Partner Security Update Shawn Wells Chief Security Strategist 18-AUG-2016
Slide 1

Slide 2

45 MINUTES, 3 GOALS (+15 MIN Q&A) 1. Share Security Initiatives • • • • Common Criteria FIPS 140-2 Configuration Baselines – DoD STIG, NIST USGCB Tooling Certifications (OpenSCAP) 2. Live Demo • DoD STIG Configuration Compliance Scanning • Patch & Vulnerability Scanning • Certification/Accreditation Paperwork Generation
Slide 3
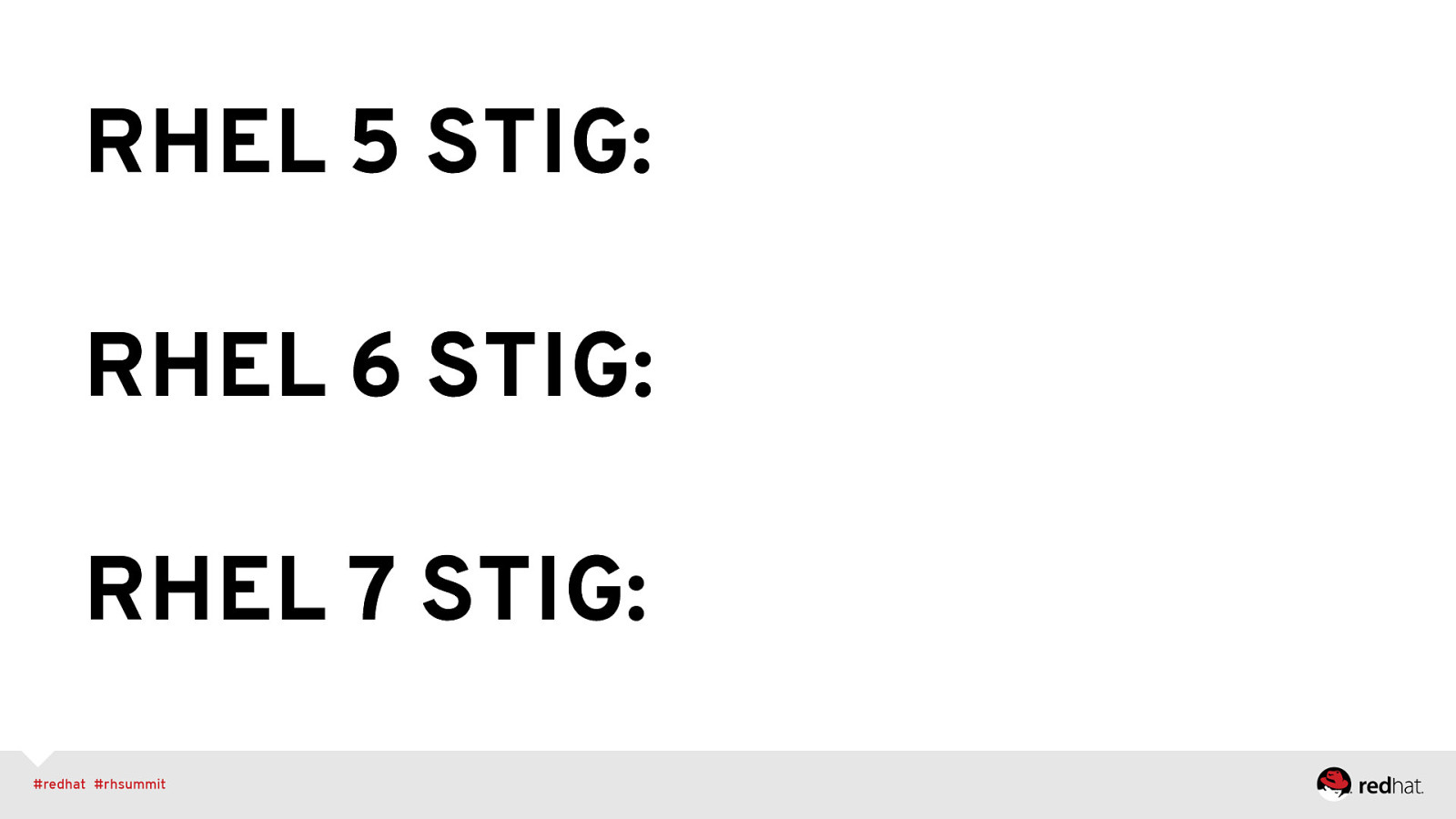
RHEL 5 STIG: RHEL 6 STIG: RHEL 7 STIG:
Slide 4
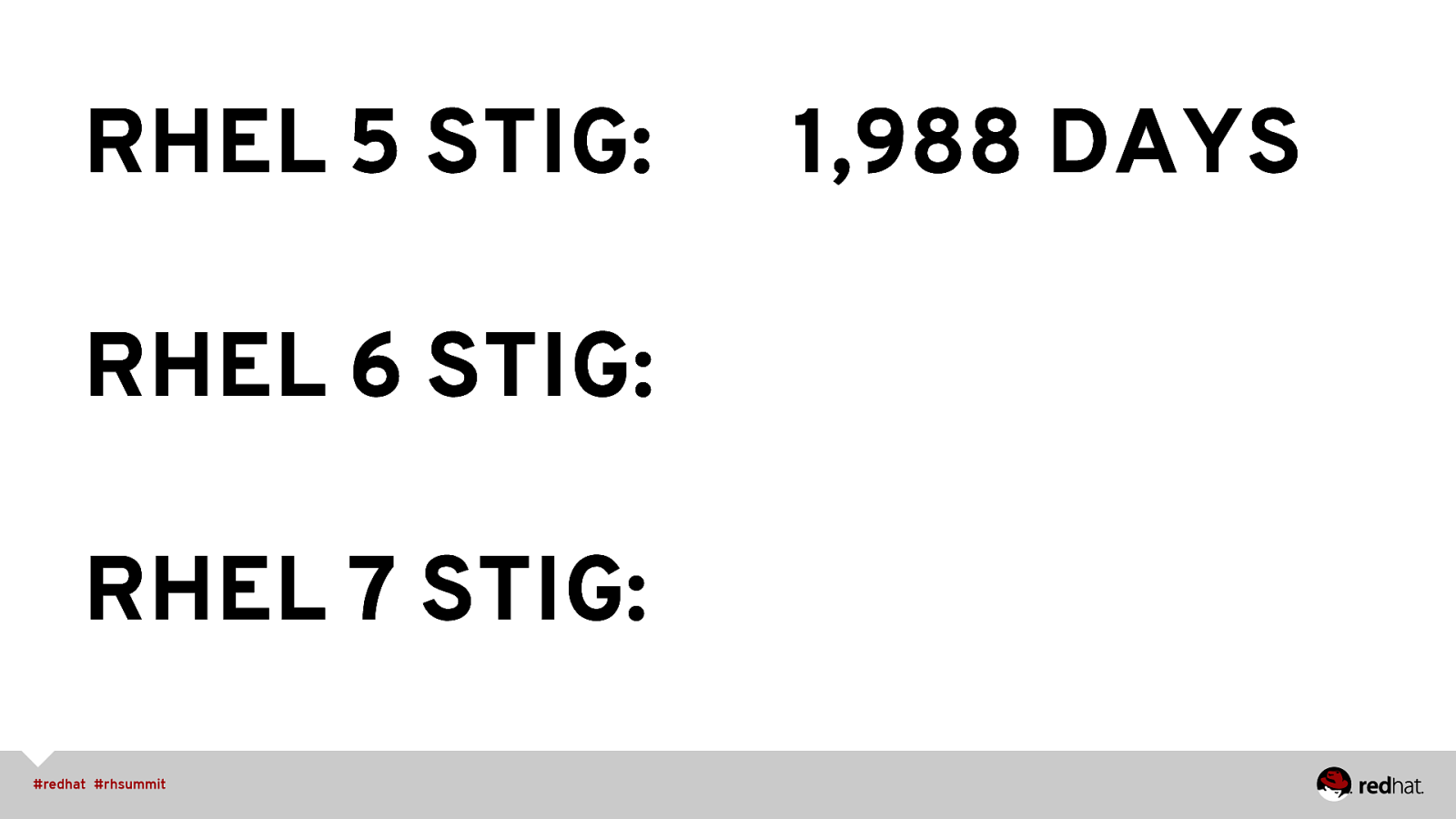
RHEL 5 STIG: RHEL 6 STIG: RHEL 7 STIG: 1,988 DAYS
Slide 5

RHEL 5 STIG: 1,988 DAYS RHEL 6 STIG: 932 DAYS RHEL 7 STIG:
Slide 6
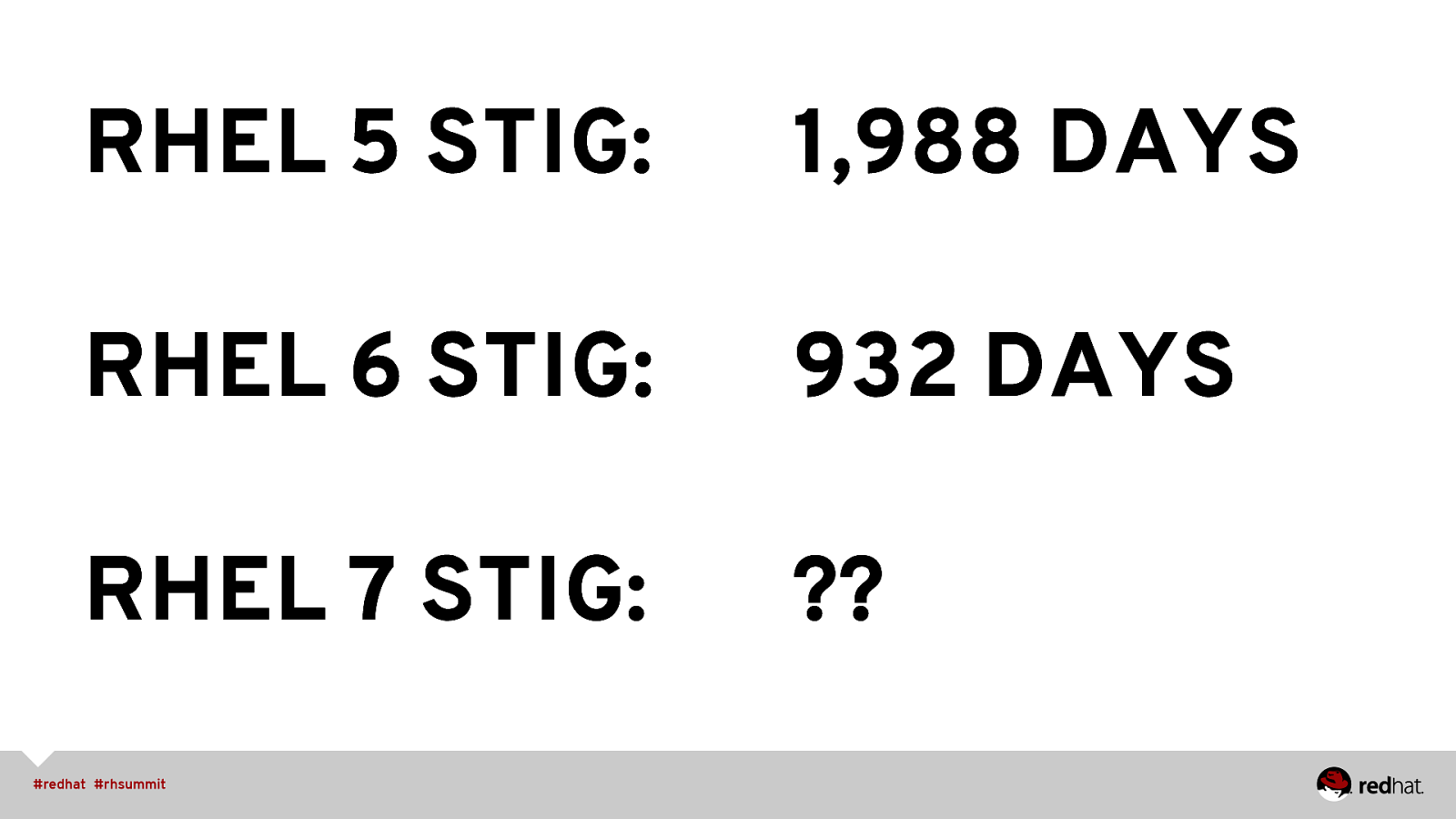
RHEL 5 STIG: 1,988 DAYS RHEL 6 STIG: 932 DAYS RHEL 7 STIG: ??
