Steve Orrin | Shawn Wells
Slide 1

Slide 2
IMPORTANCE OF PLATFORM SECURITY What are Intel and Red Hat doing to help you secure your systems and infrastructure?
Slide 3
CYBER SECURITY DEFENSE HOST & SYSTEM SECURITY 3 NETWORK DATA & THREAT APPLICATIONS INTELLIGENCE IDENTITY & ACCESS
Slide 4
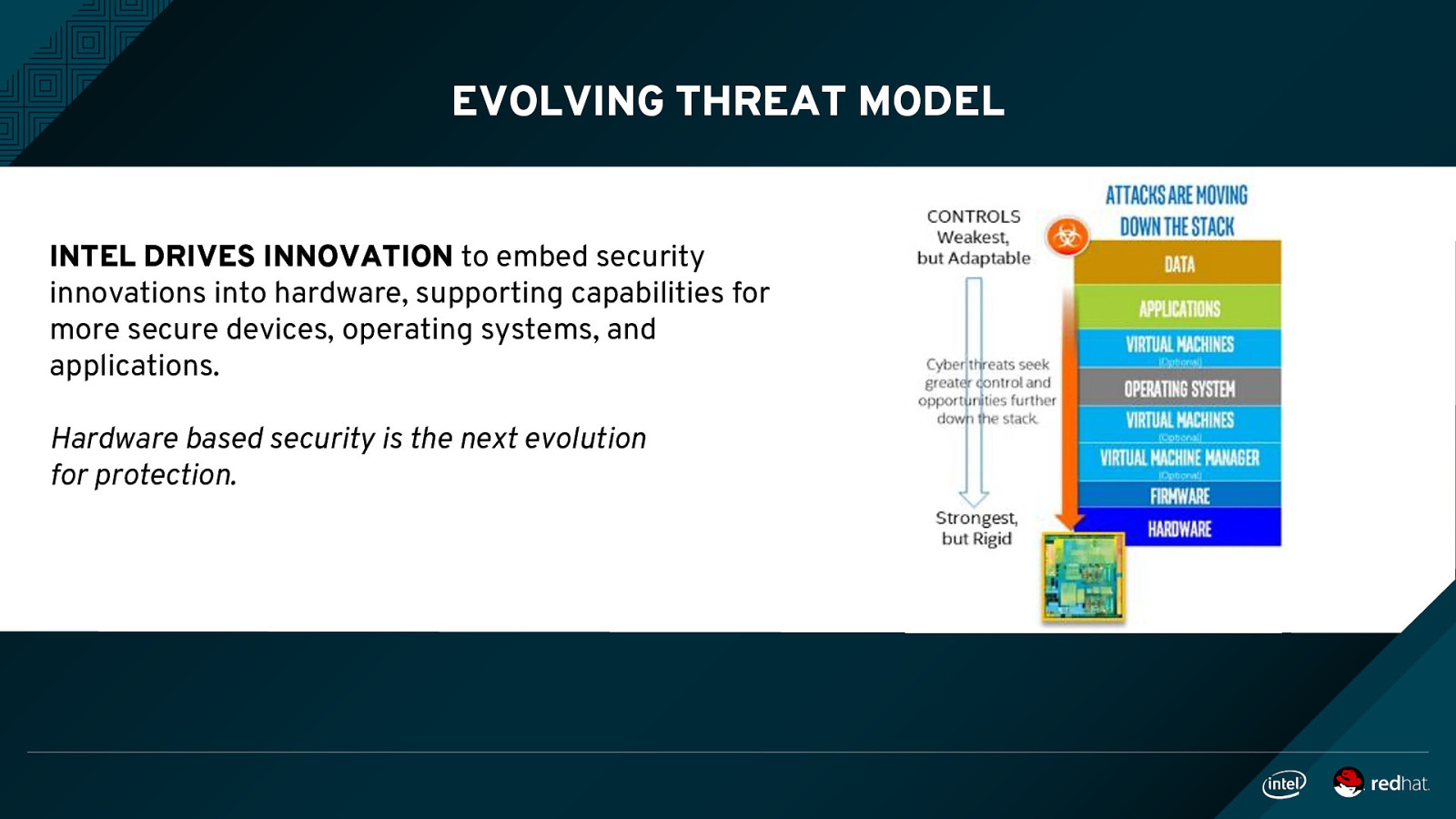
EVOLVING THREAT MODEL INTEL DRIVES INNOVATION to embed security innovations into hardware, supporting capabilities for more secure devices, operating systems, and applications. Hardware based security is the next evolution for protection.
Slide 5
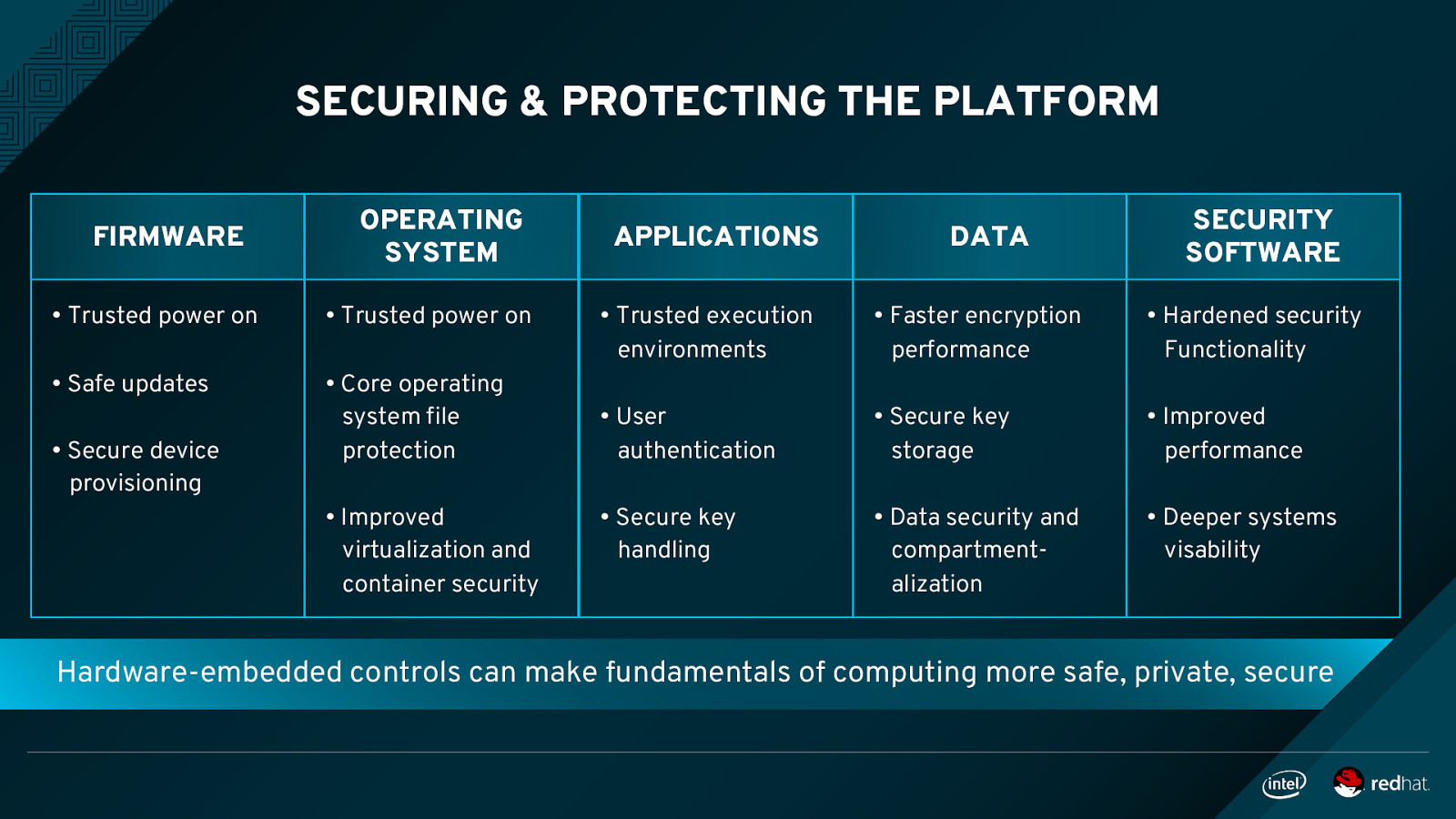
SECURING & PROTECTING THE PLATFORM FIRMWARE OPERATING SYSTEM • Trusted power on • Trusted power on • Safe updates • Core operating system file protection • Secure device provisioning • Improved virtualization and container security APPLICATIONS DATA SECURITY SOFTWARE • Trusted execution environments • Faster encryption performance • Hardened security Functionality • User authentication • Secure key storage • Improved performance • Secure key handling • Data security and compartmentalization • Deeper systems visability Hardware-embedded controls can make fundamentals of computing more safe, private, secure
Slide 6
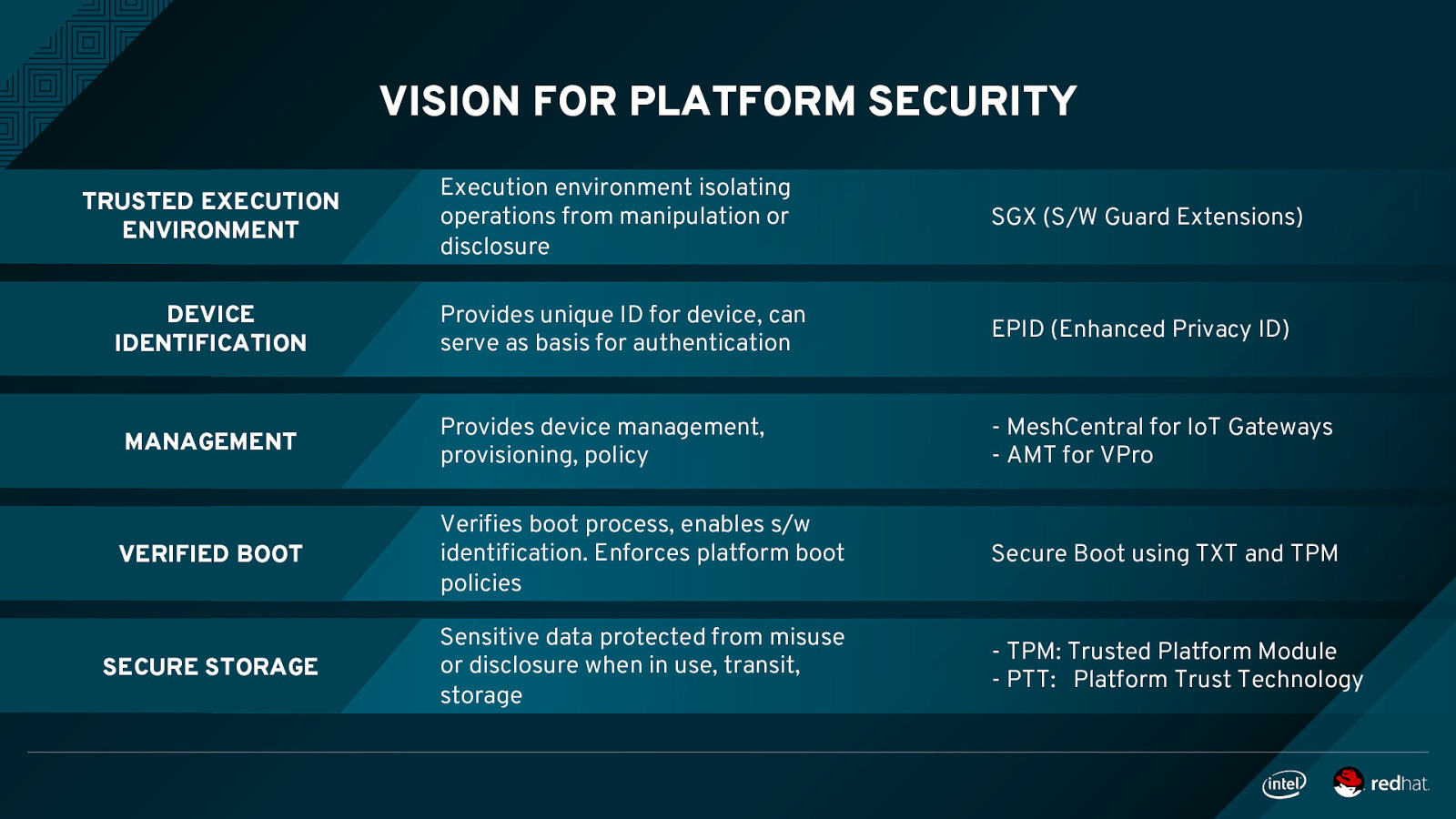
VISION FOR PLATFORM SECURITY Execution environment isolating operations from manipulation or disclosure SGX (S/W Guard Extensions) Provides unique ID for device, can serve as basis for authentication EPID (Enhanced Privacy ID) MANAGEMENT Provides device management, provisioning, policy
- MeshCentral for IoT Gateways - AMT for VPro VERIFIED BOOT Verifies boot process, enables s/w identification. Enforces platform boot policies Secure Boot using TXT and TPM SECURE STORAGE Sensitive data protected from misuse or disclosure when in use, transit, storage
- TPM: Trusted Platform Module - PTT: Platform Trust Technology TRUSTED EXECUTION ENVIRONMENT DEVICE IDENTIFICATION
Slide 7

INTEL SECURITY ESSENTIALS PLATFORM INTEGRITY Intel Platform Protection Technology with Boot Guard Verifies OEM pre-OS boot loader code executing out of reset Intel Platform Protection Technology with OS Guard Helps prevent malicious code from executing out of application memory space Intel Trusted Execution Technology (TXT) TCG Compliant Secure Boot with attestation Framework & common root-of-trust security capabilities across Intel processors
