Slide 1

Slide 2
WHY ARE WE LOSING THE INFOSEC BATTLE? how do we get back into the race? 2 Steve Orrin | Shawn Wells
Slide 3
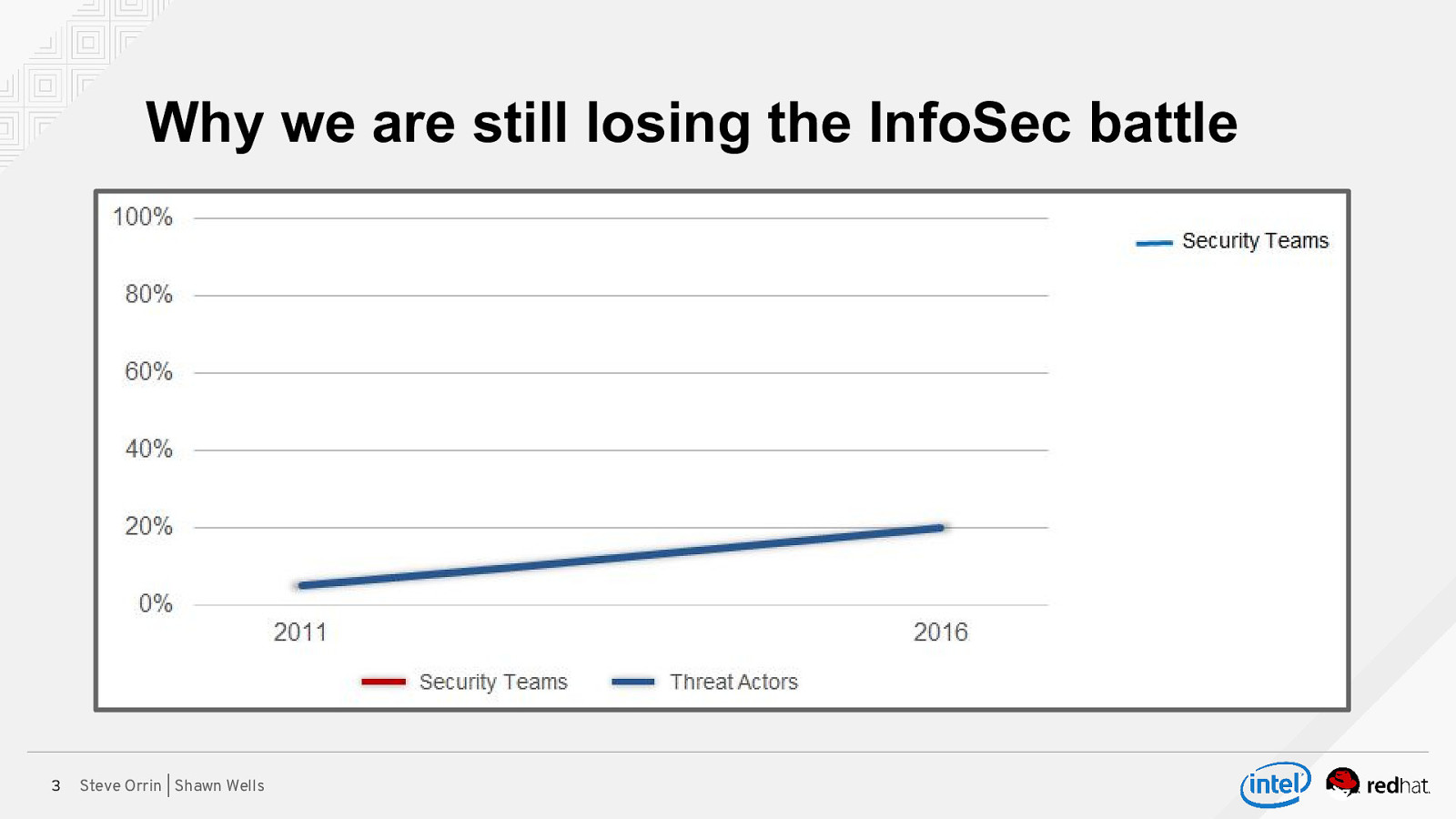
Why we are still losing the InfoSec battle 3 Steve Orrin | Shawn Wells
Slide 4
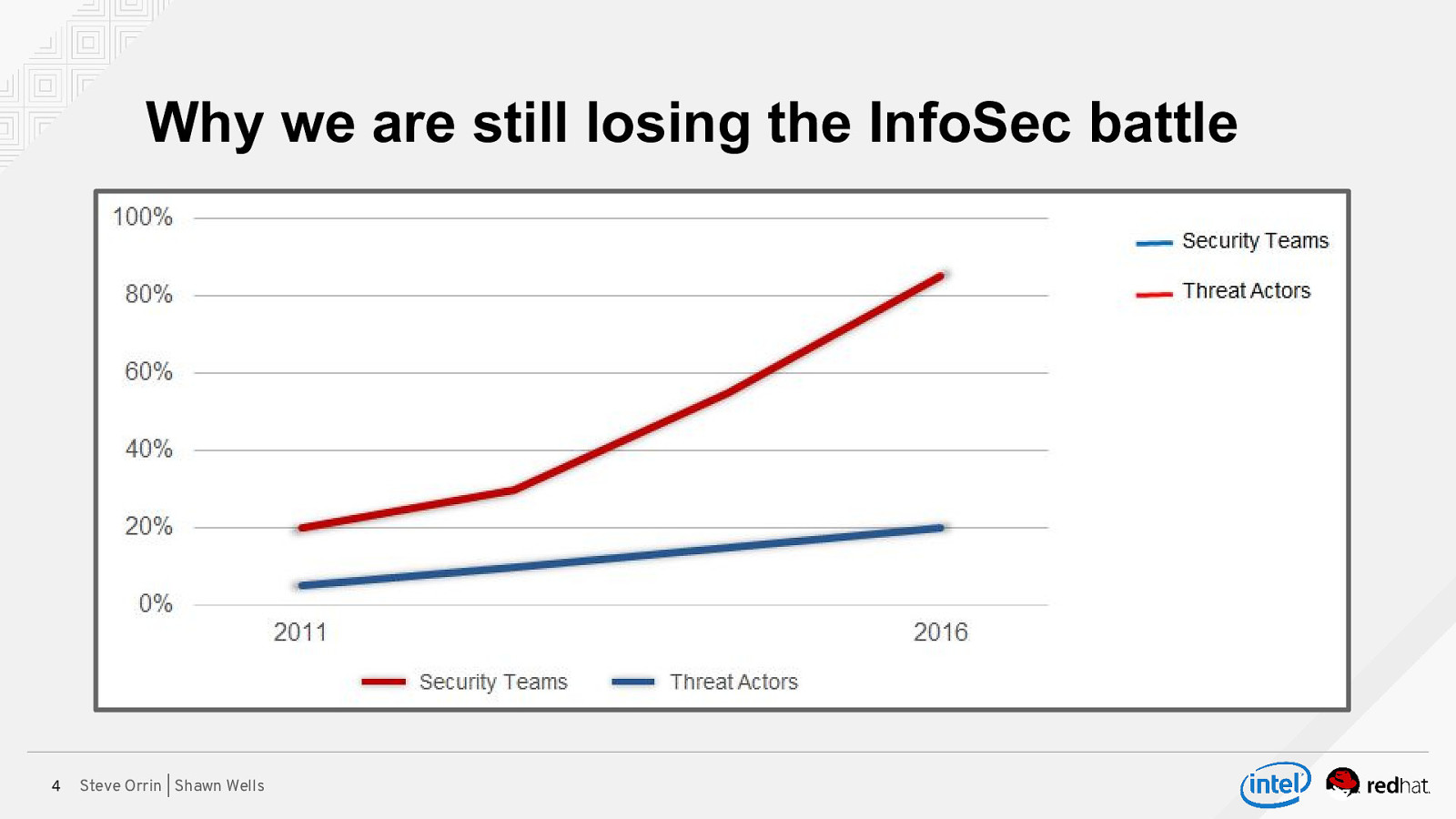
Why we are still losing the InfoSec battle 4 Steve Orrin | Shawn Wells
Slide 5
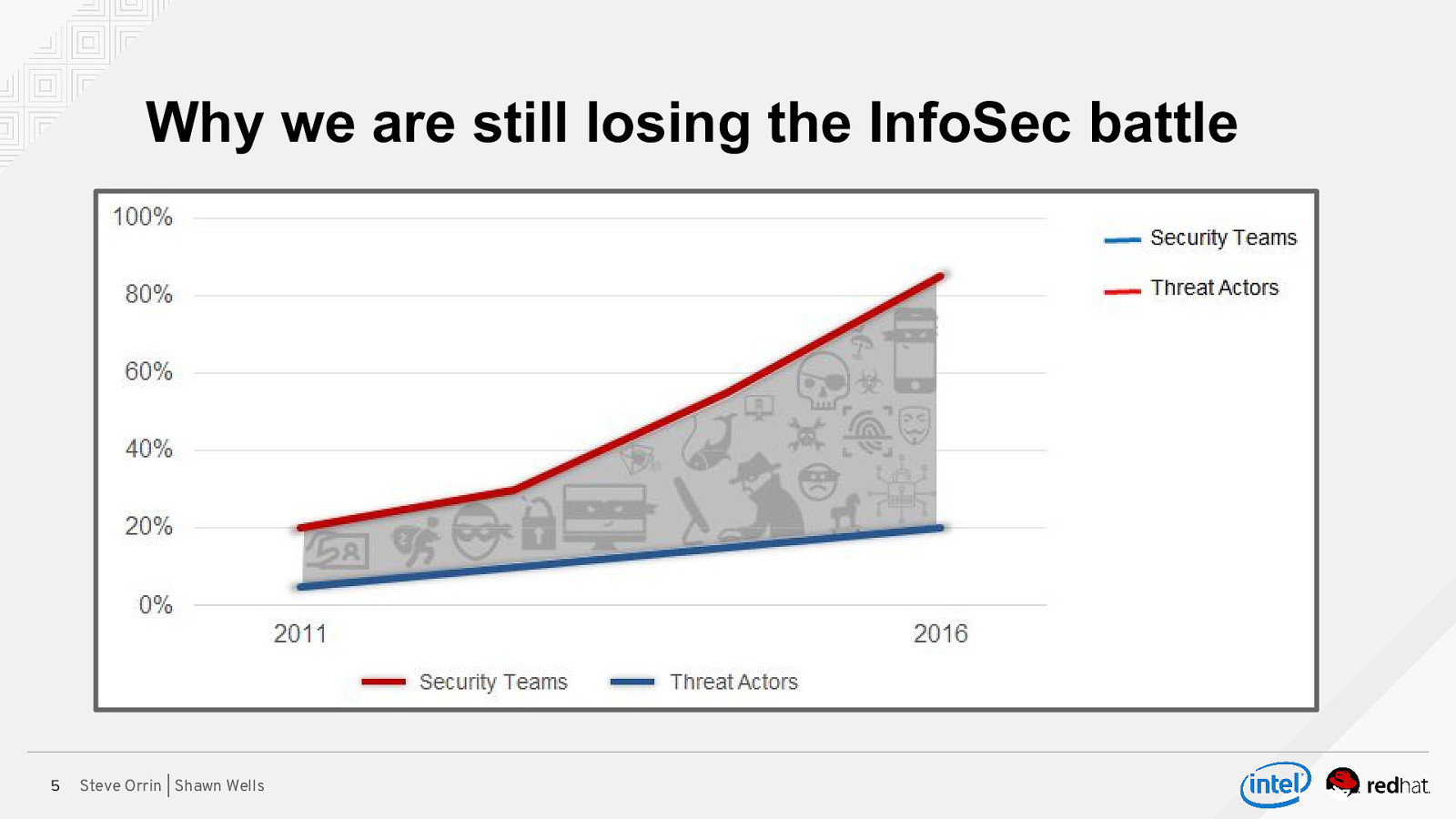
Why we are still losing the InfoSec battle 5 Steve Orrin | Shawn Wells
Slide 6
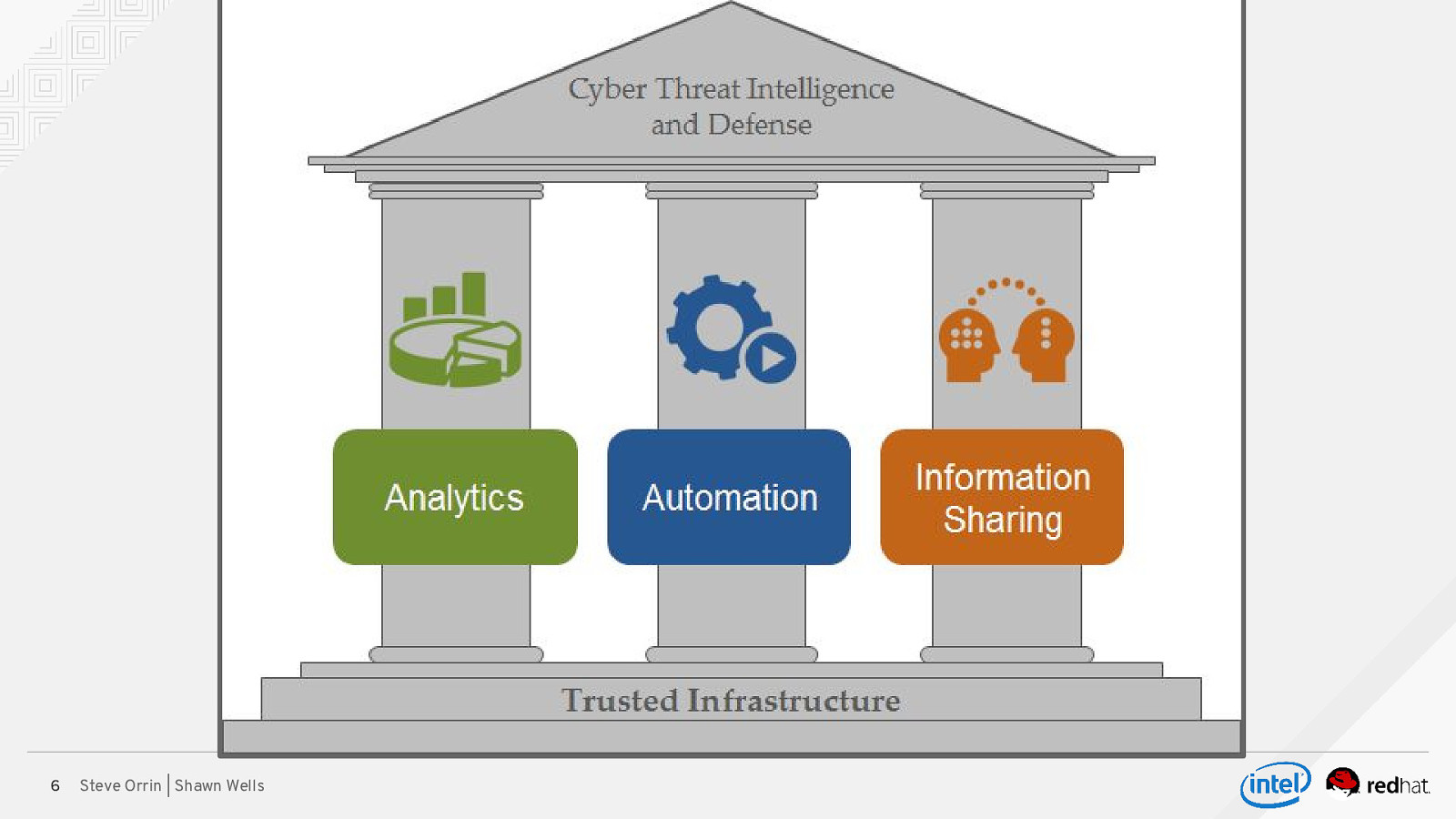
6 Steve Orrin | Shawn Wells
Slide 7
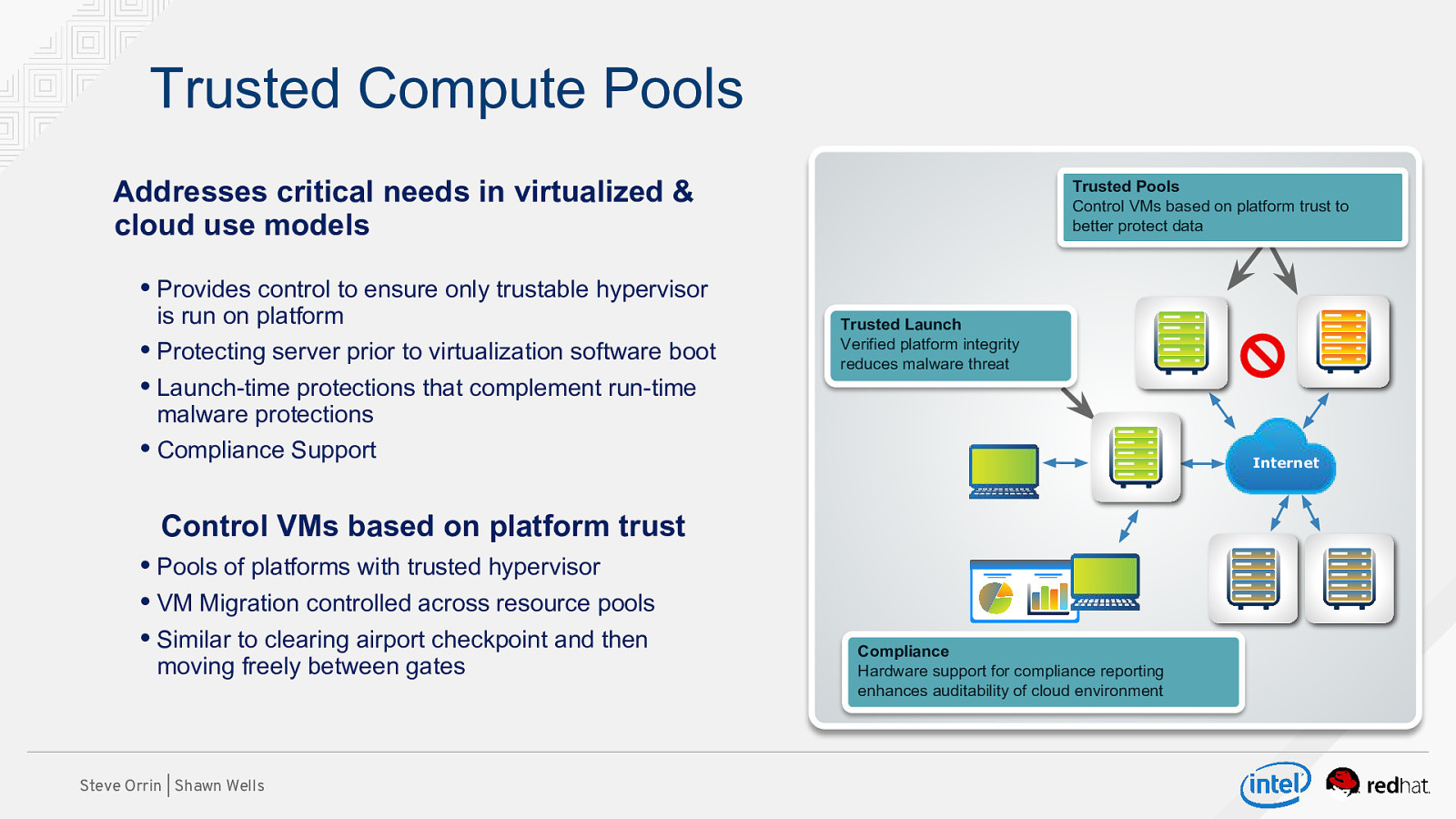
