Presented with Shut Down the Hackers
Slide 1

Slide 2

50 MINUTES, 3 GOALS (+10MIN Q&A) 1. Discuss existing & emerging technologies for continuous monitoring - Vulnerability Management - Configuration Management 2. Share DoD Centralized Super Computing Facility story 3. Data standardization technologies
Slide 3
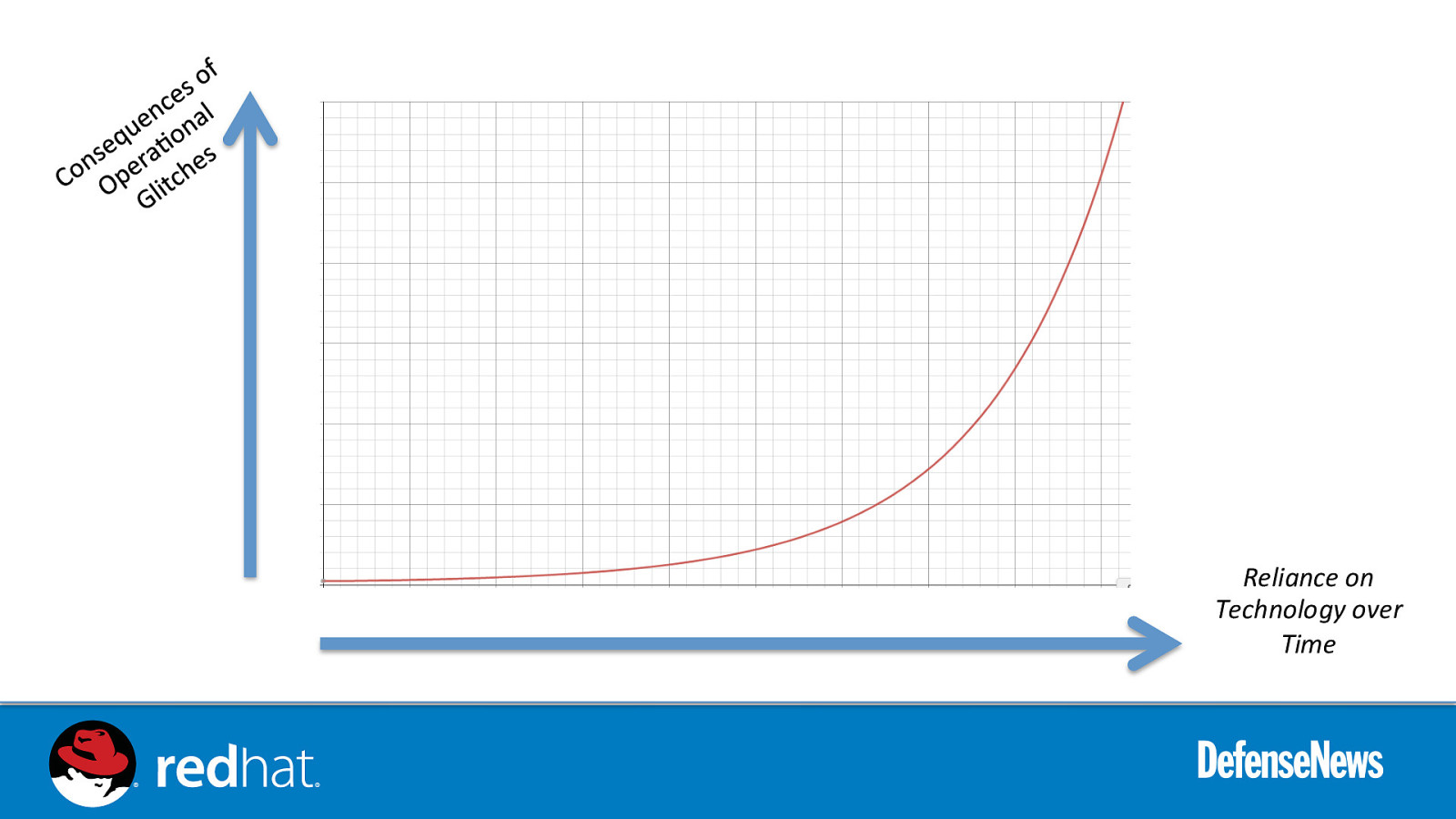
Reliance on Technology over Time
Slide 4
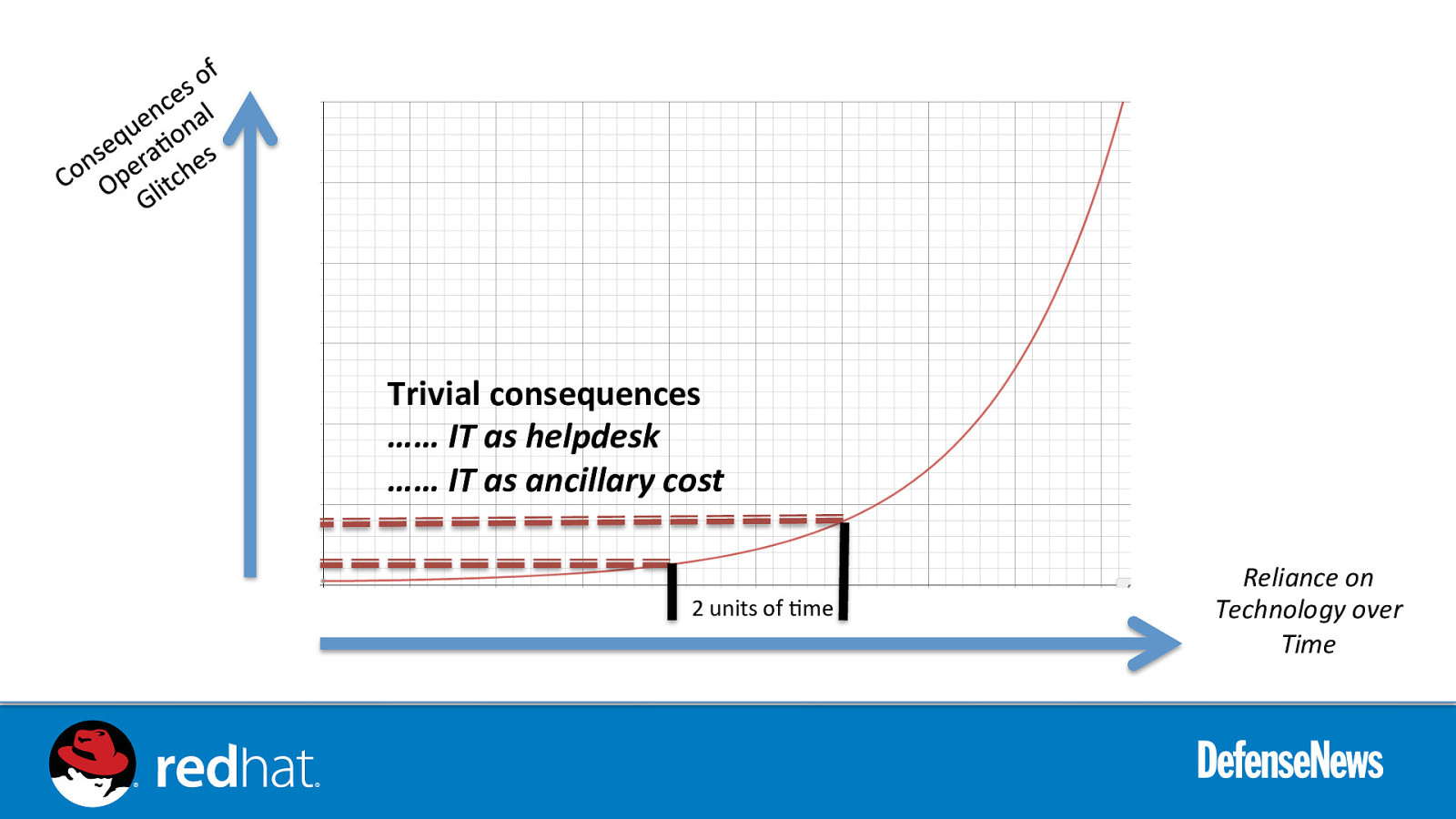
Trivial consequences …… IT as helpdesk …… IT as ancillary cost 2 units of 0me Reliance on Technology over Time
Slide 5
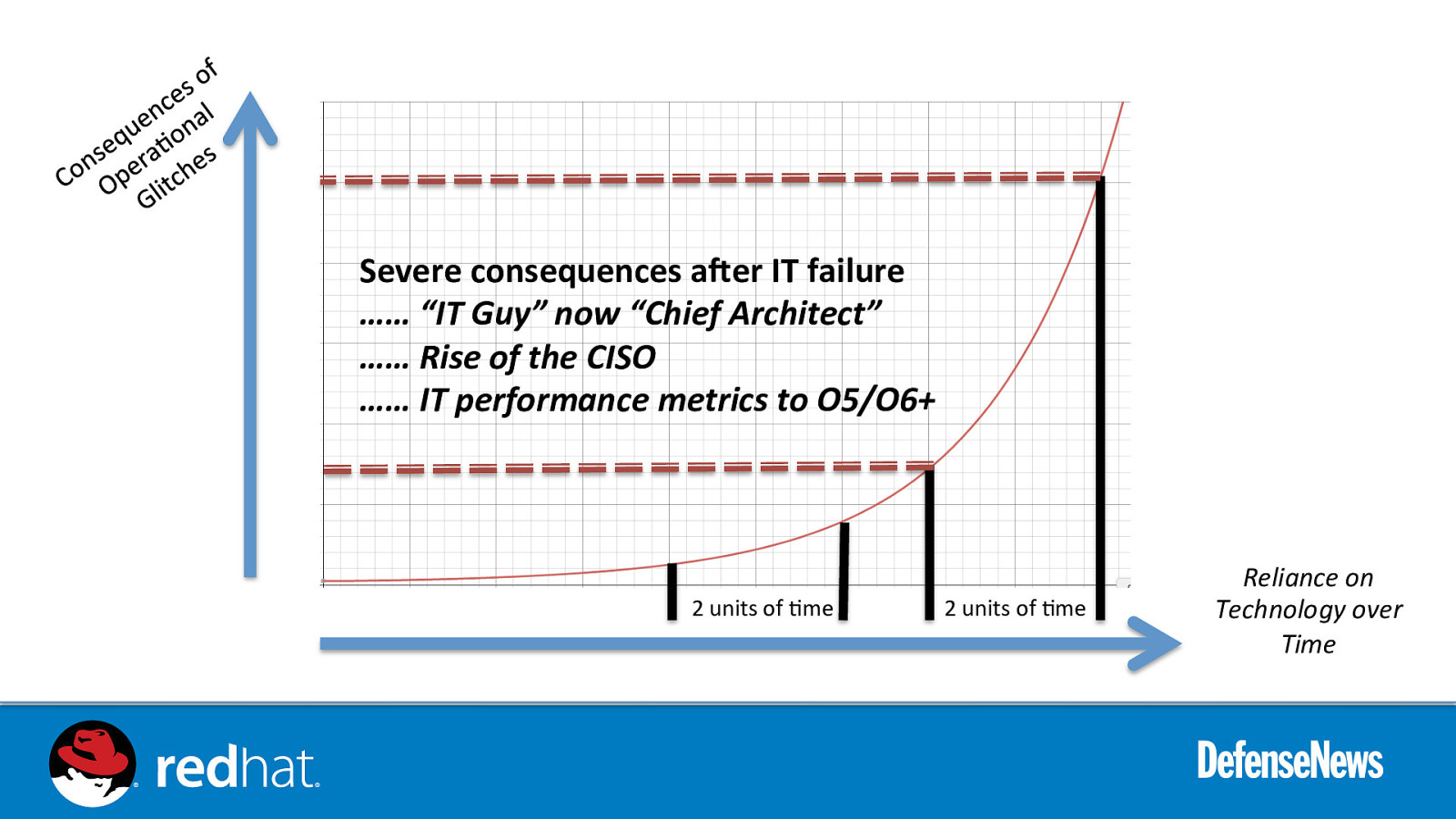
Severe consequences a6er IT failure …… “IT Guy” now “Chief Architect” …… Rise of the CISO …… IT performance metrics to O5/O6+ 2 units of 0me 2 units of 0me Reliance on Technology over Time
Slide 6

Ever-Increasing Capability & Complexity Biplane: 0 LOC FUNCTIONALITY & COMPLEXITY OPERATIONAL RISK
Slide 7

Ever-Increasing Capability & Complexity Biplane: 0 LOC Lunar Module: 2K LOC FUNCTIONALITY & COMPLEXITY OPERATIONAL RISK
Slide 8

Ever-Increasing Capability & Complexity Biplane: 0 LOC Lunar Module: 2K LOC FUNCTIONALITY & COMPLEXITY OPERATIONAL RISK F-35: 9.9M LOC
Slide 9
Slide 10
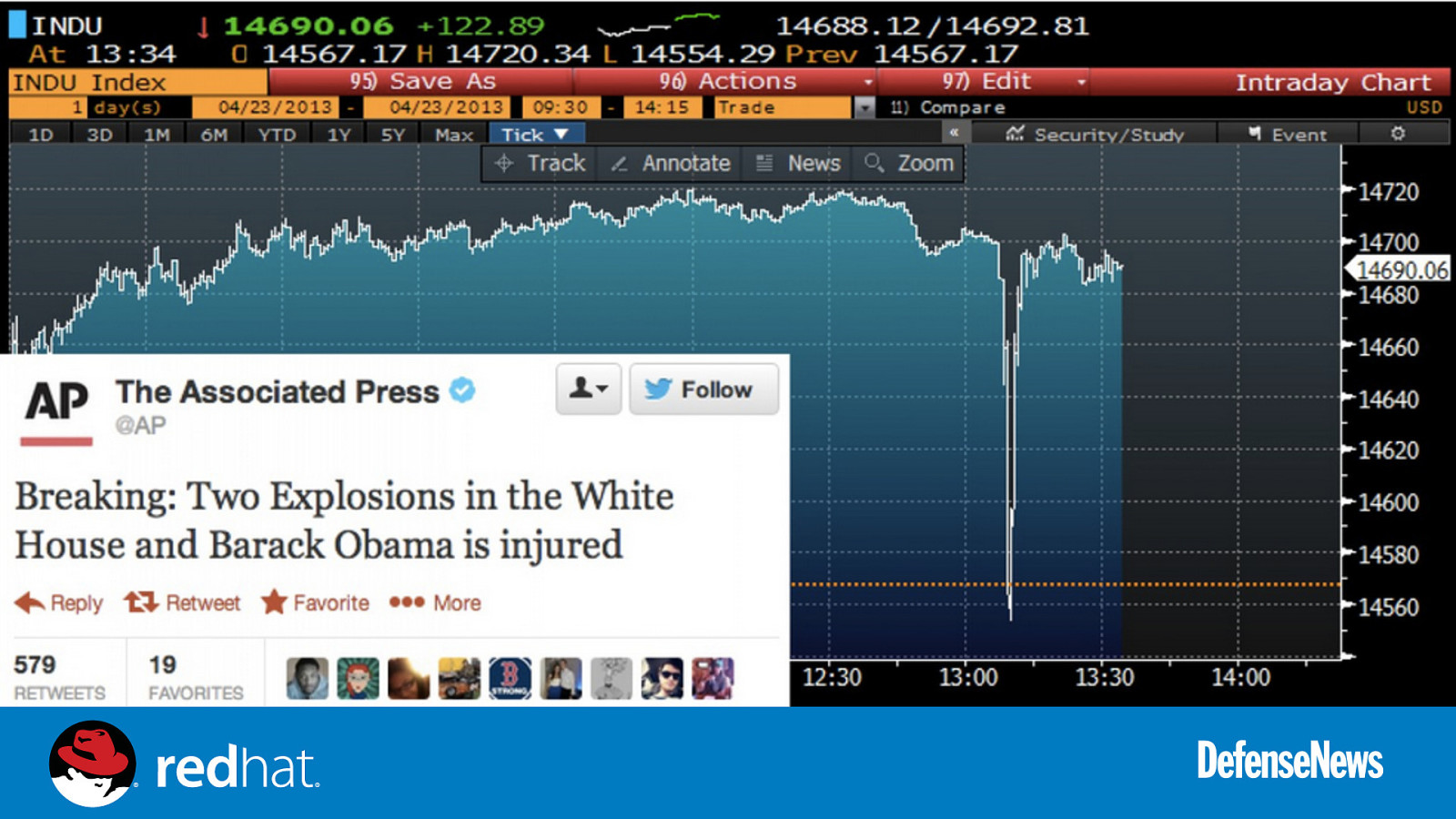
April 2013
Slide 11
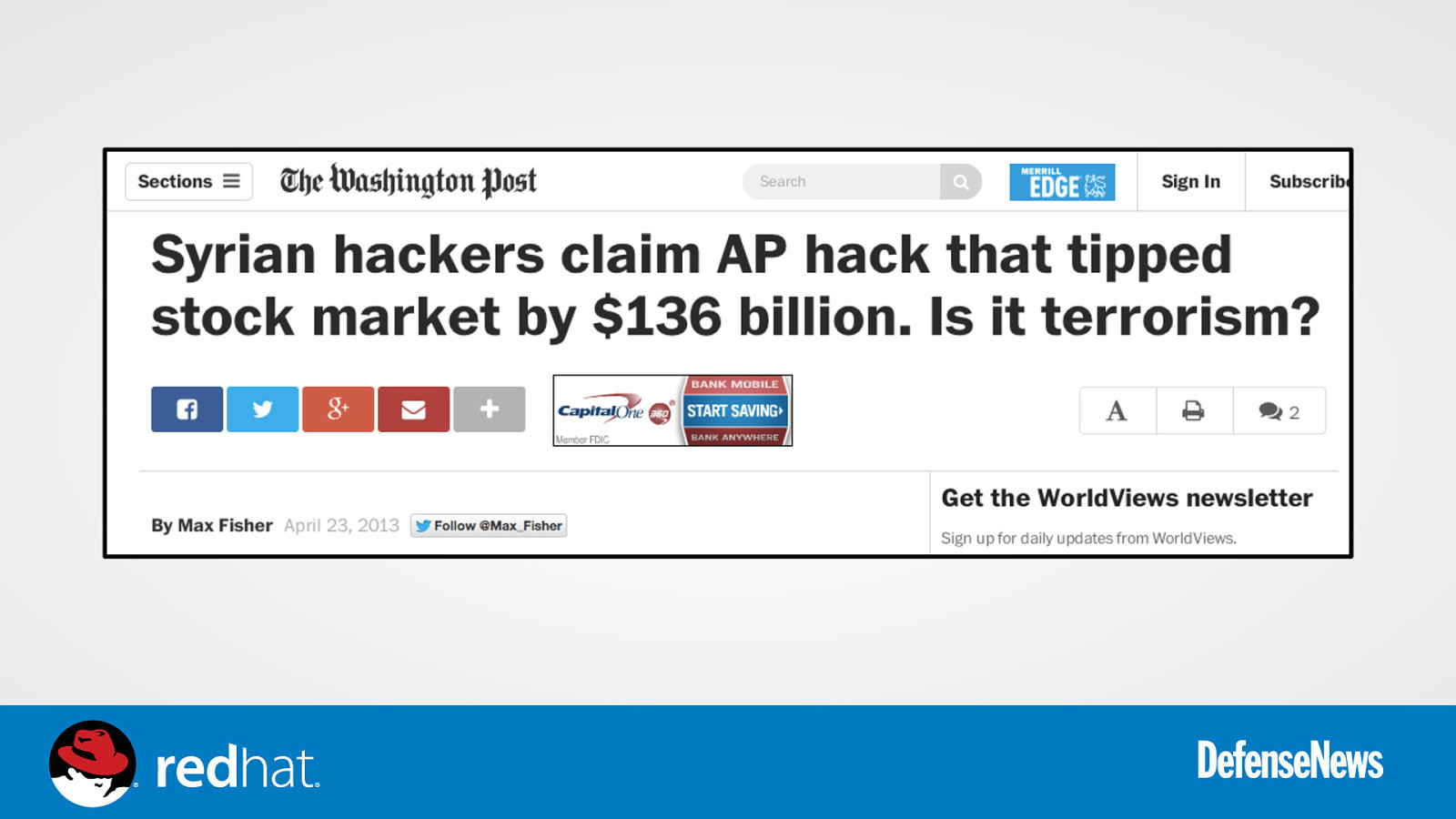
Slide 12

