Aligning & Sharing Cybersecurity Practices Between Federal and State Shawn Wells Chief Security Strategist U.S. Public Sector shawn@redhat.com || 443-534-0130
Slide 1

Slide 2
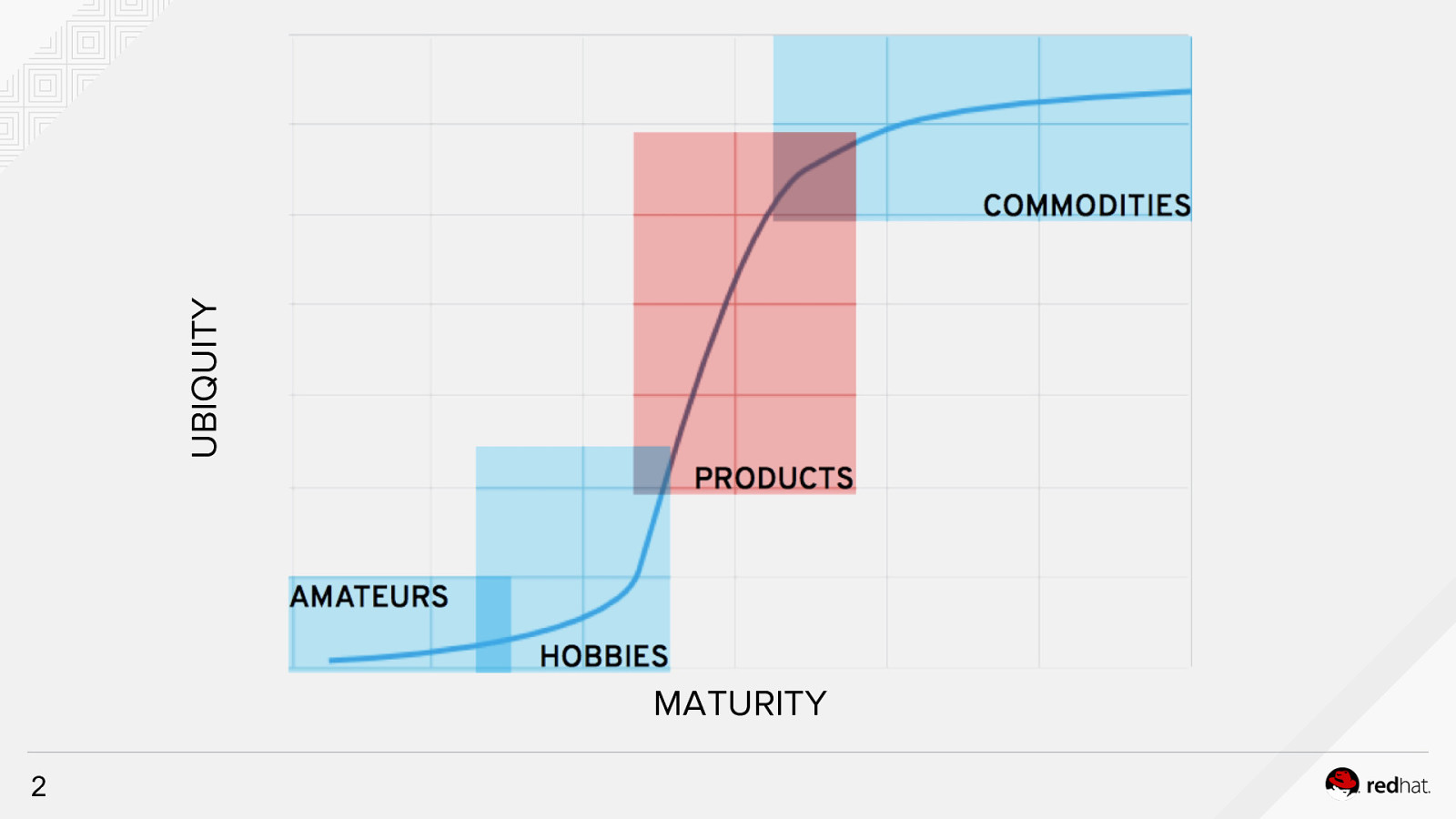
UBIQUITY MATURITY 2
Slide 3
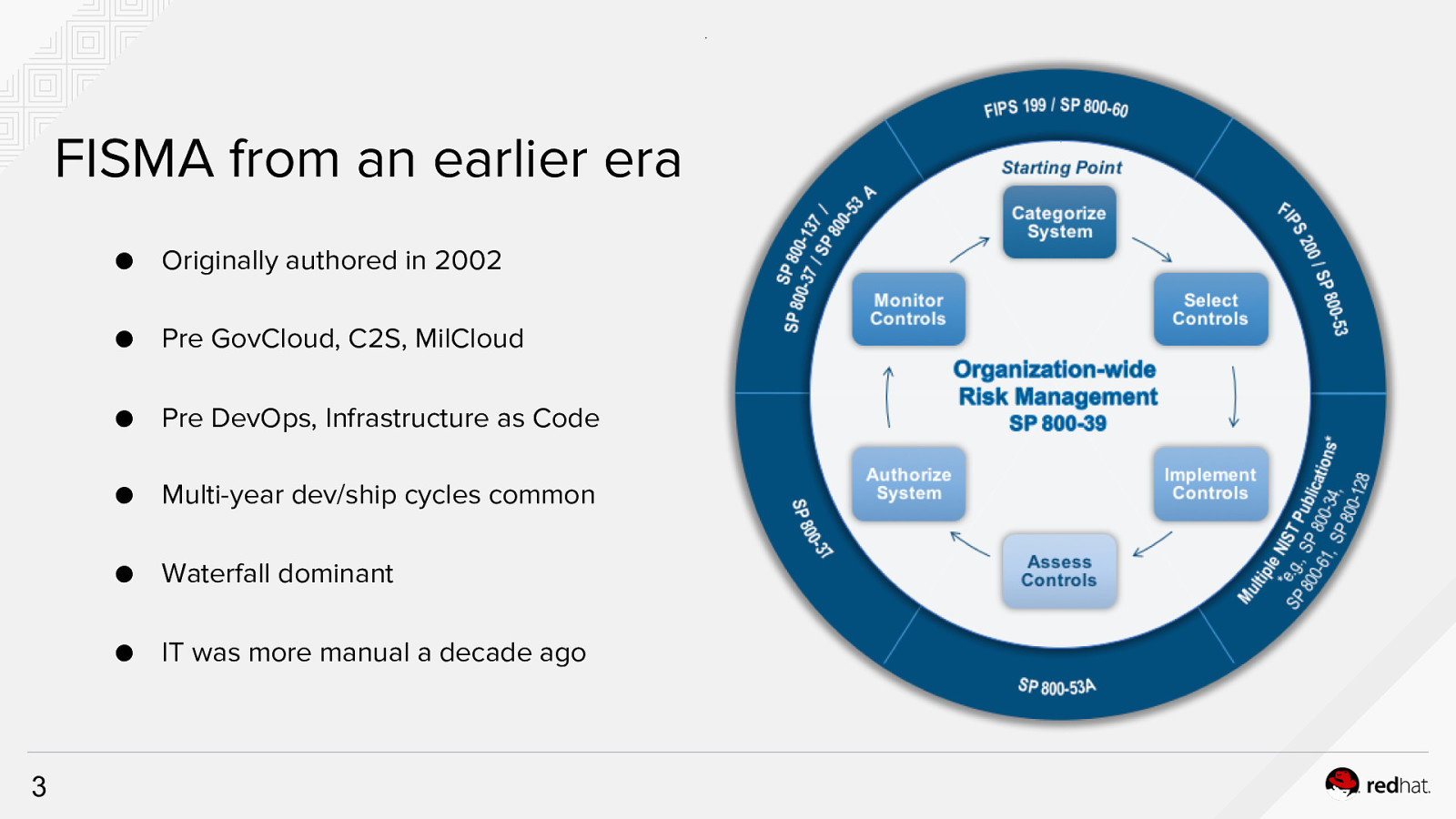
FISMA from an earlier era ● Originally authored in 2002 ● Pre GovCloud, C2S, MilCloud ● Pre DevOps, Infrastructure as Code ● Multi-year dev/ship cycles common ● Waterfall dominant ● IT was more manual a decade ago 3
Slide 4
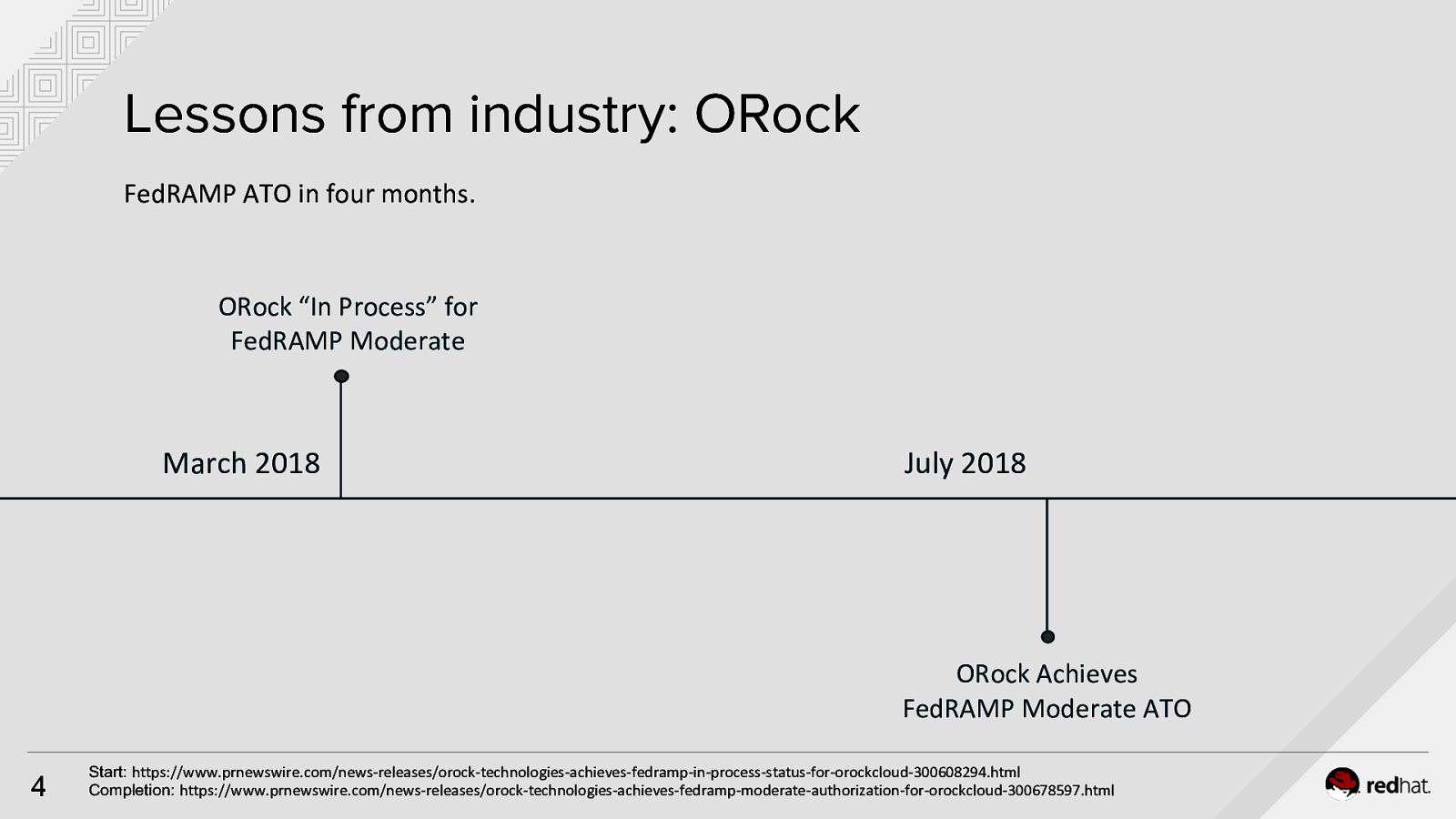
Lessons from industry: ORock FedRAMP ATO in four months. ORock “In Process” for FedRAMP Moderate March 2018 July 2018 ORock Achieves FedRAMP Moderate ATO 4 Start: https://www.prnewswire.com/news-releases/orock-technologies-achieves-fedramp-in-process-status-for-orockcloud-300608294.html