Continuous Change and IT Security Shawn Wells Chief Security Strategist U.S. Public Sector shawn@redhat.com || 443-534-0130
Slide 1

Slide 2
The Problem Applications require complicated installation and integration every time they are deployed 2
Slide 3
THE PROBLEM DEVELOPERS 3 I.T. OPERATIONS
Slide 4
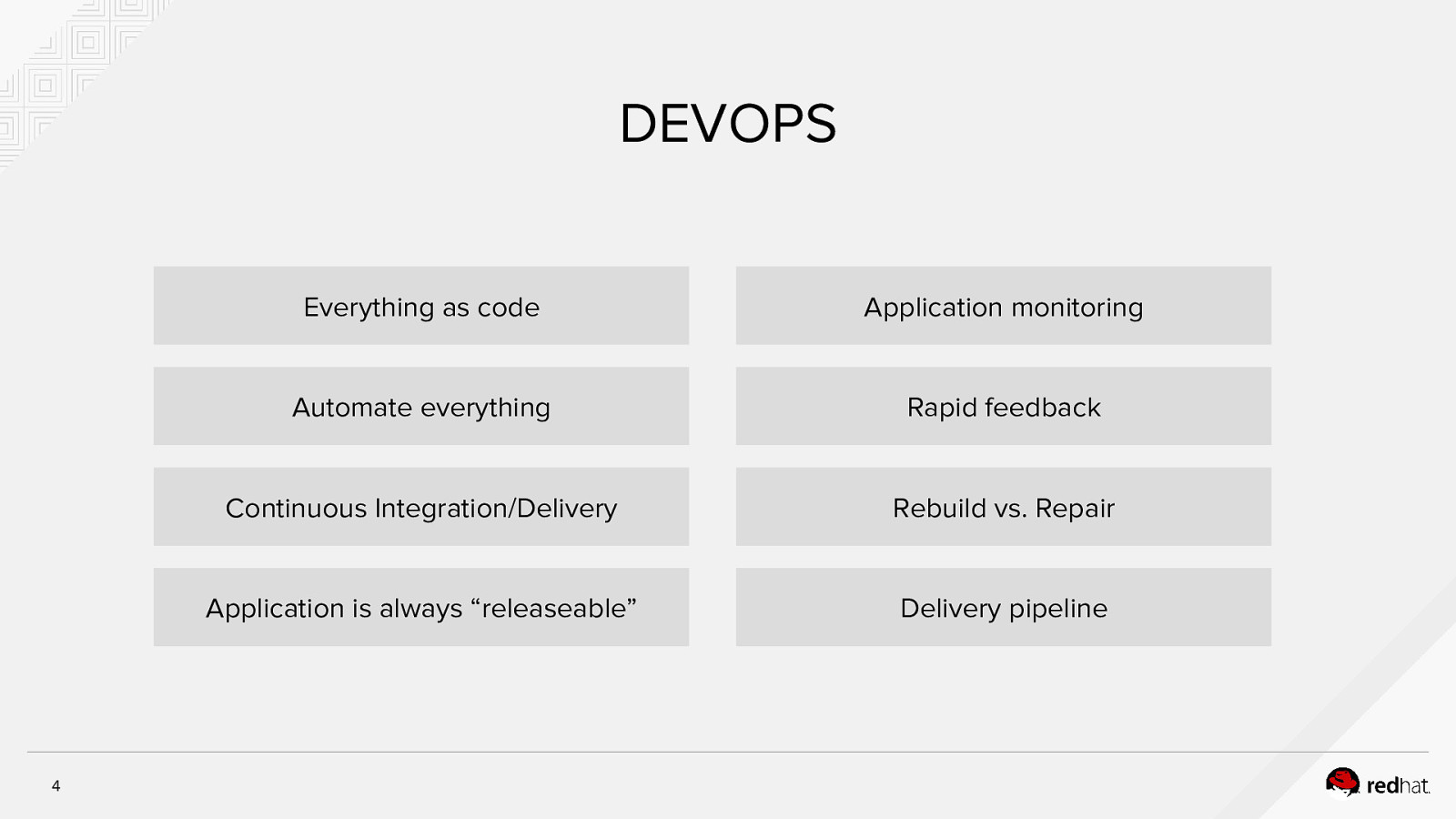
DEVOPS 4 Everything as code Application monitoring Automate everything Rapid feedback Continuous Integration/Delivery Rebuild vs. Repair Application is always “releaseable” Delivery pipeline
Slide 5
A Solution Adopting a container strategy will allow applications to be easily shared and deployed. 5
Slide 6
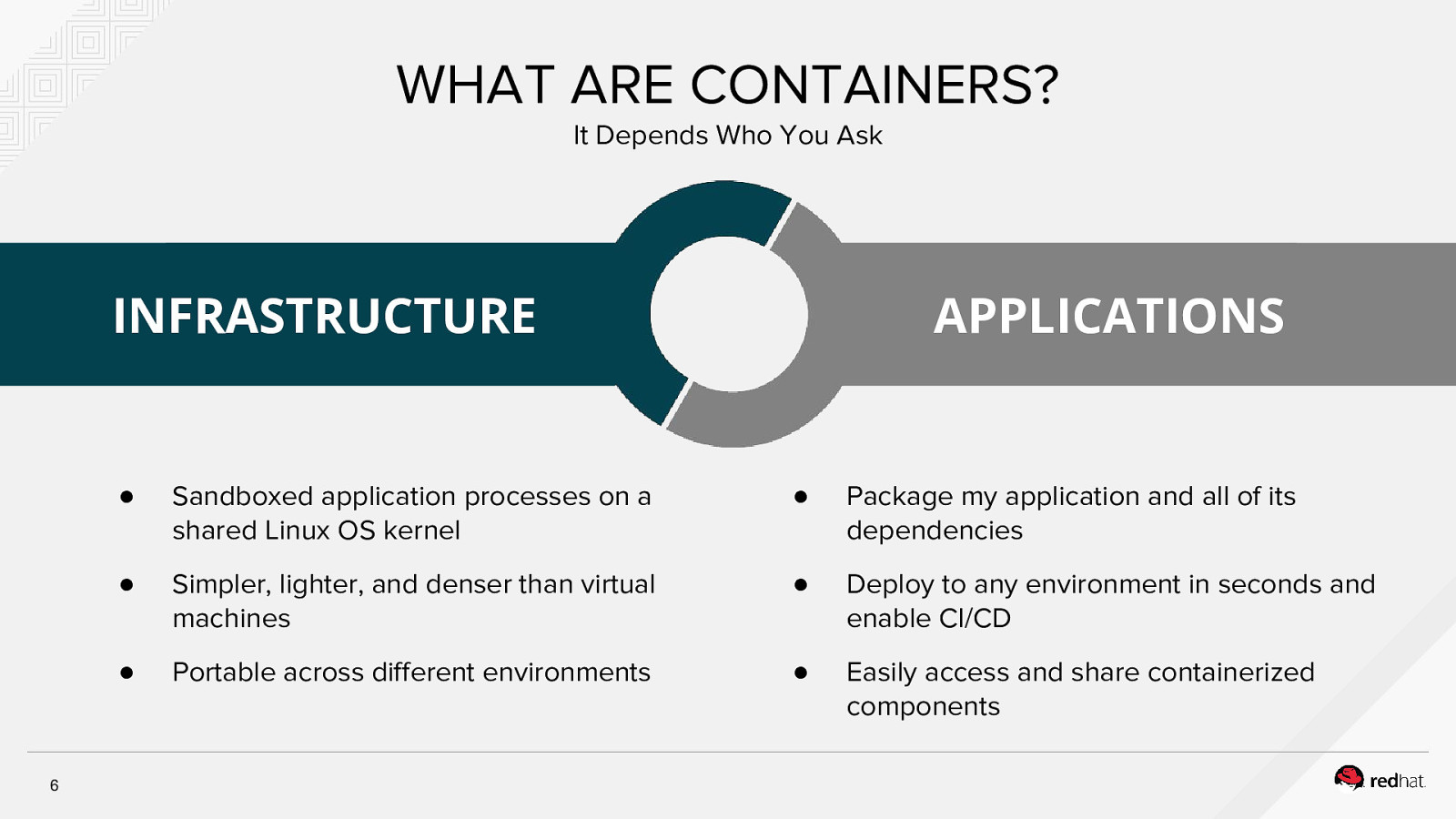
WHAT ARE CONTAINERS? It Depends Who You Ask APPLICATIONS INFRASTRUCTURE 6 ● Sandboxed application processes on a shared Linux OS kernel ● Package my application