Slide 8
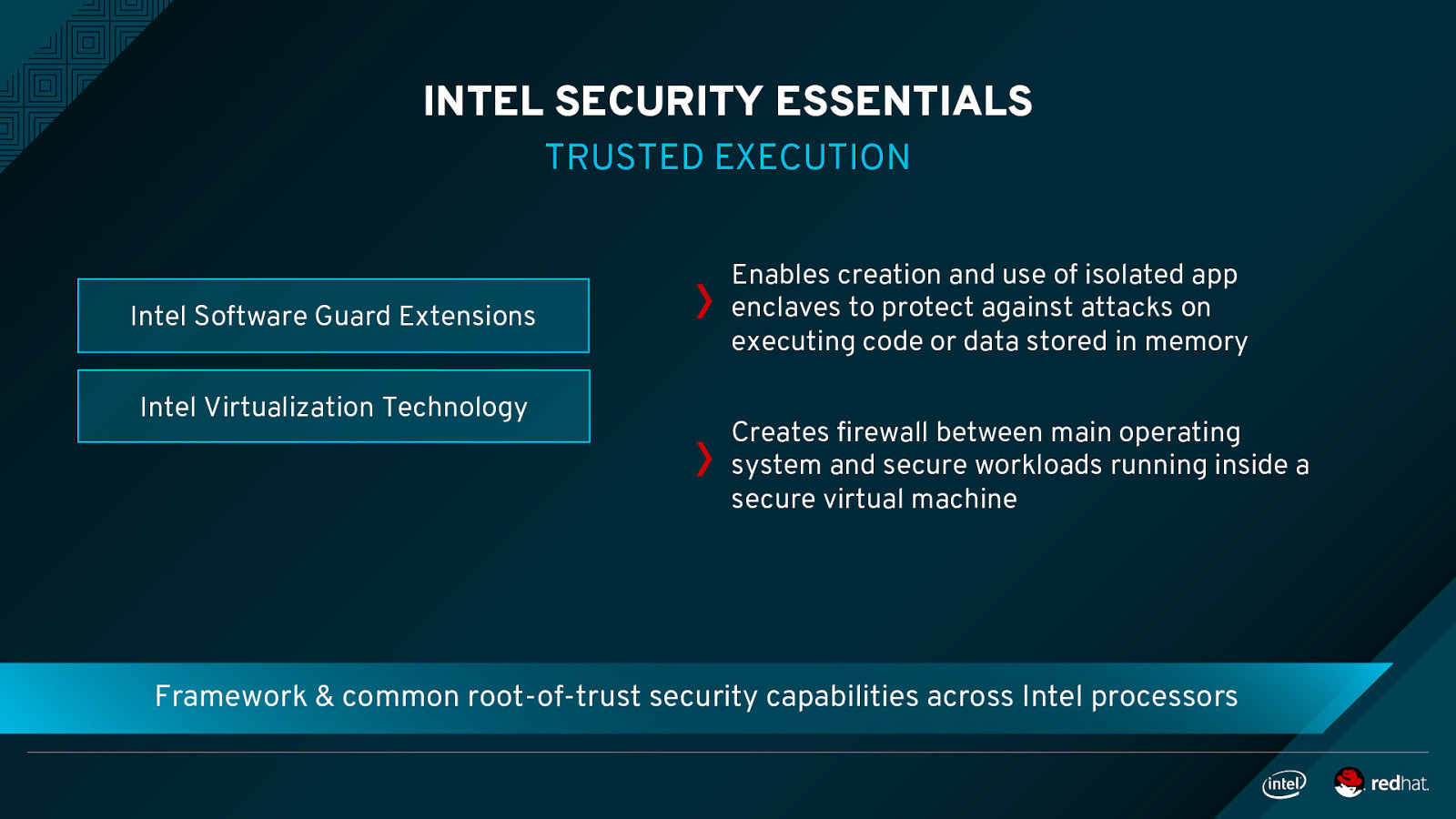
INTEL SECURITY ESSENTIALS TRUSTED EXECUTION Intel Software Guard Extensions Intel Virtualization Technology Enables creation and use of isolated app enclaves to protect against attacks on executing code or data stored in memory Creates firewall between main operating system and secure workloads running inside a secure virtual machine Framework & common root-of-trust security capabilities across Intel processors
Slide 9

INTEL SECURITY ESSENTIALS PROTECTED DATA, KEYS, IDENTITY Intel Platform Trust Technology Integrated H/W TPM enables secure storage of keys/credentials, boot block measurements for remote attestation Intel Enhanced Privacy ID Cryptographic scheme provides direct anonymous attestation of hardware for privacy Framework & common root-of-trust security capabilities across Intel processors
Slide 10

INTEL SECURITY ESSENTIALS CRYPTO ACCELERATORS Intel Data Protection Technology with Secure Key Intel Advanced Encryption Standard New Instructions High entropy source of random numbers to generate keys Accelerates math calculations for AES-NI encryption Framework & common root-of-trust security capabilities across Intel processors
Slide 11
WHAT IS PLATFORM SECURITY SECURE BOOT CRYPTO ACCELERATION ATTESTATION & ASSURANCE
Slide 12
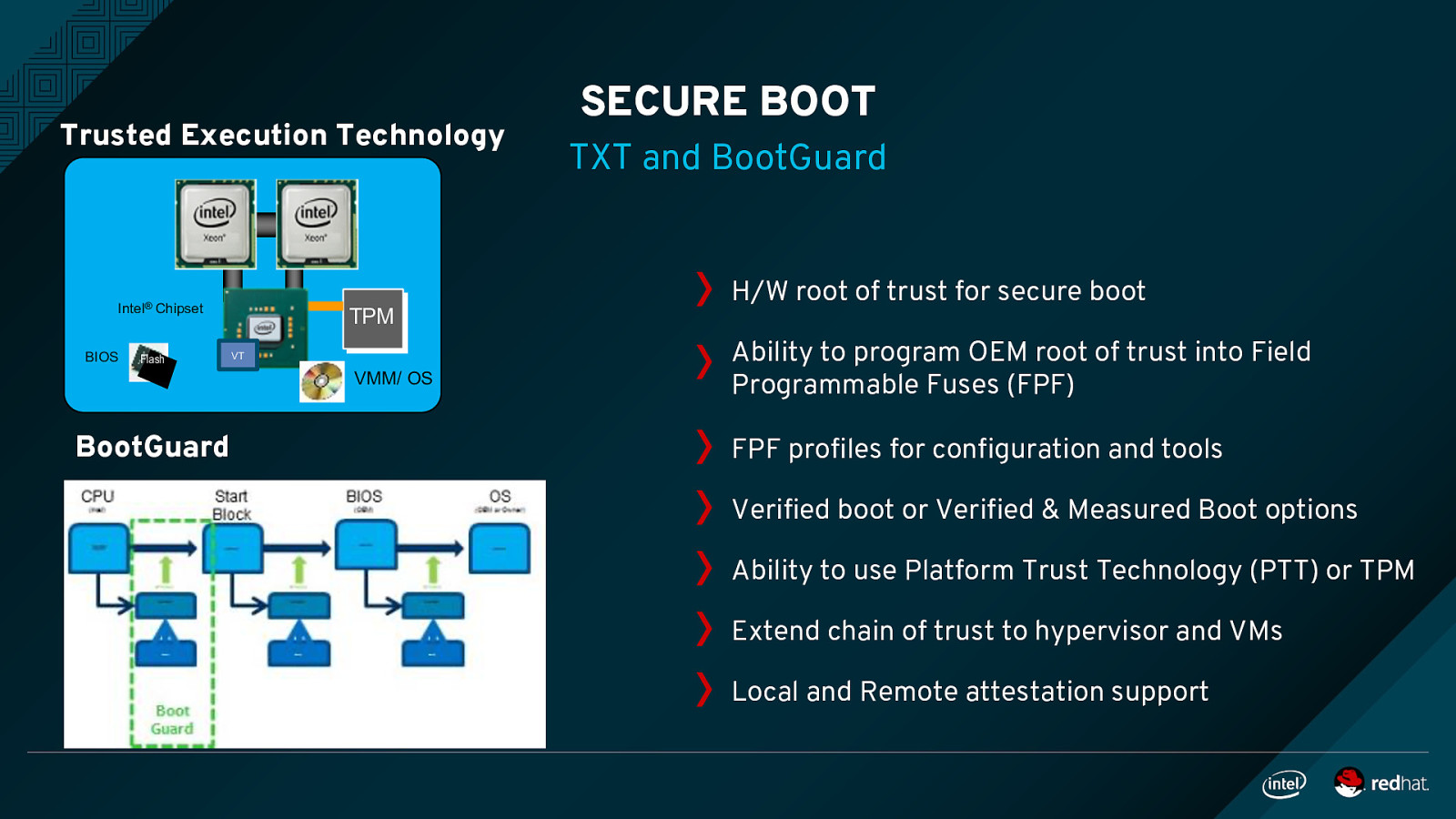
Trusted Execution Technology Intel® Chipset BIOS Flash TPM VT VMM/ OS BootGuard SECURE BOOT TXT and BootGuard H/W root of trust for secure boot Ability to program OEM root of trust into Field Programmable Fuses (FPF) FPF profiles for configuration and tools Verified boot or Verified & Measured Boot options Ability to use Platform Trust Technology (PTT) or TPM Extend chain of trust to hypervisor and VMs Local and Remote attestation support
Slide 13
HARDWARE ACCELERATED CRYPTOGRAPHY AES-NI DRNG ADOX/ADX UBIQUITOUS DATA PROTECTION WITH CRYPTOGRAPHIC ACCELERATION STRONGER ENCRYPTION WITH ON-BOARD DIGITAL RANDOM NUMBER GENERATOR INSTRUCTION FOR USE IN LARGE INTEGER ARITHMETIC (> 64b) AES-NI allows significant performance at a lower price-point with no custom hardware. High degree of entropy provides quality random numbers for encryption keys and other operations. Common use is Public Key cryptography (e.g. RSA). DRNG solves the problem of limited entropy in virtual and container platforms.
