#RSAC SESSION ID: TECH-F02 Integrated Solutions for Trusted Clouds and SDI Steve Orrin Shawn Wells Federal Chief Technologist Intel Corp Chief Security Strategist Red Hat Public Sector
Slide 1

Slide 2

In the next 45 minutes … • Modern challenges for security and compliance in cloud stacks • Building block technologies: hardware & software • Step through reference designs • What’s coming next? • • SDN, SDS, containers, PaaS/SaaS, Audit as a Service Demos! 2 #RSAC
Slide 3
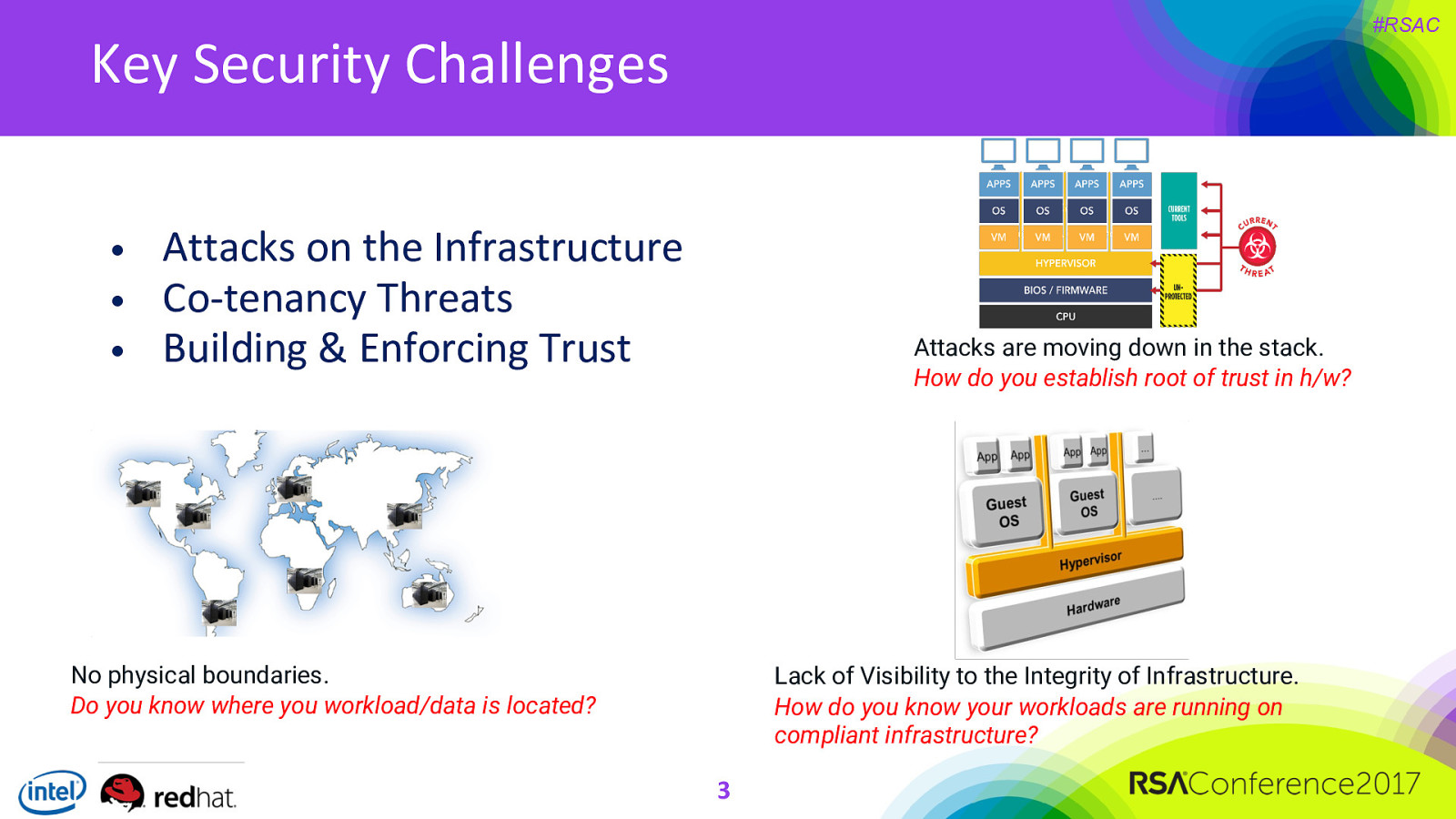
#RSAC Key Security Challenges • • • Attacks on the Infrastructure Co-tenancy Threats Building & Enforcing Trust Attacks are moving down in the stack. How do you establish root of trust in h/w? No physical boundaries. Do you know where you workload/data is located? Lack of Visibility to the Integrity of Infrastructure. How do you know your workloads are running on compliant infrastructure? 3
Slide 4
Compliance & Regulatory Challenges • • • • Achieving audit visibility Commingled regulatory environments Continuous monitoring Data use 4 #RSAC
Slide 5
Building Blocks of Trustworthy Clouds • Create a chain of trust rooted in hardware that extends to include the hypervisor • Provide visibility for compliance and audit • Use trust as part of the Policy Management for Cloud Activity • Trust as part of the VM Migration and Dynamic Provisioning Policies • Server tagging for richer policy decisions • Leverage infrastructure capabilities/services to address data protection requirements 5 #RSAC
Slide 6
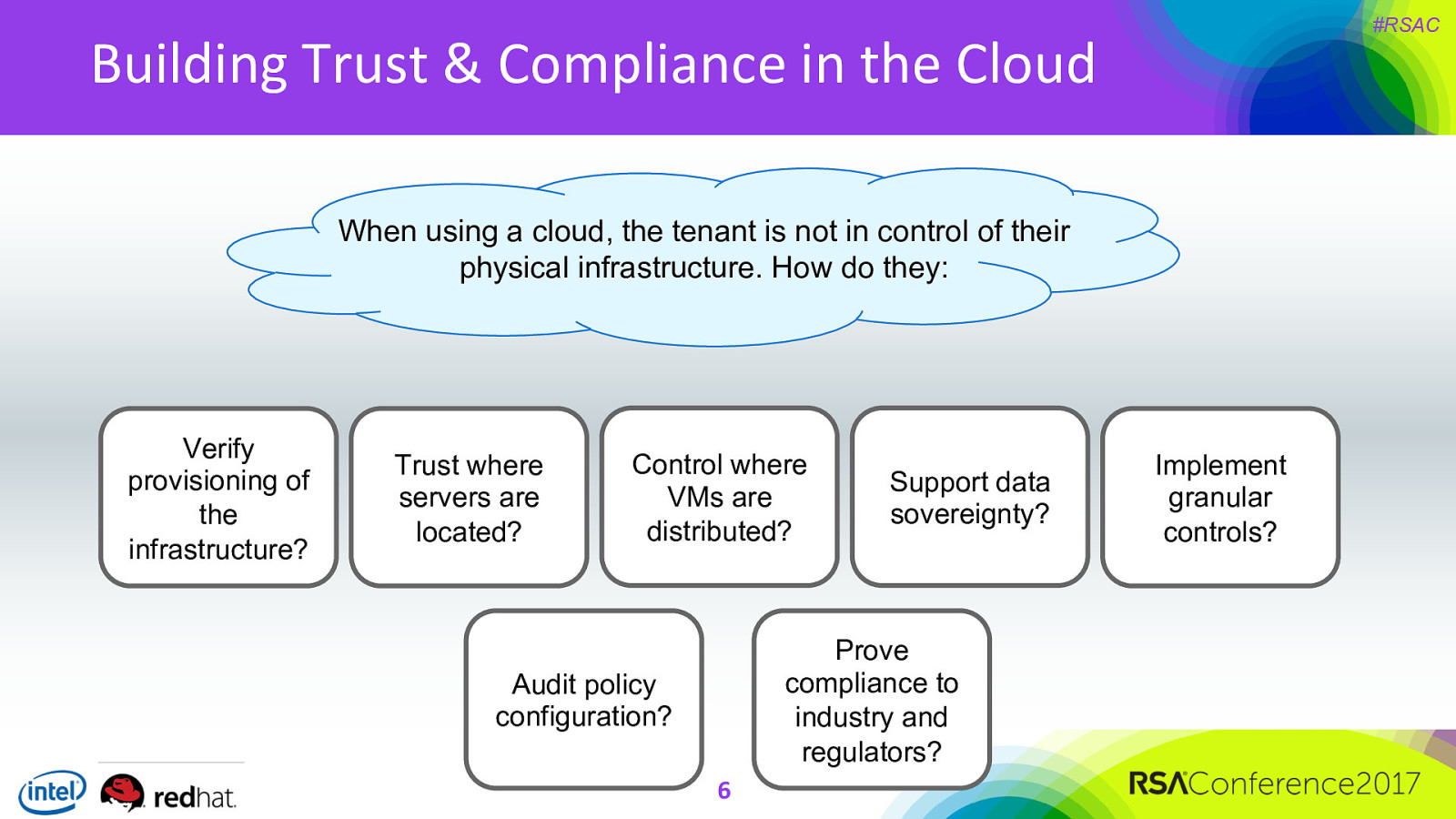
#RSAC Building Trust & Compliance in the Cloud When using a cloud, the tenant is not in control of their physical infrastructure. How do they: Verify provisioning of the infrastructure? Trust where servers are located? Control where VMs are distributed? Support data sovereignty? Prove compliance to industry and regulators? Audit policy configuration? 6 Implement granular controls?