Completion: https://www.prnewswire.com/news-releases/orock-technologies-achieves-fedramp-moderate-authorization-for-orockcloud-300678597.html
Slide 5
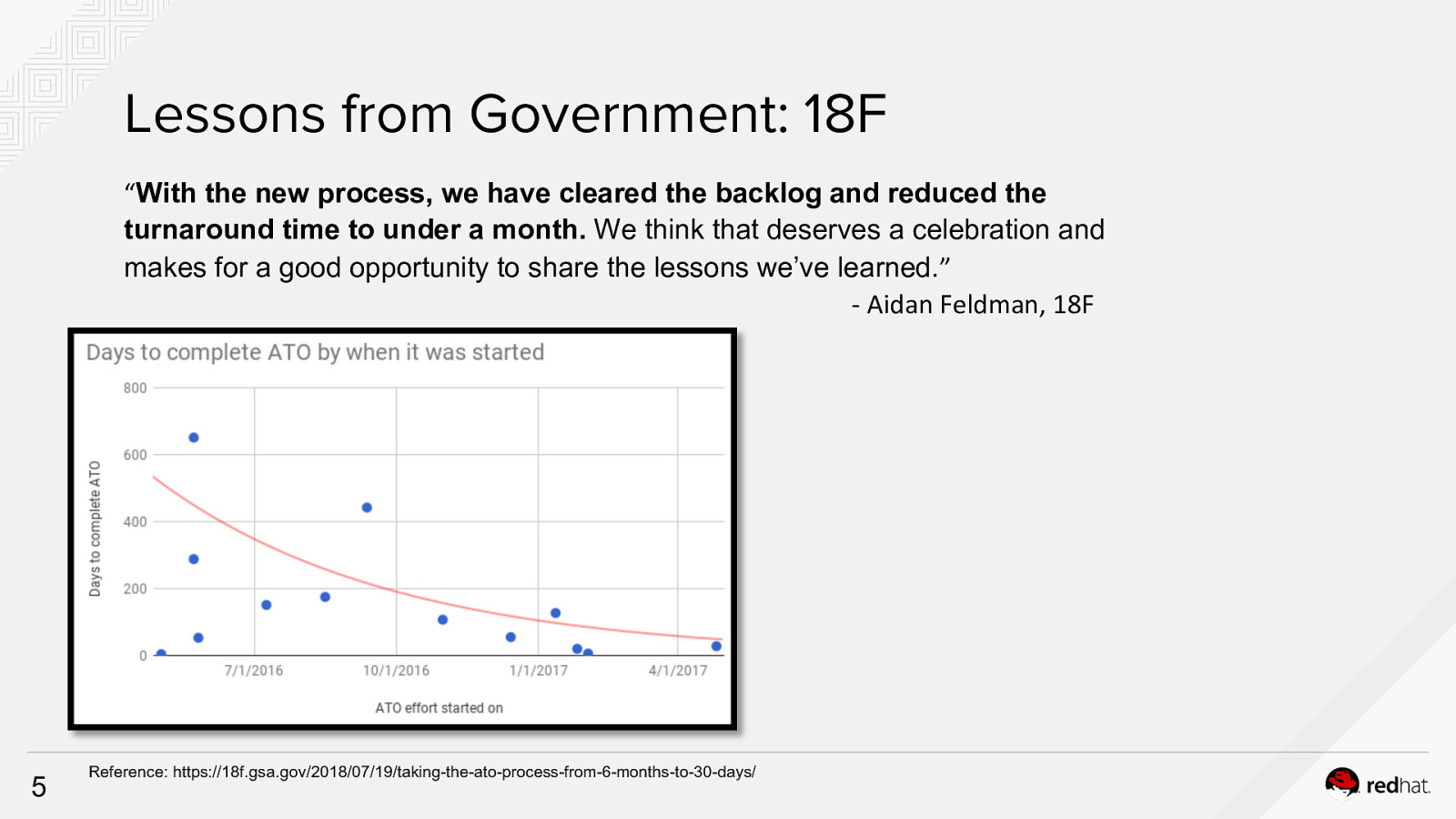
Lessons from Government: 18F “With the new process, we have cleared the backlog and reduced the turnaround time to under a month. We think that deserves a celebration and makes for a good opportunity