Red Hat Security Update SHAWN WELLS Unclass: shawn@redhat.com JWICS: wellshaw@nro.ic.gov (+1) 443-534-0130 THIS BRIEFING IS UNCLASSIFIED 1
Slide 1

Slide 2

In the next hour … - Factual information to answer security compliance questions - Learn how to use Red Hat security compliance as a competitive advantage during sales cycle - Understand where Red Hat technologies & services fit into certification and accreditation stages of the deal
Slide 3
Understanding Common Criteria - Internationally standardized evaluation process to validate commercial technologies perform as advertised
Slide 4
Understanding Common Criteria - Internationally standardized evaluation process to validate commercial technologies perform as advertised - NSTISSP No. 11: Mandates government agencies only procure software which has been FIPS and Common Criteria certified. Effective since 1-JULY-2002. - No waiver process! - Products “In Evaluation” may receive conditional Deferred Compliance Authorization (DCA), which will be revoked if technology fails to pass Common Criteria
Slide 5
Understanding Common Criteria - Internationally standardized evaluation process to validate commercial technologies perform as advertised - NSTISSP No. 11: Mandates government agencies only procure software which has been FIPS and Common Criteria certified. Effective since 1-JULY-2002. - No waiver process! - Products “In Evaluation” may receive conditional Deferred Compliance Authorization (DCA), which will be revoked if technology fails to pass Common Criteria - Reviews development processes in addition to capabilities
Slide 6
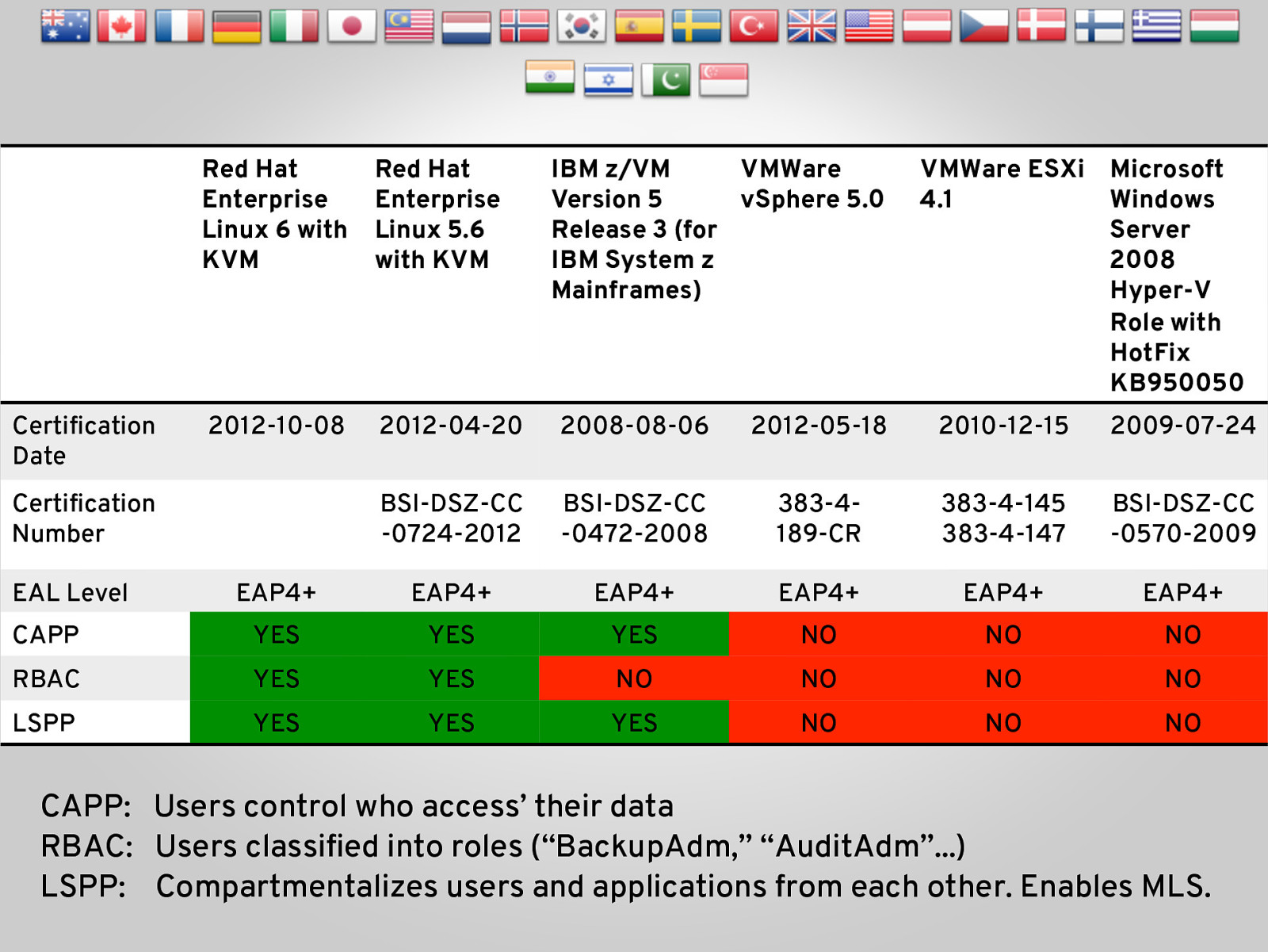
Red Hat Enterprise Linux 6 with KVM Red Hat Enterprise Linux 5.6 with KVM 2012-10-08 2012-04-20 2008-08-06 2012-05-18 2010-12-15 2009-07-24 BSI-DSZ-CC -0724-2012 BSI-DSZ-CC -0472-2008 383-4189-CR 383-4-145 383-4-147 BSI-DSZ-CC -0570-2009 EAP4+ EAP4+ EAP4+ EAP4+ EAP4+ EAP4+ CAPP YES YES YES NO NO NO RBAC YES YES NO NO NO NO LSPP YES YES YES NO NO NO Certification Date Certification Number EAL Level IBM z/VM VMWare Version 5 vSphere 5.0 Release 3 (for IBM System z Mainframes) VMWare ESXi Microsoft 4.1 Windows Server 2008 Hyper-V Role with HotFix KB950050 CAPP: Users control who access’ their data RBAC: Users classified into roles (“BackupAdm,” “AuditAdm”…) LSPP: Compartmentalizes users and applications from each other. Enables MLS.