and all of its dependencies ● Simpler, lighter, and denser than virtual machines ● Deploy to any environment in seconds and enable CI/CD ● Portable across different environments ● Easily access and share containerized components
Slide 7
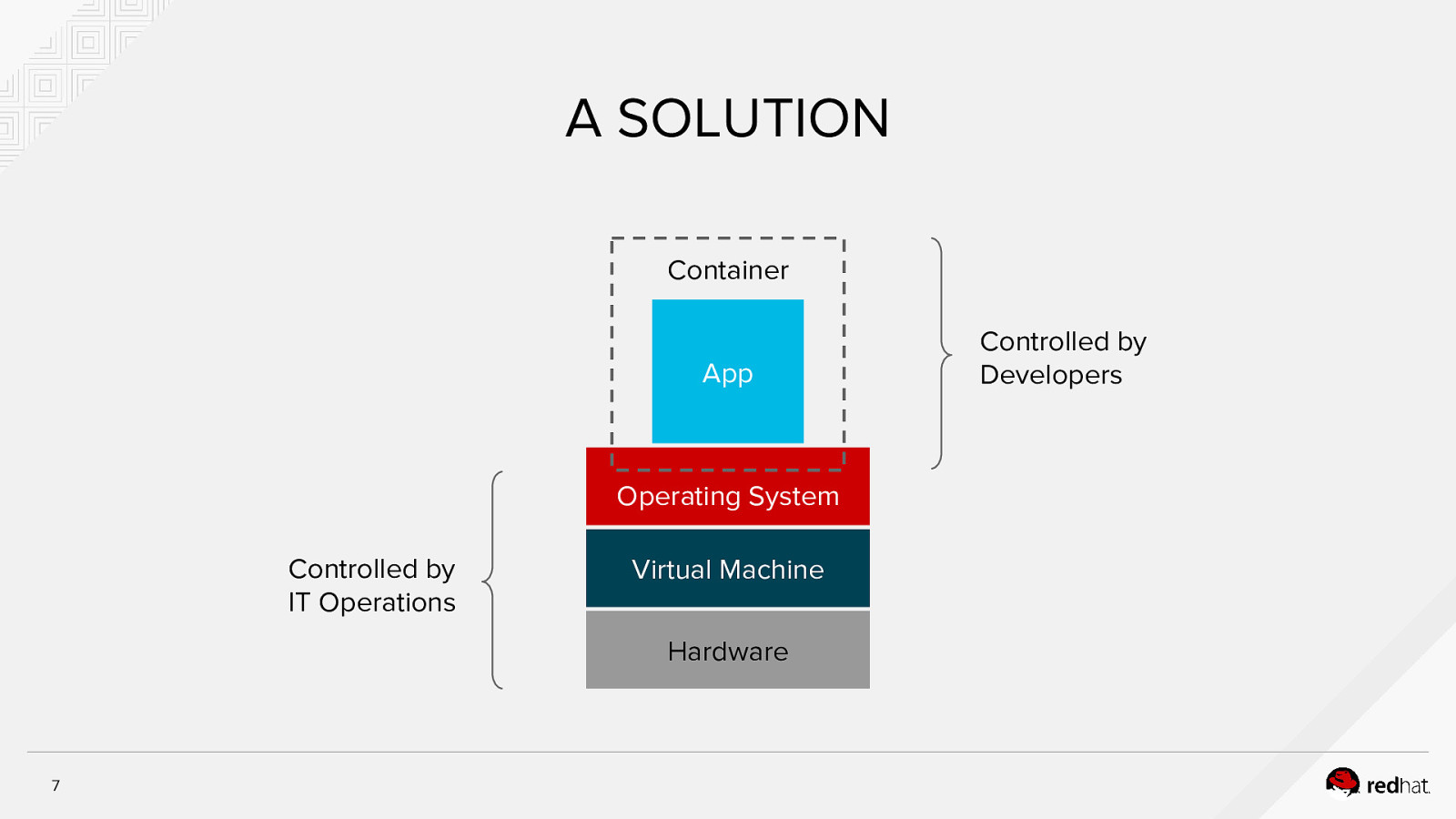
A SOLUTION Container App Operating System Controlled by IT Operations Virtual Machine Hardware 7 Controlled by Developers
Slide 8
A SOLUTION DEVELOPERS 8 I.T. OPERATIONS
Slide 9
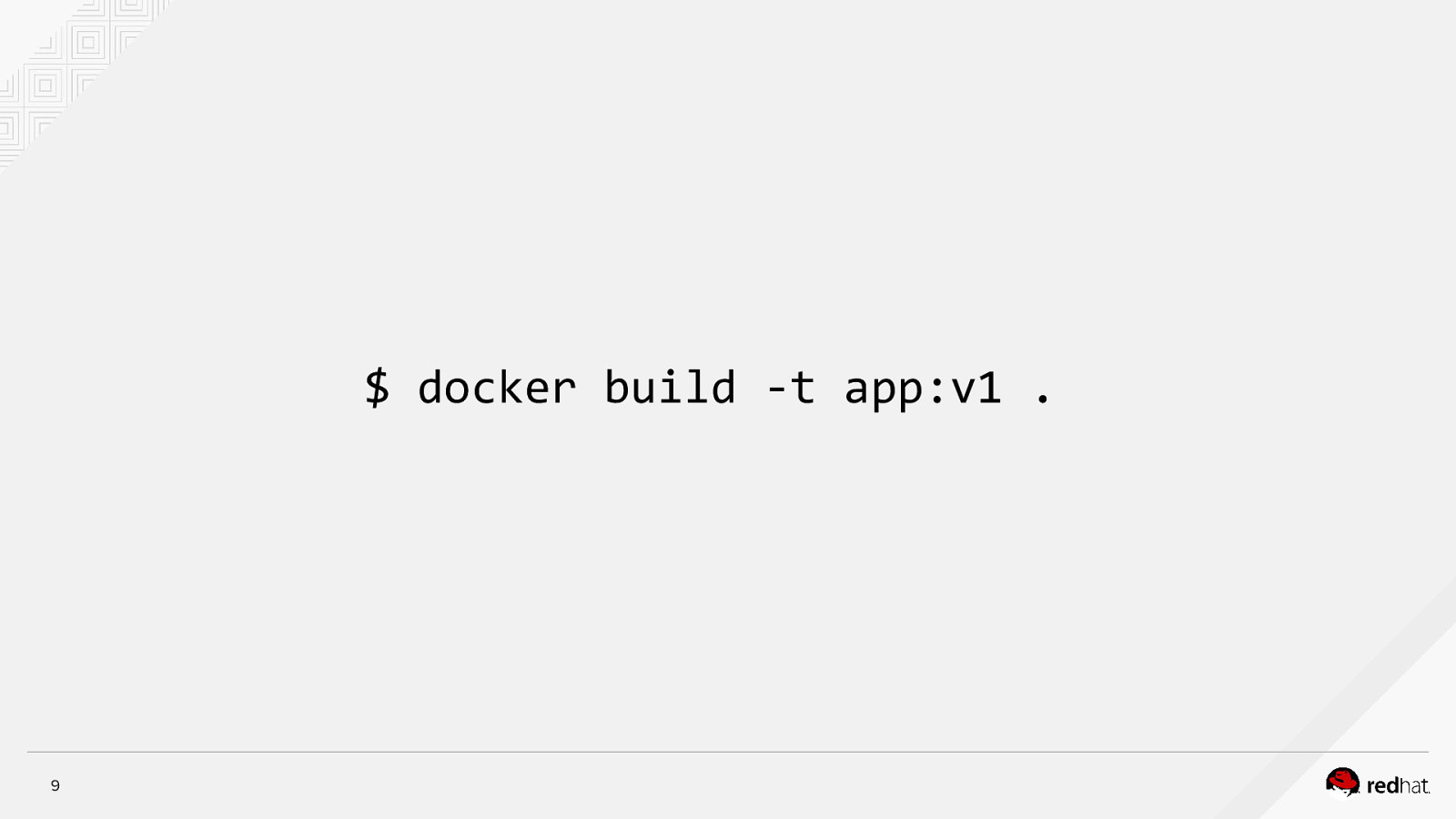
$ docker build -t app:v1 . 9
Slide 10
$ docker build -t app:v1 . $ docker run app:v1 10
Slide 11
physical virtual private cloud public cloud 11
Slide 12
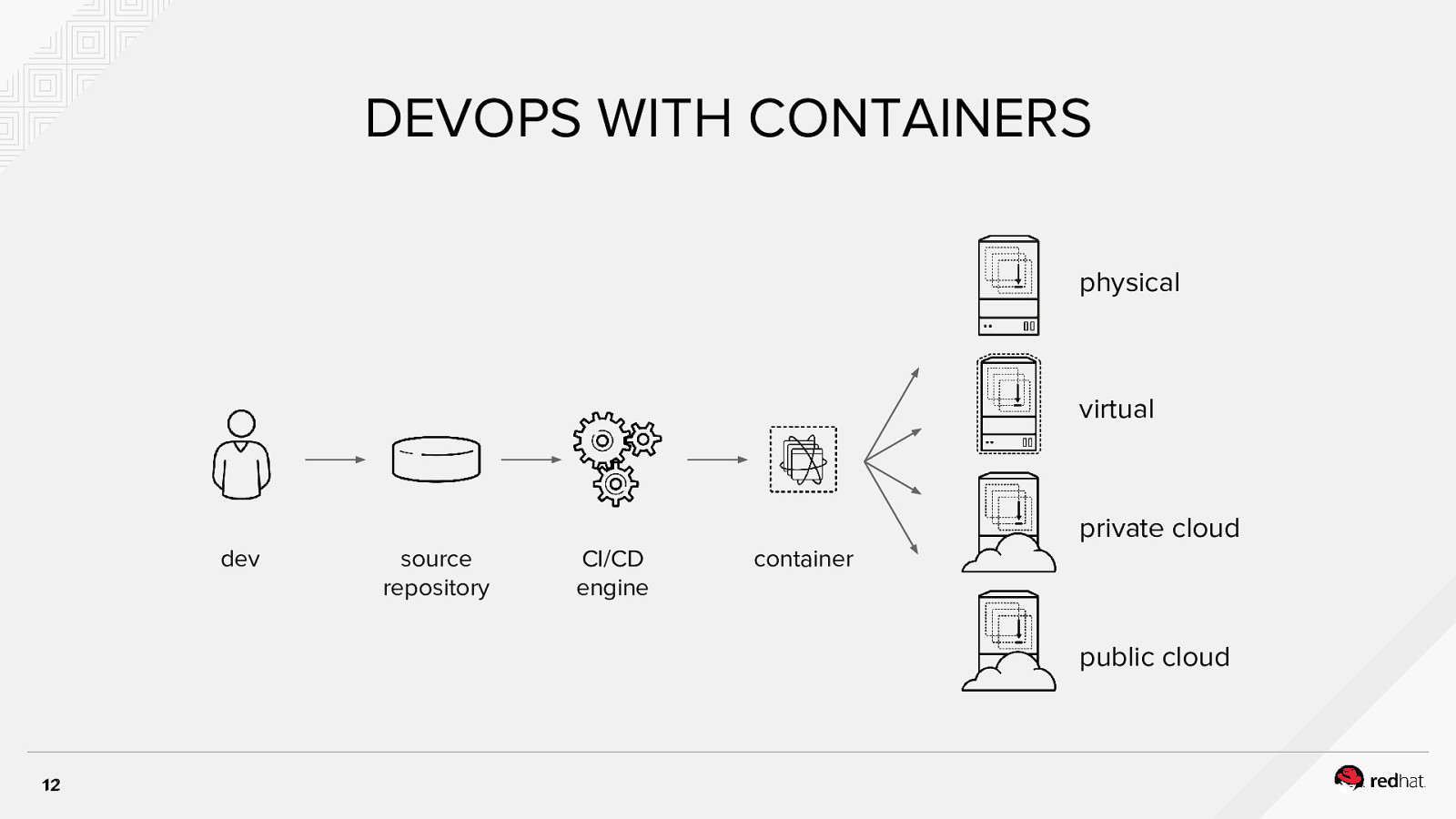
DEVOPS WITH CONTAINERS physical virtual private cloud dev source repository CI/CD engine container public cloud 12
Slide 13
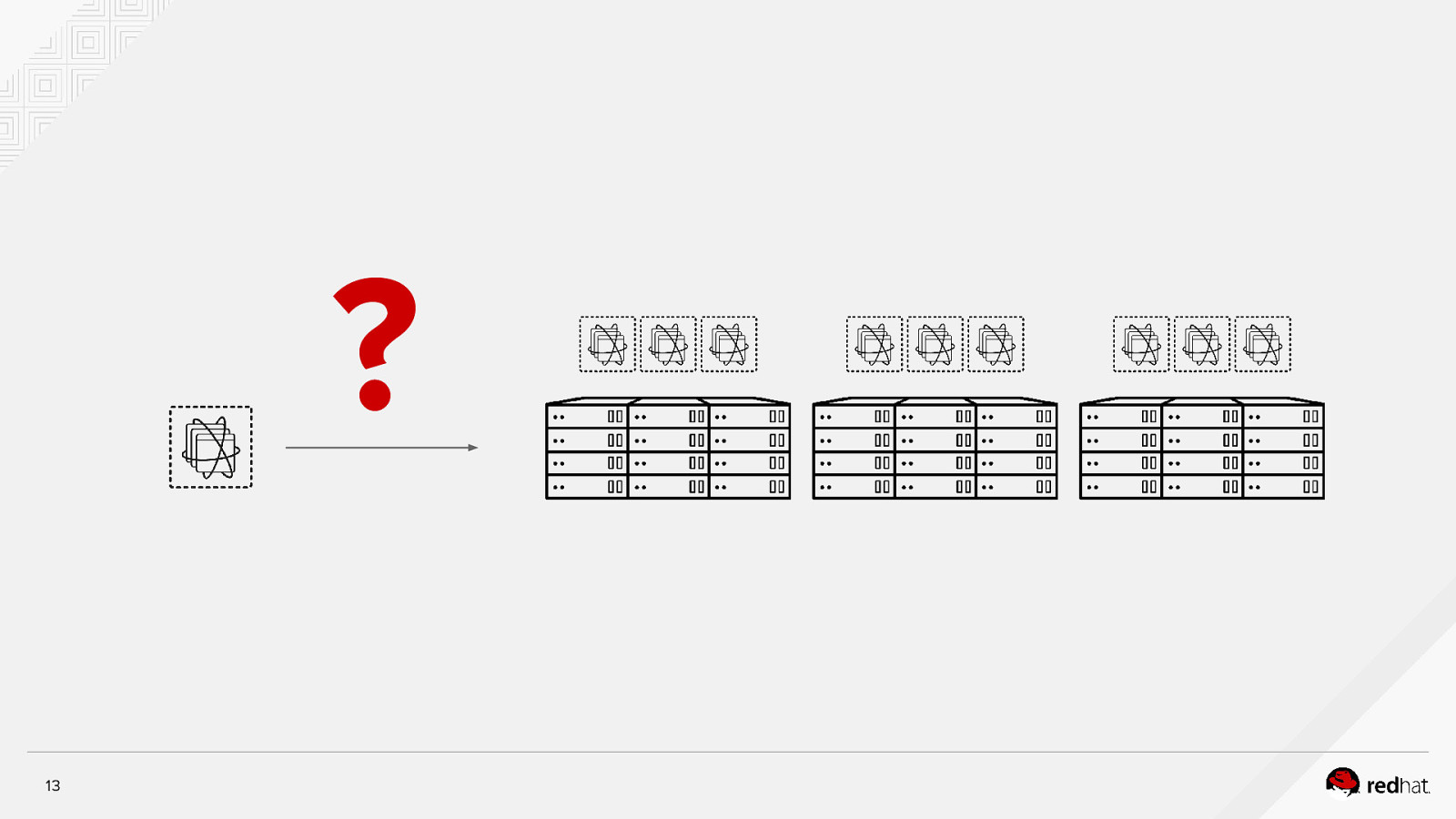