Trusted Compute Pools Addresses critical needs in virtualized & cloud use models Trusted Pools Control VMs based on platform trust to better protect data • Provides control to ensure only trustable hypervisor is run on platform • Protecting server prior to virtualization software boot Trusted Launch Verified platform integrity reduces malware threat • Launch-time protections that complement run-time malware protections • Compliance Support Internet Control VMs based on platform trust • Pools of platforms with trusted hypervisor • VM Migration controlled across resource pools • Similar to clearing airport checkpoint and then moving freely between gates Steve Orrin | Shawn Wells Compliance Hardware support for compliance reporting enhances auditability of cloud environment
Slide 8
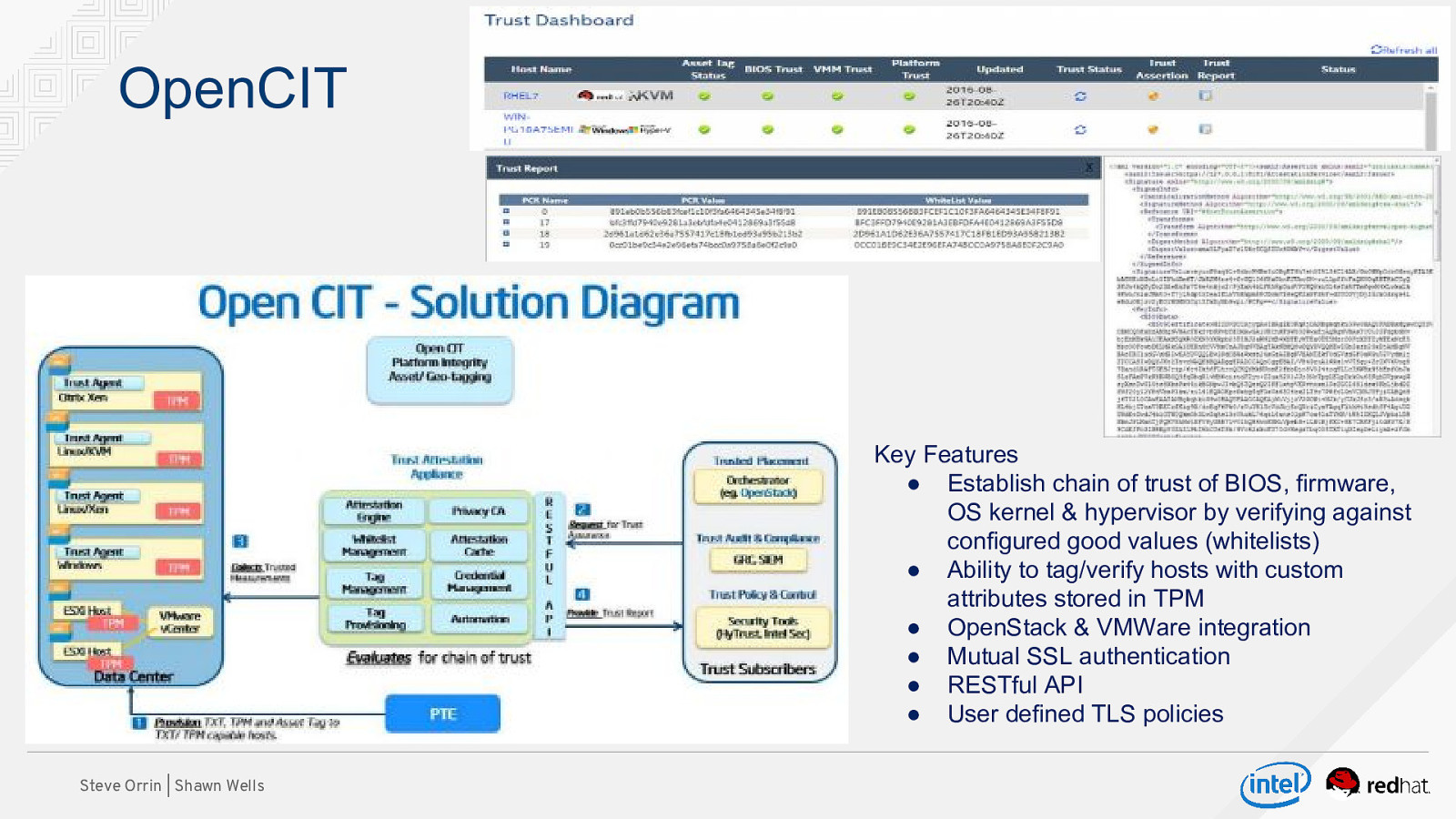
OpenCIT Key Features ● Establish chain of trust of BIOS, firmware, OS kernel & hypervisor by verifying against configured good values (whitelists) ● Ability to tag/verify hosts with custom attributes stored in TPM ● OpenStack & VMWare integration ● Mutual SSL authentication ● RESTful API ● User defined TLS policies Steve Orrin | Shawn Wells
Slide 9
Trusted Infrastructure NIST IR-7904 Reference Architecture ● Joint Collaboration between NIST, Intel Corporation, and Software Vendors to demonstrate the ability to control and audit workload and data provisioning based on system trust and geo-location http://nvlpubs.nist.gov/nistpubs/ir/2015/NIST.IR.7904.pdf 9 Steve Orrin | Shawn Wells