Slide 7
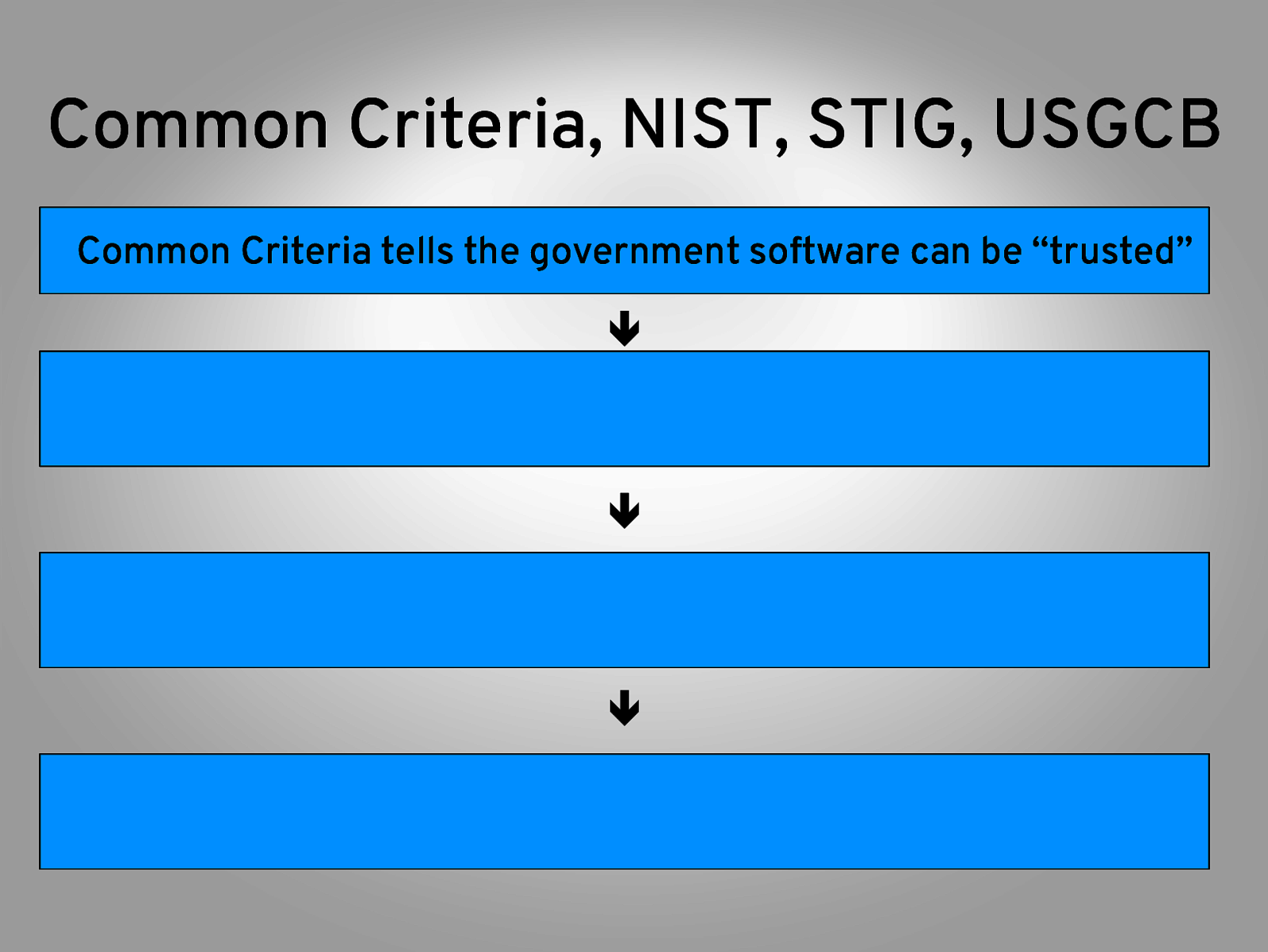
Common Criteria, NIST, STIG, USGCB Common Criteria tells the government software can be “trusted” ê ê ê
Slide 8
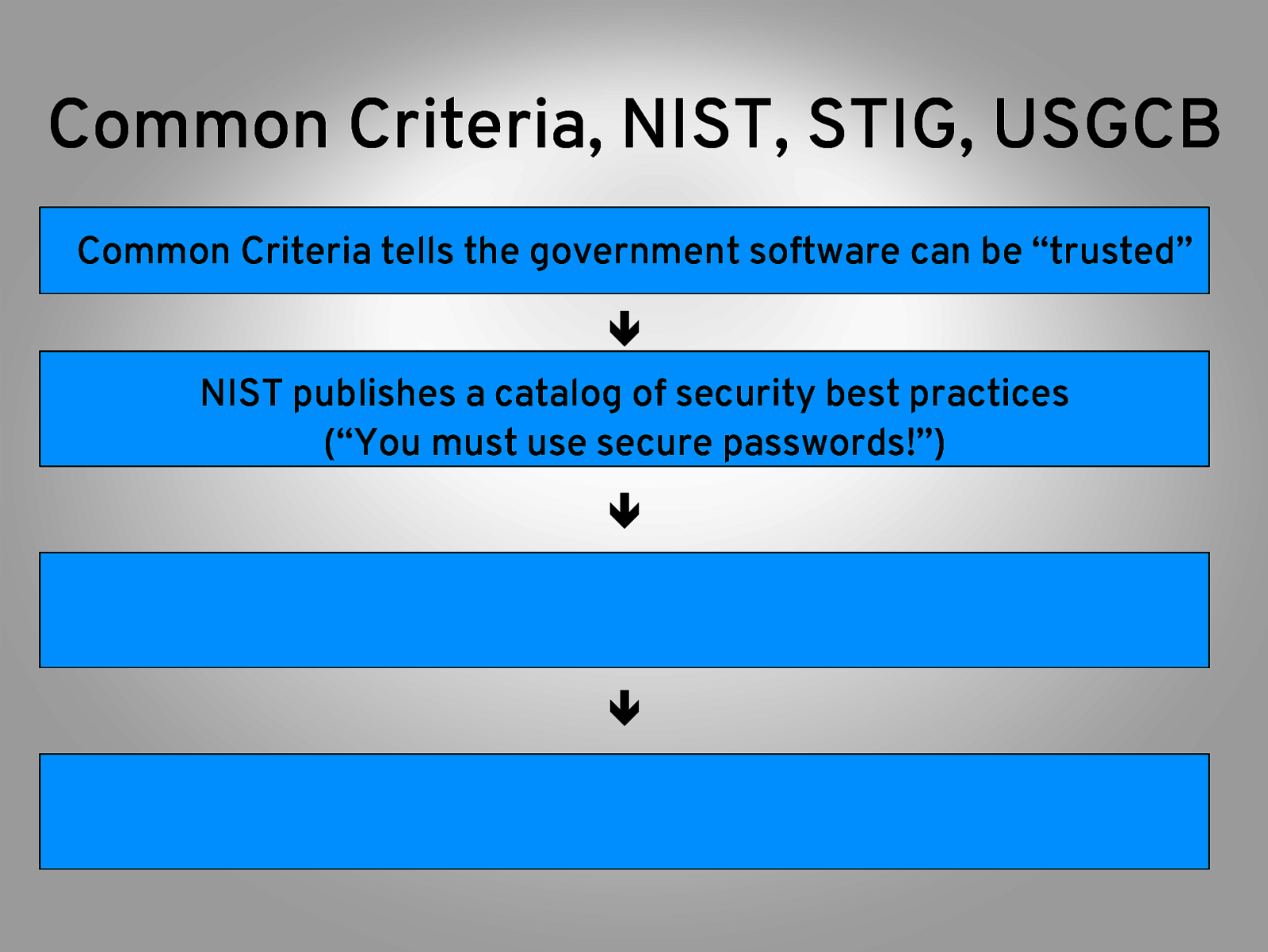
Common Criteria, NIST, STIG, USGCB Common Criteria tells the government software can be “trusted” ê NIST publishes a catalog of security best practices (“You must use secure passwords!”) ê ê