Slide 14
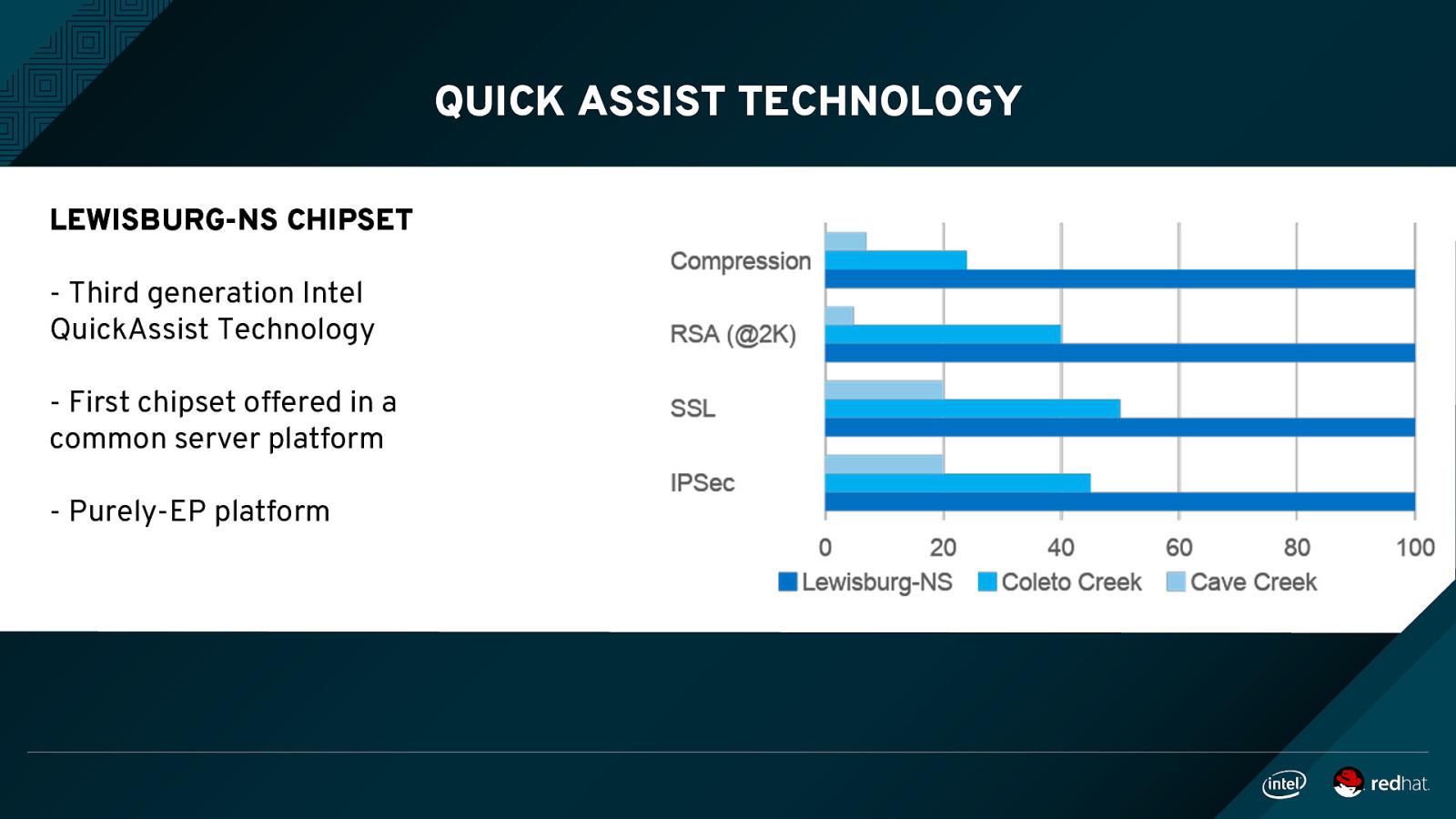
QUICK ASSIST TECHNOLOGY LEWISBURG-NS CHIPSET - Third generation Intel QuickAssist Technology - First chipset offered in a common server platform - Purely-EP platform
Slide 15
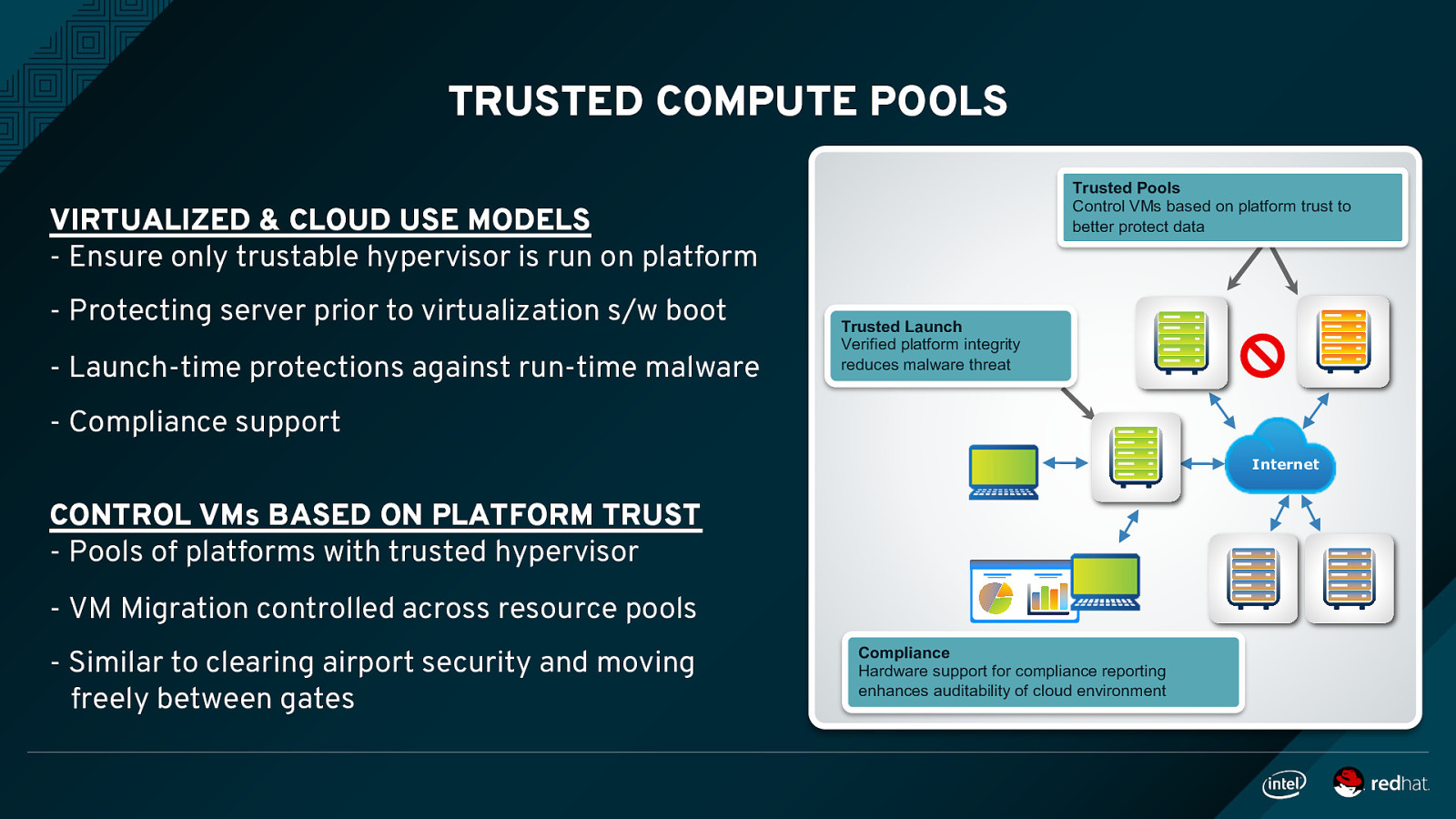
TRUSTED COMPUTE POOLS Trusted Pools Control VMs based on platform trust to better protect data VIRTUALIZED & CLOUD USE MODELS - Ensure only trustable hypervisor is run on platform - Protecting server prior to virtualization s/w boot - Launch-time protections against run-time malware Trusted Launch Verified platform integrity reduces malware threat
- Compliance support Internet CONTROL VMs BASED ON PLATFORM TRUST - Pools of platforms with trusted hypervisor - VM Migration controlled across resource pools - Similar to clearing airport security and moving freely between gates Compliance Hardware support for compliance reporting enhances auditability of cloud environment
Slide 16
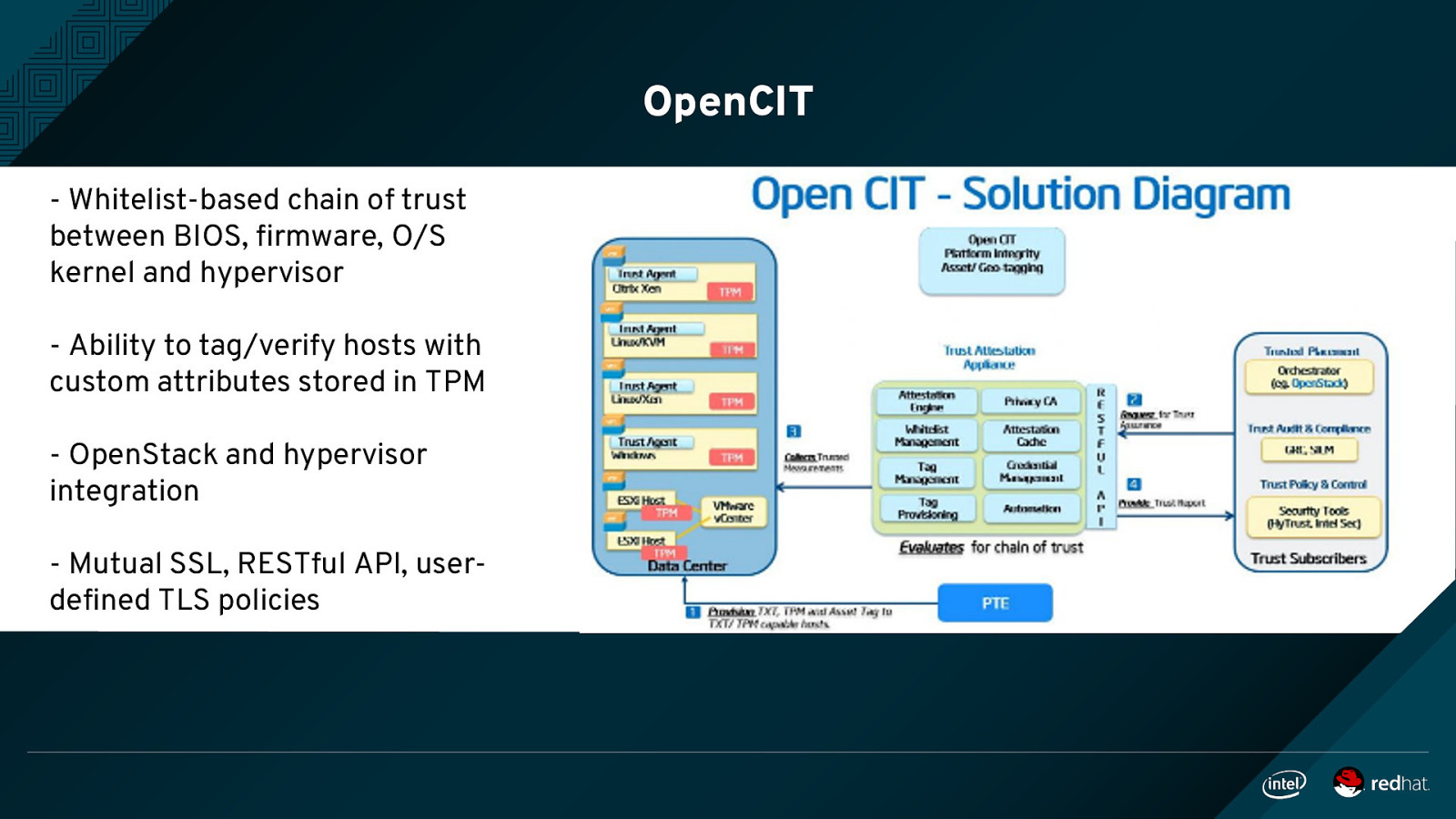
OpenCIT - Whitelist-based chain of trust between BIOS, firmware, O/S kernel and hypervisor - Ability to tag/verify hosts with custom attributes stored in TPM - OpenStack and hypervisor integration - Mutual SSL, RESTful API, userdefined TLS policies