? 13
Slide 14
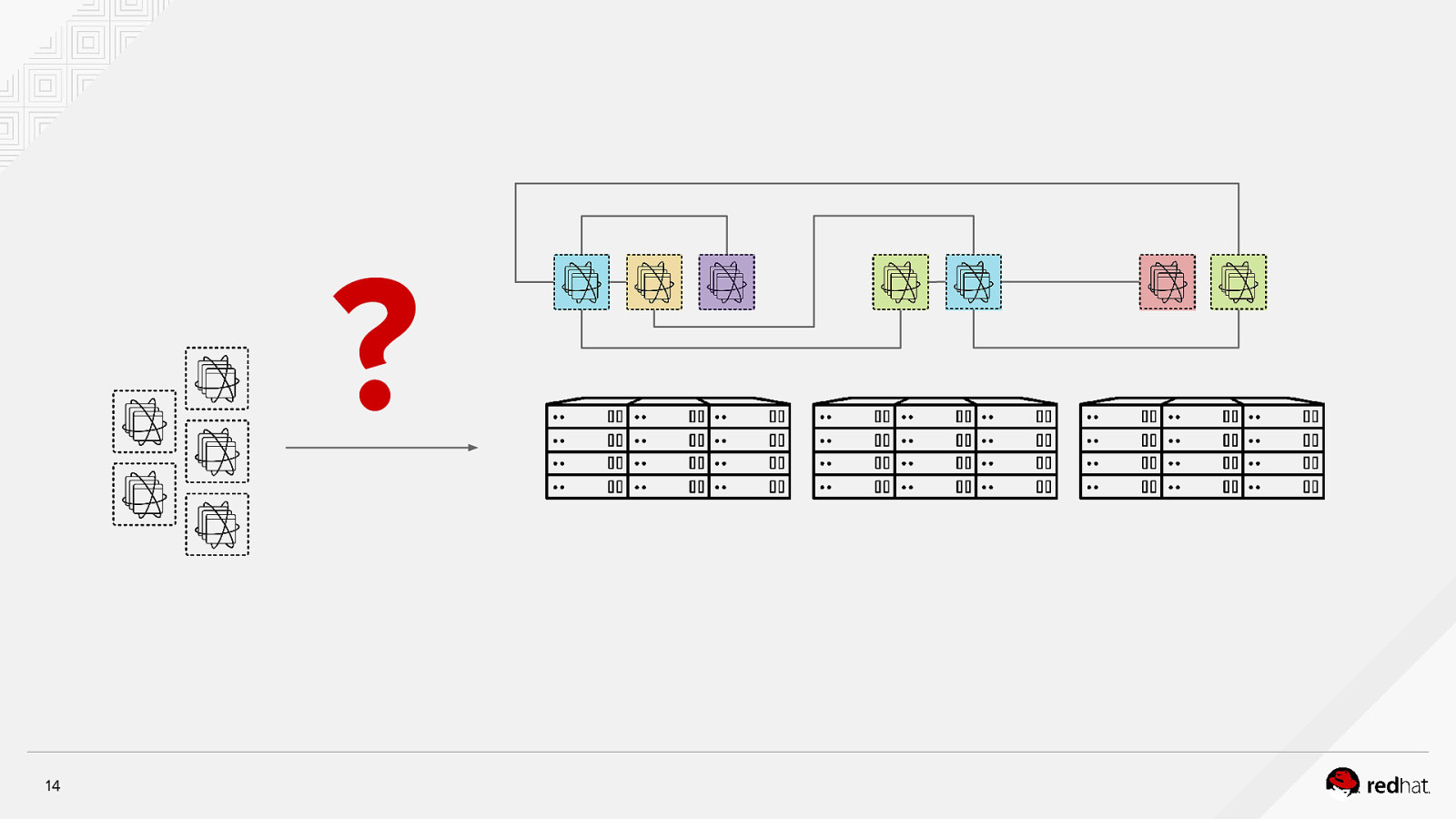
? 14
Slide 15

WE NEED MORE THAN JUST CONTAINERS 15 Scheduling Security Decide where to deploy containers Control who can do what Lifecycle and health Scaling Keep containers running despite failures Scale containers up and down Discovery Persistence Find other containers on the network Survive data beyond container lifecycle Monitoring Aggregation Visibility into running containers Compose apps from multiple containers
Slide 16

Kubernetes is an open-source system for automating deployment, operations, and scaling of containerized applications across multiple hosts kubernetes 16
Slide 17
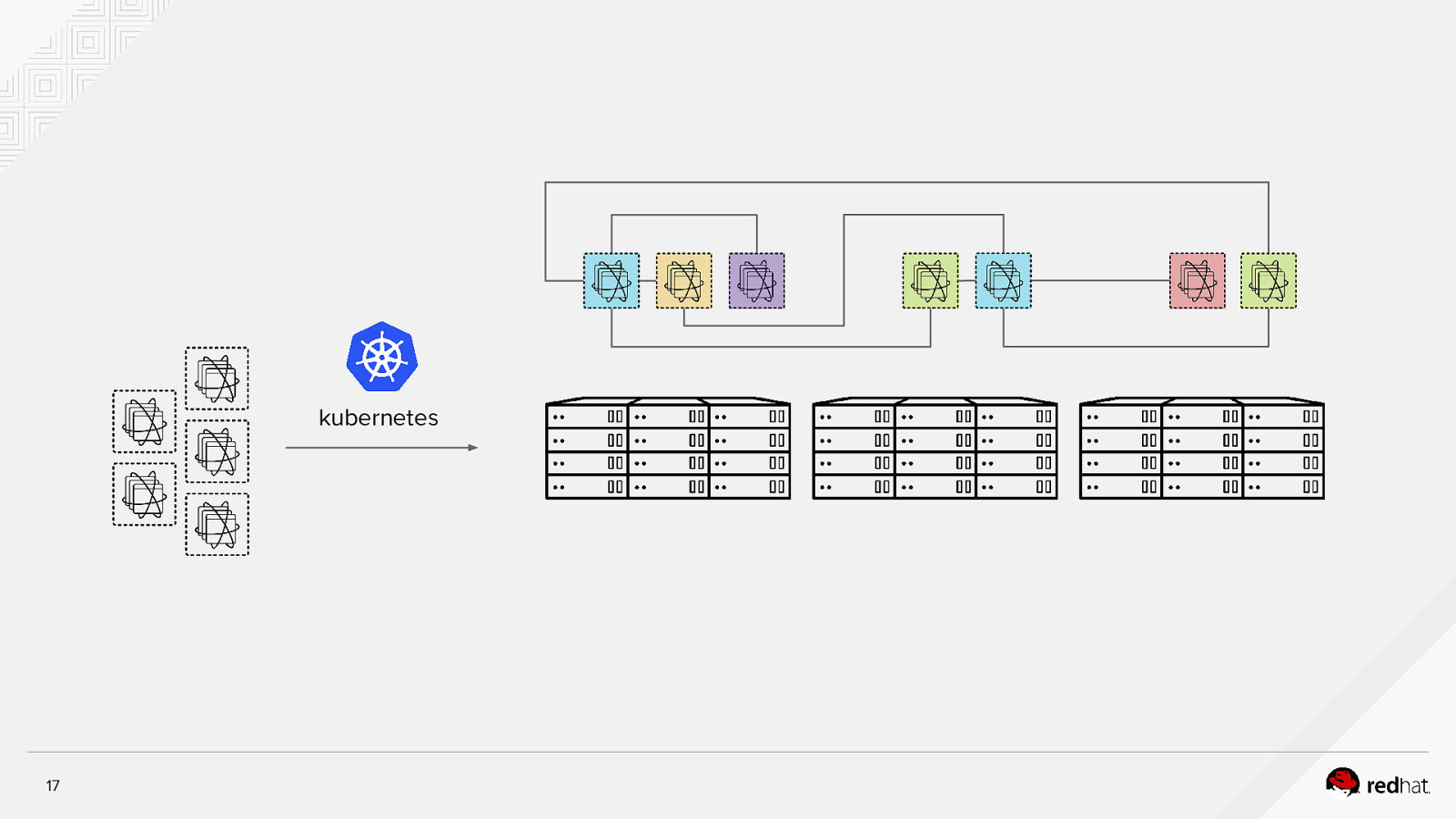
kubernetes 17
Slide 18
DEVOPS WITH CONTAINERS AND KUBERNETES 18
Slide 19

INDUSTRY CONVERGING ON KUBERNETES 19
Slide 20

INDUSTRY CONVERGING ON KUBERNETES 20
Slide 21