Slide 9
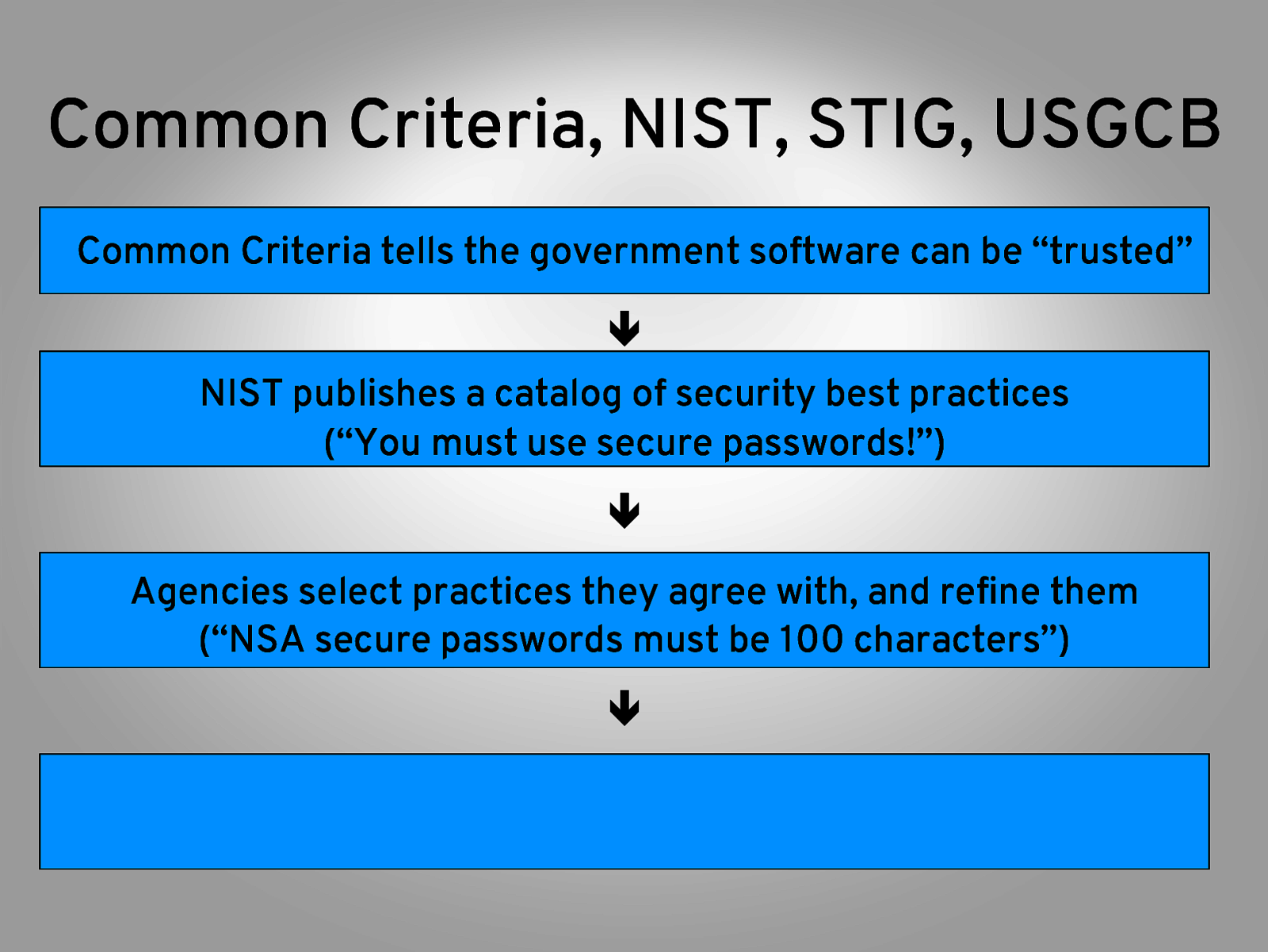
Common Criteria, NIST, STIG, USGCB Common Criteria tells the government software can be “trusted” ê NIST publishes a catalog of security best practices (“You must use secure passwords!”) ê Agencies select practices they agree with, and refine them (“NSA secure passwords must be 100 characters”) ê
Slide 10