Slide 17
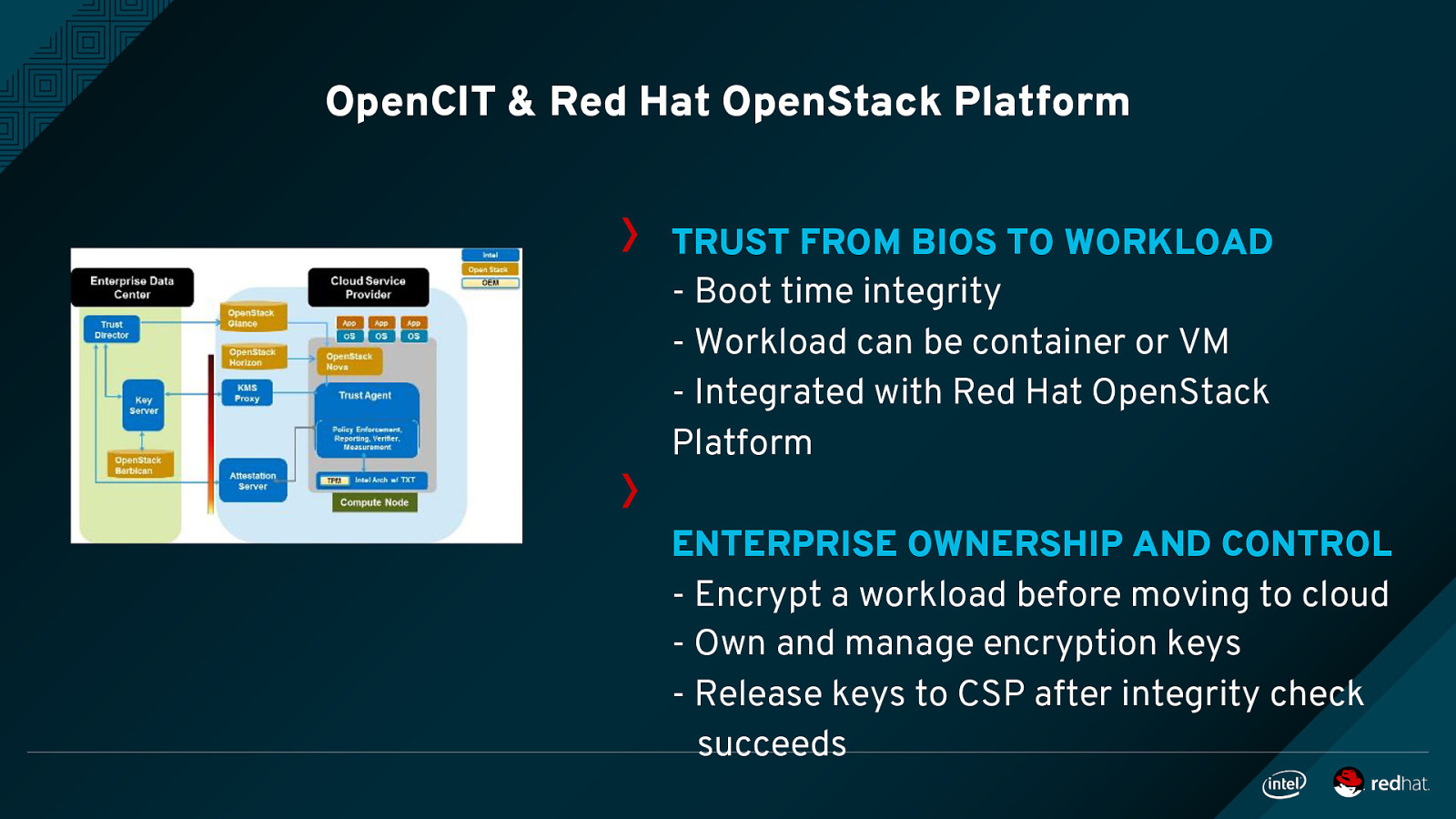
OpenCIT & Red Hat OpenStack Platform TRUST FROM BIOS TO WORKLOAD - Boot time integrity - Workload can be container or VM - Integrated with Red Hat OpenStack Platform ENTERPRISE OWNERSHIP AND CONTROL - Encrypt a workload before moving to cloud - Own and manage encryption keys - Release keys to CSP after integrity check succeeds
Slide 18
NIST IR 7904 REFERENCE ARCHITECTURE Joint Collaboration between NIST, Intel Corporation, and Software Vendors to demonstrate the ability to control and audit workload and data provisioning based on system trust and geo-location http://nvlpubs.nist.gov/nistpubs/ir/2015/NIST.IR.7904.pdf
Slide 19
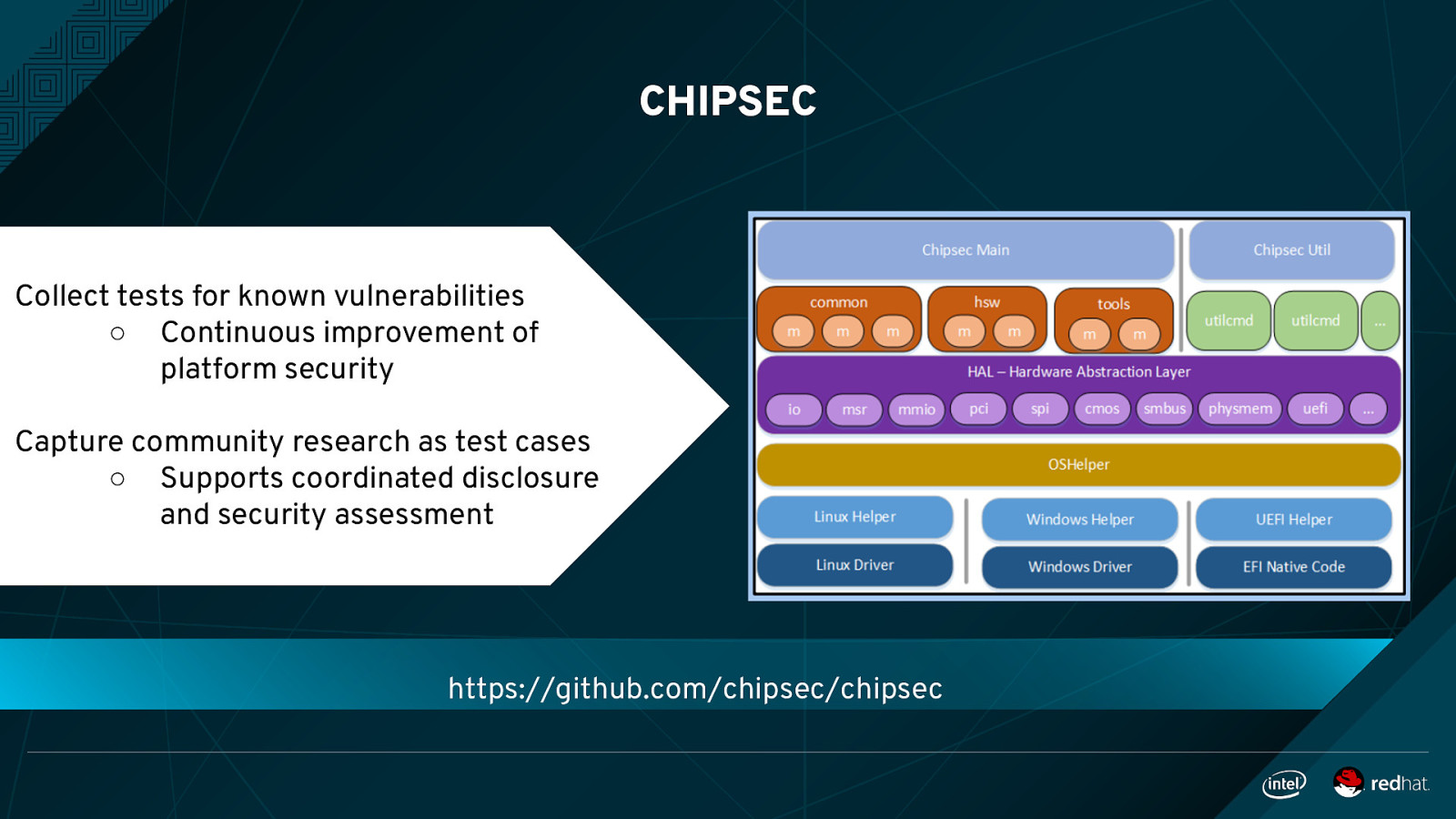
CHIPSEC Collect tests for known vulnerabilities ○ Continuous improvement of platform security Capture community research as test cases ○ Supports coordinated disclosure and security assessment https://github.com/chipsec/chipsec
Slide 20
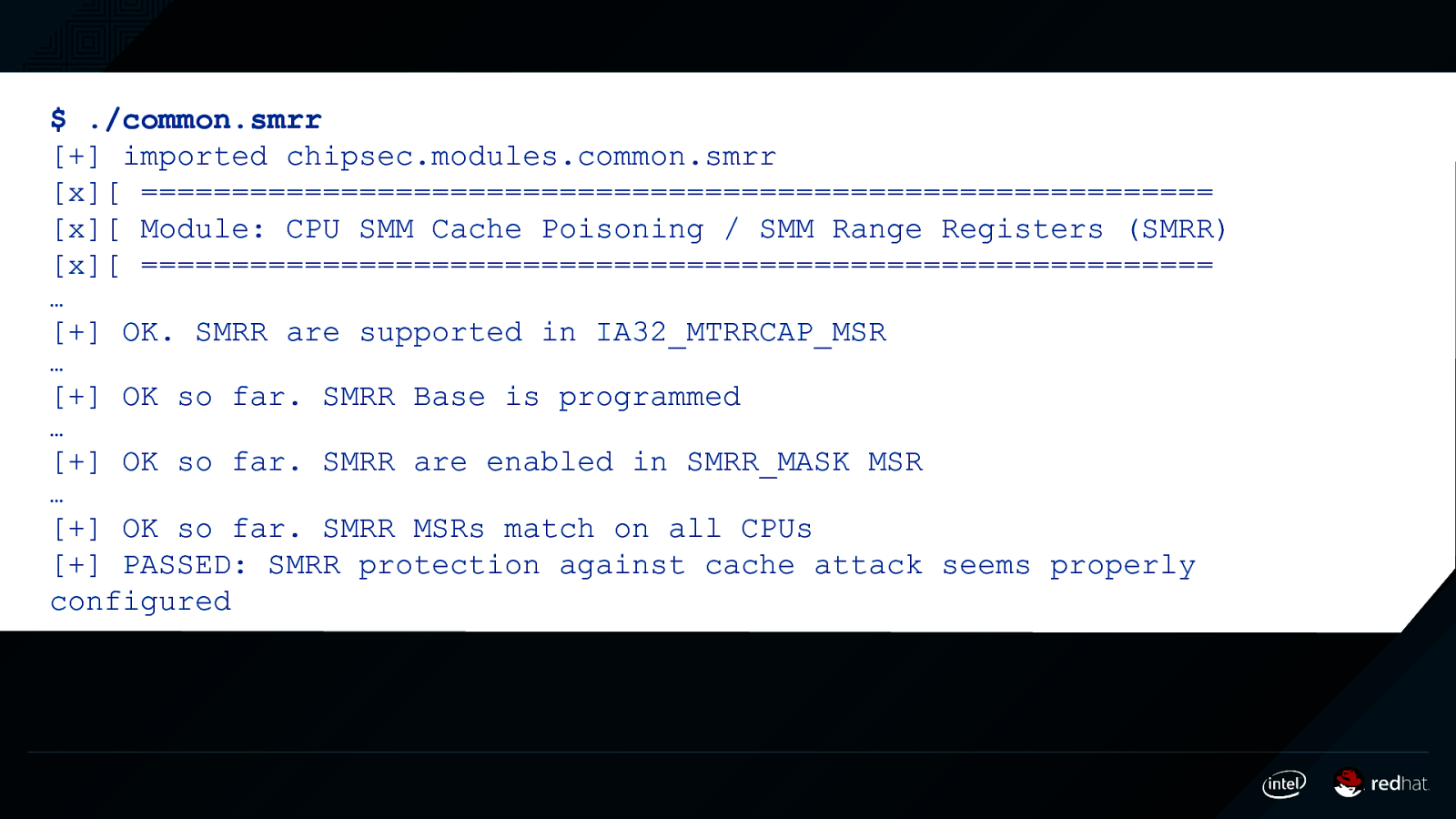
$ ./common.smrr [+] imported chipsec.modules.common.smrr [x][ =========================================================== [x][ Module: CPU SMM Cache Poisoning / SMM Range Registers (SMRR) [x][ =========================================================== … [+] OK. SMRR