to share the lessons we’ve learned.” - Aidan Feldman, 18F 5 Reference: https://18f.gsa.gov/2018/07/19/taking-the-ato-process-from-6-months-to-30-days/
Slide 6
A Challenge The FAA was encumbered by verifying security of system components upon receipt from system integrators. How could security be moved to an acquisition requirement? 6
Slide 7
Common Criteria (CC) is an international set of guidelines and specifications developed for evaluating information security products, specifically to ensure they meet an agreed-upon security standard for government deployments 7
Slide 8
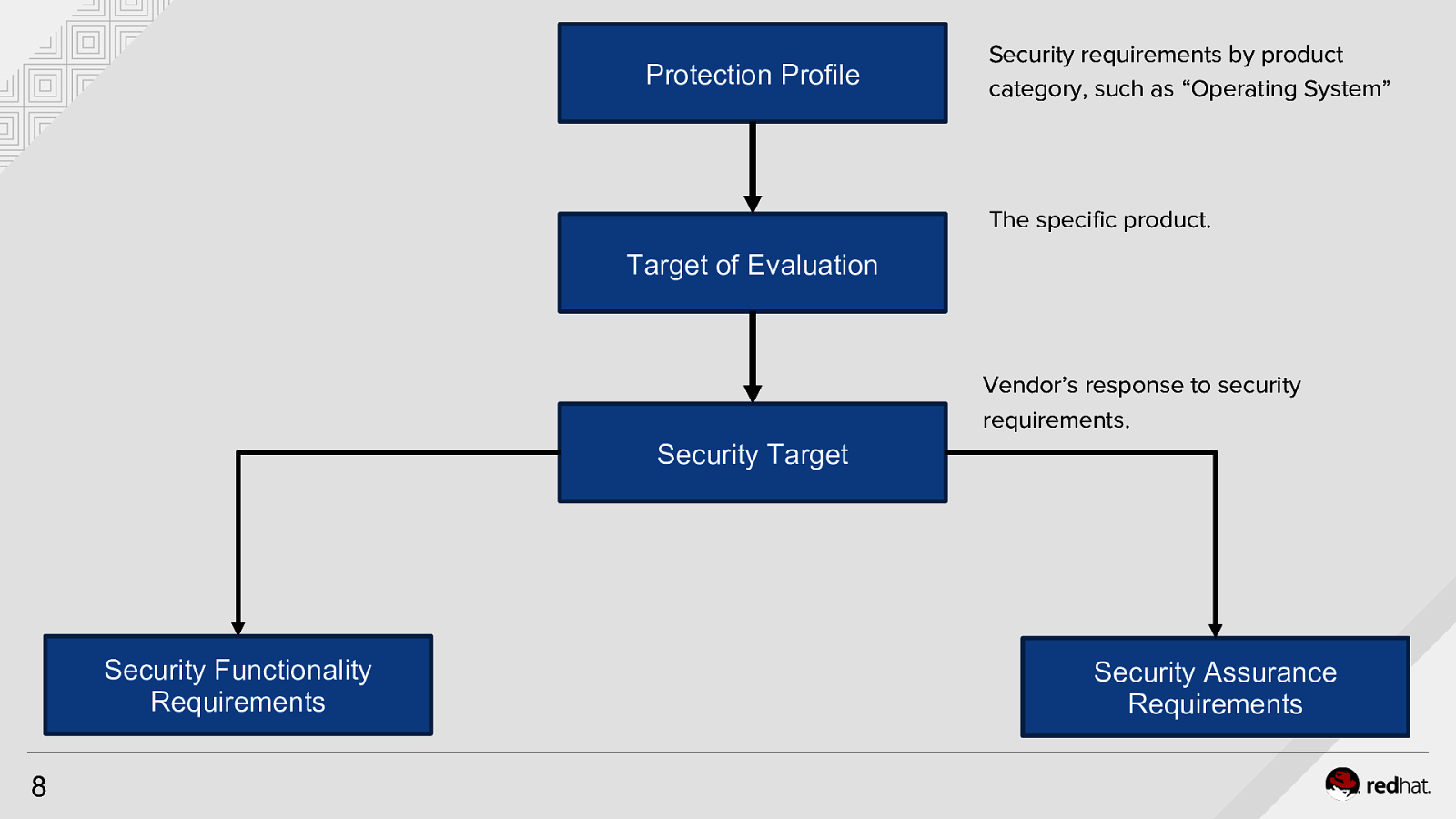
Protection Profile Security requirements by product category, such as “Operating System” The specific product. Target of Evaluation Vendor’s response to security requirements. Security Target