Slide 7

#RSAC Building Blocks
Slide 8

Building Block Technologies Hardware • TXT, AESNI, DRNG, CryptoNI Software • Linux, KVM, OpenStack, CloudForms, Ceph, VMWare (VCenter, VSphere, ESXi), OpenCIT, Hytrust, Cloud Raxak 8 #RSAC
Slide 9
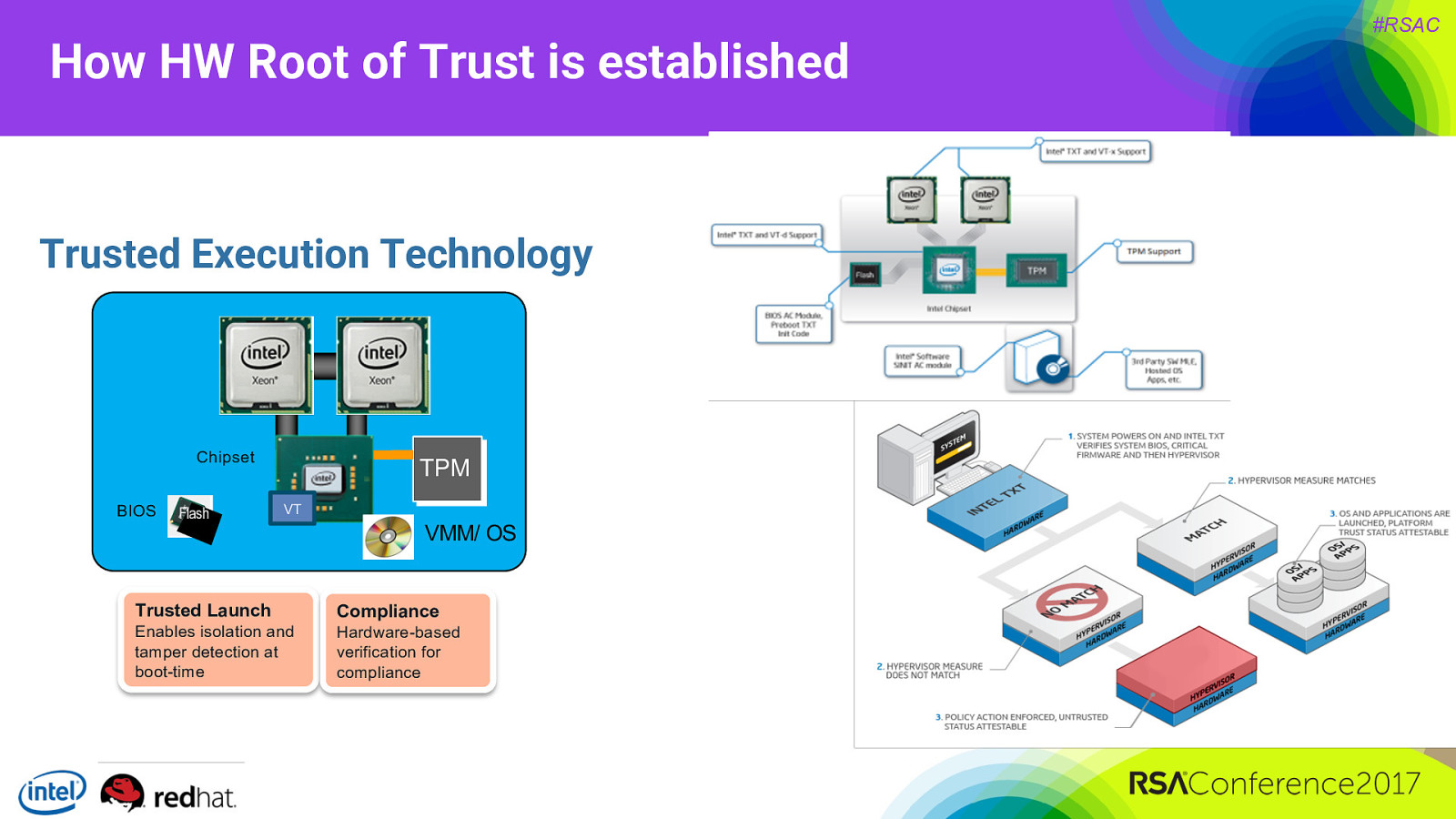
How HW Root of Trust is established Trusted Execution Technology Chipset BIOS Flash TPM VT VMM/ OS Trusted Launch Compliance Enables isolation and tamper detection at boot-time Hardware-based verification for compliance #RSAC
Slide 10
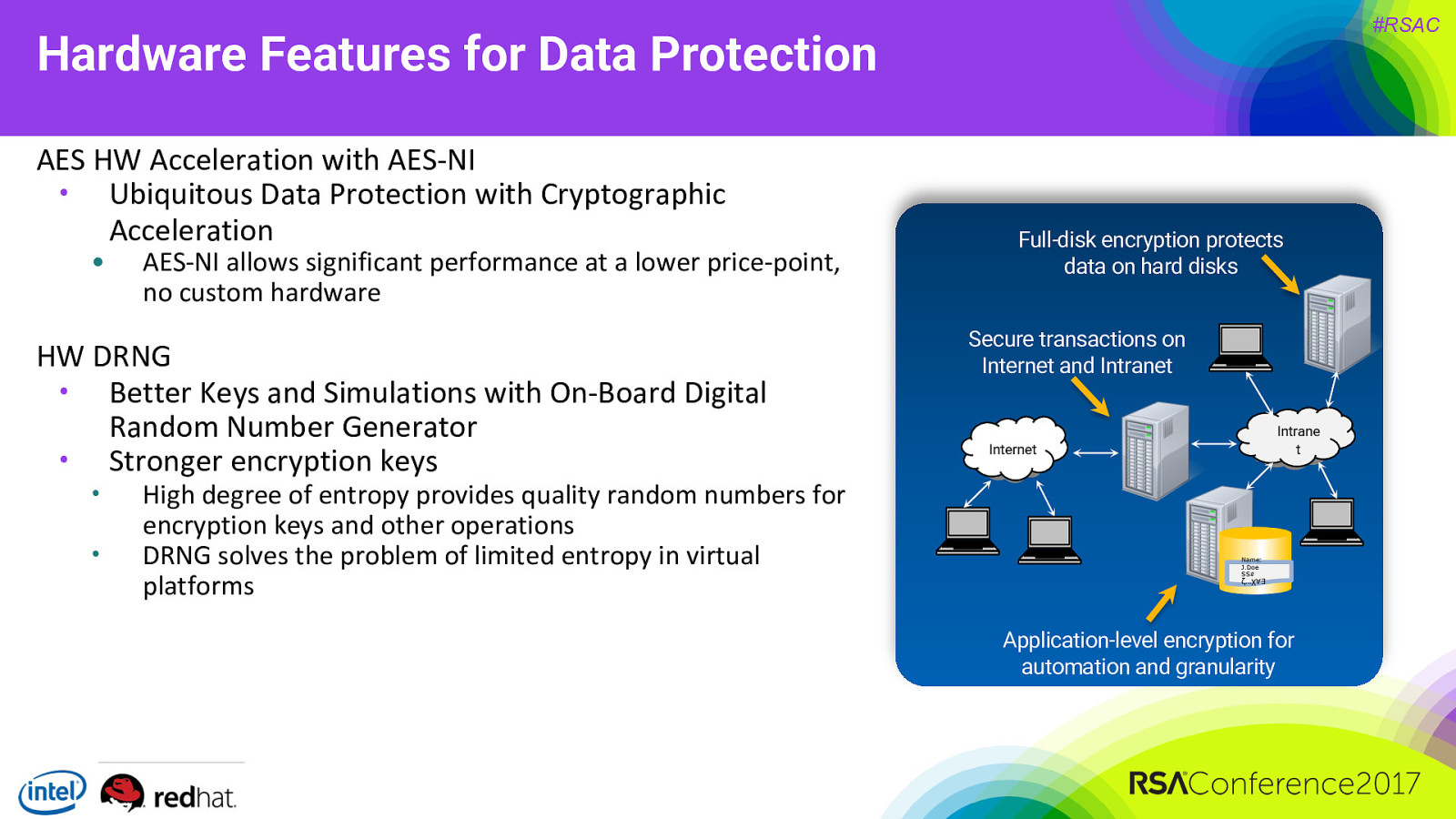
#RSAC Hardware Features for Data Protection AES HW Acceleration with AES-NI • Ubiquitous Data Protection with Cryptographic Acceleration • AES-NI allows significant performance at a lower price-point, no custom hardware HW DRNG • Better Keys and Simulations with On-Board Digital Random Number Generator • Stronger encryption keys • • High degree of entropy provides quality random numbers for encryption keys and other operations DRNG solves the problem of limited entropy in virtual platforms Full-disk encryption protects data on hard disks Secure transactions on Internet and Intranet Intrane t Internet Name: J.Doe SS# ζ…χ∀∃ Application-level encryption for automation and granularity
Slide 11
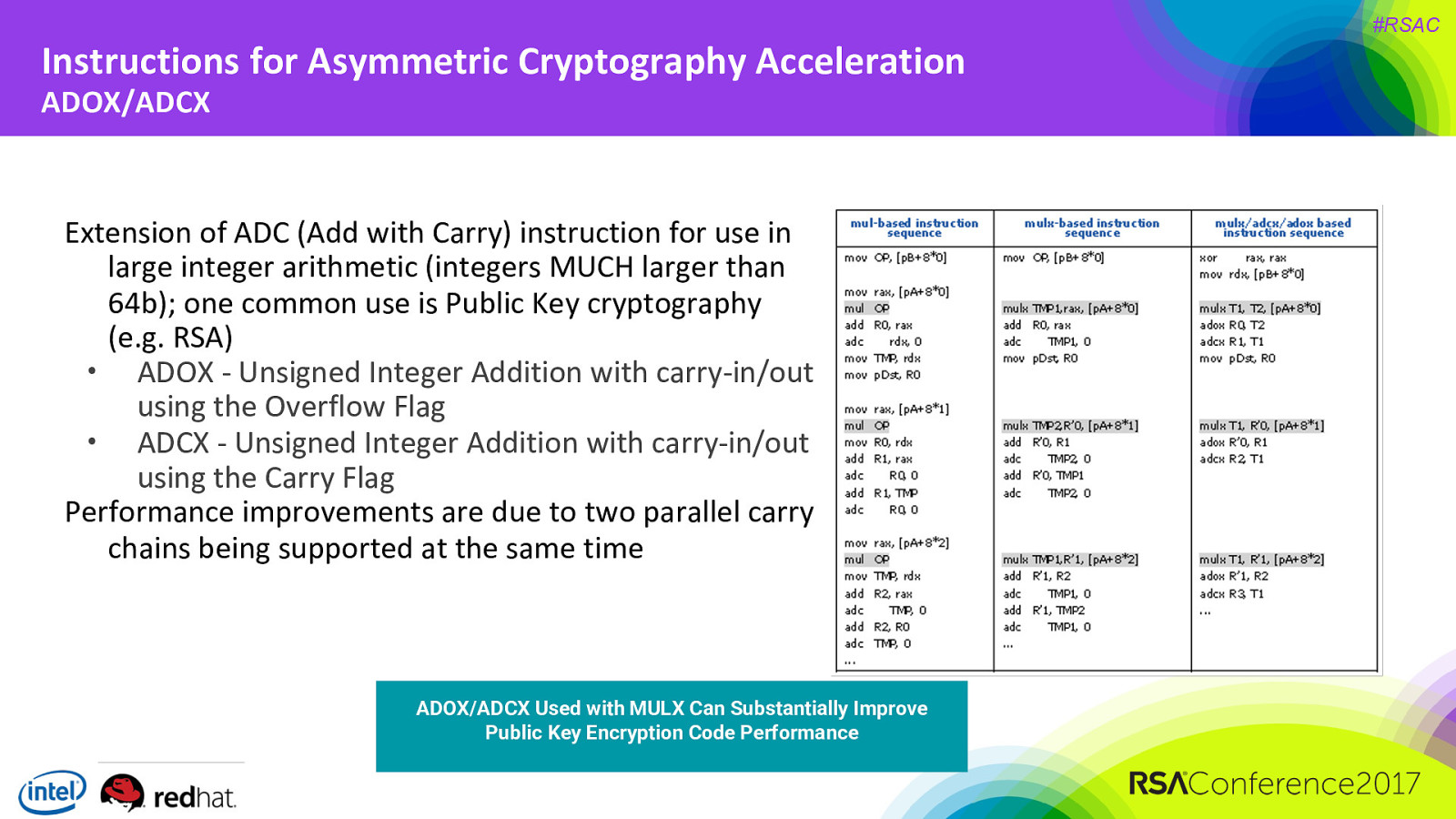
Instructions for Asymmetric Cryptography Acceleration ADOX/ADCX Extension of ADC (Add with Carry) instruction for use in large integer arithmetic (integers MUCH larger than 64b); one common use is Public Key cryptography (e.g. RSA) • ADOX - Unsigned Integer Addition with carry-in/out using the Overflow Flag • ADCX - Unsigned Integer Addition with carry-in/out using the Carry Flag Performance improvements are due to two parallel carry chains being supported at the same time ADOX/ADCX Used with MULX Can Substantially Improve Public Key Encryption Code Performance #RSAC
