Applied SCAP: Automating Security Compliance and Remediation Shawn Wells Maintainer, SCAP Security Guide 31-JULY-2014
Slide 1

Slide 2
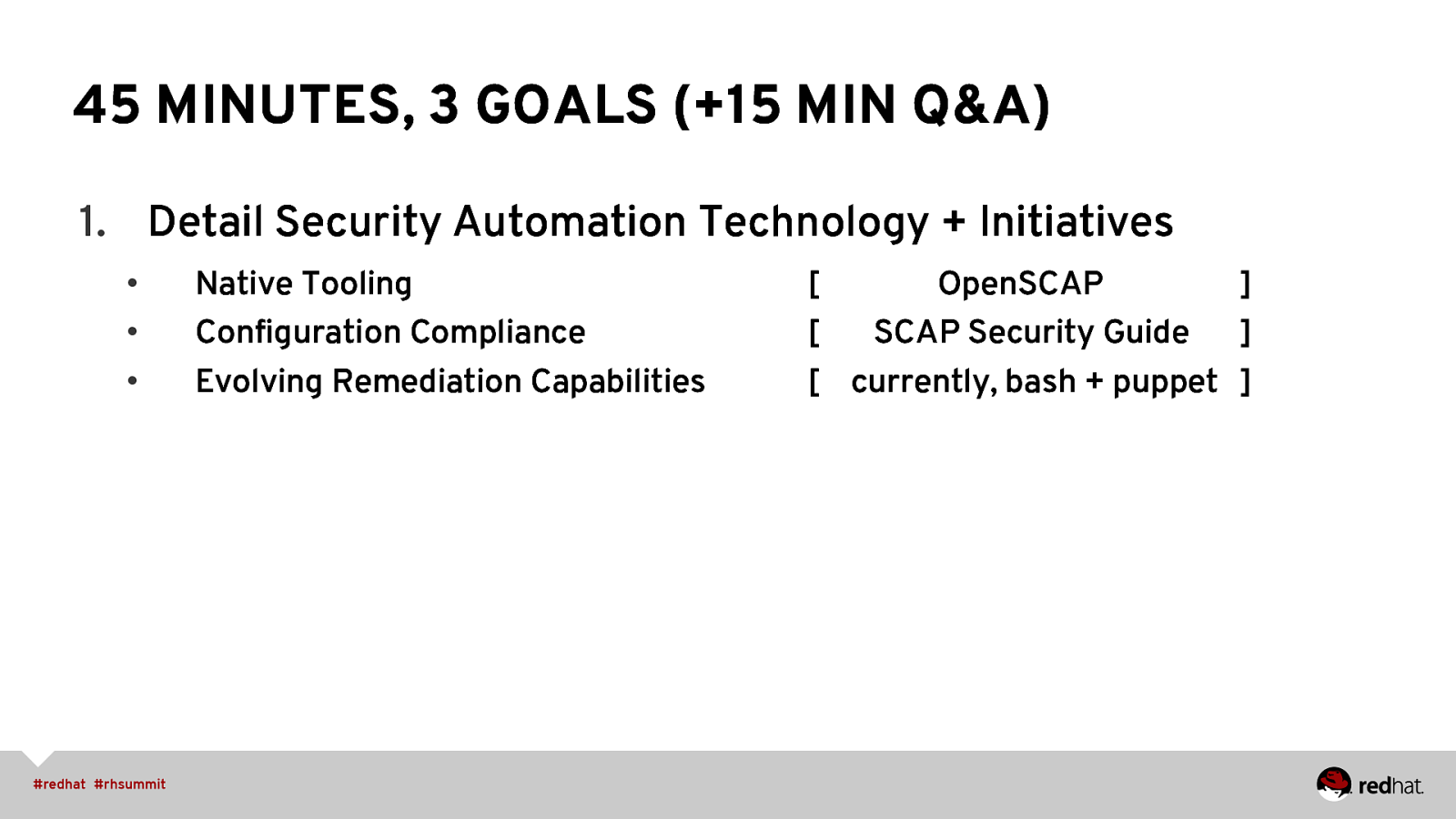
45 MINUTES, 3 GOALS (+15 MIN Q&A) 1. Detail Security Automation Technology + Initiatives • • • Native Tooling Configuration Compliance Evolving Remediation Capabilities [ OpenSCAP ] [ SCAP Security Guide ] [ currently, bash + puppet ]
Slide 3
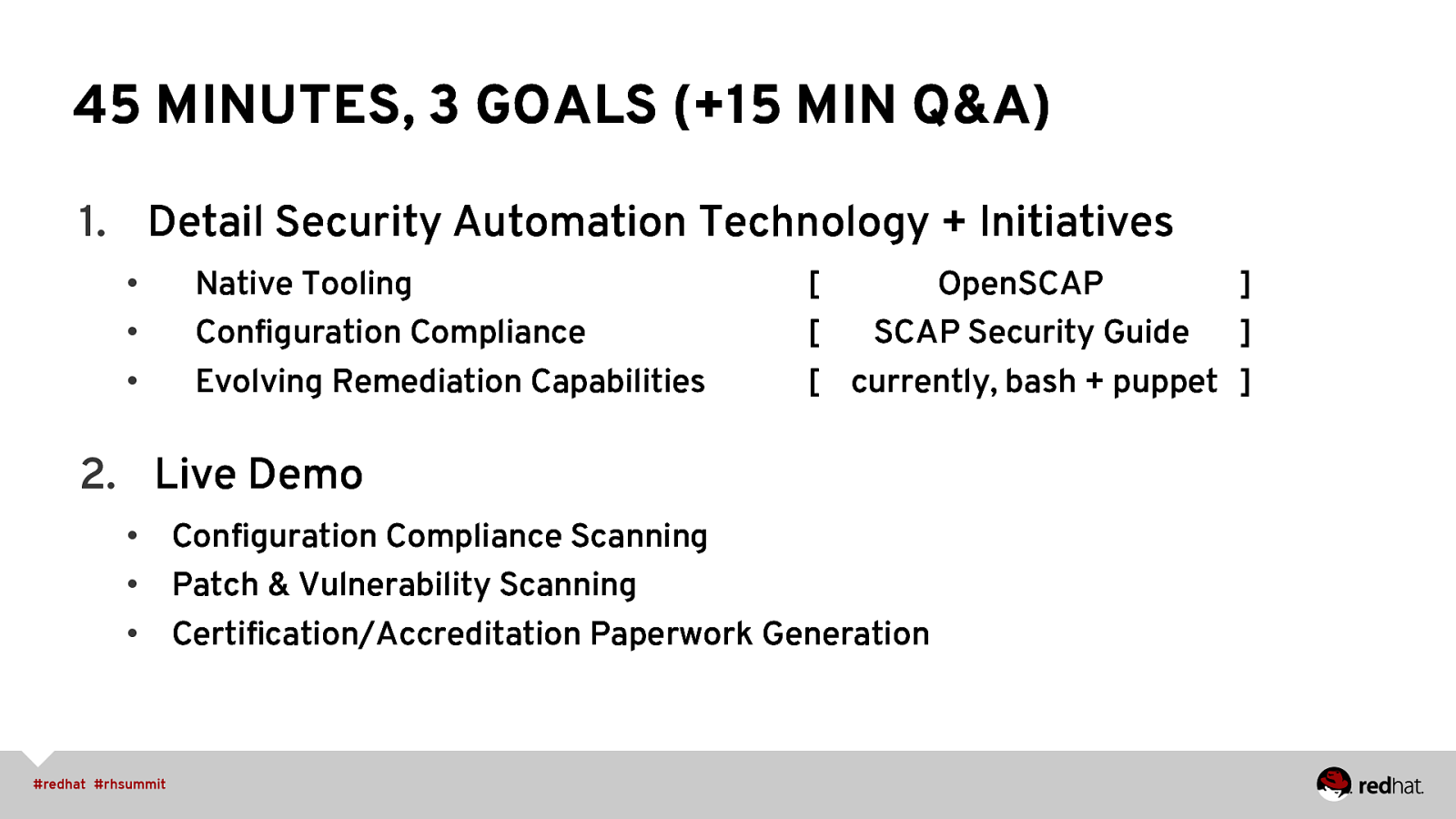
45 MINUTES, 3 GOALS (+15 MIN Q&A) 1. Detail Security Automation Technology + Initiatives • • • Native Tooling Configuration Compliance Evolving Remediation Capabilities [ OpenSCAP ] [ SCAP Security Guide ] [ currently, bash + puppet ] 2. Live Demo • Configuration Compliance Scanning • Patch & Vulnerability Scanning • Certification/Accreditation Paperwork Generation
Slide 4
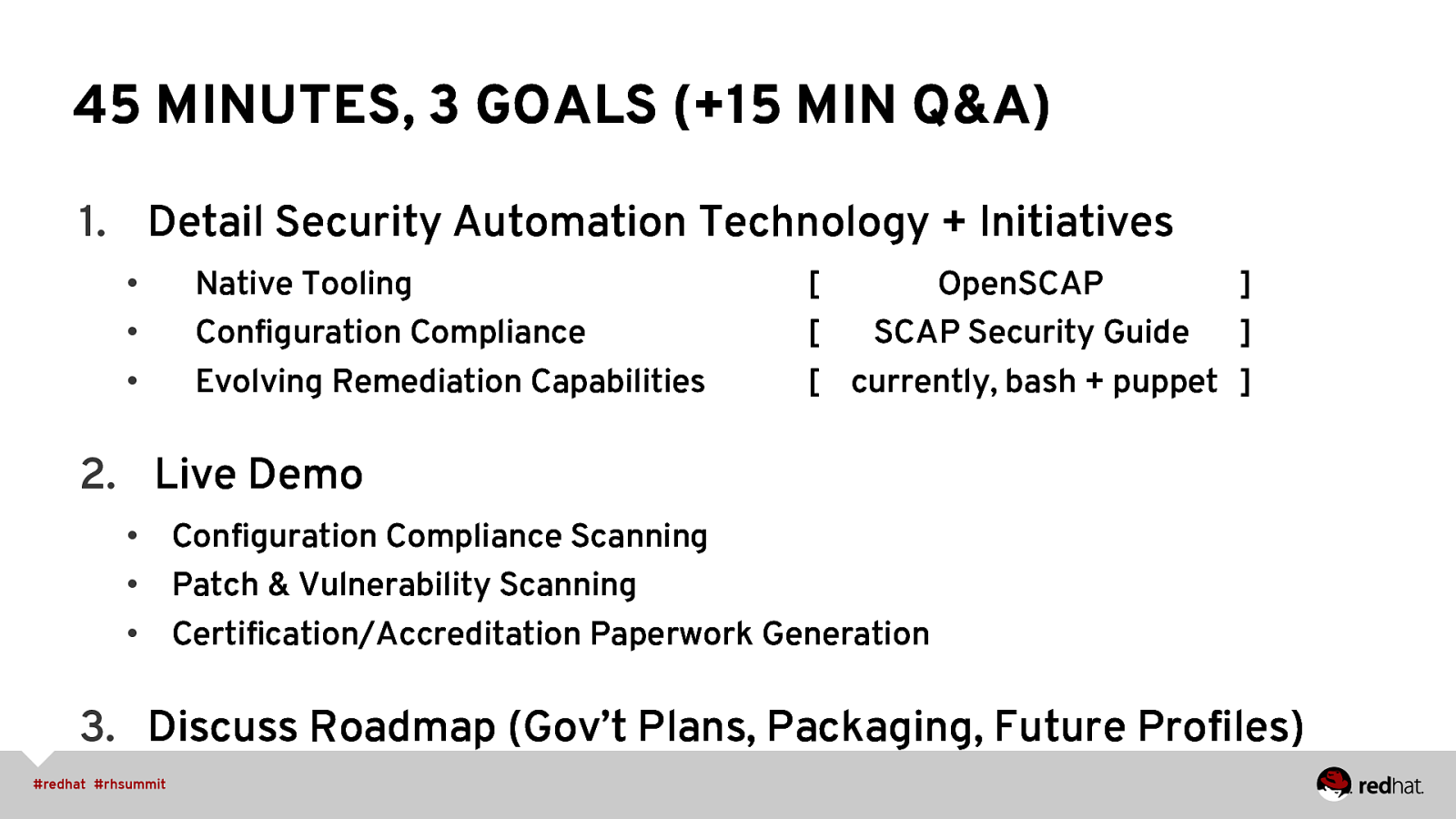
45 MINUTES, 3 GOALS (+15 MIN Q&A) 1. Detail Security Automation Technology + Initiatives • • • Native Tooling Configuration Compliance Evolving Remediation Capabilities [ OpenSCAP ] [ SCAP Security Guide ] [ currently, bash + puppet ] 2. Live Demo • Configuration Compliance Scanning • Patch & Vulnerability Scanning • Certification/Accreditation Paperwork Generation 3. Discuss Roadmap (Gov’t Plans, Packaging, Future Profiles)
Slide 5
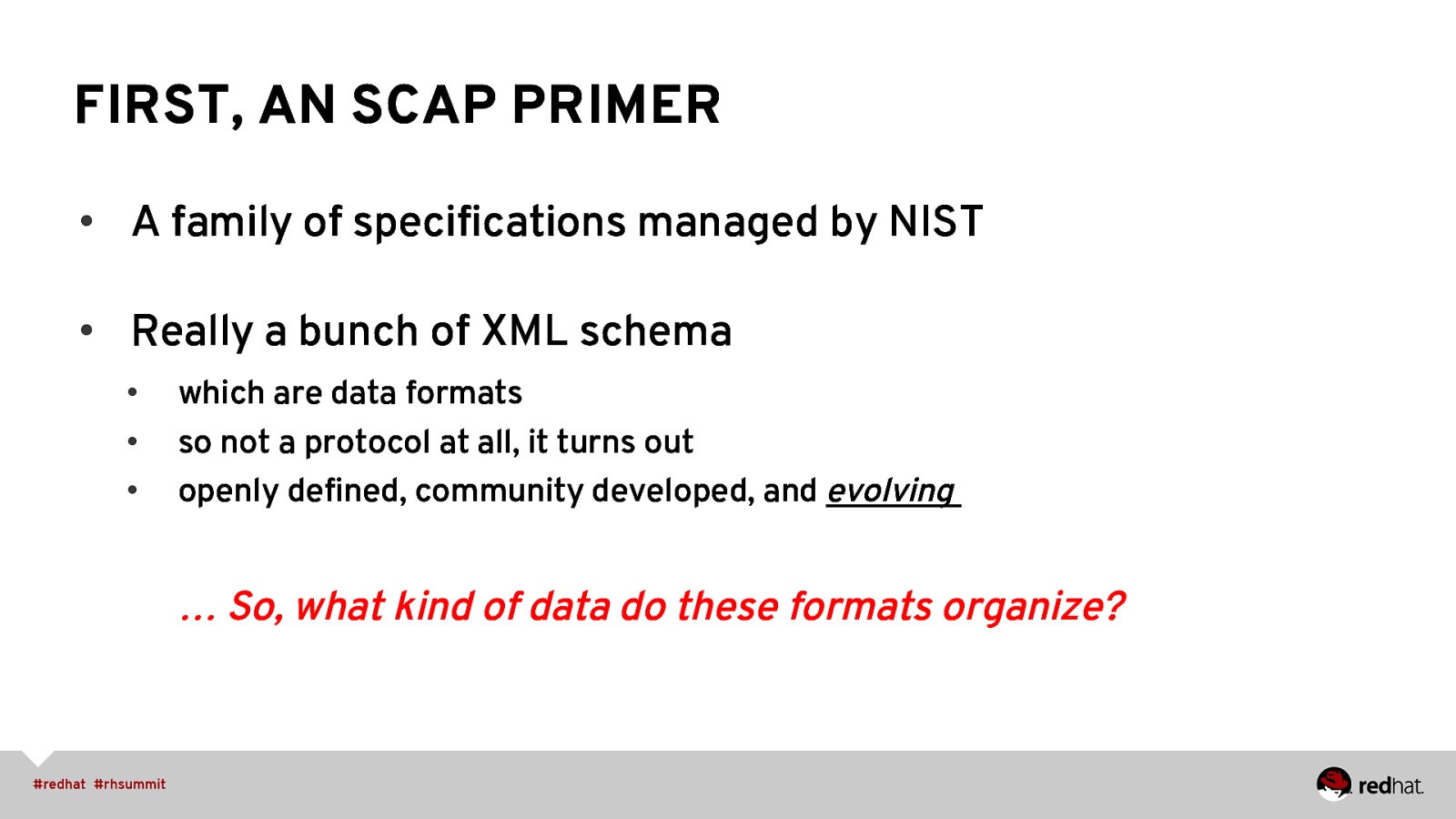
FIRST, AN SCAP PRIMER • A family of specifications managed by NIST • Really a bunch of XML schema • • • which are data formats so not a protocol at all, it turns out openly defined, community developed, and evolving … So, what kind of data do these formats organize?
Slide 6