Slide 7
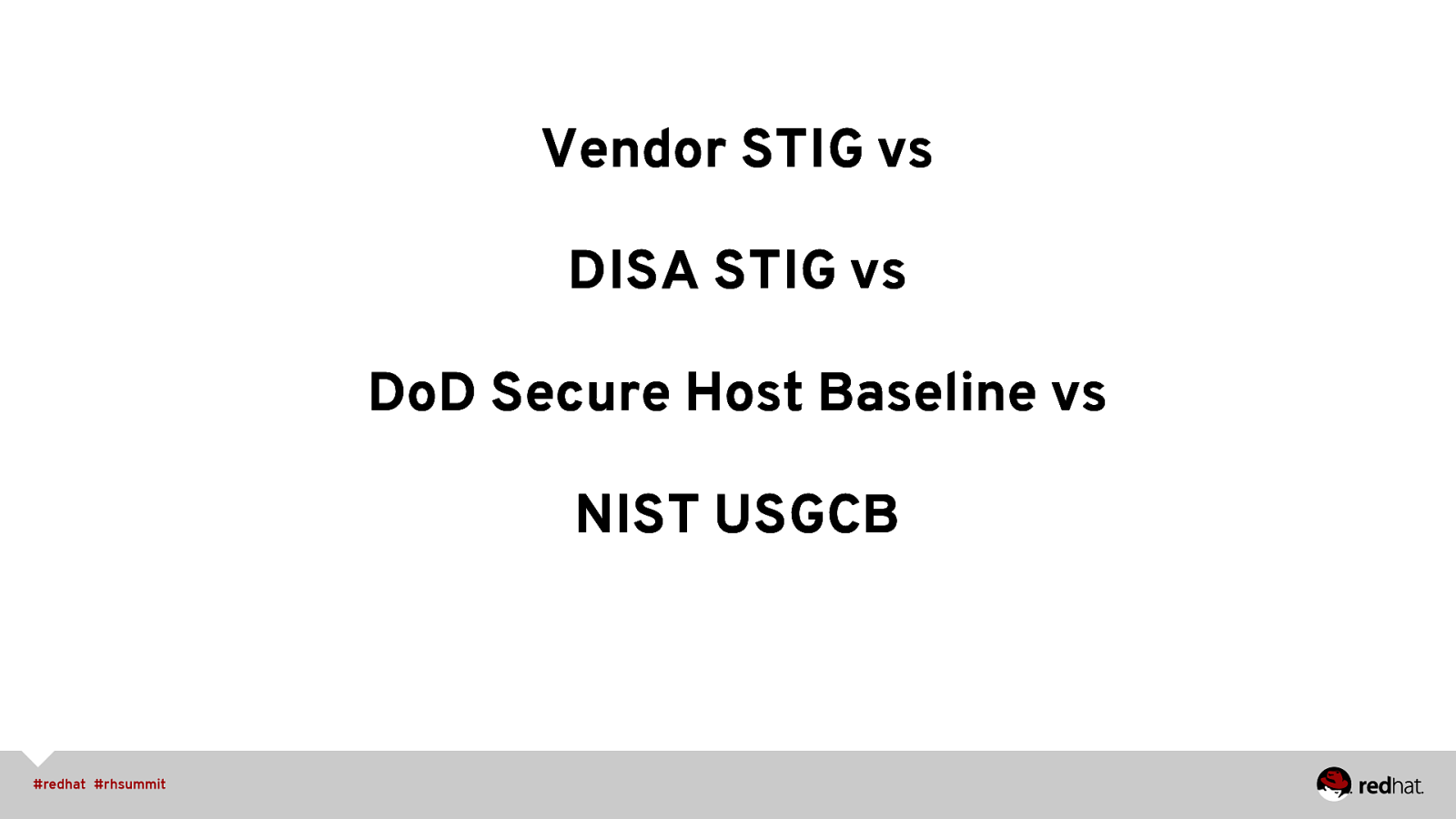
Vendor STIG vs DISA STIG vs DoD Secure Host Baseline vs NIST USGCB
Slide 8
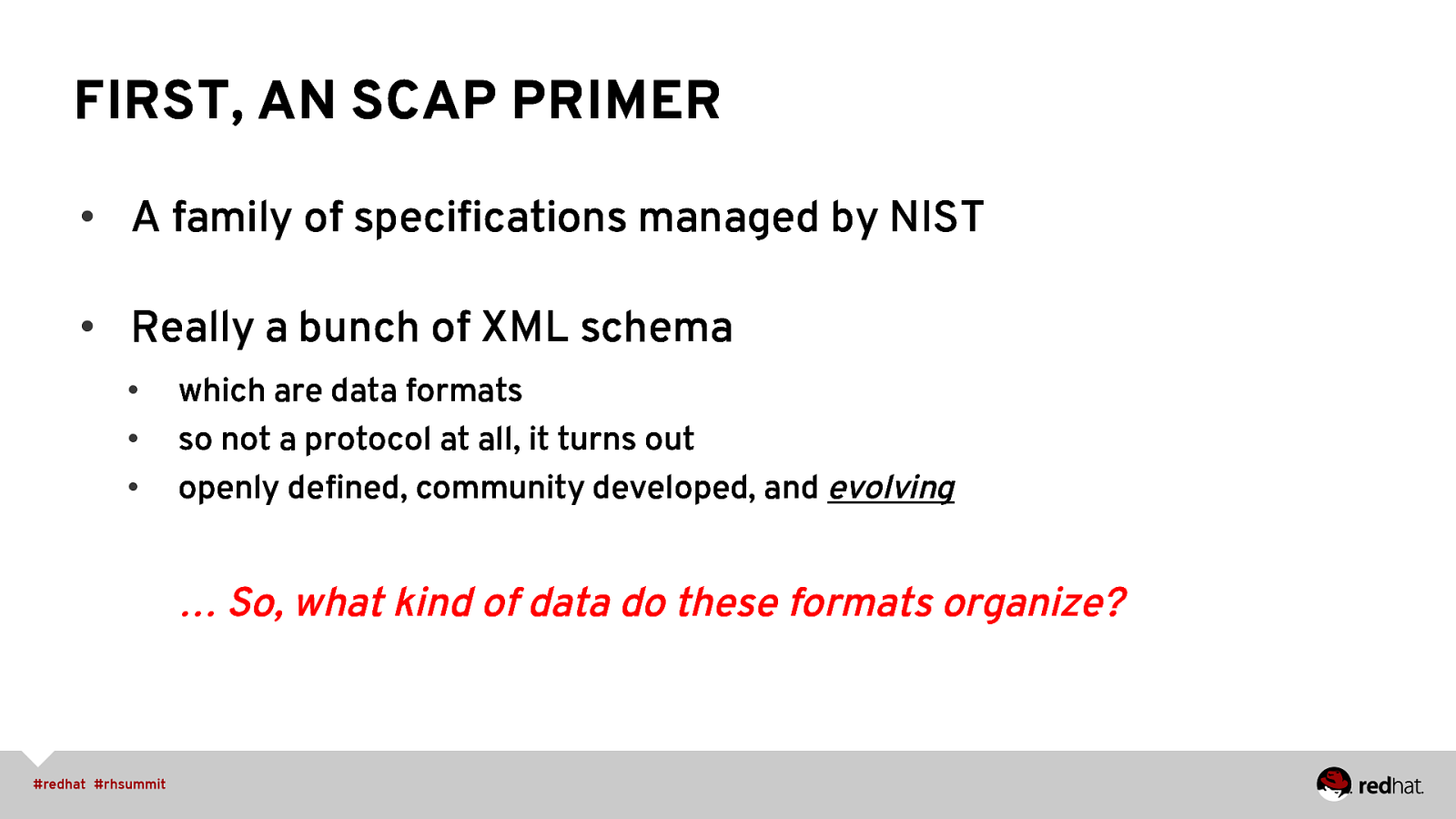
FIRST, AN SCAP PRIMER • A family of specifications managed by NIST • Really a bunch of XML schema • • • which are data formats so not a protocol at all, it turns out openly defined, community developed, and evolving … So, what kind of data do these formats organize?