Slide 10
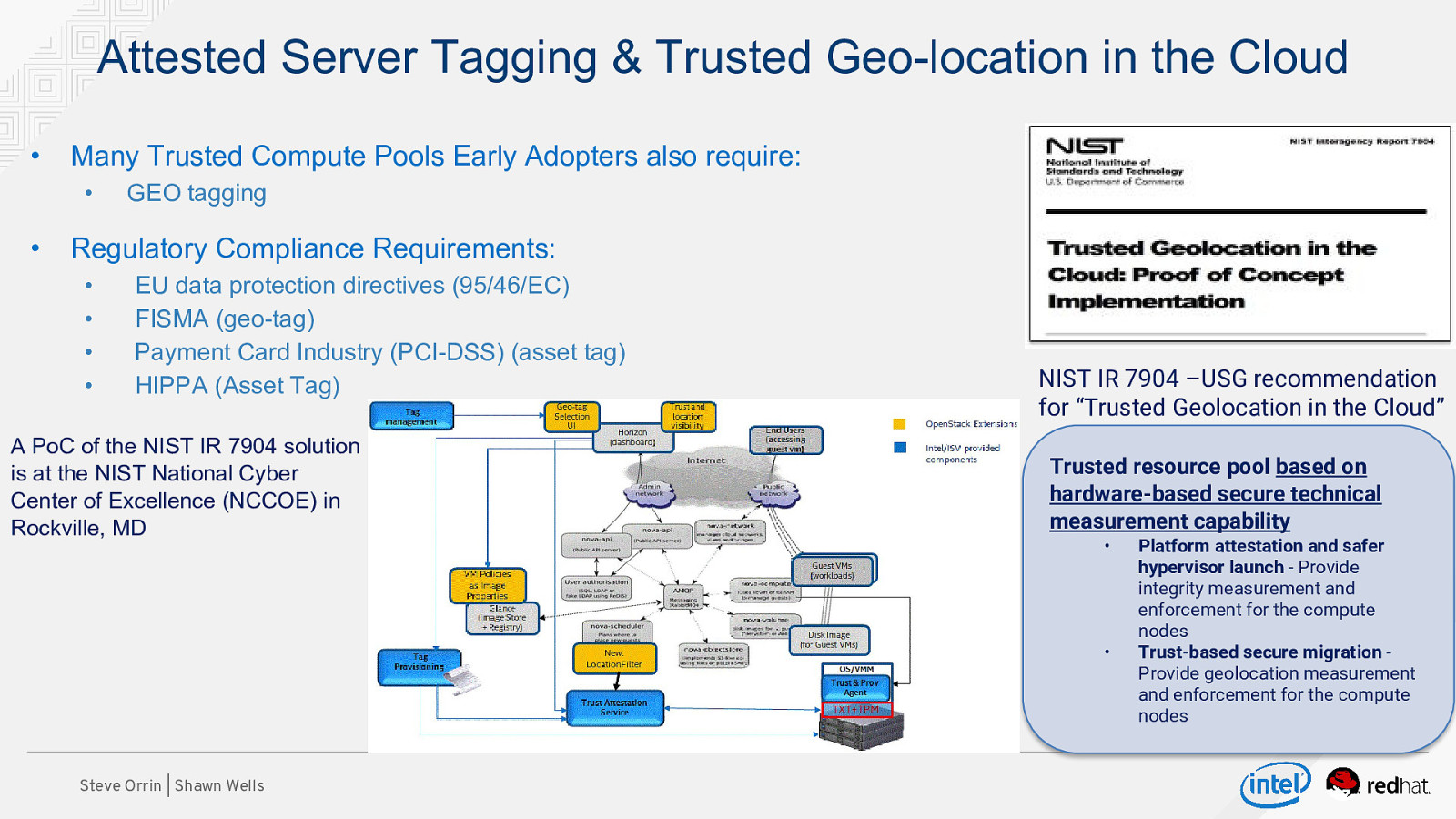
Attested Server Tagging & Trusted Geo-location in the Cloud • Many Trusted Compute Pools Early Adopters also require: • • GEO tagging Regulatory Compliance Requirements: • • • • EU data protection directives (95/46/EC) FISMA (geo-tag) Payment Card Industry (PCI-DSS) (asset tag) HIPPA (Asset Tag) A PoC of the NIST IR 7904 solution is at the NIST National Cyber Center of Excellence (NCCOE) in Rockville, MD NIST IR 7904 –USG recommendation for “Trusted Geolocation in the Cloud” Trusted resource pool based on hardware-based secure technical measurement capability • • Steve Orrin | Shawn Wells Platform attestation and safer hypervisor launch - Provide integrity measurement and enforcement for the compute nodes Trust-based secure migration Provide geolocation measurement and enforcement for the compute nodes
Slide 11
Steve Orrin | Shawn Wells
Slide 12
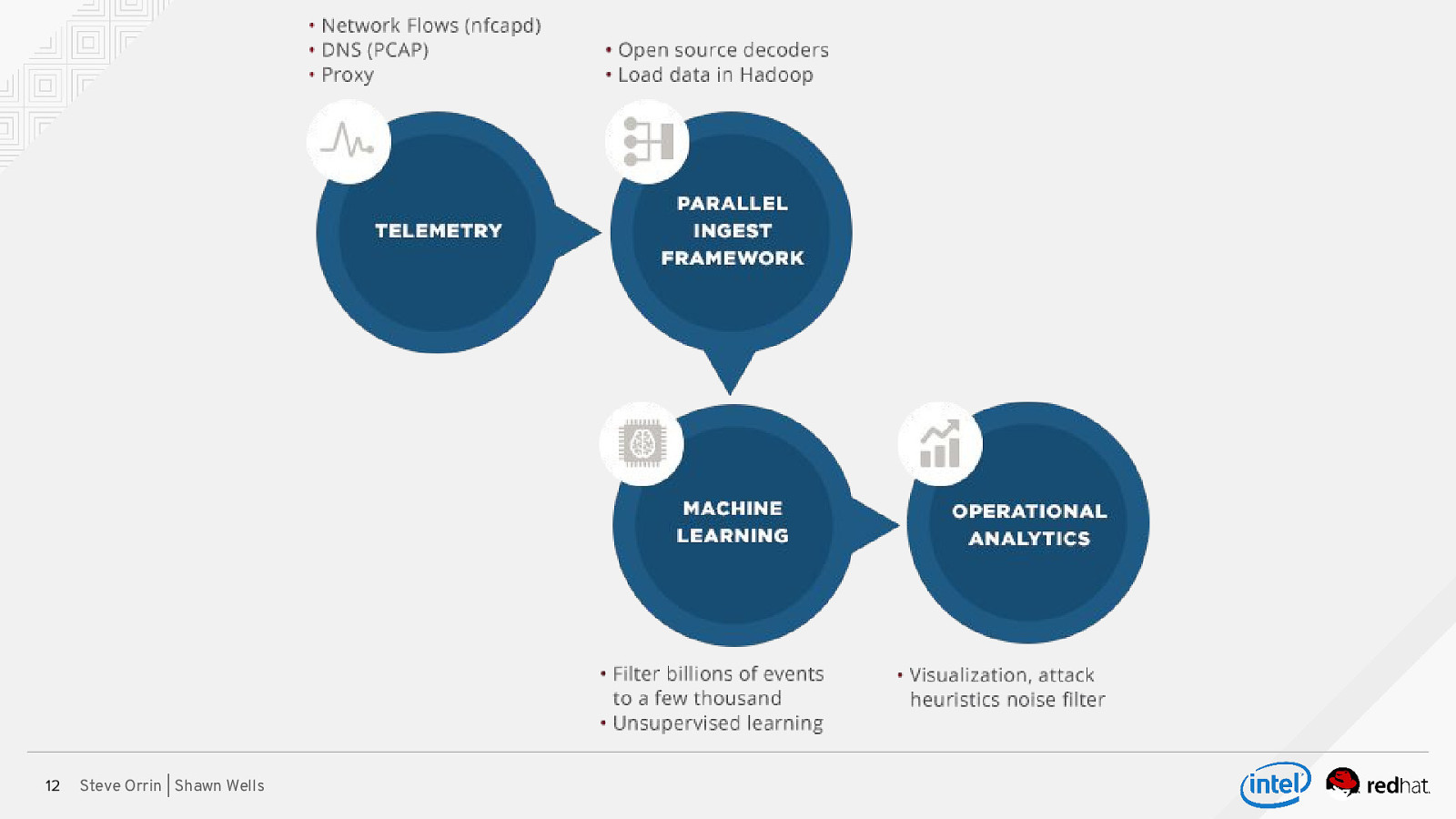
12 Steve Orrin | Shawn Wells
Slide 13
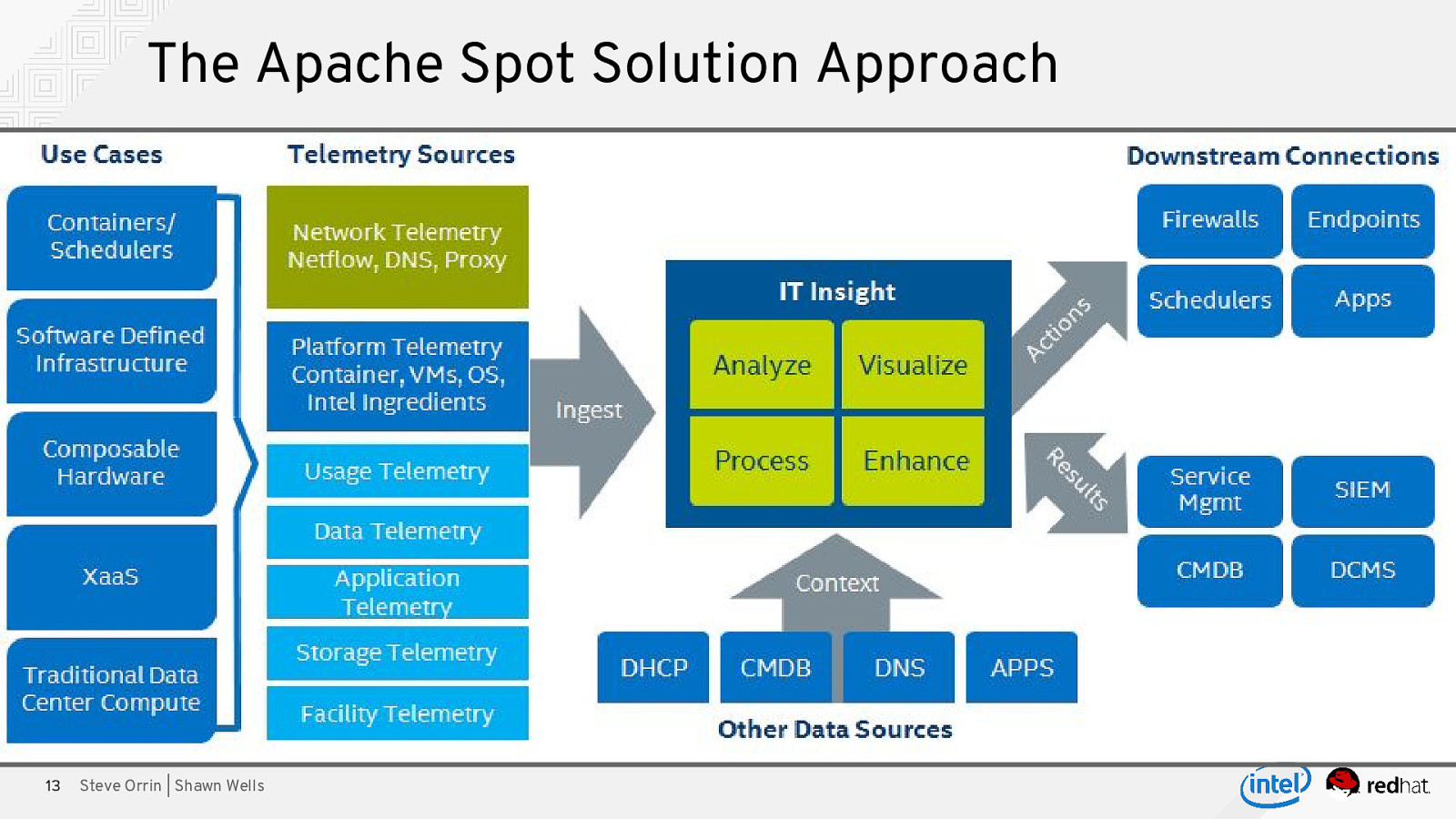
The Apache Spot Solution Approach 13 Steve Orrin | Shawn Wells
Slide 14
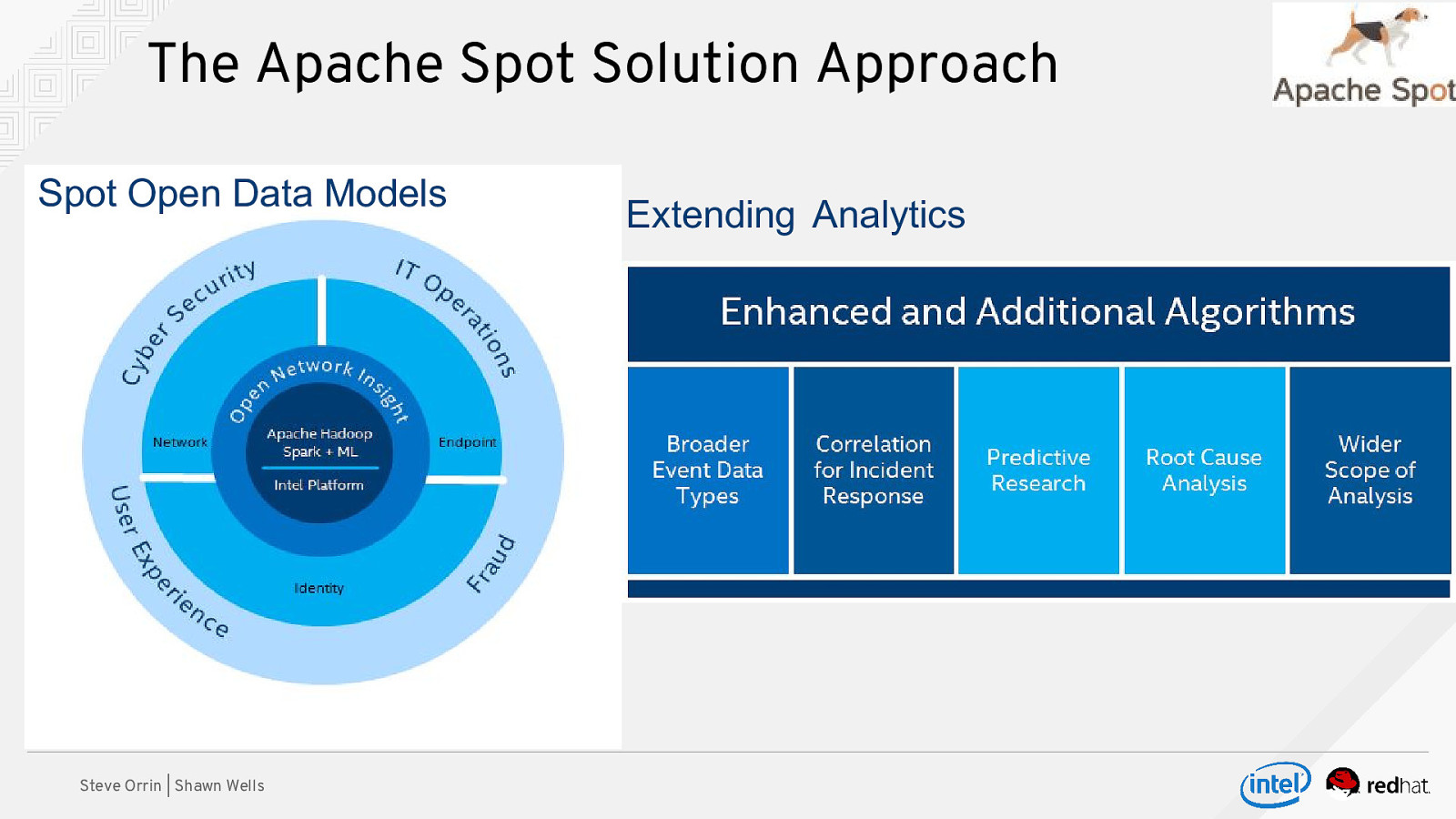
The Apache Spot Solution Approach Spot Open Data Models Steve Orrin | Shawn Wells Extending Analytics
Slide 15
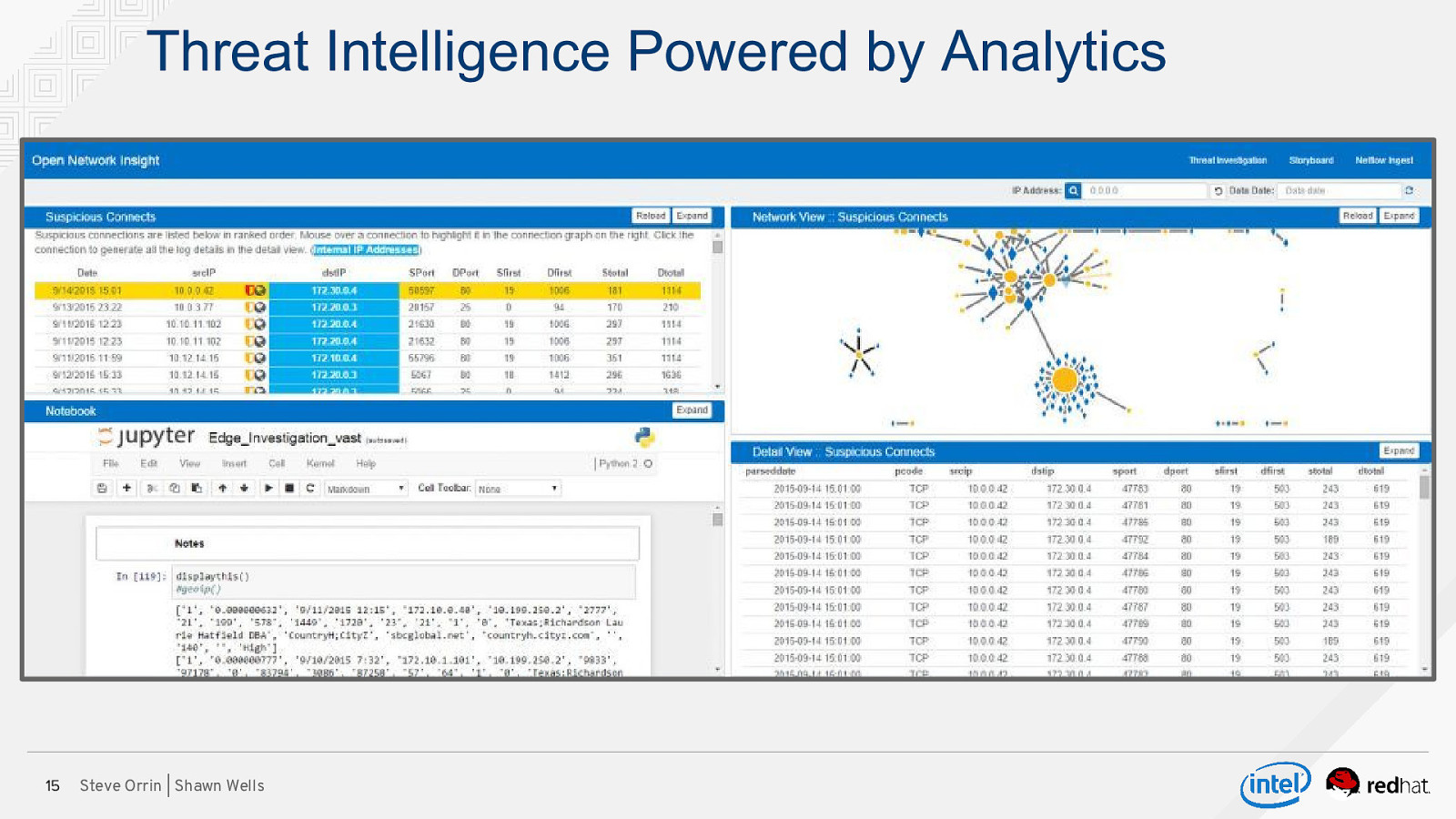