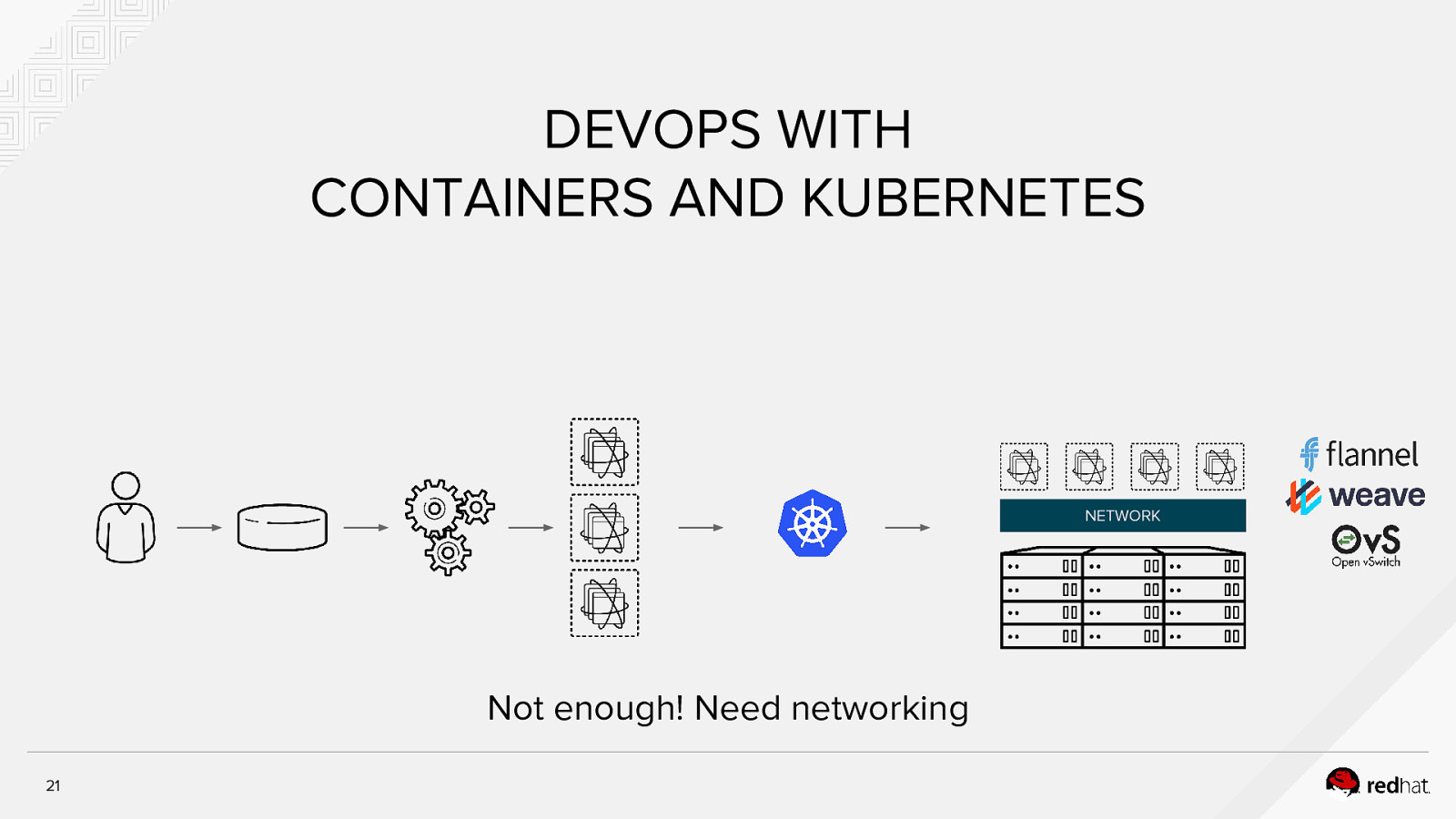
DEVOPS WITH CONTAINERS AND KUBERNETES NETWORK Not enough! Need networking 21
Slide 22
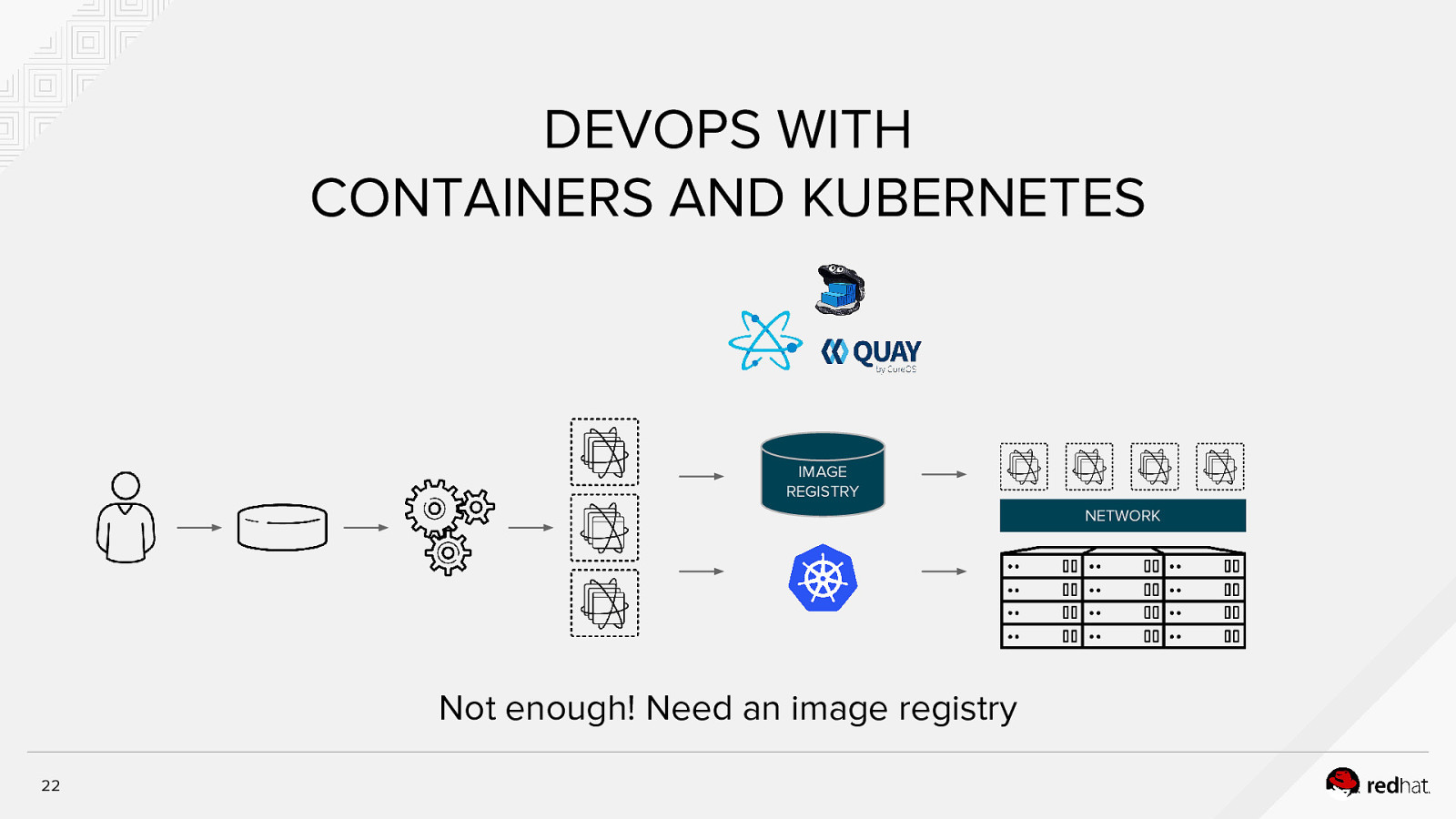
DEVOPS WITH CONTAINERS AND KUBERNETES IMAGE REGISTRY NETWORK Not enough! Need an image registry 22
Slide 23
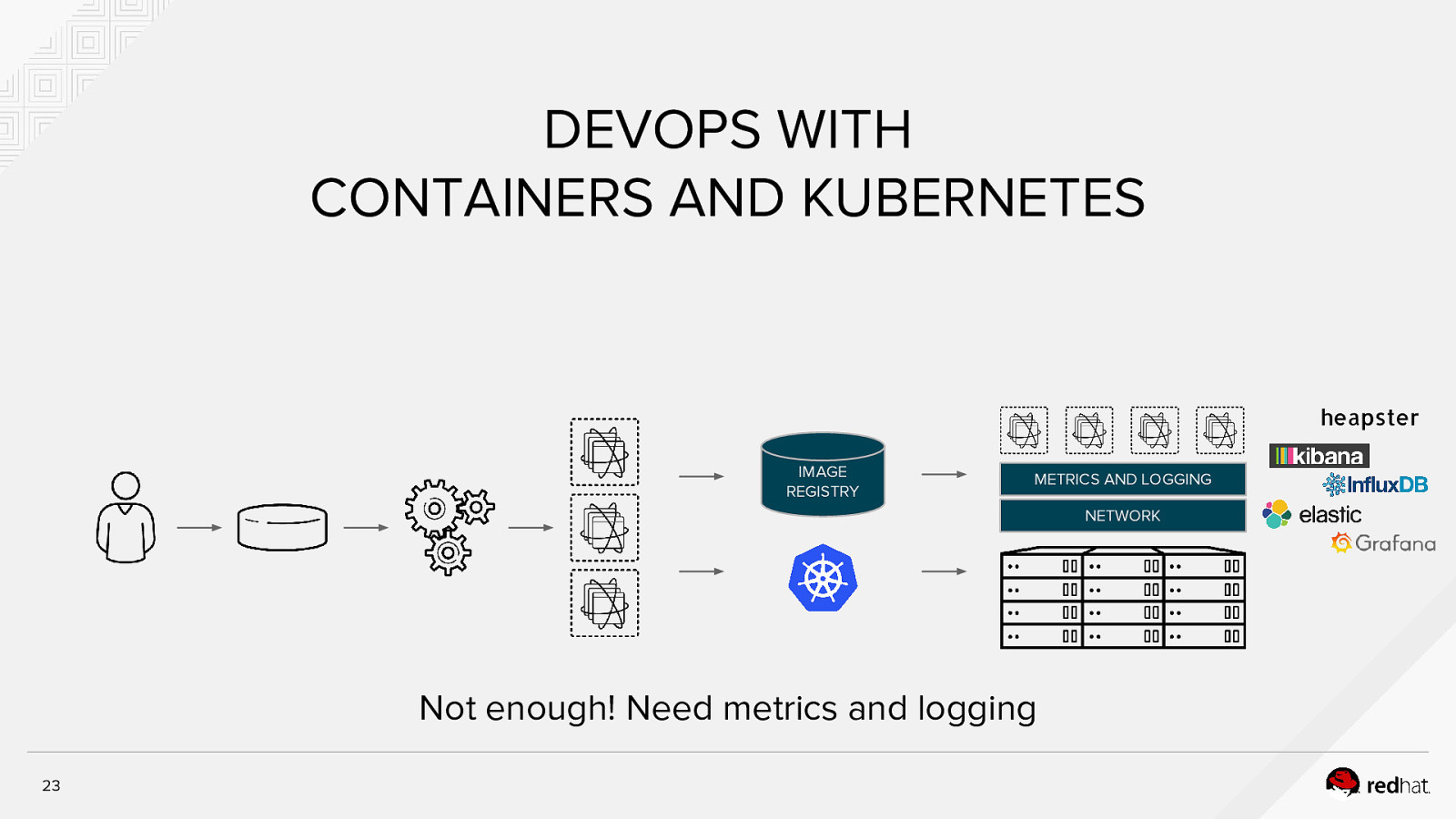
DEVOPS WITH CONTAINERS AND KUBERNETES heapster IMAGE REGISTRY METRICS AND LOGGING NETWORK Not enough! Need metrics and logging 23
Slide 24
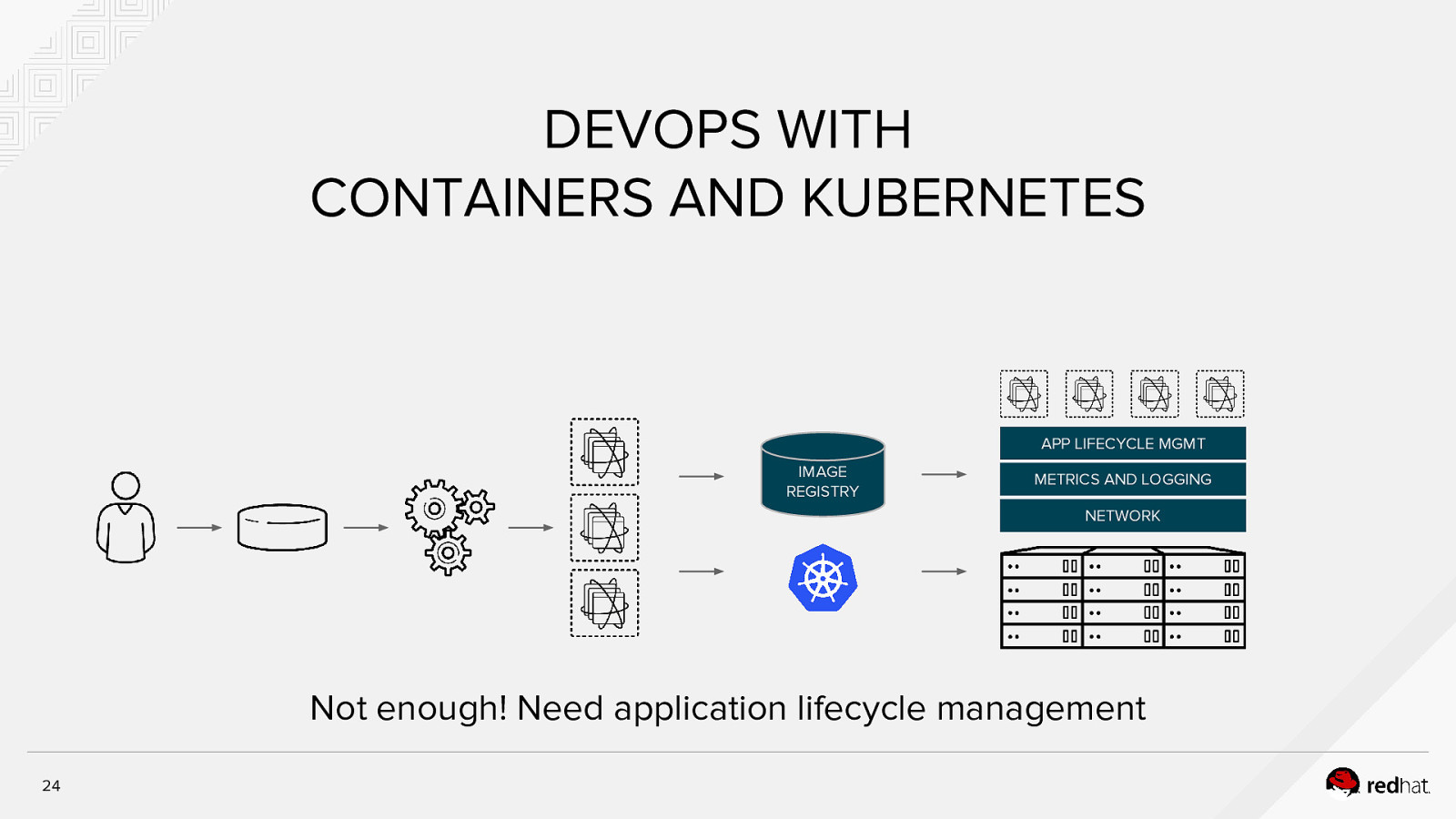
DEVOPS WITH CONTAINERS AND KUBERNETES APP LIFECYCLE MGMT IMAGE REGISTRY METRICS AND LOGGING NETWORK Not enough! Need application lifecycle management 24
Slide 25
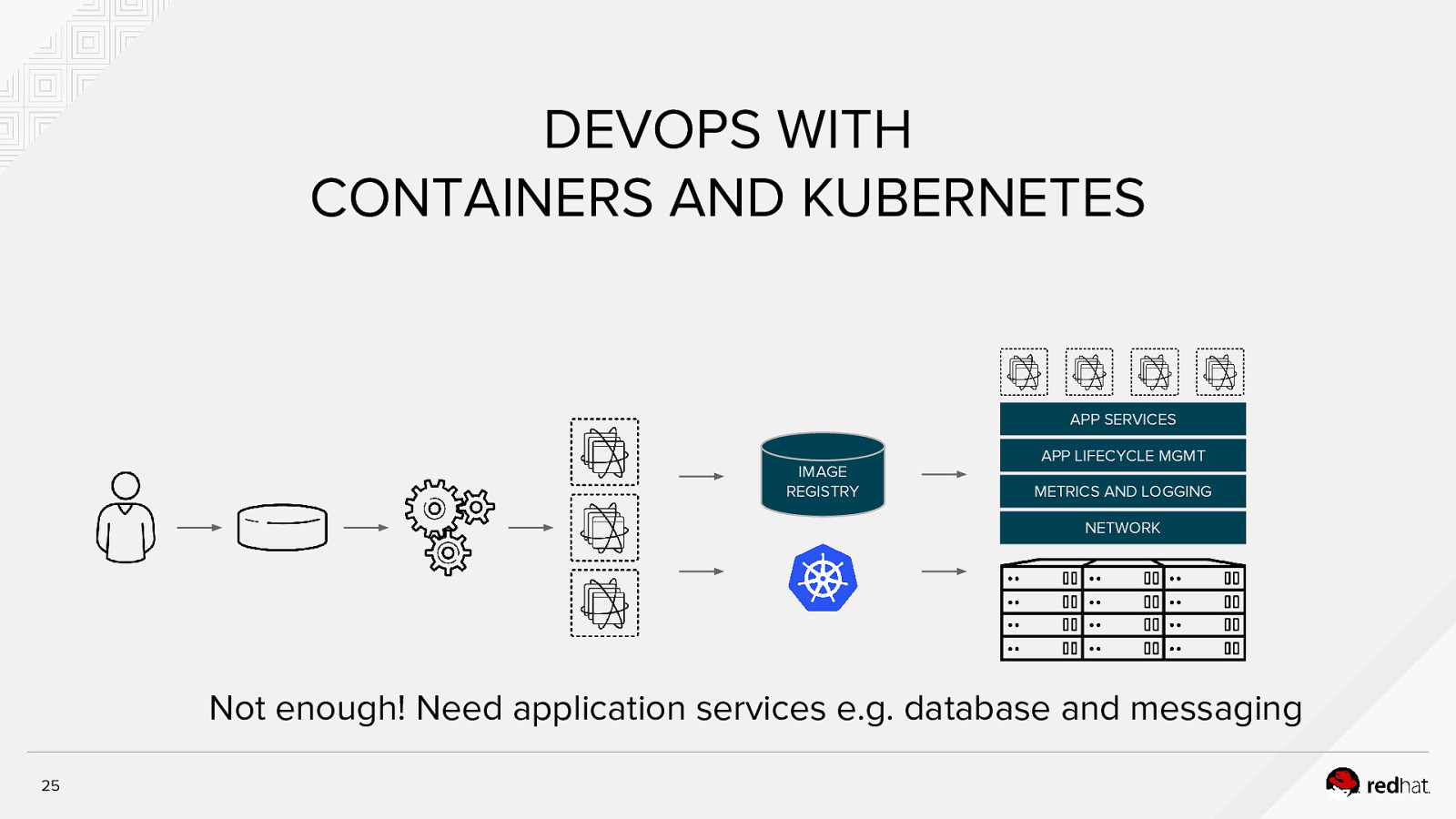
DEVOPS WITH CONTAINERS AND KUBERNETES APP SERVICES APP LIFECYCLE MGMT IMAGE REGISTRY METRICS AND LOGGING NETWORK Not enough! Need application services e.g. database and messaging 25