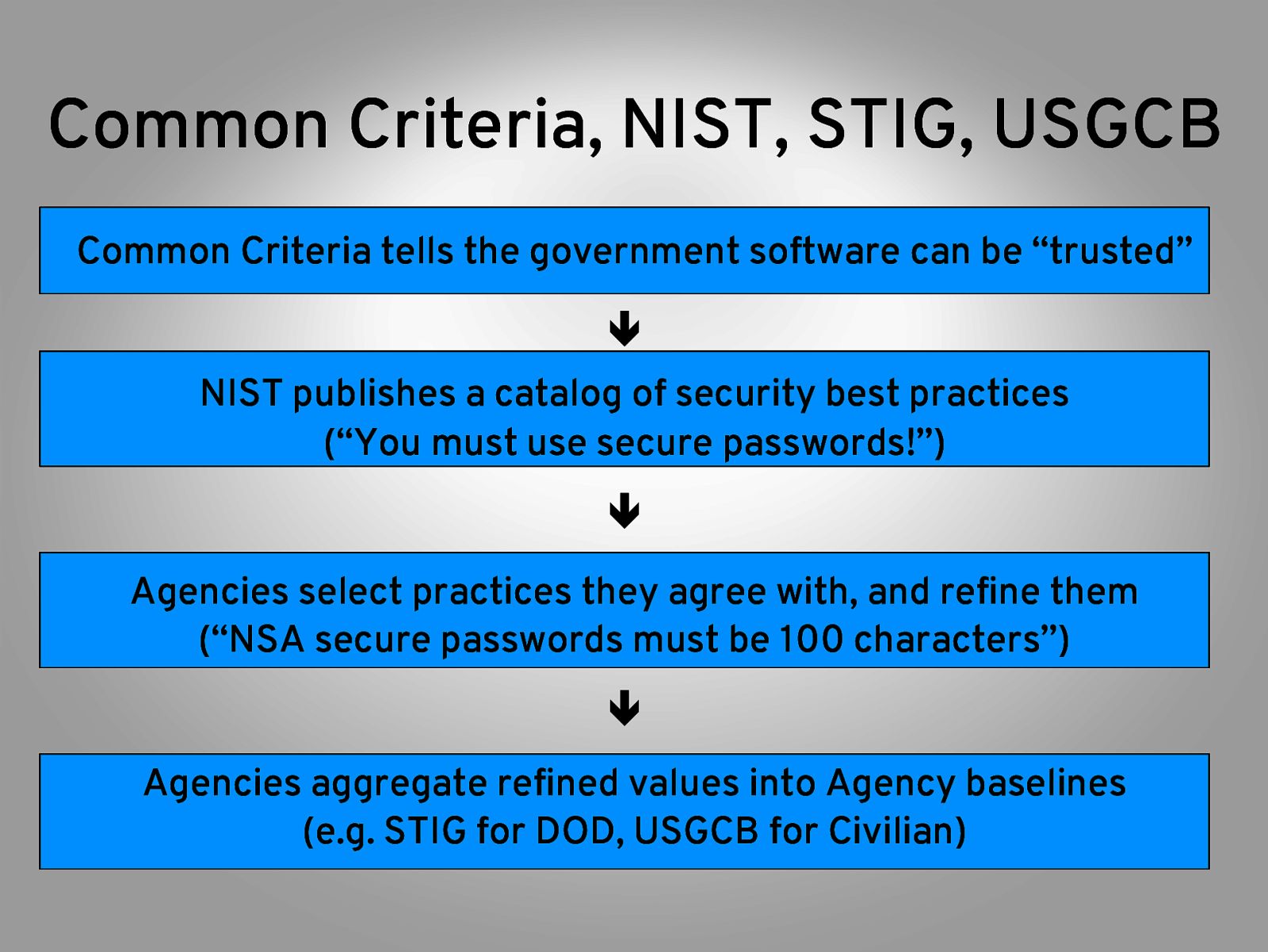
Common Criteria, NIST, STIG, USGCB Common Criteria tells the government software can be “trusted” ê NIST publishes a catalog of security best practices (“You must use secure passwords!”) ê Agencies select practices they agree with, and refine them (“NSA secure passwords must be 100 characters”) ê Agencies aggregate refined values into Agency baselines (e.g. STIG for DOD, USGCB for Civilian)