Slide 12
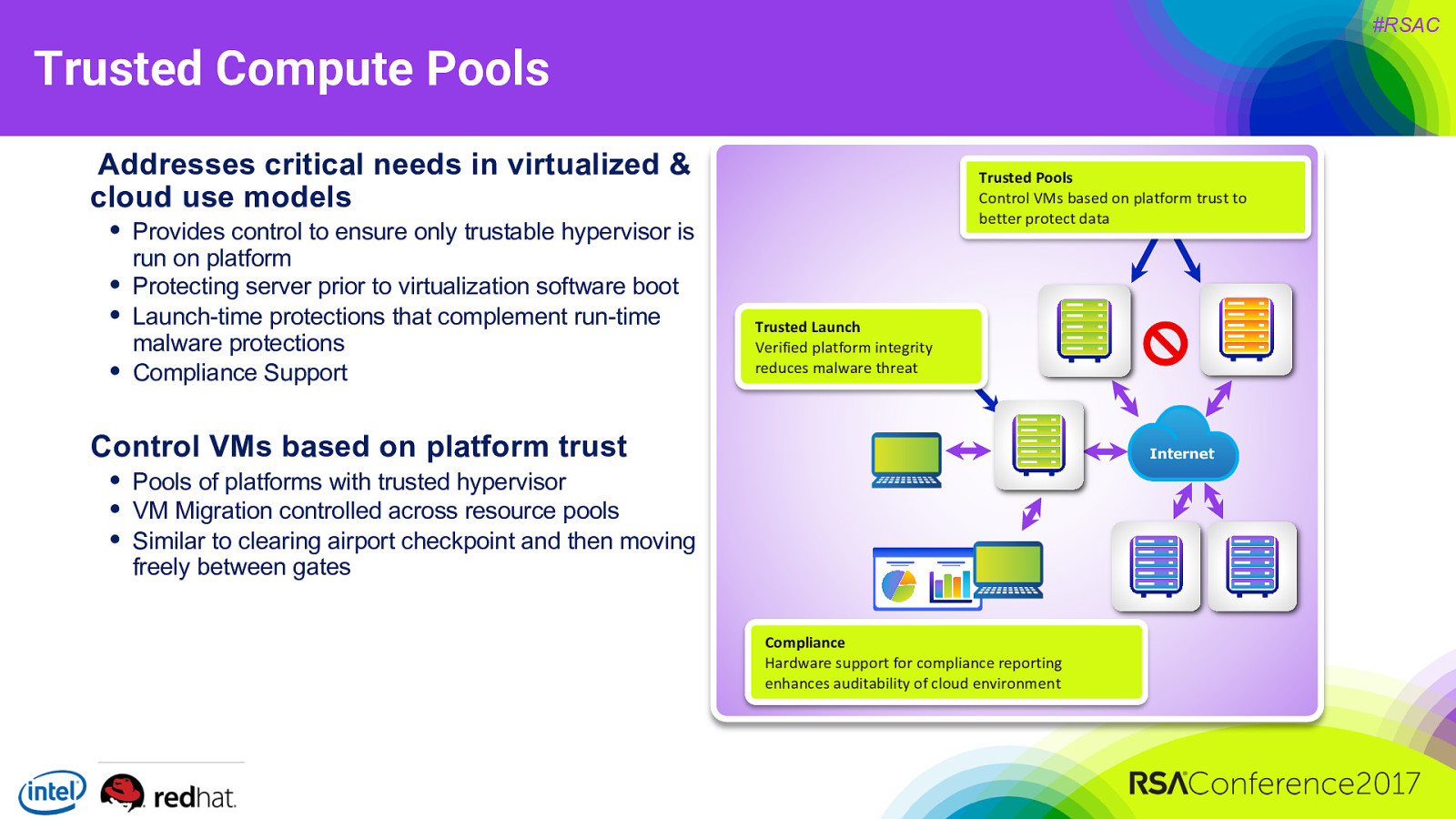
#RSAC Trusted Compute Pools Addresses critical needs in virtualized & cloud use models • Provides control to ensure only trustable hypervisor is • • • run on platform Protecting server prior to virtualization software boot Launch-time protections that complement run-time malware protections Compliance Support Trusted Pools Control VMs based on platform trust to better protect data Trusted Launch Verified platform integrity reduces malware threat Control VMs based on platform trust • Pools of platforms with trusted hypervisor • VM Migration controlled across resource pools • Similar to clearing airport checkpoint and then moving Internet freely between gates Compliance Hardware support for compliance reporting enhances auditability of cloud environment
Slide 13
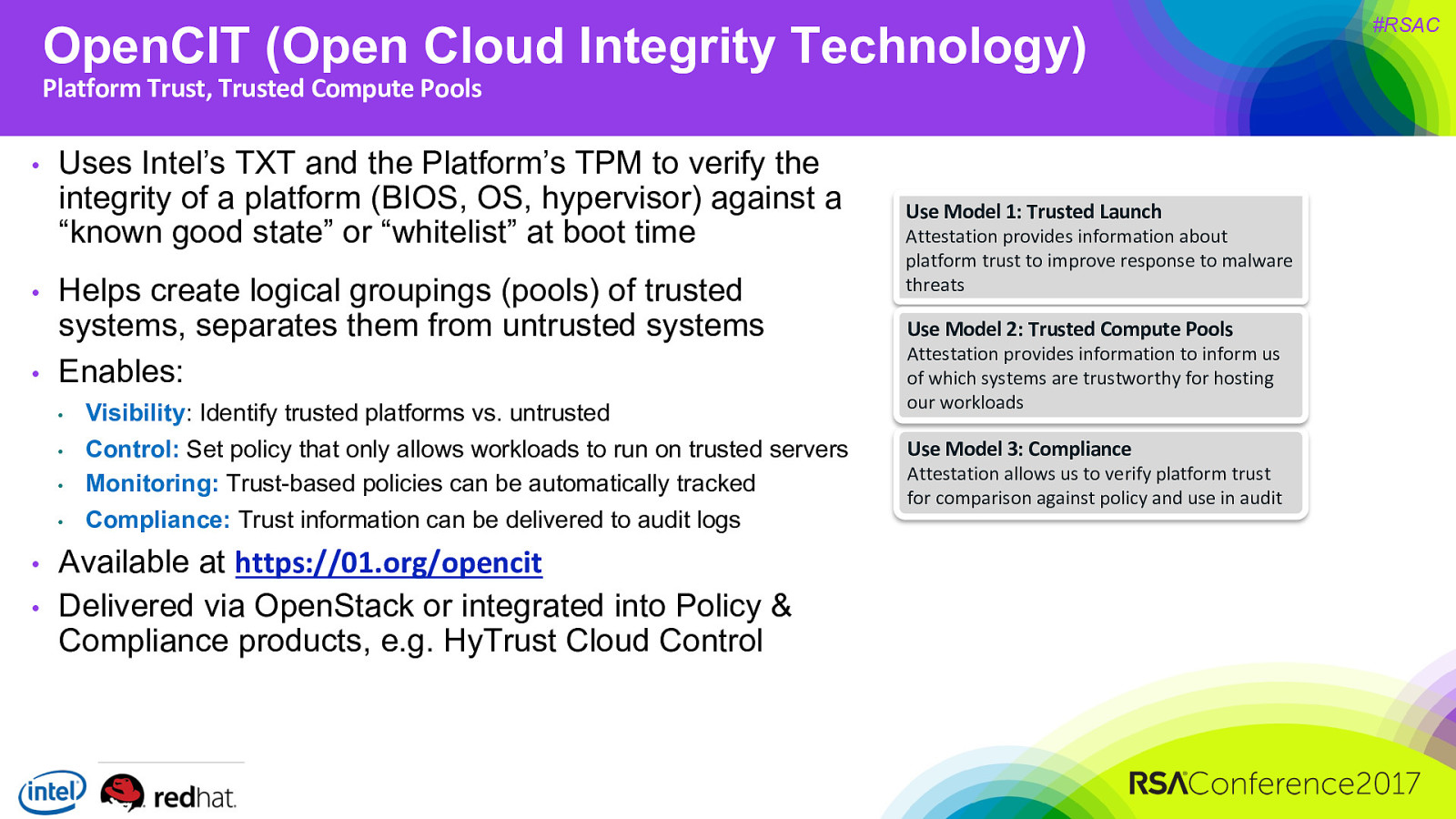
OpenCIT (Open Cloud Integrity Technology) Platform Trust, Trusted Compute Pools • • • Uses Intel’s TXT and the Platform’s TPM to verify the integrity of a platform (BIOS, OS, hypervisor) against a “known good state” or “whitelist” at boot time Helps create logical groupings (pools) of trusted systems, separates them from untrusted systems Enables: • • • • • • Visibility: Identify trusted platforms vs. untrusted Control: Set policy that only allows workloads to run on trusted servers Monitoring: Trust-based policies can be automatically tracked Compliance: Trust information can be delivered to audit logs Available at https://01.org/opencit Delivered via OpenStack or integrated into Policy & Compliance products, e.g. HyTrust Cloud Control Use Model 1: Trusted Launch Attestation provides information about platform trust to improve response to malware threats Use Model 2: Trusted Compute Pools Attestation provides information to inform us of which systems are trustworthy for hosting our workloads Use Model 3: Compliance Attestation allows us to verify platform trust for comparison against policy and use in audit #RSAC