are supported in IA32_MTRRCAP_MSR … [+] OK so far. SMRR Base is programmed … [+] OK so far. SMRR are enabled in SMRR_MASK MSR … [+] OK so far. SMRR MSRs match on all CPUs [+] PASSED: SMRR protection against cache attack seems properly configured
Slide 21
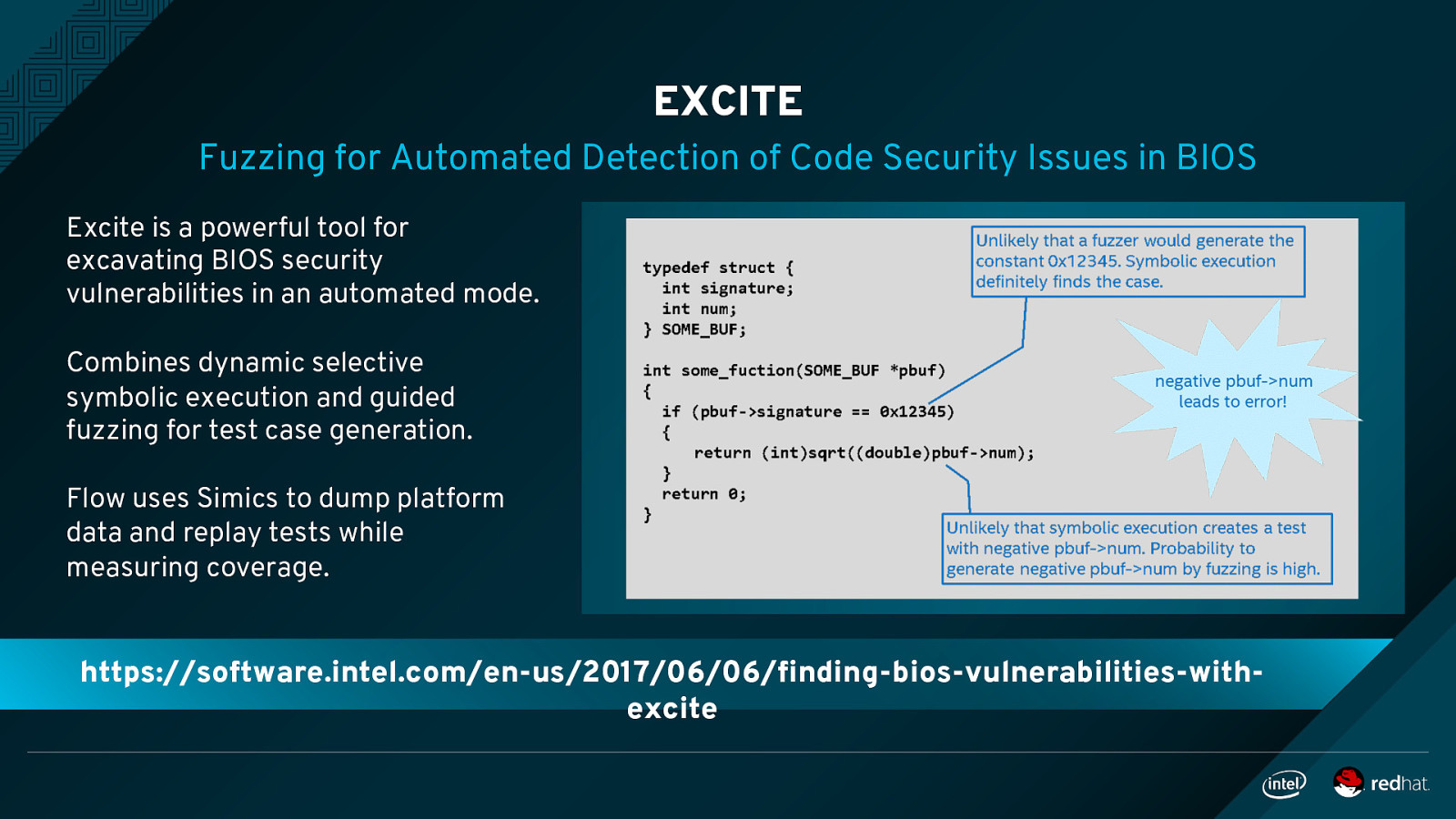
EXCITE Fuzzing for Automated Detection of Code Security Issues in BIOS Excite is a powerful tool for excavating BIOS security vulnerabilities in an automated mode. Combines dynamic selective symbolic execution and guided fuzzing for test case generation. Flow uses Simics to dump platform data and replay tests while measuring coverage. https://software.intel.com/en-us/2017/06/06/finding-bios-vulnerabilities-withexcite
Slide 22

Summary ● The threats to the platform continue to evolve deeper in the stack ● Intel & Red Hat are focused on providing access to security capabilities that: ○ ○ ○ Enhance platform security and visibility Provide efficient and performant cryptography Drive scalable assurance and compliance ● Reducing the surface area of attack and providing advanced security features in hardware, firmware and software, Intel & Red hat are hardening the platform and enabling platform trust.