Slide 11
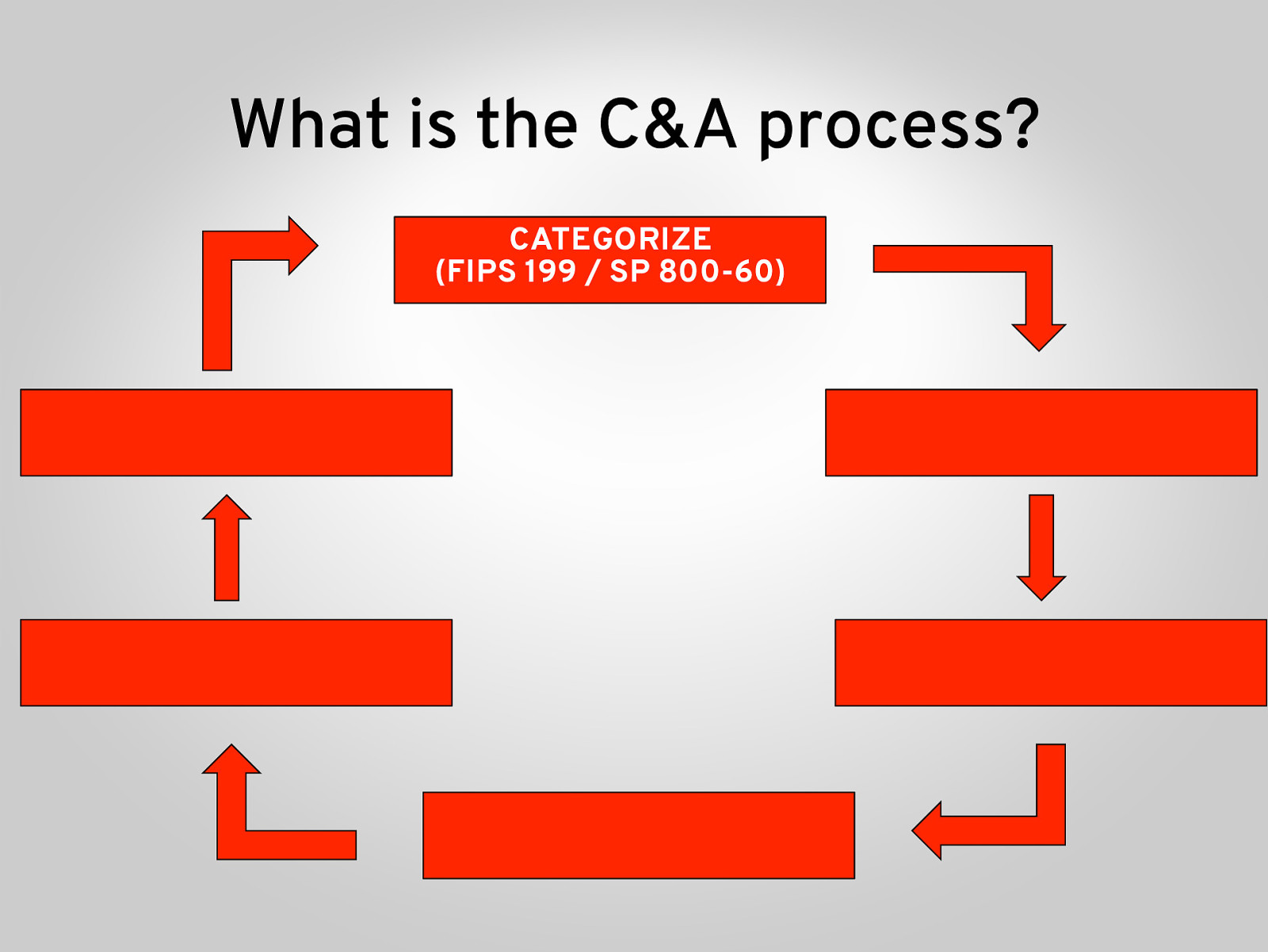
What is the C&A process? CATEGORIZE (FIPS 199 / SP 800-60)
Slide 12
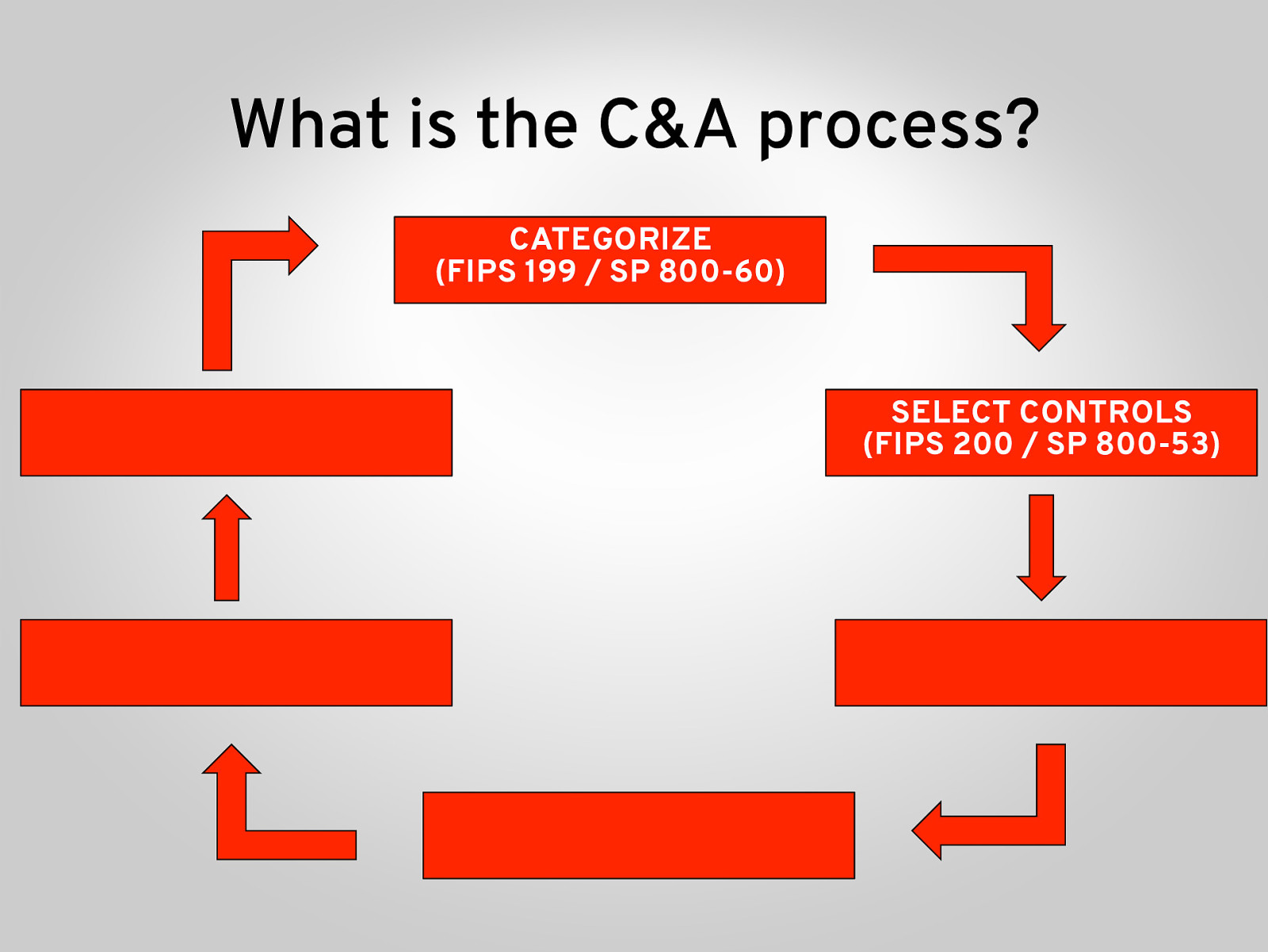
What is the C&A process? CATEGORIZE (FIPS 199 / SP 800-60) SELECT CONTROLS (FIPS 200 / SP 800-53)
Slide 13
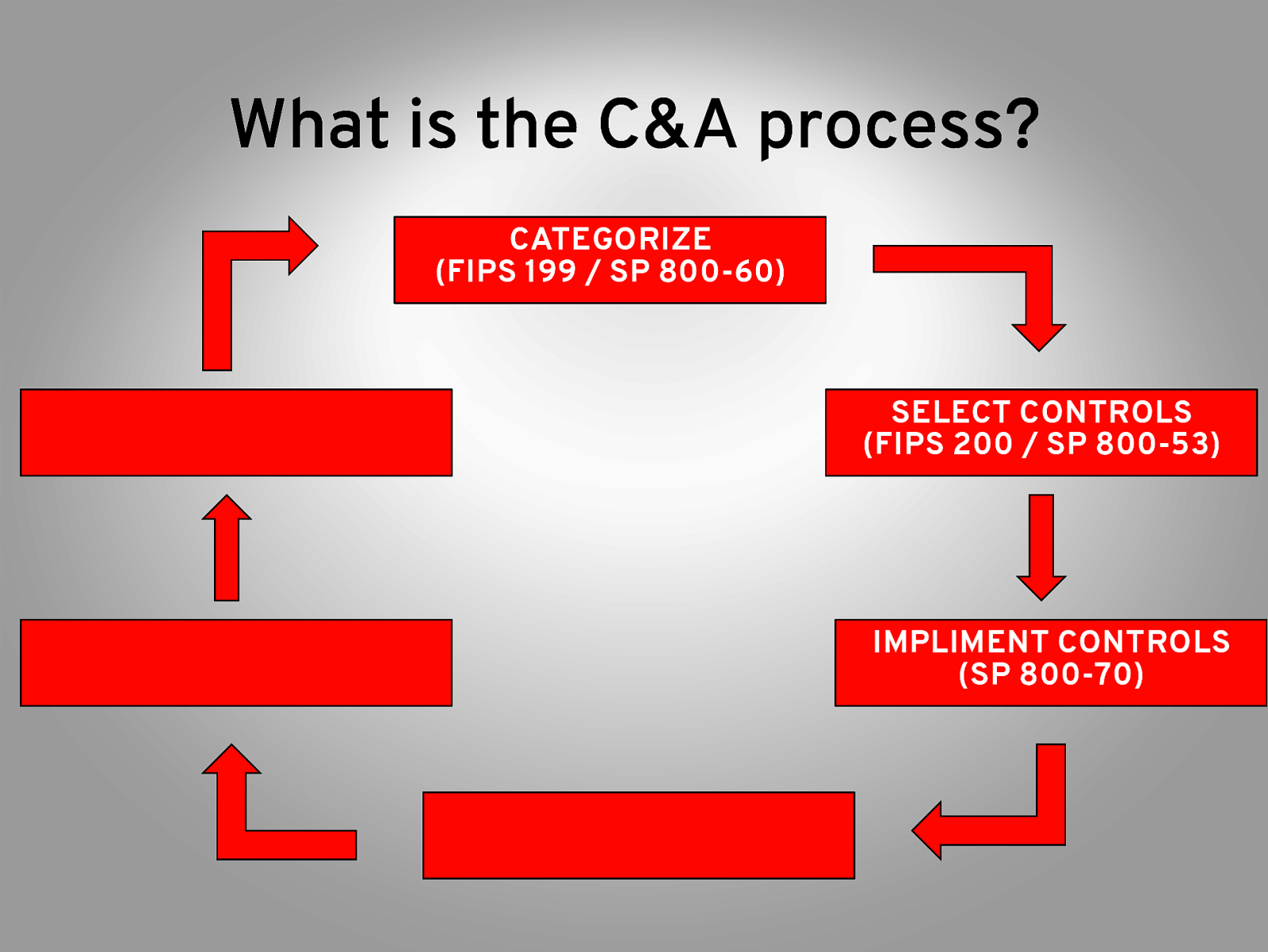