“In April 2013, AQI’s leader Abu Bakr al-‐Baghdadi declared the group was opera0ng in Syria and changed its public name to the Islamic State of Iraq and the Levant(ISIL).” h2p://www.state.gov/documents/organiza0on/ 225886.pdf “On April 30, the U.S. State Department noted that private dona0ons from Persian Gulf countries were ”a major source of funding for Sunni terrorist groups, par0cularly…in Syria,” calling the problem one of the most important counterterrorism issues during the previous calendar year. Groups such as al-‐Qaeda’s Syrian affiliate, Jabhat al-‐Nusra, and the Islamic State of Iraq and al-‐Sham (ISIS), previously known as al-‐Qaeda in Iraq, are believed to be frequent recipients of some of the hundreds of millions of dollars that wealthy ci0zens and others in the Gulf peninsula have been dona0ng during the Syrian conflict.”
Slide 13
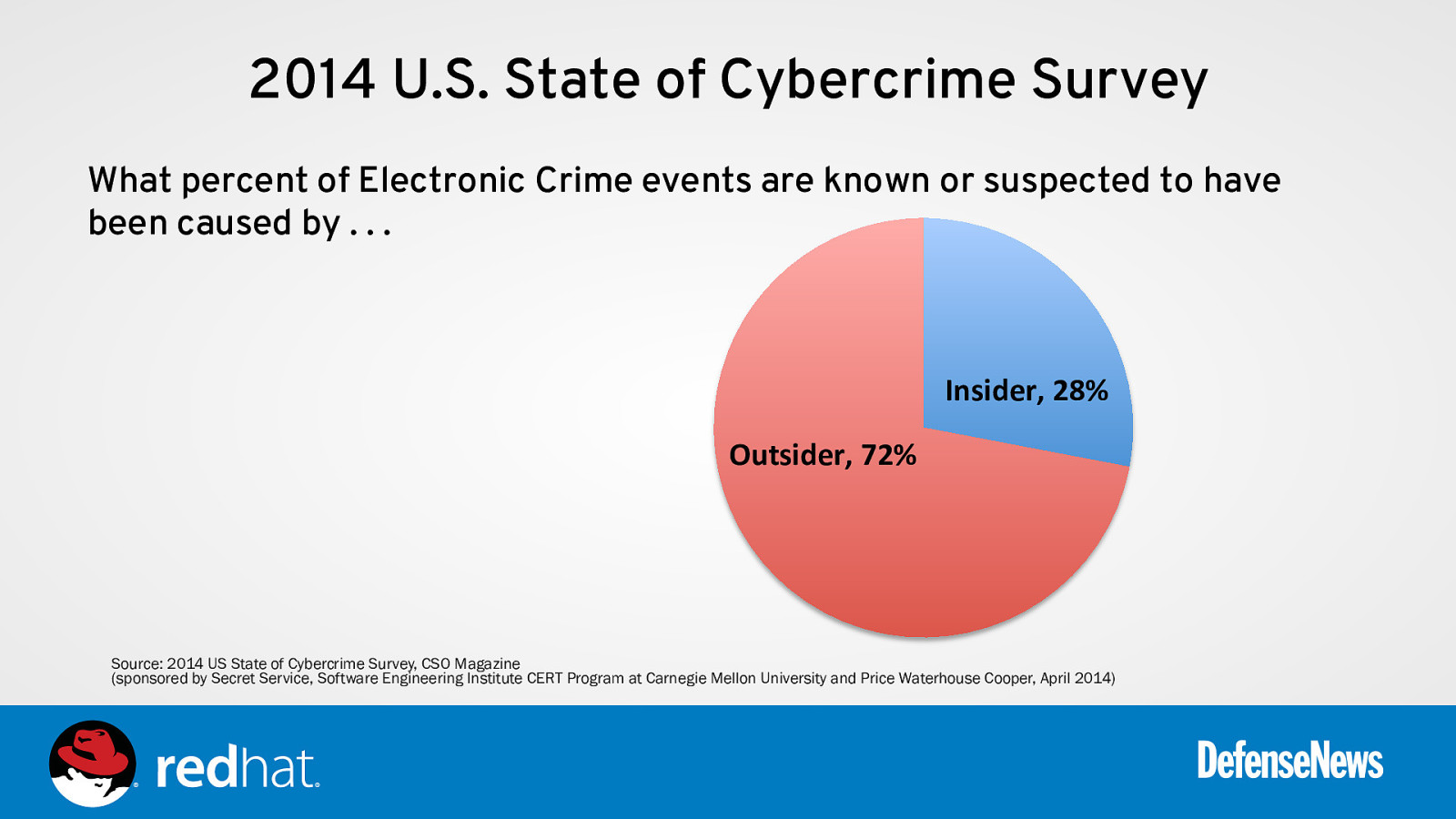
2014 U.S. State of Cybercrime Survey What percent of Electronic Crime events are known or suspected to have been caused by … Insider, 28% Outsider, 72% Source: 2014 US State of Cybercrime Survey, CSO Magazine (sponsored by Secret Service, Software Engineering Institute CERT Program at Carnegie Mellon University and Price Waterhouse Cooper, April 2014)
Slide 14
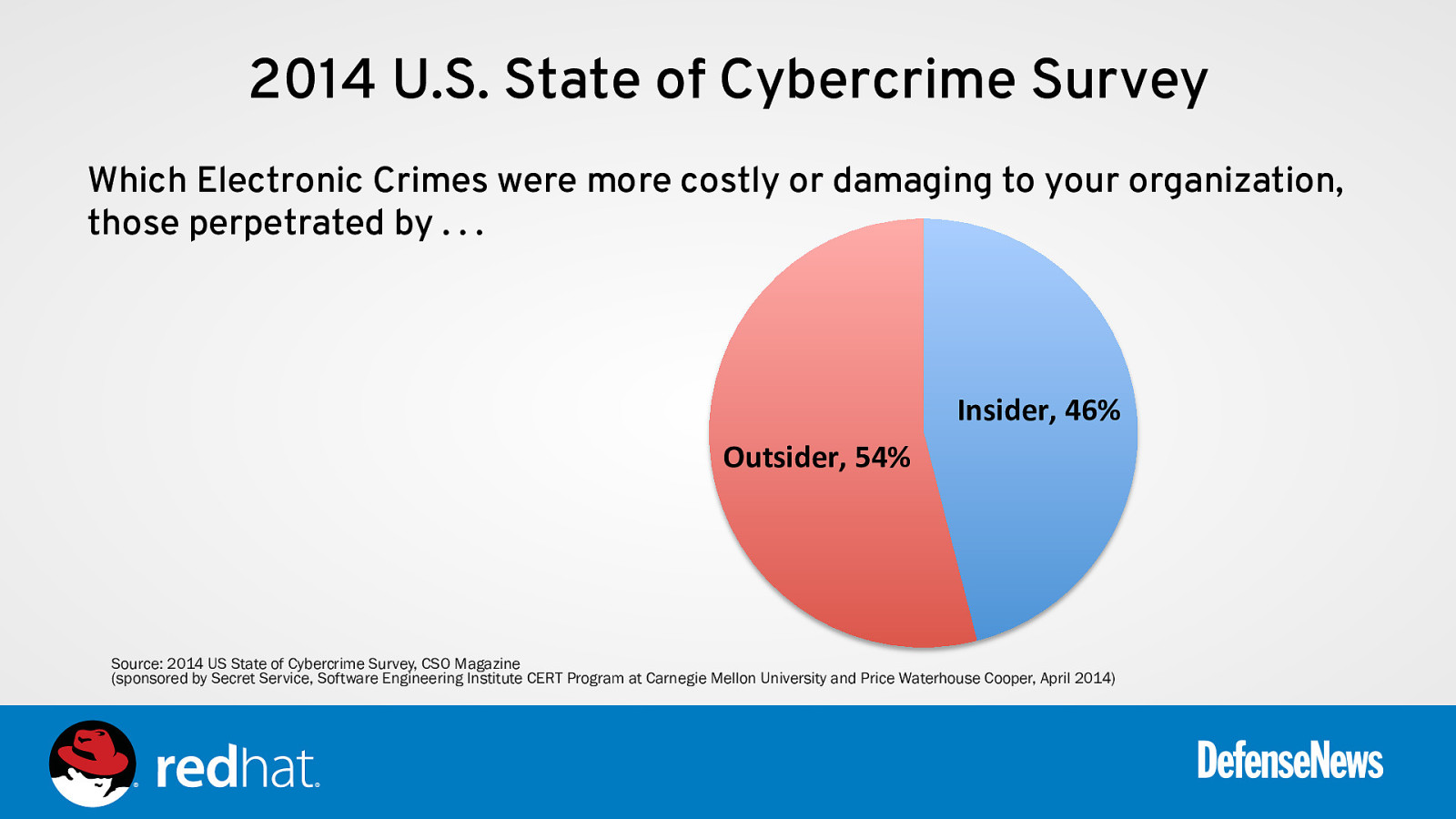
2014 U.S. State of Cybercrime Survey Which Electronic Crimes were more costly or damaging to your organization, those perpetrated by … Insider, 46% Outsider, 54% Source: 2014 US State of Cybercrime Survey, CSO Magazine (sponsored by Secret Service, Software Engineering Institute CERT Program at Carnegie Mellon University and Price Waterhouse Cooper, April 2014)
Slide 15
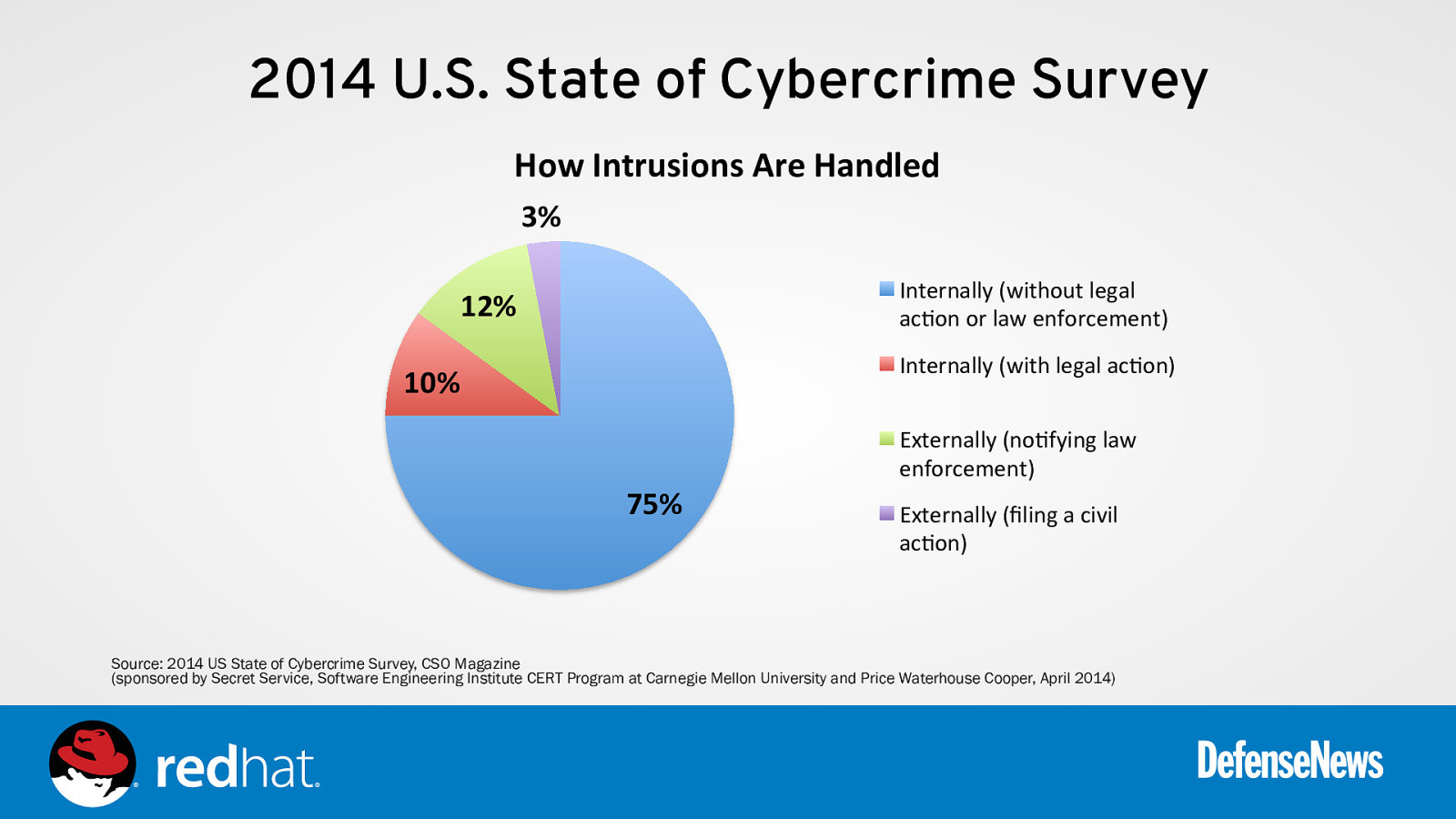