Slide 14
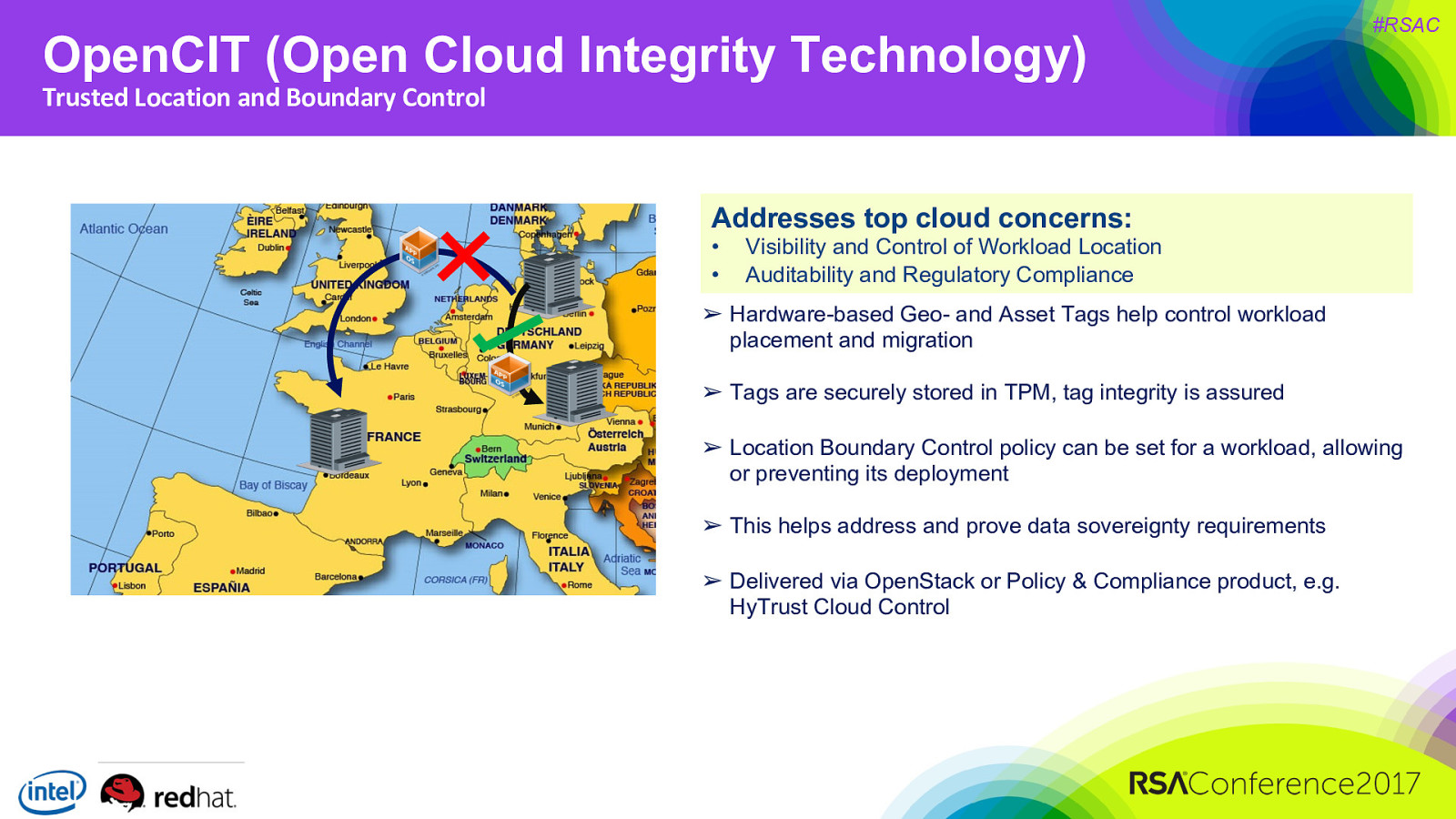
OpenCIT (Open Cloud Integrity Technology) #RSAC Trusted Location and Boundary Control Addresses top cloud concerns: • • Visibility and Control of Workload Location Auditability and Regulatory Compliance ➢ Hardware-based Geo- and Asset Tags help control workload placement and migration ➢ Tags are securely stored in TPM, tag integrity is assured ➢ Location Boundary Control policy can be set for a workload, allowing or preventing its deployment ➢ This helps address and prove data sovereignty requirements ➢ Delivered via OpenStack or Policy & Compliance product, e.g. HyTrust Cloud Control
Slide 15
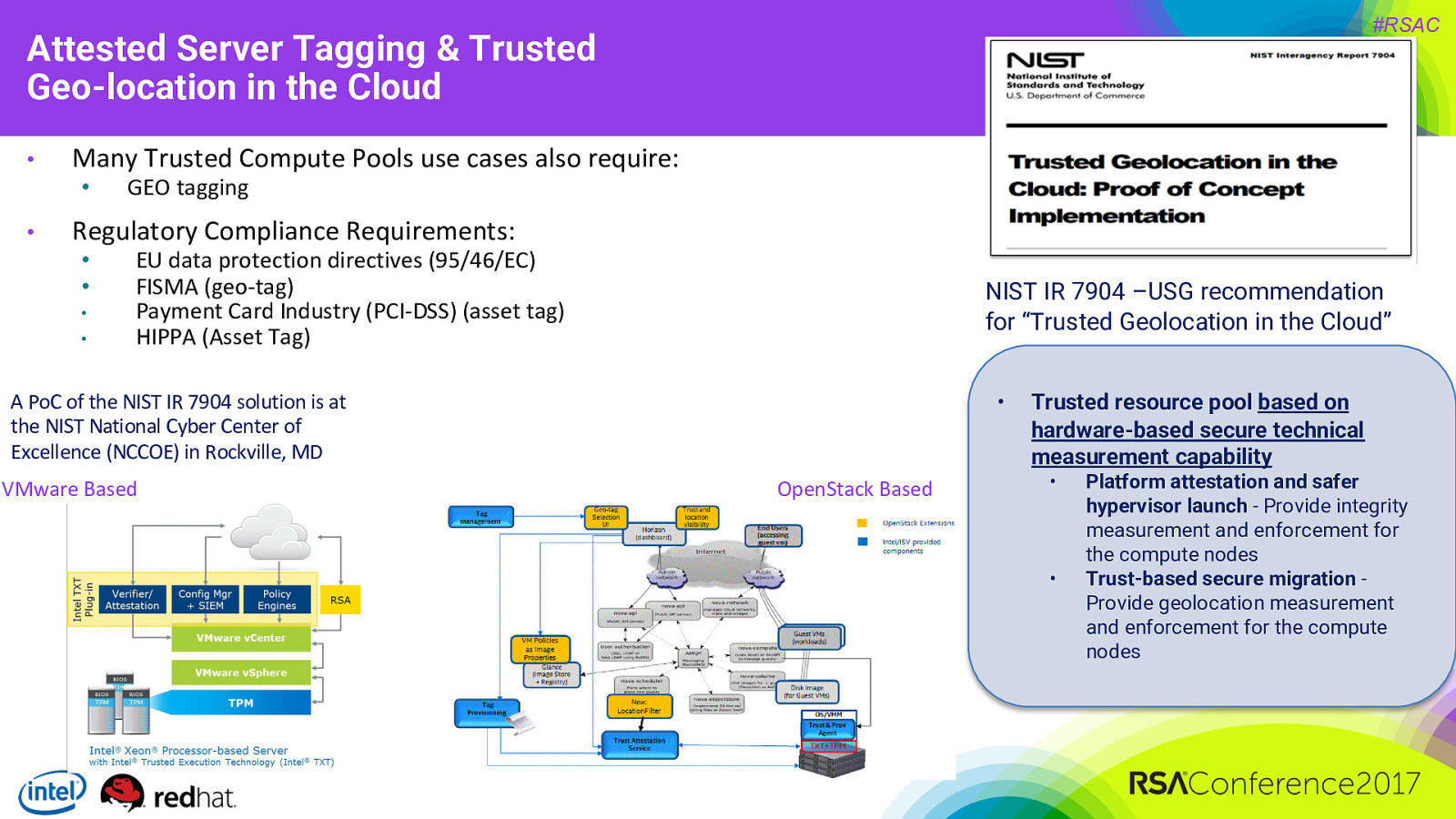
#RSAC Attested Server Tagging & Trusted Geo-location in the Cloud • Many Trusted Compute Pools use cases also require: • • GEO tagging Regulatory Compliance Requirements: • • • • EU data protection directives (95/46/EC) FISMA (geo-tag) Payment Card Industry (PCI-DSS) (asset tag) HIPPA (Asset Tag) NIST IR 7904 –USG recommendation for “Trusted Geolocation in the Cloud” A PoC of the NIST IR 7904 solution is at the NIST National Cyber Center of Excellence (NCCOE) in Rockville, MD VMware Based • OpenStack Based Trusted resource pool based on hardware-based secure technical measurement capability • • Platform attestation and safer hypervisor launch - Provide integrity measurement and enforcement for the compute nodes Trust-based secure migration Provide geolocation measurement and enforcement for the compute nodes
Slide 16
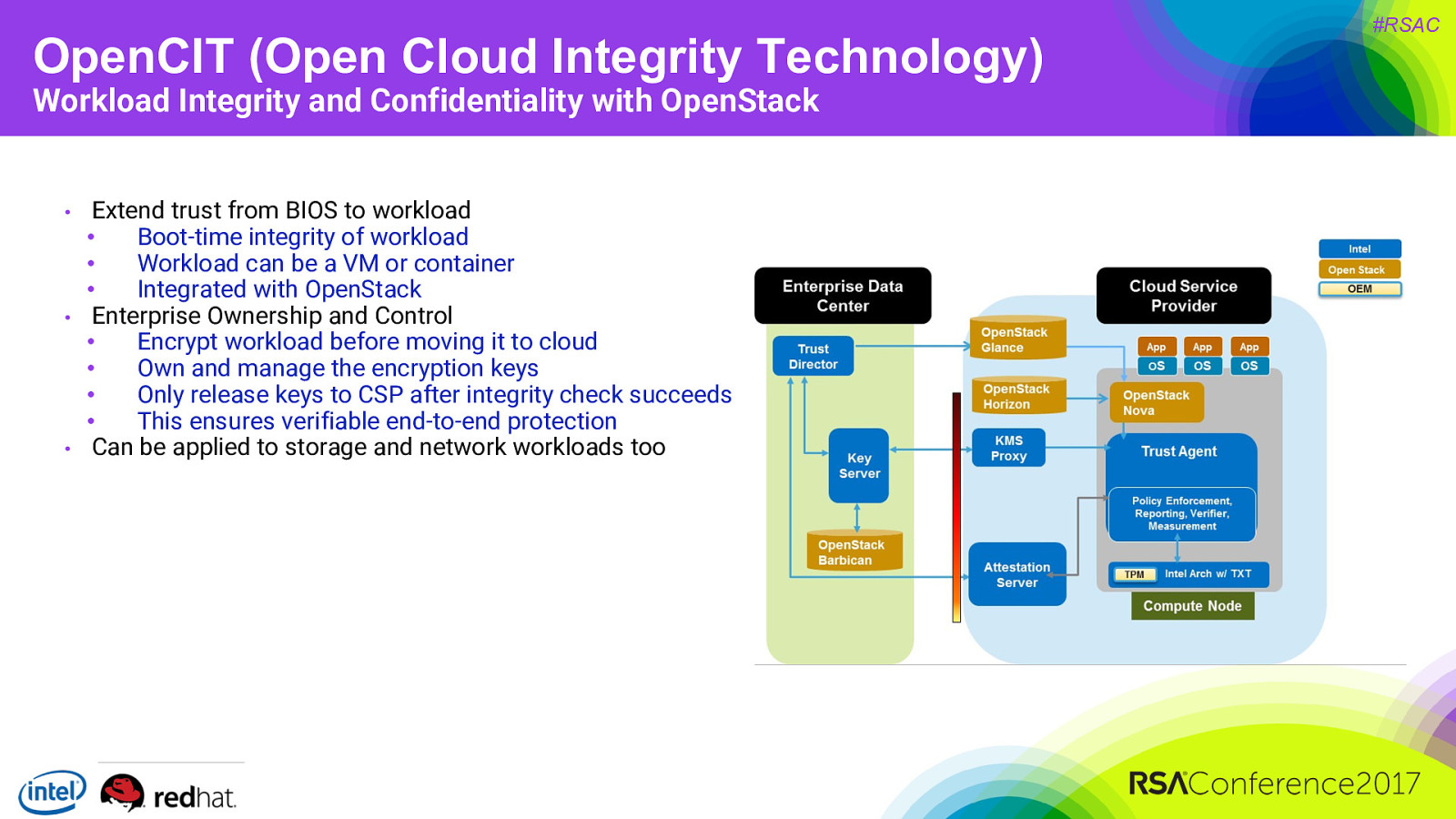