Security Functionality Requirements 8 Security Assurance Requirements
Slide 9
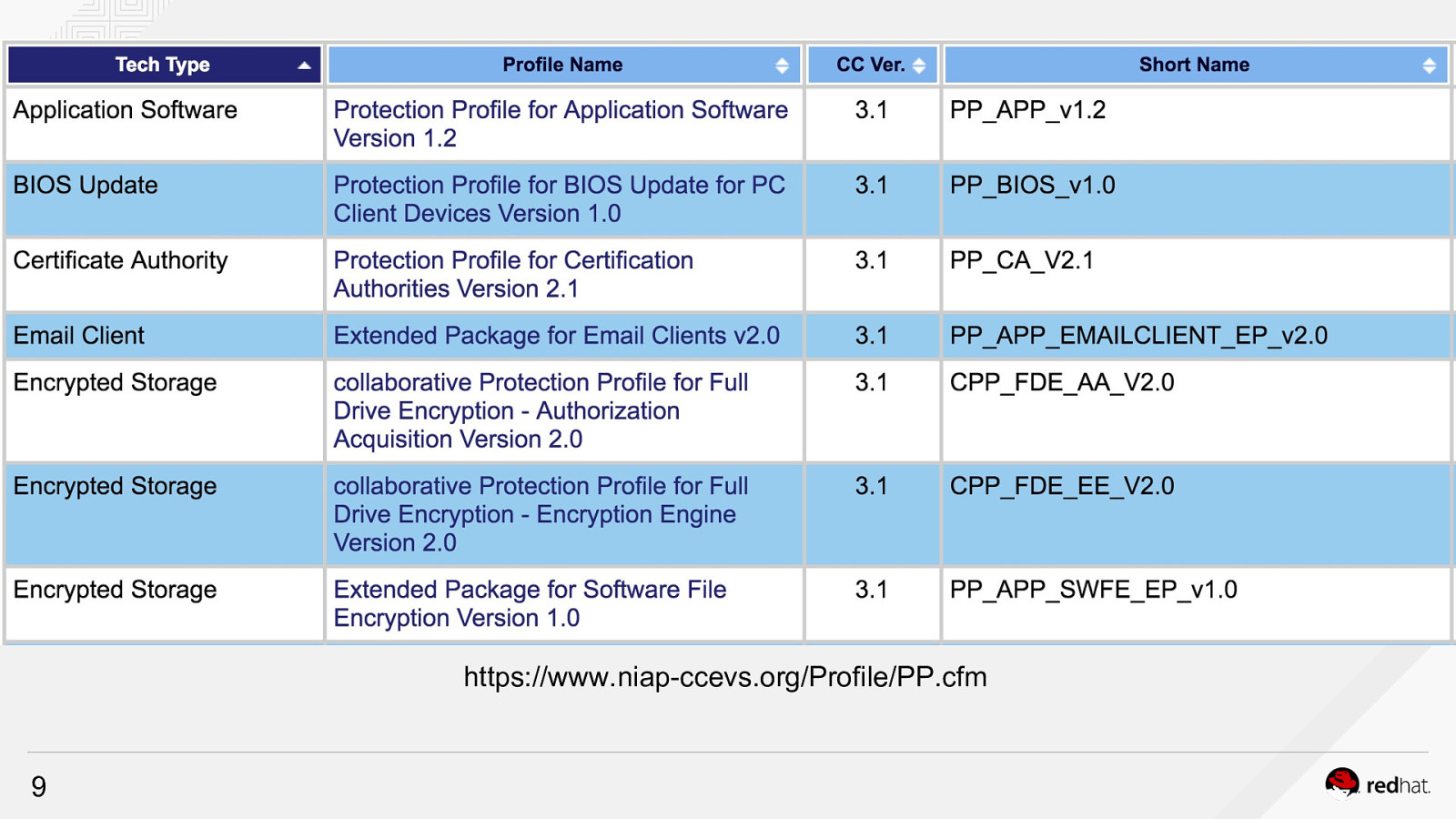
https://www.niap-ccevs.org/Profile/PP.cfm 9
Slide 10
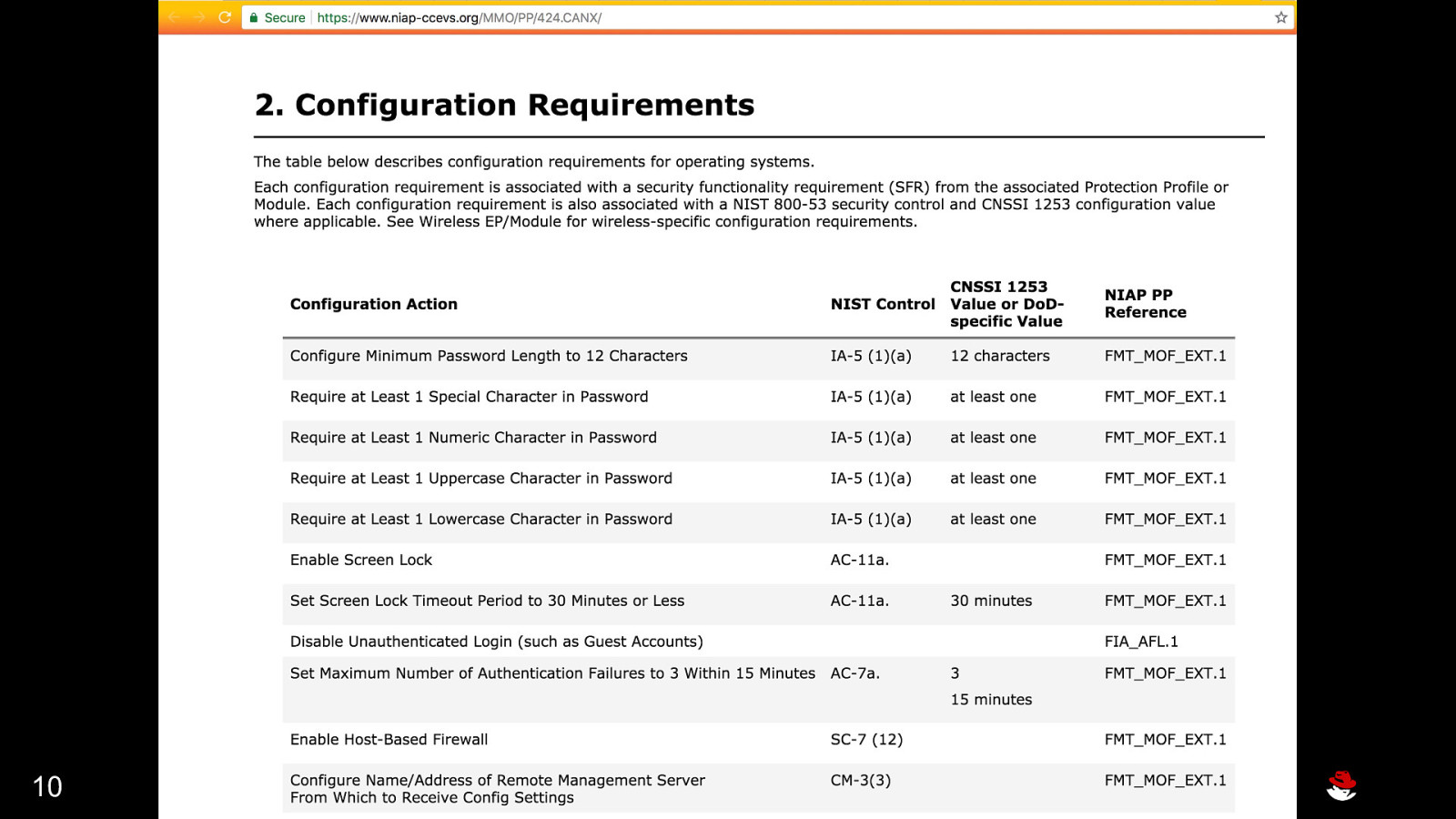
10
Slide 11
A Challenge Army Cyber required dozens of applications for defensive operations. Those applications required complicated collaboration during installation and integration every time they were deployed. 1 1