Slide 26
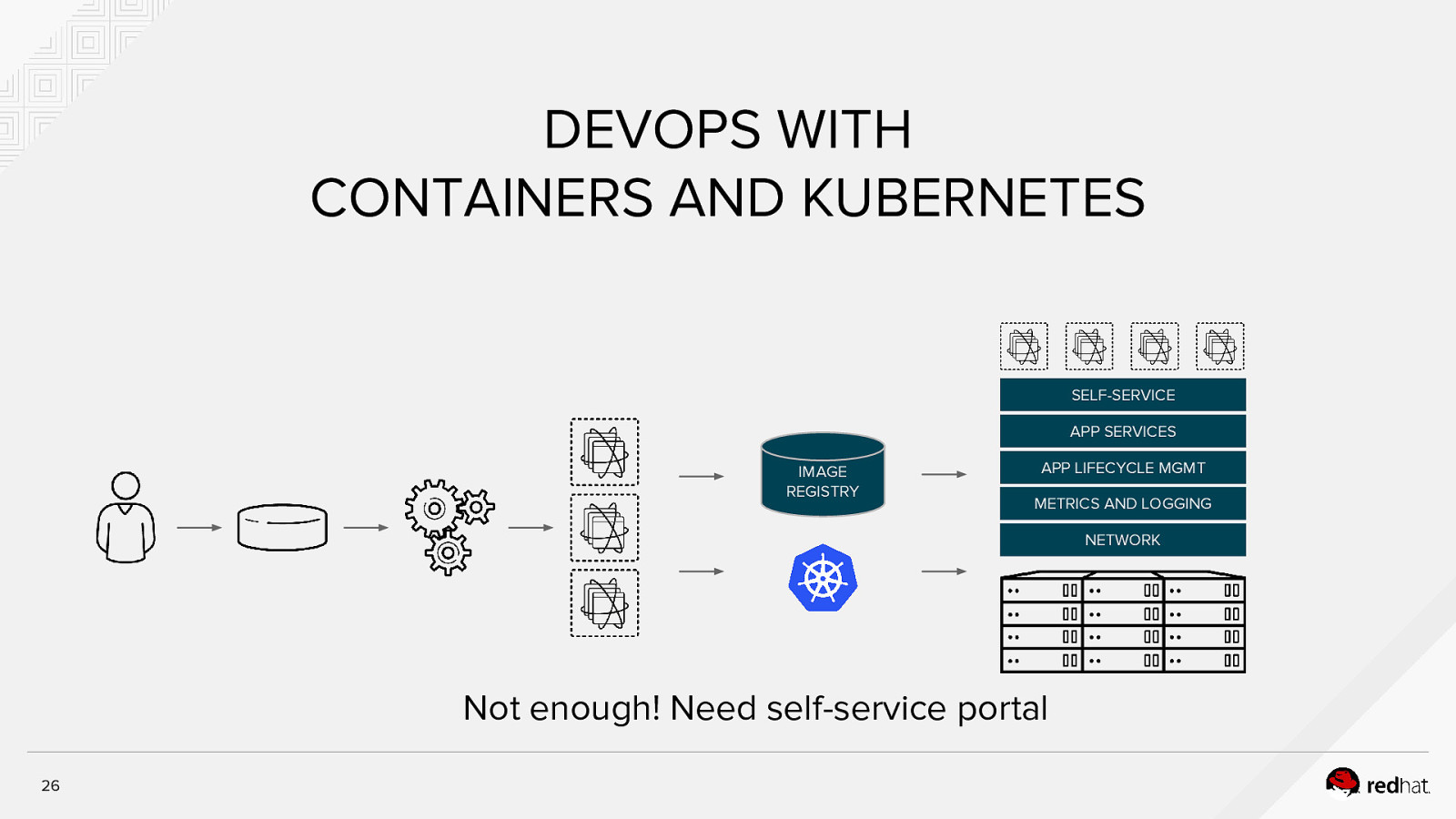
DEVOPS WITH CONTAINERS AND KUBERNETES SELF-SERVICE APP SERVICES IMAGE REGISTRY APP LIFECYCLE MGMT METRICS AND LOGGING NETWORK Not enough! Need self-service portal 26
Slide 27
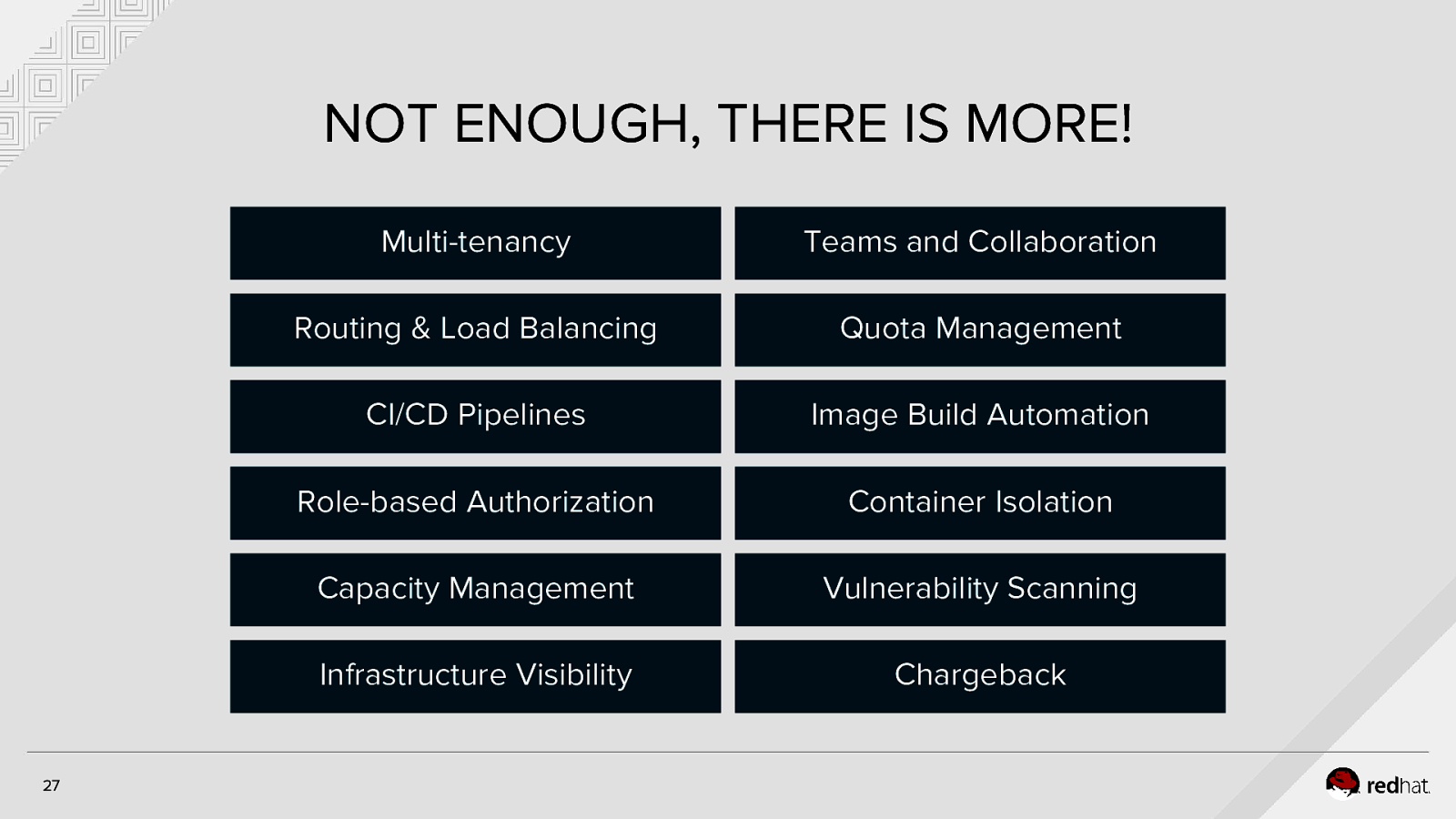
NOT ENOUGH, THERE IS MORE! 27 Multi-tenancy Teams and Collaboration Routing & Load Balancing Quota Management CI/CD Pipelines Image Build Automation Role-based Authorization Container Isolation Capacity Management Vulnerability Scanning Infrastructure Visibility Chargeback
Slide 28

Container application platform based on Docker and Kubernetes for building, distributing and running containers at scale 28
Slide 29
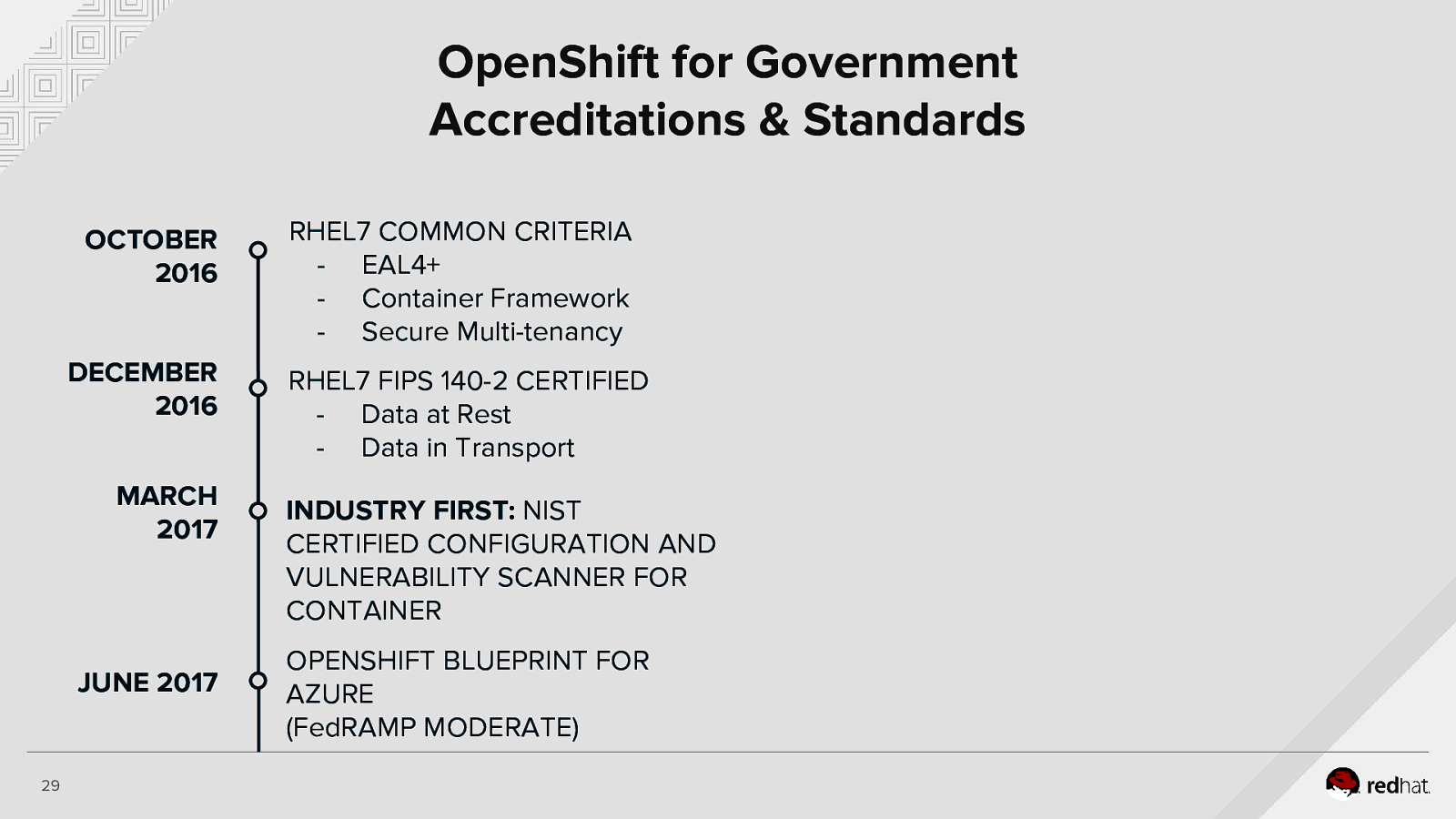