OpenCIT (Open Cloud Integrity Technology) Workload Integrity and Confidentiality with OpenStack • • • Extend trust from BIOS to workload • Boot-time integrity of workload • Workload can be a VM or container • Integrated with OpenStack Enterprise Ownership and Control • Encrypt workload before moving it to cloud • Own and manage the encryption keys • Only release keys to CSP after integrity check succeeds • This ensures verifiable end-to-end protection Can be applied to storage and network workloads too #RSAC
Slide 17

Trusted Compute Pools Industry Support Server Systems Software and Solutions DuPont deployed Intel TXT to ensure that the computing pools remained trusted, based on the original configurations across both Linux and Windows operating environments. “Security in the cloud is paramount and Virtustream has adopted some of Intel technologies around security including Intel TXT.” Don Whittington, VP & CIO, Florida Crystals …address TWSE’s business needs and increase the overall trust and security of its cloud infrastructure using Intel TXT and solutions from Cisco, HyTrust, McAfee and VMware. “Hardware-enhanced security provided by Intel TXT is critical to protect our sensitive data and was key in our selection of Virtustream for cloud services.” Joh F. Hill, CIO, Veyance Technologies Products and Solution Providers Customers #RSAC
Slide 18

#RSAC Reference Designs
Slide 19
#RSAC Real World Solutions • Private Cloud Implementations • • • Commercial Solution Providers (CSP’s) • • • VMWare + Intel + HyTrust Intel + Red Hat (RHEL/OpenStack/CloudForms/Ceph) IBM Softlayer (w/VMWare + Intel + HyTrust) CSRA (w/Intel + Red Hat) Hyper Converged Secure SCI • BlackBox + NEC + Red Hat + Intel 19
Slide 20
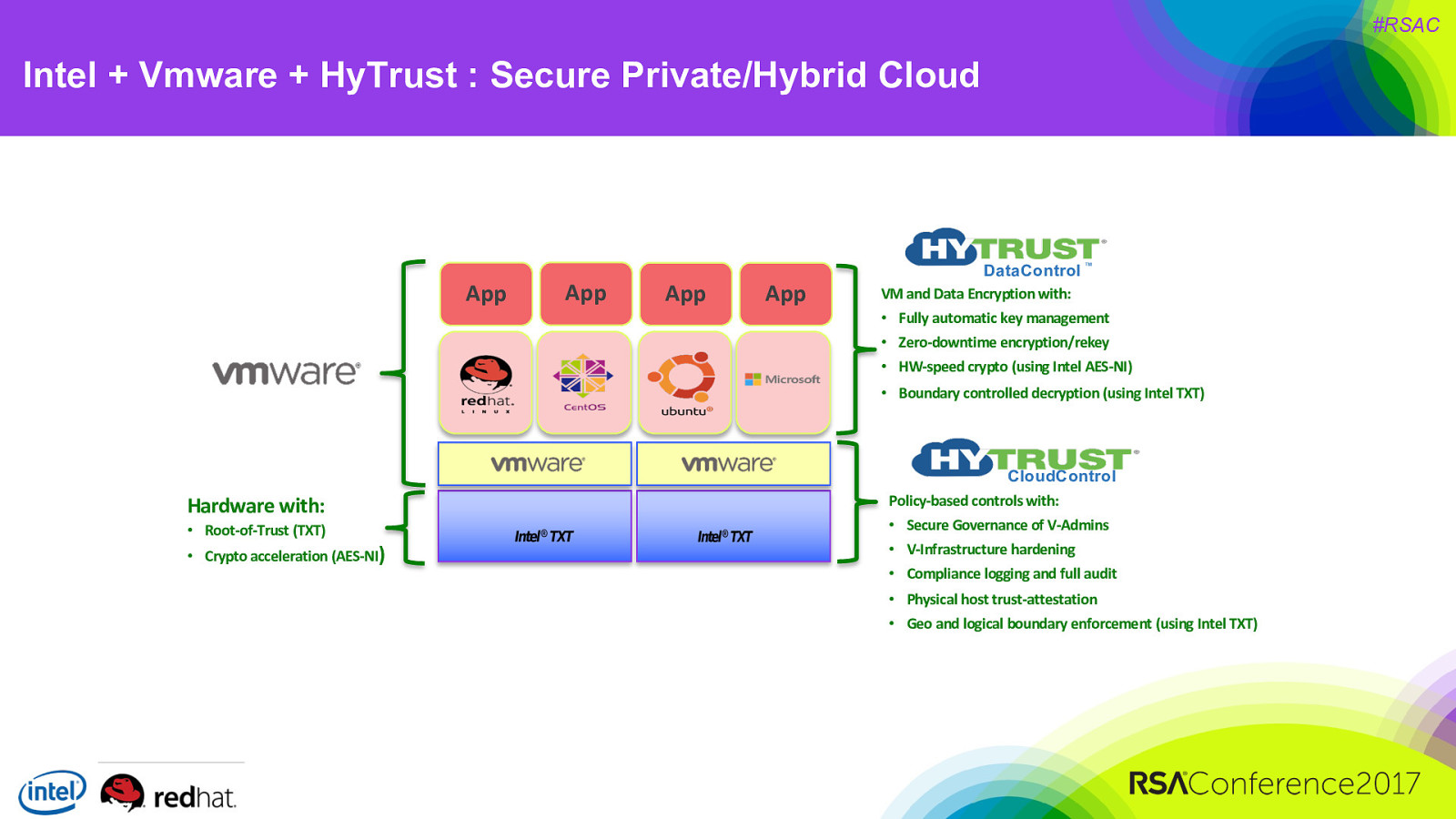