Slide 12

1 2
Slide 13
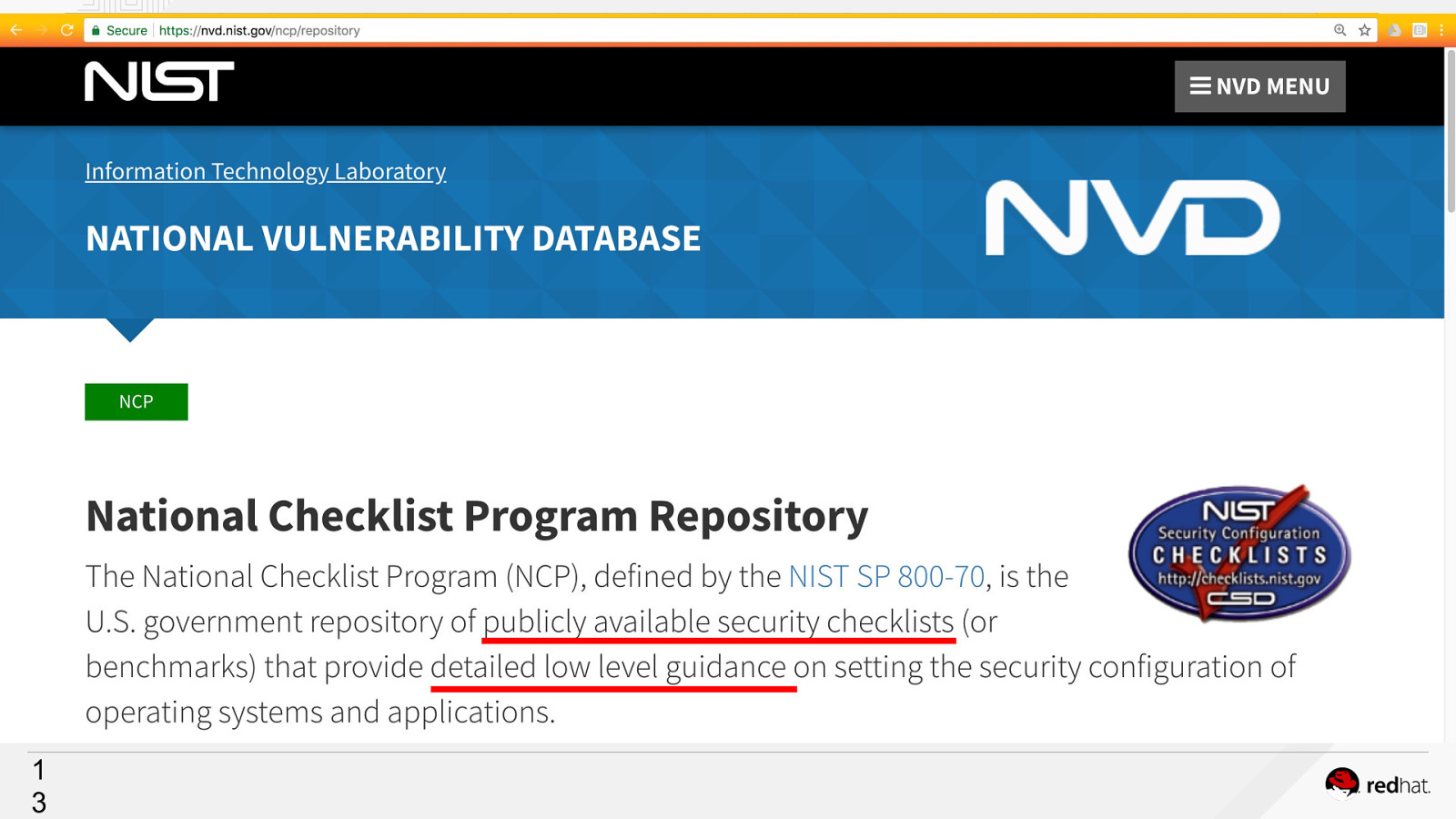
1 3
Slide 14
A Challenge Cyber attacks are happening across government. Not everyone can standup a multi-million dollar security operations center. How can we share cyber insights? How can we create a government-wide awareness of cyber events? 14
Slide 15
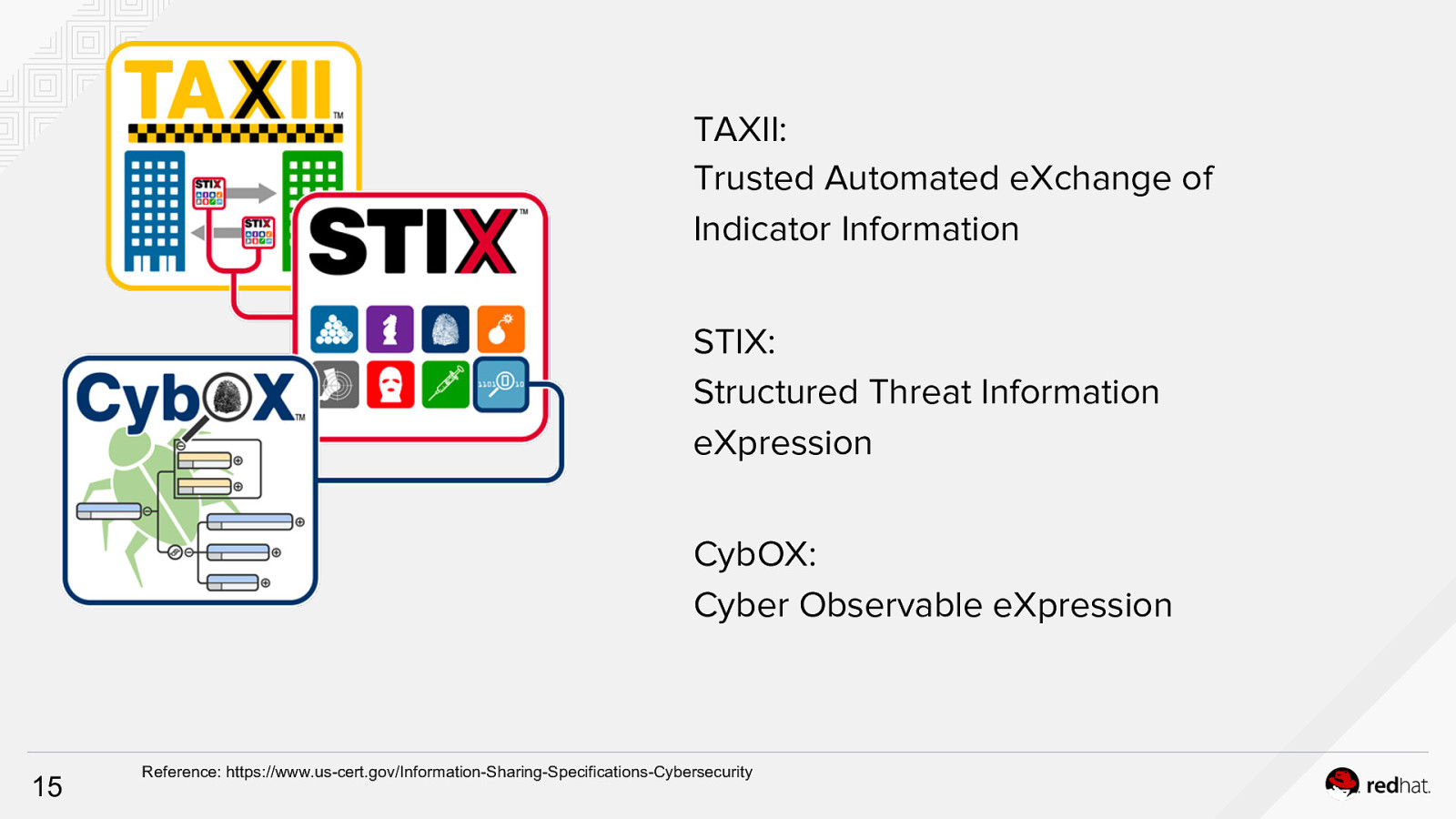