2014 U.S. State of Cybercrime Survey How Intrusions Are Handled 3% Internally (without legal ac0on or law enforcement) 12% Internally (with legal ac0on) 10% Externally (no0fying law enforcement) 75% Externally (filing a civil ac0on) Source: 2014 US State of Cybercrime Survey, CSO Magazine (sponsored by Secret Service, Software Engineering Institute CERT Program at Carnegie Mellon University and Price Waterhouse Cooper, April 2014)
Slide 16
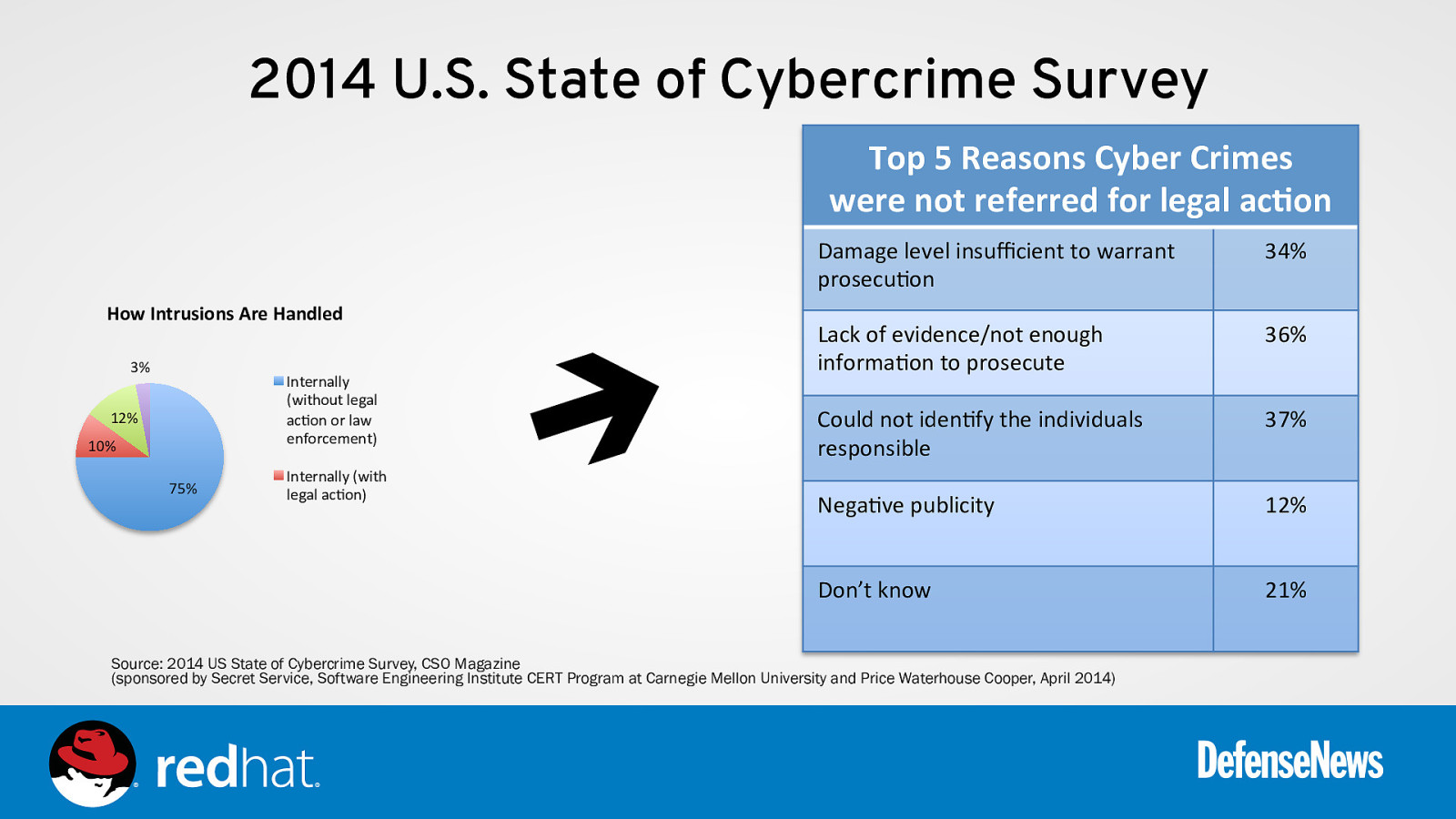
2014 U.S. State of Cybercrime Survey Top 5 Reasons Cyber Crimes were not referred for legal acNon How Intrusions Are Handled 3% Internally (without legal ac0on or law enforcement) 12% 10% 75% Internally (with legal ac0on)
è Damage level insufficient to warrant prosecu0on 34% Lack of evidence/not enough informa0on to prosecute 36% Could not iden0fy the individuals responsible 37% Nega0ve publicity 12% Don’t know 21% Source: 2014 US State of Cybercrime Survey, CSO Magazine (sponsored by Secret Service, Software Engineering Institute CERT Program at Carnegie Mellon University and Price Waterhouse Cooper, April 2014)
Slide 17
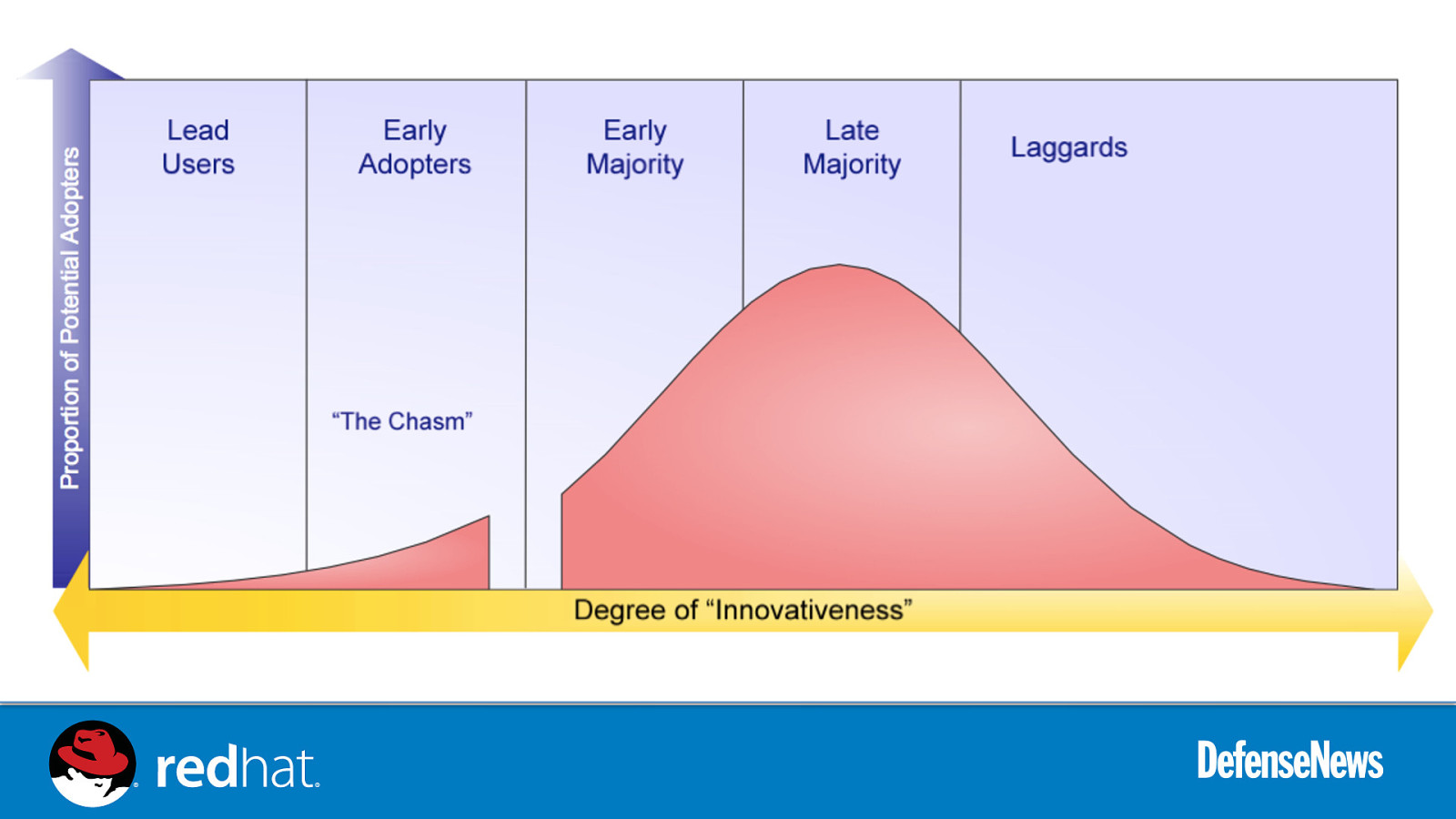
Slide 18
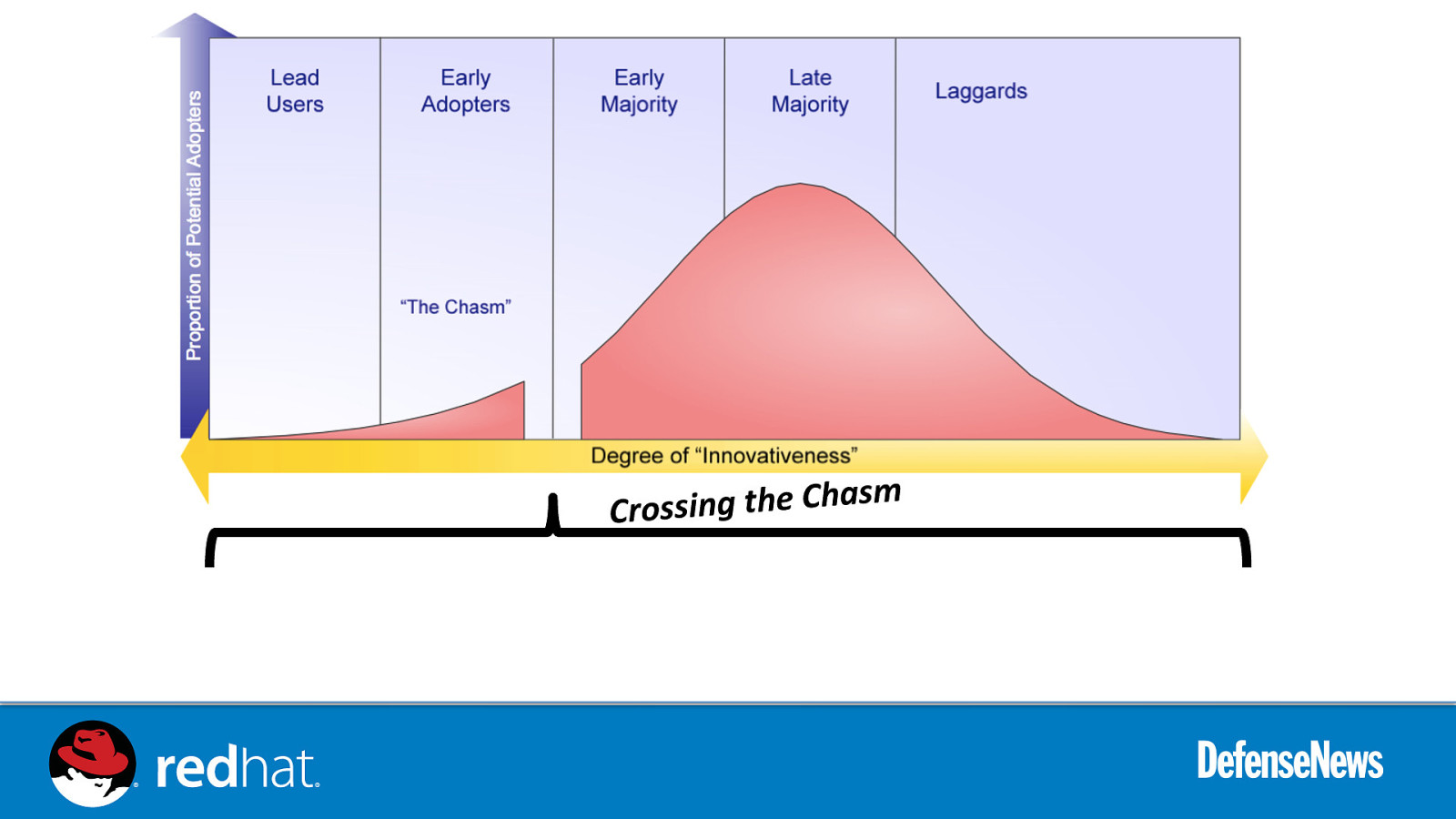
m s Crossing the Cha
Slide 19
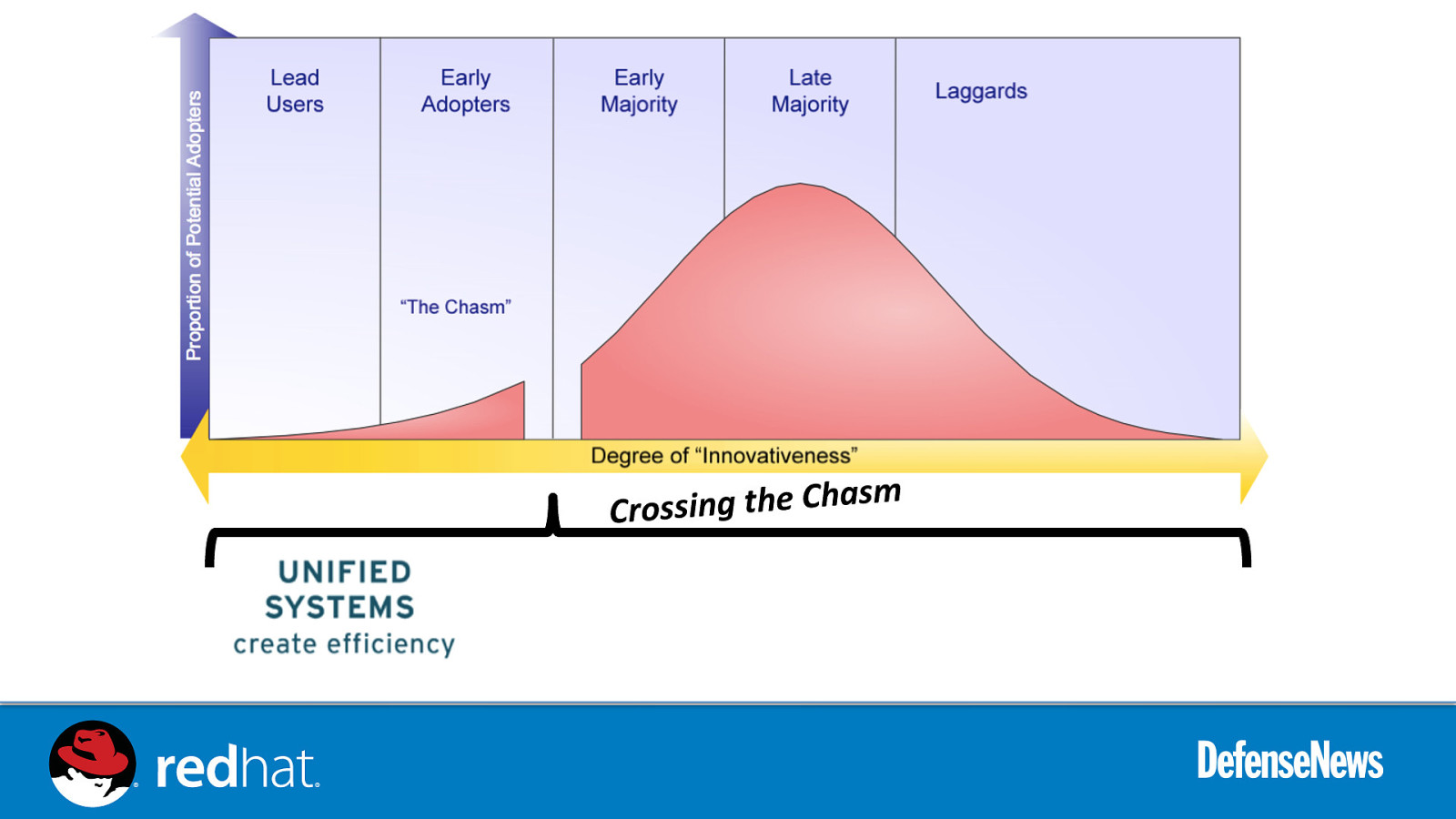
m s Crossing the Cha
Slide 20
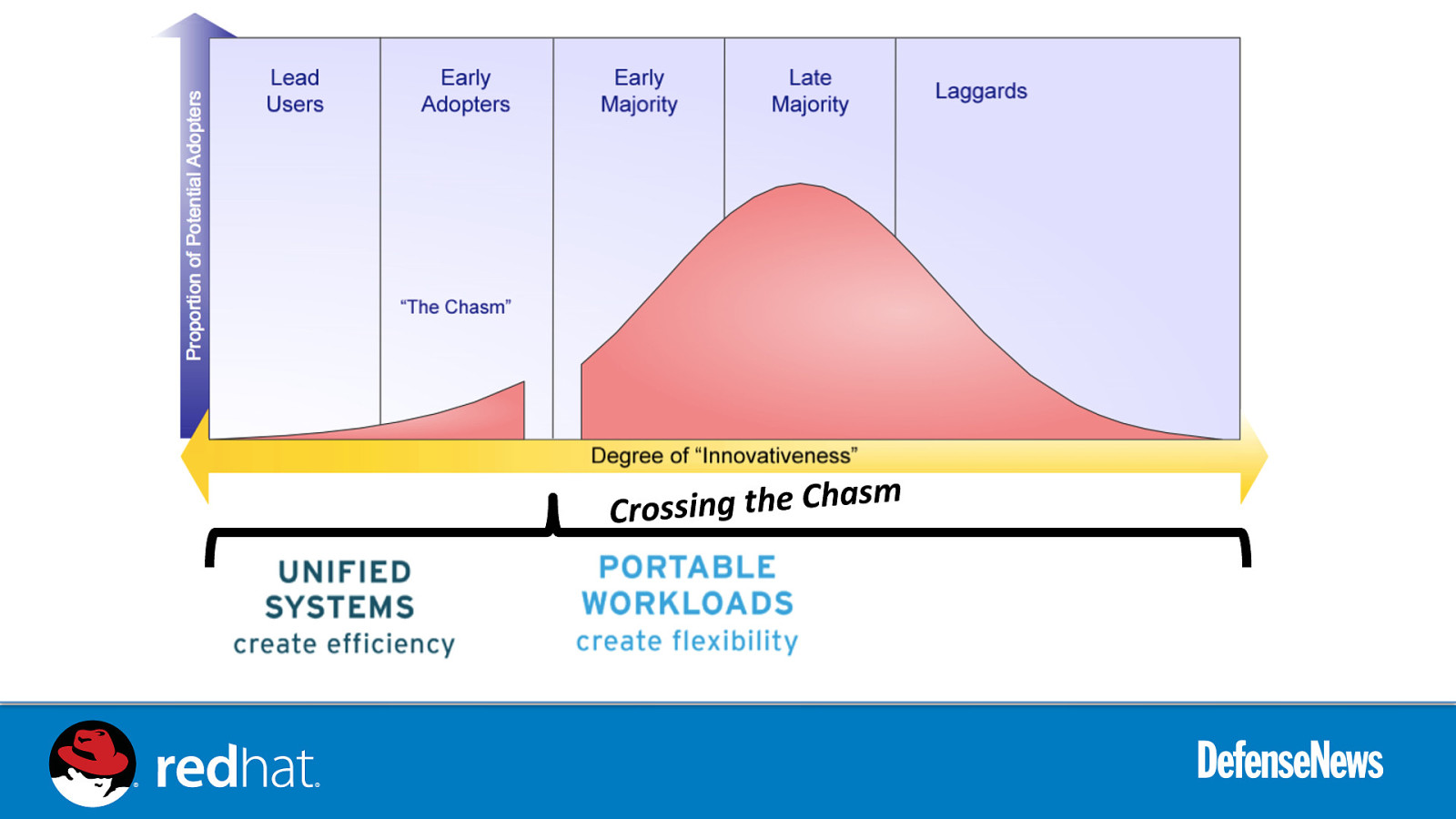
m s Crossing the Cha
Slide 21
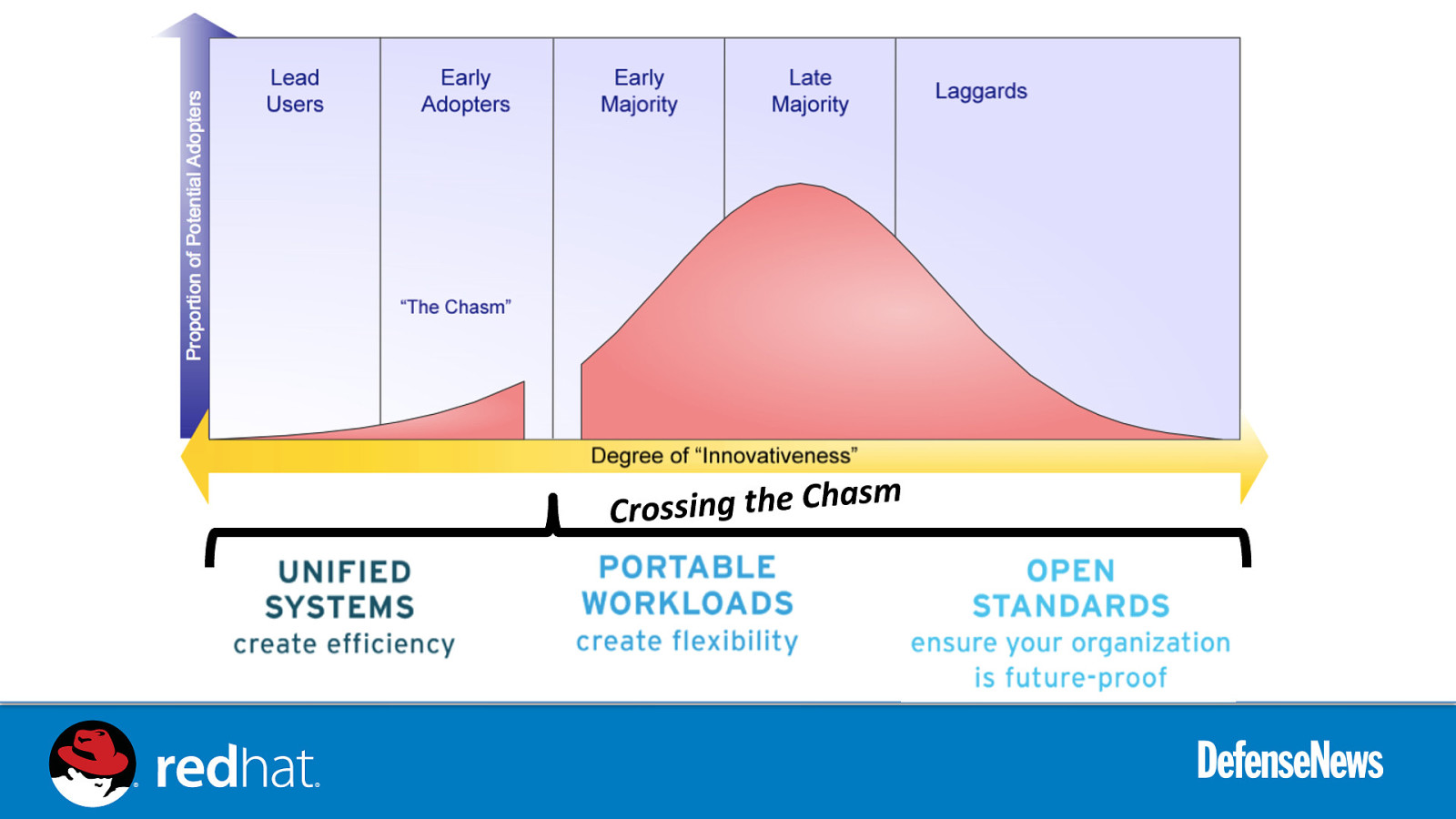
m s Crossing the Cha
Slide 22
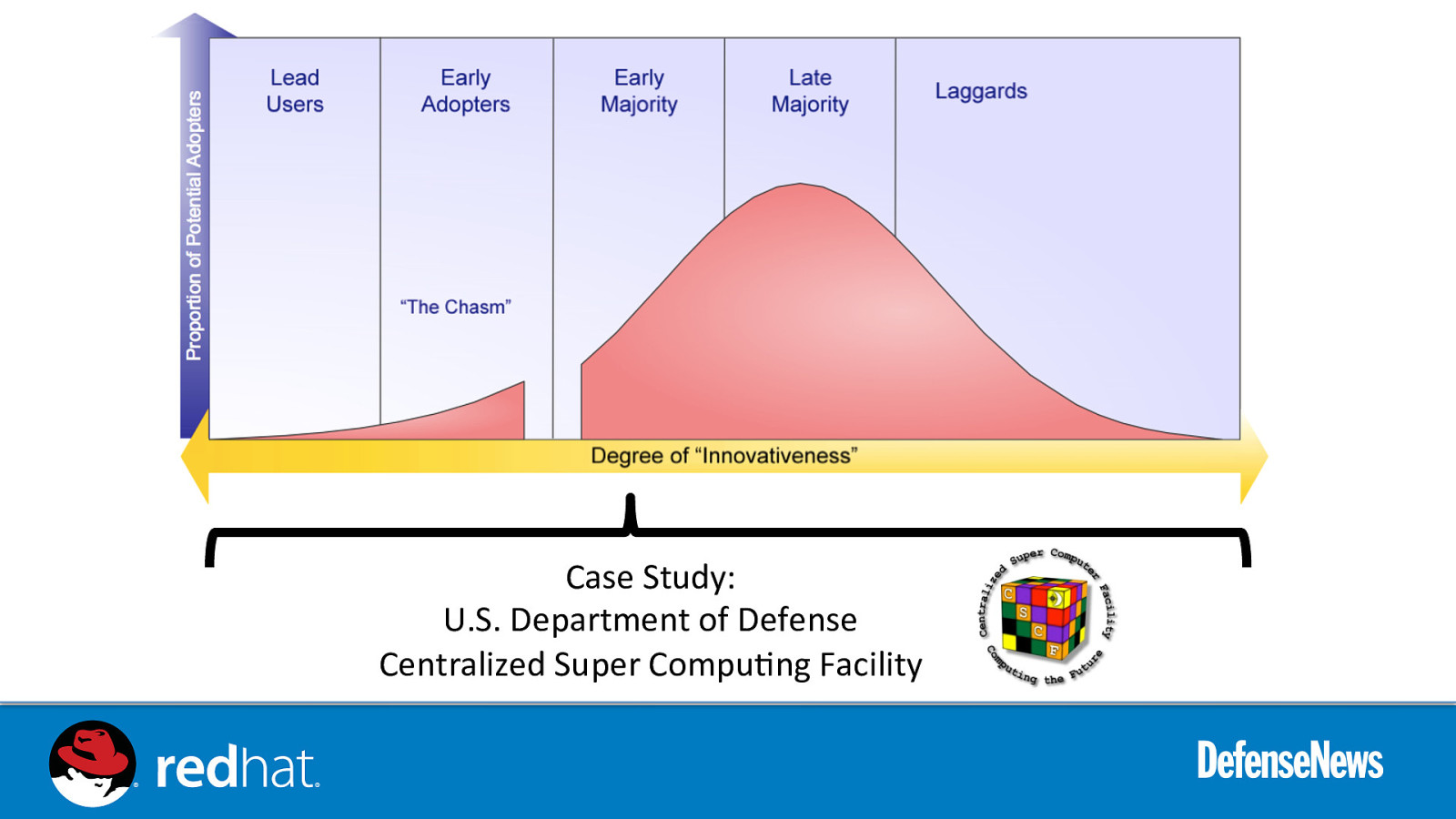
Case Study: U.S. Department of Defense Centralized Super Compu0ng Facility
Slide 23
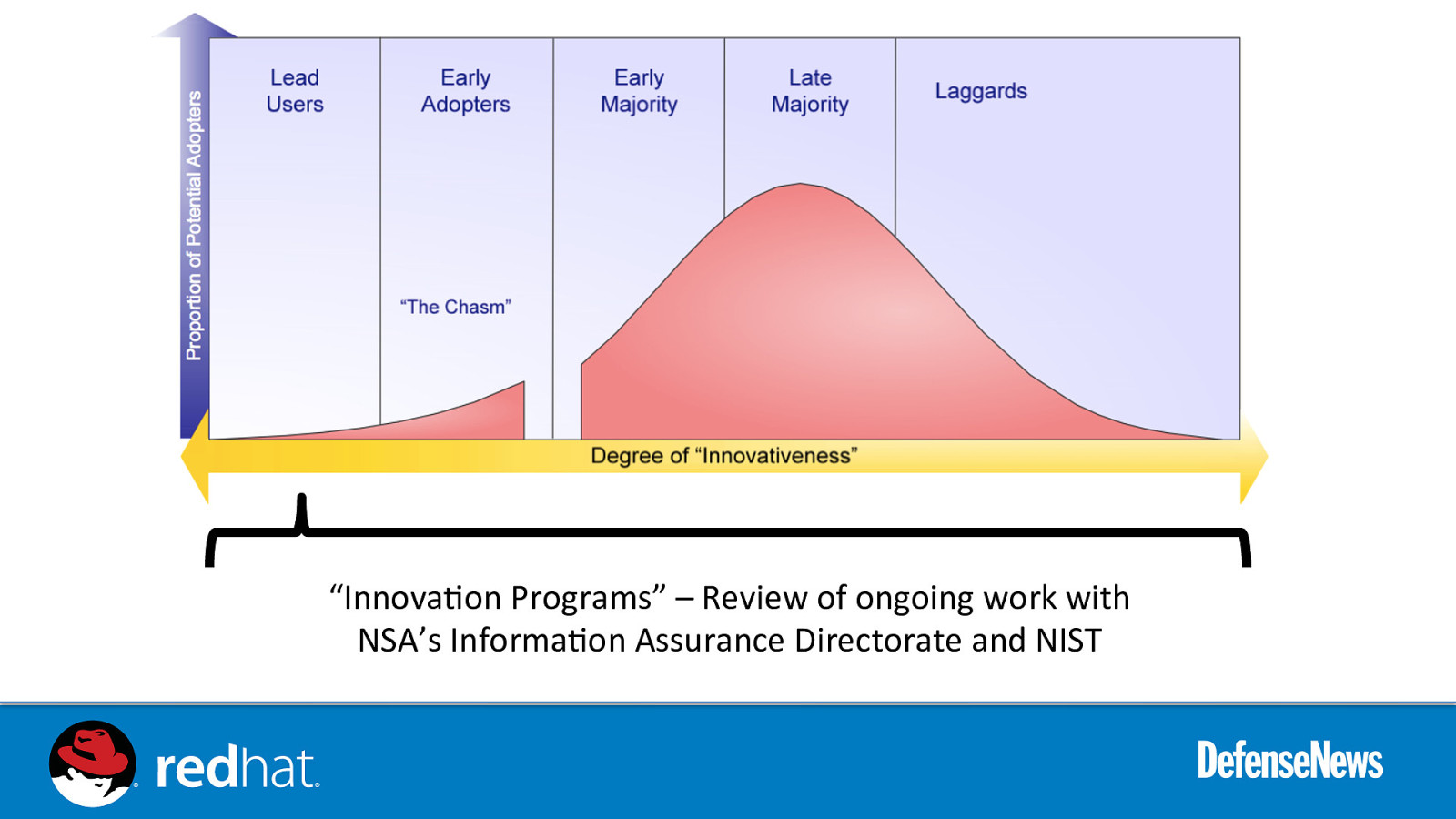
“Innova0on Programs” – Review of ongoing work with NSA’s Informa0on Assurance Directorate and NIST
Slide 24
Slide 25