#RSAC Intel + Vmware + HyTrust : Secure Private/Hybrid Cloud App App App App DataControl ™ VM and Data Encryption with: • Fully automatic key management • Zero-downtime encryption/rekey • HW-speed crypto (using Intel AES-NI) • Boundary controlled decryption (using Intel TXT) CloudControl Hardware with: • Root-of-Trust (TXT) • Crypto acceleration (AES-NI) Policy-based controls with: • Secure Governance of V-Admins • V-Infrastructure hardening • Compliance logging and full audit • Physical host trust-attestation • Geo and logical boundary enforcement (using Intel TXT)
Slide 21
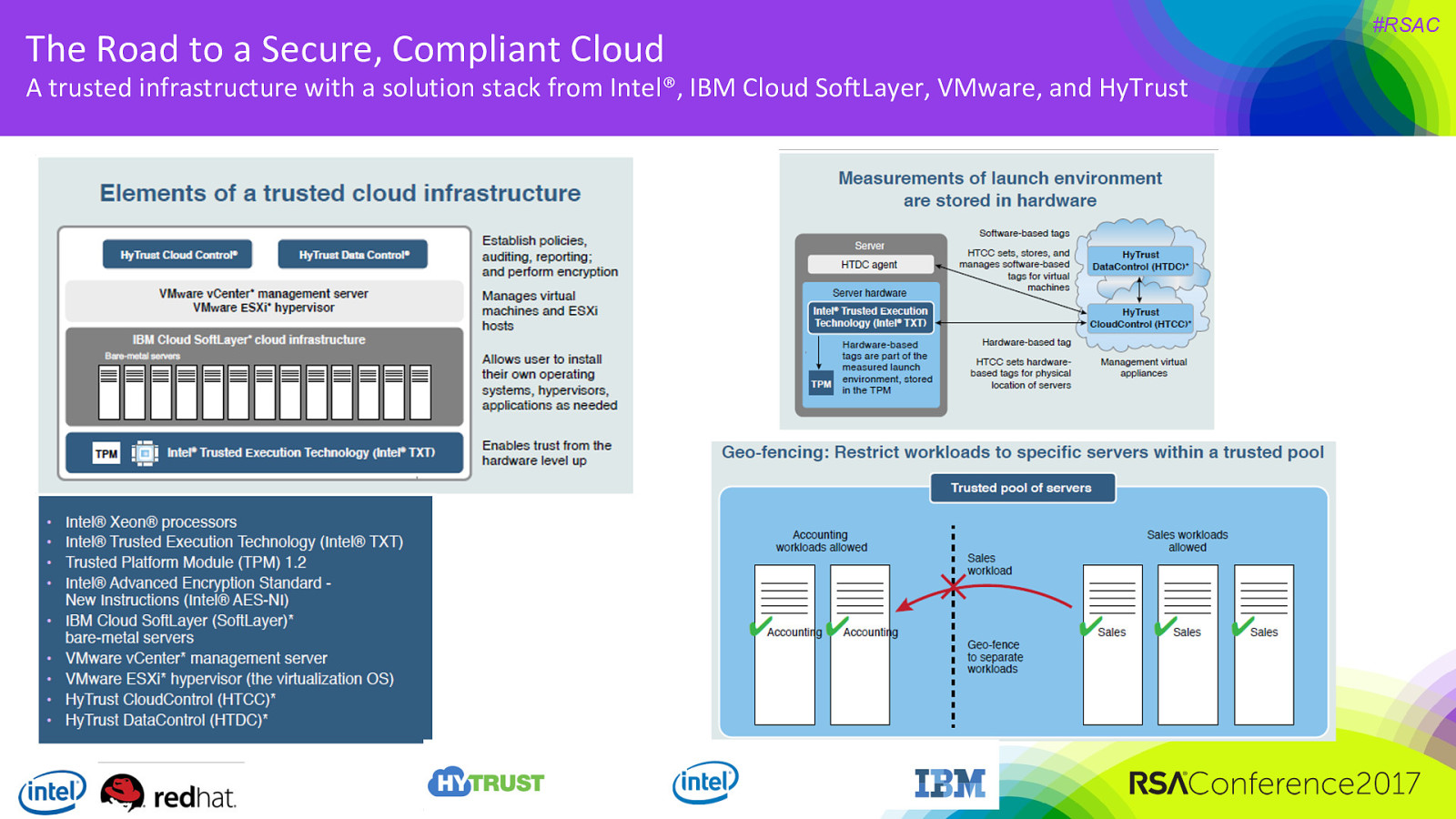
The Road to a Secure, Compliant Cloud A trusted infrastructure with a solution stack from Intel®, IBM Cloud SoftLayer, VMware, and HyTrust #RSAC
Slide 22
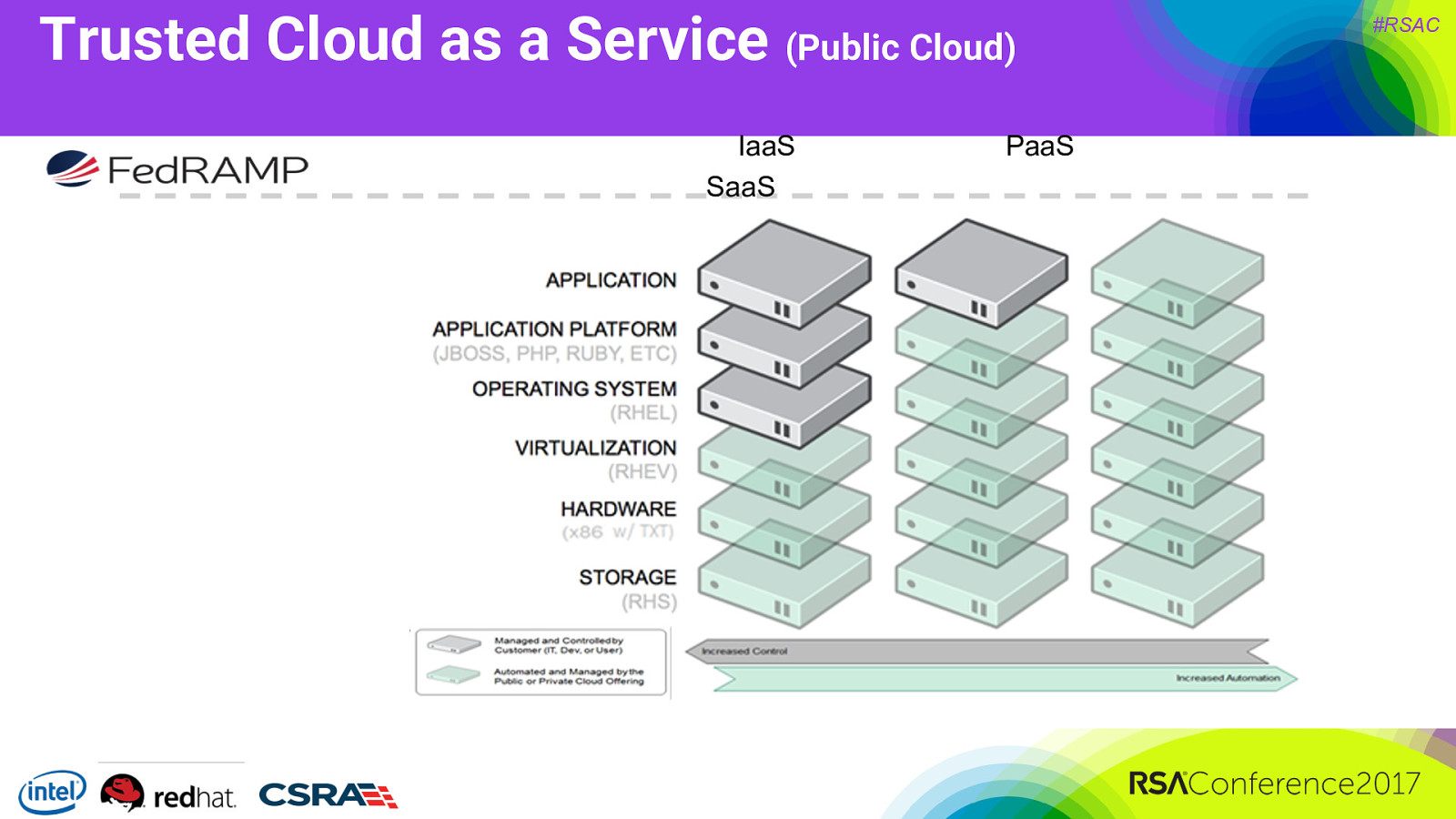
Trusted Cloud as a Service (Public Cloud) IaaS SaaS PaaS #RSAC
Slide 23
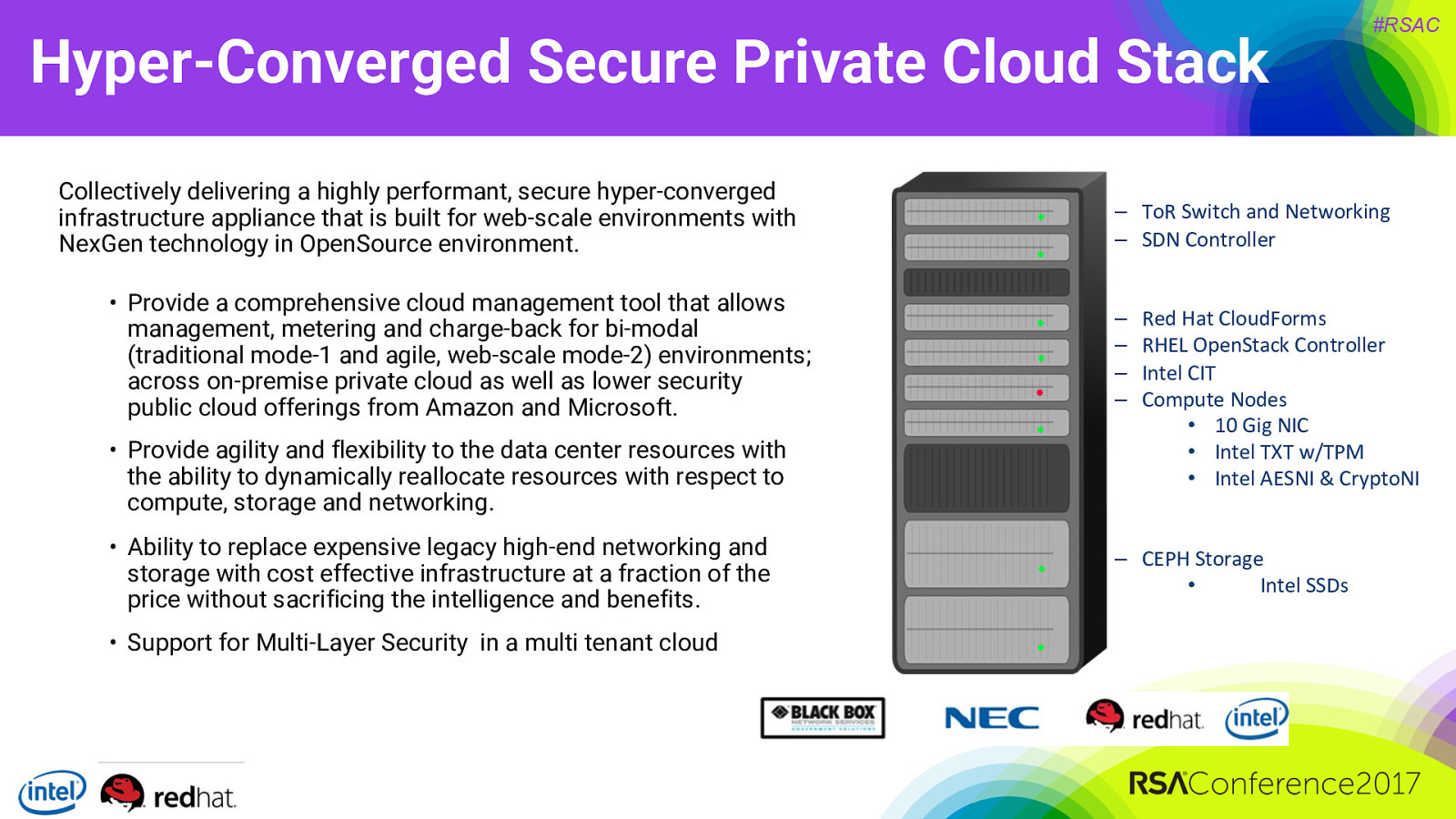
Hyper-Converged Secure Private Cloud Stack Collectively delivering a highly performant, secure hyper-converged infrastructure appliance that is built for web-scale environments with NexGen technology in OpenSource environment. • Provide a comprehensive cloud management tool that allows management, metering and charge-back for bi-modal (traditional mode-1 and agile, web-scale mode-2) environments; across on-premise private cloud as well as lower security public cloud offerings from Amazon and Microsoft. • Provide agility and flexibility to the data center resources with the ability to dynamically reallocate resources with respect to compute, storage and networking. • Ability to replace expensive legacy high-end networking and storage with cost effective infrastructure at a fraction of the price without sacrificing the intelligence and benefits. • Support for Multi-Layer Security in a multi tenant cloud #RSAC ‒ ToR Switch and Networking ‒ SDN Controller ‒ ‒ ‒ ‒ Red Hat CloudForms RHEL OpenStack Controller Intel CIT Compute Nodes • 10 Gig NIC • Intel TXT w/TPM • Intel AESNI & CryptoNI ‒ CEPH Storage • Intel SSDs
Slide 24

#RSAC Demos!