Slide 9

FIRST, AN SCAP PRIMER • Defines standardized formats … okay, but why bother? • Because you’ll get: • • Standardized inputs (e.g. a compliance baseline, status query) Standardized outputs (results) • Provides the enterprise liberty with regard to product choices • • • Avoids vendor lock-in, enables interoperability Provides common technical position to vendors Federal procurement language requires SCAP support in some cases
Slide 10

SCAP Security Guide https://fedorahosted.org/scap-security-guide/
Slide 11

Contributors Include…
Slide 12

DISA STIG, Version 1, Release 2, Section 1.1: “The consensus content was developed using an open source project called SCAP Security Guide. The project’s website is https://fedorahosted.org/scap-security-guide/. Except for differences in formatting to accommodate the DISA STIG publishing process, the content of the RHEL6 STIG should mirror the SCAP Security Guide content with only minor divergences as updates from multiple sources work through the consensus process”
Slide 13
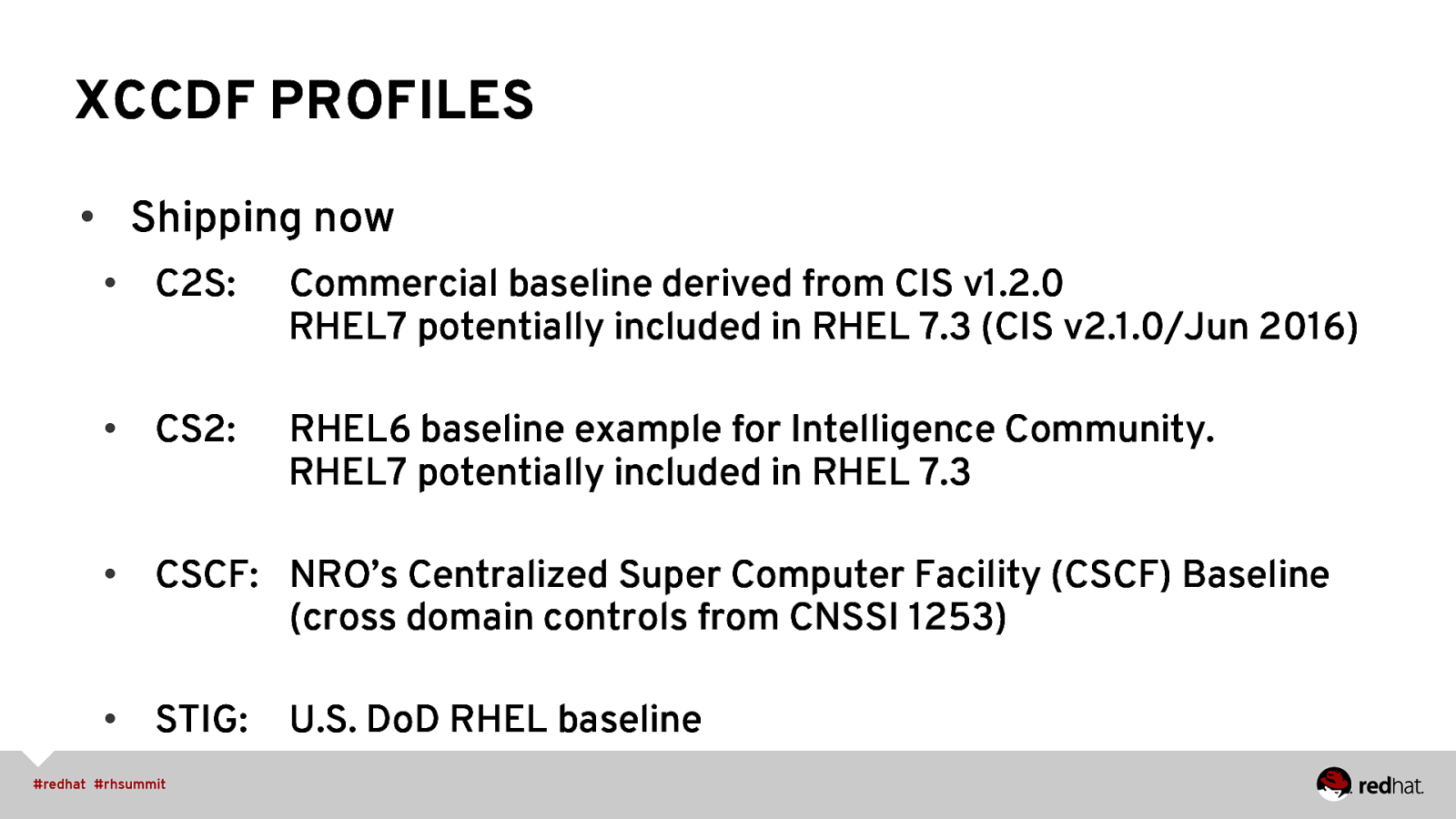
XCCDF PROFILES • Shipping now • C2S: Commercial baseline derived from CIS v1.2.0 RHEL7 potentially included in RHEL 7.3 (CIS v2.1.0/Jun 2016) • CS2: RHEL6 baseline example for Intelligence Community. RHEL7 potentially