FIRST, AN SCAP PRIMER • Defines standardized formats … okay, but why bother? • Because you’ll get: • • Standardized inputs (e.g. a compliance baseline, status query) Standardized outputs (results) • Provides the enterprise liberty with regard to product choices • • • Avoids vendor lock-in, enables interoperability Provides common technical position to vendors Federal procurement language requires SCAP support in some cases
Slide 7

SCAP Security Guide https://fedorahosted.org/scap-security-guide/
Slide 8

Contributors Include…
Slide 9

In A Nutshell, SCAP Security Guide… … has had 2,408 commits from 36 contributors, representing 224,872 lines of code … took an estimated 43 years of effort (COCOMO model) … has become upstream for all Red Hat STIGs, NIST NVD for JBoss, NSA’s RHEL SNAC Guides
Slide 10

DISA STIG, Version 1, Release 2, Section 1.1: “The consensus content was developed using an open source project called SCAP Security Guide. The project’s website is https://fedorahosted.org/scap-security-guide/. Except for differences in formatting to accommodate the DISA STIG publishing process, the content of the RHEL6 STIG should mirror the SCAP Security Guide content with only minor divergences as updates from multiple sources work through the consensus process”
Slide 11
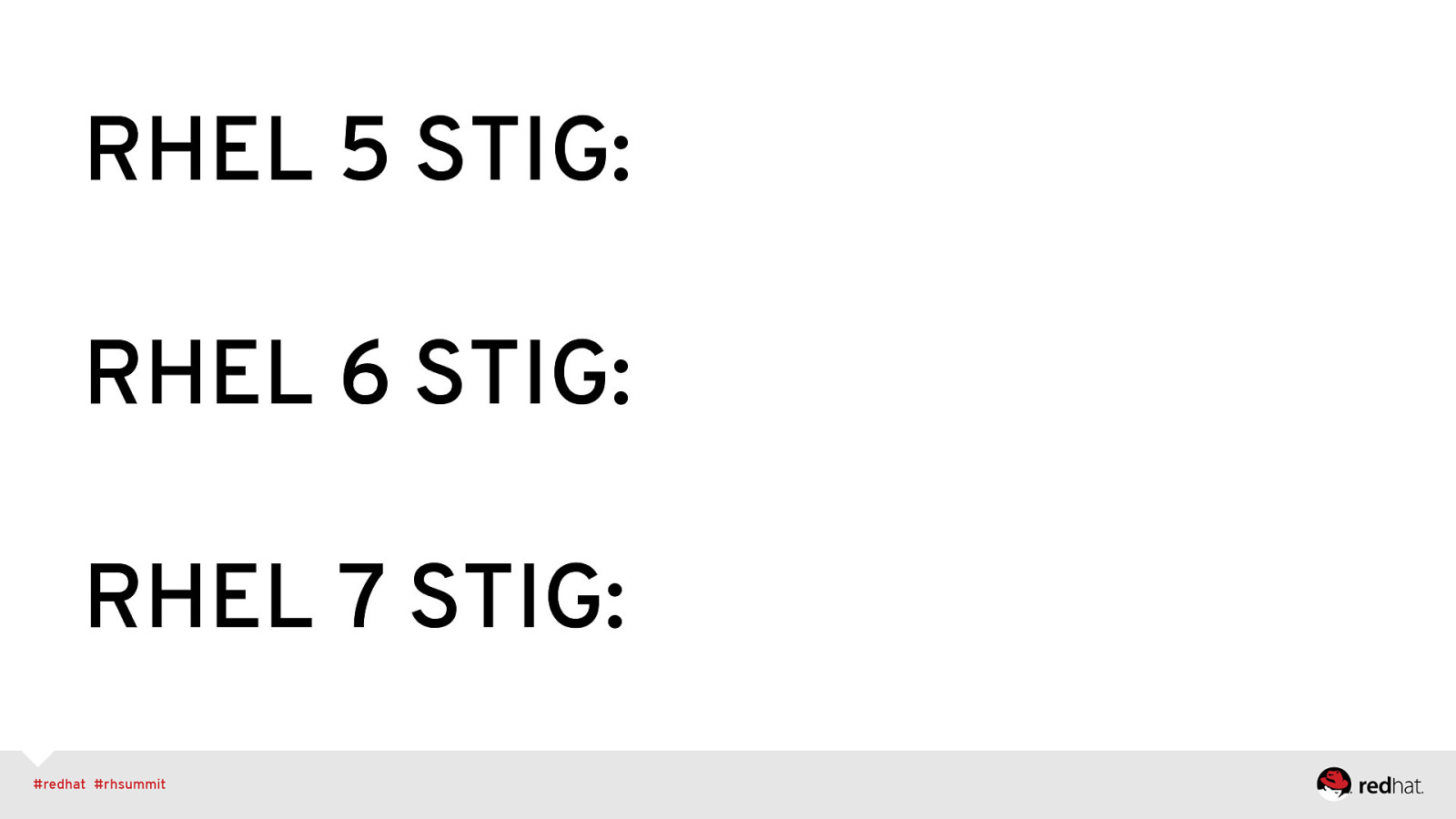
RHEL 5 STIG: RHEL 6 STIG: RHEL 7 STIG:
Slide 12
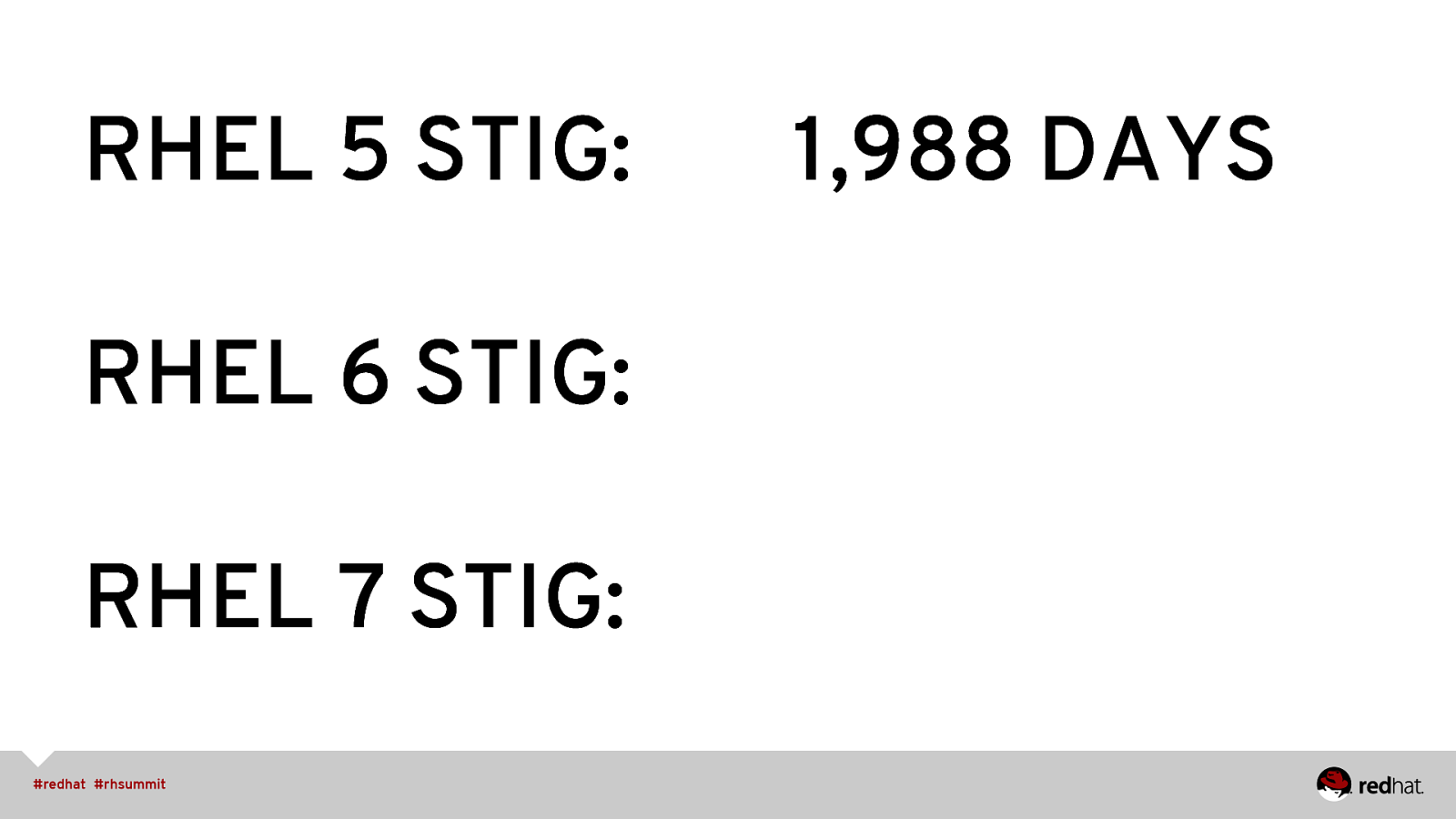
RHEL 5 STIG: RHEL 6 STIG: RHEL 7 STIG: 1,988 DAYS
Slide 13