“80% of a2acks leverage known vulnerabili0es and configura0on management sekng weaknesses” h2p://www.gao.gov/assets/120/110329.pdf
Slide 26

UNIFIED SYSTEMS - LOWERING RISK -
Correcting “tunnel vision”
Slide 27

UNIFIED SYSTEMS - LOWERING RISK -
Correcting “tunnel vision” Using math and statistics to accelerate corrective action
Slide 28

UNIFIED SYSTEMS - LOWERING RISK -
Correcting “tunnel vision” Using math and statistics to accelerate corrective action Daily risk calculations/priorities
Slide 29
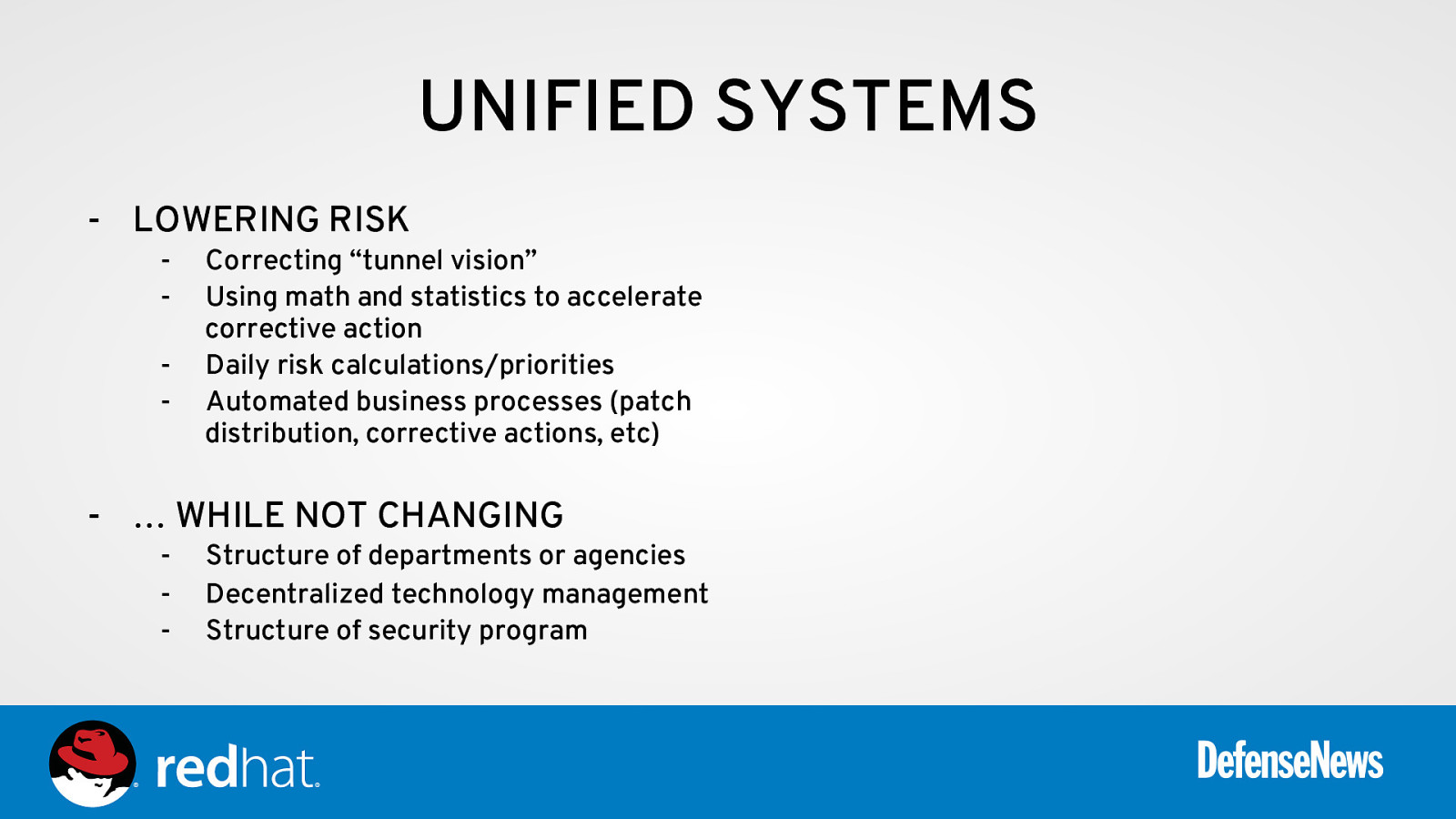
UNIFIED SYSTEMS - LOWERING RISK - Correcting “tunnel vision” Using math and statistics to accelerate corrective action Daily risk calculations/priorities Automated business processes (patch distribution, corrective actions, etc)
- … WHILE NOT CHANGING - Structure of departments or agencies Decentralized technology management Structure of security program
Slide 30
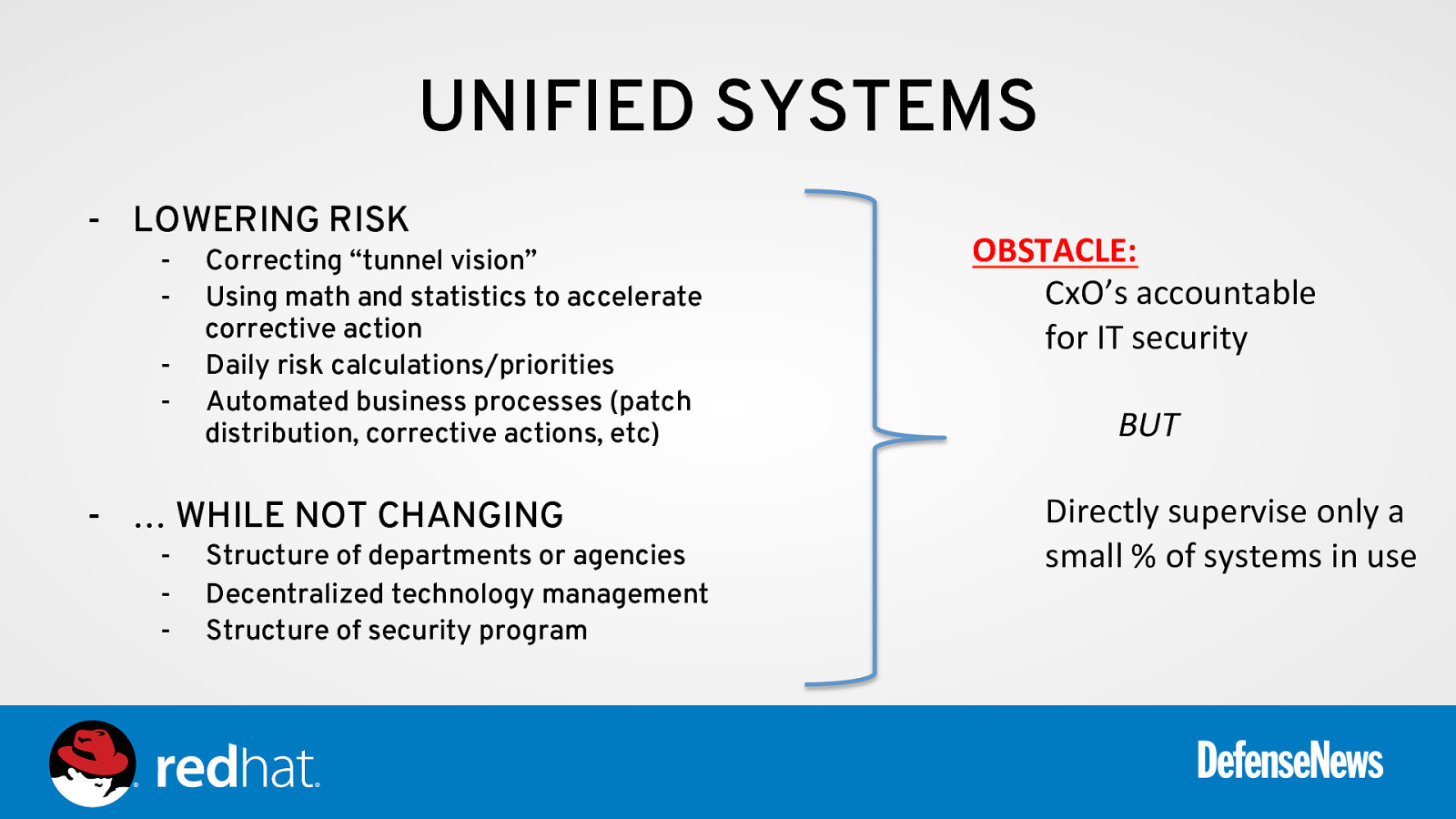
UNIFIED SYSTEMS - LOWERING RISK - Correcting “tunnel vision” Using math and statistics to accelerate corrective action Daily risk calculations/priorities Automated business processes (patch distribution, corrective actions, etc)
- … WHILE NOT CHANGING - Structure of departments or agencies Decentralized technology management Structure of security program OBSTACLE: CxO’s accountable for IT security BUT Directly supervise only a small % of systems in use
Slide 31

Slide 32

An SCAP Primer - Security Content Automation Protocol (SCAP)
Slide 33
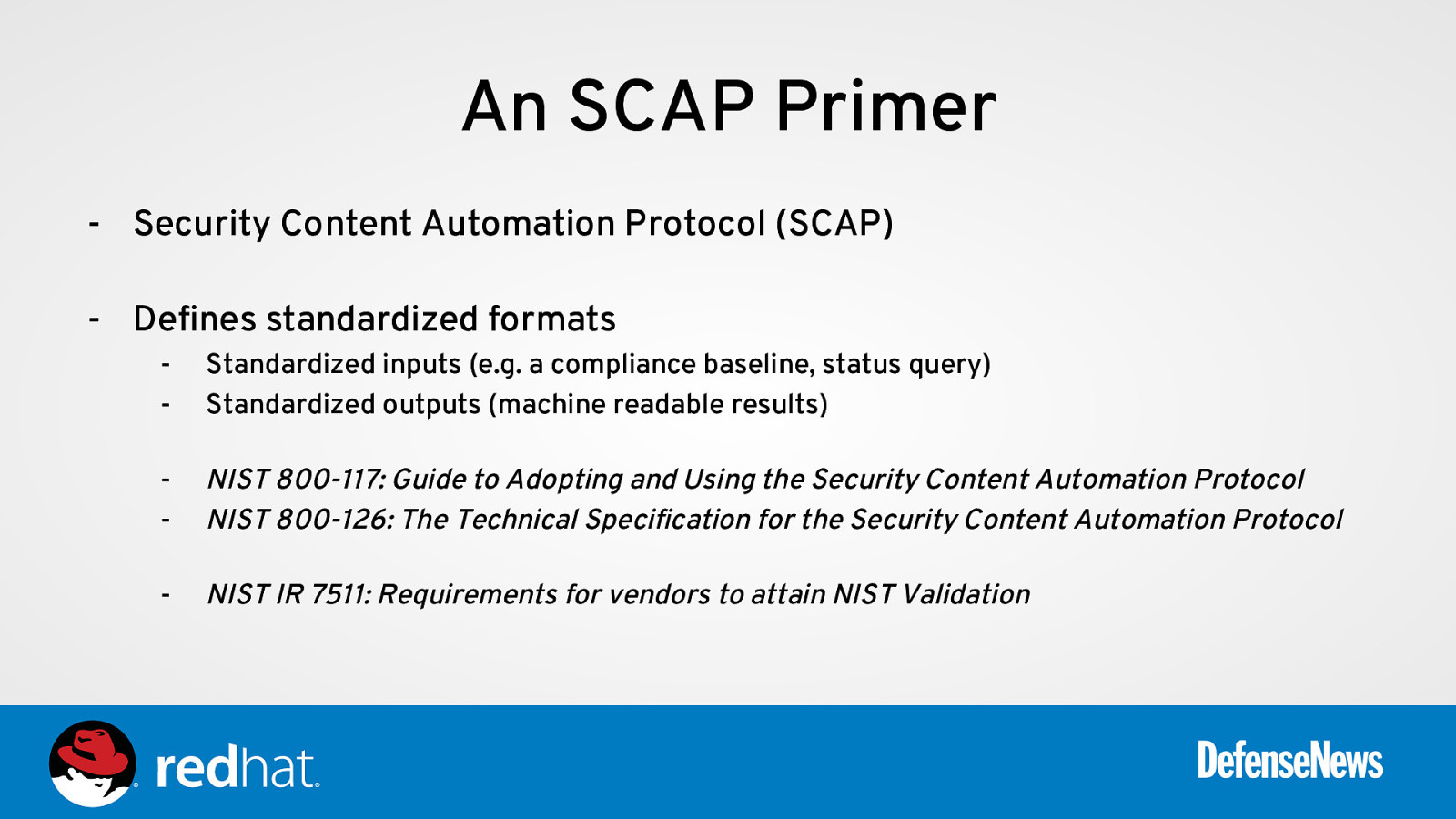
An SCAP Primer - Security Content Automation Protocol (SCAP) - Defines standardized formats - Standardized inputs (e.g. a compliance baseline, status query) Standardized outputs (machine readable results)
NIST 800-117: Guide to Adopting and Using the Security Content Automation Protocol NIST 800-126: The Technical Specification for the Security Content Automation Protocol
NIST IR 7511: Requirements for vendors to attain NIST Validation
Slide 34
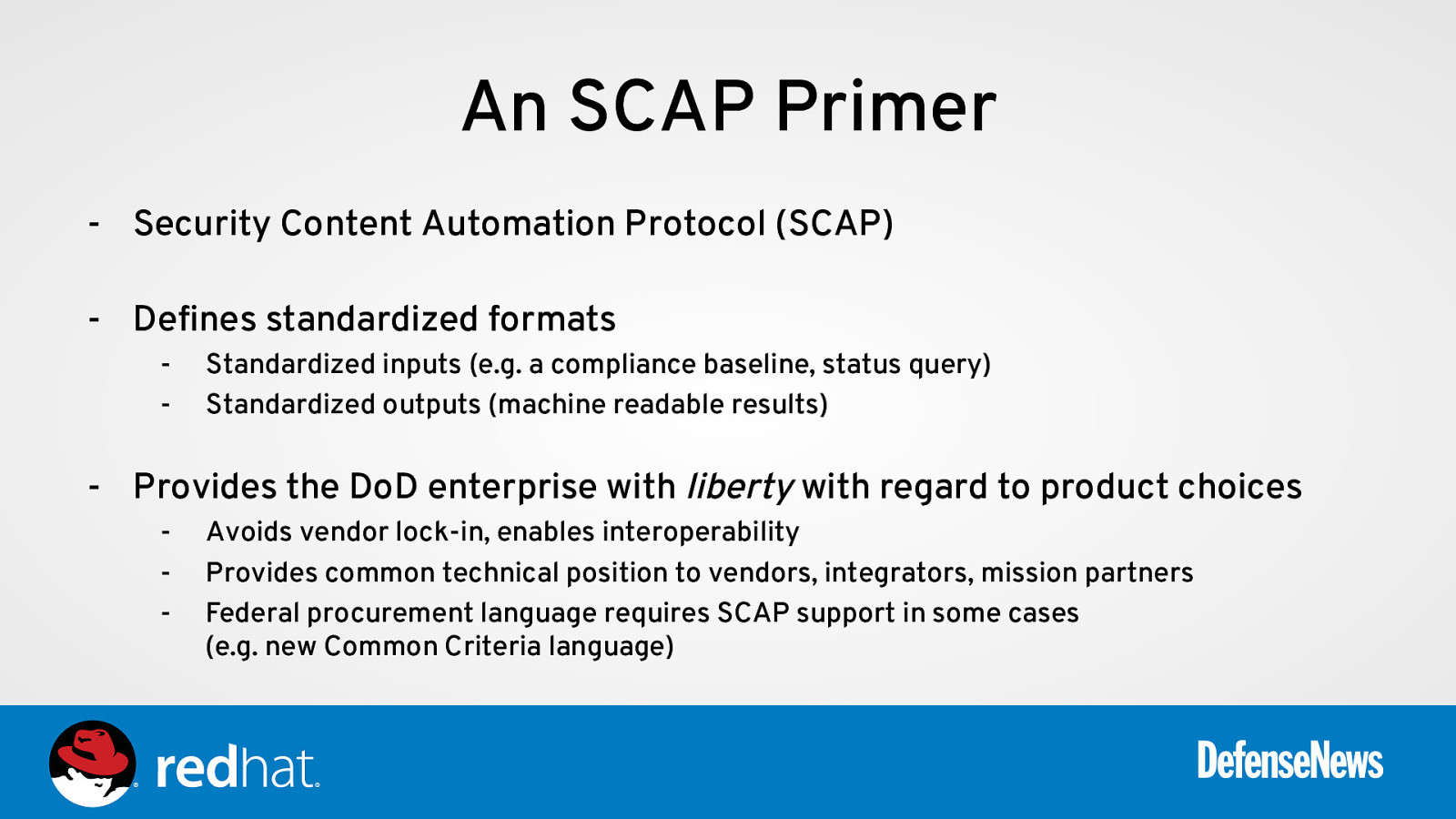
An SCAP Primer - Security Content Automation Protocol (SCAP) - Defines standardized formats - Standardized inputs (e.g. a compliance baseline, status query) Standardized outputs (machine readable results)
- Provides the DoD enterprise with liberty with regard to product choices - Avoids vendor lock-in, enables interoperability Provides common technical position to vendors, integrators, mission partners Federal procurement language requires SCAP support in some cases (e.g. new Common Criteria language)
Slide 35