included in RHEL 7.3 • CSCF: NRO’s Centralized Super Computer Facility (CSCF) Baseline (cross domain controls from CNSSI 1253) • STIG: U.S. DoD RHEL baseline
Slide 14

REMEDIATION CAPABILITIES • Bash first <fix system=”urn:xccdf:fix:script:sh”> yum -y install screen </fix>
Slide 15
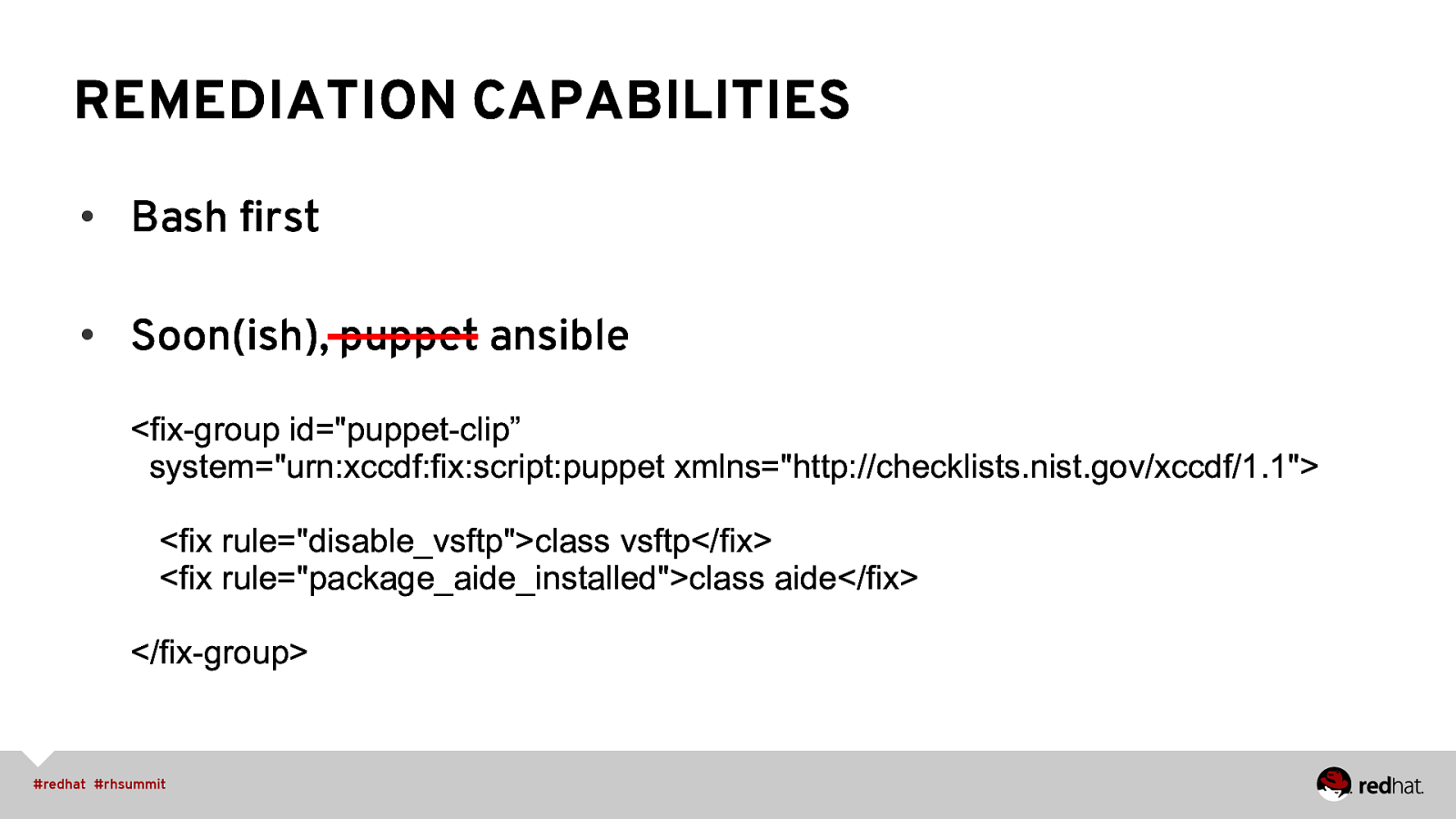
REMEDIATION CAPABILITIES • Bash first • Soon(ish), puppet ansible <fix-group id=”puppet-clip” system=”urn:xccdf:fix:script:puppet xmlns=”http://checklists.nist.gov/xccdf/1.1”> <fix rule=”disable_vsftp”>class vsftp</fix> <fix rule=”package_aide_installed”>class aide</fix> </fix-group>
Slide 16
