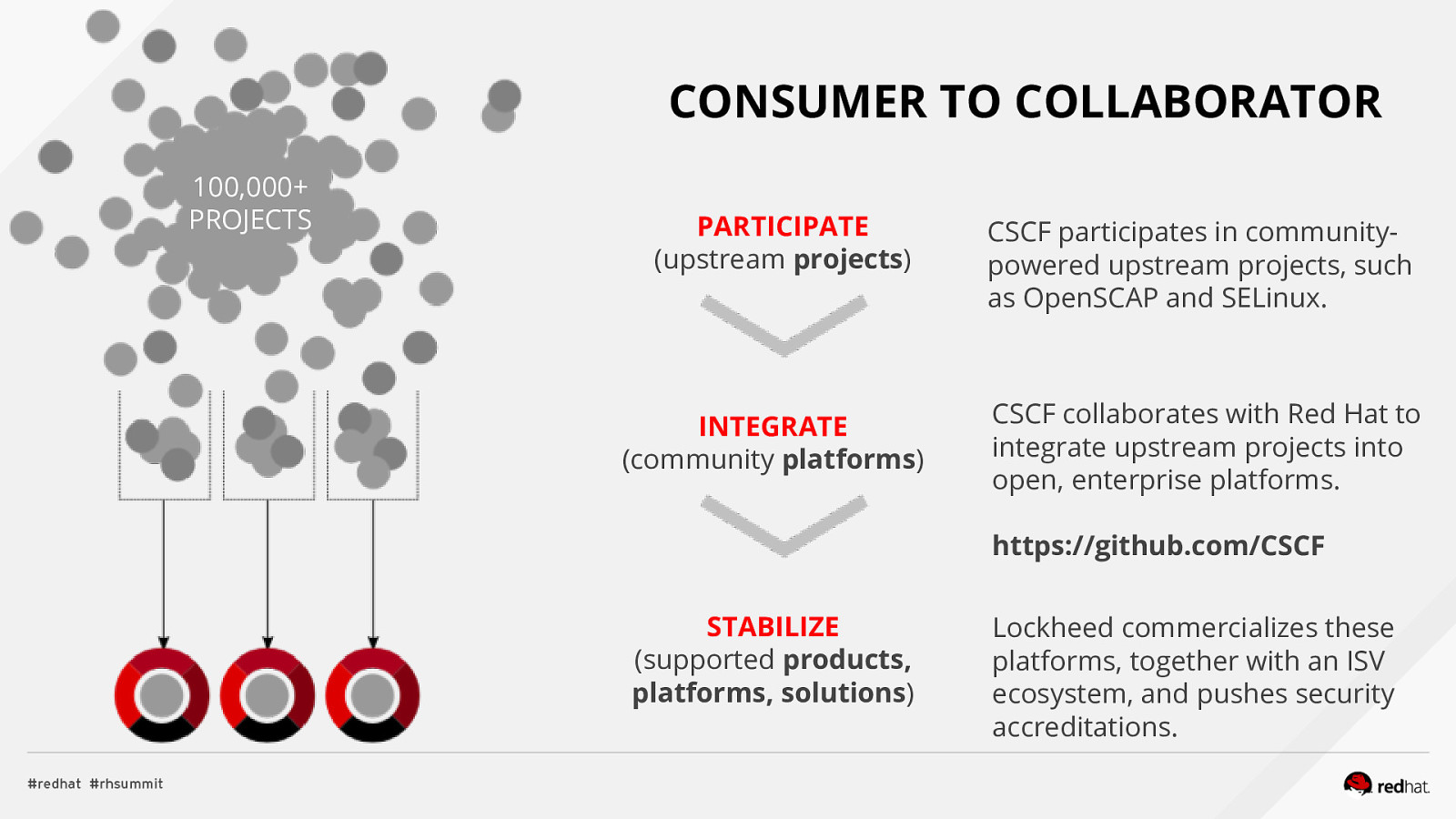
CONSUMER TO COLLABORATOR 100,000+ PROJECTS PARTICIPATE (upstream projects) INTEGRATE (community platforms) CSCF participates in communitypowered upstream projects, such as OpenSCAP and SELinux. CSCF collaborates with Red Hat to integrate upstream projects into open, enterprise platforms. https://github.com/CSCF STABILIZE (supported products, platforms, solutions) Lockheed commercializes these platforms, together with an ISV ecosystem, and pushes security accreditations.
Slide 45