SCAP Security Guide https://github.com/OpenSCAP/scap-security-guide
Slide 36

Contributors include …
Slide 37
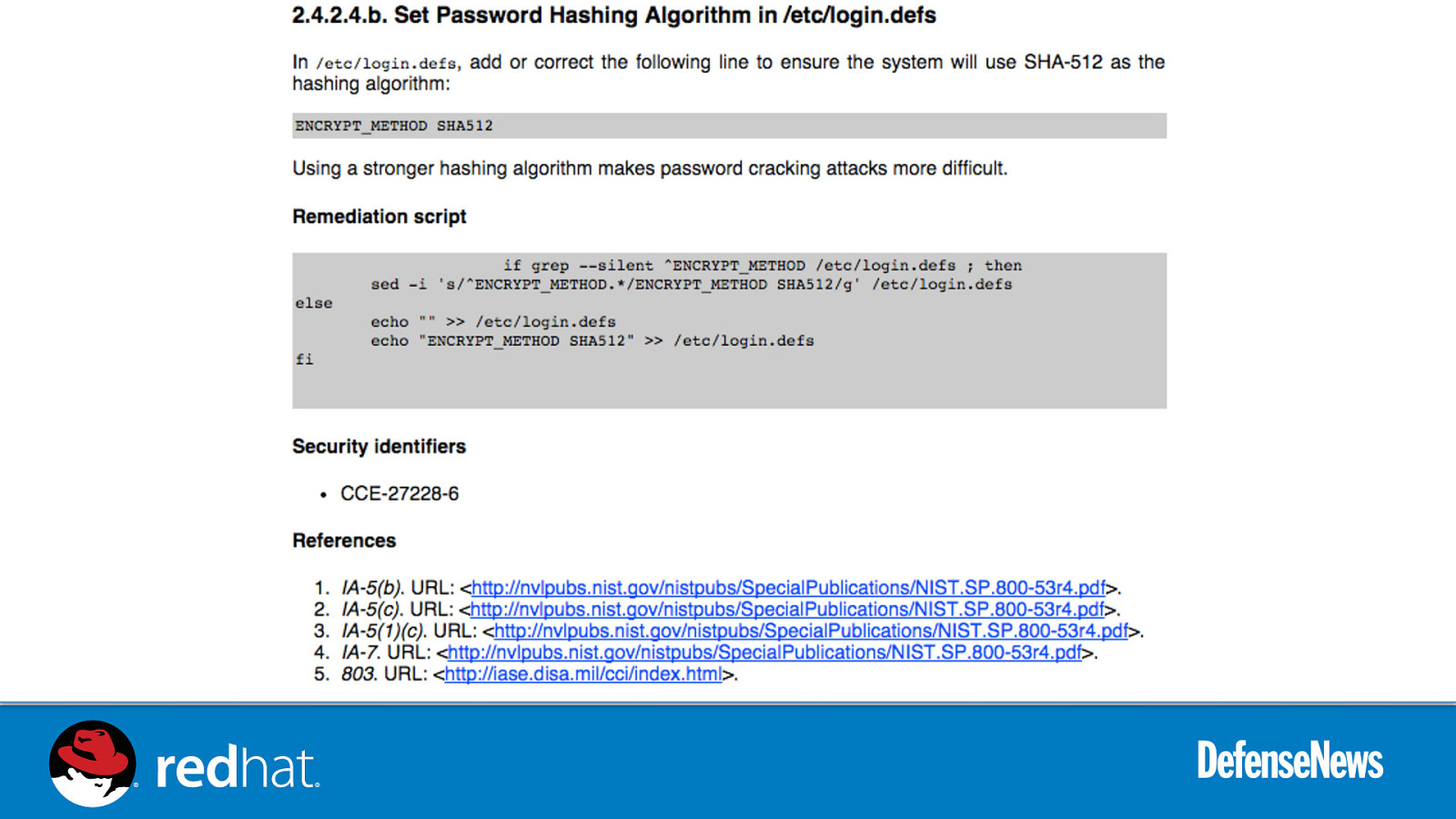
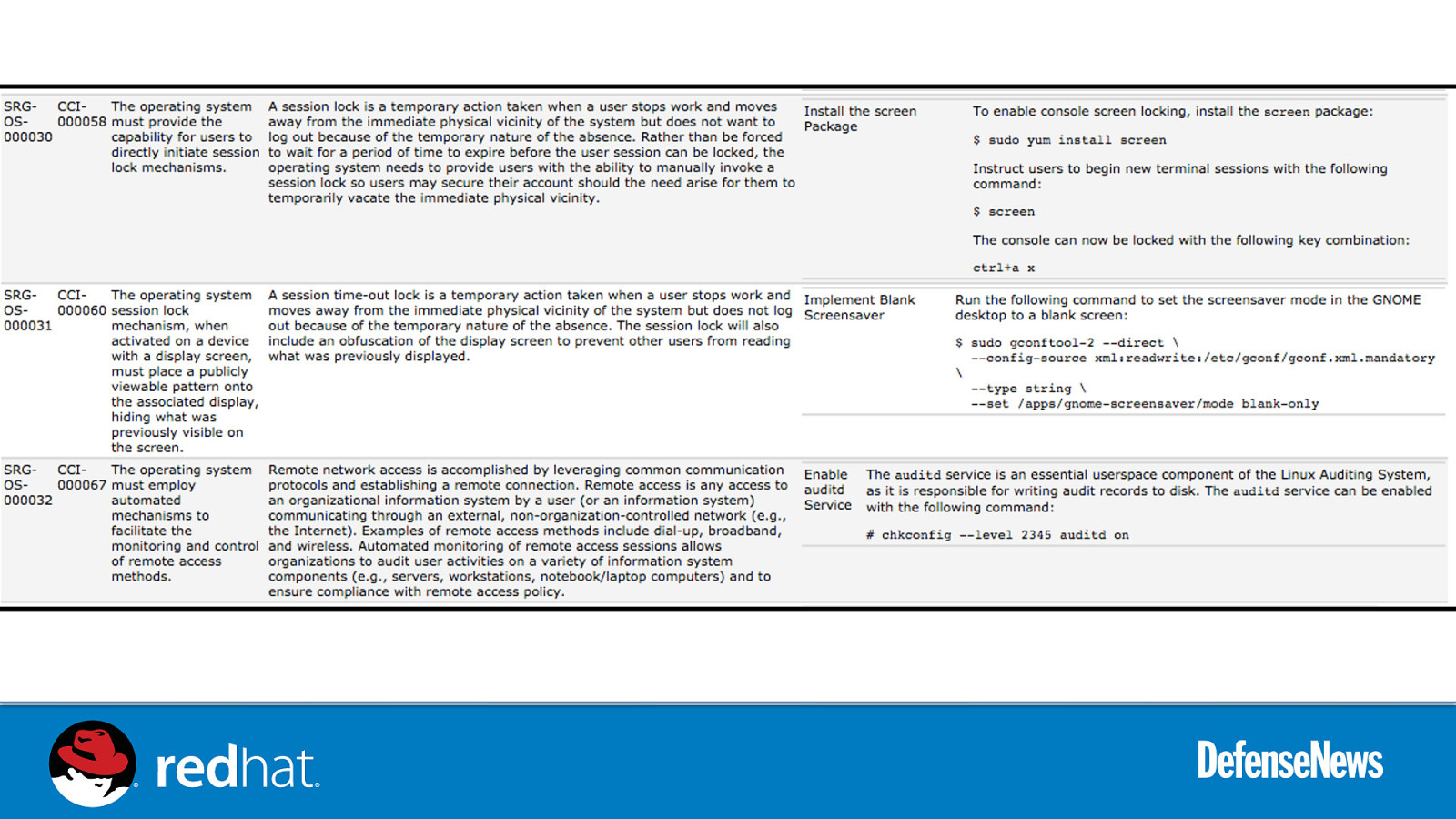
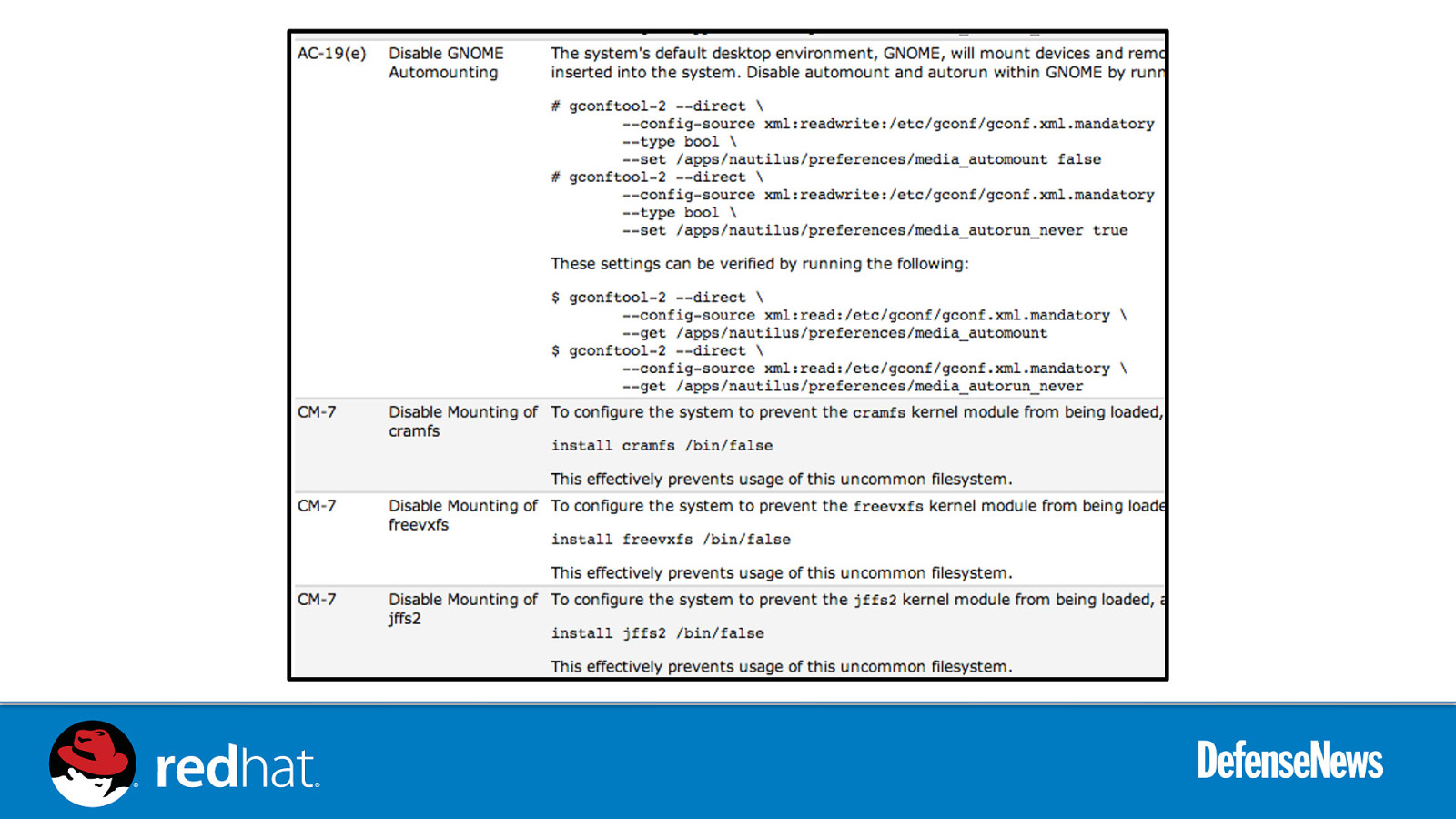
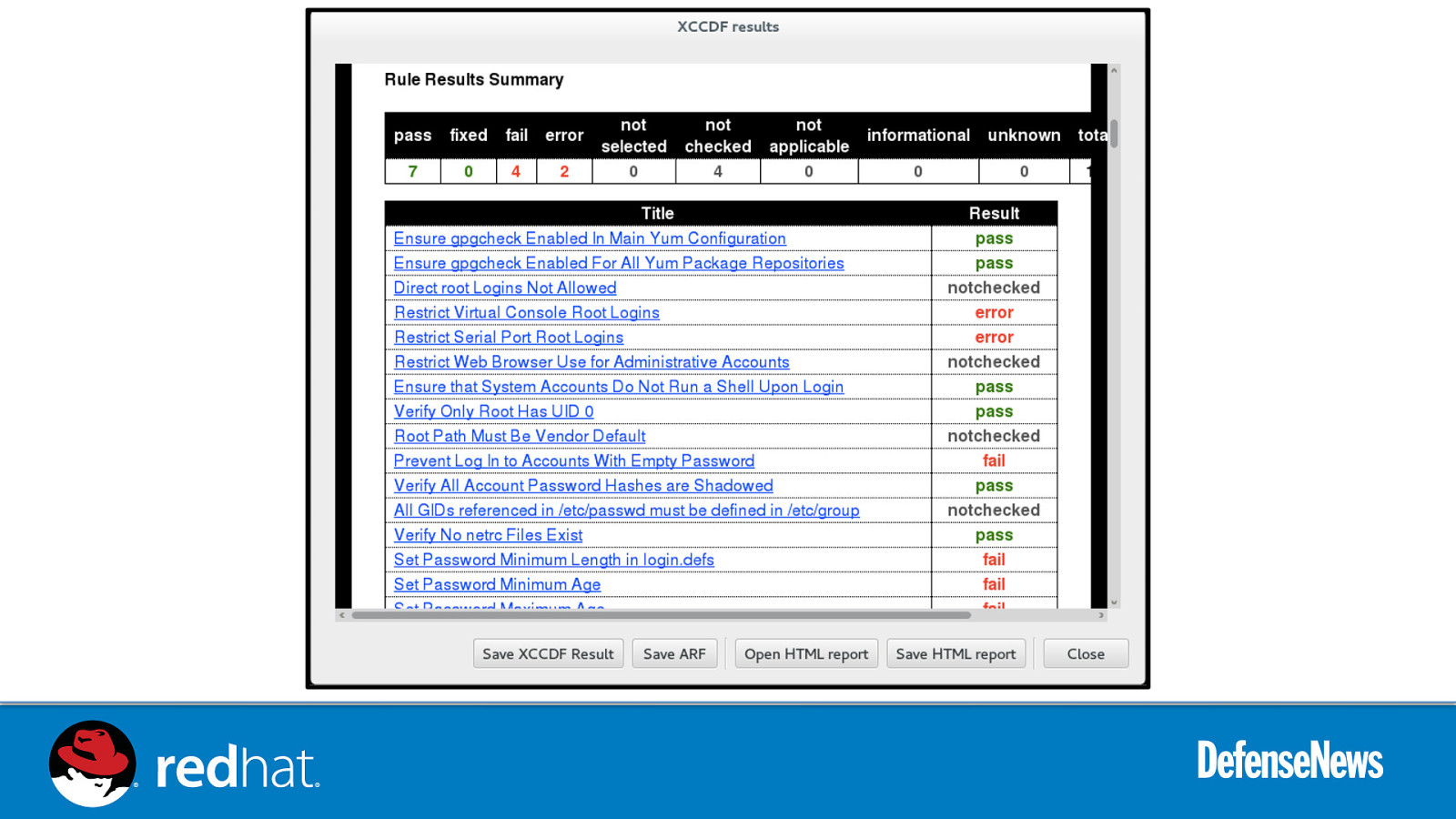
Live Demo
Slide 38