What is the C&A process? CATEGORIZE (FIPS 199 / SP 800-60) SELECT CONTROLS (FIPS 200 / SP 800-53) IMPLIMENT CONTROLS (SP 800-70)
Slide 14
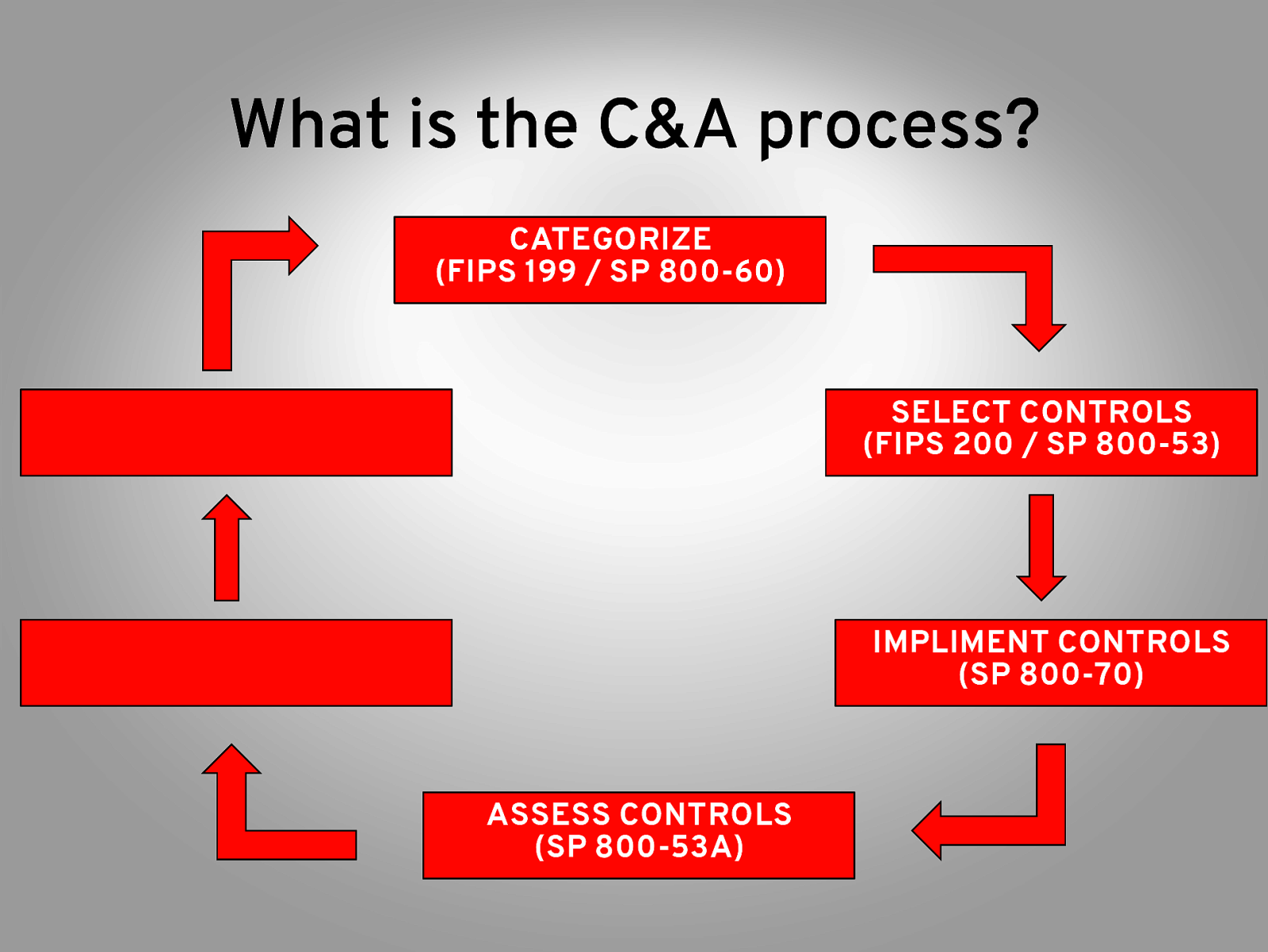
What is the C&A process? CATEGORIZE (FIPS 199 / SP 800-60) SELECT CONTROLS (FIPS 200 / SP 800-53) IMPLIMENT CONTROLS (SP 800-70) ASSESS CONTROLS (SP 800-53A)
Slide 15
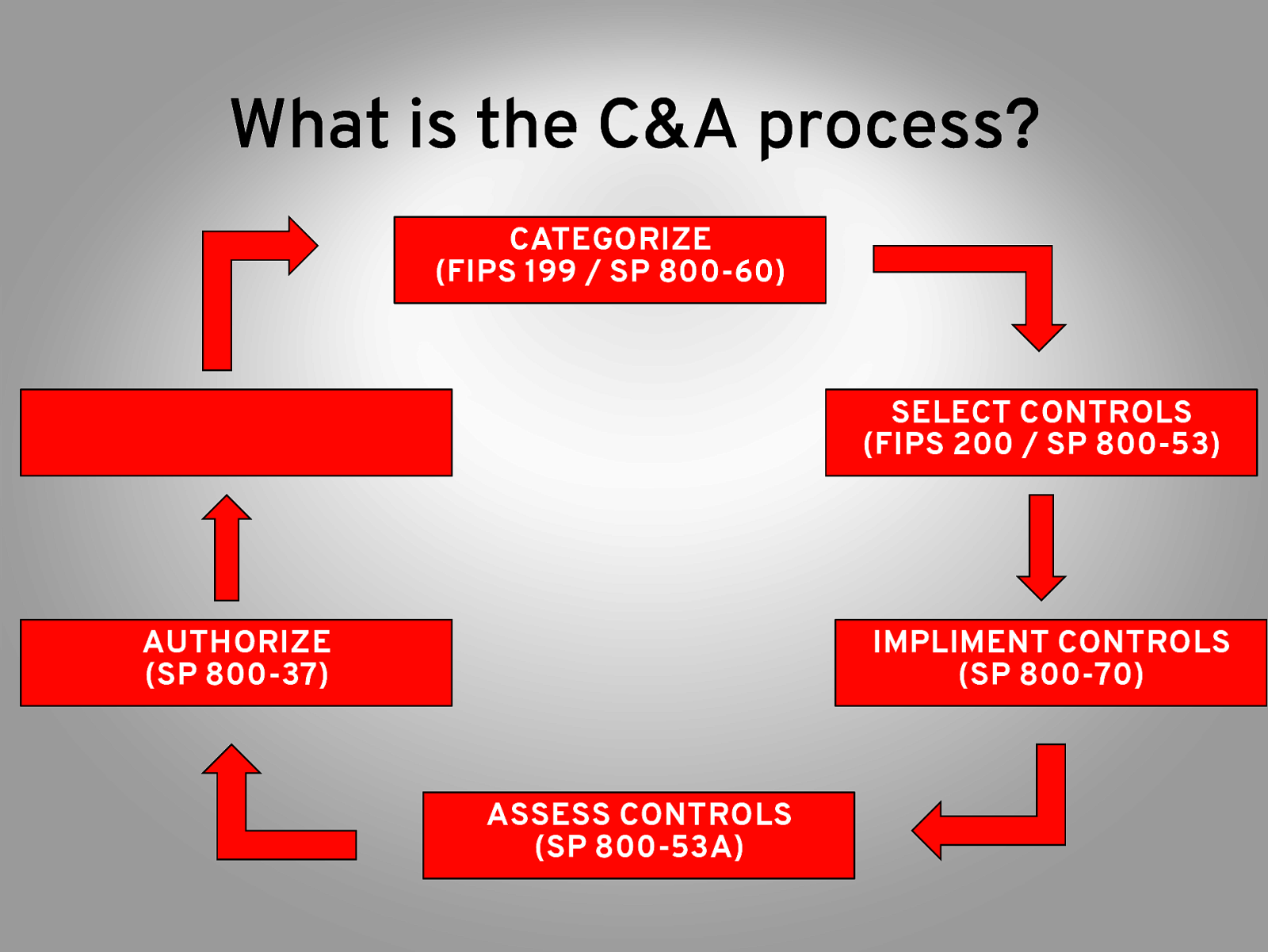