TAXII: Trusted Automated eXchange of Indicator Information STIX: Structured Threat Information eXpression CybOX: Cyber Observable eXpression 15 Reference: https://www.us-cert.gov/Information-Sharing-Specifications-Cybersecurity
Slide 16
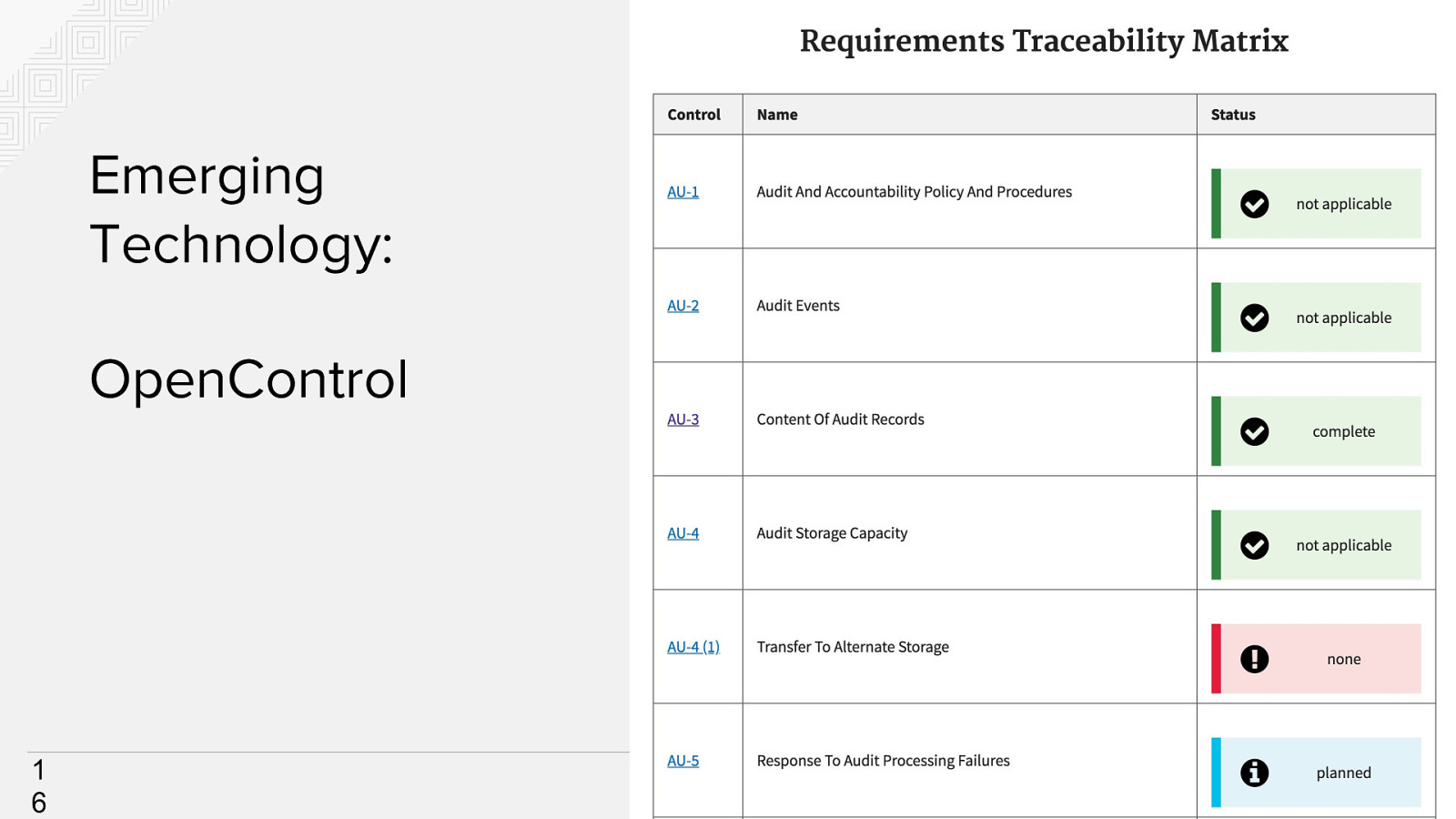
Emerging Technology: OpenControl 1 6
Slide 17
Thank you! 17 EMail: shawn@redhat.com LinkedIn: https://www.linkedin.com/in/shawndwells/ Cell: 443-534-0130 (US EST)