RHEL 5 STIG: 1,988 DAYS RHEL 6 STIG: 932 DAYS RHEL 7 STIG:
Slide 14

RHEL 5 STIG: 1,988 DAYS RHEL 6 STIG: 932 DAYS RHEL 7 STIG: +/- 90 DAYS
Slide 15

TECH + INITIATIVES Native Tooling, Configuration Compliance, Evolving Remediation Capabilities
Slide 16
TOOLS vs CONTENT
Slide 17

OpenSCAP
Slide 18
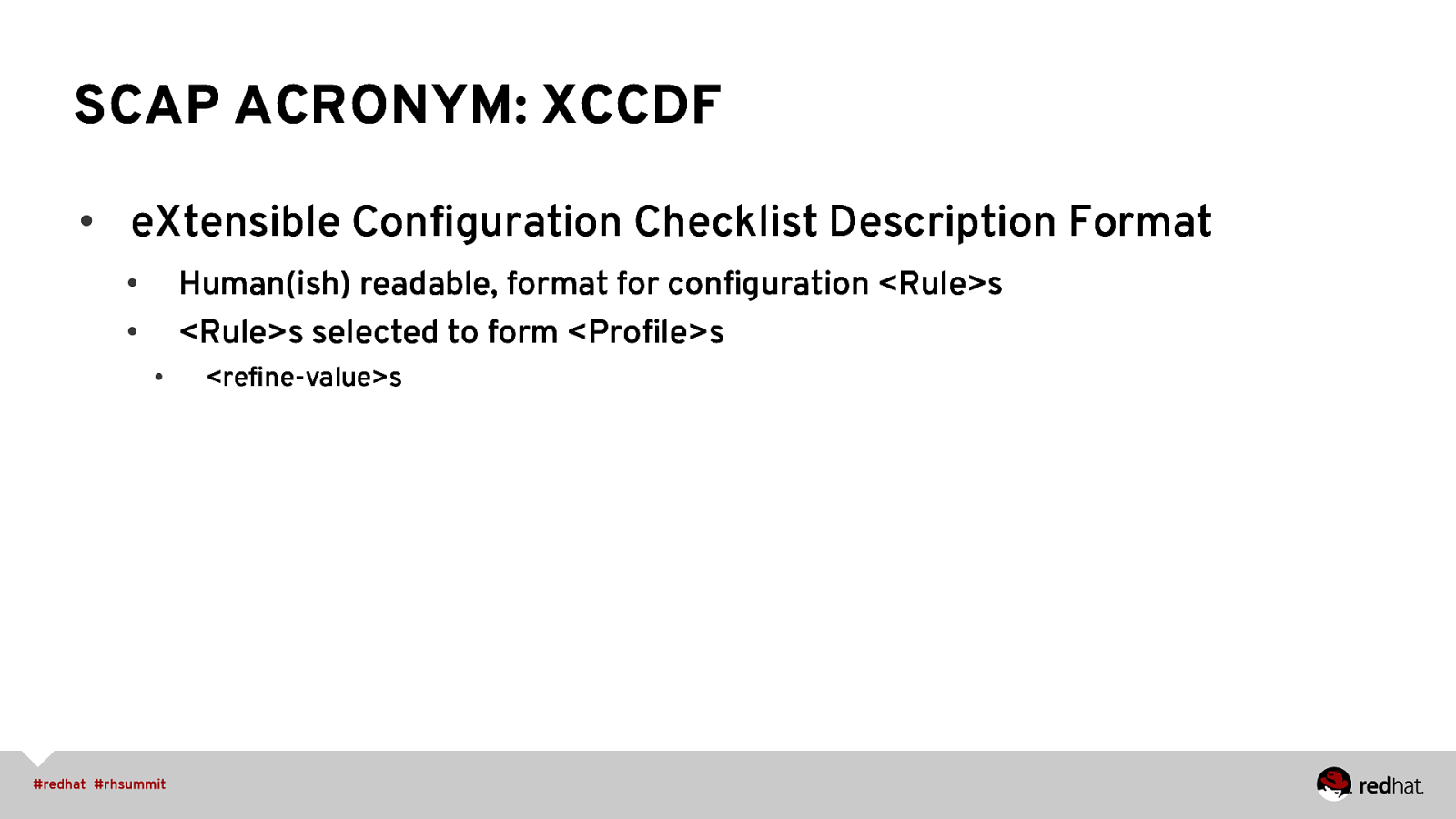
SCAP ACRONYM: XCCDF • eXtensible Configuration Checklist Description Format Human(ish) readable, format for configuration <Rule>s <Rule>s selected to form <Profile>s • • • <refine-value>s
Slide 19
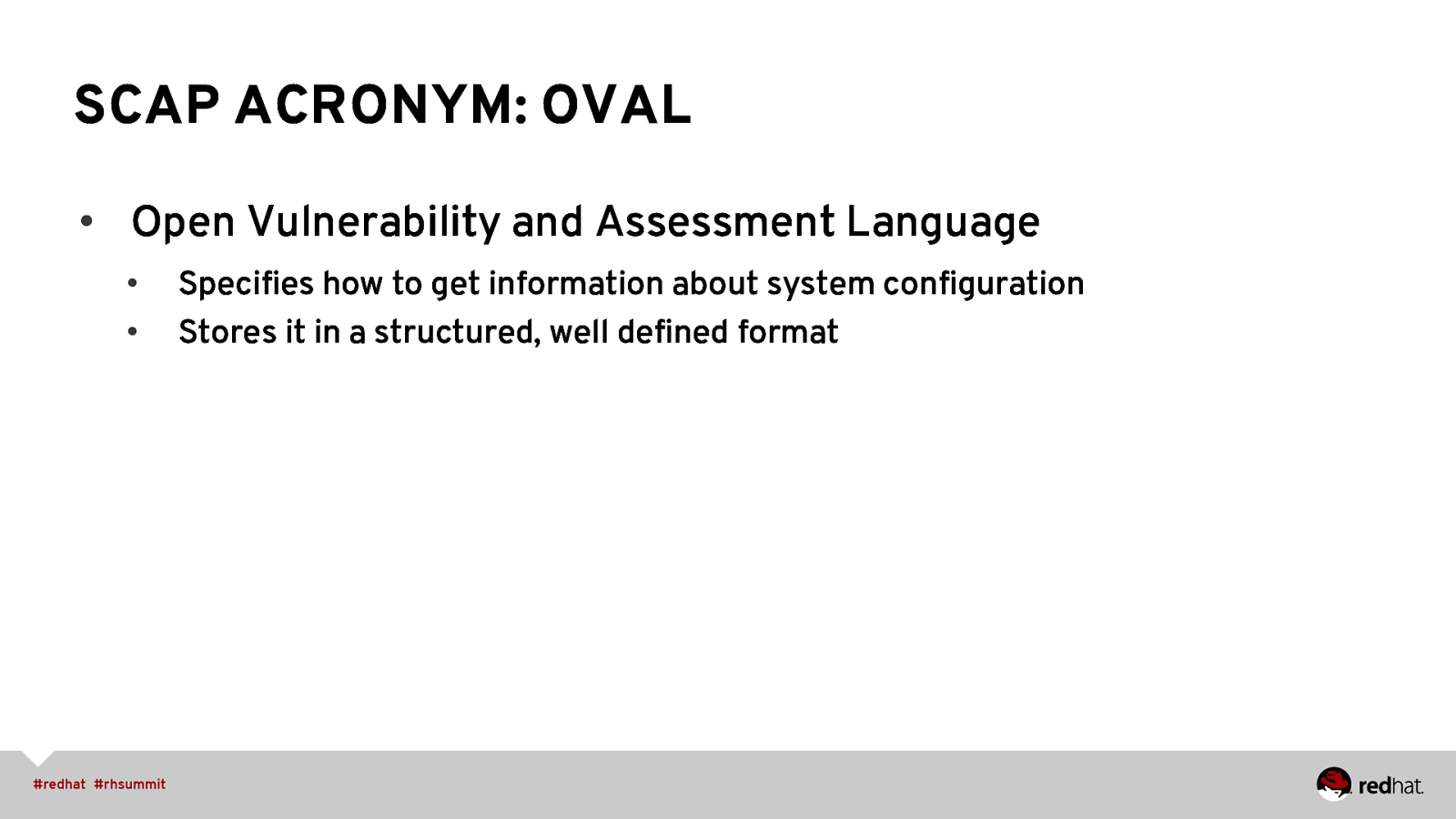
SCAP ACRONYM: OVAL • Open Vulnerability and Assessment Language • • Specifies how to get information about system configuration Stores it in a structured, well defined format
Slide 20
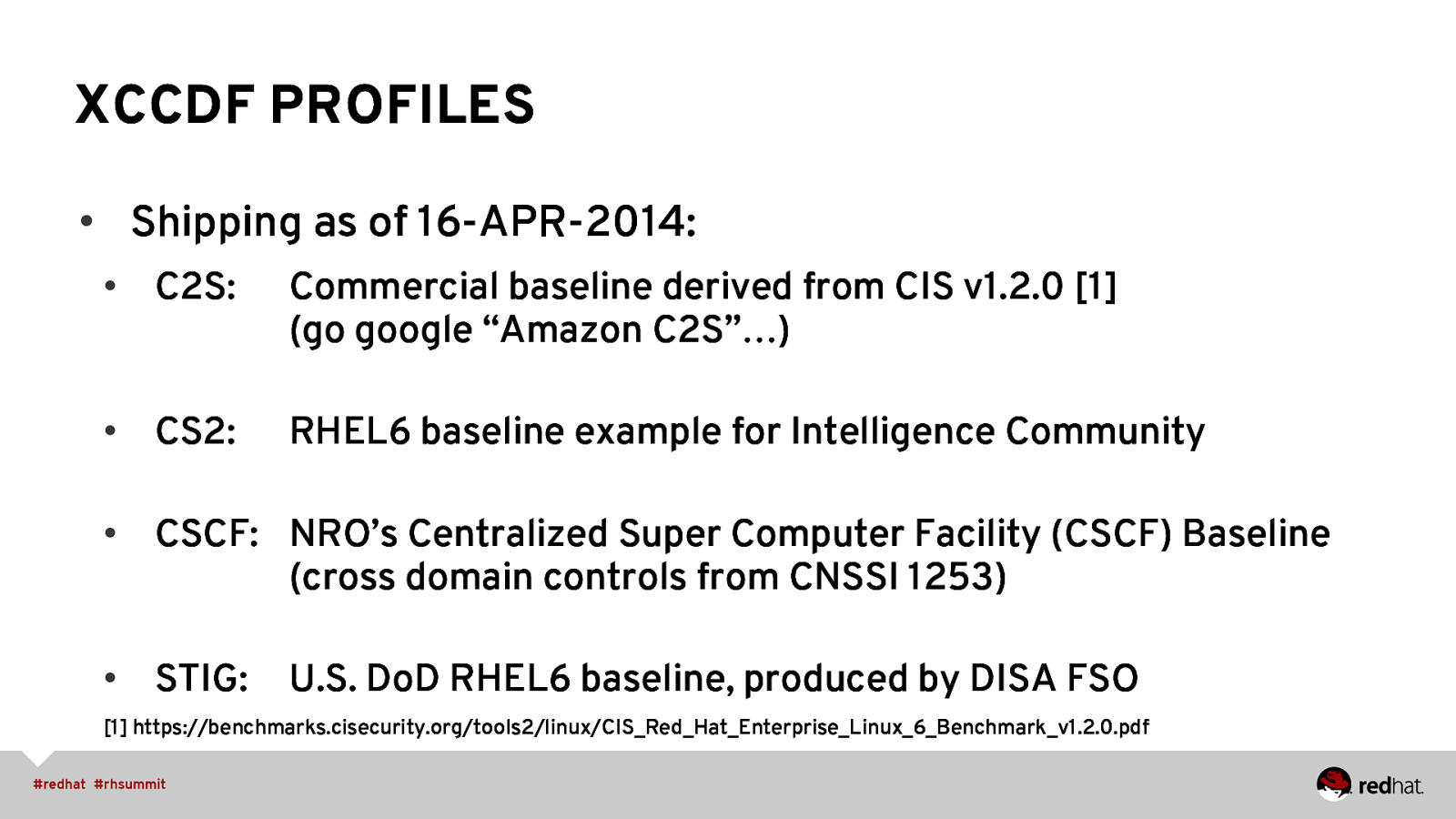
XCCDF PROFILES • Shipping as of 16-APR-2014: • C2S: Commercial baseline derived from CIS v1.2.0 [1] (go google “Amazon C2S”…) • CS2: RHEL6 baseline example for Intelligence Community • CSCF: NRO’s Centralized Super Computer Facility (CSCF) Baseline (cross domain controls from CNSSI 1253) • STIG: U.S. DoD RHEL6 baseline, produced by DISA FSO [1] https://benchmarks.cisecurity.org/tools2/linux/CIS_Red_Hat_Enterprise_Linux_6_Benchmark_v1.2.0.pdf
Slide 21