Slide 23

INNOVATION DOES NO GOOD IF YOU CAN’T SECURE IT
Slide 24
Slide 25

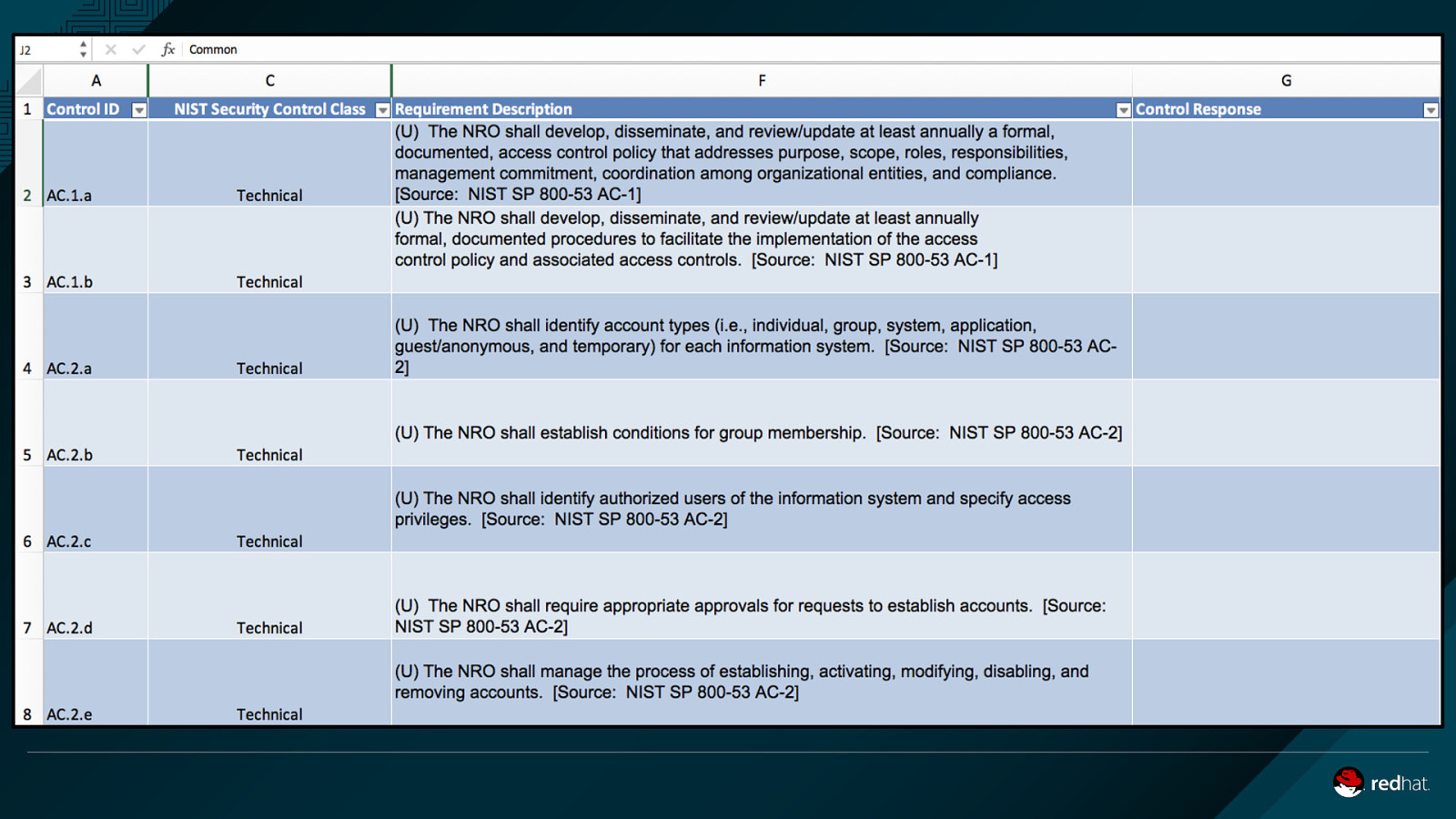
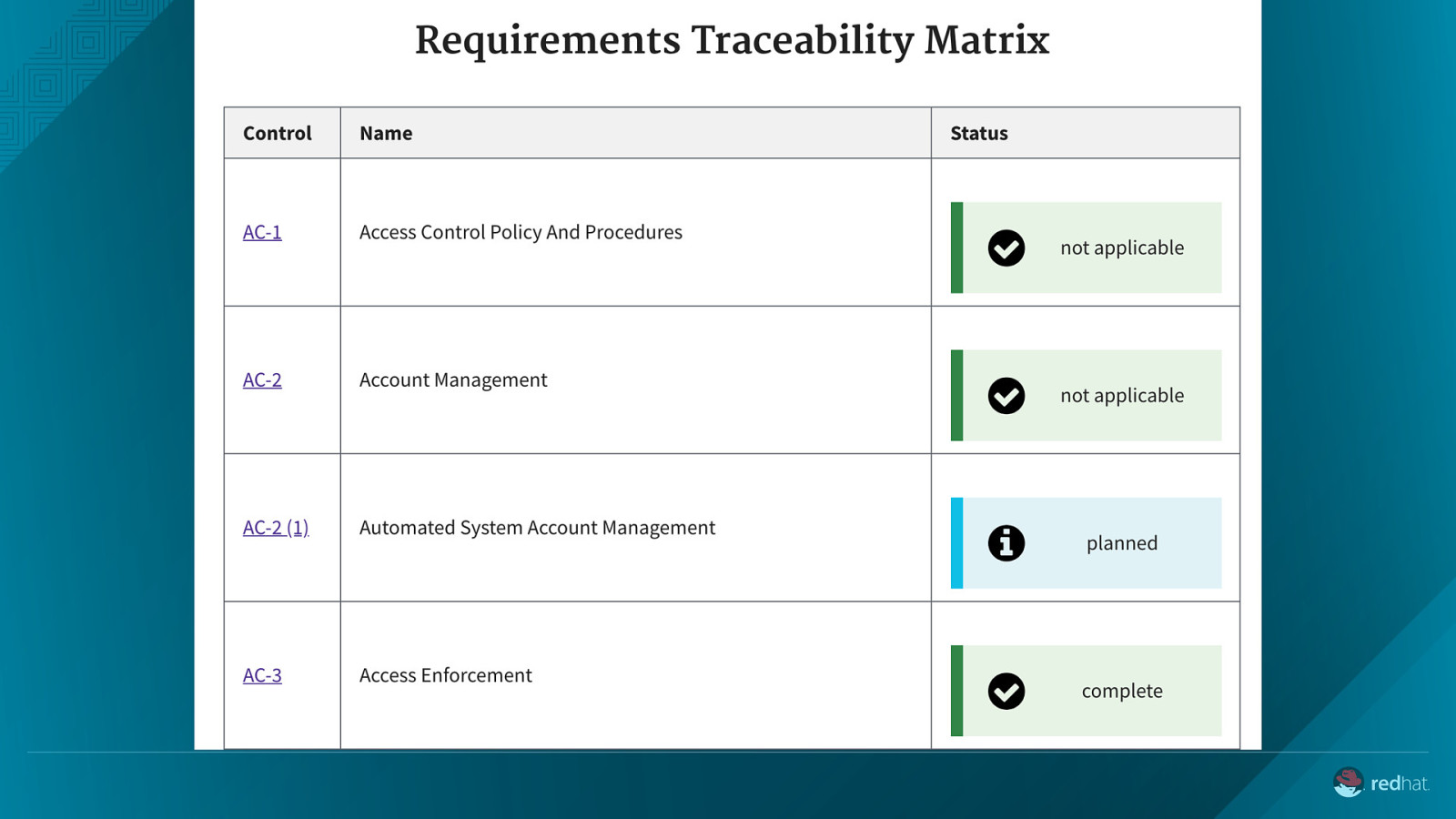
The government created a control catalog. Could we create a response catalog? Can deployment specific ATO materials be dynamically generated?