Slide 25
#RSAC Demo #1: Automated Security Scanning https://www.open-scap.org/ http://docs.openstack.org/sec/ 25
Slide 26
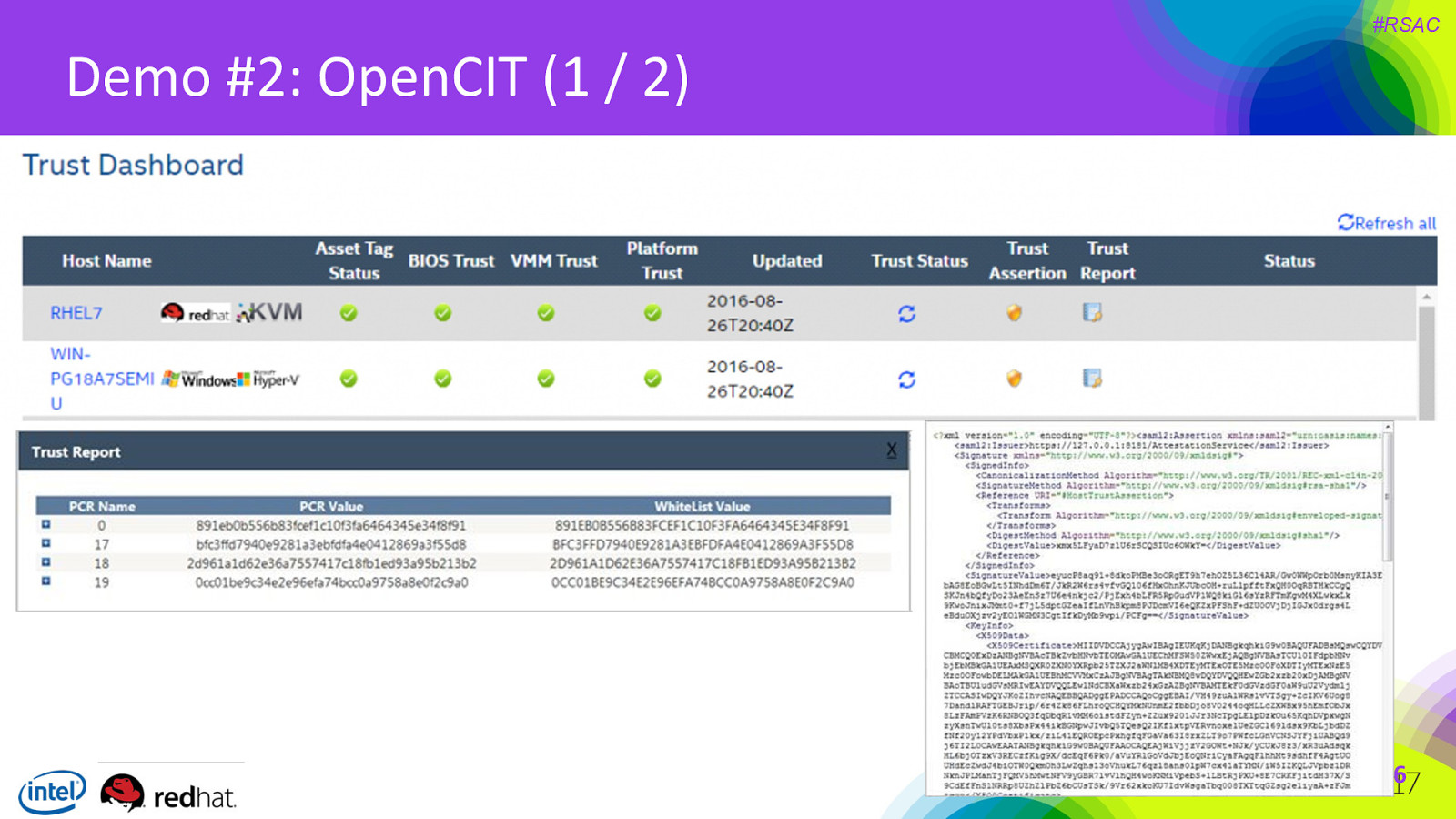
#RSAC Demo #2: OpenCIT (1 / 2) 26
Slide 27
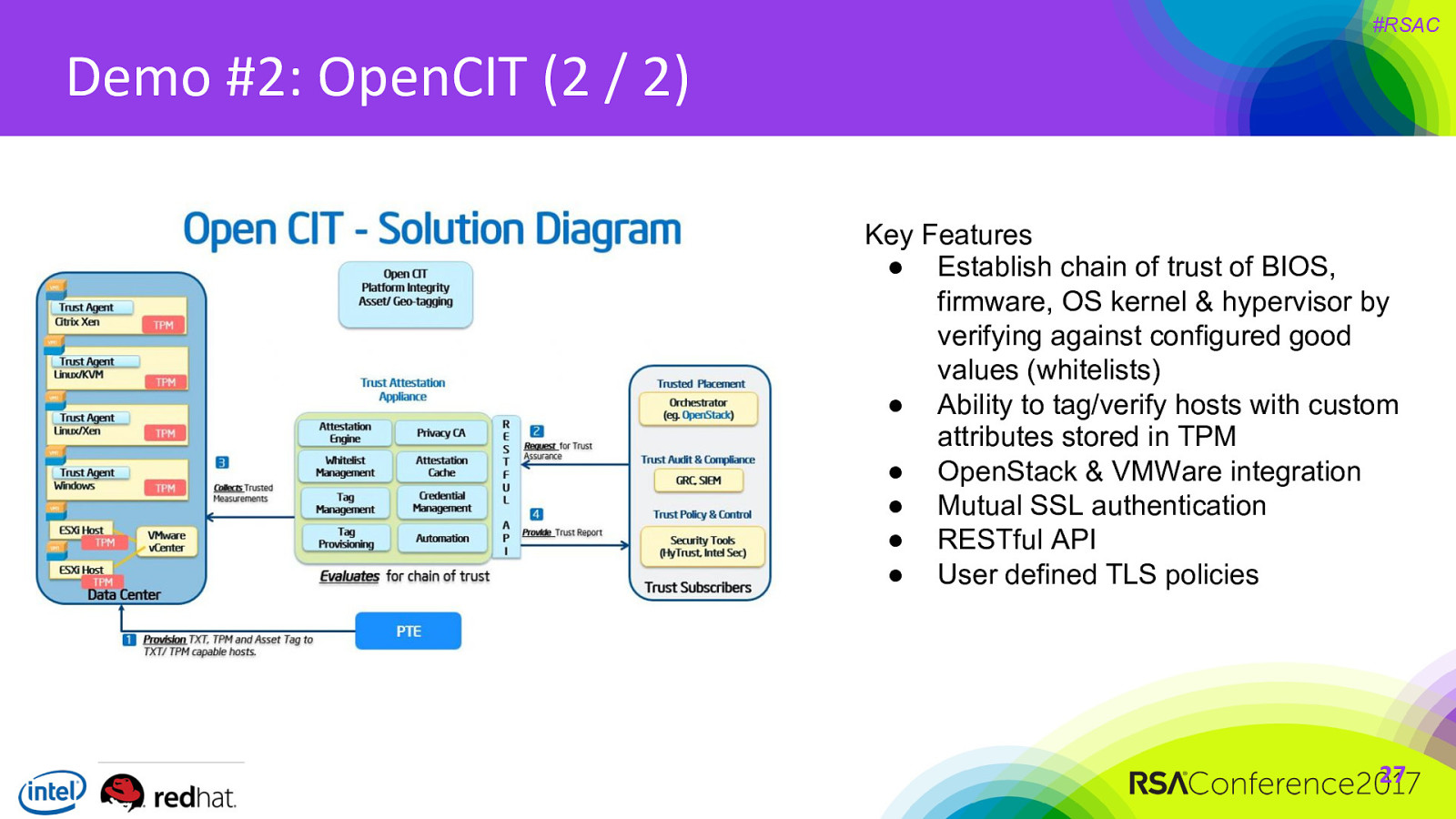
#RSAC Demo #2: OpenCIT (2 / 2) Key Features ● Establish chain of trust of BIOS, firmware, OS kernel & hypervisor by verifying against configured good values (whitelists) ● Ability to tag/verify hosts with custom attributes stored in TPM ● OpenStack & VMWare integration ● Mutual SSL authentication ● RESTful API ● User defined TLS policies 27
Slide 28

#RSAC Roadmap
Slide 29
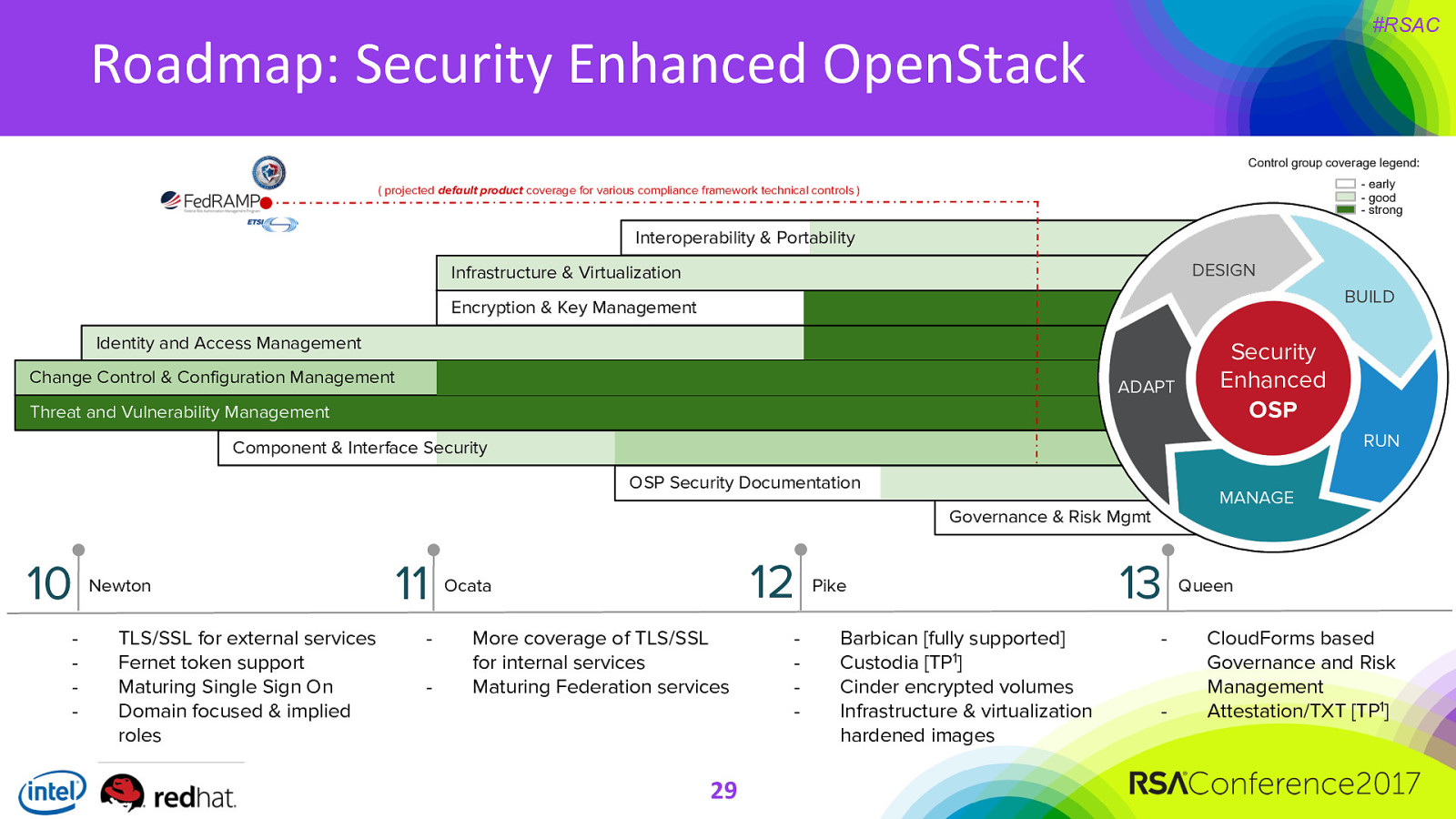
#RSAC Roadmap: Security Enhanced OpenStack Control group coverage legend: - early - good - strong ( projected default product coverage for various compliance framework technical controls ) Interoperability & Portability DESIGN Infrastructure & Virtualization BUILD Encryption & Key Management Identity and Access Management Change Control & Configuration Management ADAPT Threat and Vulnerability Management Security Enhanced OSP RUN Component & Interface Security OSP Security Documentation MANAGE Governance & Risk Mgmt 10 - Newton TLS/SSL for external services Fernet token support Maturing Single Sign On Domain focused & implied roles 11 - 12 Ocata More coverage of TLS/SSL for internal services Maturing Federation services 29
Pike Barbican [fully supported] Custodia [TP1] Cinder encrypted volumes Infrastructure & virtualization hardened images 13 - Queen CloudForms based Governance and Risk Management Attestation/TXT [TP1]
Slide 30
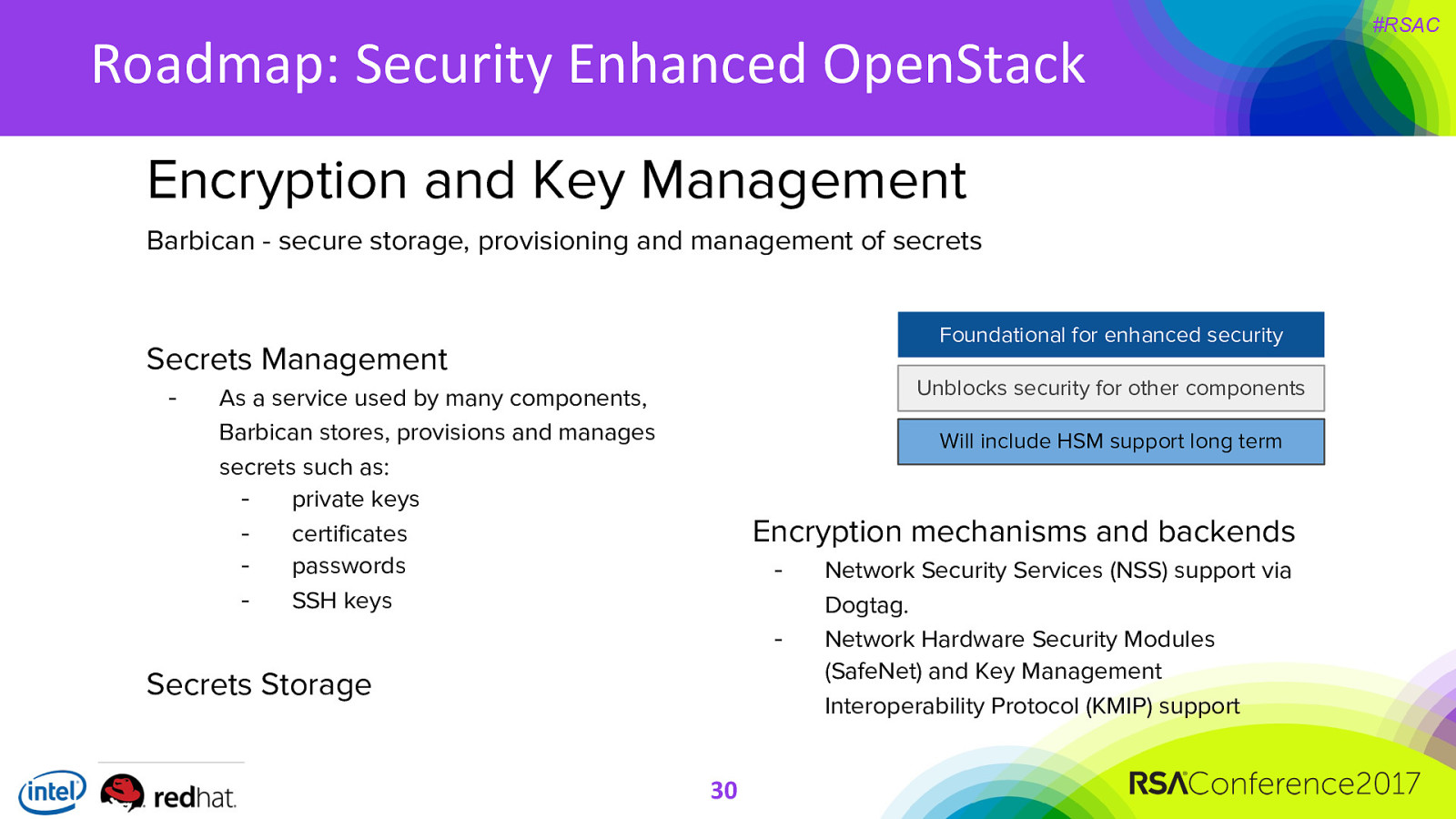
Roadmap: Security Enhanced OpenStack Encryption and Key Management Barbican - secure storage, provisioning and management of secrets Foundational for enhanced security Secrets Management - Unblocks security for other components As a service used by many components, Barbican stores, provisions and manages secrets such as: - private keys - certificates - passwords - SSH keys Will include HSM support long term Encryption mechanisms and backends - Secrets Storage 30 Network Security Services (NSS) support via Dogtag. Network Hardware Security Modules (SafeNet) and Key Management Interoperability Protocol (KMIP) support #RSAC
Slide 31
#RSAC What’s coming next • SDN, SDS, Containers, PaaS/SaaS, Audit as a Service 31
Slide 32

Summary Cloud Security begins with trust and visibility enabled by hardware and delivered by the infrastructure • Intel is driving hardware assisted security into the ecosystem of OEMs, ISVs, and CSPs • Red Hat enables the technologies in Linux and OpenStack for private, hybrid, and public cloud The risks and threats to the Cloud can be mitigated and managed • But it takes an ecosystem of software, hardware, and service providers #RSAC
Slide 33

Call to Action Work with your vendors and CSPs • Require security and trust for your workloads and data • Require visibility and the necessary feeds and monitoring to achieve compliance • For Private and Hybrid use cases, implement your policies for workload and data protection/control and then enforce them via orchestration • Make platform/HW trust a requirement on your service providers and supply chain Verify, then Trust, then Verify again • Validate that controls are configured correctly and generating the necessary ‘evidence’ (logs, reports, attestation of trust, ….) • Continuously validate trust level and residency What should be Next? • What architectures and configurations should Industry tackle next? • Where else is trust and secure orchestration needed? #RSAC
Slide 34

#RSAC Q&A
Slide 35

#RSAC Contact Us Steve Orrin Federal Chief Technologist, Intel Corp steve.orrin@intel.com Shawn Wells [LinkedIn] Chief Security Strategist, Red Hat Public Sector shawn@redhat.com 35
Slide 36

#RSAC Legal Disclaimers • • • • • INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANTED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL’S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER AND INTEL DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY, RELATING TO SALE AND/OR USE OF INTEL PRODUCTS INCLUDING LIABILITY OR WARRANTIES RELATING TO FITNESS FOR A PARTICULAR PURPOSE, MERCHANTABILITY, OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT. A “Mission Critical Application” is any application in which failure of the Intel Product could result, directly or indirectly, in personal injury or death. SHOULD YOU PURCHASE OR USE INTEL’S PRODUCTS FOR ANY SUCH MISSION CRITICAL APPLICATION, YOU SHALL INDEMNIFY AND HOLD INTEL AND ITS SUBSIDIARIES, SUBCONTRACTORS AND AFFILIATES, AND THE DIRECTORS, OFFICERS, AND EMPLOYEES