REMEDIATION CAPABILITIES • Bash first <fix system=”urn:xccdf:fix:script:sh”> yum -y install screen </fix>
Slide 22
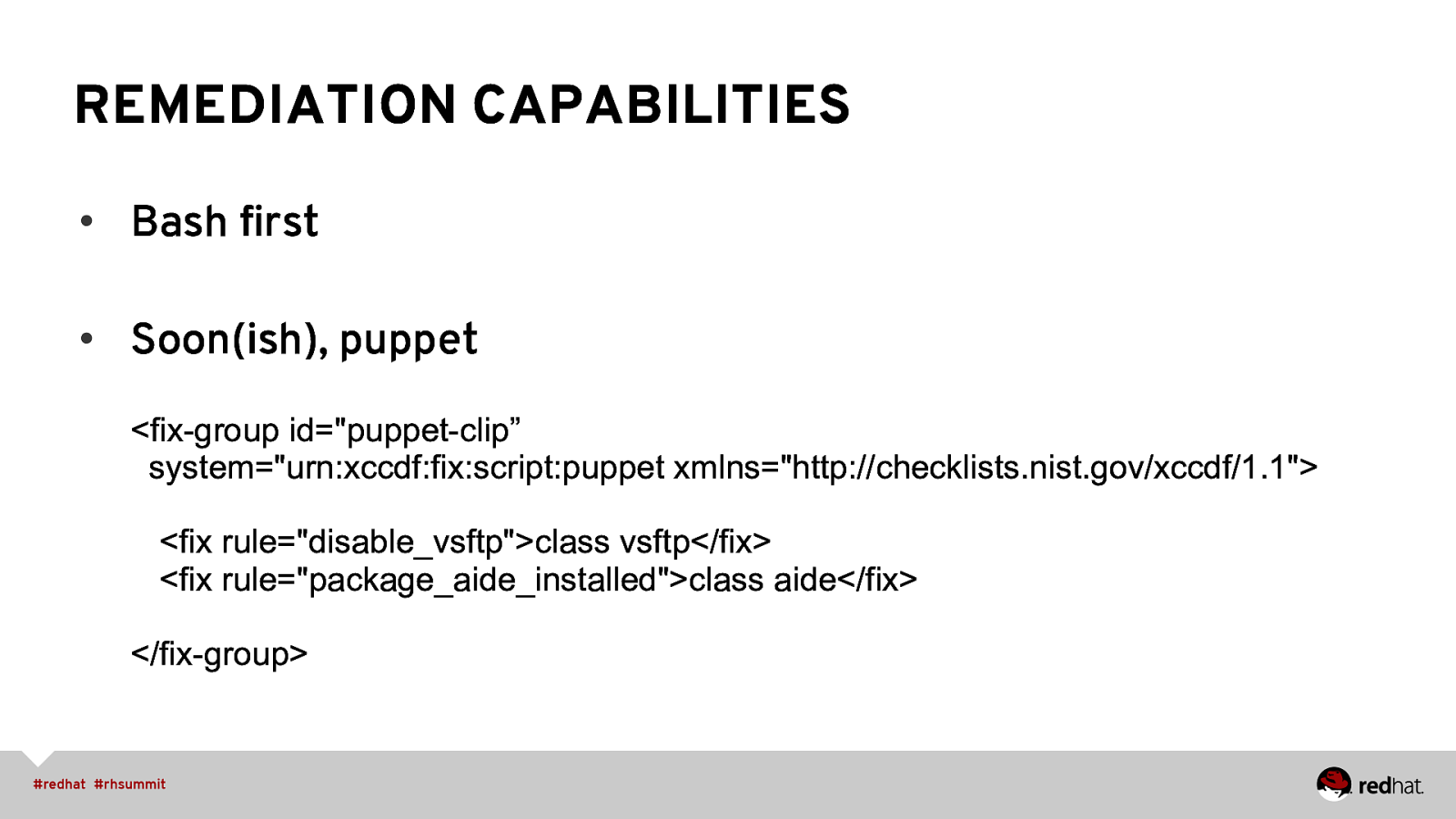
REMEDIATION CAPABILITIES • Bash first • Soon(ish), puppet <fix-group id=”puppet-clip” system=”urn:xccdf:fix:script:puppet xmlns=”http://checklists.nist.gov/xccdf/1.1”> <fix rule=”disable_vsftp”>class vsftp</fix> <fix rule=”package_aide_installed”>class aide</fix> </fix-group>
Slide 23
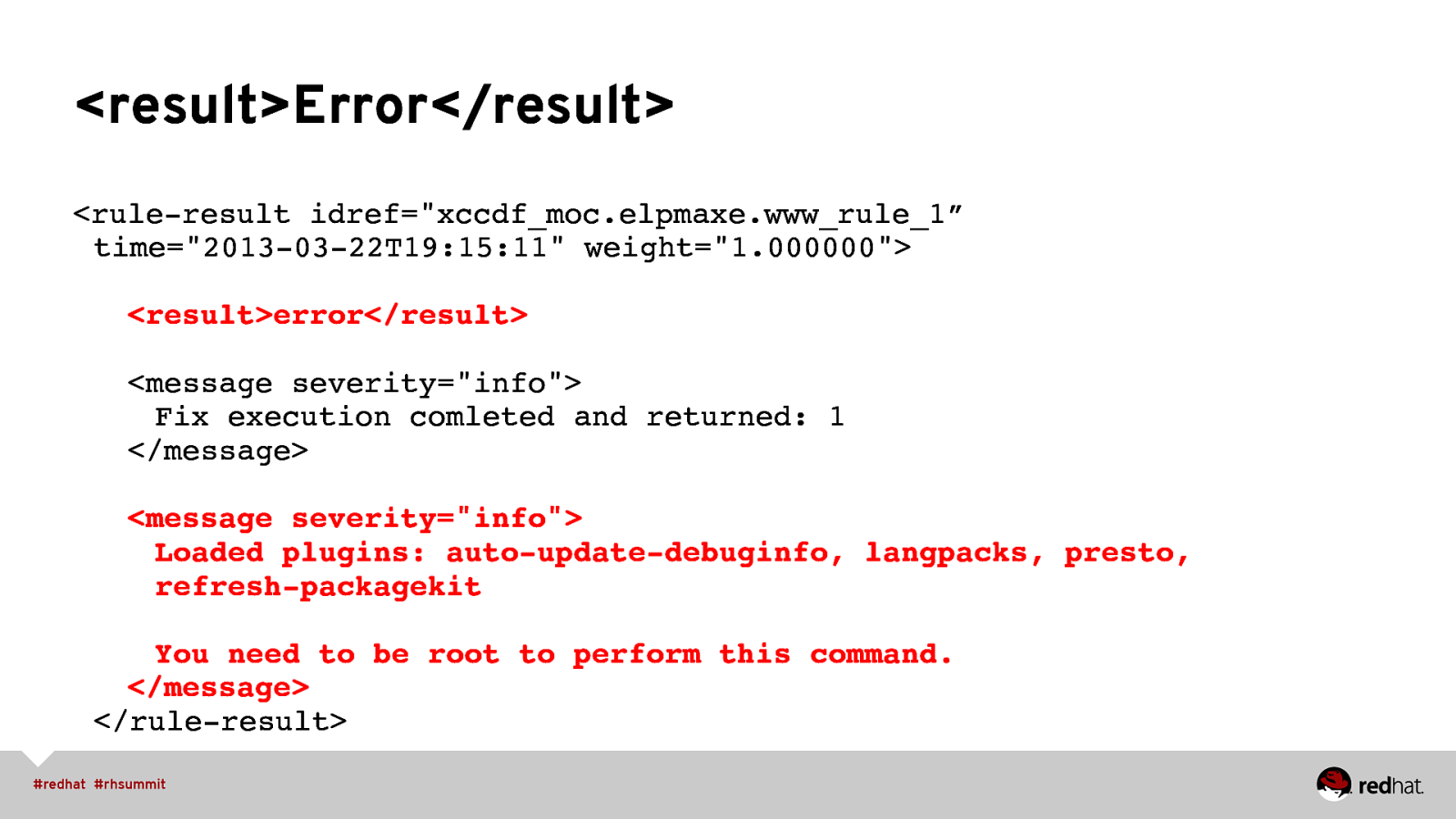
<result>Error</result> <rule-result idref=”xccdf_moc.elpmaxe.www_rule_1” time=”2013-03-22T19:15:11” weight=”1.000000”> ” “<result>error</result> ” “<message severity=”info”> ” ” “Fix execution comleted and returned: 1 ” “</message> ” “<message severity=”info”> ” ” “Loaded plugins: auto-update-debuginfo, langpacks, presto, ” ” “refresh-packagekit ” ” “You need to be root to perform this command. ” “</message> </rule-result>”
Slide 24
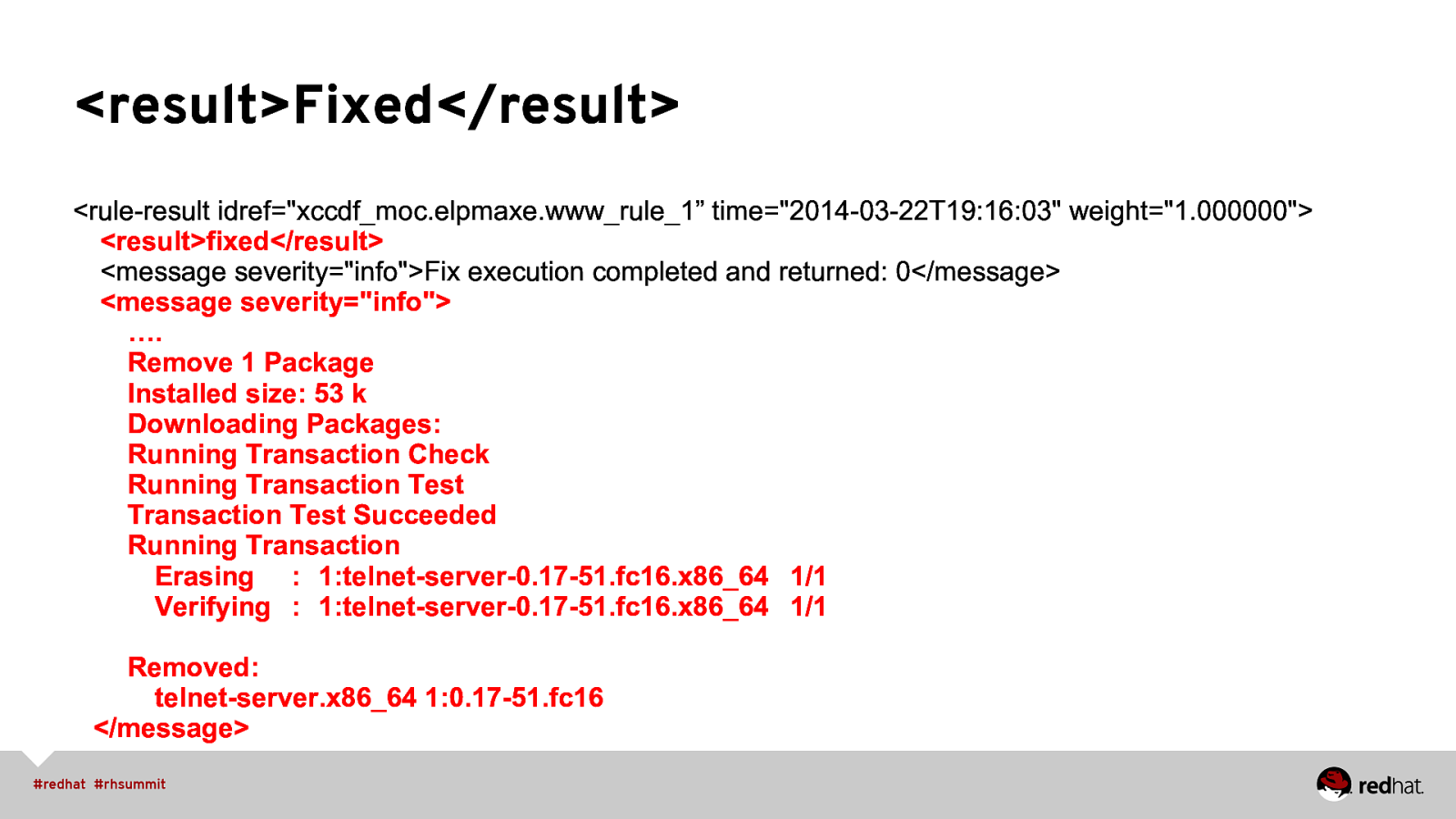
<result>Fixed</result> <rule-result idref=”xccdf_moc.elpmaxe.www_rule_1” time=”2014-03-22T19:16:03” weight=”1.000000”> <result>fixed</result> <message severity=”info”>Fix execution completed and returned: 0</message> <message severity=”info”> …. Remove 1 Package Installed size: 53 k Downloading Packages: Running Transaction Check Running Transaction Test Transaction Test Succeeded Running Transaction Erasing : 1:telnet-server-0.17-51.fc16.x86_64 1/1 Verifying : 1:telnet-server-0.17-51.fc16.x86_64 1/1 Removed: telnet-server.x86_64 1:0.17-51.fc16 </message>
Slide 25