What is the C&A process? CATEGORIZE (FIPS 199 / SP 800-60) SELECT CONTROLS (FIPS 200 / SP 800-53) AUTHORIZE (SP 800-37) IMPLIMENT CONTROLS (SP 800-70) ASSESS CONTROLS (SP 800-53A)
Slide 16
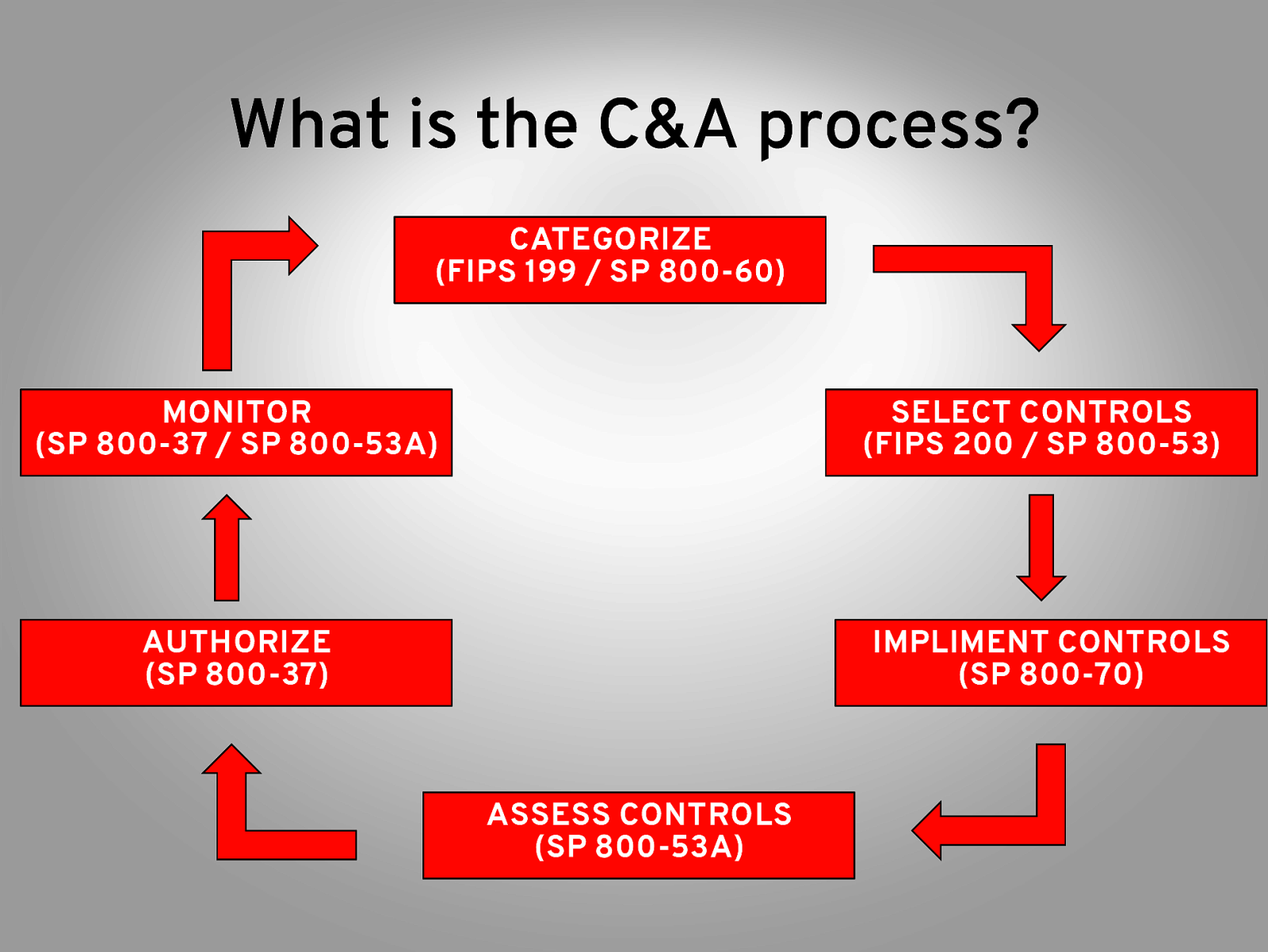
What is the C&A process? CATEGORIZE (FIPS 199 / SP 800-60) MONITOR (SP 800-37 / SP 800-53A) SELECT CONTROLS (FIPS 200 / SP 800-53) AUTHORIZE (SP 800-37) IMPLIMENT CONTROLS (SP 800-70) ASSESS CONTROLS (SP 800-53A)