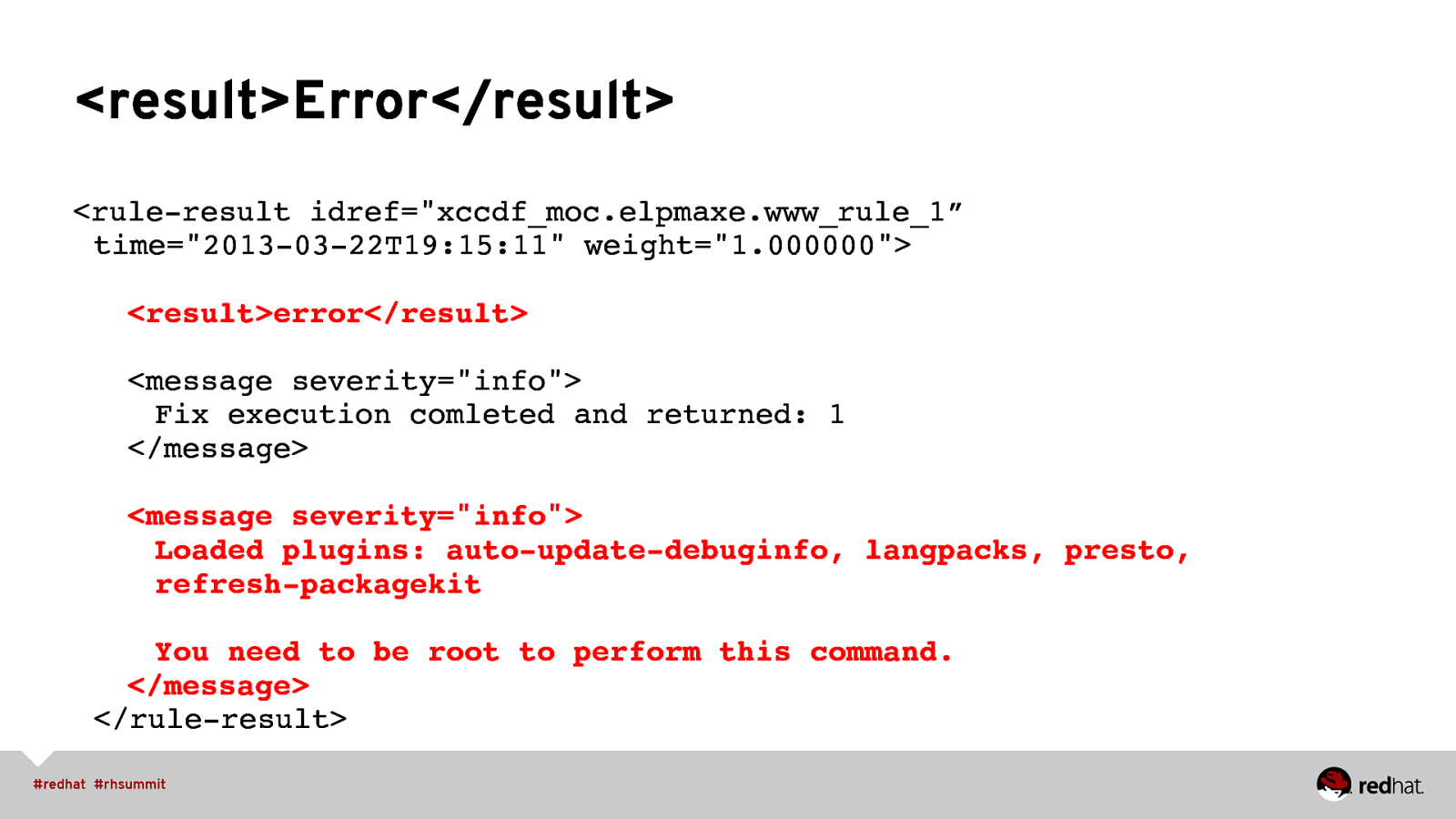
<result>Error</result> <rule-result idref=”xccdf_moc.elpmaxe.www_rule_1” time=”2013-03-22T19:15:11” weight=”1.000000”> <result>error</result> <message severity=”info”> Fix execution comleted and returned: 1 </message> <message severity=”info”> Loaded plugins: auto-update-debuginfo, langpacks, presto, refresh-packagekit You need to be root to perform this command. </message> </rule-result>
Slide 17
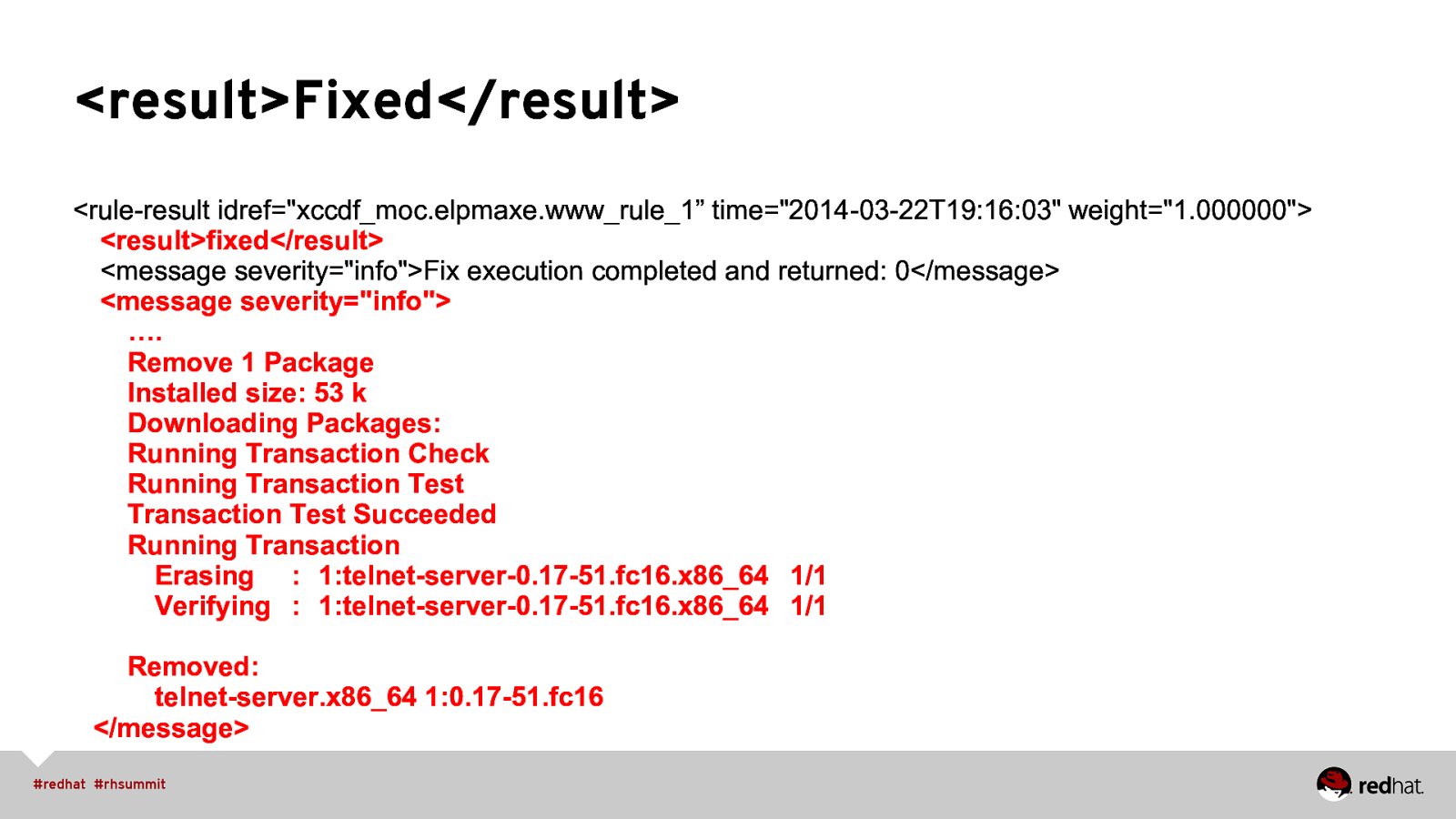
<result>Fixed</result> <rule-result idref=”xccdf_moc.elpmaxe.www_rule_1” time=”2014-03-22T19:16:03” weight=”1.000000”> <result>fixed</result> <message severity=”info”>Fix execution