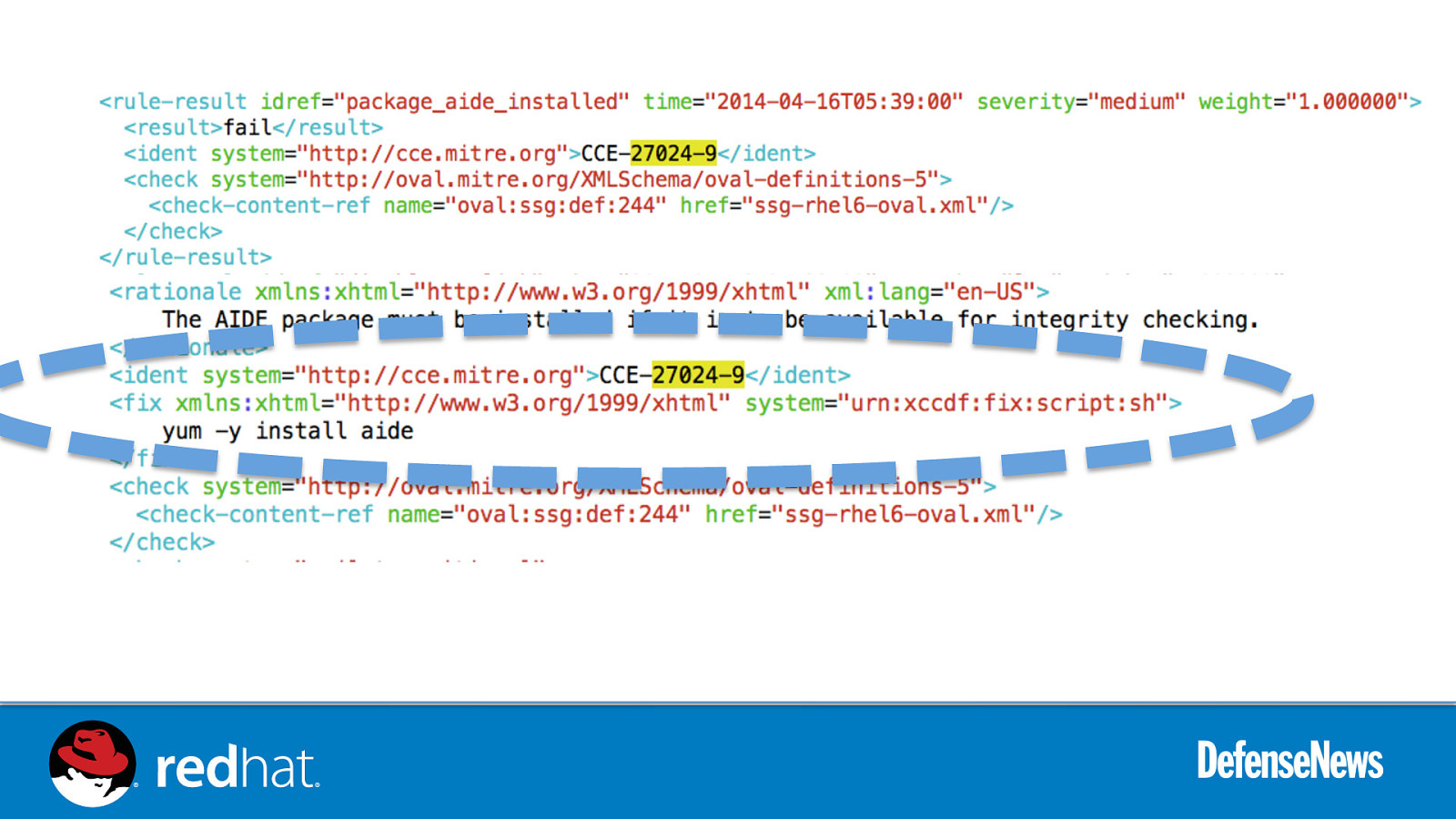
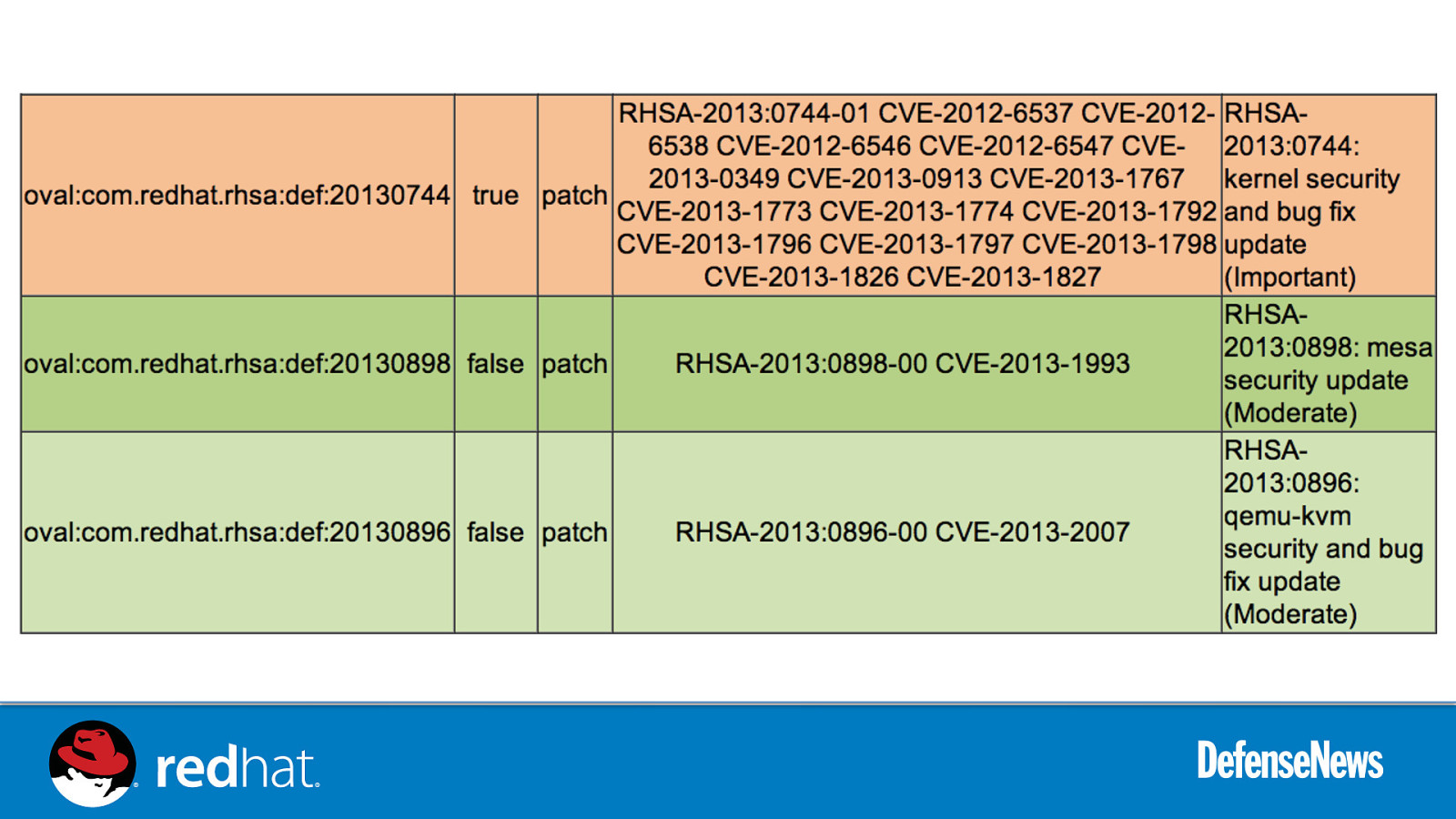
SCAP Security Guide - ~1.66M lines of code from 80 developers across DoD, IC, Civilian, industry, academia - NIST Validated tooling (OpenSCAP) - Upstream for US Gov Enterprise Linux baselines - STIG: DoD RHEL6 baseline, produced by DISA FSO C2S: Intelligence Community “Commercial Cloud” for JWICS CSCF: NRO’s Centralized Super Computing Facility (CNSSI 1253 controls) CS2: NSA RHEL6 baseline US Navy JBoss EAP
- Shipping natively in Enterprise Linux
Slide 39
Slide 40
Slide 41
Slide 42
Slide 43
Slide 44
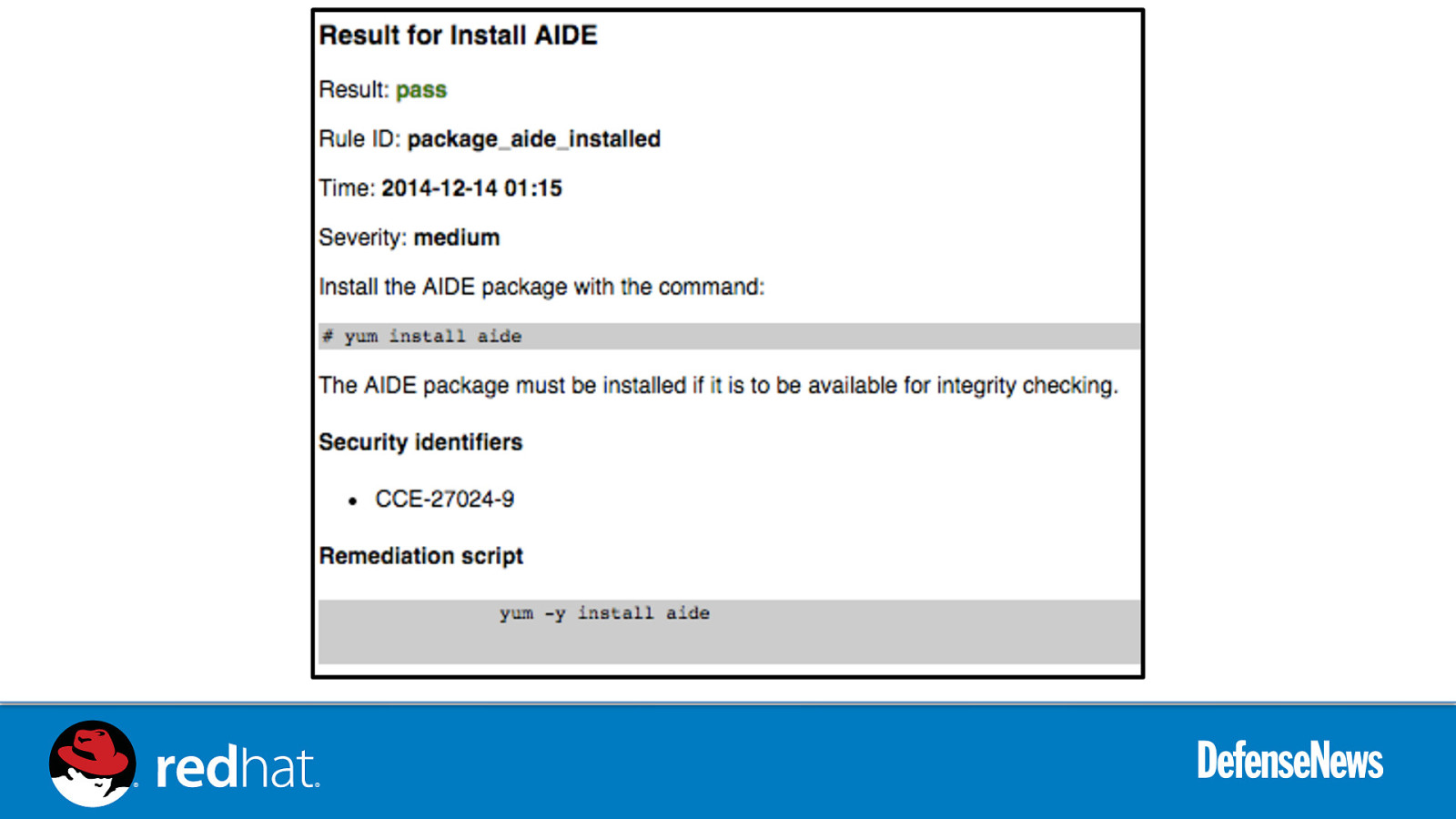
Slide 45
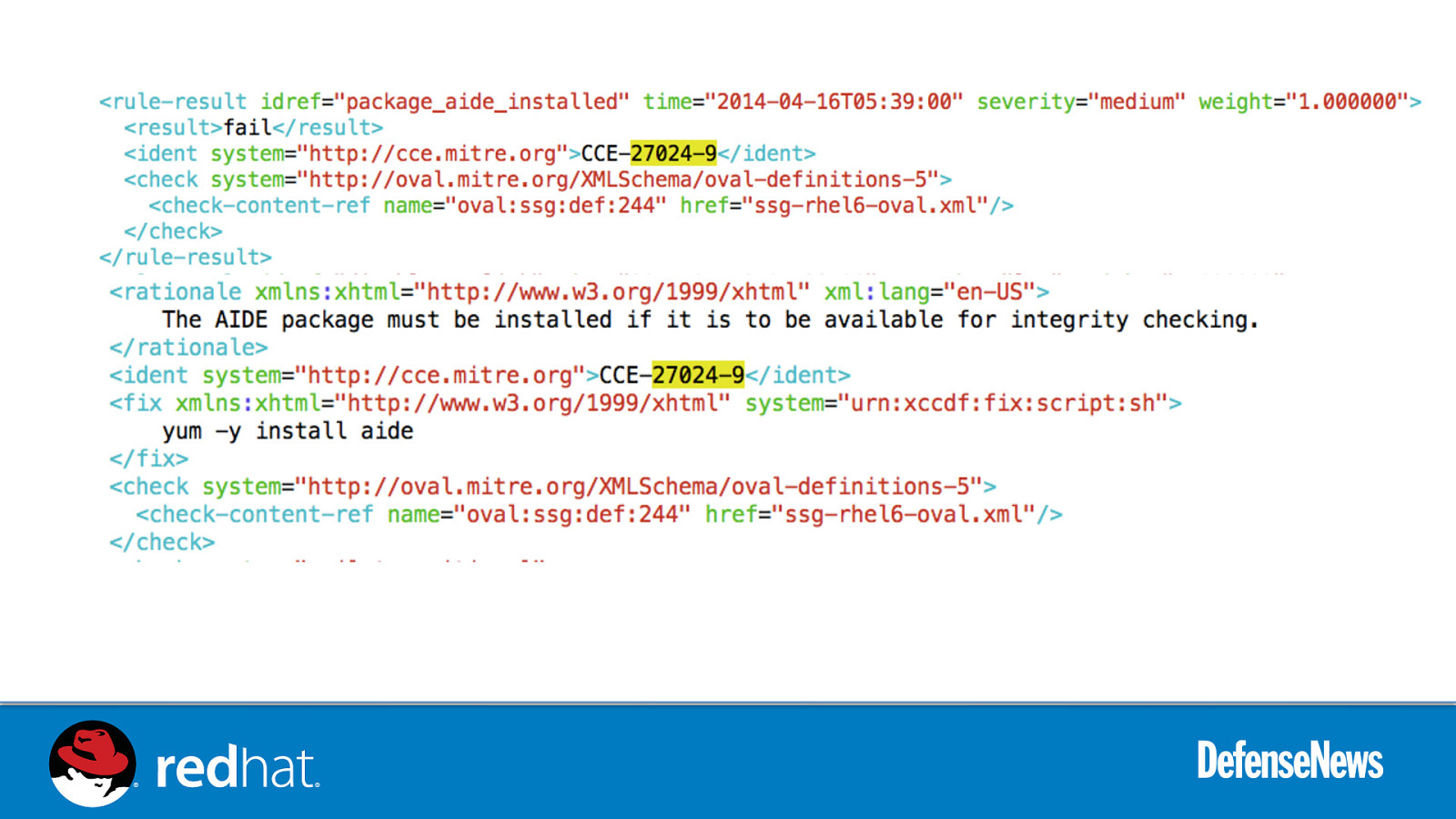
Slide 46
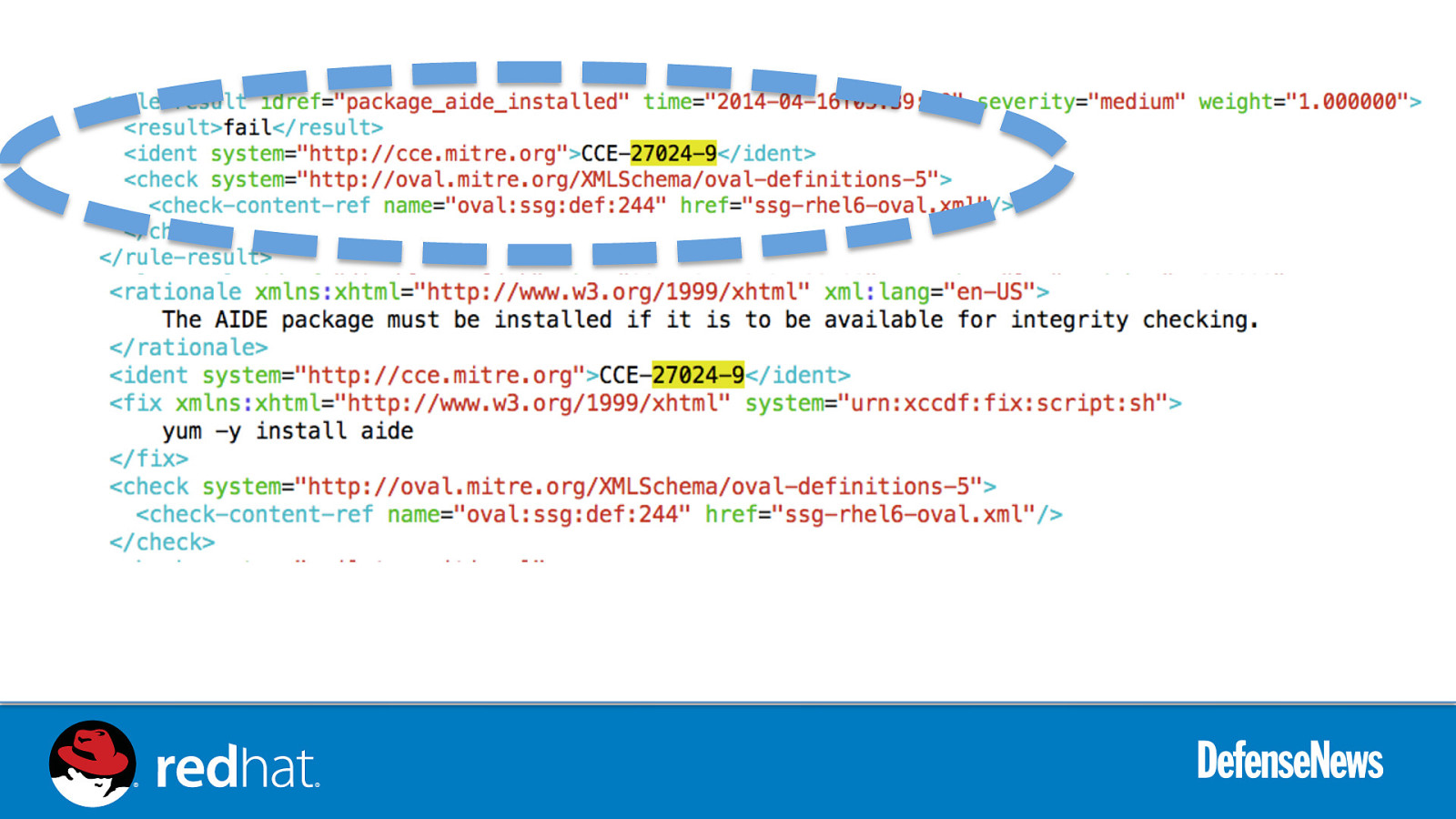
Slide 47
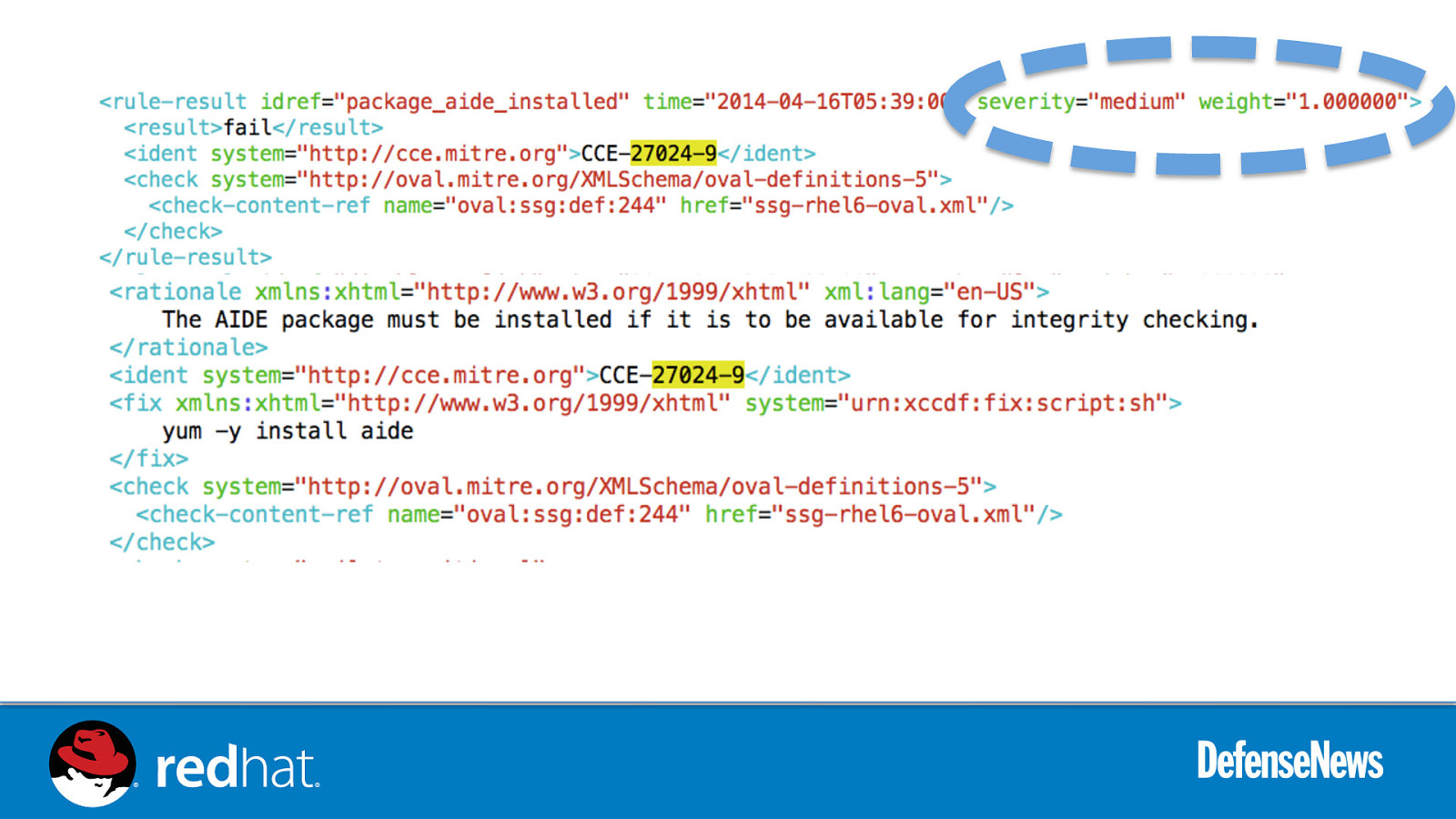
Slide 48
Slide 49
Slide 50
SCAP Deployment: CSCF • Established September 1985 to provide HPC resources for use by the classified NRT and scientific computing communities • DS&T was facilitator with SMUG committee of user groups • WF took over with consolidation of WF to current management • CSCF is currently located in ADF-E • Applications support – code optimization, code parallelization, conversion, algorithm development/modification • O&M support – OS configuration, help desk, backups, disaster recovery, etc
Slide 51
SCAP Deployment: CSCF • CSCF followed the ICD 503 Six steps with standard controls and Cross Domain System (CDS) controls (CDS is approximately equal to MLS) • Controls were straight forward • Testing was very problematic • Testers unfamiliar with Linux, much less MLS. • Test Output Formatting • CSCF moving to SCAP with Red Hat using the xml and html outputs to standardize on with Red Hat support
Slide 52
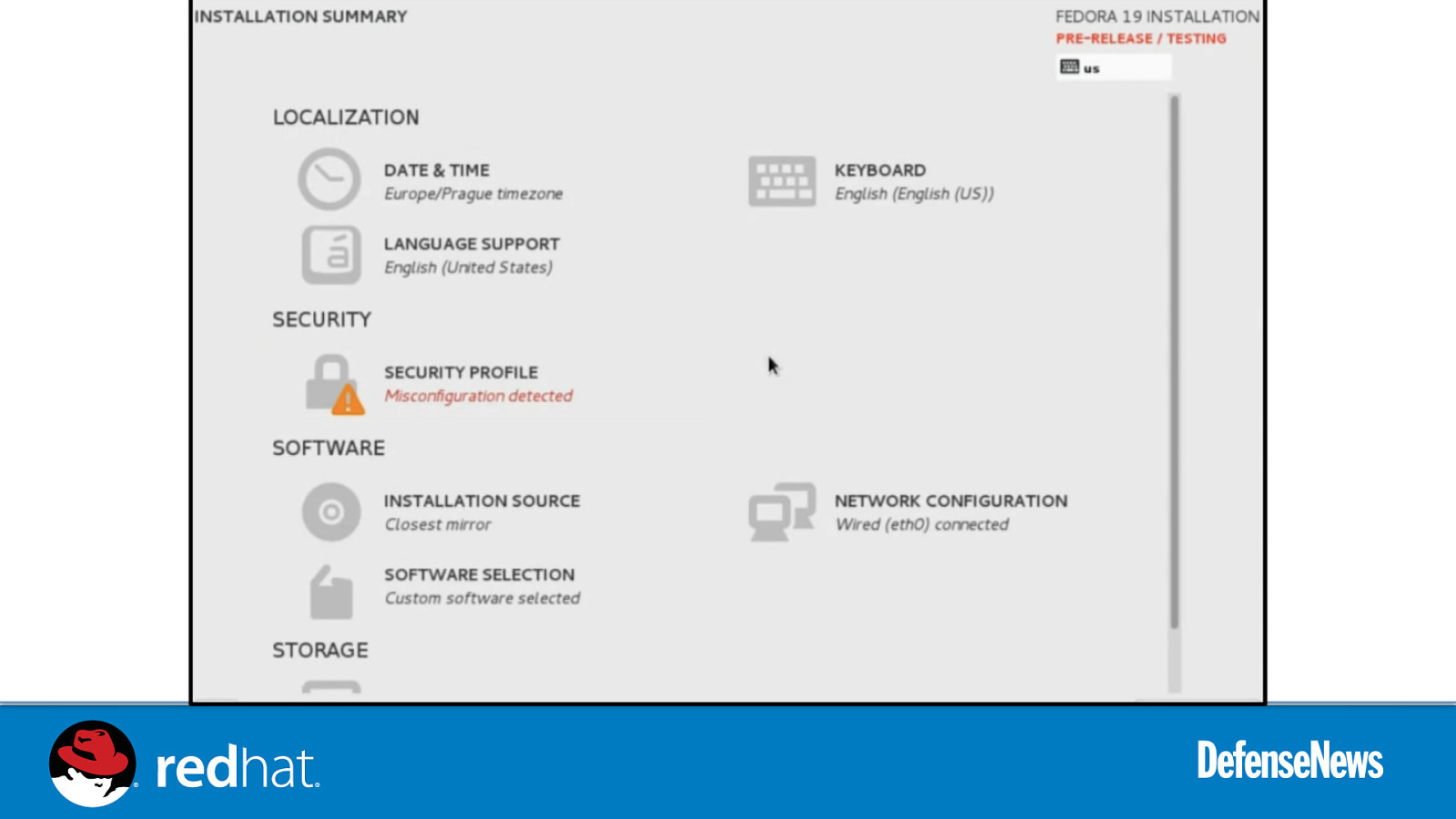
Slide 53
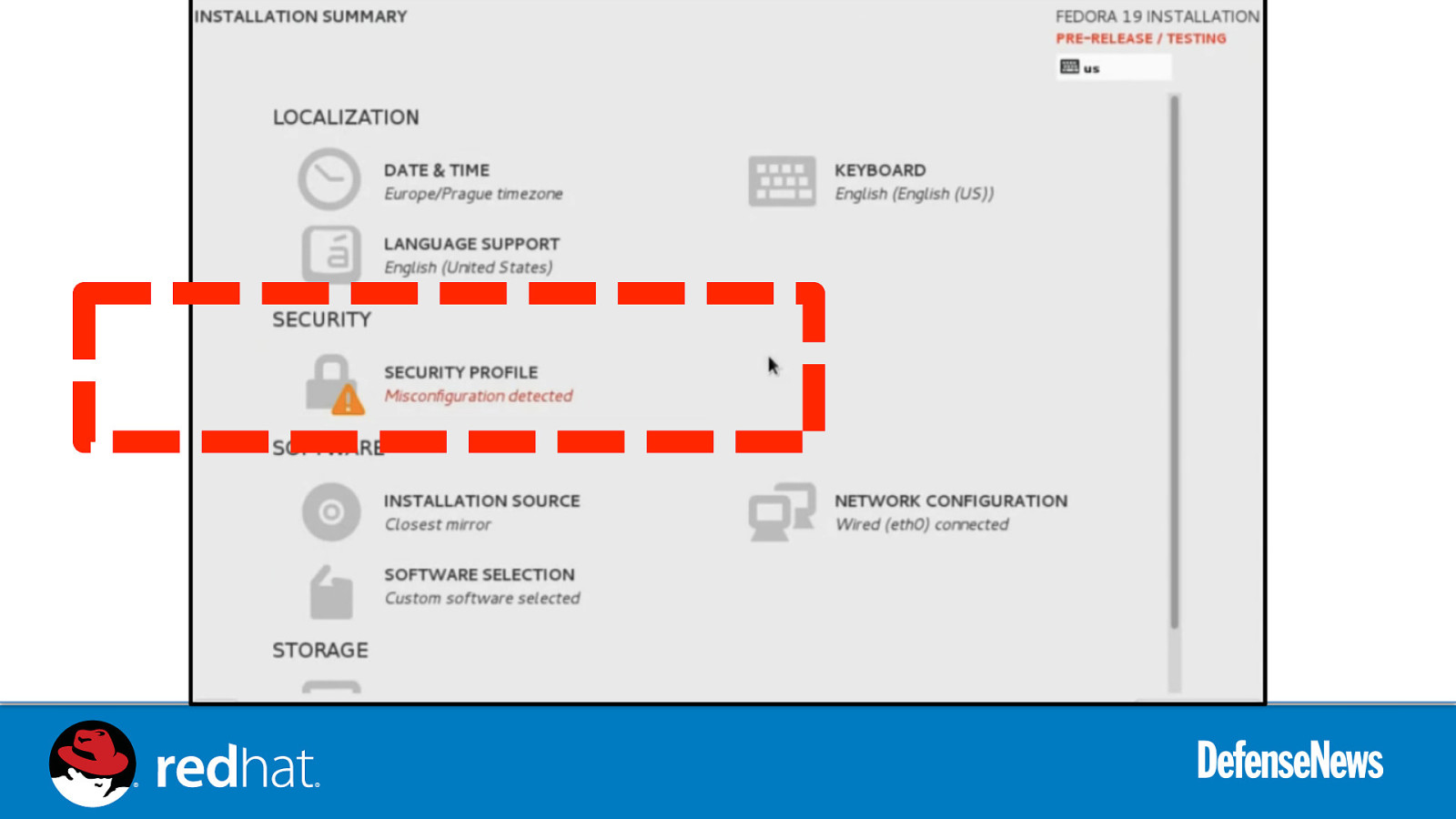
Slide 54
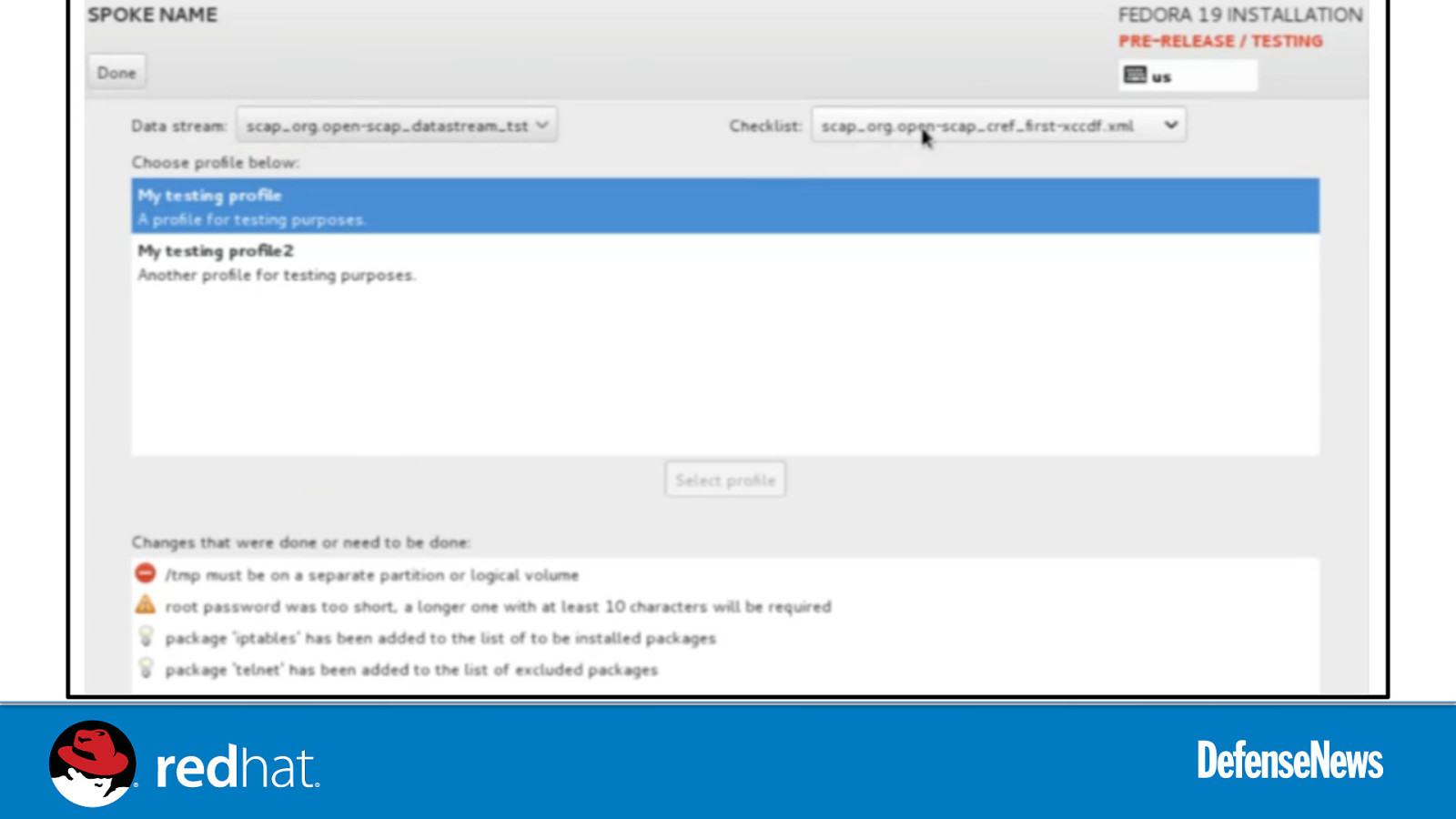
Slide 55
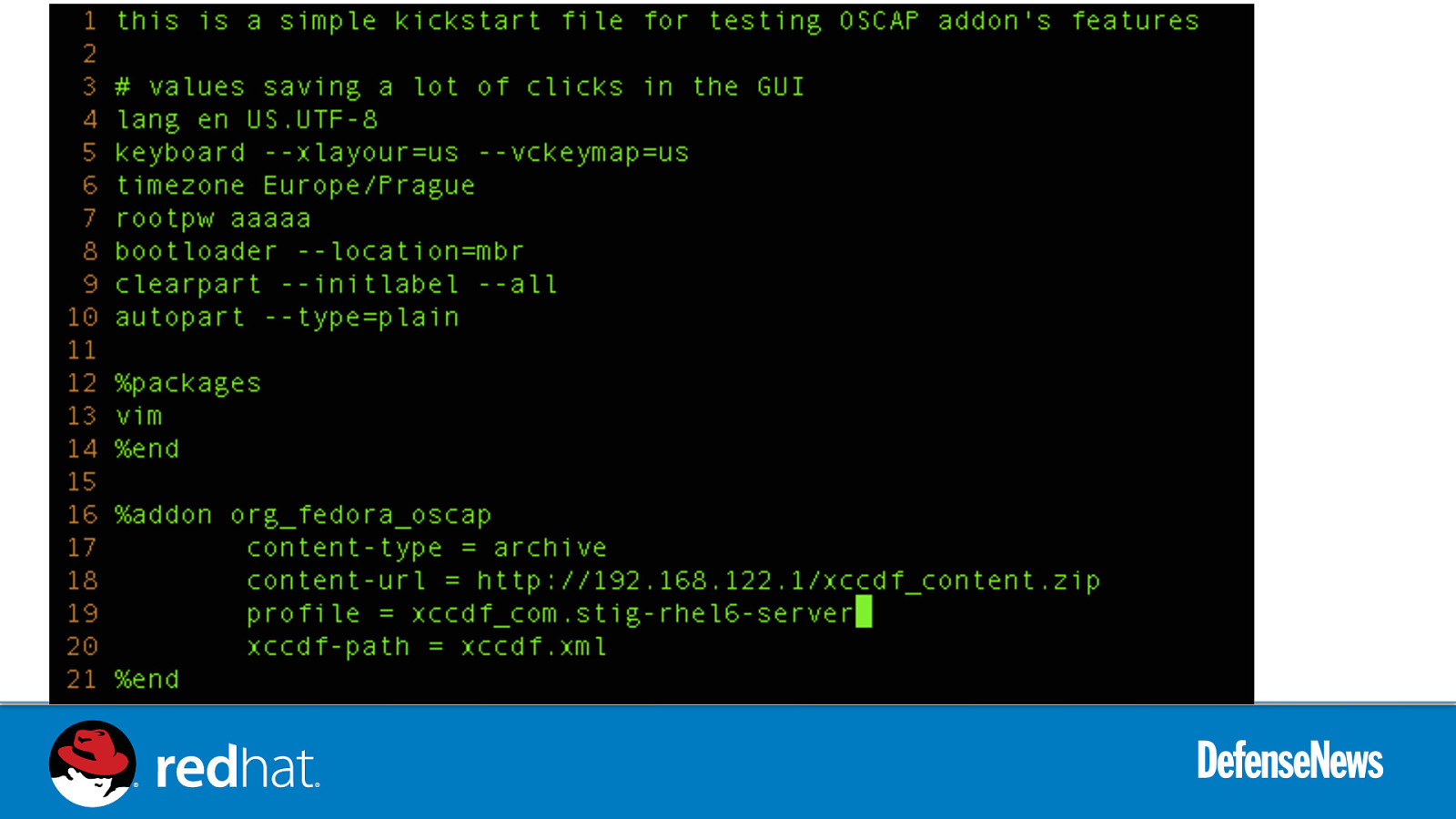
Slide 56
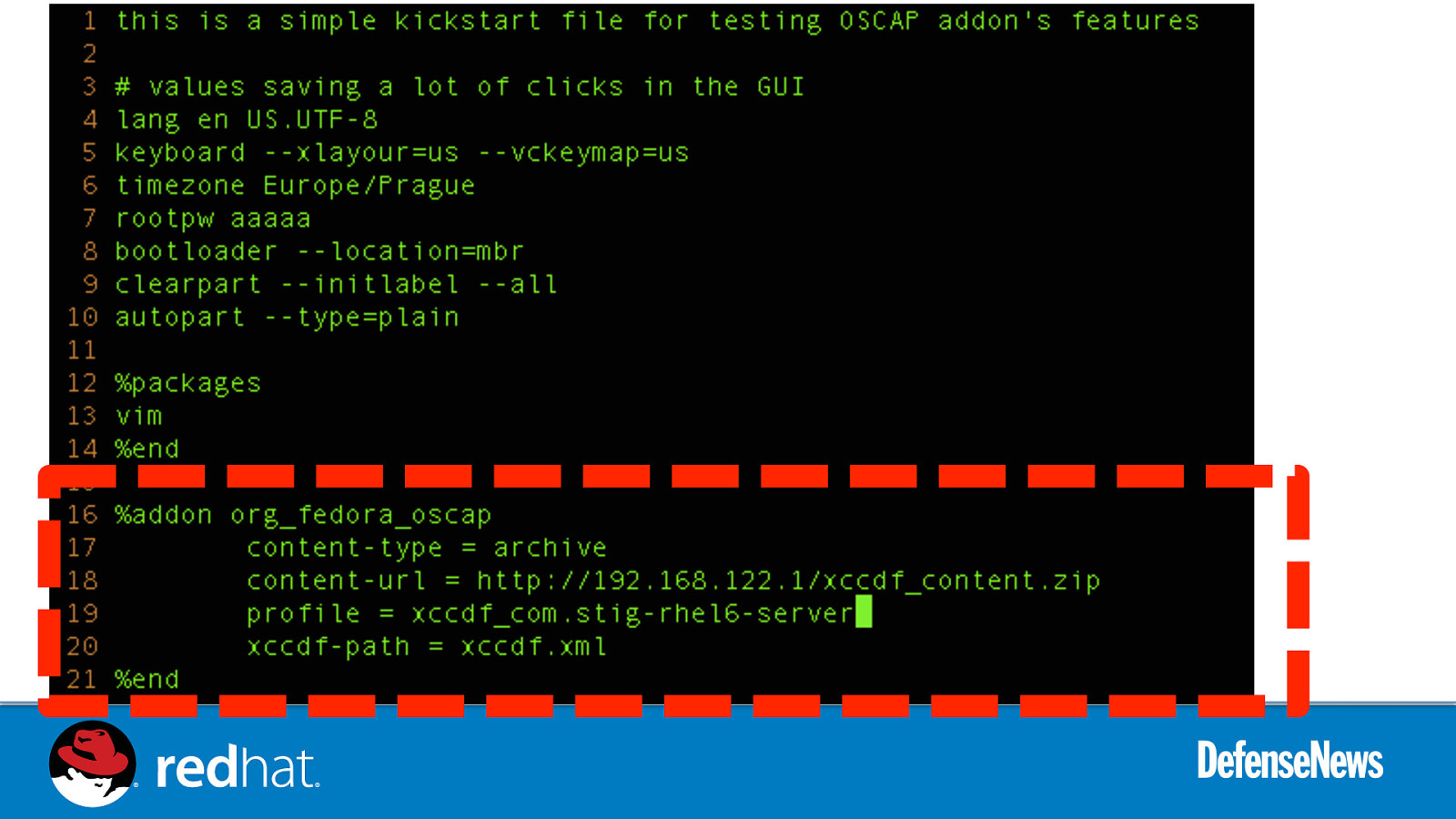
Slide 57