MLS ECOSYSTEM ECOSYSTEM PARTNERS ● LMC/CSCF ● Red Hat ● Altair ● Seagate ● Mellanox ● ViON ● Bay Microsystems ● SGI ● Cray ● Splunk ● Crunchy Data MLS Ecosystem Objective - Provide MLS capable versions of ● UNLV/NSCEE software capabilities integrated with the RHEL MLS configuration to solve complex system configuration and support problems
Slide 46
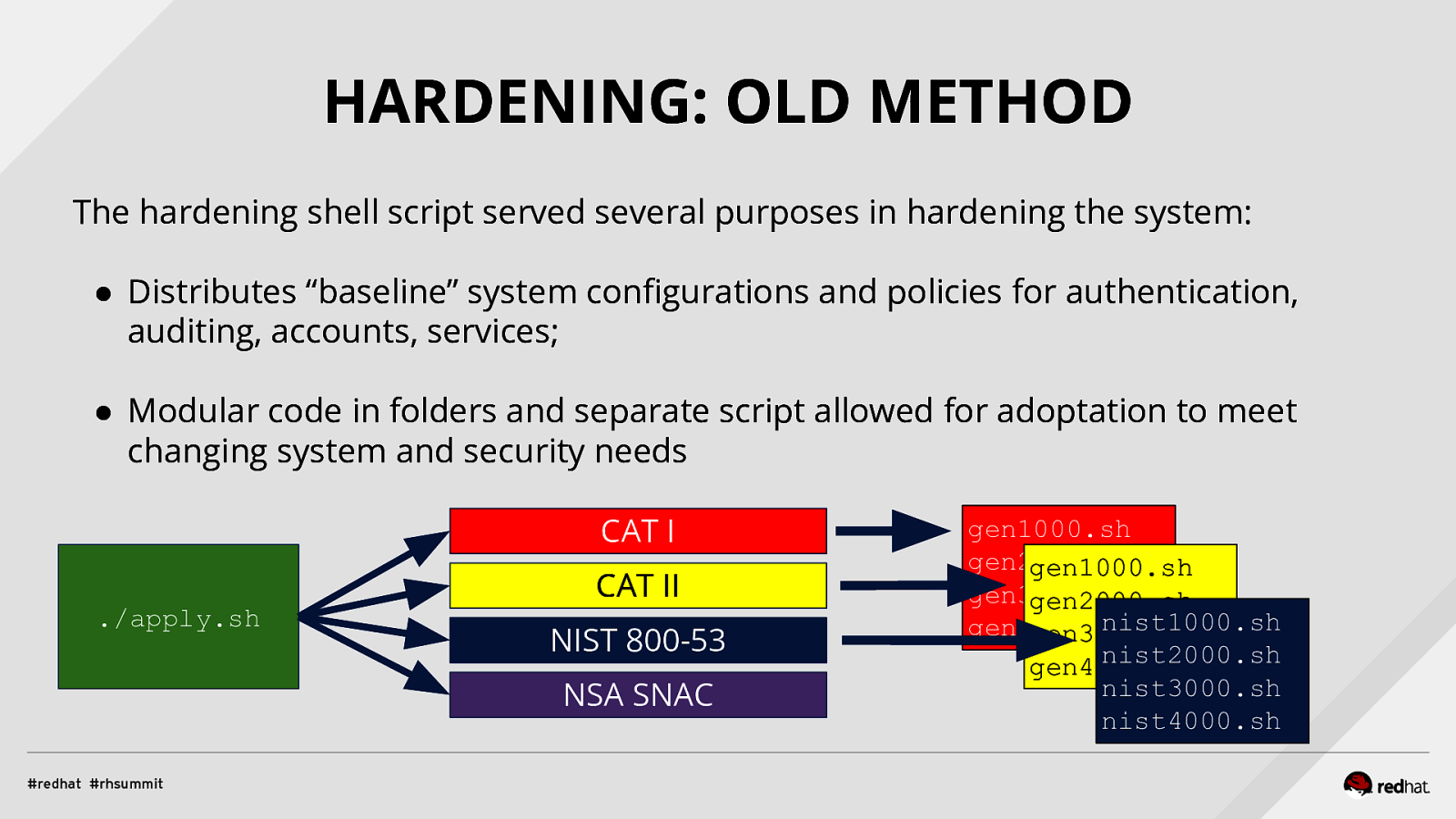
HARDENING: OLD METHOD The hardening shell script served several purposes in hardening the system: ● Distributes “baseline” system configurations and policies for authentication, auditing, accounts, services; ● Modular code in folders and separate script allowed for adoptation to meet changing system and security needs CAT I CAT II ./apply.sh NIST 800-53 NSA SNAC gen1000.sh gen2000.sh gen1000.sh gen3000.sh gen2000.sh nist1000.sh gen400.sh gen3000.sh nist2000.sh gen400.sh nist3000.sh nist4000.sh
Slide 47
C&A TESTING: OLD METHOD Technical control testing is a subset of overall system controls ● SECSCN - Legacy system security scanner useful for DCID 6/3 testing. Isn’t flexible enough to test most of ICD503 technical controls ● Bash script to manually test each control - System testers required a bash script to manually test each system control not checked by SECSCN ● Interactive tests - Tests that couldn’t be automatically checked in a bash script or special test cases Initially took 12+ months from paperwork submittal until initial approval
Slide 48

HARDENING: NEAR FUTURE METHOD Use OSCAP Anaconda Addon to specify CSCF-MLS profile during system build. Then apply custom configurations ● CSCF’s SCAP profile distributes hardened system configurations and policies for authentication, auditing, accounts, services ● Apply custom configurations separately from security relevant changes
Slide 49
C&A: CURRENT & FUTURE METHOD Current ( 90 days from submittal to approval ) : ● SECSCN: still in use for familiarity ● NESSUS: vulnerability scan ● OpenSCAP: Configuration Compliance checklist ● Small set of interactive checks Future ( Targeting <30 days from submittal to approval ): ● Drop SECSCN and NESSUS ● Fully utilize Anaconda-SCAP to provision directly into secure configuration ….DRAMATICALLY SIMPLIFIED
Slide 50
Slide 51

CONTACT INFO Shawn Wells Director, Innovation Programs shawn@redhat.com Jeff Blank Tech Director, OS and Applications Division, NSA IAD blank@eclipse.ncsc.mil Sarah Storms Project Engineer, CSCF, Lockheed Martin sarah.b.storms@lmco.com Josh Koontz Systems Engineer, CSCF, Lockheed Martin joshua.koontz@lmco.com