REMEDIATION REVIEW • Bash first • Soon(ish), puppet • Reference Šimon Lukašík’s blog for a great write-up: http://isimluk.livejournal.com/3573.html • Thank you Peter Vrabec & Martin Preisler for the work on OpenSCAP!
Slide 26

LIVE DEMO Patch & vuln. Scanning, configuration baseline scanning, Certification & Accreditation Paperwork Generation
Slide 27

ROADMAP Gov’t Initiatives, SSG Packaging, Future Profiles
Slide 28

Government Initiatives • Continuous Diagnostics and Mitigations (CDM) http://www.dhs.gov/cdm • SCAP path forward • Evaluation + Configuration activities for Certification and Accreditation
Slide 29

RPM Packaging • Currently in EPEL, both Fedora and RHEL (thank you, Jan Lieskovsky!) • SSG scheduled to ship in RHEL 6.6 • https://bugzilla.redhat.com/show_bug.cgi?id=1038655 • RHEL 7 GA
Slide 30

SCAP + Anaconda Integration • <fix> elements targeting installation process • Kickstart support allowing specification of SCAP content • UI screen(s) that provide ways to set values • Project started as Vratislav Podzimek’s masters thesis http://is.muni.cz/th/324874/fi_m/?lang=en (thanks, Vratislav!) • https://fedorahosted.org/oscap-anaconda-addon/
Slide 31
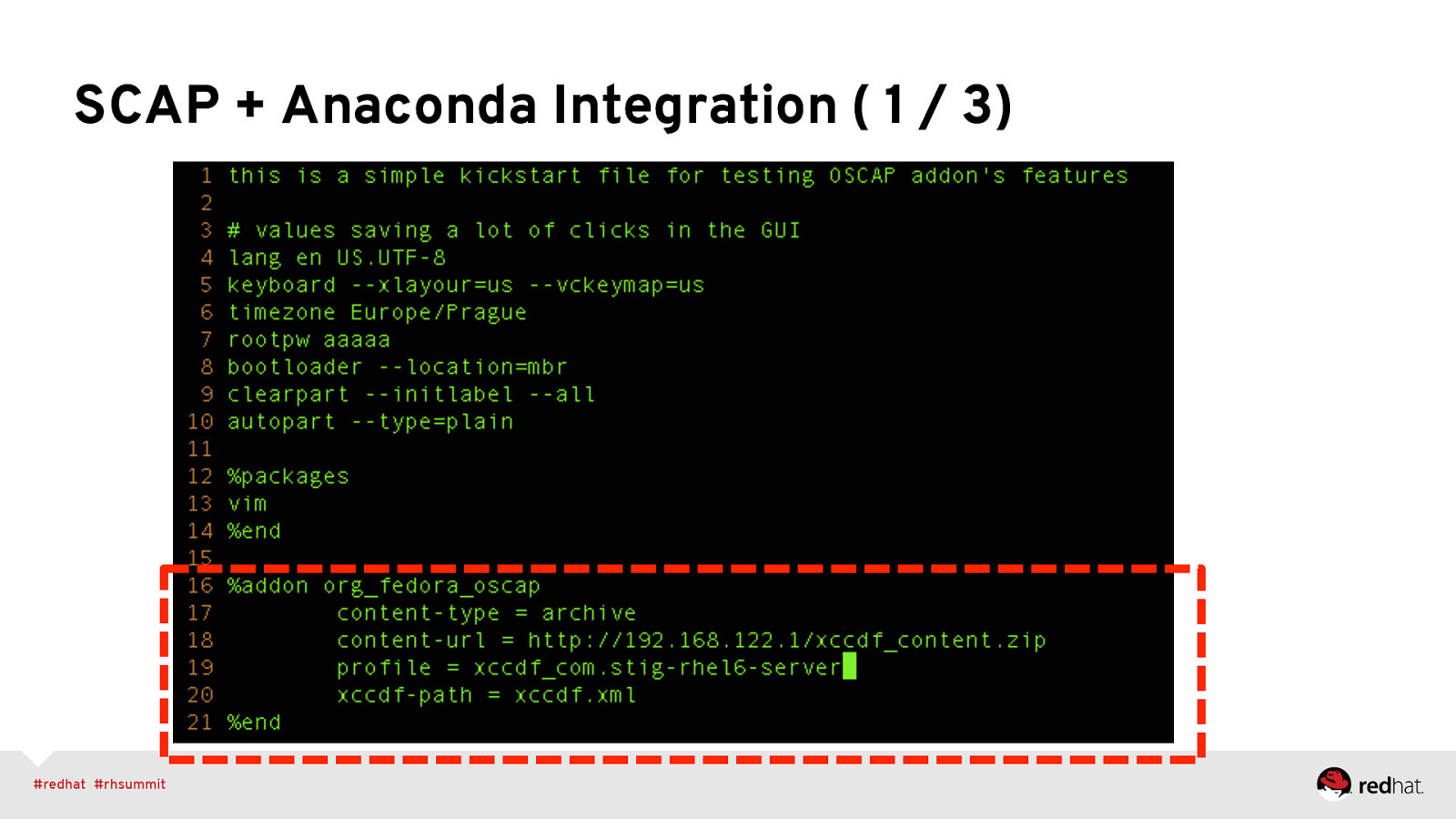
SCAP + Anaconda Integration ( 1 / 3)
Slide 32
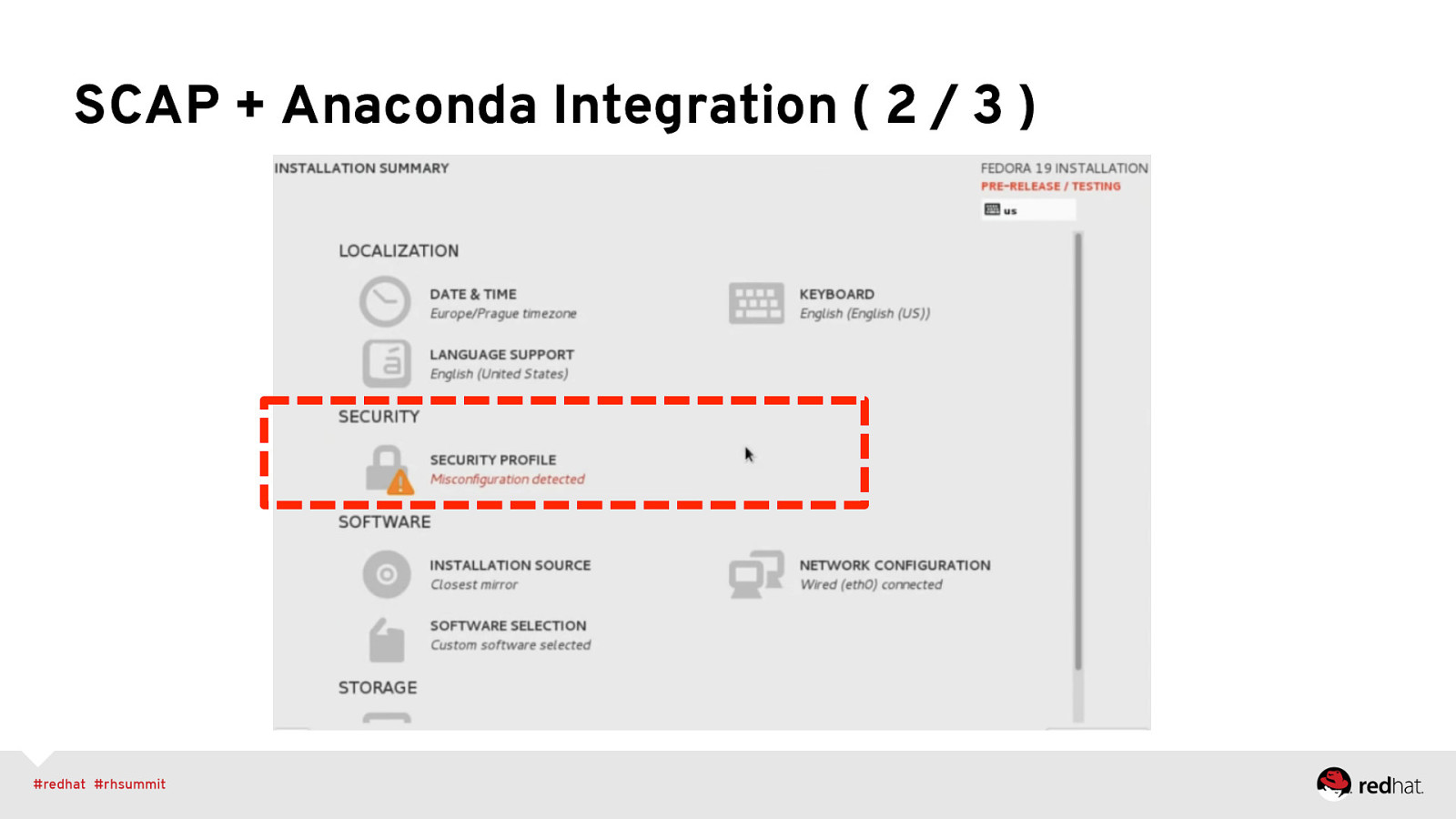
SCAP + Anaconda Integration ( 2 / 3 )
Slide 33
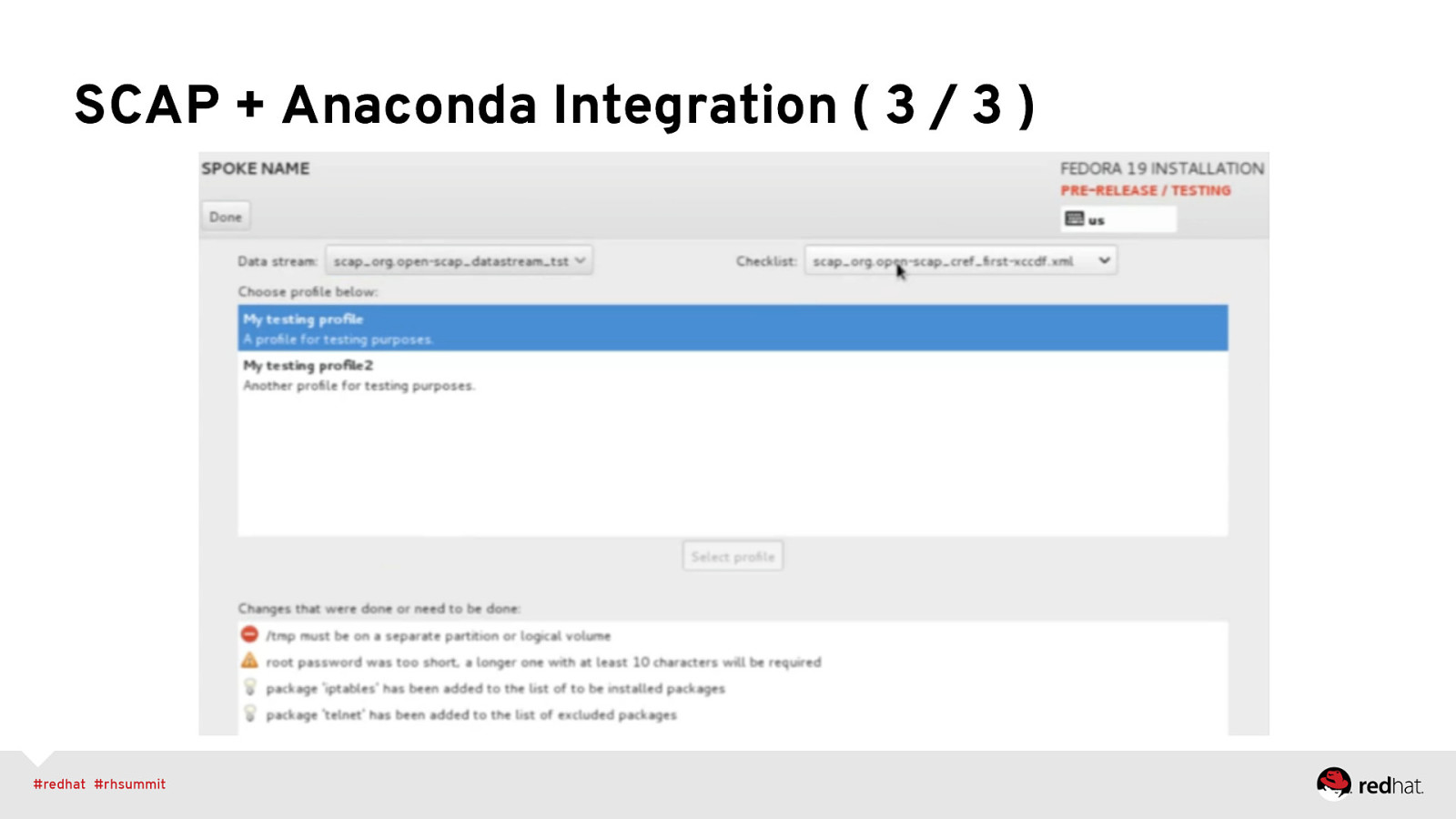
SCAP + Anaconda Integration ( 3 / 3 )
Slide 34