Threat Intelligence Powered by Analytics 15 Steve Orrin | Shawn Wells
Slide 16

Automation and Information Sharing Enhances Security ● ● ● 16 Capabilities ○ Automated provisioning of patches & updates ○ Automated system/node refresh ○ Dynamic Security controls ○ SW defined Network and Host Security services ○ Automated Workload configuration for Security Baselines ○ Automated Compliance Benefits ○ Real time threat response and mitigation (get the human out of the loop) ○ Reduce window of exposure ○ Reduce risk during active attacks and campaigns Information Sharing - Beyond IoC’s! ○ Sharing Automation scripts, techniques, and best known practices must be a key part of the Information Sharing Steve Orrin | Shawn Wells
Slide 17
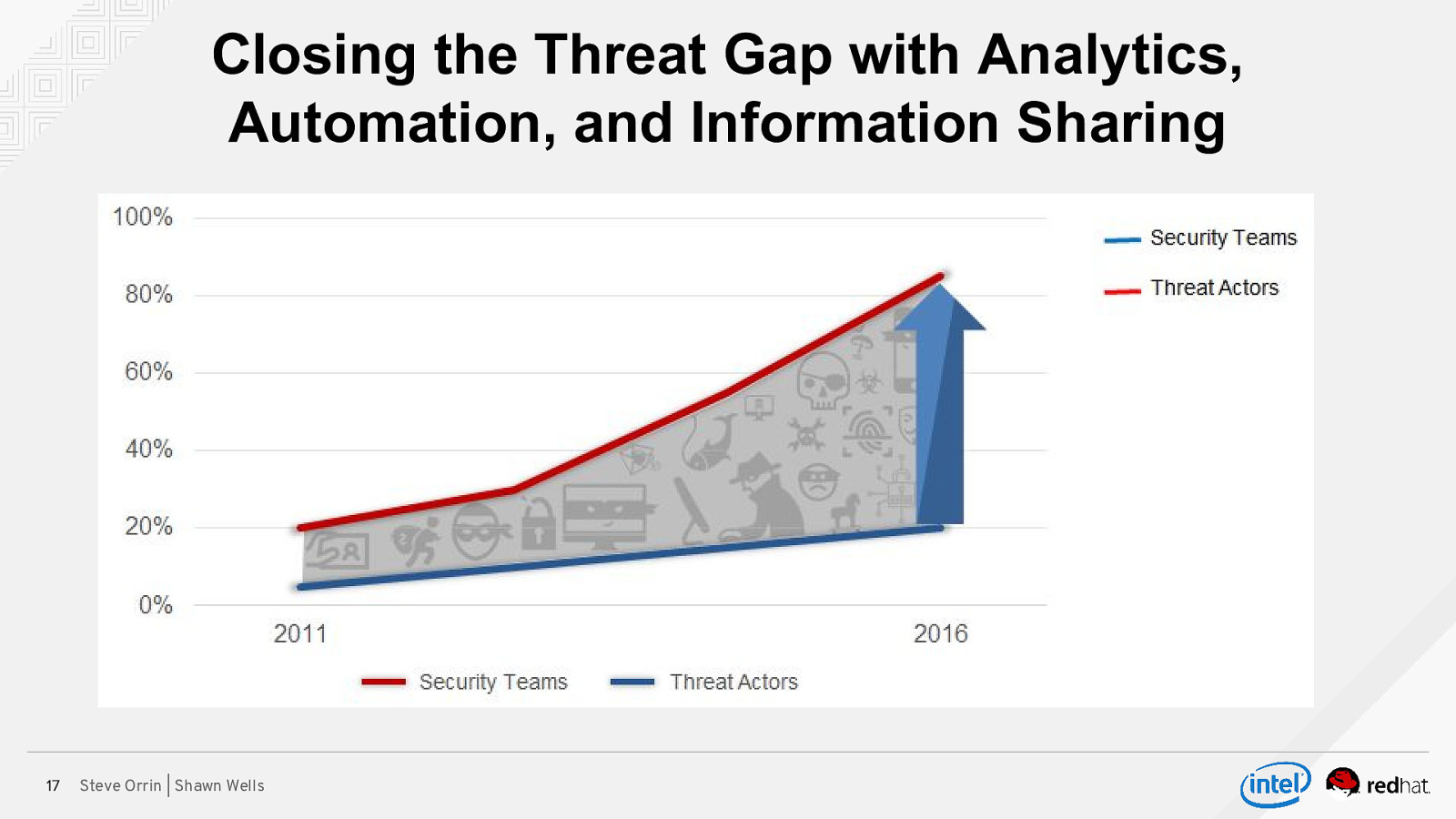
Closing the Threat Gap with Analytics, Automation, and Information Sharing 17 Steve Orrin | Shawn Wells
Slide 18

18 Steve Orrin | Shawn Wells
Slide 19

19 Steve Orrin | Shawn Wells
Slide 20

● 100% free, legal, redistributable ● Software. Artwork. Project Code. EVERYTHING. ● Never cutting corners. 20 Steve Orrin | Shawn Wells
Slide 21

● Everyone has something to give. ● Thousands of active contributors. ● Disagreement, then discussion, then consensus. 21 Steve Orrin | Shawn Wells
Slide 22

● Technical excellence. ● Upstream collaboration. ● Our features become part of others. 22 Steve Orrin | Shawn Wells
Slide 23