completed and returned: 0</message> <message severity=”info”> …. Remove 1 Package Installed size: 53 k Downloading Packages: Running Transaction Check Running Transaction Test Transaction Test Succeeded Running Transaction Erasing : 1:telnet-server-0.17-51.fc16.x86_64 1/1 Verifying : 1:telnet-server-0.17-51.fc16.x86_64 1/1 Removed: telnet-server.x86_64 1:0.17-51.fc16 </message>
Slide 18
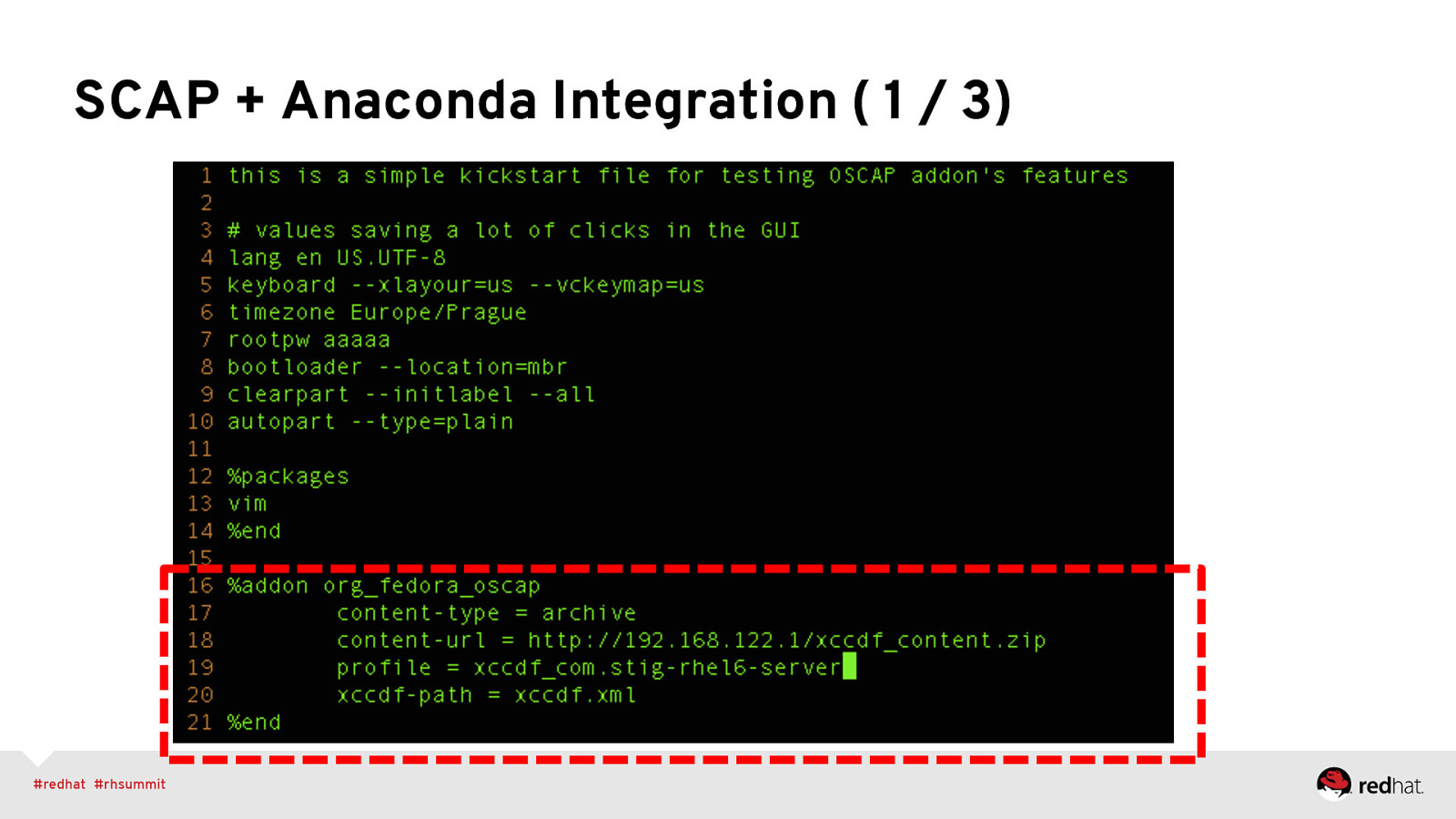
SCAP + Anaconda Integration ( 1 / 3)
Slide 19
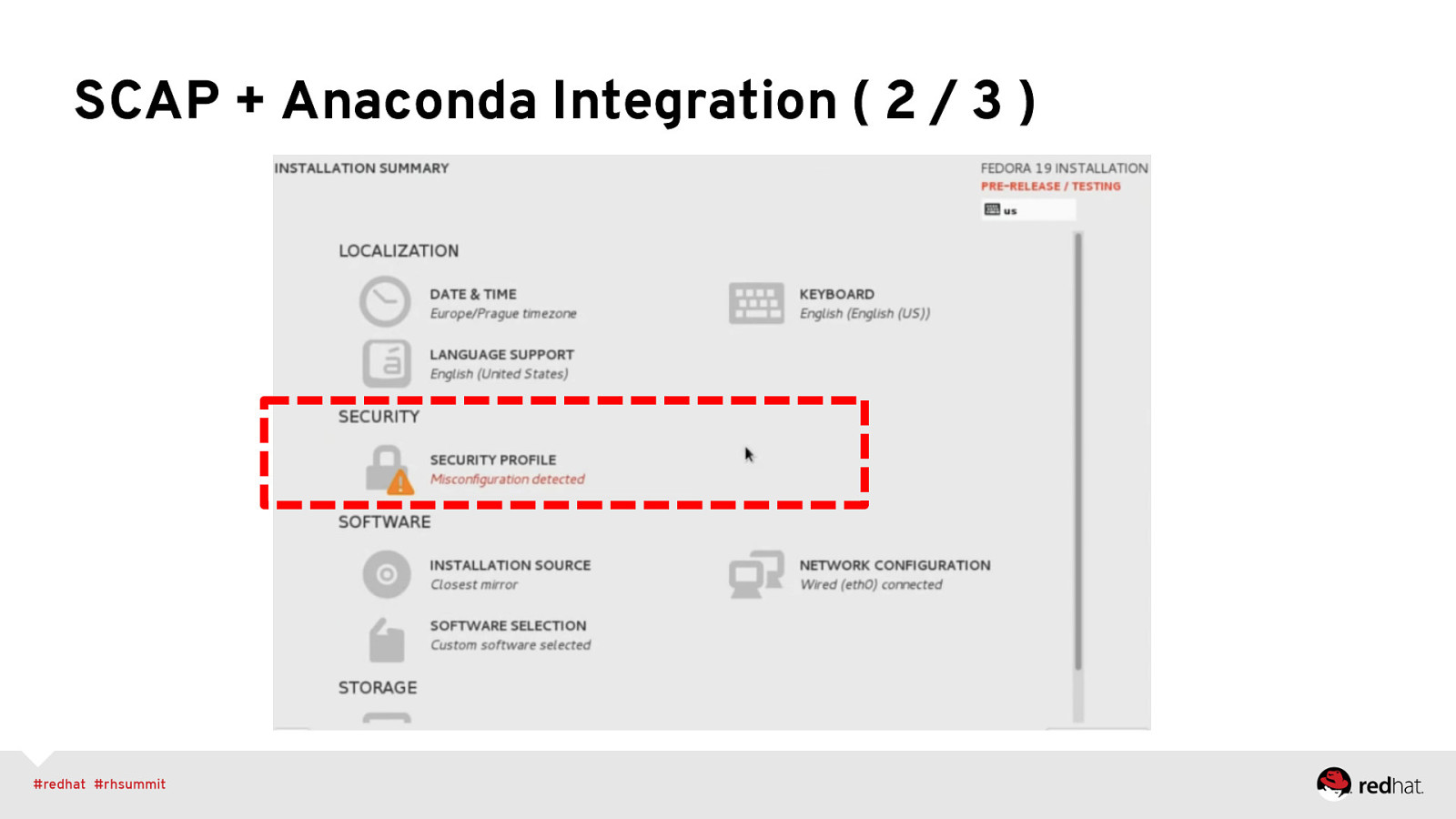
SCAP + Anaconda Integration ( 2 / 3 )
Slide 20
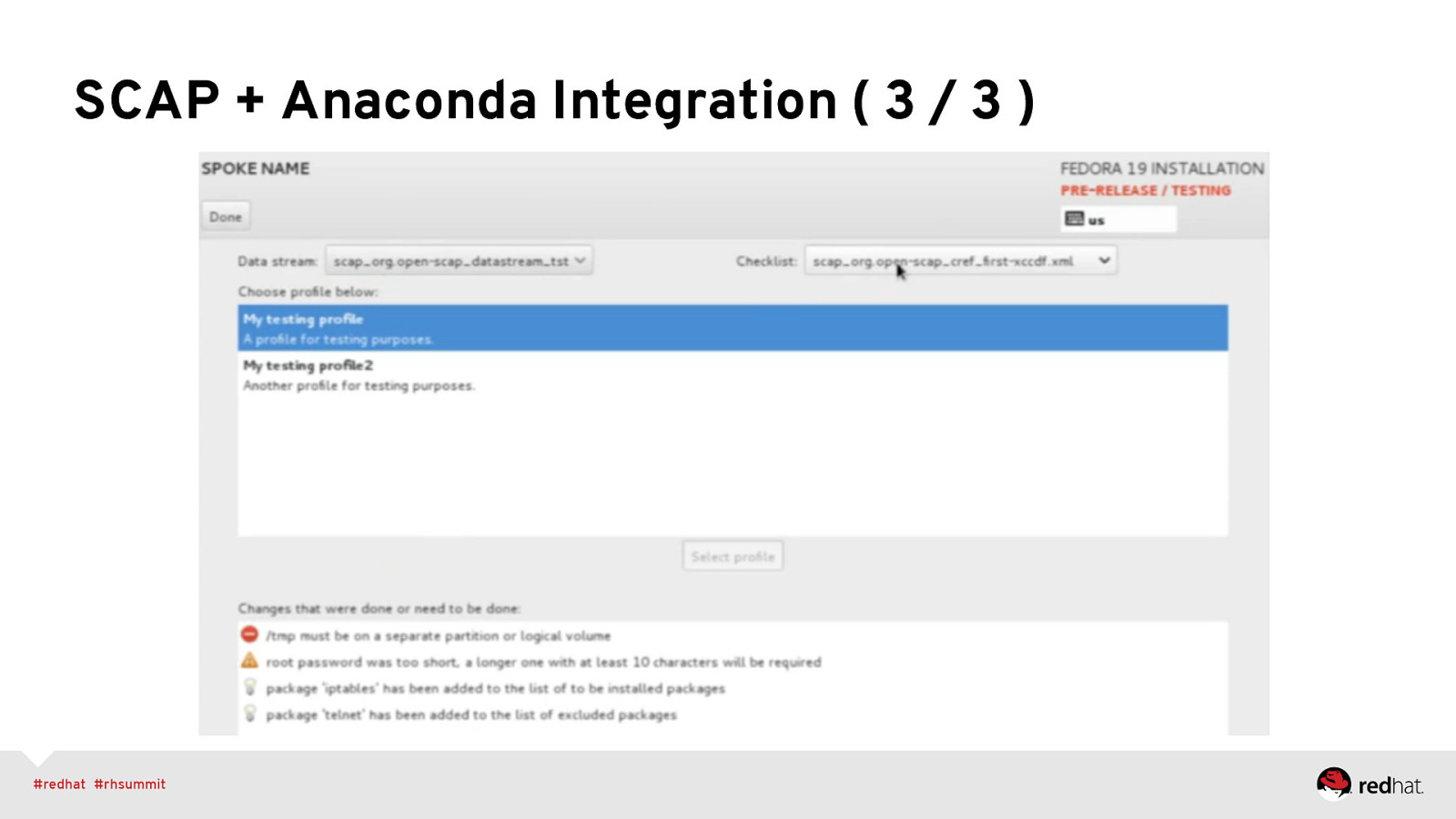
SCAP + Anaconda Integration ( 3 / 3 )