SCAP Workbench GUI tool that serves as an SCAP scanner and provides tailoring functionality. Primary Goals: • Lower the initial barrier of using SCAP. • Great for hand-tuning content before enterprise deployment (e.g. via spacewalk/RHN Satellite) https://fedorahosted.org/scap-workbench/
Slide 35
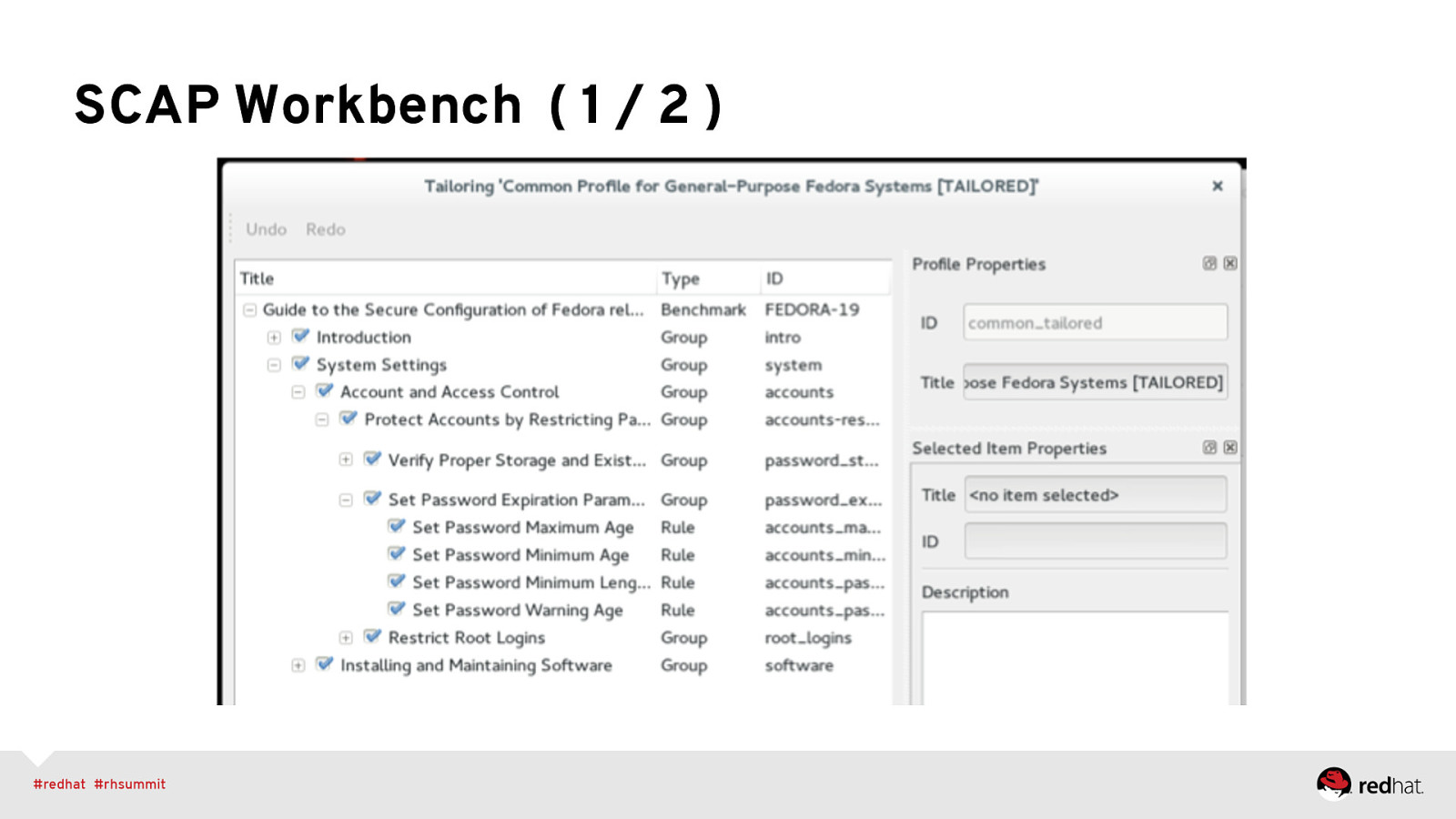
SCAP Workbench ( 1 / 2 )
Slide 36
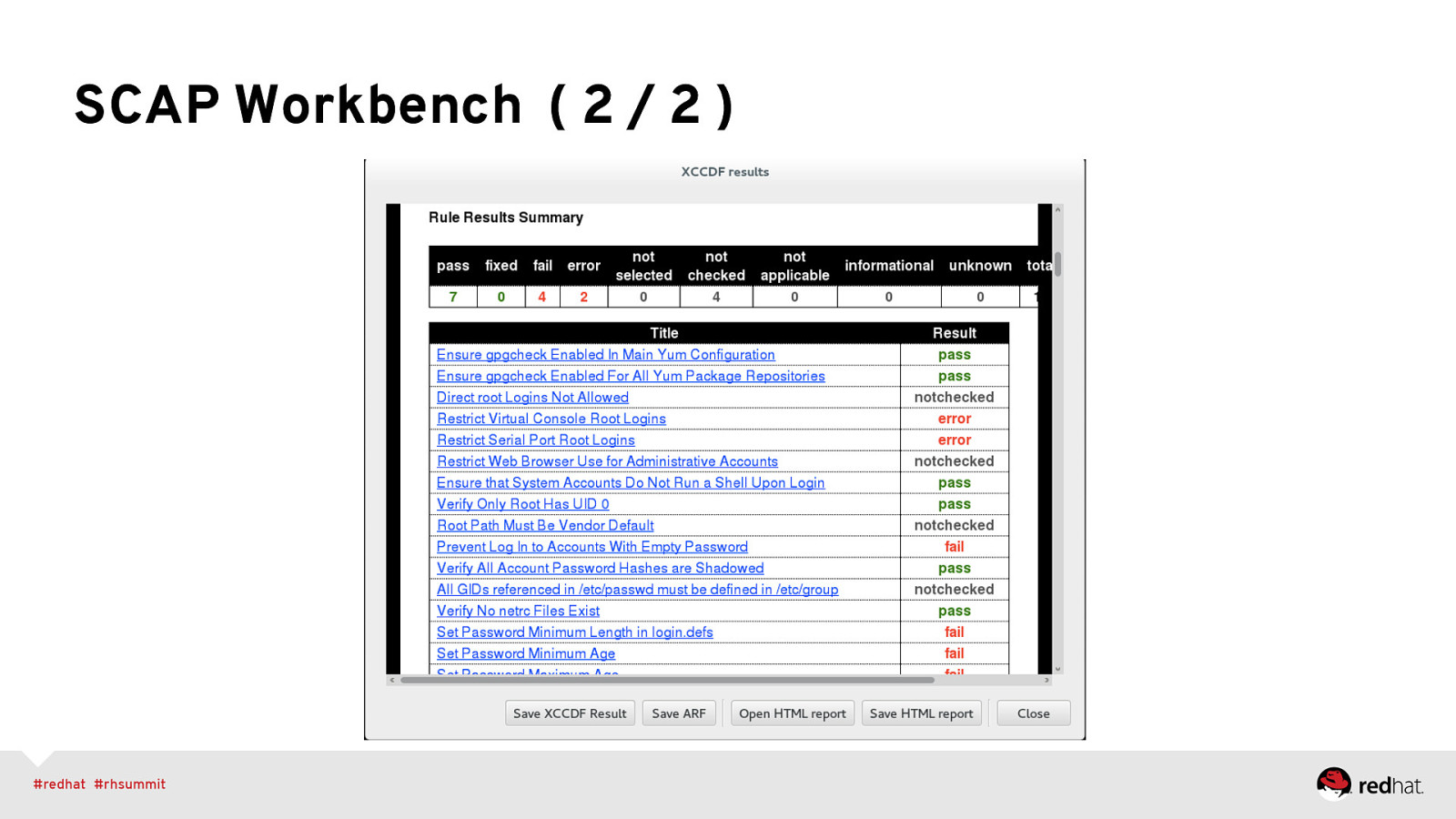
SCAP Workbench ( 2 / 2 )
Slide 37

37
Slide 38

SUPPLEMENTAL Helpful Links
Slide 39

Helpful Links (to community projects) • SCAP Security Guide: https://fedorahosted.org/scap-security-guide/ • OpenSCAP: http://open-scap.org/ • OSCAP Anaconda: https://fedorahosted.org/oscap-anaconda-addon/ • SCAP Workbench: https://fedorahosted.org/scap-workbench/
Slide 40

Helpful Links (to government baselines) • DISA’s Security Technical Implementation Guides (STIGs) http://iase.disa.mil/stigs/ • NIST National Checklist Program Repository http://web.nvd.nist.gov/view/ncp/repository • NSA Security Configuration Guides http://www.nsa.gov/ia/mitigation_guidance/security_configuration_guides/
Slide 41
Helpful Links (to communities of interest) • Red Hat’s Government Security User Group (gov-sec) http://www.redhat.com/mailman/listinfo/gov-sec • Military Open Source Software (Mil-OSS) http://mil-oss.org/
Slide 42
Replicating the Demo - Assumes RHEL 6 and EPEL already enabled! - Assumes httpd installed, DocumentRoot /var/www/html/ - My IP was 10.211.55.3. Change as appropriate. - This is meant to replicate the demo, not fully explain it. Come to Summit next year!
Slide 43

Step 1: Install $ yum install scap-security-guide $ rpm –ql scap-security-guide … /usr/share/doc/scap-security-guide-0.1/rhel6-guide.html … /usr/share/man/en/man8/scap-security-guide.8.gz … /usr/share/xml/scap/ssg/content … /usr/share/xml/scap/ssg/content/ssg-rhel6-ds.xml
Slide 44