PORTABLE WORKLOADS
Slide 58
Data Sources
Slide 59
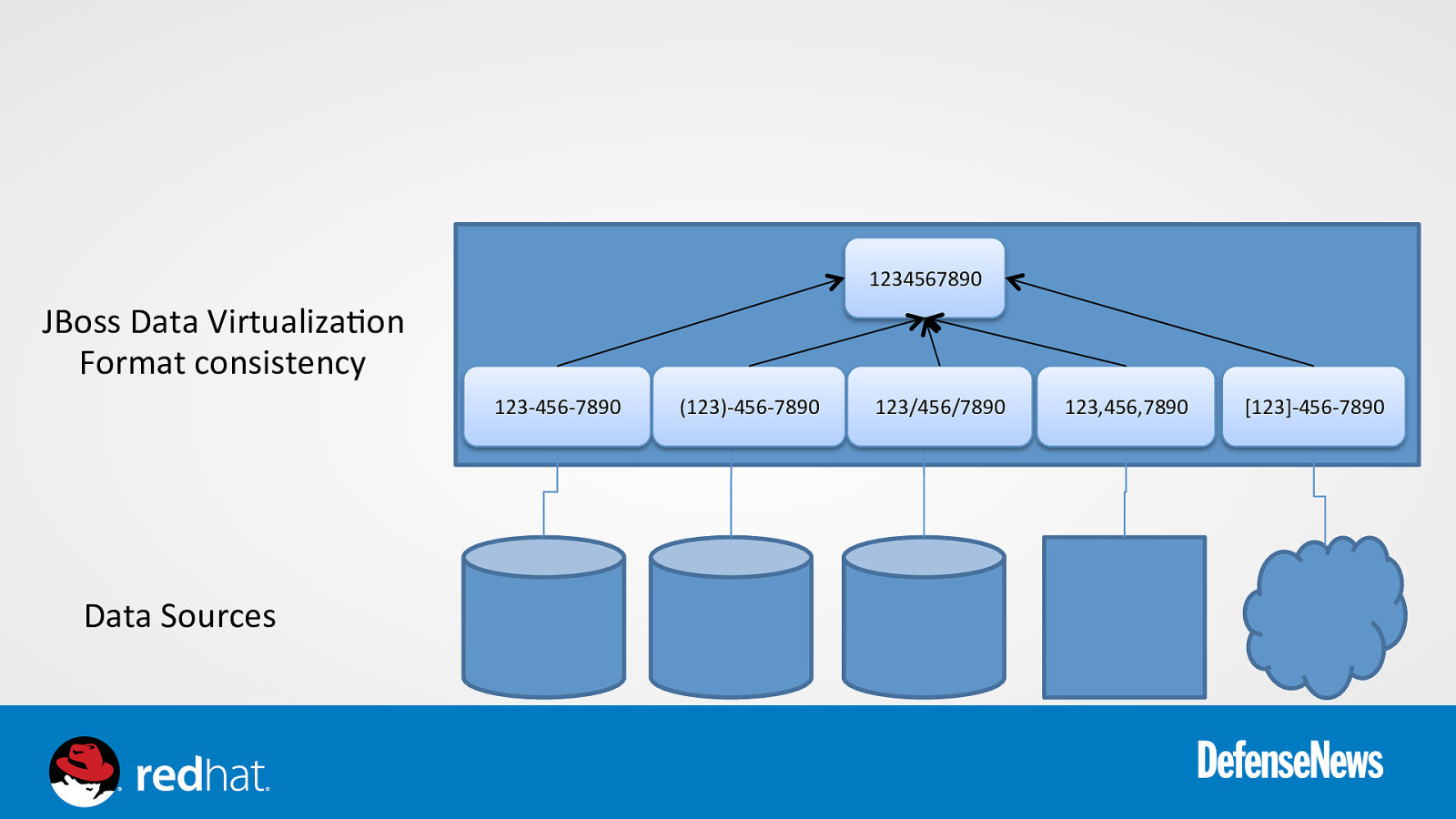
1234567890 JBoss Data Virtualiza0on Format consistency 123-‐456-‐7890 Data Sources (123)-‐456-‐7890 123/456/7890 123,456,7890 [123]-‐456-‐7890
Slide 60
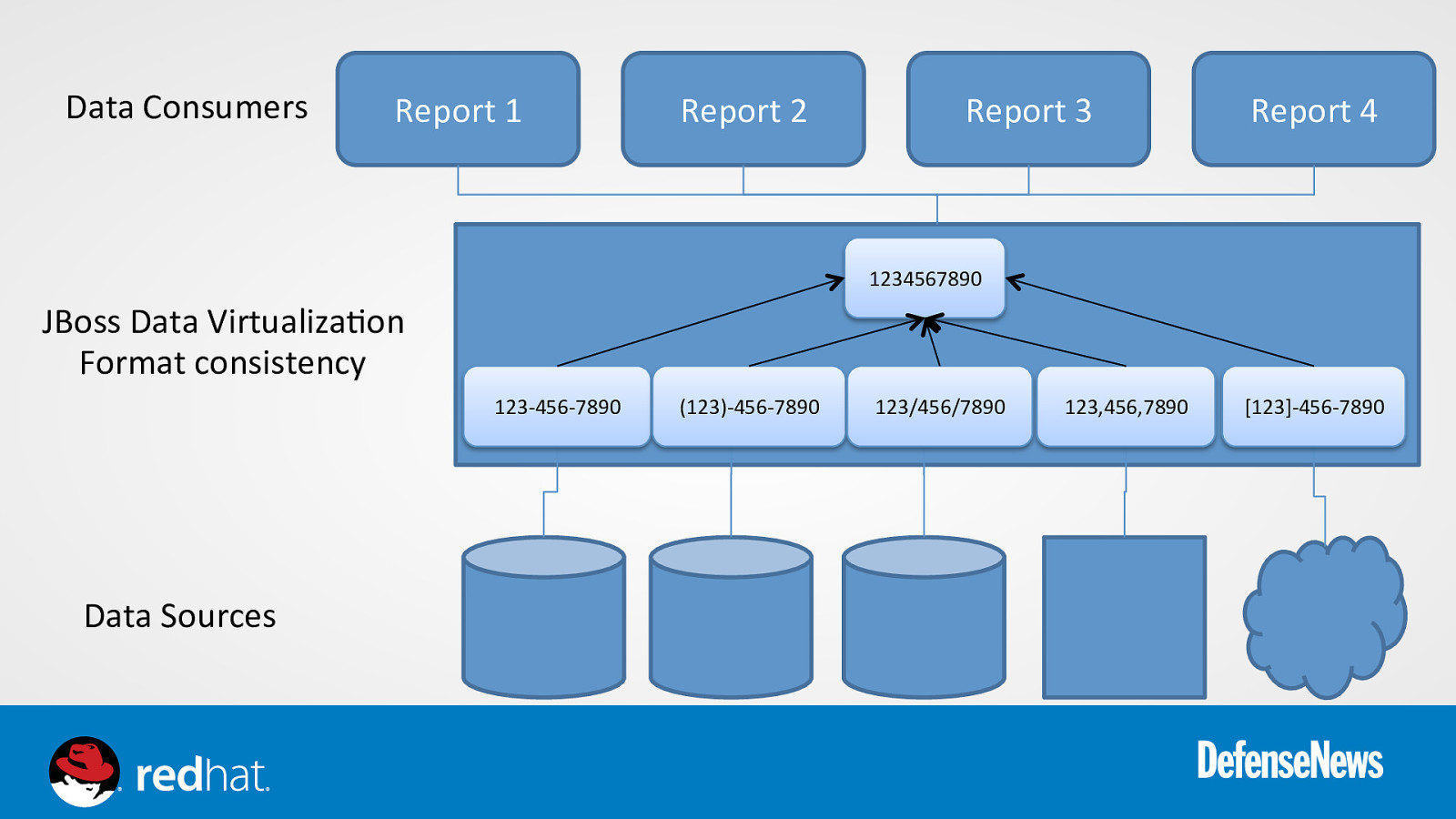
Data Consumers Report 1 Report 2 Report 3 Report 4 1234567890 JBoss Data Virtualiza0on Format consistency 123-‐456-‐7890 Data Sources (123)-‐456-‐7890 123/456/7890 123,456,7890 [123]-‐456-‐7890
Slide 61
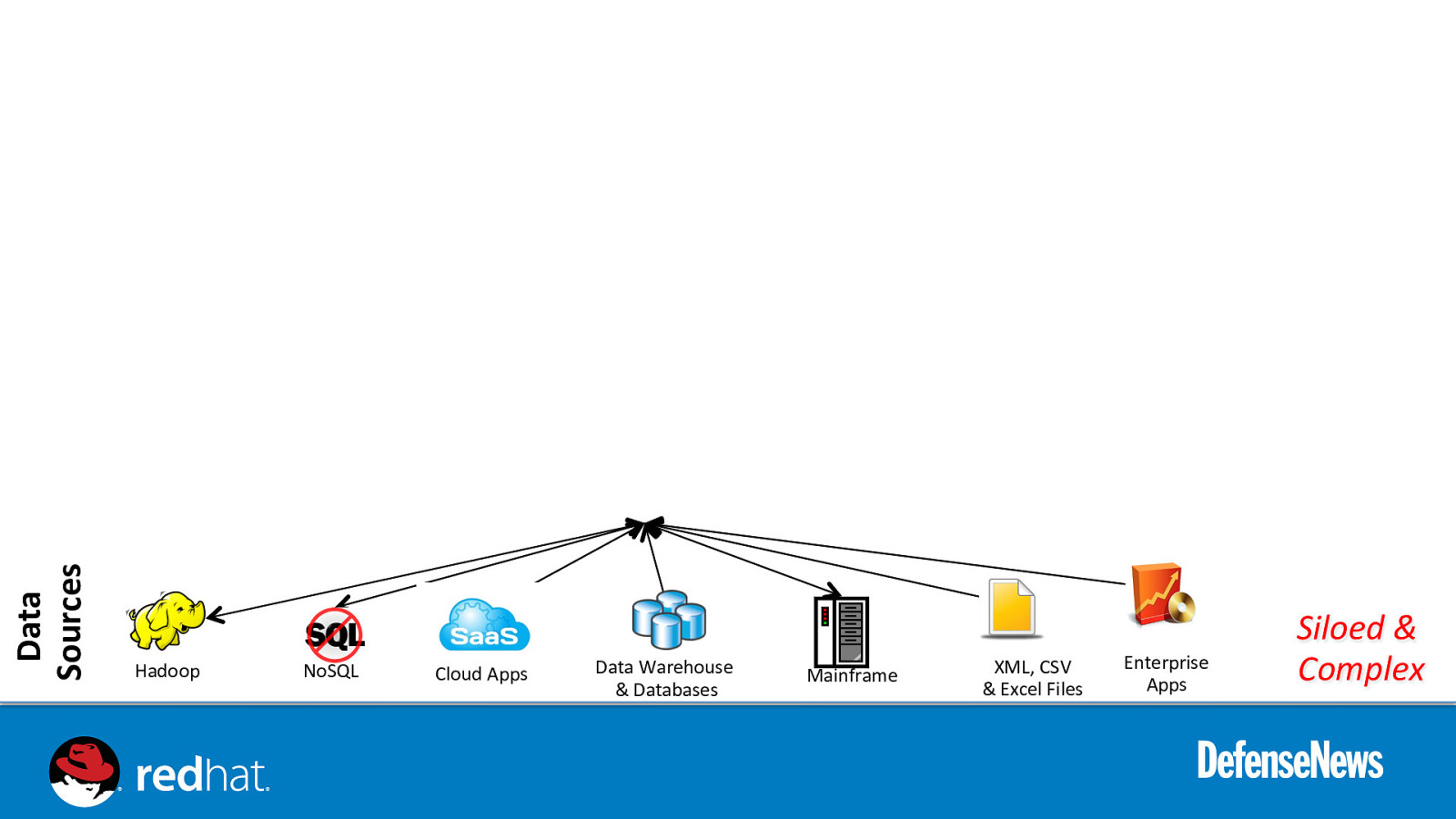
Data Sources Hadoop NoSQL Cloud Apps Data Warehouse & Databases Mainframe XML, CSV & Excel Files Enterprise Apps Siloed & Complex
Slide 62
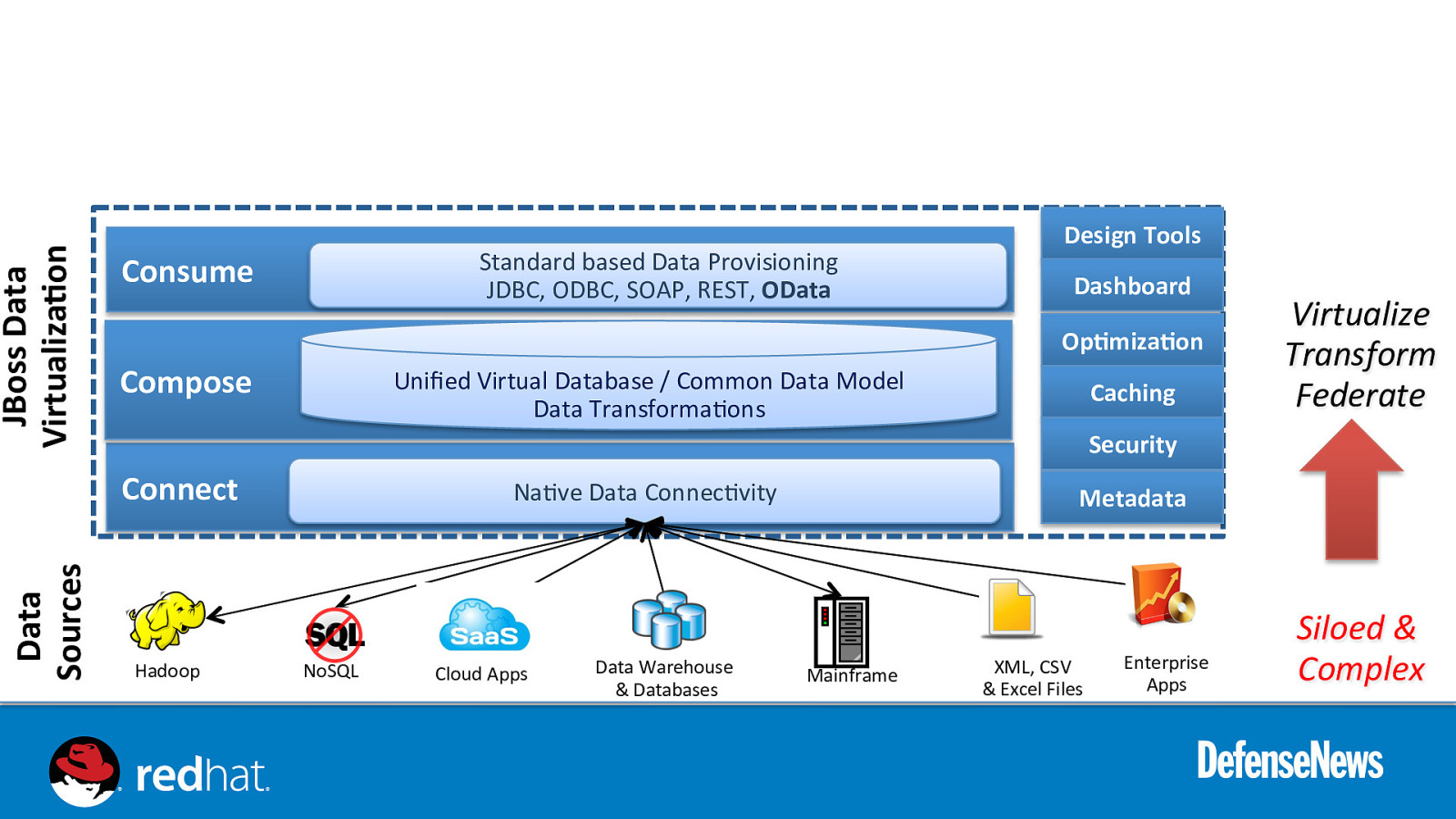
JBoss Data VirtualizaNon Standard based Data Provisioning JDBC, ODBC, SOAP, REST, OData Consume Dashboard OpNmizaNon Compose Unified Virtual Database / Common Data Model Data Transforma0ons Caching Virtualize Transform Federate Security Connect Data Sources Design Tools Hadoop Na0ve Data Connec0vity NoSQL Cloud Apps Data Warehouse & Databases Metadata Mainframe XML, CSV & Excel Files Enterprise Apps Siloed & Complex
Slide 63