OpenShift for Government Accreditations & Standards OCTOBER 2016 DECEMBER 2016 MARCH 2017 JUNE 2017 29 RHEL7 COMMON CRITERIA - EAL4+ - Container Framework - Secure Multi-tenancy RHEL7 FIPS 140-2 CERTIFIED - Data at Rest - Data in Transport INDUSTRY FIRST: NIST CERTIFIED CONFIGURATION AND VULNERABILITY SCANNER FOR CONTAINER OPENSHIFT BLUEPRINT FOR AZURE (FedRAMP MODERATE)
Slide 30
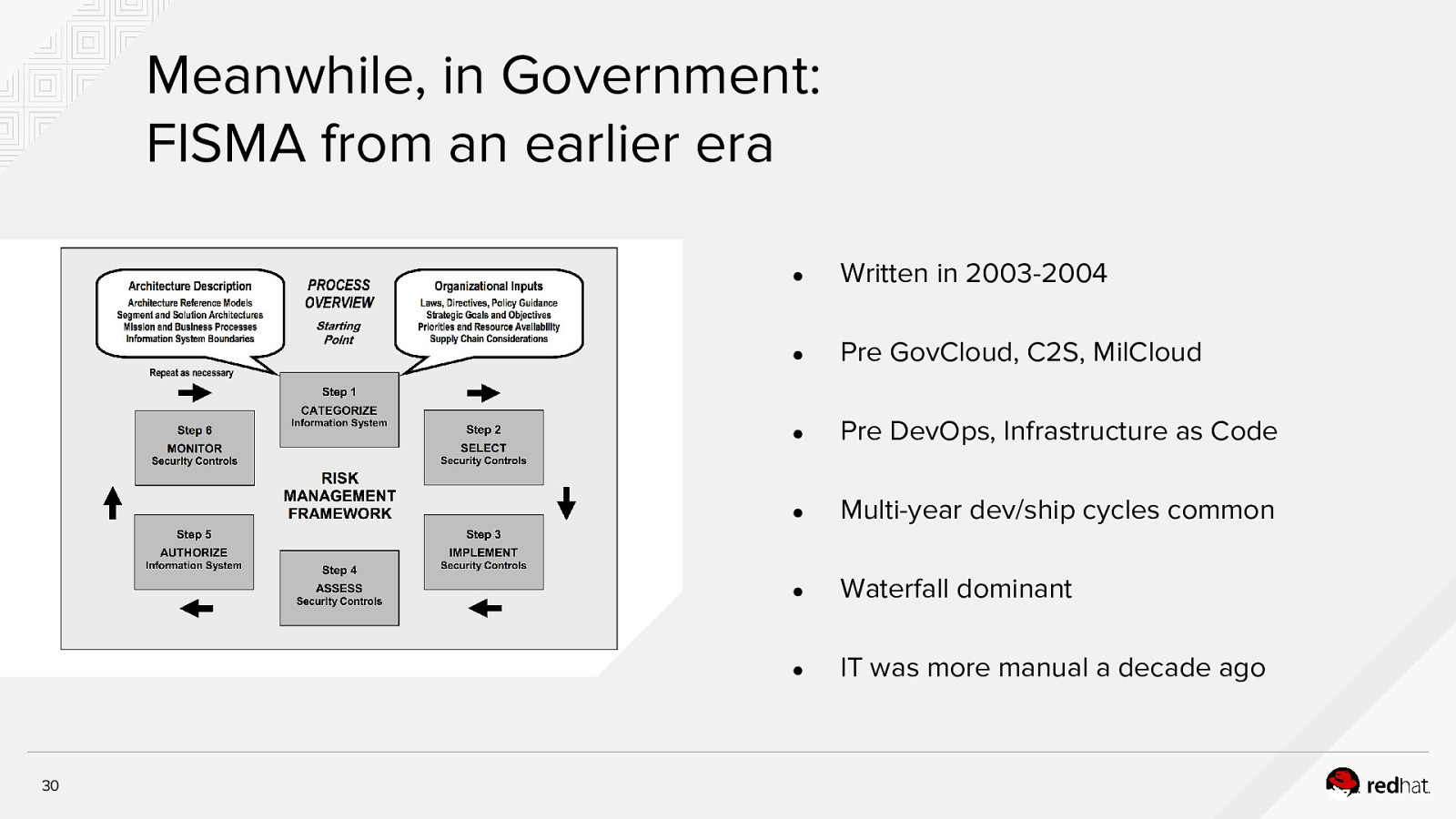
Meanwhile, in Government: FISMA from an earlier era 30 ● Written in 2003-2004 ● Pre GovCloud, C2S, MilCloud ● Pre DevOps, Infrastructure as Code ● Multi-year dev/ship cycles common ● Waterfall dominant ● IT was more manual a decade ago
Slide 31
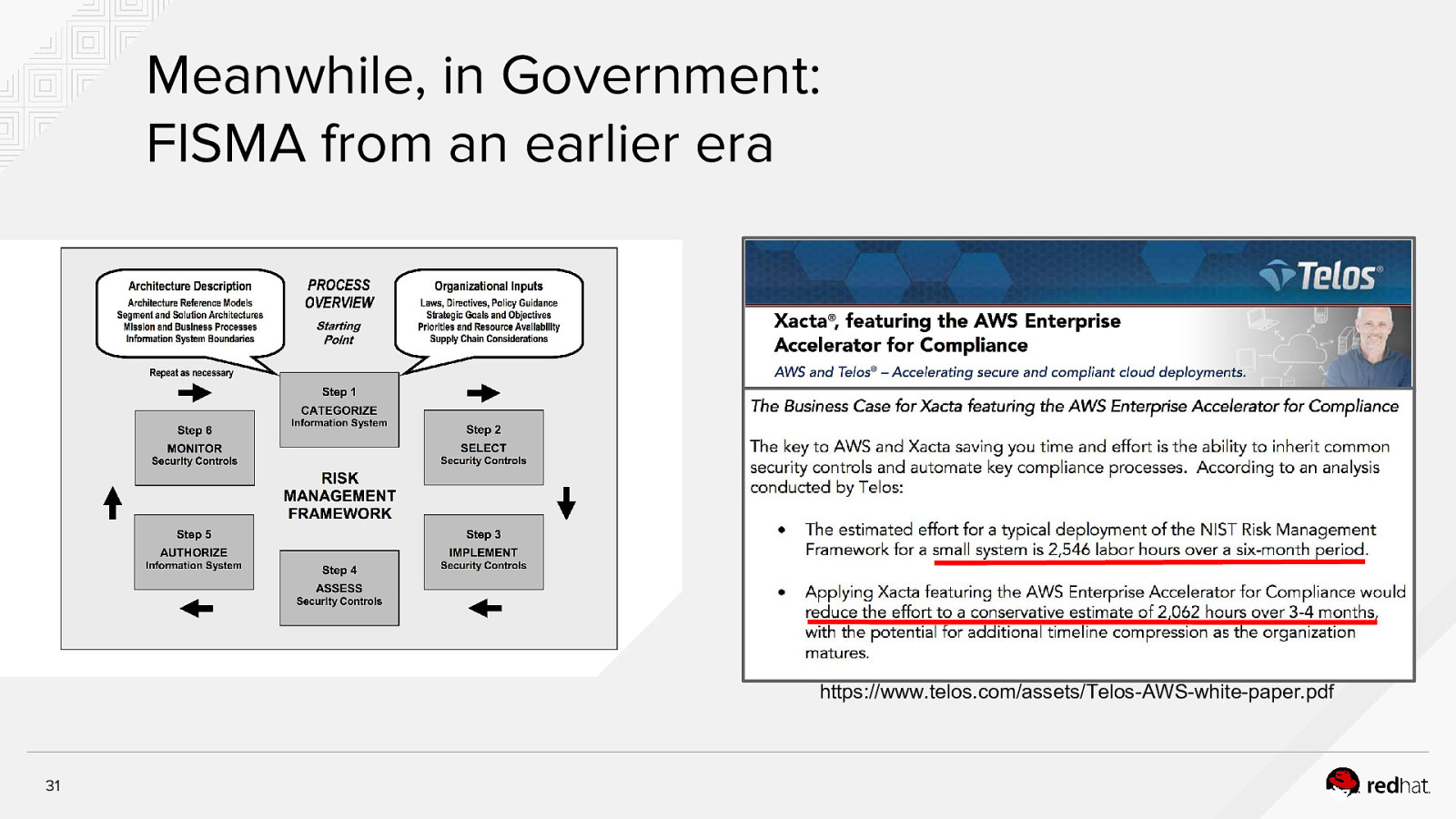
Meanwhile, in Government: FISMA from an earlier era https://www.telos.com/assets/Telos-AWS-white-paper.pdf 31
Slide 32
18F’s Project Boise https://boise.18f.gov ● ● ● ● ● 32 No lingua franca Workflows are localized, proprietary Automating ATOs is a huge, vague goal Continuous Monitoring portends a growing compliance burden Compliance prompts collaboration