Step 2: Review Prose Guide $ cp /usr/share/doc/scap-security-guide-0.1/*.html /var/www/html $ firefox http://10.211.55.3/rhel6-guide.html - Review “Check Procedure,” “Security Identifiers,” “References”
Slide 45
Step 3: JBoss, too! $ firefox http://10.211.55.3/JBossEAP5_Guide.html
Slide 46
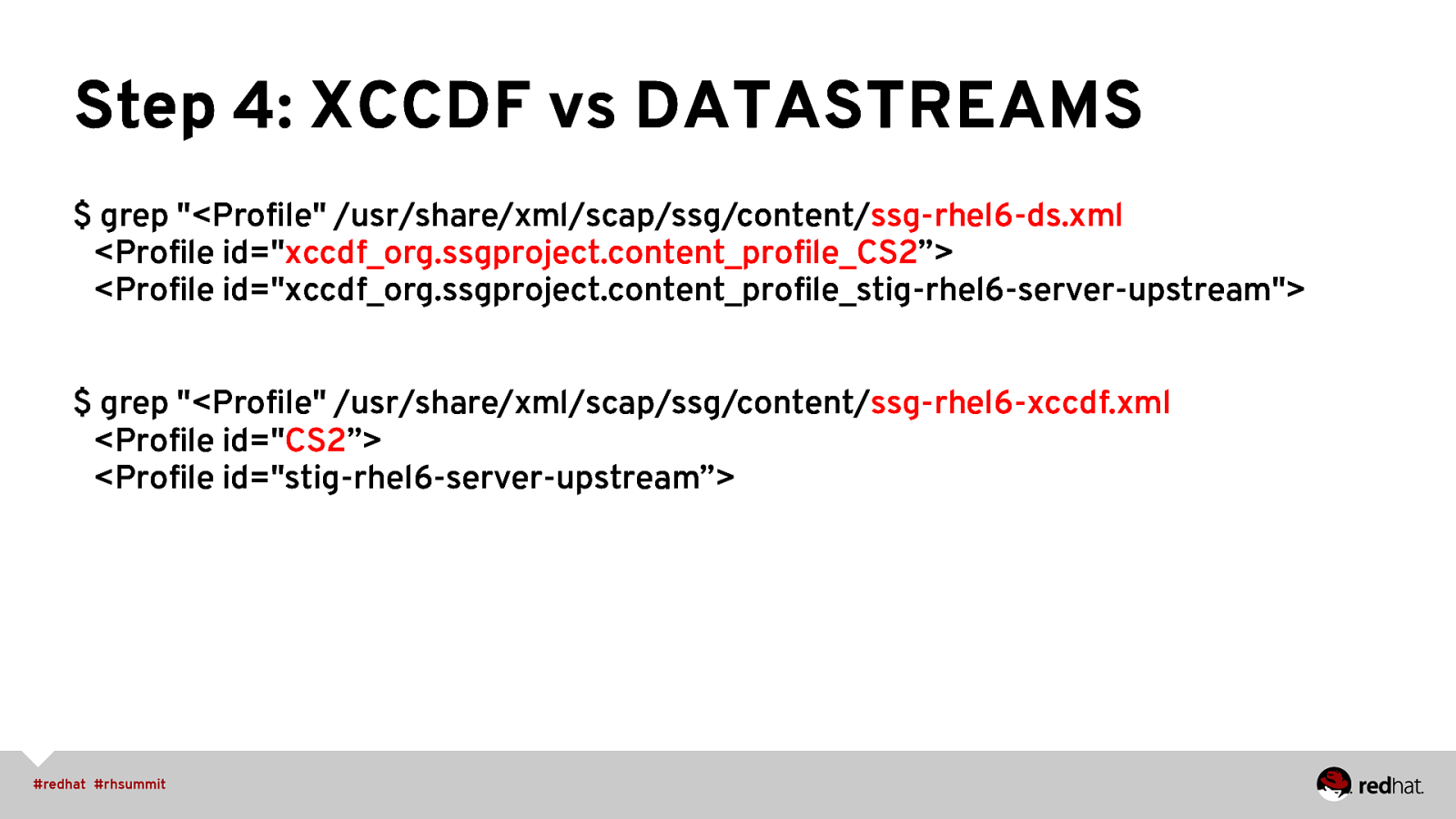
Step 4: XCCDF vs DATASTREAMS $ grep “<Profile” /usr/share/xml/scap/ssg/content/ssg-rhel6-ds.xml <Profile id=”xccdf_org.ssgproject.content_profile_CS2”> <Profile id=”xccdf_org.ssgproject.content_profile_stig-rhel6-server-upstream”> $ grep “<Profile” /usr/share/xml/scap/ssg/content/ssg-rhel6-xccdf.xml <Profile id=”CS2”> <Profile id=”stig-rhel6-server-upstream”>
Slide 47