● Innovation. ● We don’t wait for others to do the heavy lifting. ● Rapid release cycle. ● Community R&D lab. 23 Steve Orrin | Shawn Wells
Slide 24

24 Steve Orrin | Shawn Wells
Slide 25

Fedora Red Team ● Offensive tooling ● Exploit Curation ● Offensive Standards ● Offensive Reference Architectures 25 Steve Orrin | Shawn Wells https://fedoraproject.org/wiki/SIGs/Red_Team
Slide 26
Fedora Blue Team ● Defensive tooling ● Active Cyber Defense platforms ● Reference architectures https://tbd 26 Steve Orrin | Shawn Wells
Slide 27

27 Steve Orrin | Shawn Wells
Slide 28
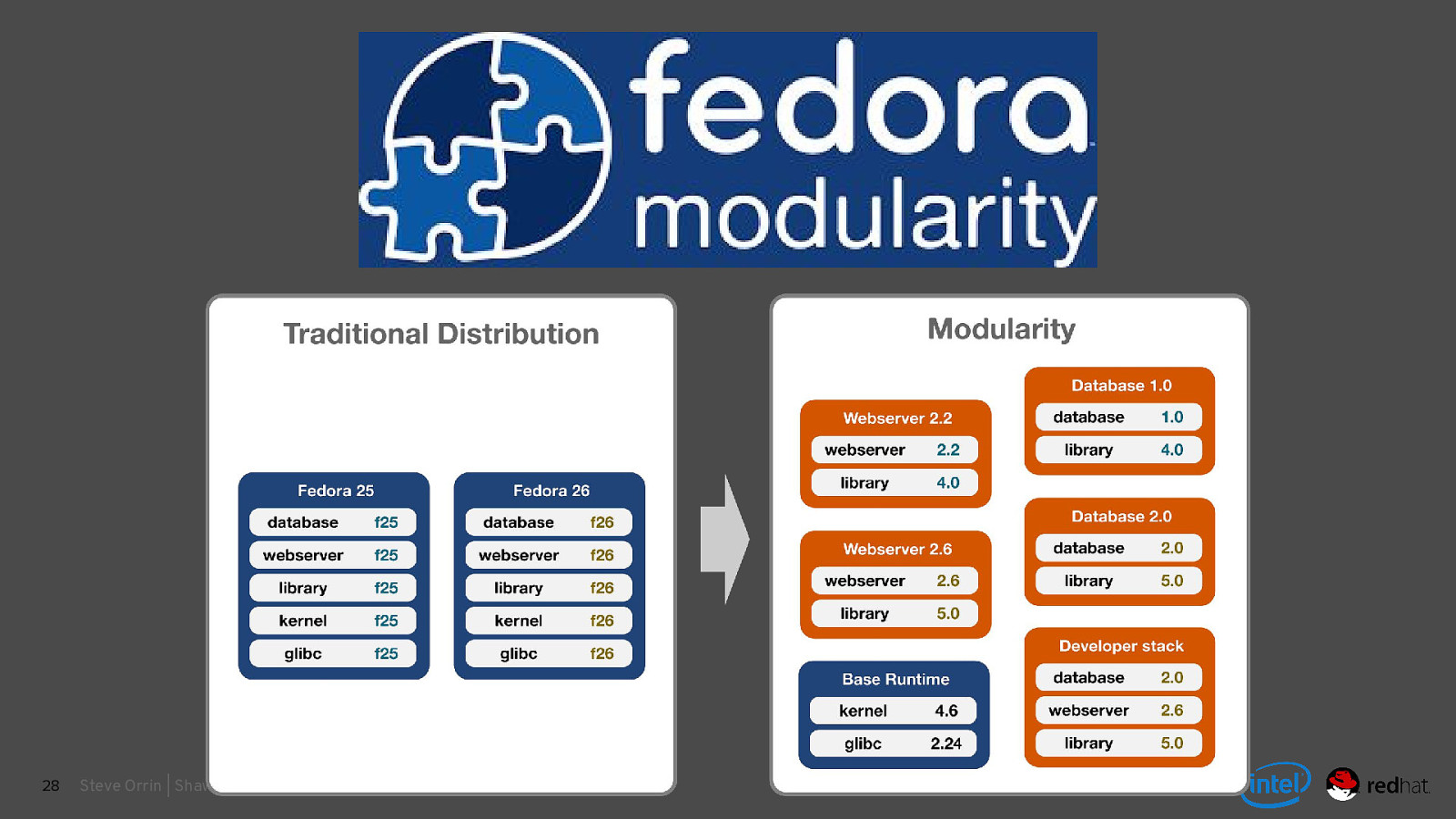
28 Steve Orrin | Shawn Wells
Slide 29

Thank you! ADD NAME (View > Master > Slide master)