Slide 26
Structured language for ATO responses, created by 18F
Slide 27
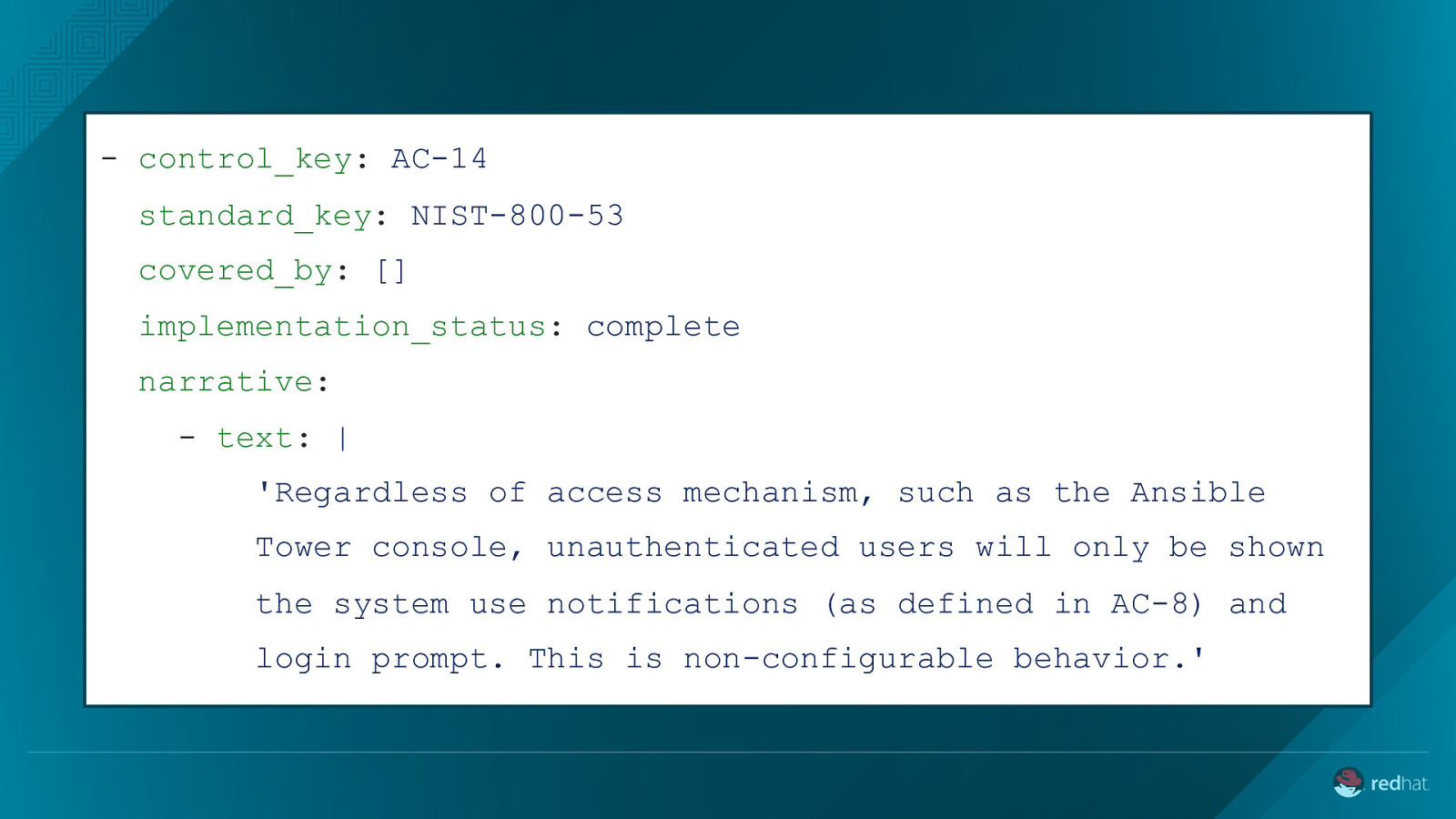
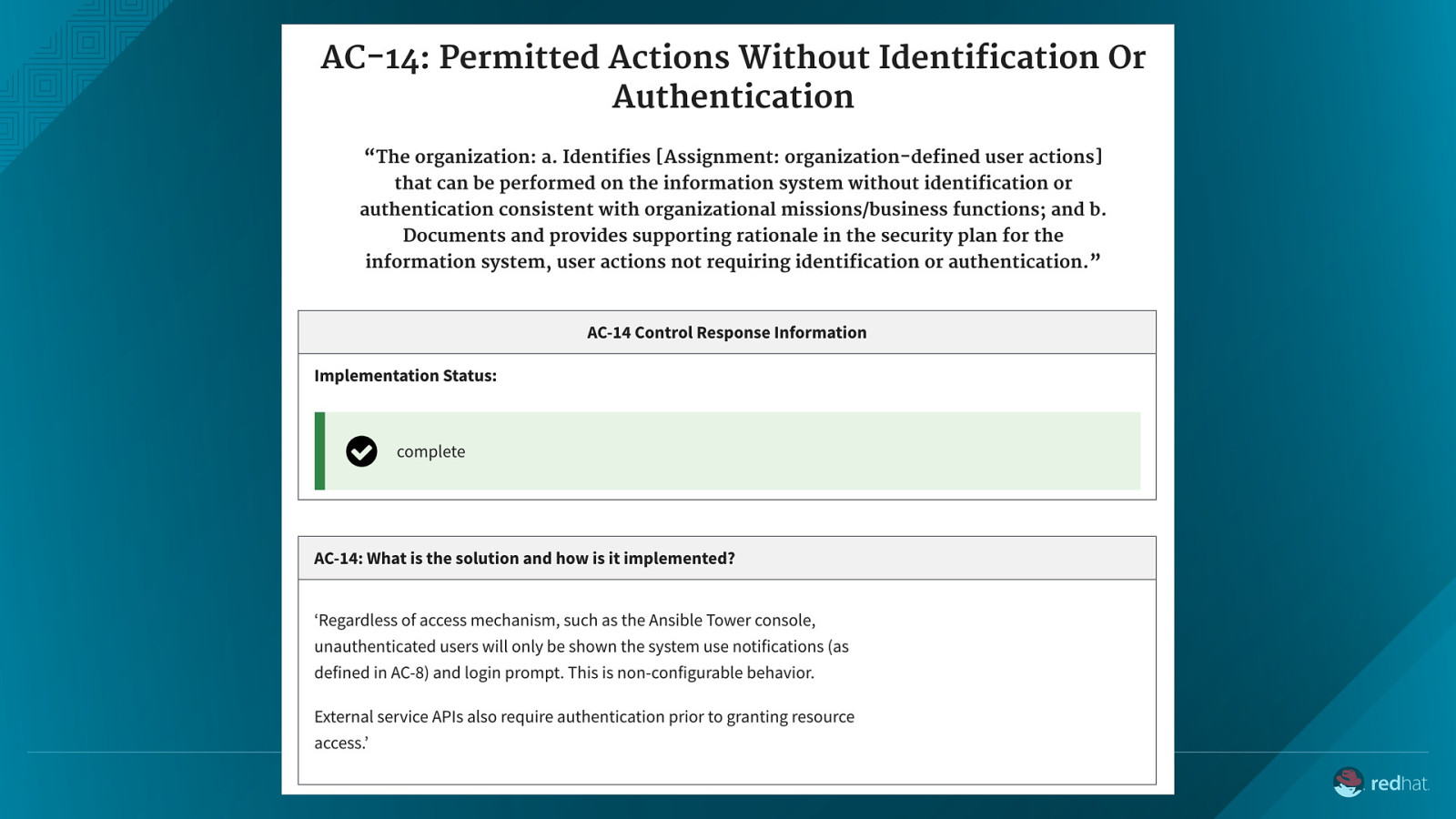
- control_key: AC-14 standard_key: NIST-800-53 covered_by: [] implementation_status: complete narrative: - text: | ‘Regardless of access mechanism, such as the Ansible Tower console, unauthenticated users will only be shown the system use notifications (as defined in AC-8) and login prompt. This is non-configurable behavior.’
Slide 28
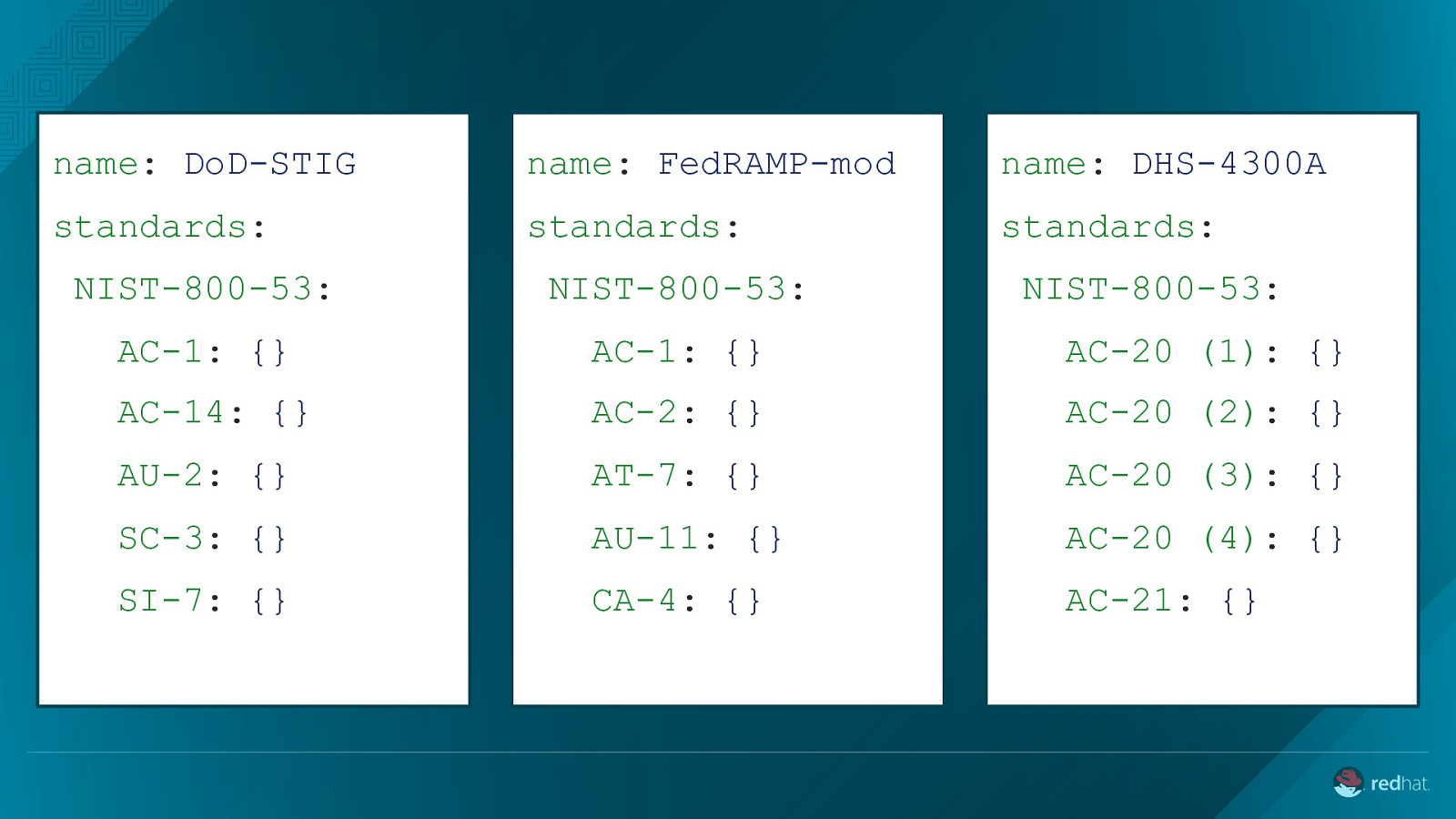
name: DoD-STIG name: FedRAMP-mod name: DHS-4300A standards: standards: standards: NIST-800-53: NIST-800-53: NIST-800-53: AC-1: {} AC-1: {} AC-20 (1): {} AC-14: {} AC-2: {} AC-20 (2): {} AU-2: {} AT-7: {} AC-20 (3): {} SC-3: {} AU-11: {} AC-20 (4): {} SI-7: {} CA-4: {} AC-21: {}
Slide 29
Slide 30
Slide 31

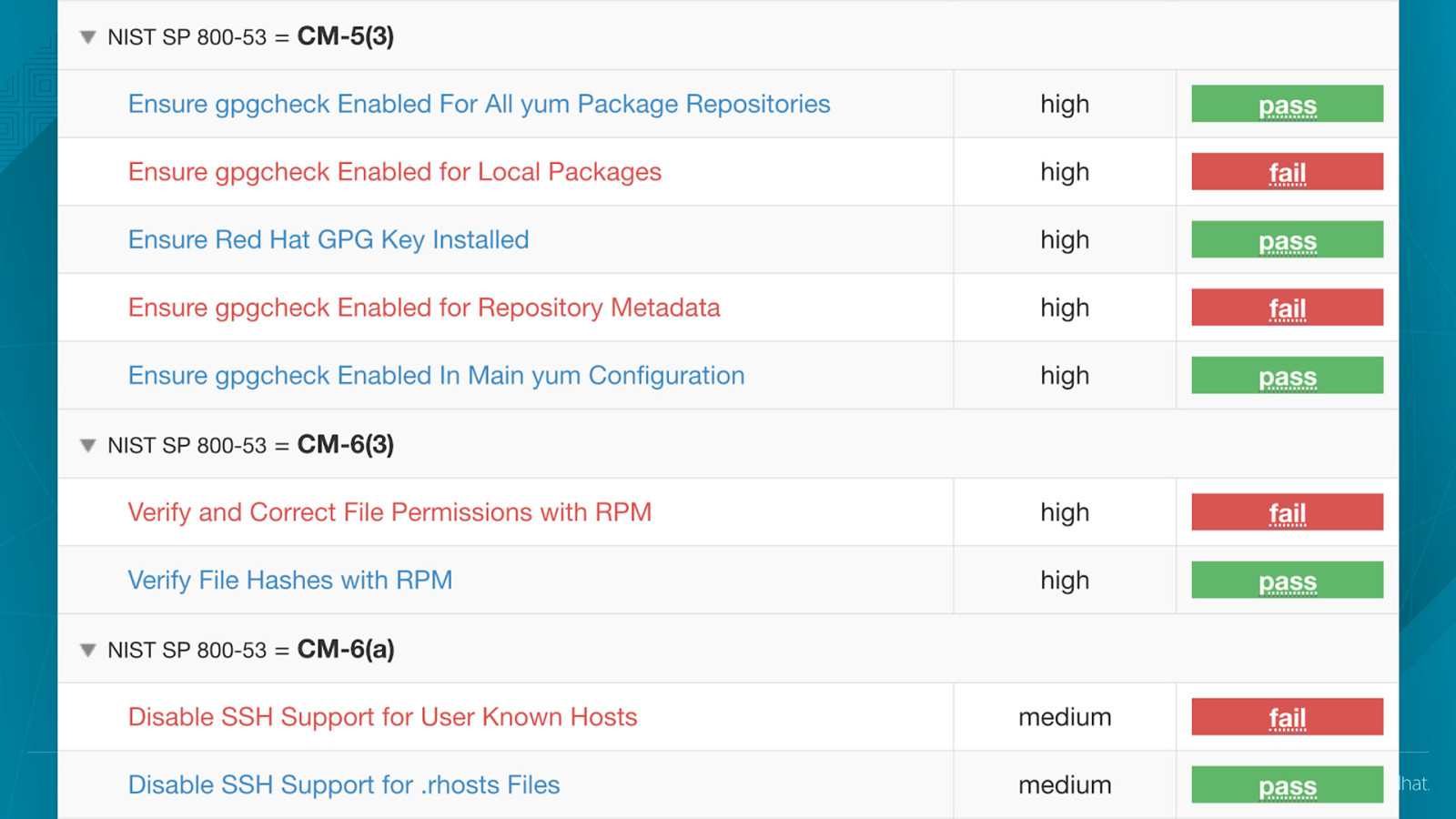
Automated configuration scans, co-founded with NSA Information Assurance