Step 5: Run a scan! $ sudo oscap xccdf eval —profile C2S \ —cpe /usr/share/xml/scap/ssg/content/ssg-rhel6-cpe-dictionary.xml \ —report /var/www/html/summit-report.html \ —results /var/www/html/summit-results.xml \ /usr/share/xml/scap/ssg/content/ssg-rhel6-xccdf.xml Console Output: • Pass • Fail • “notchecked”: (a) not applicable; (b) no OVAL associated … and unclear which reason!
Slide 48
Step 6: HTML Results $ firefox /var/www/html/summit-report.html
Slide 49
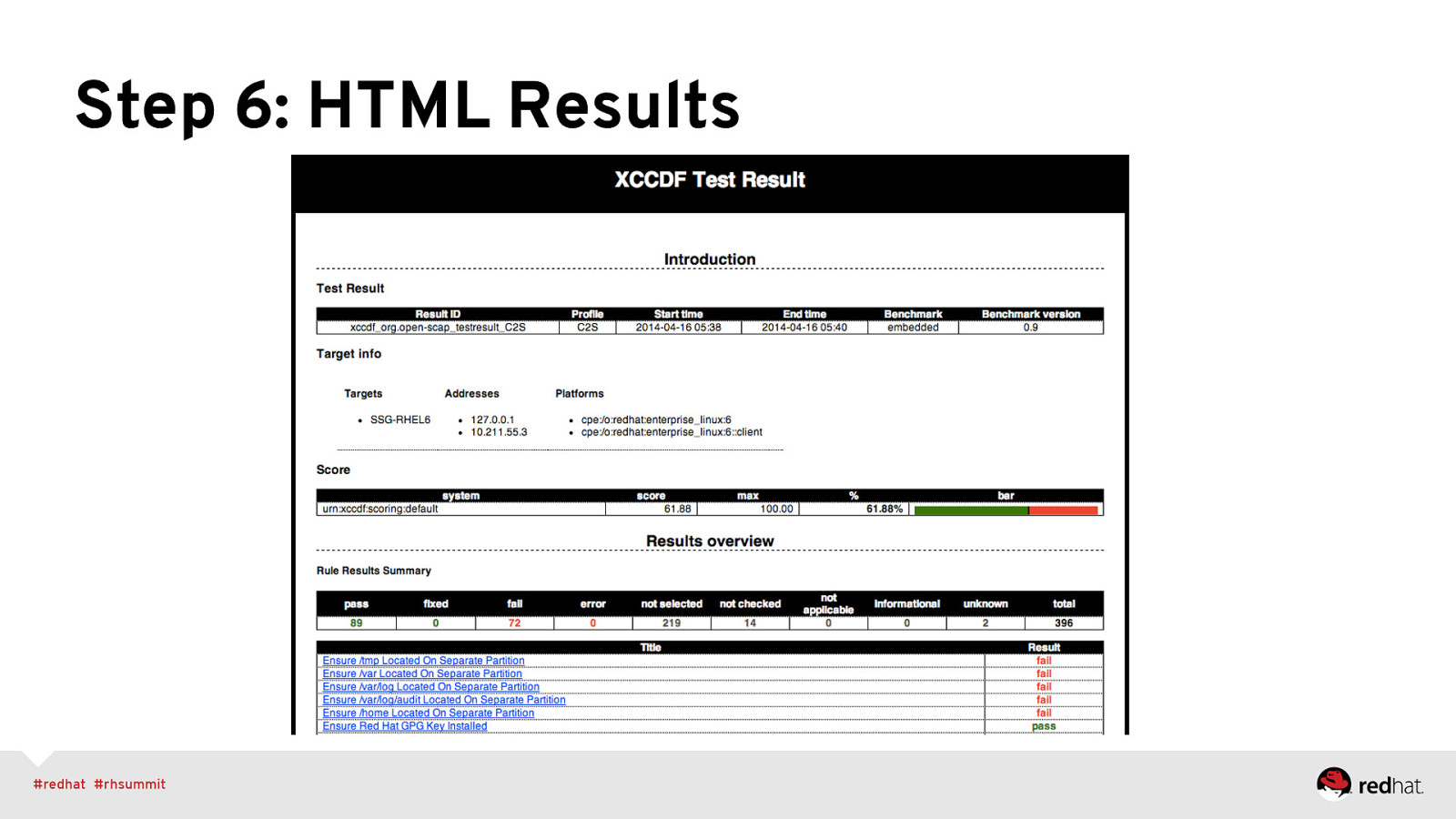
Step 6: HTML Results
Slide 50
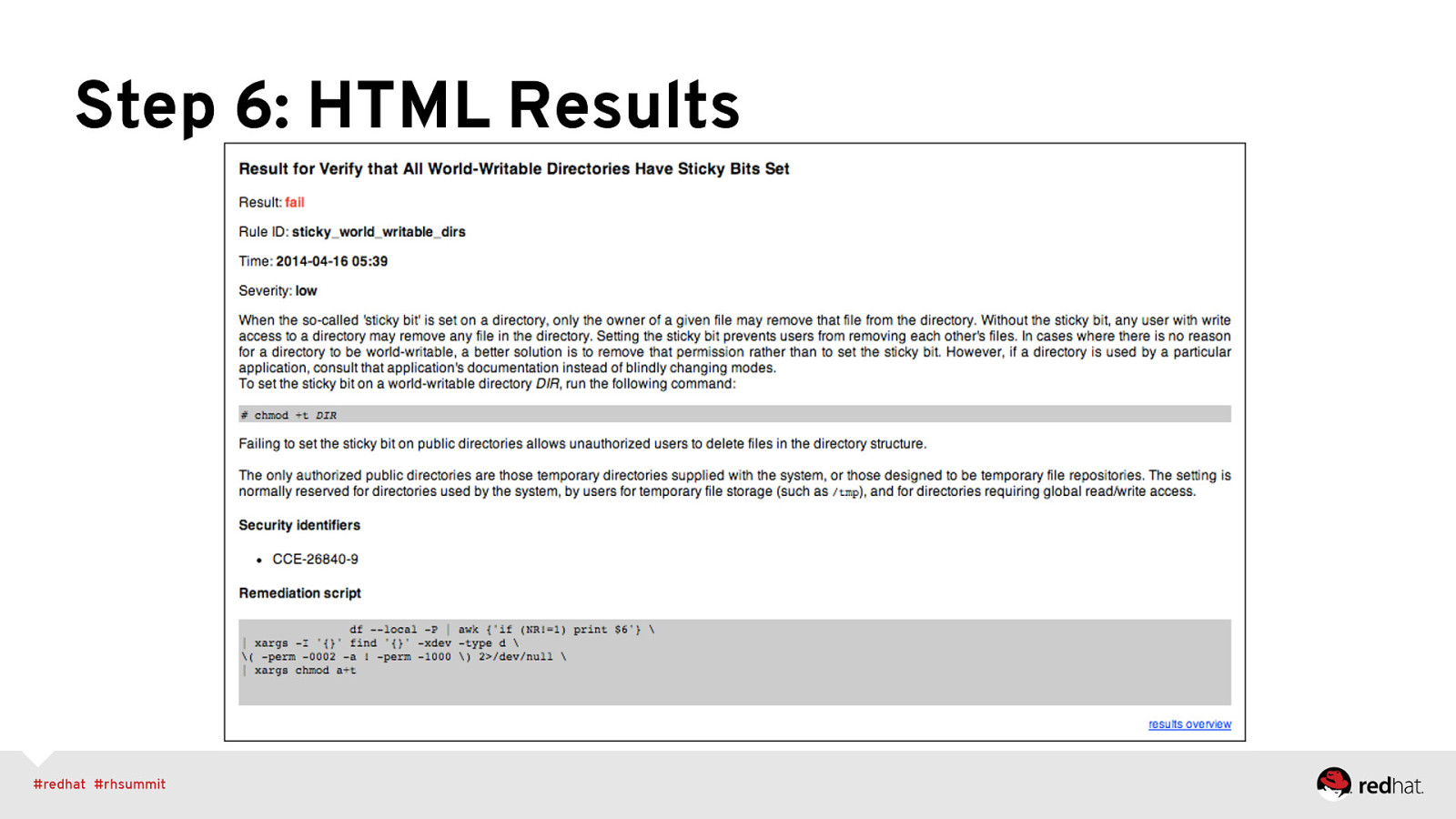
Step 6: HTML Results
Slide 51
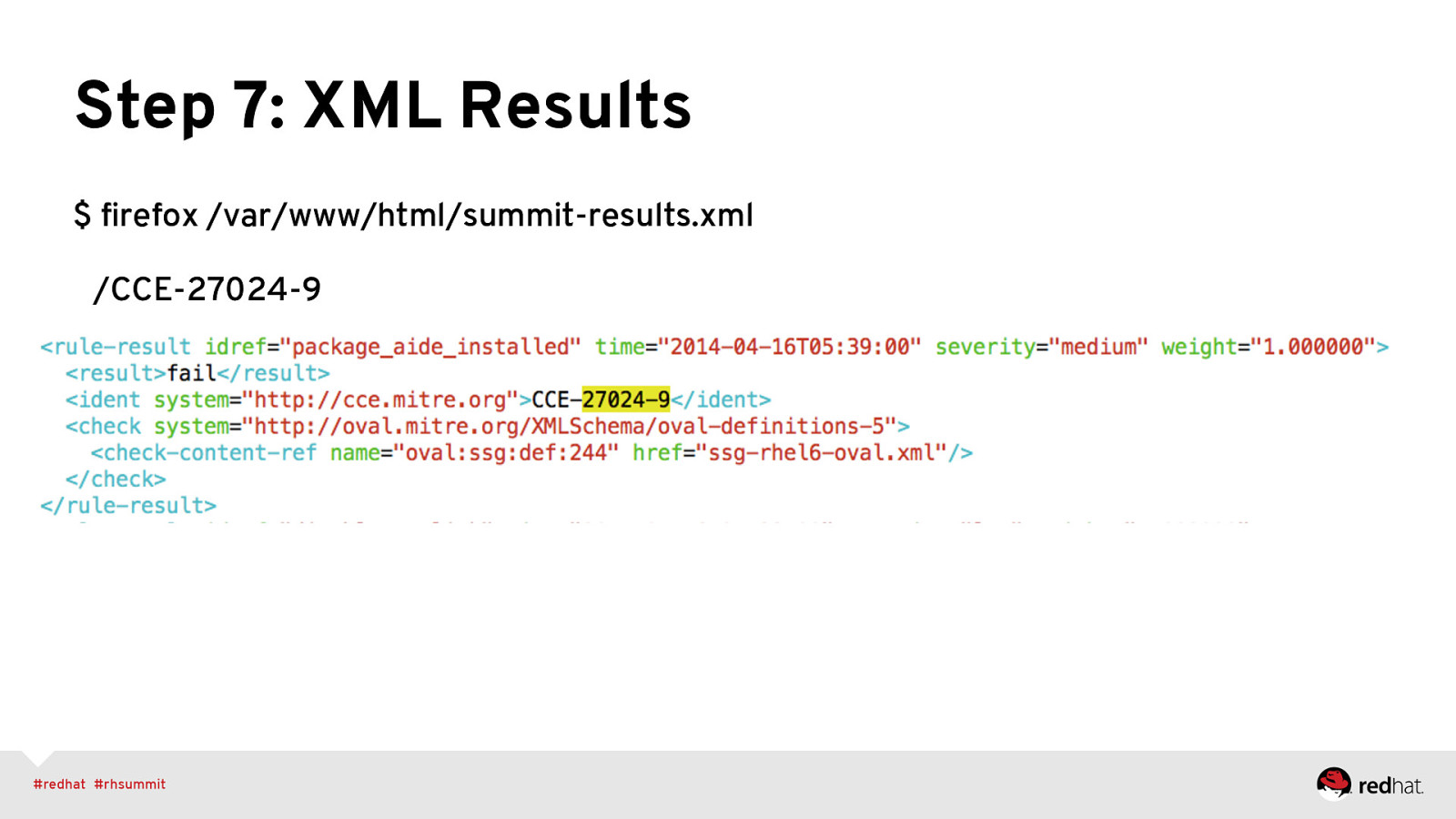
Step 7: XML Results $ firefox /var/www/html/summit-results.xml /CCE-27024-9
Slide 52
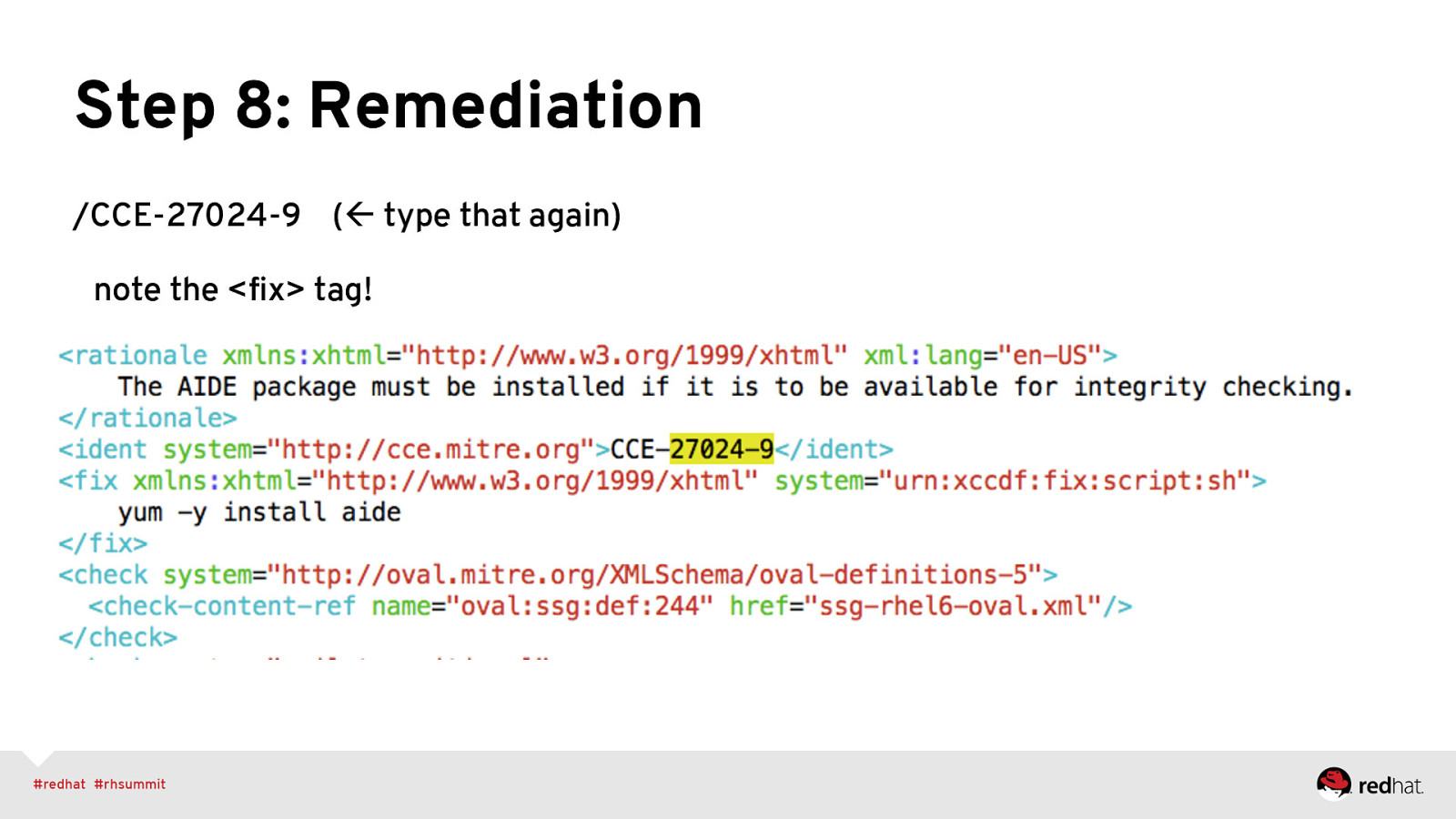
Step 8: Remediation /CCE-27024-9 (ß type that again) note the <fix> tag!
Slide 53
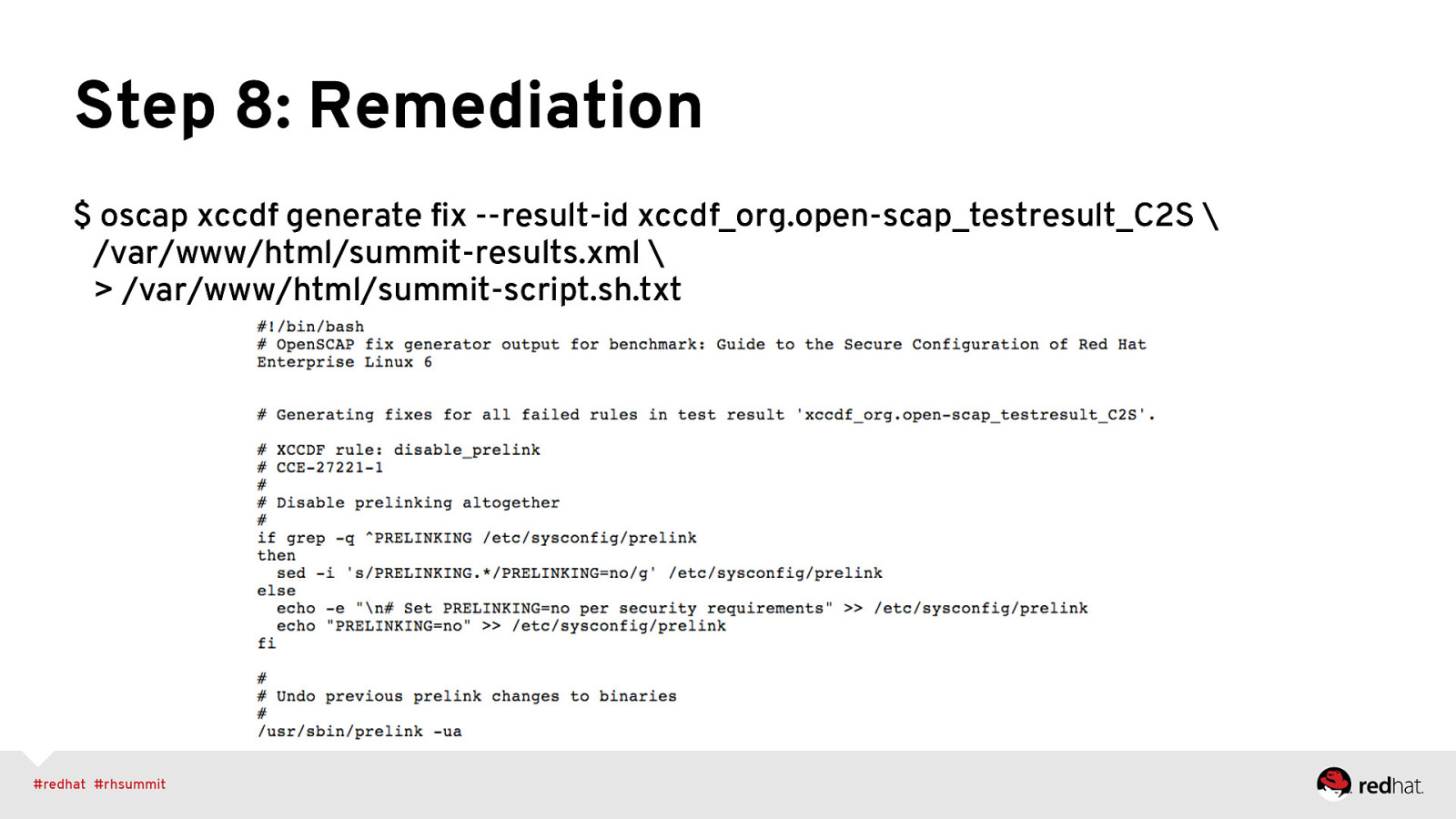
Step 8: Remediation $ oscap xccdf generate fix —result-id xccdf_org.open-scap_testresult_C2S \ /var/www/html/summit-results.xml \ > /var/www/html/summit-script.sh.txt