Slide 33

Community created portfolio of tools and content to assess systems for known vulnerabilities. Project: https://open-scap.org Code: https://github.com/OpenSCAP 33
Slide 34

https://github.com/nsagov 34
Slide 35
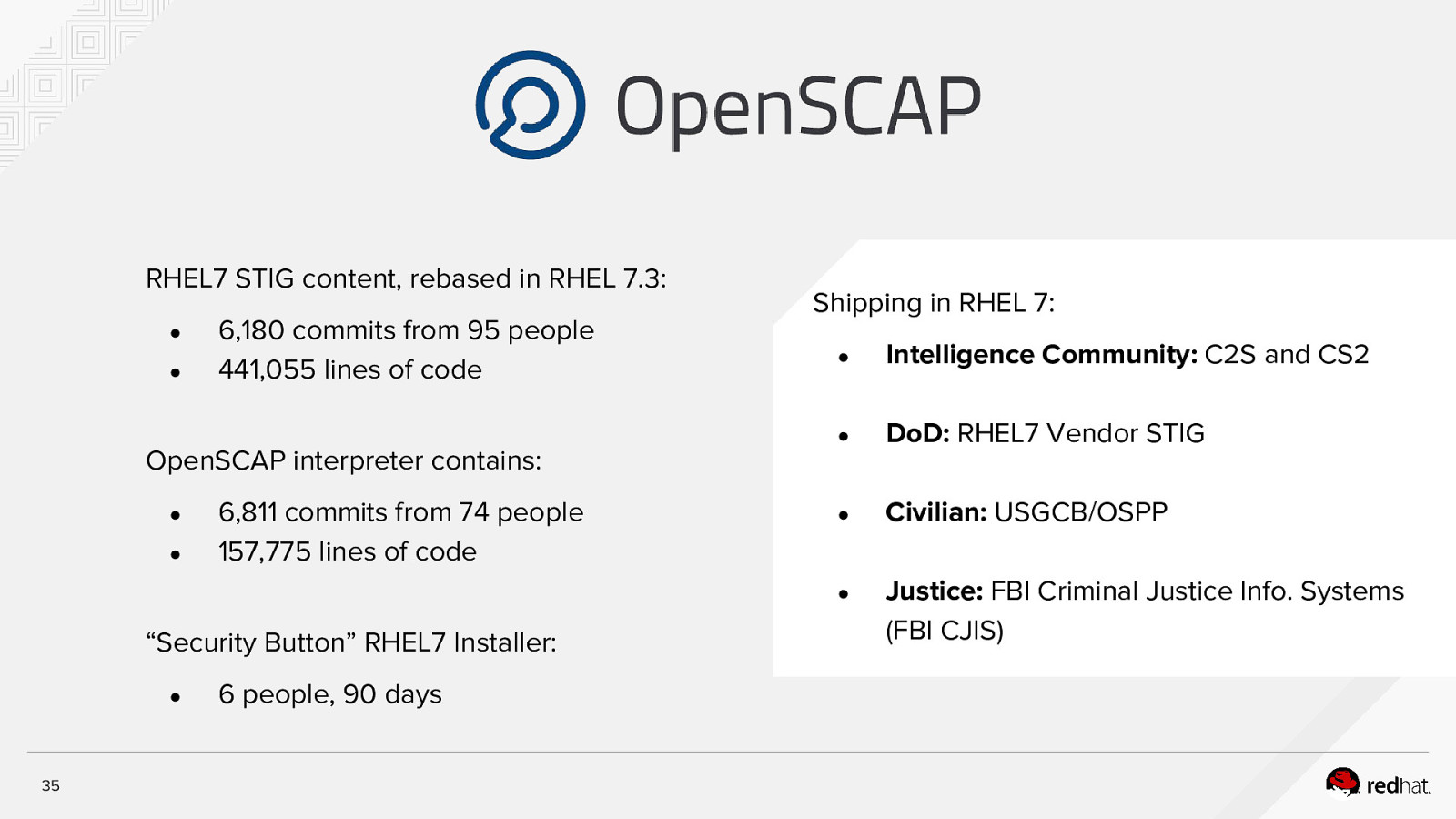
RHEL7 STIG content, rebased in RHEL 7.3: ● ● 6,180 commits from 95 people 441,055 lines of code Shipping in RHEL 7: ● Intelligence Community: C2S and CS2 ● DoD: RHEL7 Vendor STIG ● Civilian: USGCB/OSPP ● Justice: FBI Criminal Justice Info. Systems (FBI CJIS) OpenSCAP interpreter contains: ● ● 6,811 commits from 74 people 157,775 lines of code “Security Button” RHEL7 Installer: ● 35 6 people, 90 days
Slide 36
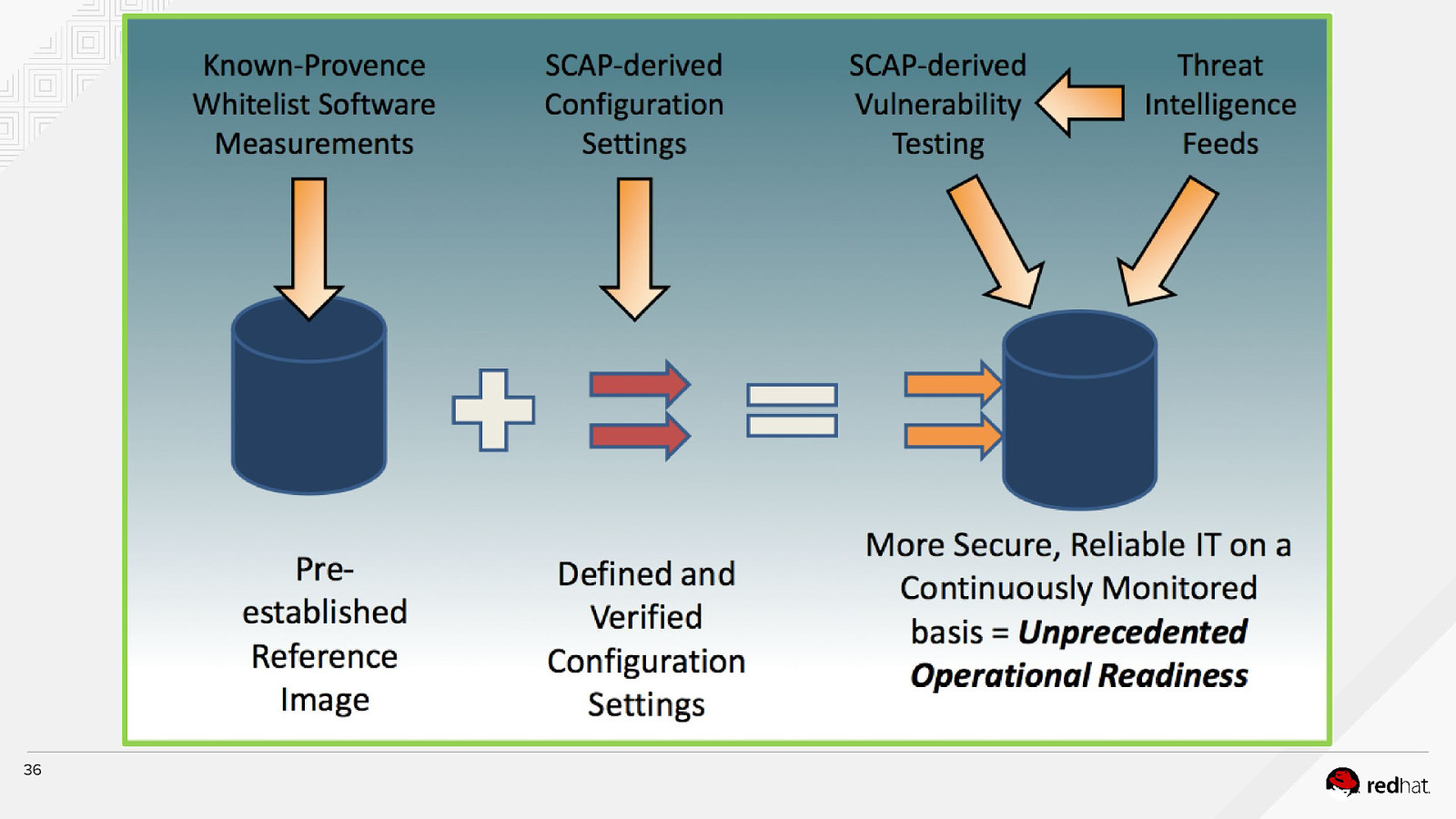
36
Slide 37