OF EACH, HARMLESS AGAINST ALL CLAIMS COSTS, DAMAGES, AND EXPENSES AND REASONABLE ATTORNEYS’ FEES ARISING OUT OF, DIRECTLY OR INDIRECTLY, ANY CLAIM OF PRODUCT LIABILITY, PERSONAL INJURY, OR DEATH ARISING IN ANY WAY OUT OF SUCH MISSION CRITICAL APPLICATION, WHETHER OR NOT INTEL OR ITS SUBCONTRACTOR WAS NEGLIGENT IN THE DESIGN, MANUFACTURE, OR WARNING OF THE INTEL PRODUCT OR ANY OF ITS PARTS. Intel may make changes to specifications and product descriptions at any time, without notice. Designers must not rely on the absence or characteristics of any features or instructions marked “reserved” or “undefined”. Intel reserves these for future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them. The information here is subject to change without notice. Do not finalize a design with this information. The products described in this document may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current characterized errata are available on request. Contact your local Intel sales office or your distributor to obtain the latest specifications and before placing your product order. Copies of documents which have an order number and are referenced in this document, or other Intel literature, may be obtained by calling 1-800-548-4725, or go to: http://www.intel.com/design/literature.htm Intel, the Intel logo, Intel Xeon, Xeon logo, and the Look Inside. logo are trademarks of Intel Corporation in the U.S. and/or other countries. *Other names and brands may be claimed as the property of others. Copyright © 2017 Intel Corporation. All rights reserved.
Slide 37

#RSAC Legal Disclaimers - Continued • Intel processor numbers are not a measure of performance. Processor numbers differentiate features within each processor family, not across different processor families: Go to: Learn About Intel® Processor Numbers http://www.intel.com/products/processor_number • Some results have been estimated based on internal Intel analysis and are provided for informational purposes only. Any difference in system hardware or software design or configuration may affect actual performance. • Software and workloads used in performance tests may have been optimized for performance only on Intel microprocessors. Performance tests, such as SYSmark and MobileMark, are measured using specific computer systems, components, software, operations and functions. Any change to any of those factors may cause the results to vary. You should consult other information and performance tests to assist you in fully evaluating your contemplated purchases, including the performance of that product when combined with other products. • Intel does not control or audit the design or implementation of third party benchmarks or Web sites referenced in this document. Intel encourages all of its customers to visit the referenced Web sites or others where similar performance benchmarks are reported and confirm whether the referenced benchmarks are accurate and reflect performance of systems available for purchase. • Relative performance is calculated by assigning a baseline value of 1.0 to one benchmark result, and then dividing the actual benchmark result for the baseline platform into each of the specific benchmark results of each of the other platforms, and assigning them a relative performance number that correlates with the performance improvements reported. SPEC, SPECint, SPECfp, SPECrate, SPECpower, SPECjbb, SPECompG, SPEC MPI, and SPECjEnterprise* are trademarks of the Standard Performance Evaluation Corporation. See http://www.spec.org for more information. TPC Benchmark, TPC-C, TPC-H, and TPC-E are trademarks of the Transaction Processing Council. See http://www.tpc.org for more information. Intel® Advanced Vector Extensions (Intel® AVX)* are designed to achieve higher throughput to certain integer and floating point operations. Due to varying processor power characteristics, utilizing AVX instructions may cause a) some parts to operate at less than the rated frequency and b) some parts with Intel® Turbo Boost Technology 2.0 to not achieve any or maximum turbo frequencies. Performance varies depending on hardware, software, and system configuration and you should consult your system manufacturer for more information. No computer system can provide absolute security. Requires an enabled Intel® processor, enabled chipset, firmware and/or software optimized to use the technologies. Consult your system manufacturer and/or software vendor for more information • • • • *Intel® Advanced Vector Extensions refers to Intel® AVX, Intel® AVX2 or Intel® AVX-512. For more information on Intel® Turbo Boost Technology 2.0, visit http://www.intel.com/go/turbo