Slide 32
Slide 33

ANSIBLE PLAYBOOKS AVAILABLE ON GALAXY, INCLUDING … DoD STIG C2S • Last updated for RHEL 7.6 • Available in any RHEL image, not just highside AMIs • Lowside development with same security settings as higher environments FBI CJIS HIPAA • Criminal Justice Information Services (CJIS) • Used by federal and commercial healthcare • Police, court systems, evidence handling systems https://galaxy.ansible.com/RedHatOfficial
Slide 34

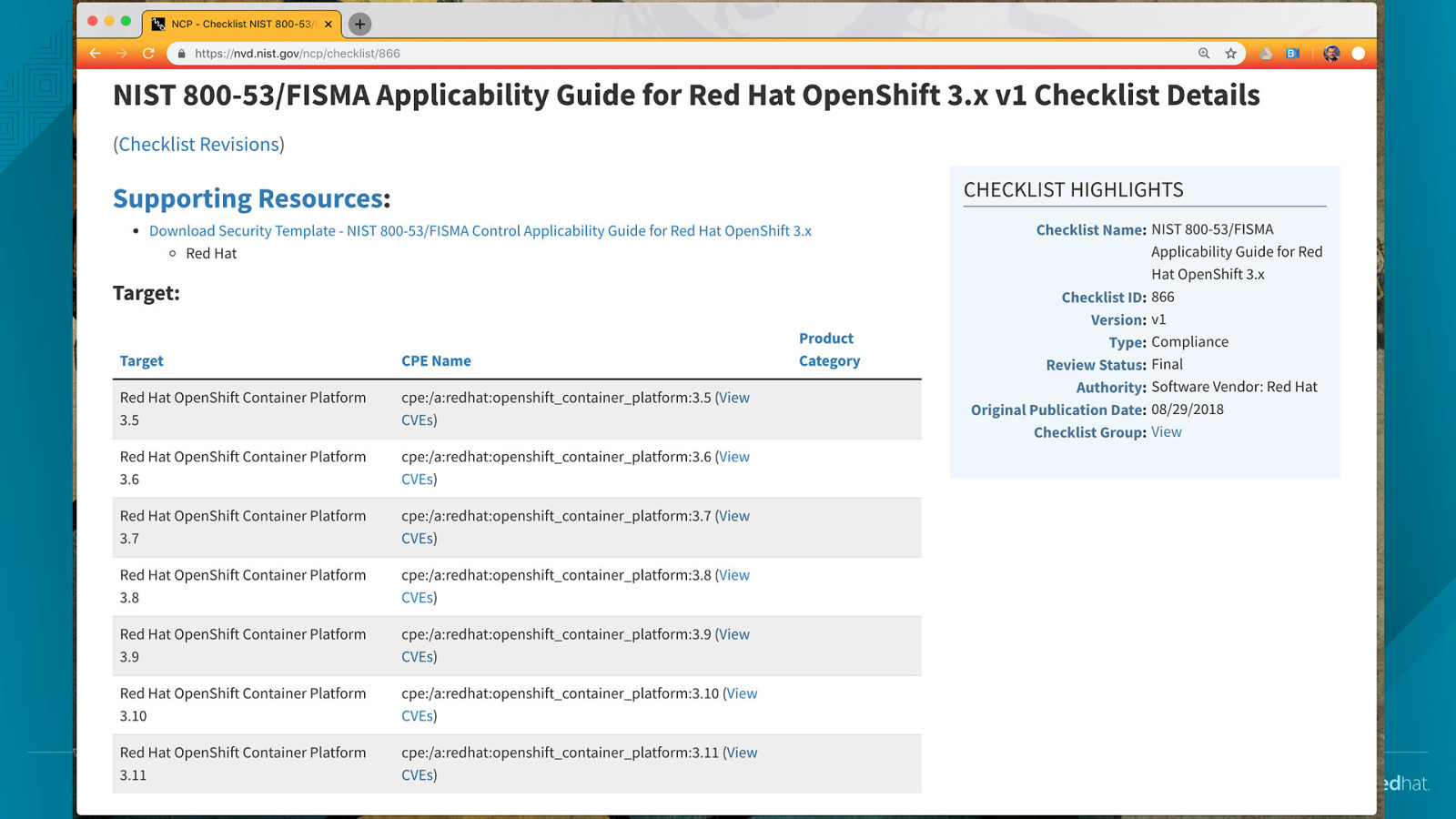
NIST NATIONAL CHECKLIST PROGRAM The National Checklist Program (NCP) is the U.S. Government repository of publicly available security checklists, that provide detailed low level guidance, on setting the security configuration of system components and applications https://nvd.nist.gov/ncp/repository?authority=Red+Hat&startIndex=0
Slide 35
Slide 36
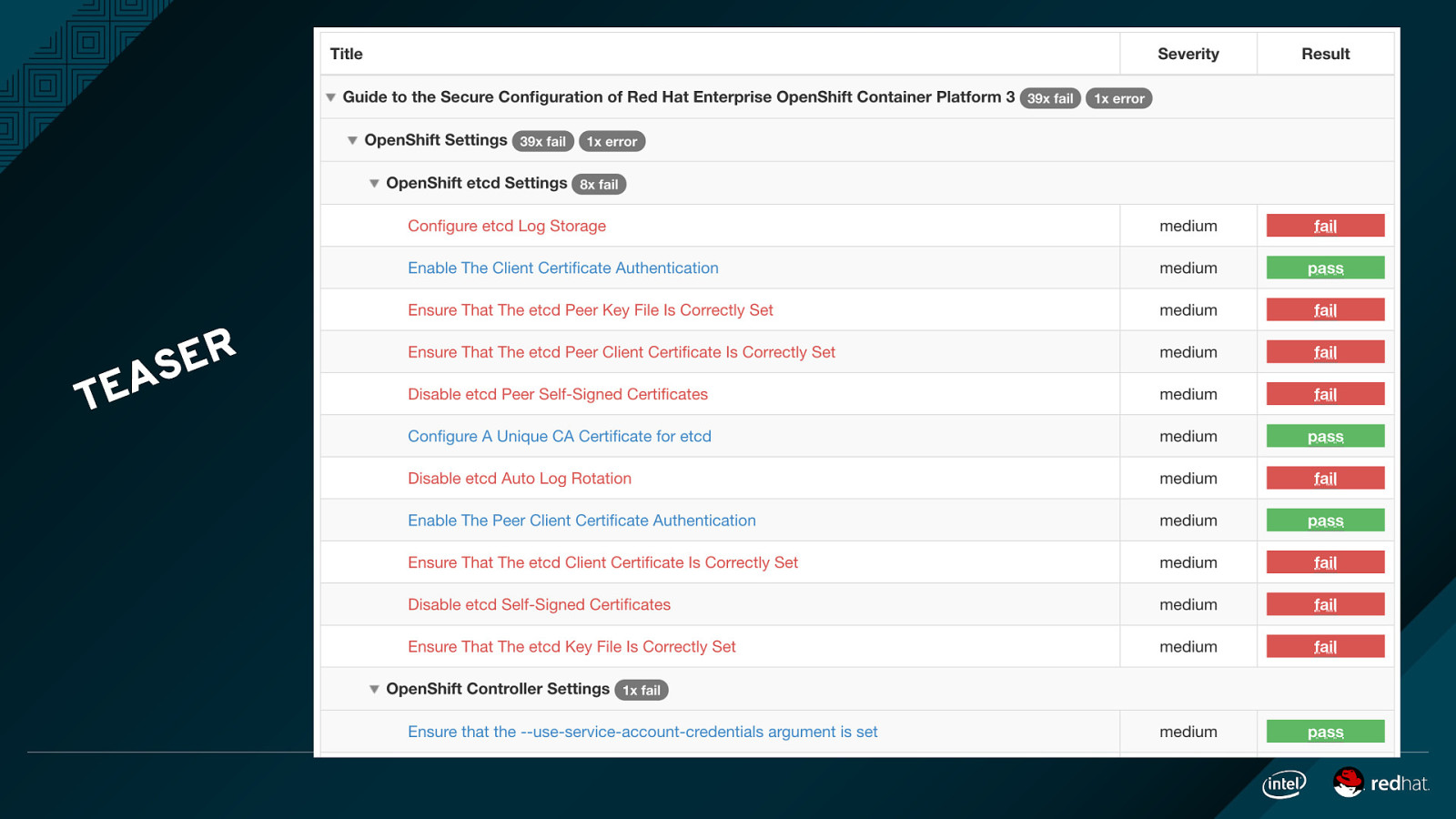
T R E S EA
Slide 37
Slide 38
Slide 39

Slide 40

THANK YOU