Data Consumers JBoss Data VirtualizaNon BI Reports & Analy0cs Mobile Applica0ons Standard based Data Provisioning JDBC, ODBC, SOAP, REST, OData Consume SOA Applica0ons & Portals Compose Easy, Real-‐Cme InformaCon Design Tools Dashboard OpNmizaNon Unified Virtual Database / Common Data Model Data Transforma0ons Caching Virtualize Transform Federate Security Connect Data Sources ESB, ETL Hadoop Na0ve Data Connec0vity NoSQL Cloud Apps Data Warehouse & Databases Metadata Mainframe XML, CSV & Excel Files Enterprise Apps Siloed & Complex
Slide 64
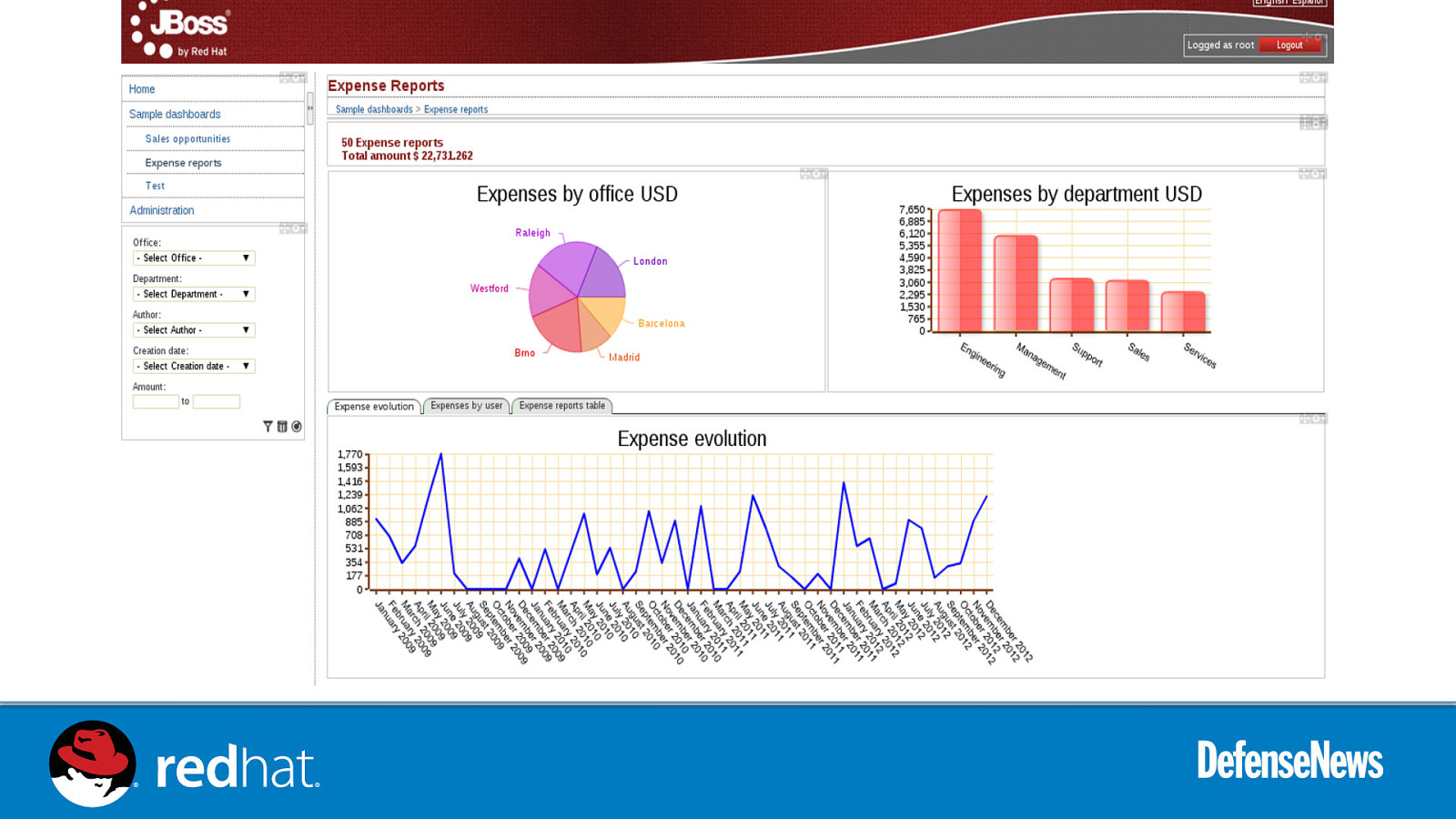
Slide 65
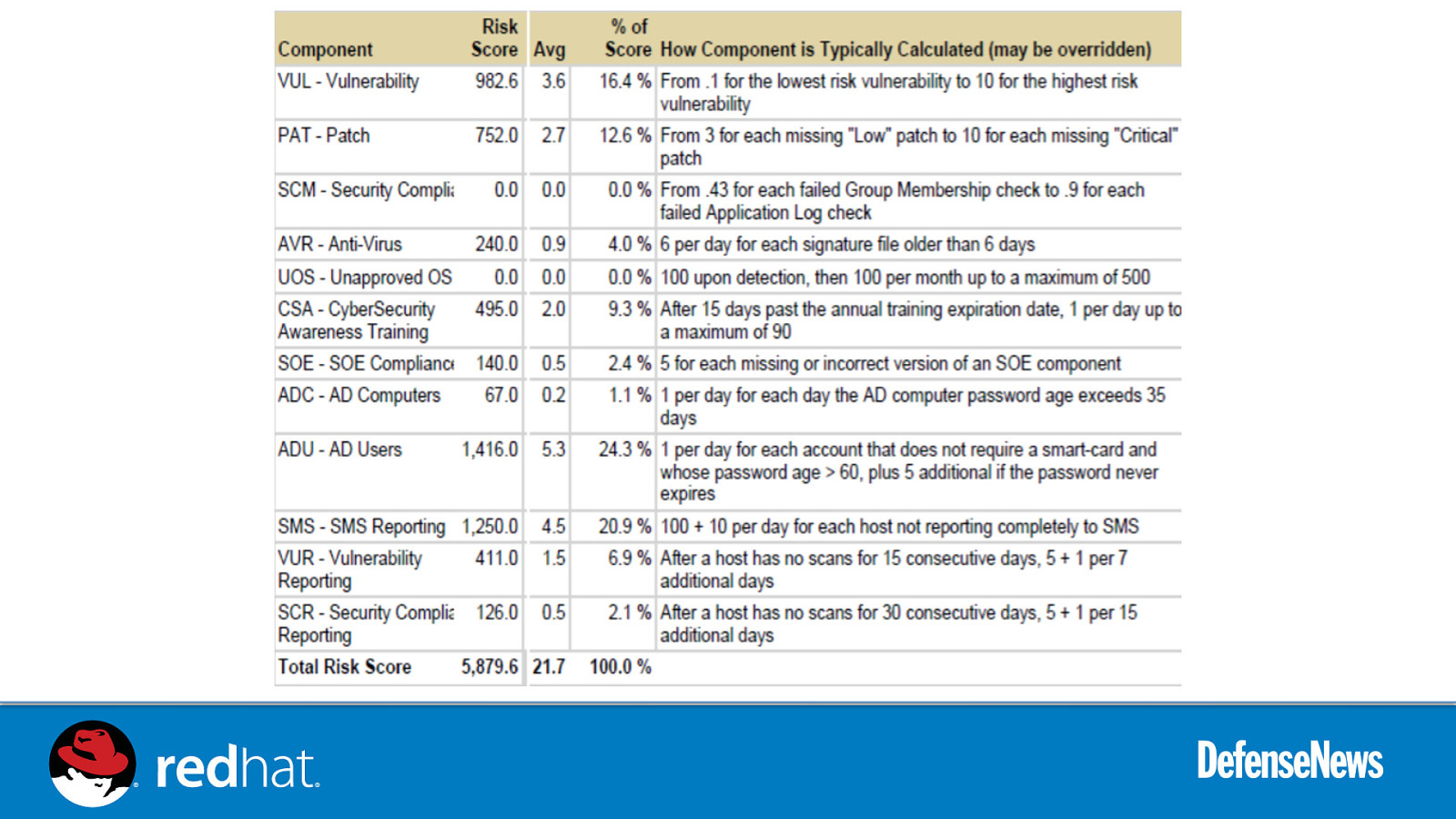
Slide 66

Shawn Wells Director, Innova0on Programs Red Hat Public Sector shawn@redhat.com || 443-‐534-‐0130