Slide 17
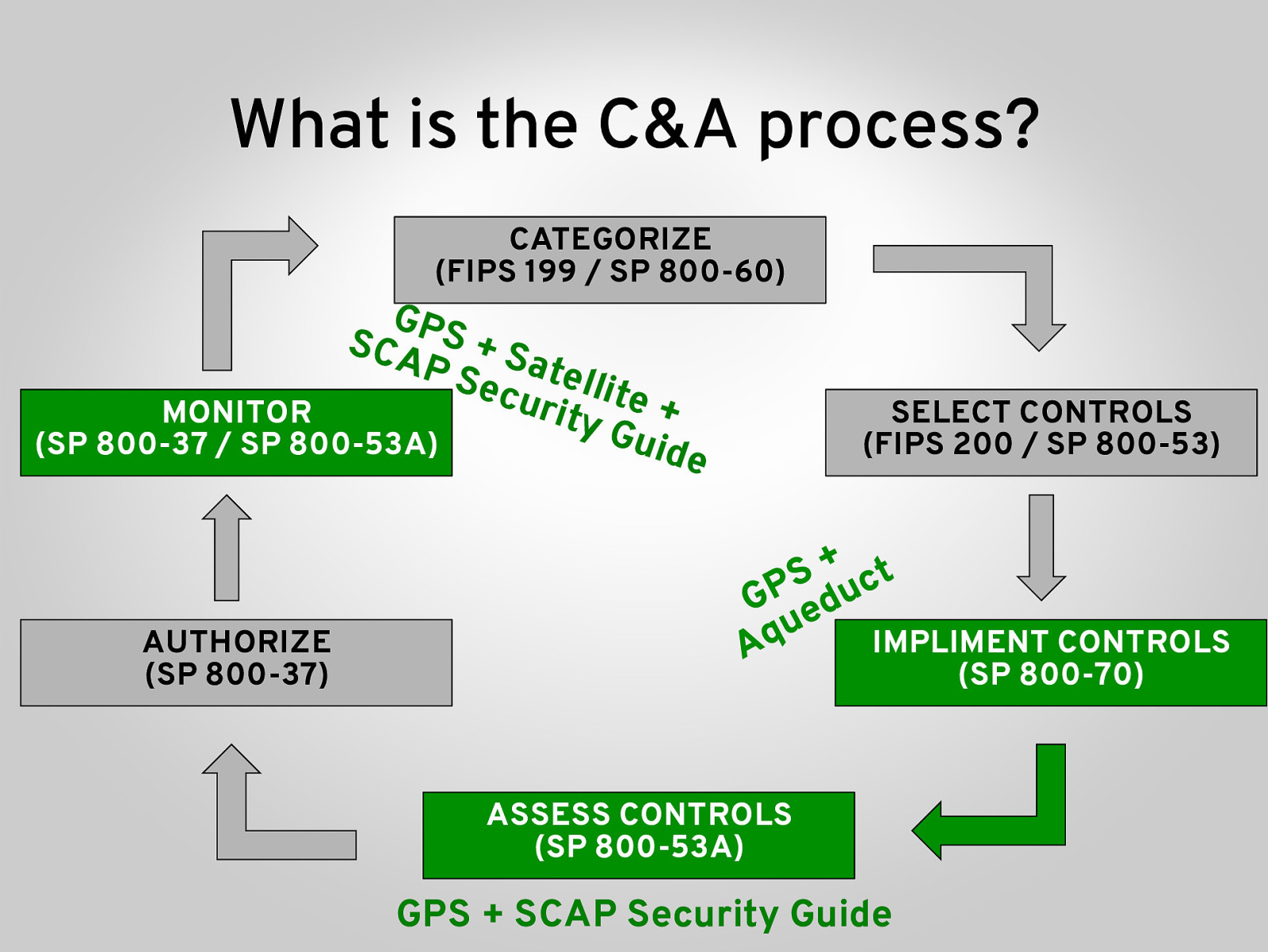
What is the C&A process? CATEGORIZE (FIPS 199 / SP 800-60) GPS SCA + S P S atell ecu i te + r MONITOR i ty G uide (SP 800-37 / SP 800-53A) AUTHORIZE (SP 800-37) SELECT CONTROLS (FIPS 200 / SP 800-53) IMPLIMENT CONTROLS (SP 800-70) ASSESS CONTROLS (SP 800-53A) GPS + SCAP Security Guide
Slide 18