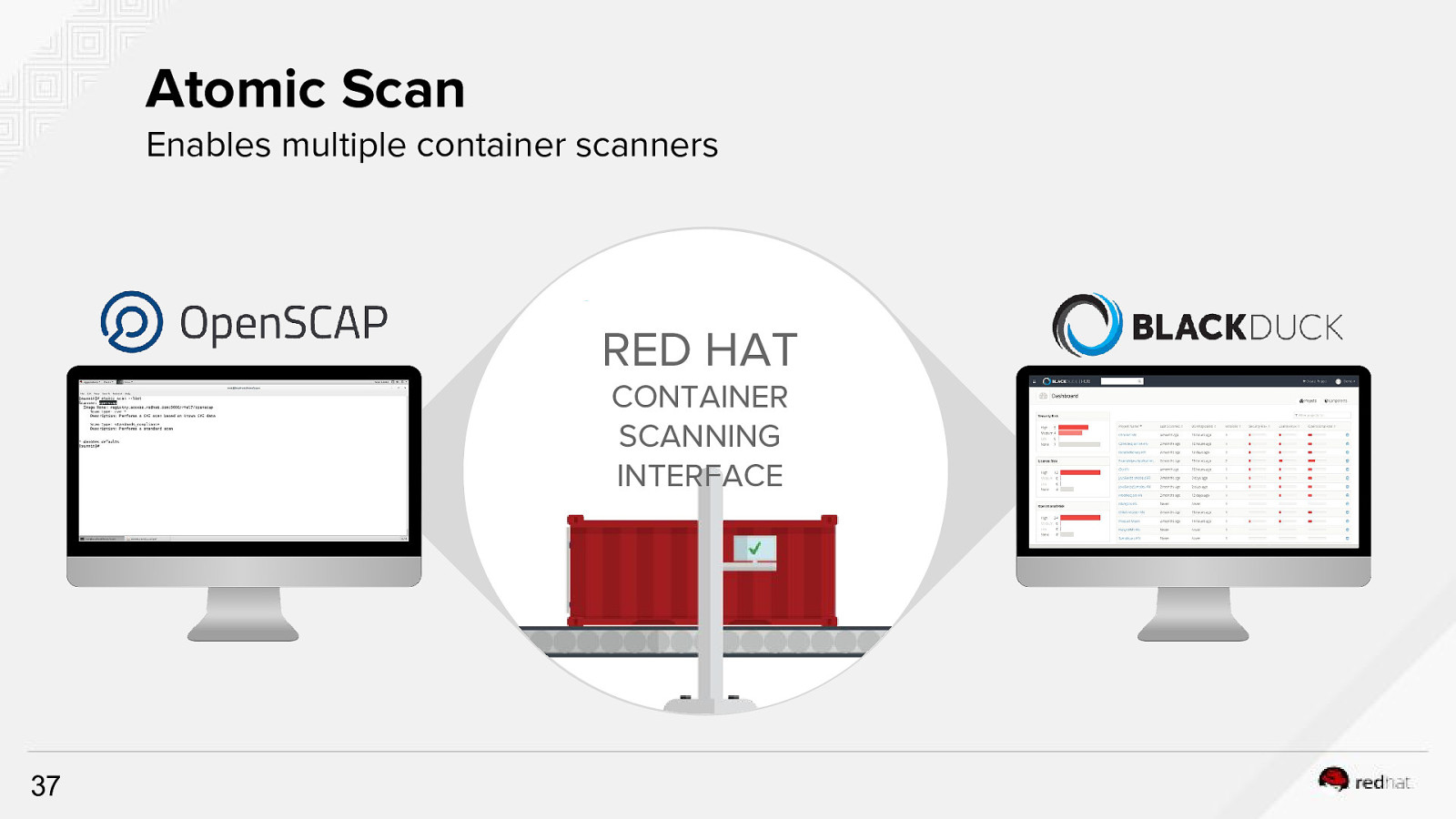
Atomic Scan Enables multiple container scanners Red Hat container scanning CONTAINER API RED HAT SCANNING INTERFACE 37
Slide 38
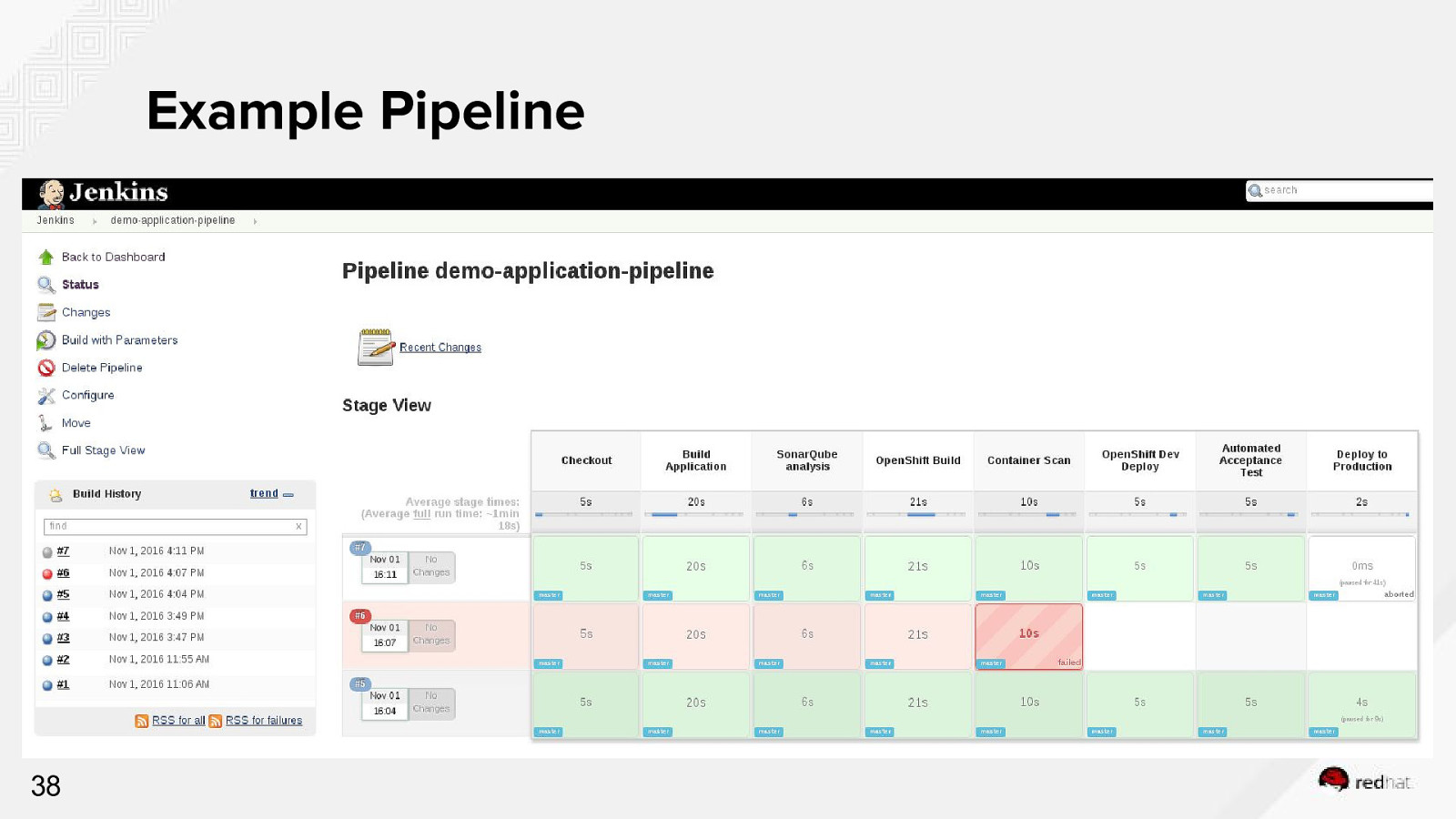
Example Pipeline 38
Slide 39
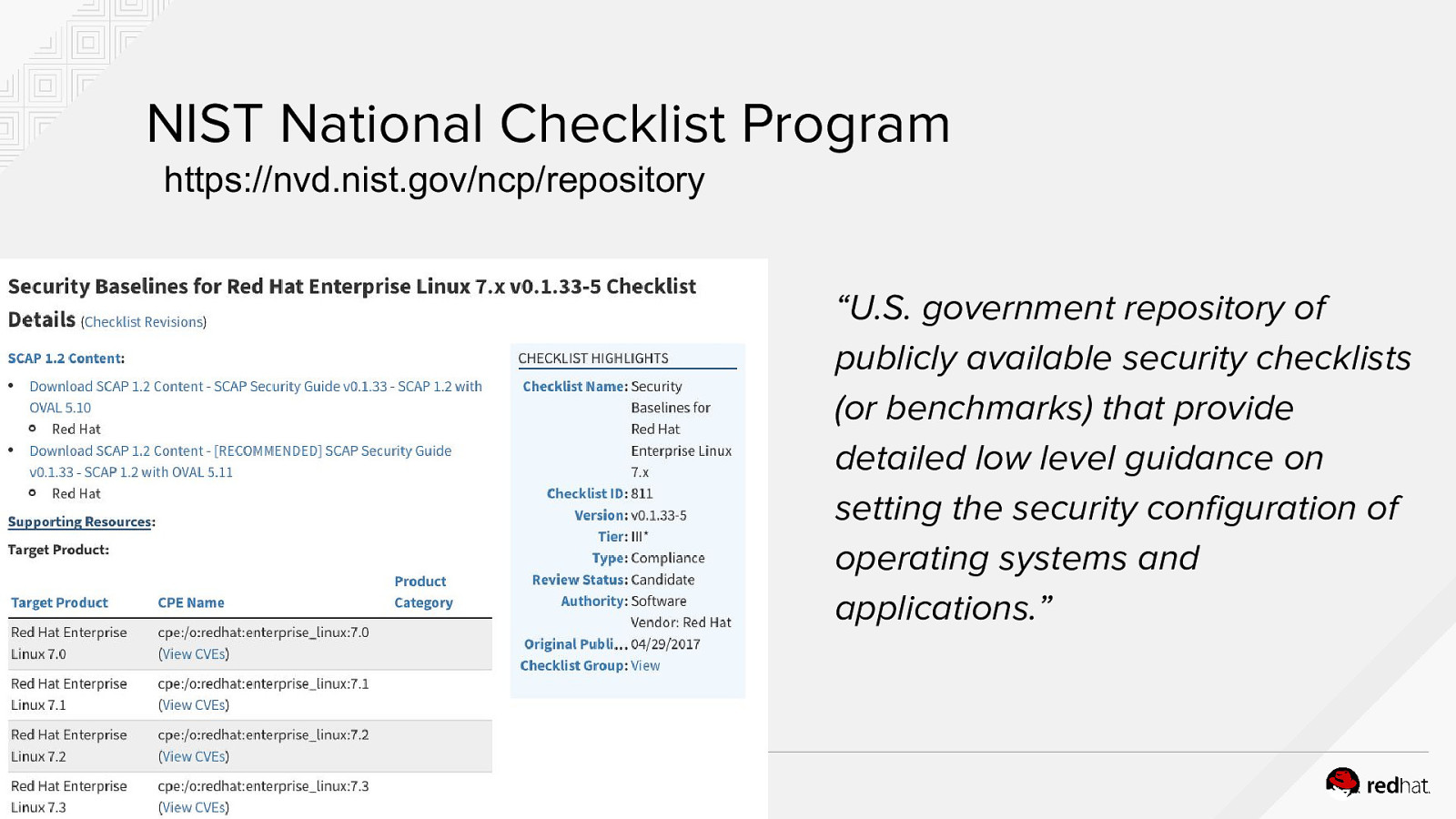
NIST National Checklist Program https://nvd.nist.gov/ncp/repository “U.S. government repository of publicly available security checklists (or benchmarks) that provide detailed low level guidance on setting the security configuration of operating systems and applications.” 39
Slide 40

Contact Info EMail: shawn@redhat.com LinkedIn: https://www.linkedin.com/in/shawndwells/ Cell: 443-534-0130 (US EST) OpenSCAP Slides + Videos: https://github.com/OpenSCAP/scap-security-guide/wiki/Collateral-and-References OpenShift Ansible Scripts: https://github.com/redhatdemocentral/ocp-install-demo 40